CHAPTER 9: APRIL: LINKING INFOSEC WITH INFOGOV
A linguistic journey to information governance
As we’ve established, the information security industry loves its acronyms and abbreviations, so in this instance we have InfoSec for information security, and for information governance we have InfoGov.
As an ISM you need to be thinking more broadly, as this is the trajectory at the moment. Information security begets information assurance begets information governance. If we are truly protecting information assets, holistically, this is where we will end up. So, be prepared to think more widely than your current scope of understanding, and do a lot of reading and extra learning.
In the same way as we have seen other acronyms in our space, including GRC (governance, risk and compliance), we need to really start living and breathing the meaning of the words. Governance is supposed to mean visibility of governance across the whole organisation. Risk, in this instance, is again supposed to mean risk management across the organisation, not just specifically IT risk. Business risk, financial risk, reputational risk, information risk – they all need to be dealt with holistically. Finally, the compliance leg of this triangle requires an appreciation of the whole legislative, regulatory and standards requirements for your organisation, not just compliance with a firewall policy. It is far beyond this. It is compliance with everything that we have been talking about in this book, all the policies, procedures, standards and guidelines combined. This is because they should have been crafted with an understanding of the compliance landscape and, therefore, you can evidence that you are complying with everything that is required of you.
The international standard ISO/IEC 38500:2008 described the corporate governance of IT as being ‘the system by which the current and future use of IT is directed and controlled’. Corporate governance of IT involves evaluating and directing the use of IT to support the organisation, and monitoring this use to achieve plans. It includes the strategy and policies for using IT within an organisation. However, what we are talking in this chapter are the links from information security to information governance. This takes IT governance to the next level, beyond just the technology, in keeping with all the movements over the last few years across ‘big data/raw data’, the information spring if you will. What is required is a holistic view. So let’s take a journey through the various stages from IT security through to information governance, in the next section.
How did we get here?
Research can show that the journey to IA, which precedes information governance, is via the following themes that have emerged over time:
- physical security
- operational security (OpSec)
- computer security (CompuSec)
- communications security (ComSec)
- IT security (ITSec)
- information systems security (InfoSec), which merged ComSec and CompuSec following rapid changes in technology and, thus, combined in a new paradigm to become InfoSec, internationally recognised in the Common Criteria for Information Technology Security Evaluation Protection Profiles (see www.commoncriteriaportal.org/)
- system safety
- system reliability.
System safety is not something that we have found ourselves focusing on to any great extent in the information security industry, although there are a number of publications that put it squarely inside our boundaries. In many ways, this is a better lens through which to view things, as it provides a broader perspective and adds weight and sense to the need to provide the levels of protection that we may often be seeking, based on risk assessment, that have a deeper meaning.
The classic triad of ‘CIA’ was originally a ComSec definition covering:
- Confidentiality of information: ensuring it is accessible only to those authorised to have access and ensuring data is kept private whether manual or electronic.
- Integrity of information: safeguarding the accuracy (inputs and outputs) and completeness of information through the application of controls and management checks.
- Availability of information: ensuring that only authorised users have access to information when required during its life cycle; making sure information stays in the right hands, in the right place, at the right time.
In 1991, John McCumber presented a pedagogic framework at the National Computer Security Conference on this subject and highlighted the constituent parts of InfoSec, including the need for a ‘common language/terminology in order to communicate effectively’. The model embraced the need to embed the people, process and technology triad as an overlay on the three main goals of security (achieving the CIA of the information you are seeking to protect). McCumber articulated these in the manner of ‘Education, Training and Awareness (people); Policy and Practices (process) and Technology’. (McCumber, 1991 and 2004) The original model, presented by McCumber, for InfoSec, is shown in Figure 6.
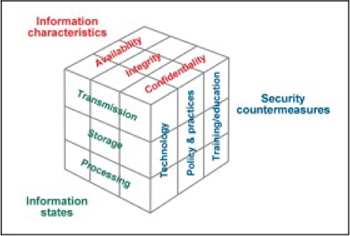
Figure 6: Model of three main security goals (source: McCumber, 1991)
So, InfoSec was very much about the integration of personnel security, computer security, communications security and operational security into an identifiable profession. InfoSec ‘in any language, in any culture, in any country’ is relative to the protection of those information systems. (Kovacich, 1998)
A decade after McCumber’s InfoSec model was described, there was an update, in 2001, that became a seminal paper in terms of articulating the definition and direction of (IA) for the coming years. Maconachy, working at the US National Security Agency at the time, saw IA as embracing the triad of information security, but needing to be articulated in terms of four dimensions (Maconachy et al, 2001):
- Information states – can be aligned with protective marking classifications and types in the UK.
