Chapter 17. Cyber Terrorism
Chapter Objectives
After reading this chapter and completing the exercises, you will be able to do the following:
![]() Defend against computer-based espionage.
Defend against computer-based espionage.
![]() Employ defenses against computer-based terrorism.
Employ defenses against computer-based terrorism.
![]() Choose appropriate defense strategies for your network.
Choose appropriate defense strategies for your network.
![]() Employ defenses against information warfare.
Employ defenses against information warfare.
Introduction
To this point, we have covered a wide variety of threats to computer networks, but these threats have primarily been carried out by lone perpetrators, including virus infections that spread randomly via e-mail and the Internet. Because computer systems and networks are such an integral part of all types of organizations, it is only natural that they have become a primary target for espionage and terrorism. Computer-based espionage, which is the use of computer systems to obtain confidential information, can be directed at all types of organizations, including businesses, governments, and political organizations. Because most sensitive data is stored on computer systems, it is only reasonable to assume that most illegal efforts to acquire that data will be a remote attack via the computer network.
The threat of computer-based terrorist acts, or cyber terrorism, is also growing. People around the world are aware of the threat of terrorist attacks in the form of bombs, hijackings, releasing a biological agent, or other means. Unfortunately, many people have not considered the possibility of cyber terrorism. Cyber terrorism is the use of computers and the Internet connectivity between them to launch a terrorist attack. It is a strong possibility that, in time, someone or some group will use computer methods to launch a military or terrorist attack against our nation. Some experts make the case that the MyDoom virus was an example of domestic economic terrorism.
Defending Against Computer-Based Espionage
Espionage is not necessarily making daring midnight raids into the files of some foreign government. Though that scenario makes the best plots for movies, espionage is simply any attempt to acquire information to which you do not have legitimate access. Whether by law or by some company policy, the person perpetrating espionage is not supposed to be accessing this information but is trying to do so anyway. Generally speaking, a spy wishes to get unauthorized information without anyone realizing he has acquired the data, so espionage is best conducted without any of the drama typically shown in novels or movies.
A variety of motives can lead a person or organization to engage in espionage. Most people think of political/military motivations for espionage, and those often are the motivation for spying. However, there are also economic motivations that might lead one to commit acts of espionage. It is a widely known fact that some businesses will purchase information from less-than-reputable sources. This information might well be sensitive data from a competitor.
Consider that most business data, scientific research data, and even military data is stored on computer systems and transmitted over telecommunications lines. As a result, any person or group interested in retrieving that data illicitly can attempt to compromise the security of those systems to get the data rather than attempt to physically infiltrate the target organization. This means that the tactics we have discussed for hackers can also be used for illicitly gathering information from a target. Of course, spyware can also play a role in computer-based espionage. Having spyware on a target computer can allow an intruder access to sensitive data directly from the machine that is producing the data.
Even if a person is physically located within the organization and wishes to steal information, computer technology can be used to facilitate this process. Employees from within an organization are frequently the source for leaks of sensitive or confidential data. This can be for a variety of reasons, including any of the following:
![]() For money: The person will be compensated by some other party who is interested in the data.
For money: The person will be compensated by some other party who is interested in the data.
![]() Due to a grudge: The person believes he has been wronged in some way and wishes to exact retribution.
Due to a grudge: The person believes he has been wronged in some way and wishes to exact retribution.
![]() Due to ideology: The person feels ideologically opposed to some course of action the organization is taking and chooses to divulge some information in order to disrupt the organization’s activities.
Due to ideology: The person feels ideologically opposed to some course of action the organization is taking and chooses to divulge some information in order to disrupt the organization’s activities.
Whatever the motivation, you must be aware that it is entirely possible for a member of your organization to divulge data to an outside party. Technology makes this easier to do. A person carrying out boxes of documents is likely to arouse suspicion, but a USB flash drive or CD fits in a pocket or briefcase. Camera-enabled cell phones can be used to photograph diagrams, screens, and so on and to send them to some other party. Some companies ban the use of camera cell phones as well as removing portable media (floppy drives, CD drives, etc.) from workstations. These measures may be more extreme than most organizations require. Even so, you must take some steps to decrease the danger posed by members of your own organization disclosing data. The following list includes 11 steps you might take. You must make the decision of which steps to include based on a complete assessment of the organization’s security needs:
1. Always use all reasonable network security: firewalls, intrusion-detection software, anti-spyware, patching and updating the operating system, and proper usage policies.
2. Give the personnel of the company access to only the data that they absolutely need to perform their jobs. Use a “need-to-know” approach. One does not want to stifle discussion or exchange of ideas, but sensitive data must be treated with great care.
3. If possible, set up a system for those employees with access to the most sensitive data in which there is a rotation and/or a separation of duties. In this way, no one employee has access and control over all critical data at one time.
4. Limit the number of portable storage media in the organization (such as CD burners, zip disks, and flash drives) and control access to these media. Log every use of such media and what was stored. Some organizations have even prohibited cell phones because many phones allow the user to photograph items and send the pictures electronically.
5. Do not allow employees to take documents/media home. Bringing materials home may indicate a very dedicated employee working on her own time or a corporate spy copying important documents and information.
6. Shred documents and melt old disks/tape backups/CDs. A resourceful spy can often find a great deal of information in the garbage.
7. Do employee background checks. You must be able to trust your employees, and you can only do this with a thorough background check. Do not rely on “gut feelings.” Give particular attention to information technology (IT) personnel who will, by the nature of their jobs, have a greater access to a wider variety of data. This scrutiny is most important with positions such as database administrators, network administrators, and network security specialists.
8. When any employee leaves the company, scan his or her PC carefully. Look for signs that inappropriate data was kept on that machine. If you have any reason to suspect any inappropriate usage, then store the machine for evidence in any subsequent legal proceedings.
9. Keep all tape backups, sensitive documents, and other media under lock and key, with limited access to them.
10. If portable computers are used, then encrypt the hard drives. Encryption prevents a thief from extracting useable data from a stolen laptop. A number of products on the market accomplish this encryption, including the following:
![]() TrueCrypt (http://www.truecrypt.org/). This is an open source product that is available for Macintosh, Windows or Linux and is very easy to use. It provides 256 bit AES Encryption.
