Firewalls and NNM Port Usage
There may be situations where the NNM system and the network it is managing are separated by a firewall.This section reviews NNM requirements for various network services in a general way.
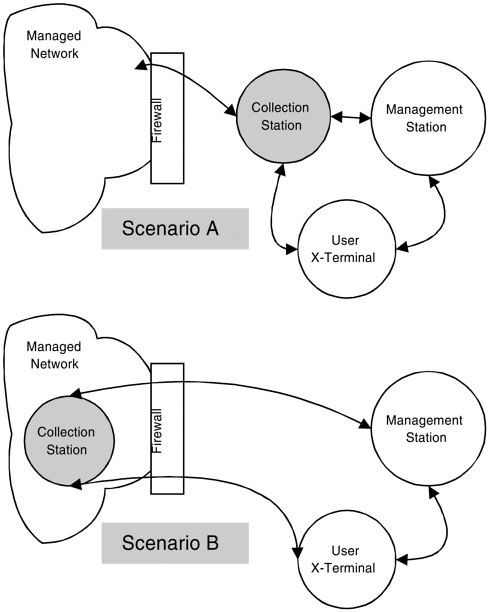
There are two main scenarios to consider while reading the rest of this section. In scenario A the managed network and the NNM collection stations are separated by a firewall. NNM must be able to probe through the firewall to reach its management domain. The NNM users have direct access to their NNM system. Scenario B situates the NNM collection station inside its management domain. The users are located on the other side of the firewall and so is the management station. Now both the users and the management station must pass through the firewall to reach the collection station. See Figure 10-2.
Figure 10-2. Relationship between NNM and the firewall.
Scenario A requires the collection station to manage its network through a firewall. This relaxes the security requirements of the collection station and simplifies the pinholes the firewall must endure. Scenario B places the collection station inside the firewalled network it is managing, posing additional security requirements upon it. X-Windows traffic from the users, plus management station traffic, must be allowed to pass through the firewall, making this a more complex situation.
To communicate across a firewall you need a complete understanding of the protocols NNM uses. The details are given in the following paragraphs and the data is summarized in Table 10-1.
The netmon daemon sends ICMP echo and parameter requests. In general, SNMP get requests on UDP port 161, and the associated replies are necessary for normal operations, including topology updates between a collection station and its management station. SNMP traps may be received on UDP port 162. If there is a collection station on the other side of the firewall, then there will be pmd to pmd traffic on TCP port 162. HTTP server discovery uses requests on port 80 and 280.
To gain access to the NNM system across a firewall, the telnet protocol on TCP port 23 must be passed. To run ovw across the firewall, X-Windows traffic on TCP port 6000 must be passed. Alternatively, the web-based NNM console could be used for access. It uses port TCP port 8880.
If there is a name server that must be accessed across the firewall, then UDP port 53 must also pass through.
Should the convenience of FTP be important, then TCP ports 20 and 21 must also pass the firewall.
| Service | Protocol | Source Port | Source | Destination Port | Destination |
|---|---|---|---|---|---|
| SNMP | UDP | 1024-65535 | Mgmt station | 161 | Managed nodes |
| SNMP Trap | UDP | 1024-65535 | Nodes | 162 | Mgmt station |
| OV events | TCP | 1024-65535 | Collection station | 162 | Mgmt station |
| ICMP | IP | N/A | Mgmt station | N/A | Managed nodes |
| HTTP | TCP | 1024-65535 | Mgmt station | 80 or 280 | Managed nodes |
| Telnet | TCP | 1024-65535 | Mgmt station | 23 | CS/managed nodes |
| X-Windows OVW | TCP | 1024-65535 | Collection station | 6000 | Mgmt station |
NNM uses these TCP and UDP port numbers to communicate with managed devices, management stations, and users. A firewall must be configured to pass these packets for full NNM functionality.
Given the security implications of allowing telnet and X-Windows access across the firewall, both the NNM system and the firewall should be configured to pass only traffic to and from well-known systems. Configure the file /etc/snmpd.conf on the collection station to allow the management station to perform the necessary SNMP set operation on the collection station by configuring this line:
set-community-name: secret [1] VIEW: 1.3.6.1.4.1.11.2.17.4.3.1.1
[1] Of course you should not actually use “secret” as the community string; it is too easy to guess.
