TO SOME NETWORK ADMINISTRATORS, A FIREWALL is the key component of their infrastructure's security. To others, a firewall is a hassle and a barrier to accomplishing essential tasks. In most cases, the negative view of firewalls stems from a basic misunderstanding of the nature of firewalls and how they work. This chapter will help dispel this confusion.
This chapter clearly defines the fundamentals of firewalls. These include what a firewall is, what a firewall does, how it performs these tasks, why firewalls are necessary, the various firewall types, and filtering mechanisms. Once you understand these fundamentals of firewalls, you will able to look beyond the unschooled opinions, common mythology, and marketing hype surrounding them, and the crucial benefits of effective firewall architecture will become clear. Like any tool, firewalls are useful in solving a variety of particular problems and in supporting essential network security.
A firewall is like a border sentry. A firewall is like a gateway. A firewall is like a traffic control device. A firewall is a filtering device that enforces network security policy and protects the network against external attacks.
As a filtering device, a firewall watches for traffic that fails to comply with the rules defined by the firewall administrator. Firewalls can focus on packet header, packet payload, packet header and payload, the content of a session, the establishment of a circuit, and possibly other assets. Most firewalls focus on only one of these, rather than all of them. The most common filtering focus is on the header of the packet, with the payload of a packet a close second. Many firewall products focus on more than one aspect of communication filtering.
Filtering allows what you want on your network and denies what you do not. Filtering relies on filtering rules. Each rule has a pattern of concern and a response the firewall will make if an incoming element matches the pattern.
Firewalls follow a philosophy or stance of security known as deny by default, allow by exception. All the rules on a firewall are exceptions. Some exception rules define what you allow. Some exception rules define what you wish to deny. The final option, sometimes called the final rule, is anything that did not match one of the exceptions denied by default.
Firewall filtering compares each packet received to a set of exception rules. These rules state that content in the packet is either allowed or denied. If the packet matches an allow rule, it continues on to its destination. If the packet matches a deny rule, then the packet is dropped. Hence, a deny rule prevents the packet from reaching its destination. If a packet fails to match any rule, then the firewall drops the packet by default.
The filtering rules are the exceptions to the deny all rule that is the final and absolute rule of a firewall. In fact, if a deny by default rule didn't exist, the filtering device would not be a firewall at all. Instead, it would be more like a router or switch, allowing traffic to pass, even if it did not match an expected pattern or rule. So, keep in mind the security stance of deny by default, allow by exception. A firewall is a filtering device that helps support this stance.
Think of a firewall as a sentry along the borders of a country. The term firewall is not exactly the best term that could have been selected for this device or service that performs essential security filtering for hosts and networks. The term firewall comes from a building and automotive construction concept of a wall that is built to prevent the spread of a fire from one area into another. The firewall in a building or car engine compartment is a physical block against the spread of fire.
Network security administrators use the term firewall to refer to a device or service that allows some traffic but denies other traffic. This is not the same as a building's firewall, which only allows a fire to spread if the firewall fails. In network security, firewalls allow traffic through that's considered safe—or at least authorizes traffic without the entire firewall failing. Additionally, if a firewall does fail, it fails into a secured state. This means that when the firewall is offline, is locked/frozen, or otherwise experiences a problem, it stops all traffic, rather than allowing all traffic through. This is known as fail-safe or fail-secure.
Better ways to envision the job of the firewall are a sentry, doorman, or even border guard. These people positioned at the entrance or exit of a building watch for unauthorized attempts to enter the secured area. Some people are allowed to enter; others are prevented. In the event that the sentry isn't present, the doorway is locked, so only those with a key can enter. Think of a firewall as a border sentry.
A gateway is an entrance or exit point to access a controlled space. We all use gateways everyday in a variety of ways. An on-ramp is a gateway to the highway, a doorway is a gateway to a building, and a personal computer is a gateway to the Internet—and to your organization's network. You can also think of a firewall as the gate at a gateway. The firewall stands at the entrance of a network to block unwanted traffic.
Gateways are important because, typically, high levels of traffic pass through a gateway. Thus, positioning a firewall at a network gateway is an aspect of secure design. If the gateway already exists in the network infrastructure, then positioning the firewall at that point is an obvious security improvement. A firewall so positioned watches over all traffic crossing that gateway point.
If a network is still in its design phase, a network designer might make the secure choice to create a gateway in the network's layout. However, in this situation, the concentration point would be known as a choke point instead of a gateway. If a gateway is an access point to other areas of resources, a choke point is a specialized kind of gateway that focuses on traffic to a single concentrated pathway to simplify the process of filtering.
Whether labeled as a gateway for resource access or a choke point to control security, the result is the same. A firewall positioned at a gateway provides filtering services across all traffic. The choke point provides filtered access to resources. As a wise poet once said: "Good fences make good neighbors." So too, good gateways and well-positioned firewalls make secure networks.
You can also think of a firewall as a traffic control device. A significant amount of network security is little more than controlling traffic. Authorized traffic passes through the digital intersection, while unauthorized, unwanted, abnormal, or obviously malicious traffic is blocked.
The very basic and original form of the modern firewall was a screening router. Routers analyze traffic based on destination address. The best-known available route to the destination informs the Forwarding decision. However, screening routers added in additional rules that could discard traffic based on destination or source address. Once filtering expanded to address protocols and even ports, the screening router became the basic static packet filtering firewall.
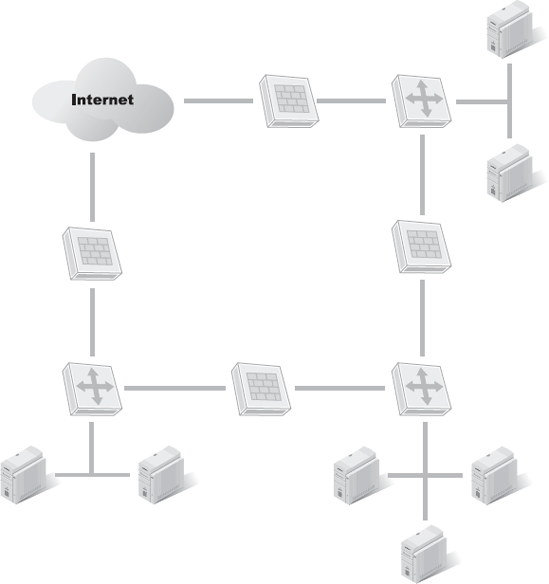
In addition to filtering, firewalls can also offer routing functions, which are a holdover from this router ancestry. A multi-homed firewall can grant traffic access to one or another interface or segment based on the results of filtering. Traffic for a private LAN could traverse one segment, while traffic destined for the DMZ could follow another (see Figure 2-1). A firewall is an efficient, necessary traffic control device on the highway that is your network.
A firewall enforces your organization's network security policy. Specifically, a firewall enforces the network traffic access control security policy. A firewall is the physical embodiment of the security policy. It's the most obvious or direct enforcement of access control on your network's traffic. No device more than your firewall is as directly involved in allowing authorized traffic and denying all else.
A security policy defines the goals, objectives, and procedures of security. Every security policy focusing on network security requires the deployment of a firewall. The firewall's job is to impose all restrictions and boundaries defined in the security policy on all network traffic. A firewall enforces your organization's network security policy just as a traffic policeman enforces the motor vehicle laws of a town or state.
A firewall's critical function is to protect your network against external attacks. It's no secret that threats from without are numerous. The onslaught of attacks is almost unbelievable, like a constant flood against every Internet-connected node. If it were not for vigilant hardening of hosts and the use of firewalls, the Internet and private networking as we know it could not exist.
It's no accident that some threats to computer networks are called viruses: external threats seem to continuously change and evolve. Some attacks are targeted specifically for your network or organization. Some attacks are untargeted and random. Instead, they are directed toward any host that happens to have a specific vulnerability. Malicious code relentlessly infects and compromises unprotected computer systems. Flooding attacks attempt to interrupt timely Internet communications. And these are only some of the external threats facing your organization's network.
A firewall stands as a sentry, as a front guard, as a defense against all attacks and attempts at system compromise. The good news is that many firewalls are well hardened against all known-to-date attacks. These firewalls can withstand the blitzkrieg of the attacks without faltering. A firewall protects the network against the substantial asset damage that external attacks can cause.