TrueCrypt (http://www.truecrypt.org/). This is an open source product that is available for Macintosh, Windows or Linux and is very easy to use. It provides 256 bit AES Encryption.
![]() Bitlocker (http://windows.microsoft.com/en-us/windows7/products/features/bitlocker). Windows 7 introduced drive encryption with Bitlocker in the higher end versions of the product.
Bitlocker (http://windows.microsoft.com/en-us/windows7/products/features/bitlocker). Windows 7 introduced drive encryption with Bitlocker in the higher end versions of the product.
![]() CheckPoint software (http://www.checkpoint.com/products/full-disk-encryption/) makes a commercial drive encryption product that is fairly easy to use.
CheckPoint software (http://www.checkpoint.com/products/full-disk-encryption/) makes a commercial drive encryption product that is fairly easy to use.
11. Have all employees with access to any sensitive information sign non-disclosure agreements. Such agreements give you, the employer, a recourse should an ex-employee divulge sensitive data. It is amazing how many employers do not bother with this rather simple protection.
Unfortunately, following these simple rules will not make you totally immune to corporate espionage. However, using these strategies will make any such attempts much more difficult for any perpetrator and, thus, you will improve your organization’s data security.
Packet Sniffers
Clearly, spyware is an important method of espionage attack. A key logger can record passwords and usernames, a screen capture utility can create images of confidential documents, and even cookies can reveal sensitive information. However, all of these items require software to be physically installed on the target system. A packet sniffer, however, need not be on the target system in order to gather information. A packet sniffer is an application that intercepts packets traveling on a network or the Internet and copies their contents. Some packet sniffers simply give a raw dump of the contents in hexadecimal format. Other sniffers are more sophisticated. We will look at a few of the most widely used packet sniffers here.
CommView
CommView is available for purchase from www.tamos.com/download/main/, but there is also a free trial version you can download at the same URL. In addition to basic packet sniffing, it also gives you statistics regarding any packets it captures. There is also a version of CommView for wireless packet sniffing as well. There is even a 64-bit version of this product. This particular product was originally developed specifically for use by security professionals. The vendor, TamoSoft, produces security products for a number of major companies like Cisco and Lucent. As we explore other packet sniffers you will see that some of them were originally designed as tools for hackers. Recall in Chapter 11 we used hackers’ tools to analyze security vulnerabilities on your network.
When you first launch this product you will see a screen like the one shown in Figure 17.1. From the toolbar or the various drop-down menus you can select a number of options including:
![]() Start Capture
Start Capture
![]() Stop Capture
Stop Capture
![]() Change Settings/Rules
Change Settings/Rules
If you choose View Statistics, you see a screen like the one shown in Figure 17.2. From this dialog box, you can elect to view protocol type, source/destination IP or MAC address, packets per second, and more. This sort of information is more useful for network analysis than for packet interception.
After you have initiated packet capture, you can view packets on the main screen, including the raw hexadecimal contents, as shown in Figure 17.3. Once you have the hexadecimal contents of the packet, you can convert the hexadecimal data into actual readable text. The hexadecimal data is in ASCII Format and can be converted to ASCII Code, thus yielding the actual data contained in the packet. Note that this screenshot was taken from a live system, so some portions are redacted.
EtherDetect
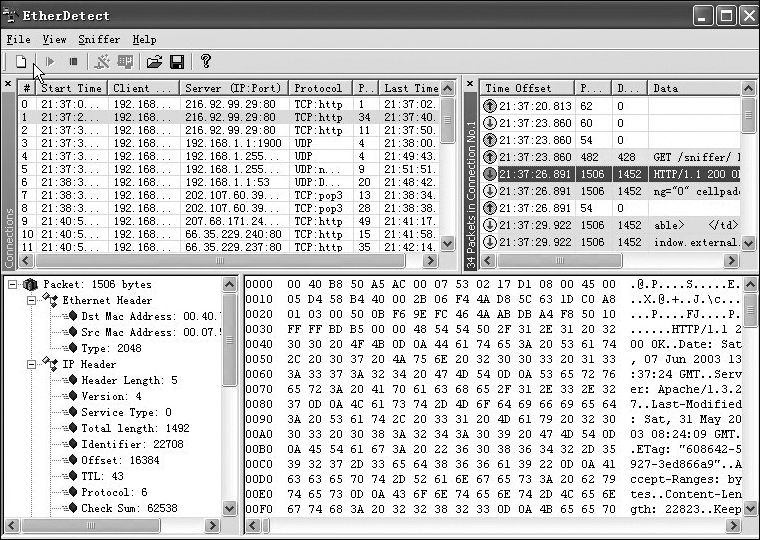
EtherDetect is a widely known and used Windows-based packet sniffer available at www.etherdetect.com/. It is unclear whether EtherDetect was originally developed for security professionals or for hackers. However, some of its features, such as the ability to focus on specific packets, seem more appropriate for hackers. This, however, makes it an excellent tool for a security professional to study. This packet sniffer is much simpler than CommView; however, it also is not as feature-rich. For example, it does not offer the statistical analysis or graphs of CommView, but for basic packet sniffing, it does just fine. In Figure 17.4 you can see the output from EtherDetect, including the raw packet information.
Ethereal
The primary strength of Ethereal (http://download.cnet.com/Ethereal-Network-Protocol-Analyzer/3000-2085_4-10492160.html)is the fact that it works on multiple platforms. It is available for Windows, Linux, Solaris, and even Macintosh. It is also open source. That means that you can actually see the source code, and if you have the skills, modify it to suit your needs.
You can find many other packet sniffers on the Internet. The fact that these products are so widely available should make you realize that anyone can intercept and copy data from packets being sent. That is why you should, at a minimum, encrypt all data that leaves your network. You should also consider encrypting data that is going from PC to PC within your network. Many home wireless network kits offer the option of encrypting all wireless transmissions.
What to Look for with a Packet Sniffer
A packet sniffer can be of use to either a hacker or a security professional. The hacker is, obviously, hoping first and foremost to get data from the packets. If your data is unencrypted, then it can be read right out of the packet. Secondly she may be hoping to find out information about your network such as the IP address of servers, routers, or workstations. This information can be useful if she wishes to execute a Denial of Service attack, IP spoofing, or many other forms of attacks.
