In this section, we will go over the basics of vulnerability scanning and verify what is happening when the host scan is performed with the help of Wireshark.
Host discovery, port scanning, and OS detection are part of vulnerability scanning. During this process, vulnerabilities are identified and addressed with a proper mitigation plan by the security auditor. For example:
- The security auditor scans hosts to check that only allowed ports are open to the external world
- The hacker scans the ports to find out which services are up and running, for example during this host scan process if the DB ports are open to the outside world then the DB system is compromised for attacks.
Open the host_scan.pcap file in Wireshark; the sample capture shows how the external client is scanning the ports:
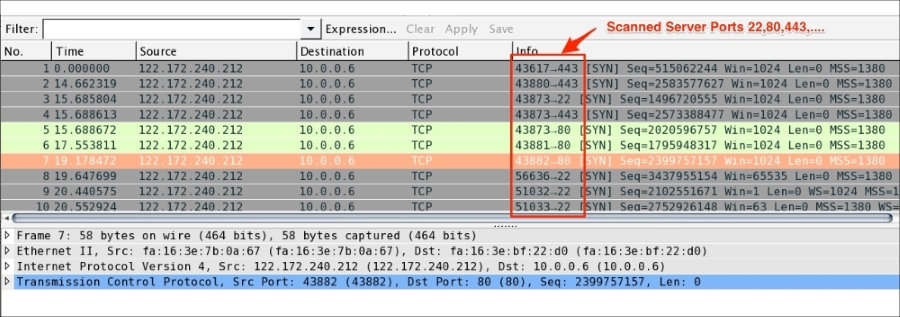
During this process, a SYN packet is sent to the all the ports for common services on each host, such as DNS, LDAP, HTTP and many more. If we get the ACK from the host, the host is considered ACTIVE on that port.
The security auditor or hacker can use network scanner tools to get the port, host, and OS information. For example, the nmap network utility command can be used to scan the active/open ports:
The online nmap tool can be found at https://pentest-tools.com/network-vulnerability-scanning/tcp-port-scanner-online-nmap.
SSL scans are done by different users (for example, security auditors and hackers) to achieve their own objectives:
- The security auditor uses a SSL scanner to find the weakest cipher suites or vulnerable SSL protocol versions present in the SSL server, to remove them
- The hacker uses a SSL scanner to hack the encrypted SSL communication by finding weak cipher suites or vulnerable protocol versions in the SSL server
An example using the nmap command to find available ciphers and the supported protocol version in a given server port 636 LDAP is as shown:
[root@ ~]# nmap --script ssl-cert,ssl-enum-ciphers -p 636 10.10.1.3To find available ciphers and the supported protocol version in a given server port 443 HTTPS [root@ ~]# nmap --script ssl-cert,ssl-enum-ciphers -p 443 10.10.1.3