- Security services – these are the five pillars.
- Security countermeasures – we refer to these as controls or safeguards in the UK, embracing people, process and technology aspects.
- Time – this aligns with the security development life cycle as our information is in constant flux dependent upon time.
Information assurance should be viewed as ‘both multidisciplinary and multidimensional’. The dimensions are represented as information states, security countermeasures and security services – and these are all understood to be affected by time. Information can have a greater sensitivity, depending on when it is produced or released. Information assurance is both art and science, so it needs to be tackled through multidisciplinary efforts (Petersen et al, 2004).
The information states can also be overlaid with the approach of creating information profiles that correspond to levels of protection required for information (UK CESG, Protection Profiles), which correspond with the likely countermeasures to be implemented in the solution space:
In 2002, Debra Herrmann proposed a broader definition of IA as an engineering discipline that cuts across the safety domain, and some 10 years on we are finally seeing some real traction in this safety space.
Herrmann contended that a ‘safe, reliable and secure system by definition has proactively built-in error/fault/failure (whether accidental or intentional) prevention, detection, containment, and recovery mechanisms’ (Herrmann, 2002, p.9). Herrmann saw IA as a three-dimensional challenge, encompassing ‘safety, reliability and security’. This book should be mandatory reading for all IA professionals across the UK!
The most fulsome and concise definition of IA can be found in a US Air Force instruction bulletin (US Department of the Air Force, 2001) which describes IA in terms of information operations (military language) and includes reference to the need to also be able to restore systems and how to do so, which means you need to be able to protect, detect and react to situations:
Information operations that protect and defend information and information systems by ensuring their availability, integrity, authentication, confidentiality, and non-repudiation. This includes providing for restoration of information systems by incorporating protection, detection, and reaction capabilities. (US Department of the Air Force, 2001)
Most other US Department of Defense publications also refer to the same definition (NIST, CNSS, CNSSI, etc.).
Key to understanding IA is separating it out in terms of appreciating to what the ‘information’ is referring. For example, the function and responsibility of an organisation’s security personnel are to protect corporate assets. Information systems and the information that they store, process and transmit are some of the most valuable assets. Information assurance includes those actions that protect and defend information and information systems.
Information assurance should be seen as both a business enabler and a business protector, ensuring that users of information systems are not unwittingly exposing themselves to unacceptable risk. This has equally been expressed as IA representing a migration from a preventative approach to an enabling approach (McFadzean, 2005).
A combination of this thinking was then brought from the US to the UK by the independent partnership organisation – the Information Assurance Advisory Council (IAAC) – who described IA as follows:
Information Assurance is the certainty that the information within an organisation is reliable, secure and private. IA encompasses both the accuracy of the information and its protection, and includes disciplines such as information security management, risk management and business continuity management. (IAAC, 2003)
Information is fundamental to the business of government. Effective IA is at the core of ensuring that this asset is safeguarded appropriately. The continued growth throughout government of the use of ICT systems, all linked together, carries with it increased vulnerability. In addition, these ICT systems are under threat of attack from foreign intelligence services, criminal gangs, and even individuals inside the organisation.
Information security in itself requires controls to be implemented, the best of which are preventive (in the most obvious sense of preventing any breach of security from taking place in the first instance). These are, for example, firewalls, user access control mechanisms, encryption of data and communications, digital signatures and data backup systems, and detective controls, such as IDSs or security monitoring platforms, which form the basic components of security architecture. The various technical controls are usually complemented by a framework of security policies, procedures and guidelines aimed at controlling the actions of the users to whom the framework applies.
This was at a time when the discourse of the period was beginning to change, as departmental IT went through the push and pull of decentralisation and the struggle to manage information assets really began, as Wylder pointed out (Wylder, 2004, p.21).
Wylder’s writing is some of the most comprehensive at the time, with regard to the breadth and depth of information security and what a professional should be doing in terms of their role.
There are a number of basic steps that are found sequentially in most information security standards (ISO27001, ISACA BMIS, etc.), which build towards the identification and implementation of an ISMS (Dimitriadis, 2011). These are:
- Business impact analysis – looking at the impact on the business, following the realisation of a threat, usually in terms of the monetary, reputation or legal impact.
- Risk analysis – the possibility of the occurrence of a security incident is calculated, based on a database of security weaknesses. This step needs to take into account technical controls that are already in place to reduce risk and any other complementary controls already available.