For the security professional, there are many things you might use a packet sniffer for:
![]() Checking to see if your packets are encrypted.
Checking to see if your packets are encrypted.
![]() Checking to see if the encryption is strong enough.
Checking to see if the encryption is strong enough.
![]() Establishing a baseline of normal activity on your network.
Establishing a baseline of normal activity on your network.
![]() Monitoring traffic when it exceeds the level of normal activity.
Monitoring traffic when it exceeds the level of normal activity.
![]() Looking for malformed packets. These may signal a buffer overflow attempt.
Looking for malformed packets. These may signal a buffer overflow attempt.
![]() Monitoring a suspected attempted DoS in progress.
Monitoring a suspected attempted DoS in progress.
The specifics of configuring a packet sniffer are unique to each product. However most offer very simple instructions that any competent network administrator can follow. Virtually all packet sniffers display the following data:
![]() Source IP address of the packet
Source IP address of the packet
![]() Destination IP address of the packet
Destination IP address of the packet
![]() Protocol of the packet
Protocol of the packet
![]() Contents of the packet, usually in hexadecimal form
Contents of the packet, usually in hexadecimal form
For some readers, getting information from hexadecimal form may be difficult. Remember that hexadecimal numbers can be easily converted to decimal with the free Windows calculator. Also many ASCII tables give hexadecimal and decimal. This is useful because this data you are viewing in a packet sniffer is, in most cases, simply ASCII codes. So once you convert the hexadecimal to its ASCII code you can put together the data.
Defending Against Computer-Based Terrorism
When discussing computer-based terrorism, or cyber terrorism, the first question might be “What is terrorism?” According to the FBI, “cyber terrorism is the premeditated, politically motivated attack against information, computer systems, computer programs, and data that results in violence against noncombatant targets by sub-national groups or clandestine agents” (Savino, 2000). In short, cyber terrorism is just like other forms of terrorism. It is only the means of the attack that has changed. Clearly the loss of life due to a cyber attack would be much less than that of a bombing. In fact it is highly likely that there would be no loss of life at all. However significant economic damage, disruptions in communications, disruptions in supply lines, and general degradation of the national infrastructure are all quite possible via the Internet.
There are several ways that a computer- or Internet-based terrorist attack could cause significant harm to a nation. These include:
![]() Direct economic damage
Direct economic damage
![]() Economic disruption
Economic disruption
![]() Compromising sensitive/military data
Compromising sensitive/military data
![]() Disrupting mass communications
Disrupting mass communications
Economic Attack
There are a variety of ways that a cyber attack can cause economic damage. Lost files and lost records are one way. In addition to stealing that data, it could simply be destroyed, in which case the data is gone and the resources used to accumulate and analyze the data are wasted. To use an analogy, consider that a malicious person could choose to simply destroy your car rather than steal it. In either case, you are without the car and will have to spend additional resources acquiring transportation.
In addition to simply destroying economically valuable data (remember that there is very little data that does not have some intrinsic value), there are other ways to cause economic disruption. Some of those ways include stealing credit cards, transferring money from accounts, and fraud. But it is a fact that anytime IT staff is involved with cleaning up a virus rather than developing applications or administering networks and databases, there is economic loss. The mere fact that companies now need to purchase antivirus software, intrusion-detection software, and hire computer security professionals means that computer crime has already caused economic damage to companies and governments around the world. However, the general damage caused by random virus outbreaks, lone hacking attacks, and online fraud is not the type of economic damage that is the focus of this chapter. This chapter is concerned with a concerted and deliberate attack against a particular target or targets for the exclusive purpose of causing direct damage.
A good way to get a firm grasp on the impact of this type of attack is to walk through a scenario. Group X (which could be an aggressive nation, terrorist group, activist group, or literally any group with the motivation to damage a particular nation) decides to make a concerted attack on our country. They find a small group of individuals (in this case, six) that are well versed in computer security, networking, and programming. These individuals, motivated either by ideology or monetary needs, are organized to create a coordinated attack. There are many possible scenarios under which they could execute such an attack and cause significant economic harm. The example outlined below is just one of those possible attack modalities. In this case, each individual has an assignment, and all assignments are designed to be activated on the same specific date.
![]() Team member one sets up several fake e-commerce sites. Each of these sites is only up for 72 hours and portends to be a major stock brokerage site. During the brief time they are up, the site’s real purpose is only to collect credit card numbers/bank account numbers and so forth. On the predetermined date, all of those credit card and bank numbers will be automatically, anonymously, and simultaneously posted to various bulletin boards/Web sites and newsgroups, making them available for any unscrupulous individual that wishes to use them.
Team member one sets up several fake e-commerce sites. Each of these sites is only up for 72 hours and portends to be a major stock brokerage site. During the brief time they are up, the site’s real purpose is only to collect credit card numbers/bank account numbers and so forth. On the predetermined date, all of those credit card and bank numbers will be automatically, anonymously, and simultaneously posted to various bulletin boards/Web sites and newsgroups, making them available for any unscrupulous individual that wishes to use them.
![]() Team member two creates a virus. This virus is contained in a Trojan horse. Its function is to delete key system files on the predetermined date. In the meantime, it shows a series of business tips or motivational slogans, making it a popular download with people in business.
Team member two creates a virus. This virus is contained in a Trojan horse. Its function is to delete key system files on the predetermined date. In the meantime, it shows a series of business tips or motivational slogans, making it a popular download with people in business.
![]() Team member three creates another virus. It is designed to create distributed Denial of Service attacks on key economic sites, such as those for stock exchanges or brokerage houses. The virus spreads harmlessly and is set to begin its distributed Denial of Service attack on the predetermined date.
Team member three creates another virus. It is designed to create distributed Denial of Service attacks on key economic sites, such as those for stock exchanges or brokerage houses. The virus spreads harmlessly and is set to begin its distributed Denial of Service attack on the predetermined date.
![]() Team members four and five begin the process of footprinting major banking systems, preparing to crack them on the predetermined date.
Team members four and five begin the process of footprinting major banking systems, preparing to crack them on the predetermined date.
![]() Team member six prepares a series of false stock tips to flood the Internet on the predetermined date.
Team member six prepares a series of false stock tips to flood the Internet on the predetermined date.