Understanding these definitions and distinctions are only the beginning of understanding firewalls. These topics are explored further in this chapter as well as in Chapters 7-11.
A firewall is an essential part of network security. However, it's not the whole of network security. Don't make the mistake of deploying a firewall while ignoring other security management activities. A firewall is only one piece of the large complex puzzle of network security.
There are many things a firewall is not. Don't be fooled by the marketing. Some of these "deficiencies" can become cloudy as vendors sell combination or multi-function solutions. Often, these devices are designed for the SOHO or home user and thus were never intended to provide commercial-grade protections.
A firewall is primarily for network traffic filtering.
But it's not an authentication system. Firewalls aren't designed to check logon credentials, compare biometric scans, or even confirm the validity of digital certificates. These are the functions of an authentication service, typically hosted on a domain controller or primary network server.
That said, you might find it necessary for a firewall to allow authentication before granting access to a resource or allowing a session. Some firewalls can have enhancement features that provide for firewall-hosted authentication services. However, in many cases, a better solution would be to have the firewall offload that task to a dedicated authentication server or service, such as 802.1x, Public Key Infrastructure (PKI), or directory services. Most security experts do not recommend using a firewall to authenticate users, or at least not as a replacement for a network's directory service or centralized authentication solution. Firewalls are not authentication systems.
A firewall is not a remote access server. Connections from remote users do not have an endpoint at the firewall. Instead, the endpoint is a remote access server (RAS) or network access server (NAS). A firewall may function before or after the RAS/NAS to filter remote access traffic. However, that doesn't mean the firewall is the RAS/NAS itself.
Your firewall should of course filter all remote traffic. Especially since remote traffic is much more likely to be purposefully malicious or accidentally damaging than local traffic. Why? An organization has much more control over who can connect to their network locally than it does when it allows remote connectivity. Remember: A firewall does not replace a remote access server.
Like Superman, your firewall does not have x-ray vision into encrypted traffic; in other words, it cannot see the contents of encrypted traffic. A firewall can filter on the header of traffic using transport mode encryption, since the original header is in plain text form. However, a firewall cannot filter the original header of traffic using tunnel mode encryption, since the only plain text component is a temporary tunnel header that only includes information about the endpoints of the tunnel. It's like trying tell what's in the boxcars of a train, by observing only the locomotive and the caboose.
Position your firewall where it can be most effective. If the security design requires that all traffic content be examined by a firewall, then you need to position the firewall after encryption is removed from the traffic. If the security design only requires filtering on non-encrypted traffic, then positioning the firewall is not as critical.
Firewalls designed for use by Web e-commerce sites may have an additional ability to act as the endpoint of a Secure Sockets Layer (SSL) or Transport Layer Security (TLS) tunnel from an Internet client. This grants the client protection for their data as the information traverses the Internet. This allows a firewall to filter the content of the traffic before the Web server receives and processes the information.
Encryption is one method to evade filtering. Users and hackers can employ client-side encryption solutions that encode the data before transmission or create unauthorized encrypted encapsulation tunnels to prevent firewall filtering. In this situation, your network security policy may stipulate that the firewall needs to block encrypted transmission initiated by clients, especially if the destination is on the Internet. It's important to remember that firewalls are powerful, but they don't have x-ray vision into encrypted traffic.
A firewall is also not a malicious code scanner. Firewalls are traditionally rule-based filtering products. These rule sets usually have only a few dozen to at most a few hundred rules. To filter malicious code, the rule list would need millions of entries. As of Dec 2009, the AVG Anti-Virus definition database #270.14.88/2538 was tracking 24,303,360 malicious code infection definitions. That number of entries is simply impractical to include in a firewall rule set.
Some firewall products include an enhancement or add-on module for malicious code scanning. Such an enhancement is just an add-on component, not a core feature of a firewall. In most cases, it's more efficient and more secure to use separate anti-malware scanners than to add this function to your firewall.
Many firewall rules block traffic with spoofed addresses, uncommon ports, unauthorized protocols, invalid header constructions or values, etc. Such rules block a significant amount of traffic caused by malicious code, but these rules do not themselves directly block malware from entering or leaving a network. Keep in mind that your firewall can do many things, but it's not a malicious code scanner.
A firewall is also not an intrusion detection system. An intrusion detection system or IDS is a type of network burglar or intruder alarm that detects and responds to unauthorized activity inside your network. An IDS performs this task by monitoring all network traffic. While an IDS can be deployed on a network border or outside the network against the Internet, most IDSs operate inside private networks so that they can watch all internal network traffic.
A firewall can only detect malicious traffic when such traffic enters one of the firewall's interfaces. Firewalls generally don't watch over general interior network activity. Either firewalls are border devices for networks and subnets, or they are software products watching over a single host. In either case, they cannot see the same traffic nor perform the same tasks as an IDS. A firewall, therefore, is not interchangeable with a good intrusion detection system.
Note
IDSs can detect a plethora of unwanted activities, use several methods of detection, and can perform a wide range of responses, both passive and active. You'll find more on IDSs in Chapter 1 in the section, "Common Network Security Components" and in Chapter 15 in the section, "Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS)".
A common misconception is that firewalls protect against insider attacks; they cannot. A firewall can be a border device or a firewall can be software on a host. A border firewall can filter traffic entering or leaving a network or subnet. So a border firewall is unable to see any interior traffic (Figure 2-2). When an attacker from an inside client attacks a target that is also an internal host, a border firewall is not part of the communication and thus cannot detect nor block the attack.
A host software firewall can only see the traffic entering or leaving that one host. A host software firewall is unable to see any other interior traffic
Of course, if traffic does not pass through its interfaces, a firewall cannot filter the traffic. A firewall can only filter on what it sees. If malicious or unwanted traffic does not enter an interface of a firewall, the firewall will not be able to filter that traffic (see Figure 2-2). So you'll want to place firewalls on each host, on every border gateway or choke point, and between each significant subnet or interior network division. Another thing firewalls can't do is protect against social engineering. Social engineering is the category of attacks that focus on the personnel of an organization. These attacks get information from people just by asking for it in clever ways or convincing someone to perform an action that breaches network security. The only real protection against social engineering is worker training and awareness. A firewall cannot stop the attack stemming from social engineering.
A firewall can't protect against the threat posed by removable media. The widespread use of removable media has been a significant threat to every computer in existence, even those not connected to the Internet, an external network, or even a single other computer through a network link. Removable media include USB hard drives, USB thumb drives, CDs, DVDs, Blu-ray discs, HD-DVD discs, other optical discs, flash memory cards, firewire storage devices, tape media, e-mail attachments, and more. Removable media can leak information out of an organization or smuggle malicious code in. A firewall is not involved in the use of removable media nor any of the contents these devices may contain. A firewall cannot protect your network against the ongoing threat posed by removable media. Again, the best defense against this threat is good company policy, worker training, and awareness.
A firewall, of course, cannot protect against physical incursions or attacks. Physical attacks bypass any and all logical and electronic protection mechanisms. A firewall does not protect against theft of devices, planting of eavesdropping mechanisms, disconnection of cables, connecting a rogue notebook to an open node, destruction of equipment, dousing electronics with liquids, building fires, or any other form of physical attack. Only effective physical defenses can deter physical attacks. A firewall is not designed or intended to thwart physical attacks.
Firewalls aren't insurance against inept or ignorant administrators. Computer equipment and software can only do what it's designed and programmed to do. If an administrator mis-configures a security device, the device doesn't automatically compensate for that oversight. If a security administrator fails to learn about all the features and defaults of new equipment, the product cannot secure itself autonomously. Security requires training, research, careful planning, thoughtful implementation, and ongoing review and maintenance. This process is known as security management—and it takes work. The old expression was never more true than today: "Garbage in, garbage out." What you put into network security is precisely what you will get out of it. So remember that a firewall can't compensate for ineptitude or ignorance on the part of administrators.
In the same vein, firewalls can't compensate for poor security management. Proactive security management is essential for the success of any security endeavor. Security management is the process of reviewing, testing, tuning, and updating an organization's security policies and security infrastructure. This is an ongoing effort that requires knowledge, research, and vigilance. The threats and risks facing an organization are constantly evolving to become more persistent and virulent. Your security strategy should be just as rigorous and purposeful in defense. Keeping up to date on the most current threats to and trends in network security is a big part of this job. Networking, conferencing, and reading the latest industry literature are ways to keep yourself and your security efforts sharp.