- Risk management – once identified, the risks are prioritised in relation to the impact level and business appetite for risk.
- ISMS implementation – this is a robust management framework implementation, including consideration of human, cultural, technical, business and external factors, and requires metrics, measurement and continuous improvements.
Unfortunately, what we have ended up experiencing in implementation terms is a lack of consistency, as each sector, industry and organisation has appeared to implement security on the basis of their specific business needs and created different security definitions to suit themselves.
As mentioned earlier, IA must be maintained throughout the life cycle of a system, as threats change with the changing political or business environment, vulnerabilities appear and disappear as the configuration of the system changes and new weaknesses are discovered, and the impact of systems failure changes as dependency on a system develops. This is where CESG (the UK Government’s Communications-Electronics Security Group, known formally as CESG) come in with the various accreditation schemes, etc. (UK CESG, Certification).
Often security is thought of as an event rather than a process, as a stitch in time rather than a thread that runs throughout each phase of a system’s life cycle. Security is often not considered during the initial planning, design and development of the system. Attempts to retrofit security into the system after it is developed are typically more expensive and less effective than if it is incorporated from inception. Likewise, security does not end once the system has been accredited and approved to operate under certain conditions. Throughout the system’s operational and maintenance phase, the system’s compliance with the terms of its accreditation must be verified. Even when the system’s life cycle is over, security policies and procedures must govern the secure destruction and disposal of the system. (Boyce and Jennings, 2002, p.170)
It can be shown that in the UK, IA broadens out to include data protection and privacy (because of the close confidentiality links and the Organisation for Economic Cooperation and Development (OECD) guidance requirements), information management and quality, records management, and much more. However, the assurance function cannot be deployed until the risks are fully understood (Schou and Shoemaker, 2007, p.13). The OECD guidance clearly states that the ‘use of an information system and its security should respect the legitimate rights and interests of others and should be compatible with the legitimate use and flow of data and information in a democratic society’. That requirement has not diminished, rather increasing in importance in the past two decades.
In the late 1990s, the term IA was known only by small groups of security experts, often considered to be ‘paranoid’ or ‘rigid’. Today, IA is well known by a much wider audience involved with public sector projects and contracts, ranging from high-level executives to engineers in many disciplines. Many have sought information on IA processes through reading papers and attending briefings. Yet, unfortunately, in the late 2000s, it appeared that the status quo was very similar, with only a small number of professionals truly understanding the breadth of meaning and the scale of available material upon which to draw experience, understanding and wisdom (Hutton, 2008).
Today, you can choose from ‘information security’, ‘information risk’, ‘information risk management’, ‘information protection’ or ‘information assurance’ and also the US-centric, all-embracing umbrella of ‘governance, risk and compliance (GRC)’ (Tone at the Top, 2010). GRC, itself, is prone to as many as 22 different definitions (Marks, 2011), although the most favoured is that provided by the Open Compliance and Ethics Group (OCEG, 2011). Fundamentally, GRC is not about technology, but about business processes and doing them better. It is a lens through which an organisation can understand their business and appreciate why these elements need to work together in harmony (risk management and strategy), addressing fragmented processes, removing silos and working pan-organisationally. The international standard, ISO31000, for risk management provides a definition and is of value in this context (British Standards Institution, 2009).
The goal is to transform information security into a multidisciplinary field in which technologists work closely with experts in ‘soft issues’, such as public policy, economics and sociology (Shostack and Stewart, 2008, p.103). ISACA picked up this concept well in their Business Model for Information Security (see Figure 7), seeking to provide an ‘in-depth explanation to a holistic business model which examines security issues from a systems perspective’ (ISACA, 2009).
Even if you do not like the term (information assurance), it has a long history, which clearly not enough people are aware of, so this section seeks to pull the pieces together. It can be seen from most of what is widely available in published form that IA is often used as a synonym for security (Boyce and Jennings, 2002). Whilst it may be that ‘attempts to create strictly defined vocabulary within information security are likely doomed to failure as long as English remains a living language’ (Shostack and Stewart, 2008), it is important to appreciate that practical issues flow from definitions. Security may historically have been an IT issue, but assurance raises the bar to a much more organisational issue which, given the importance of valuing information as an asset and the need to protect both reputation and personal privacy, clearly shows the breadth of the requirement.
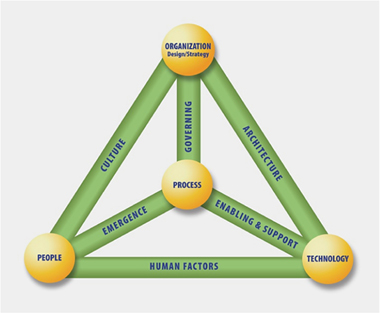
Figure 7: ISACA BMIS – business model for information security
The Business Model for Information Security, © 2010, ISACA. ® All rights reserved. Used by permission.