If each of these individuals is successful in his or her mission, on the predetermined date, several major brokerages and perhaps government economic sites are taken down, viruses flood networks, and files are deleted from the machines of thousands of businesspeople, economists, and stock brokers. Thousands of credit cards and bank numbers are released on the Internet, guaranteeing that many will be misused. It is also highly likely that the cracking team members four and five will have some success—meaning that possibly one or more banking systems are compromised. It does not take an economist to realize that this would easily cost hundreds of millions of dollars, perhaps even billions of dollars. A concerted attack of this nature could easily cause more economic damage to our country than most traditional terrorists attacks (i.e., bombings) have ever done.
You could extrapolate on this scenario and imagine not just one group of six cyber terrorists, but five groups of six—each group with a different mission and each mission designed to be committed approximately two weeks apart. In this scenario, the nation’s economy would literally be under siege for two and one-half months.
This scenario is not particularly far-fetched when you consider that, in past decades, nuclear scientists were sought after by various nations and terrorist groups. More recently, experts in biological weapons have been sought by these same groups. It seems extremely likely that these groups will see the possibilities of this form of terrorism and seek out computer security/hacking experts. Given that there are literally thousands of people with the requisite skills, it seems likely that a motivated organization could find a few dozen people willing to commit these acts.
Compromising Defense
Economic attacks seem the most likely form of attack because the process is relatively easy (for someone with appropriate technical skills) and it carries low risk for the attacker. However, more direct assaults on a nation’s national defense, via computer, are certainly possible. When computer security and national defense are mentioned together, the obvious thought that comes to mind is the possibility of some hacker breaking into highly secure systems at the Department of Defense, Central Intelligence Agency (CIA), or National Security Agency (NSA). However, such an intrusion into one of the most secure systems in the world is very unlikely—not impossible, but very unlikely. The most likely outcome of such an attack would be that the attacker is promptly captured. Such systems are hyper-secure, and intruding upon them is not as easy as some movies might suggest. By “hyper-secure,” think back to the numeric security ratings we gave in Chapter 12 and think about systems with a rating of 9 or 10. This means systems with intrusion detection, multiple firewalls, anti-spyware, honey pots, hardened operating systems, dedicated IT staff, and more. However, there are a number of scenarios in which breaking into less secure systems could jeopardize our national defense or put military plans at risk. Two such scenarios are outlined here.
Consider less sensitive military systems for a moment, for example, systems that are responsible for basic logistical operations (e.g., food, mail, fuel). If someone cracks one or more of these systems, he could perhaps obtain information that several C-141s (an aircraft often used for troop transports and parachute operations) are being routed to a base that is within flight distance of some city—a city that has been the focal point of political tensions. This same cracker (or team of crackers), also finds that a large amount of ammunition and food supplies, enough for, perhaps, 5,000 troops for two weeks, is simultaneously being routed to that base. Then on yet another low-security system the cracker (or team of crackers) notes that a given unit, for example, two brigades of the 82nd airborne division, have had all military leaves cancelled. It does not take a military expert to conclude that these two brigades are preparing to drop in on the target city and secure that target. Therefore, the fact that a deployment is going to occur, the size of the deployment, and the approximate time of that deployment have all been deduced without ever attempting to break into a high-security system.
Taking the previous scenario to the next level, assume the hacker gets deep into the low-security logistical systems. Then assume that he does nothing to change the routing of the members of the brigades or the transport planes—actions that might draw attention. However, he does alter the records for the shipment of supplies so that the supplies are delivered two days late and to the wrong base. So there would be two brigades potentially in harm’s way, without a resupply of ammunition or food en route. Of course, the situation could be rectified, but the units in question may go for some time without resupply—enough time, perhaps, to prevent them from successfully completing their mission.
These are just two scenarios in which compromising low-security/low-priority systems can lead to very significant military problems. This further illustrates the serious need for high security on all systems. Given the interconnectivity of so many components of both business and military computer systems, there clearly are no truly “low-priority” security systems.
General Attacks
The previously outlined scenarios involve specific targets with specific strategies. However, once a specific target is attacked, defenses can be readied for it. There are many security professionals that work constantly to thwart these specific attacks. What may be more threatening is a general and unfocused attack with no specific target. Consider the various virus attacks of late 2003 and early 2004. With the exception of MyDoom, which was clearly aimed at the Santa Cruz Organization, these attacks were not aimed at a specific target. However, the sheer volume of virus attacks and network traffic did cause significant economic damage. IT personnel across the globe dropped their normal projects to work to clean infected systems and to shore up the defenses of systems.
This leads to another possible scenario in which various cyber terrorists continuously release new and varied viruses, perform DoS attacks, and work to make the Internet in general, and e-commerce in particular, virtually unusable for a period of time. Such a scenario would actually be more difficult to combat, as there would not be a specific target to defend or a clear ideological motive to use as a clue to the identity of the perpetrators.
Certainly no incidents of the magnitude I have described in these scenarios have yet occurred. However, several smaller, less destructive incidents lend credence to the fear that cyber terrorism is a growing threat. These incidents were reported in testimony before the U.S. House of Representatives Special Oversight Panel on Terrorism Committee on Armed Services (Denning, 2000):
![]() In 1996, a computer hacker allegedly associated with the White Supremacist movement temporarily disabled a Massachusetts ISP and damaged part of the ISP’s record-keeping system. The ISP had attempted to stop the hacker from sending out worldwide racist messages under the ISP’s name. The hacker signed off with the threat, “You have yet to see true electronic terrorism. This is a promise.”
In 1996, a computer hacker allegedly associated with the White Supremacist movement temporarily disabled a Massachusetts ISP and damaged part of the ISP’s record-keeping system. The ISP had attempted to stop the hacker from sending out worldwide racist messages under the ISP’s name. The hacker signed off with the threat, “You have yet to see true electronic terrorism. This is a promise.”
![]() In 1998, ethnic Tamil guerrillas swamped Sri Lankan embassies with 800 e-mails a day over a two-week period. The messages read, “We are the Internet Black Tigers and we’re doing this to disrupt your communications.” Intelligence authorities characterized it as the first known attack by terrorists against a country’s computer systems.
