Chapter 8
Reporting After Analysis
Introduction
It has been my experience that in most cases no analysis is conducted without the end result being a reporting on the findings of the analysis, of course I am sure that in some government spaces, the reverse may be true. Reporting provides many things that benefit an organization, it helps to establish best practices, build the skills of analysts, providing a reference database that can be searched, and among other things, may provide details records of due diligence if accusations are ever leveled against the organization.
Reporting is an interesting endeavor that is an art to be developed. Ranked high as one of the least favorite things to do, right next to public speaking, report writing is a unique process that can span the gambit from professional technical reports containing facts and details to opinionated fiction writing full of assumptions hearsay and outright false statements.
In the end however, it is the job of the analyst to ensure that they provide a professional report that contains the facts of the analysis, the actions they took to examine the media, the extent of the compromise, other systems involved, data that was transferred, network end points, legal considerations such as downstream liability for data breaches and so much more. The report should include many items, the details of which will be explored in this chapter, providing enough detail and definition that those who are not technical, as well as C level executives and legal counsel, can understand the who, what where, when, and how of the events.
Digital media exploitation, okay, digital forensic reports, what about data recovery reports, what should these types of reports be referred to as, perhaps an analysis report is vague enough to encompass all of the above mentioned titles. The truth of the matter is that each organization and each analysis will require unique data sets to be reported on and it is up to the analyst to ensure that the questions that are being asked in the request to analyze media are answered with direct statements when the report is finalized.
Getting Started
There are several templates available for an analyst who prefers to take the work and customize it to their organizational needs, which is something that I believe most of us have done at one time or another. Several of the Linux based forensic appliances provide investigative templates that can be utilized for the reporting of an examination.
Generally speaking there are several primary categories that are contained within an analysis report. These primary concerns include:
At a very high level, that is the sum total of an analysis report. An overview of the case, providing what the case is about, who asked for the case, the authority to search and any additional documents that were provided by the submitter of the digital media. The next high level category is the summary of findings, often times referred to as the Executive Summary, which includes a review of the artifacts that were identified during the course of the analysis. However, the artifacts should only be relevant to the request being made. The details of findings are just that and should include the information located during the course of the analysis, such as excerpts or full text from system logs, Web history searches, user account information and hash values, malware reports, keyword, and keyword search results and more. Finally, there is an appendices section which should include sections indicated software used by the analyst, analyst notes, automated malware reports, and other such information.
Report writing and what to include within a report seems to be a debate that comes and goes a few times a month, it is like an artist reviewing their painting, they are never finished, I think that the same applies to the information and data sets that are included within a digital media analysis report.
A former professional colleague of ours would engage us in discussions on reports, what belonged in them, what others wanted to place in them and more. Overtime, there seemed to be a consensus that the reports would contain what was needed in order to answer the request that was submitted with media for examination. That list grows and shrinks depending on the organization, the professionalism of the analyst, development of new tools and techniques as well as legal requirements and more.
There are several sections, consisting of about 30 different areas that could be included however this is something that has to be considered by the analyst. Most organizations have a standard template that will be followed.
Note that these fields take into consideration that the request could be coming from law enforcement, corporate or data recovery professions.
There are multiple sections of data that can or should be included within an analysis report, ranging from the legal right to search the media to the individuals involved in the collection of the data sets through chain of custody forms. We will now explore several of these categories of data and provide brief explanations so that the reasoning behind their inclusion can be justified, if need be.
First, there should be a report header that details any of the case information, listing involved parties, the person requesting the analysis and the contact information for each of these persons. By listing this information the analyst has the information during the course of the analysis, so that if there are any questions, the source can be questioned directly. In addition, by providing the contact details of the parties involved, C level executives and legal counsel that may be reviewing the report have an easily accessible in the event they have questions as well.
The second data set that should be provided should address the question of why the analysis is taking place. Providing a restatement of the request generally answers the question as to why the request for analysis is being submitted and what purpose will be served. This section is typically closely tied to the legal authority to search the asset, which may or may not be included in the report. In some cases, such as with Law Enforcement cases, there are search authorities, such as Consent searches or a Search Warrant. In either case, consideration for inclusion of these documents as an appendix should be made. Corporate investigations may have to comply with a Law Enforcement request or an examination may be in accordance with administrative actions, HR complaints, or as a normal business process to protect their own assets. No matter the justification, inclusion in the report may benefit the organization in the future.