Keep in mind that a firewall is a focal point of security. It's an embodiment—a physical representation—of your organization's security policy. When you use them well and wisely, firewalls provide reliable and consistent security from external threats. However, firewalls are a tool with limitations and are only part of the complete security strategy. By itself, a firewall cannot protect a network against every threat. A firewall cannot compensate for the lack of informed, state-of-the-art security management.
Furthermore, and this follows from everything we've discussed so far, firewalls are not a substitute for a solid, written security policy. A firewall is nothing but a reliable border sentry. It is not the complete security infrastructure and strategy. Even the decision to deploy a firewall is a significant strategic undertaking that shouldn't be taken for granted. Thorough research and planning will help design and deploy an effective firewall. A firewall policy ensures the success of your network's firewall. A company-wide security policy ensures the success of your organization's security infrastructure. Firewalls are in no way a substitute for such a security policy.
Finally, firewalls are not a perfect solution. As we've noted, a firewall is a border sentry, reliable but limited. A firewall can only filter what it sees. It can only perform filtering according to the rule sets defined by the security administrator. It cannot self-adjust to changing conditions or future threats. A firewall is only a part of a complete security infrastructure. Firewalls are mostly software, even when operating on dedicated hardware. They are software, written by fallible humans; they can, and do, therefore, have bugs and flaws. A firewall is never the perfect solution—but it is part of the solution.
Fortunately, in spite of all the things a firewall is not, a firewall is a solid filtering solution. A firewall can and should protect the borders of networks and individual hosts. No security strategy—or deployment—is complete without properly installed firewalls.
"Who needs a firewall?" Anyone who uses a computer to interact with and exchange resources with any other computer! Your personal computer needs a firewall. Your home network needs firewalls. Your company network needs firewalls. Every network needs firewalls. They are a fundamental of network communication.
High-speed Internet connectivity has become ubiquitous. Most computer users now have high-speed access at home, at work, and even on the go through mobile devices. Often, these broadband connections are always-on connections. This means computers and networks are online all the time—and exposed to attacks. A drawbridge is easy to cross if it's always down. When a system is always connected, it can be the focus of a concerted attempt to discover its vulnerabilities and breach its security.
How likely is it that a computer will be discovered and attacked over the Internet? Almost guaranteed. Most systems are detected, scanned, and probed within minutes of obtaining a public IP address. It is technical suicide to connect your system to the Internet before installing a firewall, as well as installing the latest vendor patches for the hardware, OS, and installed applications.
Does this mean that there are armies of hackers just waiting to find new targets to attack? Unfortunately, yes. Not, however, in the way you might think. Malicious programs perform most of the scanning and attacking automatically. These are commonly known as agents, robots, zombies, or just 'bots. Groups of malicious code, known as botnets, scour the Internet for new victims constantly.
Another wrinkle in being constantly online over a broadband connection is the throughput speed. High-speed links to the Internet enable high-speed attacks against your system. On older, slower connections, the same risks existed, but the attacks were slower or fewer simply because the link to a targeted system throttled the speed of the attack. With 10 Mbps and faster connections common, attacks can occur at near-lightning speed.
This is not to suggest that only slow-speed Internet links are secure. On the contrary, you should take full advantage of high-speed Internet connections. However, you need to protect your systems with firewalls. A firewall will impose a significant barrier to most attacks that originate from the Internet.
With a firewall protecting your system from the Internet, hacker scans will be nearly worthless. Responses to probing packets will be filtered. An outsider will learn little about your infrastructure. This, in turn, means they will discover fewer vulnerabilities, thus wage fewer attacks. And even then, those attacks will more likely fail.
Firewalls are not only used for Internet protection. Don't forget that significant levels of threat exist internally. Firewalls stand guard against network segments inside your private network (Figure 2-3). Think of a firewall as a tool to prevent abuse or misuse of LAN resources. Each major department, subnet, or other relevant distinction within an organization should have firewall protection. This will ensure that accidental compromises, as well as intentional abuses, are minimized internally. All networks protect against both internal threats as well as external ones.
Don't overlook that, while a firewall has its origins in routing, you still want to use a dedicated router for routing and a dedicated firewall for filtering. In many cases, the combination or multi-function devices offer lots of features, but not necessarily best of breed performance and efficiency. These may be money-savers for small networks, but they are often cause for expense for larger networks. If a device fails to perform at commercial levels when necessary, the repercussions can cost more than deploying the proper safeguards in the first place.
Firewalls should be used to protect a resource, no matter where that resource resides on your network. A hardware firewall can protect a single host or a network of hosts, while a software firewall can only protect a single host. Don't limit your definition of a firewall to just a border sentry device. Think of it, instead, as a sentry device in general, able to protect anything placed behind its filtering service.
Host firewalls protect a host and protect a network from the host. A host firewall's job is to filter traffic entering or leaving a single computer system. Attacks and malicious traffic can come from the Internet or the local network. A host firewall can protect the host against such threats. However, the host itself could be compromised by malicious code or be controlled by a malicious user. In this situation, the host firewall protects the network from the threats coming from the host.
Another way of looking at this is that a host firewall also protects the network from a user in general. A user is the most risky element in a network infrastructure. Even if every other component, hardware or software, does what it was programmed and configured to do, you can decide to violate security. Thus, the free will of human users is one of the biggest risks to every computing environment.
Users can be ignorant, make mistakes, be tricked by a Trojan horse, be the target of social engineering attacks, and perform malicious actions on purpose. The security of a host system, including general system hardening, anti-malware scanning, Internet client restrictions, blocking of non-approved software, and a host firewall, are all designed to protect the network from the risk of human users.
Firewalls protect against Internet threats, internal network threats, protect resources generally, and protect against the risk of users. These capabilities alone might make installing a firewall on every host and on every segment seem like the obvious follow through.
However, deploying firewalls everywhere has two significant drawbacks: cost and over-dependence. Most commercial grade firewalls are costly. Even if they have no purchase cost, due to promotions or being open source, the ongoing maintenance costs of firewalls add up significantly over time. With firewalls deployed on every host and on every segment, the overhead of firewall management would far exceed the total IT budget of most businesses.
A second drawback to ubiquitous deployment of firewalls is over-dependence. Firewalls are only part of a complete security solution, not a whole solution by themselves. By deploying firewalls on every host and every segment, other essential security endeavors might be overlooked or deemed unnecessary. This would be a disastrous security stance. Firewalls cannot compensate for poor security policy, poor security management, or a lack of proper system hardening.
With these concerns, how can your organization determine how many firewalls to deploy and where to deploy them? In most cases, this requires a process risk assessment and risk management. Risk assessment is a process of examining values, threat levels, likelihoods, and total cost of compromise versus the value of the resource and the cost of the protection. While many other factors affect risk assessment, this essential business and security process is as follows:
Determine the overall value of the resource or asset. Known as the asset value (AV), this calculation should include both tangible and intangible costs and value.
Determine the threats that face that asset. For each threat, calculate the exposure factor (EF), or the amount of potential harm expressed as a percentage. This will create a list of asset-threat pairs with a corresponding EF.
Calculate the single loss expectancy (SLE): SLE = AV × EF. This is the amount of potential loss that could be experienced due to a single occurrence of compromise against this asset for a specific threat. This will add an SLE value to each asset-threat pair.
For each threat, calculate the potential number of times the threat could be a realized attack within a year's time. This is known as the annualized rate of occurrence (ARO).
Calculate the annualized loss expectancy (ALE): ALE = SLE × ARO. This is the amount of potential loss that can be experienced due to any compromise of this asset for a specific threat within a year. This will add an ALE value to each asset-threat pair.
Sort the list of asset-threat pairs by the ALE. The highest ALE is the biggest risk for this specific asset/resource.
Take the asset-threat with the largest ALE and determine the possible counter-measures that could be used to protect against that threat. This creates asset-threat-countermeasure triplets.
For each asset-threat-countermeasure triplet, calculate a new ARO. The countermeasure should reduce the ARO. A perfect countermeasure would reduce the ARO to zero. There are few perfect countermeasures.
With the new ARO, calculate a new ALE for each asset-threat-countermeasure triplet.
For each asset-threat-countermeasure triplet, calculate the potential cost/benefit. The formula for this is: (Original ALE — New ALE) — cost of the countermeasure per year.