In 1998, ethnic Tamil guerrillas swamped Sri Lankan embassies with 800 e-mails a day over a two-week period. The messages read, “We are the Internet Black Tigers and we’re doing this to disrupt your communications.” Intelligence authorities characterized it as the first known attack by terrorists against a country’s computer systems.
![]() During the Kosovo conflict in 1999, NATO computers were blasted with e-mail bombs and hit with DoS attacks by hacktivists protesting the NATO bombings. In addition, businesses, public organizations, and academic institutes received highly politicized virus-laden e-mails from a range of Eastern European countries, according to reports. Web defacements were also common. After the Chinese Embassy was accidentally bombed in Belgrade, Chinese hacktivists posted messages such as, “We won’t stop attacking until the war stops!” on U.S. government Web sites.
During the Kosovo conflict in 1999, NATO computers were blasted with e-mail bombs and hit with DoS attacks by hacktivists protesting the NATO bombings. In addition, businesses, public organizations, and academic institutes received highly politicized virus-laden e-mails from a range of Eastern European countries, according to reports. Web defacements were also common. After the Chinese Embassy was accidentally bombed in Belgrade, Chinese hacktivists posted messages such as, “We won’t stop attacking until the war stops!” on U.S. government Web sites.
![]() In Australia in 2000, a disgruntled former consultant hacked into a waste management control system and released millions of gallons of raw sewage on the nearby town.
In Australia in 2000, a disgruntled former consultant hacked into a waste management control system and released millions of gallons of raw sewage on the nearby town.
![]() In 2001, two hackers cracked a bank system used by banks and credit card companies to secure the personal identification numbers of their customers’ accounts. Of even more concern is the fact that the same system is used by the U.S. Treasury Department to sell bonds and treasury bills to the public over the Internet.
In 2001, two hackers cracked a bank system used by banks and credit card companies to secure the personal identification numbers of their customers’ accounts. Of even more concern is the fact that the same system is used by the U.S. Treasury Department to sell bonds and treasury bills to the public over the Internet.
![]() Most readers who even occasionally read or watch the news are aware of the conflict between India and Pakistan regarding control of the Kashmir province. Fewer people are aware that hackers have gotten involved in this conflict as well. According to the Hindustan Times News, in April of 2003 Pakistani hackers defaced 270 Indian Web sites. Indian hackers calling themselves “Indian Snakes” spread the Yaha worm as “cyber-revenge.” The worm aimed at performing DDoS attacks on some Pakistani sources, including ISPs, the Web site of Karachi Stock Exchange, and governmental sites.
Most readers who even occasionally read or watch the news are aware of the conflict between India and Pakistan regarding control of the Kashmir province. Fewer people are aware that hackers have gotten involved in this conflict as well. According to the Hindustan Times News, in April of 2003 Pakistani hackers defaced 270 Indian Web sites. Indian hackers calling themselves “Indian Snakes” spread the Yaha worm as “cyber-revenge.” The worm aimed at performing DDoS attacks on some Pakistani sources, including ISPs, the Web site of Karachi Stock Exchange, and governmental sites.
![]() Also in 2003 a group calling itself the Arabian Electronic Jihad Team (AEJT) announced its existence and stated that its goal was to destroy all Israeli and American Web sites as well as any other “improper” sites.
Also in 2003 a group calling itself the Arabian Electronic Jihad Team (AEJT) announced its existence and stated that its goal was to destroy all Israeli and American Web sites as well as any other “improper” sites.
![]() In December of 2009 a far more disturbing story than all of these came out. Hackers broke into computer systems and stole secret defense plans of the United States and South Korea. Authorities speculated that North Korea was responsible. The information stolen included a summary of plans for military operations by South Korean and U.S. troops in case of war with North Korea, though the attacks traced back to a Chinese IP address. This case is clearly an example of cyber espionage and a very serious one at that.
In December of 2009 a far more disturbing story than all of these came out. Hackers broke into computer systems and stole secret defense plans of the United States and South Korea. Authorities speculated that North Korea was responsible. The information stolen included a summary of plans for military operations by South Korean and U.S. troops in case of war with North Korea, though the attacks traced back to a Chinese IP address. This case is clearly an example of cyber espionage and a very serious one at that.
Clearly cyber terrorism is a growing problem. In this author’s opinion (as well as the opinions of many other security experts), the only reason we have not seen more damaging and more frequent attacks is that many terrorist groups do not have the computer skills required. It can therefore only be a matter of time before such groups either acquire those skills or recruit those who do.
China Eagle Union
No discussion of cyber terrorism would be complete without a discussion of the China Eagle Union. This group consists of several thousand Chinese hackers whose stated goal is to infiltrate western computer systems. A number of web resources regarding this group exist:
![]() www.thedarkvisitor.com/2007/10/china-eagle-union/
www.thedarkvisitor.com/2007/10/china-eagle-union/
![]() https://news.hitb.org/node/6164
https://news.hitb.org/node/6164
![]() http://archives.cnn.com/2001/WORLD/asiapcf/east/04/27/china.hackers/index.html
http://archives.cnn.com/2001/WORLD/asiapcf/east/04/27/china.hackers/index.html
![]() Members and leaders of the group insist that not only does the Chinese government have no involvement in their activities, but that they are breaking Chinese law and are in constant danger of arrest and imprisonment. Many analysts find this claim dubious. Whether the Chinese government is involved in these attacks or not, some experts consider a state of cyber warfare to currently exist between China and the United States.
Members and leaders of the group insist that not only does the Chinese government have no involvement in their activities, but that they are breaking Chinese law and are in constant danger of arrest and imprisonment. Many analysts find this claim dubious. Whether the Chinese government is involved in these attacks or not, some experts consider a state of cyber warfare to currently exist between China and the United States.
The good news is that the particular attacks discussed in this section caused little damage and were clearly the product of amateurs. However, it is my contention that it may only be a matter of time before more damaging attacks are perpetrated by far more skilled cyber terrorists. Yet, it is clear that cyber terrorism, at least on a low intensity scale, has already actually happened. As a network administrator or security professional you have the choice either to heed these warnings and begin to take these issues seriously or simply wait until disaster strikes.