Next, and this section could really only apply to law enforcement cases, is to consider if the report or case would benefit from detailing out the analyst’s experience and expertise in the field, sort of a mini CV providing details of training and/or education in this field. This section, if included would serve as an attempt to head off any challenges to the analyst, but may also provide a defense attorney with too much background information. Tread wisely when considering whether or not to include too much information.
A chain of custody form might be a good idea to include as an appendix to an analysis report. This type of information, who had the evidence, when, was it secured, etc. is great to include with cases that involve lawyers and criminal or civil proceedings. The chain of custody is something that will eventually be provided through discovery, so there is a good chance that including it as an appendix in a written report will assist in heading off any questions.
Moving on to the next section, the circumstances of the case and what is the scope of the search? Both of these data sets are very important to report writing. The allegations will help to determine what is to be searched for and the scope will help limit the areas of the data to be searched. For instance, with multi user systems the scope of the search might only be limited to one or two user profiles. Consider a corporate file server and the amount of users that access, would the entire system have to be searched or is it limited?
Next, there should be a section that will be inclusive of the case agent, which is just the person that actually seized the evidence, this section should be the seizure notes from the field, who seized the media, what did they seize, how was it secured, are there any pictures of the scene showing how the media was sitting when the seizure occurred and more. Combine this information with the contact information for the agent in the field and if there are any questions, the analyst can contact the field agents and get clarification. As for the what was seized section, this should be a detailed listing including:
• Any damage- this will cover any accusations of damage by the analysis process.
Processing of each of these data elements should include the above mentioned identification as well as hash values for acquisition and verification, to prove there was no alteration.
Next, what was done with the media once it was received should be listed; perhaps this is the start of the analyst notes section. How did the analyst receive the media, was it stored in a media safe, was an image taken by a triage engineer and the images stored on a server? All of these questions should be answered in this section.
Far be it from me to dictate to an analyst their process, but the following processes should be performed and recorded. These processes should be performed and listed within the notes section of the report, perhaps an appendix. This list is not in a set order:
• Review the request for analysis so that you are aware of what is being asked of you.
• Record any notes that will be helpful.
• Create the analysis directory structure for exportation of files, analysis and more.
• Organize the bookmarks within your forensic framework. This helps with organization.
• Verify the evidence through verification hash.
• Scan the device for malicious code.
• Draft a glossary, provide terms used so that those not technically savvy understand the terms.
• Perform a Registry analysis, an in depth analysis.
• Set the proper time zone, best practices may be to set to UTC.
• Detail the device information.
• Perform a signature analysis.
• Perform a manual review of the evidence.
• Hash analysis and hash sets.
• Identify any password protected or encrypted files and attempt to recover the passwords.
• Web artifacts (Email and Web history).
• Client based Email analysis.
• IM and social networking analysis.
This is by no means to be considered a comprehensive list. Throughout an analysis of this nature, one of the key points is the relevance to the request. Without relevance and the data being placed into context, it is simply a series of facts.
What software was identified on the suspect system and what software was used for analysis? This is very important information to include in a report since the software used for analysis is constantly under development and listing the version number will help if there are any issues in the future. It also helps for others who follow your analysis so that they can verify your results.
Write the report as though the reader has no idea what they are reading. Everything should be explained in depth so that there are no questions left unanswered. The finalized report should list the above items as well as the items that were analyzed.
In the forward we discussed how we have been asked for check lists on what to do in order to conduct a forensic analysis, how to report the information and how to find the digital evidence. This is something that cannot be provided, but what can be provided is a series of steps that can be used as a reminder of the processes that need to be run in order to uncover or reveal digital evidence. There is a mindset that an analyst must have in order to be effective. Anyone can run tools and look at the report, in fact, many new forensic analysts’ do just that, they trust the tools. An analyst interprets the data and verifies the results; it is this diligence that sets analysts apart.
Now that the disclaimers have been presented let us review the data fields mentioned above and detail how the information should be presented in a report.
Note
There was a time when the well-known commercial products reporting capabilities left a lot to be desired. As such, most examiners simply created their own templates and imported bookmarks and data from these products into their company’s template. We are not going to delve into the reporting capabilities of the commercial products. However, we are going to note that the commercial products have made some significant changes to the way their products produce reports. We will mention one in particular. Guidance Software, Inc. EnCase V7 reporting capabilities has changed significantly. The user now has the ability to create an entirely customizable format. Some of the options include; creating a table from bookmarks, formatting of that table and what metadata to include, Styles and fonts, pictures/logos, custom header/footer data, and such.