Sort the asset-threat-countermeasure triplets by their potential cost/benefit. The triplet with the greatest cost/benefit is the best choice.
In short, if the best cost/benefit for a particular asset-threat is for a firewall, then installing one is a good business, security, and budget decision. If some other countermeasure has a better cost/benefit, then that countermeasure is the better choice.
Performing detailed risk analysis is a complex task. Many small companies or home network enthusiasts might not want to spend the effort to perform a complex risk assessment. This is understandable, but failing to perform a full risk assessment doesn't mean that you have no risk or that you have no assets worth protecting.
At a minimum, you need to protect any and all data that is personally identifiable. This includes personal communications like e-mails, any custom crafted document, picture, video, or other file type, all medical information, all financial information, configuration settings, passwords and other credentials. Identity theft is one of the most frequent and devastating crimes of the interconnected world. Worrying only about your neighbors, the random home burglary, or the pickpocket on the street is nothing short of tunnel vision. Today, you must be concerned about all would-be criminals across the globe attempting to gain access to your electronic assets over the Internet.
Who needs a firewall? Everyone with a networked computer needs a firewall. Why are firewalls necessary? Firewalls are critical because threats and malicious entities lurk on the Internet, on private networks, and possibly within your own home!
A zone of risk is any segment, subnet, network, or collection of networks that represent a certain level of risk. The higher the risk, the more security you need to protect against that risk. The less of a risk associated with a zone, the less security is necessary because the threats of that zone pose less chance of harm.
The flipside of zones of risk is zones of trust. Highly trusted zones naturally require less security, while zones of low trust require more security.
Each zone of risk needs to be clearly and distinctly isolated from any other risk zone, especially if those zones have different levels of risk. The primary tool used to isolate zones from each other is the firewall.
Most networks have two to four zones of risk. These include the private network, DMZ, extranet, and the Internet. See Figure 2-4. The private network zone has the lowest risk and is the zone of the highest trust. The Internet zone has the highest risk and is the zone with the least trust. A DMZ has less risk than the Internet, but is not as trusted as the private network. A DMZ zone has medium-high risk or medium-low trust. An extranet has more risk than the private network and more trust than the Internet. An extranet zone has medium-low risk or medium-high trust. See Table 2-1.
Your organization's written security policy should define where these zones exist and dictate the security requirements for each zone. Such requirements would include traffic management, use of firewalls, use of VPNs to cross the zone divisions, hardening of systems, malicious code scanning, and so on. Firewalls are likely found at risk zone divisions and may be the best cost/benefit security countermeasure in some circumstances. The next step is to understand what a firewall can do at these points and how it performs these tasks.
Firewalls work along a communication pathway. This can be the gateway point of a network, a choke point within a network, a point of zone transition, or on a host. In these locations, the firewall interrupts the traffic flow to inspect packets or sessions. If the contents are authorized, they continue to their destination. If the contents are not authorized, they are blocked and dropped.
Firewalls operate on a bastion host basis (Figure 2-5). This is most obvious in the case of hardware firewalls, but it's true of host software firewalls, as well. A bastion host firewall stands guard along the pathway of potential attack, positioned to take the brunt of any attack. A firewall acts as the vanguard, as the front line of defense against any attack. A bastion host can also be called a sacrificial host.
In the case of a host software firewall, the firewall will attempt to prevent all malicious interactions to and from the host. In the event that the firewall itself is compromised, it usually disconnects the system from the network. While this is a form of DoS, it's often a preferred fail-safe/fail-secure response over defaulting to an open unrestricted and unfiltered connection. This is especially true if the connection is directly to the Internet. Bastion host deployment is discussed further in Chapter 8.
If the firewall is able to rebuff an attack, then the resources are secure. If the firewall falls due to the attack, it prevents any further communication with the resources behind it. Think of a firewall as a dead-man switch. If the firewall fails or goes offline, so does the connection it was filtering.
The most common function of a firewall is to screen or filter traffic. The firewall checks any packet received on its interface against its rule set to determine whether to forward or drop the packet. As we discovered earlier, firewalls typically function on a deny-by-default, allow-by-exception security policy.
The firewall performs most traffic filtering based on information in a packet or segment header. This can include the IP address of the source and destination, as well as the source and destination port. Some firewalls can also filter or block specific protocols or certain uses of protocols. For example, a firewall could block all streaming media protocols and block just the Internet Control Message Protocol (ICMP) type 3 (destination unreachable) and 11 (timeout exceeded).
Firewalls differentiate between networks or subnets. A firewall serves as a clear and distinct boundary between one network area and another. By positioning a firewall between network divisions or subnets, the network designer and security administrators are using traffic management and control for traffic attempting to cross that intersection. Firewalls serve as boundary devices both on the edge of networks facing the Internet, as well as internally between different divisions within an organization.
Open and unrestricted internal communications might sound like a good idea, but in practice such traffic causes severe degradation of overall infrastructure performance and stability. By preventing or at least limiting communications between certain divisions of an organization, traffic efficiency increases. Additionally, traffic control and management decreases risk.
For example, by blocking communications between the programming group's network and the production network, unapproved versions of software cannot leak out. Additionally, blocking general access to the accounting subnet, the research and development subnet, the DMZ, and the extranet from the production network protects against data leakage, spread of malicious code, and other forms of fraud and abuse.
Firewalls can act as a general filter for malicious activity or as a one-way sieve. As a general filter, a firewall will allow all normal benign traffic to pass through. This is the type of firewall used to protect a DMZ or differentiate subnets within a LAN. A general filter firewall works to stop malicious activities.
A general filter firewall can allow communication using any protocol on any port or to limit communications to specific protocols and ports (amongst other limitations). If only a few specific resources hosted behind the firewall are to be accessed by external users, the firewall can allow access to those specific internal systems based on IP address and port, but block all other inbound requests.
A sieve firewall will only allow traffic to originate from the private or trusted side. A sieve firewall will allow non-malicious responses to return from the public or less-trusted side, but it will generally block or prevent any initiation or inbound communication request from the outside. A sieve firewall typically protects a private LAN or an extranet.
Firewalls can support special inbound authorized connections with the LAN, such as VPN links from telecommuters. This is an important feature for an extranet, as well, since VPN access is often the only method to reach hosted resources through the Internet.
Firewalls can provide port-forwarding services. Port forwarding is a form of static reversal of network translation. In traditional or dynamic NAT or network address translation, external entities cannot initiate communications with internal systems because any packet received by the outside interface of the NAT system will not find a matching mapping in the translation table and therefore drops the packet as invalid.
With port forwarding or static NATing, a translation mapping is coded so that an external IP address and port combination are fixed and redirect traffic to a specific internal system, even if the internal system uses a private IP address. The combination of an IP address and a port number is known as a socket. In Figure 2-6, the external port 208.40.235.38:8081 is forwarded to an internal server's port at 192.168.5.74:80. Port forwarding can also be called static NAT, traffic forwarding, service redirection, reverse proxy, and "punching a hole through the firewall." Port forwarding and reverse proxy are discussed further in Chapter 8.
The alias "punching a hole through the firewall" points out a very important concern: namely, that using port forwarding reduces the effective security provided by the firewall. Without port forward or other similar services, a firewall can rebuff attempts to communicate with internal systems. Using port forwarding, you create a pathway across the primary border sentry. Several hacker exploits can take advantage of port forwarding to reach other internal systems on other ports than what was "allowed" by the port forwarding settings. These attacks are usually variations of fragmentation manipulation and are discussed in Chapter 4 "Network Security Threats and Issues."
Managing and controlling traffic is a primary concern and function of firewalls. Only authorized communications are allowed; everything else is blocked. The act of determining what to allow and what to block depends on the filtering features of the firewall. These include packet inspection, connection or state management, stateful inspection, and others. These filtering concepts are defined later in this chapter in the section, "Types of Filtering."
In addition, firewalls can block or filter outbound traffic. This function can block spoofed traffic or anything with an invalid IP address as the destination or source. Specific protocols or ports can be blocked, as well. And of course specific domain names or destination addresses can be blocked.
Firewalls can also filter based on content. The firewall can intercept specific content in a packet leaving the network before it reaches the outside. This could result in the packet being discarded, an entire connection being dropped, or the packet being edited to remove the blocked content and replace it with something else. Content filtering can focus on domain name, URL, filename, file extension, or keywords in the content.