Choosing Defense Strategies
At this point, you have gained an awareness of the dangers of cyber terrorism and computer-based espionage. Now the question is what can be done to prepare an adequate defense. For businesses and individual organizations, the following steps can be taken:
![]() Ensure that you have as tight a security as is practical for your organization. Realize that failure to secure your network is not simply a danger to your organization but might be a threat to national security.
Ensure that you have as tight a security as is practical for your organization. Realize that failure to secure your network is not simply a danger to your organization but might be a threat to national security.
![]() Make certain you do adequate background checks for all network administrators and security personnel. You do not wish to hire someone who is likely to participate in cyber terrorism or espionage.
Make certain you do adequate background checks for all network administrators and security personnel. You do not wish to hire someone who is likely to participate in cyber terrorism or espionage.
![]() If a computer breach occurs or is even attempted, report the incident to the appropriate law enforcement agency. This may not lead to the capture of the perpetrator, and your organization may not even consider the incident worthy of prosecution. However, if law enforcement agencies are not aware of such incidents, they cannot investigate and prosecute them.
If a computer breach occurs or is even attempted, report the incident to the appropriate law enforcement agency. This may not lead to the capture of the perpetrator, and your organization may not even consider the incident worthy of prosecution. However, if law enforcement agencies are not aware of such incidents, they cannot investigate and prosecute them.
What can be done on a state and national level to defend against this sort of attack?
![]() Greater law enforcement attention to computer crimes: Computer crimes often do not get the attention that other crimes do and, therefore, might not be as thoroughly investigated.
Greater law enforcement attention to computer crimes: Computer crimes often do not get the attention that other crimes do and, therefore, might not be as thoroughly investigated.
![]() Better training for law enforcement: Simply put, most law enforcement agencies are well-equipped to track down thieves, murderers, and even con men but not to track down hackers and virus writers.
Better training for law enforcement: Simply put, most law enforcement agencies are well-equipped to track down thieves, murderers, and even con men but not to track down hackers and virus writers.
![]() Industry involvement: More involvement from industry is critical, such as Microsoft’s offering of cash bounties for information leading to the capture of virus writers.
Industry involvement: More involvement from industry is critical, such as Microsoft’s offering of cash bounties for information leading to the capture of virus writers.
![]() Federal government involvement: Also critical is more involvement by the FBI, Defense Department, and other agencies in defense against computer-based crime and terrorism. A coordinated planned response should be formulated.
Federal government involvement: Also critical is more involvement by the FBI, Defense Department, and other agencies in defense against computer-based crime and terrorism. A coordinated planned response should be formulated.
Nothing can make one completely safe from any attack. However these steps can be taken to decrease the dangers.
Of even more immediate interest to companies is protecting against industrial espionage. As we have pointed out, this is a real phenomenon and one which you must guard against. If the espionage is conducted by a hacker breaking into your system to steal information, then the various security techniques we have discussed throughout this book are the appropriate defense. However, what can you do to stop an employee who has access to sensitive data and decides to participate in such espionage? Remember that this can occur for many reasons. Perhaps that employee is angry over being passed over for promotion, perhaps he feels the company is doing something unethical and wants to damage the company, or it could be as simple as that person committing espionage for monetary gain.
Whatever the reason, protecting yourself against authorized users divulging data is much harder. Remember the seven steps we mentioned in the section on industrial espionage (removing floppy drives, prohibiting camera phones, etc.). These can also be helpful. Also recall our discussion in Chapter 11 on least privileges. Even if a person requires access to sensitive data, she should have access only to the data she absolutely needs. For example, a manager of your eastern region marketing division would clearly need access to sales data for that region, but she would not need access to the sales data for the entire nation.
Defending Against Information Warfare
We have examined the use of computers and the Internet for espionage and for terrorism. Now let’s look at a third type of attack. Information warfare certainly predates the advent of the modern computer and, in fact, may be as old as conventional warfare. In essence, information warfare is any attempt to manipulate information in pursuit of a military or political goal. When you attempt to use any process to gather information on an opponent or when you use propaganda to influence opinions in a conflict, these are both examples of information warfare. Previously we discussed the role of the computer in corporate espionage. The same techniques can be applied to a military conflict in which the computer can be used as a tool in espionage. Although information gathering will not be re-examined in this chapter, information gathering is only one part of information warfare. Propaganda is another aspect of information warfare. The flow of information impacts troop morale, citizens’ outlooks on a conflict, the political support for a conflict, and the involvement of peripheral nations and international organizations.
Propaganda
Computers and the Internet are very effective tools that can be used in the dissemination of propaganda. Many people now use the Internet as a secondary news source, and some even use it as their primary news source. This means that a government, terrorist group, political party, or any activist group could use what appears to be an Internet news Web site as a front to put their own political spin on any conflict. Such a Web site does not need to be directly connected to the political organization whose views are being disseminated; in fact, it is better if it is not directly connected. The Irish Republican Army (IRA), for example, has always operated with two distinct and separate divisions: one that takes paramilitary/terrorist action and another that is purely political. This allows the political/information wing, called Sinn Fein, to operate independently of any military or terrorist activities. In fact, Sinn Fein now has their own Web site where they disseminate news with their own perspective (www.sinnfein.org). In this situation, however, it is fairly clear to whoever is reading the information that it is biased toward the perspective of the party sponsoring the site. A better scenario (for the party concerned) occurs when there is an Internet news source that is favorably disposed to a political group’s position without having any actual connection at all. This makes it easier for the group to spread information without being accused of any obvious bias. The political group (be it a nation, rebel group, or terrorist organization) can then “leak” stories to this news agency.
Information Control
Since World War II, control of information has been an important part of political and military conflicts. Below are just a few examples.
![]() Throughout the Cold War, Western democracies invested time and money for radio broadcasts into communist nations. This well-known campaign was referred to as Radio Free Europe. The goal was to create dissatisfaction among citizens of those nations, hopefully encouraging defection, dissent, and general discontent. Most historians and political analysts agree that this was a success.
Throughout the Cold War, Western democracies invested time and money for radio broadcasts into communist nations. This well-known campaign was referred to as Radio Free Europe. The goal was to create dissatisfaction among citizens of those nations, hopefully encouraging defection, dissent, and general discontent. Most historians and political analysts agree that this was a success.
![]() The Vietnam War was the first modern war in which there was strong and widespread domestic opposition. Many analysts believe that opposition was due to the graphic images being brought home via television.