The Report Header
The report header should be somewhat similar to a formal written letter’s header. What we mean by this is that there are certain categories and formats that need to be present. Outside of the inclusion of a cover sheet, the first data that should be presented to the reader is who the report is for, date, who drafted the report and what the subject of the report is. This information will present the reader with a timeframe for context, by providing the date and time of the report, the reader will be pulled back into the report from the other items that require their attention. The next piece of the header information that needs to be included is the subject of the report field. In most cases the report will be provided to a manager or executive and they may need to have the quick reference of the subject of the report. And lastly, your name has to be included within the header as the author of the report so that you can be contacted if there are questions. For this reason it is very important that the report be clear and concise as well as free from grammatical and spelling errors. A basic example is:

Note: this is just an example of a report header.
The next section is a section that simply recaps or paraphrases what the request for the analysis is asking for. Think back to your school days when you were tasked with writing a 500 word essay, the first and last paragraphs are a rephrasing of each other. That is exactly what this next section is comprised of. This information can come through many channels and could be all inclusive; it could be an Email requesting an analysis or a self instigated examination as a normal course of business. The description within this section is a simple restatement of the request which could be as simple as: network monitoring logs indicated that HOST XXXX may have been infected with malicious code. Since DATE/TIME network logs reflect that HOST XXXX has been sending a great deal of network traffic to the following IP. Below is a sample template that is similar to the one we used at the academy that can be customized to your individual needs.
Report for (Requester who submitted analysis request) (Date)
Examiner/Analyst: (Your information here)
SUBJECT: Network Intrusion Analysis Report
Requested Analysis
This section should include the reason why the analysis is being conducted. By presenting this information here, the reader is able to have a road map and develops expectations as to what the report will entail. This section can often times provide the analyst with a starting point or information as to what activity was observed.
Status of Analysis: Closed or Pending
In many cases an examination will not end when the report is submitted. In large incidents, reports will be coming into a central location, usually for a manager to review. If the report definitively answers the analysis question, then the status of the analysis could be indicated as closed. If not, if the analysis revealed encrypted data, encrypted volumes, or if there is still some outstanding analysis, then the status has to be listed as pending, but the reason should be listed.
Summary
This section must be a high level overview of the findings of the analysis and how that information pertains to the request for analysis. The details of the analysis will be presented later in the report, so this section really gives an almost cliff notes version of the report to the reader. This is the section that upper level management will review. This section should answer the; who, what, where, when and how in a concise manner.
Items Analyzed
Within this section, if included, the analyst needs to list the digital media that was analyzed. Examples of items analyzed could include:
Details of each of these items need to be provided, such as serial number, make model, values for acquisition hash and verification hash and any other unique identifying information.
Software
Analysis Software
| Program Name/Version | Program Description |
Given that in most cases lawyers will be involved at some point, an analyst needs to ensure that they list the software that they used during the course of the analysis so that their steps can be recreated and followed by opposing experts and the same results can be recreated. Listing the details of the software, the build, the version, the libraries used, as in AV software, and any other details that would identify the software used and the state that the software existed at that time will help to capture the state of the analysis machine.
Suspect Software
| Program Name/Version | Directory Location | Program Description |
This section may or may not be required or included. In some cases, this section may be a vital section to include in the report. For instance, if there is unique software used for image manipulation this should be included in this section. Any office software, operating system or Web browsers should all be listed with the details mentioned above.
Glossary of Terms
Providing a glossary will help the reader when and if they come across a term that they are not familiar with. Keep in mind that is a rare instance when someone that reading a report of this nature understands the technical terms. Providing a table is a good way to present the information.
| Term | Definition |
Details of Analysis
This is the meat of the report, providing details about all aspects of the request for analysis. Within this section there is a tendency to include assumptions related to the uncovered evidence, but refrain from doing so. Each of the items listed within the request should be answered within this section, but the details need to be clear and get to the point.
Registry analysis, Web artifacts, host, and Web based Email analysis, antivirus logs, network packet capture analysis and volatile data analysis should all be contained within this section and the details listed within each section. A timeline of the attacker’s activity can prove to be a valuable source of information about the intrusion. The timeline can contain entries from all of your devices directly or indirectly involved in the intrusion. Make sure that you note in the timeline the device, log or path of each particular entry.
Additional sections within the Details of findings may include: Recommendations from SANS.
Host based analysis:
• Artifacts of file downloads:
o Application compatibility cache.