Another capability of firewalls is the ability to filter based on encryption. A firewall can allow encryption without restriction. Or, a firewall can be set to block encryption on some ports and not others. Firewalls can also block encryption from and to all internal IP addresses except for servers, VPN devices, and RAS/NAS. The issue of firewalls and encryption is discussed further in Chapter 7.
Firewalls can perform intermediary functions between hosts where network administrators deem direct communication too risky. This is the basic function of a proxy. A proxy firewall positioned along a communication path can hide the identity of one or both endpoints of a communication from the participants. In most cases, proxy services hide the identities of internal systems from external entities.
Firewalls can perform address conservation through the use of an address conversion or translation system. NAT or network address translation is the most common translation service supported by networks. As discussed in Chapter 1, NAT translates between internal addresses and public external addresses. NAT allows a private network to use the RFC 1918 private IP addresses. This, in turn, provides additional security, since Internet hosts cannot address an RFC 1918 system directly.
Through the combination of all their features, functions, and capabilities, firewalls provide consistent, reliable protection for an organization's computer and electronic resources. But firewalls are not perfect and should not be the sole security component of a network infrastructure. They are only one element—although an essential one—of a network security strategy.
Firewalls can log events. Firewalls can be set to record any action into a log file. In addition, they can record the content of any malicious traffic into a log file. And they can record any abnormal network activity, performance levels, and traffic statistics into a log file. Logging events is an invaluable feature of a firewall. You can learn more about firewall logging and understanding those logs in Chapter 7.
Since perfect security products don't exist, you must rely on monitoring to watch for attempts (and any successes) to breach or violate security. Recall from Chapter 1 that security is locking things down to the best of your ability, and then watching for attempts to breach your defenses. Lock, then watch. A successful security strategy is not possible without both locking and watching. Additionally, most security components should include a locking and a watching aspect to them. Firewalls are no exception. If a proposed firewall product is unable to record a log of its actions and network activities, then you need to seek out a different firewall product. Remember the time-tested business adage: "You get what you inspect, not what you expect."
To fully understand the mechanisms of filtering employed by firewalls, you need a solid understanding of the TCP/IP protocol suite. Thorough knowledge of TCP/IP benefits a security administrator not just in the area of firewall management, but also in routing, switching, maintaining availability, improving network performance, managing network traffic, analyzing protocol, understanding vulnerabilities and exploits, and even performing penetration testing or ethical hacking.
Most networks, including the Internet, use the TCP/IP protocol. As discussed in Chapter 1, the most prevalent version in use is IPv4. However, IPv6 is gaining wider use across the globe. During this transitional period, you should learn about both versions of IP. If you need additional detailed information regarding TCP/IP, please consult:
Stevens, W. Richard, and Gary R. Wright. TCP/IP Illustrated, Volumes 1-3. Addison-Wesley Professional, 1994.
Kozierok, Charles. The TCP/IP Guide: A Comprehensive, Illustrated Internet Protocols Reference. No Starch Press, 2005.
Comer, Douglas E. Internetworking with TCP/IP, Vol 1 (5th Edition). Prentice Hall, 2005.
The ARIN IPv6 Wiki at
http://www.getipv6.info.
Note
The OSI model is the documented standard for discussing and describing network protocols. However, TCP/IP is the de facto or practical standard, as it was actually in use before the OSI model was developed into actual protocols. Few products can directly support the OSI model or its derived protocols. Instead, most products support TCP/IP, in spite of its not being the official, documented standard from the International Standards Organization.
Most protocol discussions begin with the open system interconnection reference model (OSI model). The OSI model is a standard conceptual tool used to discuss protocols and their functions. The OSI model has seven layers (Figure 2-7). Each layer communicates with its peer layer on the other end of a communication session. While the OSI model is helpful in understanding protocols, most protocols are not in full compliance with it.
Below is a brief description of the OSI model's seven layers. Each layer has unique responsibilities, functions, and features. The OSI model defines what needs to take place at each layer and leaves the actual process of accomplishing those tasks to the protocols and, ultimately, to the protocol programmers.
Application layer (Layer 7)—This layer enables communications with the host software, including the operating system. The application layer is the interface between host software and the network protocol stack. The sub-protocols of this layer support specific applications or types of data.
Presentation layer (layer 6)—This layer translates the data received from the host software into a format acceptable to the network. This layer also performs this task in reverse for data going from the network to the host software.
Session layer (layer 5)—This layer manages the communication channel, known as a session, between the endpoints of the network communication. A single transport layer connection between two systems can support multiple, simultaneous sessions.
Transport layer (layer 4)—This layer formats and handles data transportation. This transportation is independent of and transparent to the application.
Network layer (layer 3)—This layer handles logical addressing (IP addresses) and routing traffic.
Data link layer (layer 2)—This layer manages physical addressing (MAC addresses) and supports the network topology, such as Ethernet.
Physical layer (layer 1)—This layer converts data into transmitted bits over the physical network medium.
As data moves from a software application for transmission over the network, it traverses the layers of the protocol stack from top to bottom. As each layer receives data from the layer above it, that data becomes the payload with a layer specific header (Figure 2-7). At the Data link layer, where Ethernet resides, the data receives a footer, as well. This process is known as encapsulation. The inverse, known as de-encapsulation, occurs when a network communication is received. As this process takes place, the data set being manipulated receives unique names, depending on the layer it traverses. They are:
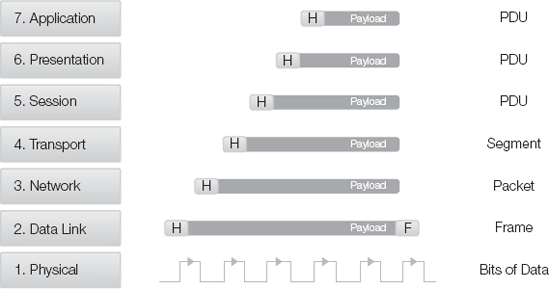
Figure 2-7. The process of encapsulation and the names of header and payload sets at each OSI layer.
The encapsulation process of adding headers (and a footer at the Data link layer) enables data exchange between layers on different systems. This is known as peer-to-peer communications. The content of a header includes information to be processed by the corresponding layer on the receiving end of a network link.
The content of the headers, mainly from layers 2-4, are the greatest concern and focus of a firewall. Application proxy firewalls and stateful inspection firewalls can also examine the headers and the payload content of layers 5-7. Learn more about the methods of filtering based on this layer information in the section, "Types of Filtering" later in this chapter.
TCP/IP is not a single protocol, but a collection of protocols. Often referred to as the TCP/IP suite, this collection includes several core protocols, such as IP, Transmission Control Protocol (TCP), and User Datagram Protocol (UDP), as well as several commonly used protocols, such as ARP, ICMP, HTTP, and TLS. In addition to these, tens of thousands of other protocols can operate within the network infrastructure created by TCP/IP.
Since the focus and purpose of this book is an introduction to network security, firewalls, and VPNs, and not an introduction to networking or protocols, firm knowledge of these sub-protocols of TCP/IP is assumed, but not essential to grasping this book's scope.
Firewalls, specifically packet-filtering firewalls, inspect the contents of headers to allow or deny frames, packets, or segments. Depending on the type of filtering and the layer or protocol focus of the filtering, the item examined and header it comes from can vary.
Packet filtering often focuses on four main headers:
The Ethernet header of the frame from the data link layer
The IP header of the packet from the network layer
The TCP header of the segment from the transport layer
The UDP header of the segment from the transport layer
Each of these four headers has numerous details that affect a filtering action. These include MAC addresses, IP addresses, TCP header flags, port numbers, and more.
You learned about the basic differences in IPv4 and IPv6 addressing in Chapter 1 in the section, "IPv4 Versus IPv6." The issue to focus on here is not the length of an address or subnet masks, both of which are important, but rather the issues of source and destination, public and private, known and unknown, benign and malicious, as well as real and spoofed addresses.
Many forms of filtering focus on IP address and/or port number to make an allow or deny decision. Such decisions or rules can focus on either the source address or the destination address found in the header of a segment, packet, or frame. In other words, port number, IP address, or MAC address can support filtering as either a source and/or destination concern.