The Vietnam War was the first modern war in which there was strong and widespread domestic opposition. Many analysts believe that opposition was due to the graphic images being brought home via television.
![]() Today, the government and military of every nation are aware of how the phrases they use to describe activities can affect public perception. They do not say that innocent civilians were killed in a bombing raid. Rather, they state that there was “some collateral damage.” Governments do not speak of being the aggressor or starting a conflict. They speak of “preemptive action.” Dissenters in any nation are almost always painted as treasonous or cowards.
Today, the government and military of every nation are aware of how the phrases they use to describe activities can affect public perception. They do not say that innocent civilians were killed in a bombing raid. Rather, they state that there was “some collateral damage.” Governments do not speak of being the aggressor or starting a conflict. They speak of “preemptive action.” Dissenters in any nation are almost always painted as treasonous or cowards.
Public perception is a very important part of any conflict. Each nation wants its own citizens to be totally in support of what it does and to maintain a very high morale. High morale and strong support lead to volunteers for military service, public support for funding the conflict, and political success for the nation’s leader. At the same time, you want the enemy to have low morale—to doubt not only their ability to be successful in the conflict, but also their moral position relative to the conflict. You want them to doubt their leadership and to be as opposed to the conflict as possible. The Internet provides a very inexpensive vehicle for swaying public opinion.
Web pages are just one facet of disseminating information. Having people post to various discussion groups can also be effective. One full-time propaganda agent could easily manage 25 or more distinct online personalities, each spending time in different bulletin boards and discussion groups, espousing the views that his political entity wants to espouse. These can reinforce what certain Internet news outlets are posting or they could undermine those postings. They can also start rumors. Rumors can be very effective even when probably false. People often recall hearing something with only a vague recollection of where they heard it and whether it was supported by any data.
Such an agent could have one personality that purports to be a military member (it would take very little research to make this credible) and could post information “not seen in newscasts” that would cast the conflict in either a positive or negative light. She could then have other online personas that entered the discussion who would agree with and support the original position. This would give the initial rumor more credibility. Some people suspect this is already occurring in Usenet newsgroups and Yahoo discussion boards.
Closely related to propaganda, disinformation is yet another type of information warfare. It is a given that one’s opponent is attempting to gather information about one’s troop movements, military strength, supplies, and so on. A prudent move would be to set up systems that had incorrect information and were just secure enough to be credible but not secure enough to be unbreakable. For example, a user may send an encrypted coded message that seems to say one thing when intercepted and decrypted but actually has a different message to a recipient who can complete the code. There are encryption schemes that do just this. The actual message is “padded” with “noise.” That noise is a weakly encrypted false message, and the real message is more strongly encrypted. This way if the message is decrypted, there exists a high likelihood that the fake message will be decrypted, not the real one. Marine General Gray put it best when he said “Communications without intelligence is noise; intelligence without communications is irrelevant” (Gray, 2004).
Actual Cases
In addition to some of the cases already listed, there have been other credible threats or actual incidents of cyber attacks in the past several years. Let’s briefly examine some of these cases.
![]() In 2002, Counterpane Internet Security reported a credible threat of a Chinese-backed, all-out cyber attack planned on the United States and Taiwan (2002). A private group of Chinese hackers, called the China Eagle Union, planned to attack routers and Web servers across the United States and Taiwan. The attack never materialized, but unconfirmed reports suggested that the CIA took the threat seriously.
In 2002, Counterpane Internet Security reported a credible threat of a Chinese-backed, all-out cyber attack planned on the United States and Taiwan (2002). A private group of Chinese hackers, called the China Eagle Union, planned to attack routers and Web servers across the United States and Taiwan. The attack never materialized, but unconfirmed reports suggested that the CIA took the threat seriously.
![]() In June of 2000, Russian authorities arrested a man they accused of being a CIA-backed hacker. This man allegedly hacked into systems of the Russian Domestic Security Service (FSB) and gathered secrets that he then passed on to the CIA (BBC Report, 2000). This example illustrates the potential for a skilled hacker using his knowledge to conduct espionage operations. This espionage is likely occurring much more often than is reported in the media, and many such incidents may never come to light.
In June of 2000, Russian authorities arrested a man they accused of being a CIA-backed hacker. This man allegedly hacked into systems of the Russian Domestic Security Service (FSB) and gathered secrets that he then passed on to the CIA (BBC Report, 2000). This example illustrates the potential for a skilled hacker using his knowledge to conduct espionage operations. This espionage is likely occurring much more often than is reported in the media, and many such incidents may never come to light.
Alternative media sources have been reporting that both the CIA and NSA have employed hackers for some time. This might be easily dismissed as false were it not for the fact that such hackers have actually been caught, as in the Russian story. One might even go so far as to say that, in our modern age, for intelligence gathering agencies not to employ cyber intelligence-gathering techniques would be a dereliction of their duty.
One problem with attempting to collect data on cyber espionage or cyber terror is the fact that many stories may never be made public, and of those that are, it is likely that not all the facts are made public. In fact if one is truly successful in any espionage act, it never becomes public.
Summary
Computer-based espionage is the use of computers, networks, and telecommunications lines to attempt to illicitly acquire information. It is also possible for employees to use portable media to smuggle data out of an organization in order to give it to a third party. There are a variety of motivations for either activity, but regardless of the motivation, you must be aware of the threat to your system’s data. Remember that the hardware is simply there to house the data; ultimately the data itself is the commodity.
There have been some low-level incidents of cyber terrorism. It also seems likely that there will be more such incidents in the future. Clearly the potential for such threats exists, and in this chapter we have examined some possible scenarios. We have also examined the role computers and the Internet can play in information warfare. It seems likely, from anecdotal evidence, that such activities are already taking place.