From IA to IG
Putting IA and InfoSec together, you actually get ‘information governance’ (IG or InfoGov). InfoGov is the set of multidisciplinary structures, policies, procedures, processes and controls implemented to manage information on all media in such a way that they support an organisation’s immediate and future regulatory, legal, risk, environmental and operational requirements. This includes information held in every form (information systems, on paper, other records). It is underpinned by a management process that takes a co-ordinated approach to information assets across an organisation. It embraces information management, including information security management, information and records management, data protection, privacy (because of close confidentiality links and the OECD guidance requirements) and physical protection. It includes aspects of corporate governance, risk management and business continuity, and must be maintained throughout an organisation’s life cycle in the face of changing threats, vulnerabilities and dependencies.
Central to IG is an understanding of the journey from IT security, through information security, to IA – all of which are about maturing to a position of being able to demonstrate justified confidence in security measures, processes and practices in the management of information. Whilst IA has been seen to be the growth area in recent years, maturing out of information security, the ultimate goal must be to embed a full IG framework across all organisations in order to fully embrace the total breadth of information-related legislation, regulation, standards, policies, procedures, technology and people issues that need to be managed, handled and protected in today’s cyber-dominated environment.
Consider, if you will, the 11 Cs of IG.
Eleven Cs of IG:
1 centralisation
2 communication
3 (legislative) compliance
4 confidence
5 confidentiality (integrity, availability)
6 conformance
7 consistency
8 content
9 continuity
10 (security) controls
11 corporate records management.
(And now for something completely different …! For those of a spiritual nature, apparently the number 11 possesses the qualities of intuition, patience, honesty, sensitivity, and spirituality, and is idealistic. Others turn to people who are ‘11’ for teaching and inspiration, and are usually uplifted by the experience. Not for nothing, nor randomly, are these things chosen!)
Your aim as an ISM should be to seek to gain a deeper understanding of IG and the principles for good information management and handling, enabling technologies and current best practices and, at the same time, gain a broad appreciation of the many facets of the information at the heart of all that you will encounter.
At a minimum, over time, you could consider your syllabus of knowledge as needing to be a broad understanding across all of these areas:
- principles of IA and beyond
- standards and best-practice management of information
- security (BP)
- software assurance (SA)
- data protection and privacy (DP)
- records management (RM)
- business continuity/disaster recovery/resilience (BC).
Table 6: Areas of knowledge required
Other security tasks for this month
Addressing user requirements
We had a need to revoke CD auto-enable on our PC build in order to achieve a government-dictated security requirement. However, sometime later, a request was received by ICT to switch the auto-run feature back on as the users were finding it too challenging (I’m being polite) to perform the sequence required of ‘Windows®, Computer, double-click on the external USB drive’! Given that this would mean having to raise an exception to a policy, careful communication and explanation was required in order to ensure that the status quo could be maintained without causing too much angst for the users.
Addressing old equipment requirements
We’ve seen over the months that there are various requirements for assisting in what might be considered to be tasks related to facilities management. The reason for your apparent ‘meddling’ is to ensure that you are actually providing the right level of care and attention to the end-of-life stage of equipment, given that your whole life cycle demands this kind of approach. So, when a user comes forward with a large box of old disks, what do we do with them? The users says they are fine to be disposed of, but how do we know what is on them, so that we can justify the decision to destroy them? It would be a laborious task to review all the disks. Every day is filled with this kind of conundrum to be solved. Perhaps a random sampling of the contents could be done – if the disks are still machine readable – and then a level of judgement applied as to whether or not the information in its entirety is actually past its retention period. Engage with the RM team, whenever possible, so that they can make the appropriate amendments to the RM systems that should be recording such information. As long as you have some evidence for the actions taken and justification for the approach, it will be easy enough to explain yourself, should anyone question this further down the line.
Ongoing anti-virus management
When your organisation experiences a serious virus (malware) outbreak, it can be a pretty defining moment for the ISM. The team was still trying to contain the Conficker attack, which had spread still further as a result of the lack of previous management of the servers (as highlighted in the penetration test results report). The extent of the damage was eventually realised when a brute-force attack was identified on a server. This was immediately isolated from the network, but it needed to be patched and this brought forward some real thorny issues of:
- why servers were not being patched;
- which ones were in or out of a management loop;
- how long it takes to make decisions about patching and updating these servers, and the reality of what a nonsense that is when you see how easily and quickly you can get exposed, and how it is likely to play out in the public perception if the media get hold of the news.