• Deleted file or file knowledge:
o Win7 search word wheel query.
Ram analysis:
• Date and time RAM was collected.
• HASH of the RAM capture file.
• List the details of the findings and present that information in a structure format for the reader. RAM analysis is a very complex data set so be sure to explain this section well.
Network analysis:
• Date and time pcap was collected.
• HASH of the PCAP file (network trace).
• List the details of the findings and present that information in a structure format for the reader. Inclusion of HEX/text is absolutely appropriate in this section of the report, showing the raw data.
Windows event logs: See Table 8 1.
Table 8.1 Relevant Windows Event Log Details
Antivirus logs: See Table 8 2.
Table 8.2 Relevant Antivirus Log Details
System logs: See Table 8 3.
Table 8.3 Relevant Windows System Log Details
Scheduled tasks log: See Table 8 4.
Table 8.4 Relevant Scheduled Task Log Details
Windows registry analysis (example report template):
HKLM (enter the HKLM that is being analyzed, reuse the table for each Hive Key)

Remediation Recommendations
This section may be a requirement for the report and the organization. As an analyst continues to investigate the compromised hosts, they will no doubt come across information that would assist in network remediation efforts. Any information of that nature should be included in this section.
Appendices
Appendices can include a great deal of information, including notes from the initial request, research during the course of the analysis and more.
At a minimum, I include a table for analyst notes; this section can be placed into a landscape view. Consider that the report contains what was relevant to the request and the notes are a detailed listing of the actions taken.
As an example:
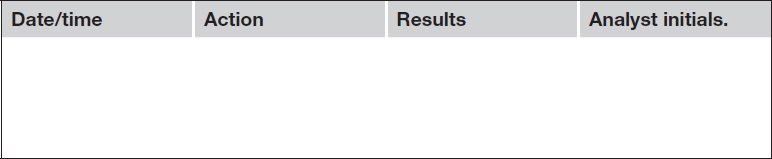
Examples of reports and information that could be included in a report (see Figure 8.1).
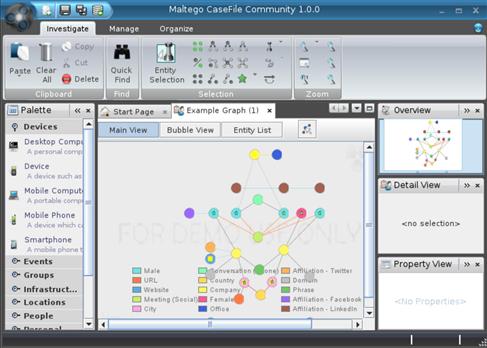
Figure 8.1 This is a Screen Shot of Maltego, a Link Analysis and Intelligence Gathering Application that is Included with BackTrack
Example 1
A visualizer for inclusion in a report. This example is from the Back Track 5 R2 distribution and is a Maltego Case file (see Figure 8.2).
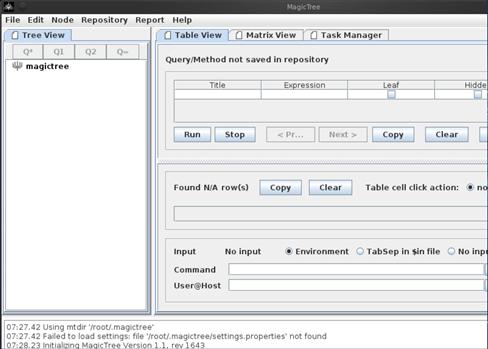
Figure 8.2 A Screen Shot of one Case Management GUI Interface
Example 2
This is a case management report form from Magic Tree again from the Back Track distribution (see Figure 8.3).
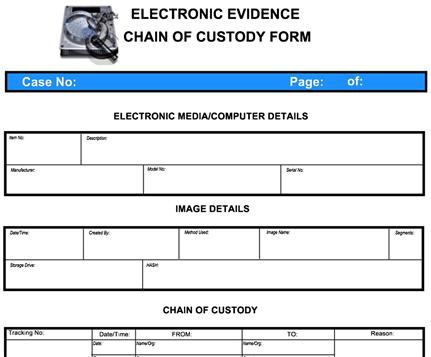
Figure 8.3 This is a Screen Shot of the Chain of Custody form Included with Helix
Example 3
This is an example of a chain of custody form from the Helix Distribution 1.7. Although this is a bit dated, there are still some very good fields within this form that can be customized for your individual or organizational needs.