Firewall filtering can focus on whether an address is public or private in both the source or destination position in the IP packet header. Generally, private addresses function on the private network and do not reach the outside. NAT will translate source-private addresses into a public address if the packet is heading towards an external destination. On the Internet, both routers and firewalls drop any IP packet that has an RFC 1918 address in the header. Firewalls can filter on whether an address is known or unknown. This function filters against addresses used for the source and/or the destination. Known addresses are usually trusted addresses. Packets with only trusted and known addresses are allowed to reach their destination. Unknown addresses are potentially not trusted. Packets with unknown addresses can be stopped in every case or further inspected before an allow or deny decision is made.
Firewalls can filter on whether an address is known to be benign or malicious, a variation of known and unknown filtering. However, instead of known addresses being trusted and unknowns not being trusted, this method twists the idea. A benign address is a known trusted address and a malicious address is a known, not trusted address. But in both cases here, the addresses are known. Any unknown address encountered using this form of filtering will require additional subsequent filtering that looks at other aspects of the traffic.
Firewalls can also filter on whether an address is real or spoofed. This form of filtering is not as clear and distinct as the previous types. Whether a segment, packet, or frame's address is the real correct address or a spoofed falsified address can be difficult to determine in every situation. When an address is a real address, in the sense that it's within the subnet ranges of a network, the methods for determining whether it's a spoofed address are few.
One method is to compare against a use table, such as that maintained by the DHCP, to see if the address is not currently assigned to any authorized system. Another method is to check the route, communication path, receipt vector, or receiving interface of the source address against what that aspect should be for a given address. For example, if a source address typically arrives on port 4 but it shows up on port 7, it's likely a spoofed source address.
Spoofed addresses can also be detected at border sentry points. When a source address comes from the opposite side of the firewall, then it's obviously a spoofed address. One clear example is when an internal LAN address appears as a source address in a packet on its way in to a network from outside. This form of spoof filtering can be part of ingress filtering.
Likewise, the same process can be used for packets leaving a network. Any packet whose source address is from the outside, such as an Internet address, but the packet is received by a firewall from an interface in the private LAN, must be from a spoofed address. This form of spoof filtering can be part of egress filtering.
These are most of the mechanisms that a firewall can use to filter or manage traffic based on addresses. The following sections examine the various types of firewalls and filtering methods.
Listing the types of firewalls is almost like listing taxonomy of the animal kingdom in biology. The variations, models, and versions are so numerous. In addition, opinions vary about what is and is not a firewall. Many experts begin the discussion of firewall types by dividing the collective into two simple, main groupings: personal and commercial.
A personal firewall is designed to provide protection to a single system or a small network, such as a SOHO network. To take full advantage of their features, most personal firewalls do not require special training or certification. Most personal firewalls offer user-friendly interfaces that may be Web-based or graphical user interfaced (GUI) in nature.
A commercial firewall is designed to provide protection for a medium-to-large business network. Most commercial firewalls are quite complex and often require special training and certification to take full advantage of their features. Most commercial firewalls use a Unix-like command line interface (CLI) that, while powerful and efficient, is not intuitive.
These two groupings do not, however, represent the complete collective of firewalls properly, as several firewalls could easily fall into either or both categories. Another common grouping method, therefore, is to classify firewalls as either hardware or software.
A hardware firewall is a dedicated hardware device specifically built and hardened to support the functions of the firewall software running on it. A hardware firewall is also known as an appliance firewall. A hardware firewall does not require any additional hardware or software for its use. All it needs is one or more network connections and a power source.
A software firewall is an application installed on a host. A software firewall is also known as a host firewall. A software firewall depends upon the host's hardware and operating system. If the host's components are not properly hardened, the software firewall will be less effective, especially if there are other communication pathways or attack points on the host. Software firewalls must compete for resources among all other processes active on the host. A software firewall is only able to protect a single host from malicious network activity. A software firewall is only able to filter traffic that reaches the network interface of its host.
With these two types of divisions, four potential combinations exist:
A personal software firewall is a product used on individual home systems, on SOHO systems, and even on client/server network work stations and servers. Generally a personal software firewall is free or less expensive than commercial software firewall products. A personal software firewall operates on its own to protect a single host.
A commercial software firewall is a product used on client/server network work stations and servers. While they can be installed onto personal or SOHO systems, they are usually expensive and are part of an overall security management or NAC system. Most commercial software firewalls can be used in an agent/console infrastructure where each host's firewall can be remotely administered from a master management console.
A personal hardware firewall is part of an integrated firewall product, such as a wireless access point or a cable/DSL modem. Another variation of the personal hardware firewall is the re-purposing of a client or server computer into a home-crafted open-source firewall. One example of this is SmoothWall, a hardened bootable Linux-based firewall. You can read a case study of deploying SmoothWall in Chapter 11.
A commercial hardware firewall is usually a device that handles the complexity of larger organizational networks. A commercial hardware firewall is often very expensive, running in the range of $10,000 or more.
The personal and commercial versions of software and hardware firewalls might include different add-ons or enhancements than their commercial equivalents. These add-ons or enhancements include antivirus, password management, registry protection, driver protection, VPN gateways, remote access support, IDS, IPS, spam filtering, and more. Usually these add-ons make the firewall products more attractive to the potential individual buyer. However, most commercial entities would generally avoid integrated firewall solutions in favor of dedicated products to handle their distinct security or management functions. An integrated device might offer easier administration, but it represents a single point of failure for multiple services. Additionally, such bundled solutions are more difficult to troubleshoot due to the complexity of the communications they support.
Another variation of firewall, in fact the original variation, is a screening router. Most appliance routers and many software routers, such as the RRAS (Routing and Remote Access Service) of Windows Server, are able to perform firewall filtering services in addition to routing. Those screening routers that perform firewall filtering might provide enough sentry security for your needs. However, if you want more advanced features, a screening router is unlikely to be the best solution for your network.
Ingress and egress filtering is a common tool for spoof filtering. A source address that comes from the opposite side of the firewall than where it is assigned is obviously a spoofed address. An example of this is when an internal LAN address appears as a source address in a packet on its way in to a network from outside. This form of spoof filtering can be part of ingress filtering.
Likewise, the same process can filter for packets leaving a network. If a packet with a source address from the outside such as an Internet address is received by a firewall from an interface inside the private LAN, this is also a spoofed address. This form of spoof filtering can be part of egress filtering.
Ingress and egress filtering can expand beyond spoofing protection and include a variety of investigations on inbound and outbound traffic. This can include black list and white list filtering, protocol and port blocking, and confirmation of authentication or authorization before communications continue.
Unfortunately, if a packet's spoofed addresses don't violate any of these concerns, the spoofed addresses might not be as easy to detect. For example, if a client spoofs an IP address to look like another client in the same subnet, the rules just described to catch spoofing would fail to notice this spoofed communication.
In addition to basic ingress and egress filtering, firewalls can support additional forms of packet examination and investigation.
Filtering is the primary function of a firewall. Through its filtering services, most of the other benefits and capabilities of firewalls apply. Firewalls can support many different forms of filtering. Additionally, the terms used for the type of filtering and the type of firewall are often used interchangeably. For example, a firewall that supports packet filtering is known as a packet filtering firewall.
The most common form of filtering is static packet filtering. Static packet filtering uses a static or fixed set of rules to filter network traffic. The rules can focus on source or destination IP address, source or destination port number, IP header protocol field value, ICMP types, fragmentation flags, and IP options. Static packet filtering is therefore mainly focused on the network layer (layer 3), but can also include transport layer (layer 4) elements. Static packet filtering focuses on header contents and does not examine the payload of packets or segments.
Static packet filtering is fast. Traffic matching a deny rule gets dropped, while traffic matching an allow rule gets to continue towards its destination. Static packet filters are invisible or transparent to hosts and users, unless their traffic is blocked, and then they will notice the actions of the firewall on their communications.
Static packet filtering requires the firewall administrator to define and tune the rule set. Most firewall rule sets, including static packet filtering rule sets, are a first-match ordered system. Static packet filtering can be problematic when the rule sets get too large. If the rules are in the wrong order or in a chaotic order, the rule set could create loopholes created or unintentionally discard authorized traffic.
The complexities of network communications, such as accepting query responses and port shifts, can be difficult to handle with static packet filtering. Static packet filtering may allow the subsequent packets of a fragmented message through, even though the lead packet was dropped. This can result in a DoS on the destination system, which would be waiting for the lead packet that never arrives.