Security metrics
Statistics, metrics and measurements – call them what you will – but you really need to get your head around them in order to be able to provide management with something tangible, be it a list or a picture with a pie chart or graph. People need to see things either improving or not – with answers or explanations for the latter and options for returning to a state of improvement. As the ISO set about the numbering scheme for information security management, 27000, it allowed for a lot of supporting standards, and so we now have ‘ISO/IEC 27004:2009 Information Technology – Security Techniques – Information Security Management – Measurement’.
There are also several existing maturity models that can be adapted to suit your needs. In the UK public sector, there is a more than adequate IA maturity model, which is supported by an IA assessment framework to help assess your progress towards achieving the required level of maturity. (Available at www.cesg.gov.uk/Pages/Search.aspx?k=Information%20Assurance%20Maturity%20Model.)
Most maturity models adopt the phased approach of grading, from no implementation to embedded. In this case (IAMM), the gradings are as follows:
- Level 1 – initial
- Level 2 – established
- Level 3 – business enabling
- Level 4 – quantitatively managed
- Level 5 – optimised.
Adopting an accepted framework relevant to your industry helps to benchmark your starting point and provides a trajectory of expected progress. This is something well worth considering from as early on as is possible in your role. You then have a level of tangibility in your management reporting and can provide graphical or pictorial representation of the current status of information security in your organisation. Think of it as seeking to provide a ‘confidence count’ – how confident you are in the data that is being collected, the way in which it is currently being represented and the way in which it could be represented to better tell the story of information security implementation and its onward journey.
Managing a more security-aware user population
The most applicable phrase here has to be ‘be careful what you wish for’. The more you heighten awareness, the more you are likely to garner responses and input from your user base. When you run regular information security awareness briefings, people feel more able to talk about issues of concern regarding information security and data protection.
And now for a completely random user share!
A concerned employee, after experiencing my open style of delivering an information security awareness briefing session, i.e. having her eyes opened, took me aside with a query. Following the sad and tragic loss of a baby, should the university have contacted her, researching how this made her feel, without reference to any data protection/privacy statement to advise about potential sharing. All it did was bring the incident back to the fore for the poor individual and upset them all over again. Greater care and caution is required, as the legal phrase in question is ‘damage and distress’. This becomes a great example of it, when an individual is stood before you, querying whether this should ever have happened to them. But in terms of the bigger picture, they certainly learnt more about the legislative wrap-around that does exist and so they know that they have a recourse in the future.
People also started to notice the little things when it came to system development, like passwords being displayed in a field on the screen in clear text, and they took the time and trouble to report these kinds of findings to the ISM, who then would have to come up with a solution and provide some feedback. The information security standards are developed on the basis of an understanding of the ‘plan, do, check, act’ loop – where you plan to do something, do it, check if it’s working and act if it isn’t. So the user feedback is vital, so that you can act if things are not working as expected.
The ‘cut and paste’ facility was worrying a lot of users, as they realised that this could be a huge risk, given the nature of the information that could easily be copied out of corporate systems. This needed to be monitored in terms of the number of applications that allowed it and the likely level of information contained in those systems. This might be leaking out as a result of users trying to be helpful, cutting and pasting information from a corporate, secure, sensitive system into an e-mail, to exchange with colleagues in other third-party locations in order to fast-track solutions.
Following delivery of another information security awareness briefing in an outlying office location, a laptop ‘appeared’ from under a desk. It clearly hadn’t been used in weeks, so was locked out of the hard-disk encryption tool. As an ISM, you need to decide whether or not you are going to start to report every one of these kinds of breach as an ‘incident’ in the appropriate system, as it can be very useful for both planning and management visibility – particularly in explaining what it is you have been getting up to!
Security awareness theme
This month’s information security theme should usually be focusing on Easter, as it occurs at this time. You could run a campaign whereby you leave chocolates (mini eggs, for example, to keep in theme!) on the desks of those users who are adhering to your clear-desk policy.
Chapter summary
This chapter has very much focused on a journey through the history of the various terms that populate the industry, to help the ISM understand their role in all things information. Whilst it may feel like the end result is greater confusion, the chapter can be used for reference on an ongoing basis, depending on the needs that arise as your role grows and embeds in your organisation.
Much like any other profession, there will be many who will disagree with the way these definitions have been represented, but the author would challenge their research and depth of reading!
