Packet Filtering With a Router
One of the components of a DMZ (see Figure 10-4 for a contextual diagram) may be a router with packet filters defined in the configuration file. These filters can be configured to defeat IP spoofing attacks, and they can limit external access to specific network servers.
Figure 10-4. The router packet filter.
The router indicated in this illustration is configured with packet filters on its interfaces. The interface connected to the untrusted network passes only packets destined for the web, mail, DNS, and telnet servers. This blocks all direct attacks on the router itself, the bastion host, or devices on the private network, to the left of the bastion host.
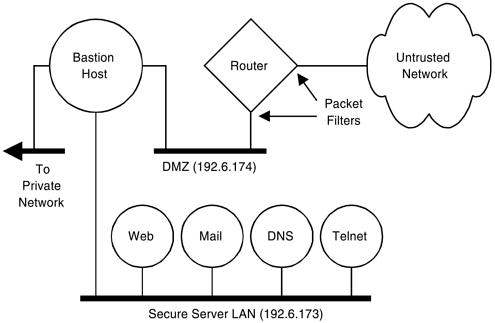
IP spoofing occurs when the source IP address of a packet that comes from the untrusted network is forged as if it originated from the corporate network. For example, suppose that the secure server LAN (SSL) is subnet 192.6.173. One router interface is on the DMZ and the other interface is connected to the untrusted network. This interface can be configured to avoid IP spoofing by blocking packets entering from the untrusted network with source IP addresses belonging to subnets 192.6.173 and 192.6.174.
The same external router might be configured to allow packets to enter the DMZ only if they meet the following criteria:
SMTP (to TCP port 25) sent to the e-mail server
DNS request (to UDP port 53) sent to the name server
HTTP replies returning to the proxy web server
HTTP requests (TCP port 80) connecting to the public web server
FTP replies returning to the proxy web server
telnet (from TCP port 23) terminating on the telnet gateway
This prevents telnet, FTP, and other clients from entering the DMZ, and allows SMTP, DNS, and HTTP clients on the untrusted network to enter the DMZ.