Additionally, static packet filters perform their analysis on individual packets, regardless of the relationship or correlation between previous or future packets in a communication stream. This could allow complex multi-packet attacks to bypass the firewall if each individual packet is not recognized as malicious on its own.
Static packet filtering should still be used as a first line of defense, in spite of its shortcomings. By using static packet filtering as the first layer of defense, subsequent layers of filtering will have less bulk to address and thus can operate more efficiently.
Stateful inspection addresses the issue of complex malicious traffic. Stateful packet filtering determines whether or not a current packet is part of an existing session and allow/deny decisions are made based on this determination. A state is a session of communication. Often, state refers to the transport layer (layer 4) protocol TCP's virtual circuits established through the three-way handshake (using the SYN, SYN/ACK, and ACK flagged segments). However, stateful inspection systems can also track commutations in layers 5-7. A stateful inspection firewall will keep track of current sessions in a state table stored in memory.
As the firewall encounters each packet, it is analyzed to determine whether the packet is part of an existing state or not. If not, it's likely to be dropped unless it's a packet used to help initiate a new authorized session. Such a stateful investigation can be considered a dynamic packet filter as well. With static packet filtering, rules had to be created to allow the outbound requests and the inbound replies. With dynamic packet filtering, once a session is established the filtering watches for packets that don't belong to authorized sessions. Using stateful inspection as dynamic packet filtering allows for simpler rule sets. A rule allows an outbound connection and the firewall's state management automatically allows the return traffic.
Note
Stateful inspection is a form of dynamic packet filtering. Dynamic packet filtering is the process of automatically created temporary filters. In most cases, the filters allow inbound responses to previous outbound requests, but on a limited timeout basis. Both forms of state or session awareness, dynamic packet filtering and stateful inspection are usually interchangeable terms.
Unfortunately, stateful inspection can sometimes be fooled through manipulation of header contents that makes malicious traffic look like part of an existing valid session. More advanced stateful inspection filters keep track of not just the basic endpoints of a session, but additional details about the session, such as the sequencing and acknowledgement numbers. This reduces the risk, but does not fully eliminate it, as a hacker can eavesdrop on a session, learn the sequencing numbers, and predict future valid sequences.
Another issue with stateful inspection is that not all traffic uses states. Specifically, UDP and ICMP are connectionless protocols. So, state management won't apply to them. For these protocols, the firewall acts as if a state does exist for these protocols and keeps track of the source and destination from outbound packets. These are added to the state table with a timeout value. If the timeout occurs before a response is received, the state is removed from the table. A hacker can fool this mechanism in the same way as any stateful protocol like TCP.
Network address translation (NAT) is not exactly a form of filtering, but is often included in lists of the filtering services or options provided by firewalls. NAT translates internal addresses into external addresses. NAT can perform this service against IP addresses as well as port numbers. Any firewall that supports NAT can be a NAT firewall. In most cases, NAT is an additional translation service to the core filtering functions of a firewall. NAT is a common, if not standard, feature of modern firewalls.
An application proxy, application firewall, or application gateway is an application-specific version of a packet filter. However, unlike a static packet filter that is only able to inspect the header of a packet or segment, an application proxy is able to inspect traffic fully at any layer, including the application payload.
An application proxy, even if given the name firewall or gateway, acts as the go-between or middleman between a client and a server. All communications for the specific application are proxied. This grants the application firewall the ability to inspect application specific elements of the traffic. Application proxies are application-specific, so specific products for e-mail, Web, file transfer, database access, VoIP, and other TCP/IP sub-protocols are available.
When an application proxy is deployed, it usually requires that all client software be re-configured to point communications to the proxy server rather than the actual intended resource server. The application proxy will also re-build the request packet before sending it to the resource server. This can include NAT services, but in most cases, it's just a process of proxying the communication. The application proxy maintains two connections, one between itself and the requesting client and a second between itself and the resource server. Thus, application proxies are not transparent filters because a client is aware the proxy is in use. The client never establishes a direct connection between itself and the resource server when a proxy is involved.
Additionally, all other firewalls monitoring a network border must deny access for the application protocols to be managed by the application proxy. This prevents a user from attempting to bypass the application proxy.
Application firewalls can filter on the content of the application payload. This can include IP addresses, domain names, URLs, sub-protocols, attachments, keywords, and more. An application proxy can inspect every aspect of an application's communications. This is known as deep packet inspection.
Application proxies can also perform caching services to improve performance and reduce connection throughput consumption. See the Chapter 1 section, "Proxy" for a discussion of proxy services.
The primary limitation of application proxy firewalls is each unique application will need its own dedicated application proxy. Generic proxy systems are usually ineffective.
A circuit proxy or circuit firewall focuses its filtering on the initial setup process of a session, state, or circuit. This form of filtering can focus on layers 3-5. It functions similarly to an application proxy, as it acts as a middleman between a client and server. A circuit proxy prevents a direct connection from existing between a client and server to protect the network.
A circuit proxy makes an allow or deny decision on the initiation of the session, state, or circuit. Once a circuit is created, no further filtering takes place. If a client is allowed to initiate communications with a resource server, then the content of their communication is unfiltered and unmonitored (at least not by the circuit proxy).
The filtering rules of circuit proxies are similar to those of static packet filtering, in that a list of rules of IP addresses, port numbers, domain names, networks, or even resource providers determines what circuits or connections are allowed and which are not. The filter set can be a deny all but allow exceptions stance, or an allow all but deny exceptions stance.
Firewalls can also filter based on content. The firewall can intercept specific content in a packet leaving the network before it reaches the outside. This could result in the packet being discarded, an entire connection being dropped, or the packet being edited to remove the blocked content and replace it with something else. Content filtering can focus on domain name, URL, filename, file extension, or some other form of keyword.
Content filtering is often a feature of application proxy firewalls, stateful inspection firewalls, and dynamic packet filtering firewalls.
A software firewall is an application installed on a host. A hardware firewall is a dedicated hardware device specifically built and hardened to support the functions of the firewall software running on it.
A software firewall is also known as a host firewall. A hardware firewall is also known as an appliance firewall.
A software firewall depends upon the host's hardware and operating system. If the host's components are not properly hardened, the software firewall will be less effective if other communication pathways or attack points on the host exist. A hardware firewall does not require any additional hardware or software for its deployment. All it needs is one or more network connections and a power source.
Software firewalls must compete for resources among all other processes active on the host. A hardware firewall has dedicated hardware resources not shared with any other service.
A software firewall is only able to protect a single host from malicious network activity. A hardware firewall can protect a single system or an entire network
A software firewall is only able to filter traffic that reaches the network interface of its host. A hardware firewall can also only filter traffic that reaches the network interfaces of its appliance. However, a hardware firewall can be positioned on a network at a choke point or gateway to analyze and filter all traffic.
A software firewall and a hardware firewall are both a form of software, but the hardware firewall has a dedicated appliance as its host, while the software firewall uses a standard client or server as its host. In either case, software flaws or bugs in programming can cause the firewall to fail.
A software firewall and a hardware firewall can both be targets of attack. Exploits can compromise their software component or physical attacks can harm their host/appliance.
A software firewall is often less expensive than a hardware firewall. A hardware firewall typically offers a wider range of features and capabilities than a software firewall.
Both software firewalls and hardware firewalls are options you can use throughout a network infrastructure.
No real distinction between a firewall designed for IPv4 versus one for IPv6 exists. Many firewalls can already support both versions of IP. If you are planning on migrating to IPv6 or have already started the conversion process, be sure your firewalls support IPv6.
A small issue affects filtering between IPv6 and IPv4 subnets. You learned in Chapter 1 that a protocol translation tool can support interaction between network using different versions of IP. This translation tool is called Network Address Translation-Protocol Translation (NAT-PT) (and was defined in RFC 2766 by the IETF. Be sure your selected firewall supports NAT-PT if you plan on communicating across an IP version barrier.
If you would like to read more on this translation issue or gain further understanding about IPv6, please visit:
The ARIN IPv6 Wiki at
http://www.getipv6.infoIPv6.com at
http://www.ipv6.com
Firewalls, specifically hardware appliance firewalls, typically have two or more network interfaces. A firewall with two interfaces is known as a dual-homed firewall, while a firewall with three interfaces is known as a triple-homed firewall or a three-legged firewall.