Test Your Skills
Multiple Choice Questions
1. Which of the following best defines espionage?
A. The use of spies to acquire military information
B. The use of any technique to acquire military information
C. Any acquisition of any data via illicit means
D. The use of any technique to acquire any data of military or political value
2. Which of the following is not one of the recommended measures to prevent employee-based industrial espionage?
A. Remove all floppy drives.
B. Monitor all copying from servers.
C. Have all employees sign confidentiality agreements.
D. Perform random polygraph tests.
3. Which of the following best defines cyber terrorism?
A. Computer crime that is directed at military installations
B. Computer crime conducted solely for political motivation
C. Computer crime that is directed at any government entity
D. Computer crime conducted for political or ideological motivation
4. Which of the following best defines a packet sniffer?
A. A product that scans the Internet seeking out packets
B. A utility that finds packets of a specific protocol
C. A program that intercepts packets and copies their contents
D. A program that provides statistical analysis of packet traffic
5. Excessive network traffic between a server and a single workstation would most likely indicate what?
A. The workstation has spyware on it.
B. A large amount of file copying to the workstation is occurring.
C. The workstation is sending a lot of e-mails.
D. The server is not working correctly.
6. What is the most likely damage from an act of cyber terrorism?
A. Loss of life
B. Compromised military strategy
C. Economic loss
D. Disrupted communications
7. Which of the following is the most likely way in which cyber terrorism could lead to loss of life?
A. By causing a missile launch
B. By causing a plane to crash
C. By disrupting safeguards at a power or chemical plant
D. By electrical discharge through a computer keyboard
8. Without compromising highly secure systems, which of the following is not a likely way for a terrorist to disrupt military operations using hacking?
A. Hacking logistical systems and disrupting supplies
B. Monitoring information to derive information about troop and supply movement and locations
C. Causing (or stopping) the launch of a missile
D. Gleaning information about troop morale from unsecured communications
9. Which of the following attacks may have been an example of domestic cyber terrorism?
A. The Sasser virus
B. The Mimail virus
C. The Sobig virus
D. The MyDoom virus
10. What differentiates cyber terrorism from other computer crimes?
A. It is organized.
B. It is politically or ideologically motivated.
C. It is conducted by experts.
D. It is often more successful.
11. Which of the following is the least likely reason the United States has not yet been the victim of a significant, large scale cyber terrorist attack.
A. Terrorist groups underestimate the impact of such attacks.
B. There are simply no people around with the requisite skills.
C. The number of people with sufficient skills is small.
D. Because such an attack would be ineffectual and not cause much damage.
12. What is information warfare?
A. Only spreading disinformation
B. Spreading disinformation or gathering information
C. Only gathering of information
D. Any use of information to manipulate any political/military situation
13. Which of the following would not be considered information warfare?
A. Spreading lies about a political opponent via the Internet
B. Broadcasting messages into a hostile area that cast your viewpoint in a positive light
C. A factual political documentary
D. Sending false information in order to deceive a hostile group
17. If a group were using the Internet in information warfare, which of the following would be the least likely use?
A. To spread propaganda
B. To spread disinformation about opponents
C. To plant slanted news stories
D. To directly recruit new members
15. Sending a false message with weak encryption, intending it to be intercepted and deciphered, is an example of what?
A. Poor communications
B. Disinformation
C. A need for better encryption
D. Propaganda
Exercises
Exercise 17.1: Analyzing Incidents
1. Using the Web or other resources, find any example of computer-based espionage or terrorism not already mentioned in this book.
2. Describe how the attack took place—what methods were used by the attackers?
3. Describe the effects of the attack. Were they economic, political, or social? Did they affect you personally in any way?
4. What steps might have been taken to prevent the attack?
Exercise 17.2: The Kosovo Crisis
1. Using the Web or other resources, research the use of cyber warfare as part of the Kosovo crisis.
2. Describe the various cyber attacks you can find. What methods were used by the attackers?
3. Describe the effects of the attack. Were they economic, political, or social? What effect might these attacks have had on you if you were living in Kosovo?
4. What steps might have been taken to prevent the attack?
Exercise 17.3: Key Loggers and Espionage
1. Recall from earlier chapters we discussed spyware and how it works. Specifically think about key loggers.
2. Describe how key loggers might be used in spying and how serious you feel the danger is.
3. How might you combat this threat?
In earlier chapters we discussed encrypting transmissions to prevent packet sniffers from picking them up. Also in this chapter we discussed packet sniffers in some detail. In a lab setting:
1. Download and install CommView on a lab computer.
2. Use it to intercept data sent between other lab computers.
3. Observe the data you pick up going across the network. Note how a packet sniffer can be used for espionage, especially if the data is not encrypted.
Exercise 17.5: Other Packet Sniffers
In earlier chapters we discussed encrypting transmissions to prevent packet sniffers from picking them up. Also in this chapter we discussed packet sniffers in some detail. In a lab setting:
1. Download and install EtherDetect or another packet sniffer on a lab computer.
2. Use it to intercept data sent between other lab computers.
3. Describe how a packet sniffer can be used for espionage, especially if the data is not encrypted.
4. Describe the data you intercepted. Could any of the contents be considered sensitive or confidential?
5. How could you safeguard the lab’s computers from this type of attack?
Projects
Project 17.1: Hackers and Espionage
Clearly, hacking techniques can be used in espionage (whether the espionage is political or economic in nature). Find a case of espionage in which hacking was used and carefully examine the techniques used. Describe the results of the case and preventative measures that should have been used. The following Web sites might be useful to you in this search:
![]() Hacking and Industrial Espionage: http://www.nationaldefensemagazine.org/archive/1999/July/Pages/Hackers4407.aspx
Hacking and Industrial Espionage: http://www.nationaldefensemagazine.org/archive/1999/July/Pages/Hackers4407.aspx
![]() Corporate Espionage http://www.economist.com/news/china/21572250-old-fashioned-theft-still-biggest-problem-foreign-companies-china-who-needs
Corporate Espionage http://www.economist.com/news/china/21572250-old-fashioned-theft-still-biggest-problem-foreign-companies-china-who-needs
Project 17.2: Information Warfare
Using the Internet, locate communications (Web sites, chat rooms, newsgroups, etc.) that you consider to be examples of information warfare. Explain what type of information warfare they are (disinformation, propaganda, etc.) and why you consider these to be examples of information warfare.
Project 17.3: Cyber Terrorism Scenario
1. Select one of the theoretical cyber terrorism scenarios presented in this chapter.
2. Study it carefully, and then write a security and response plan that addresses the scenario and protects against that specific threat, the key being a plan against a specific threat. Whatever threat you select, you should provide details regarding what technologies should be used and what policies should be implemented to defend against that specific threat.