The benefits of multiple interfaces are that the segments, subnets, or networks connected to each firewall interface are electronically isolated from each other. This prevents unfiltered traffic from leaping from one segment to another in an attempt to bypass firewall filtering.
However, for software firewalls using multiple interfaces, you need to ensure that the TCP/IP protocol feature called IP Forwarding is disabled. IP Forwarding is actually a router rule that allows traffic from one interface to exit another interface without needing to move any further up the protocol static than where IP resides. In many cases, IP Forwarding allows packets to bypass filtering. If the system is to be a firewall, you should disable this feature.
Note
If a system is to function as a router rather than a firewall, IP forwarding might be a desirable function.
Software host firewalls are most often single-homed firewalls since the host only has a single NIC. This is acceptable, since the software host firewall is not providing sentry services between network segments, but between the host and the network.
While firewalls with four or more interfaces are possible, they are rarely deployed. Such a configuration requires significantly more complex filtering and routing rules to operate effectively. It's also a significant single point of failure and a bottleneck to traffic flow between multiple network segments.
The placement of your network's firewalls depends on several key but subjective factors. No single correct answer or deployment strategy is perfect for everyone. However, several good general guidelines can be of help in planning firewall placement.
First, understand the structure of your network. Where are natural or organizational divisions on the network? Do they correspond to distinct subnets or geographic/physical locations? In many situations, placing a firewall between each division or physical location (even different floors of a building) can be beneficial. Do you have a DMZ or extranet? You will need to isolate these from the private LAN and from the Internet.
Second, know the traffic patterns of your network. What are the common vectors and pathways of communication, both between internal systems and between internal and external systems? Consider positioning firewalls so that they can filter all traffic. This may involve the creation of choke points.
Third, is Internet connectivity essential to business tasks? You should firewall-protect all Internet access points or gateways. In fact, any external gateway or portal should have a firewall.
Fourth, is any form of remote access in use, including wireless? You should position a firewall between each RAS or NAS and the private LAN. Assume all remote and wireless connections are potentially malicious.
Fifth, based on previous compromises, what are the most likely access pathways an internal or external hacker might use to breach your network? Place firewalls along these pathways.
Sixth, does any other unique aspect or feature of your IT infrastructure warrant consideration for firewall protection?
Placing a firewall everywhere mentioned in these guidelines may not be practical, cost effective, or secure. So before any deployment, conduct a risk assessment to determine whether a firewall is the best choice of countermeasure. Review the previous section, "Why Do You Need a Firewall?" for more information on conducting risk assessments.
An essential element of network security, a firewall is a filtering service used to protect your network and hosts from a variety of threats, both internal and external. Several types of firewalls are available, including screening routers, hardware appliances, and host software products. Each of these firewalls can employ one or more features for ingress and egress filtering. The common filtering features include static packet filtering, stateful inspection or dynamic packet filtering, NAT, application proxy, and circuit proxy.
802.1x
Agents
Annualized loss expectancy (ALE)
Annualized rate of occurrence (ARO)
Appliance firewall
Application layer (Layer 7)
Application proxy/firewall/gateway
Asset value (AV)
Bastion host
Border sentry
Botnets
'Bots
Circuit
Circuit proxy/firewall
Closed source
Commercial firewall
Content filtering
Cost/benefit
Data link layer (Layer 2)
Dead-man switch
De-encapsulation
Dual-homed firewall
Dynamic packet filtering
Exposure factor (EF)
Fail-safe/fail-secure
Filtering
Firewall
Frame
Gateway
Hardware address
Hardware firewall
Header
Host firewall
Intangible cost/value
Internet Control Message Protocol (ICMP)
IP address
Logical address
MAC address
Network layer (Layer 3)
Open source
Open system interconnection reference model (OSI model)
Packet
Payload
Personal firewall
Physical address
Physical layer (Layer 1)
Port forwarding
Port number
Public Key Infrastructure (PKI)
Presentation layer (Layer 6)
Reverse proxy
Risk assessment
Risk management
Rule set
Rules
Sacrificial host
Screening router
Secure Sockets Layer (SSL)
Segment
Session
Session layer (Layer 5)
Single loss expectancy (SLE)
Socket
Software firewall
Spoofing
State
Stateful inspection
Static NAT
Static packet filtering
Tangible cost/value
Transmission Control Protocol (TCP)
Transport layer (Layer 4)
Transport Layer Security (TLS)
Transport mode encryption
Triple-homed firewall
Tunnel mode encryption
User Datagram Protocol (UDP)
Zombies
Zone of risk
Zone of trust
What is another term for the individual rules in a firewall rule set?
States
Exceptions
Policies
Referrals
Sentries
Which of the following is not associated with a firewall?
Fail-secure
Sentry device
Fail-open
Choke point
Filtering service
A firewall is designed to allow what type of traffic to traverse its interfaces?
Authorized
Non-benign
Unknown
Abnormal
Malicious
What is the first step in deploying a firewall?
Determining the filtering process
Defining rules
Selecting a security stance
Purchasing a license
Writing a security policy
Which of the following is the best description of a firewall?
An authentication service
A remote access server
Resource host
A sentry device
Malicious code scanner
A border firewall cannot protect against which of the following?
Flooding attacks
Insider attacking another internal target
Protocol abuses
Unauthorized inbound service requests
Port scans
All of the following are mistakes in firewall security except:
Managing security poorly
Deploying too many firewalls
Using firewalls to provide filtering for networks and hosts
Not writing a security policy
Failing to keep current with updates and patches
What is the primary reason a firewall is an essential security product?
Low cost of deployment
Threats exist
High ROI
Native protocol encryption
Interoperability
What technique determines if a firewall is the best countermeasure choice for a particular threat against a specific asset?
Conducting a risk assessment
Reading blogs
Buying the least expensive option
Only using open-source products
Using products from a single vendor
Which of the following is not a common zone of risk?
An extranet
A DMZ
A private LAN
The Internet
Department subnets
Which of the following statements are true?
A firewall can be deployed as a bastion host.
Firewalls protect resources.
Firewalls are often the first line of defense for a network.
Firewalls are part of an overall security strategy.
All of the above
When a one-way or sieve firewall protecting your network allows external initiations of communications to occur over a specific socket, this is known as:
Static NAT
Traffic forwarding
Port forwarding
Reverse proxy
All of the above
What is ingress filtering?
Restricting traffic to a specific subnet
Preventing traffic from leaving a network
Limiting host activities to that host
Monitoring traffic on its way inbound
Blocking access to external resource sockets
Content filtering can focus on the following aspects of traffic except:
Source or destination IP address
Keywords in the payload
URLs
File extensions
Domain names
Which of the following will prevent firewall filtering from blocking malicious content?
Speed of the network
User permissions
Not being positioned at a choke point
Encrypted traffic
Cable type
Which of the following is not a valid method for determining whether a source address is spoofed?
Compare against a use table
Verify the route of reception
Check the DHCP logs
Check against RFC 1918
Perform ingress filtering
What form of filtering focuses on source or destination IP address and requires separate rules for inbound and outbound communications?
Stateful inspection
Static packet filtering
Application proxy
Circuit proxy
Dynamic packet filtering
Dynamic packet filtering is also known as:
Static packet filtering
Application proxy
Stateful inspection
Circuit proxy
Deep packet inspection
What method of filtering automatically keeps track of sessions on a limited timeout basis to allow responses to queries to reach internal clients?
Deep packet inspection
Static packet filtering
Application proxy
Dynamic packet filtering
Circuit proxy
What form of filtering allows communications regardless of content once the session is established?
Dynamic packet filtering
Circuit proxy
Stateful inspection
Application proxy
Deep packet inspection
What type of firewall requires the presence of a host operating system?
Appliance firewall
Personal firewall
Software firewall
Commercial firewall
Screening router
Based on the seven domains of a typical IT infrastructure, all of the following locations (see Figure 2-8) are appropriate locations for firewall deployment except:
Between users and workstations
Between work stations and LAN
Between LAN and WAN
Between remote access and LAN
Between remote access and application servers
What activity performed by a triple-homed firewall cannot be performed by a dual-homed firewall?
Filter content
Physically isolate subnets
Support NAT proxy services
Be deployed as an appliance
Route traffic from the Internet to either an intranet or DMZ