Data Services over Cable
The second major market for two-way cable is data, such as Internet access. The intent of data services over cable is to provide high-speed Internet access for computers with Ethernet or Universal Serial Bus (USB) ports. Personal computers, including recent models of Apple Computer, support both Ethernet and USB. Cable networks can provide high-speed, always connected services for relatively low costs. Cost advantages arise because cable provides a natural multiplexing function. That is, one cable port at the head end can connect hundreds of users simultaneously. Telephone networks, on the other hand, require a separate line card for each phone line. This cost advantage is discussed in [Gillett].
Accordingly, the idea of moving data over cable TV networks is an old one. Cable modems were merchandised as early as 1987 by companies such as Fairchild Electronics. The Fairchild M505 Broadband Modem was QPSK and QAM-modulated, yielding up to 10 Mb of full-duplex service. Many of its characteristics are surprisingly similar to the cable modems being developed today. The idea then was to use coaxial networks primarily for intranet use. So, the 1980s generation of modems lacked the scaling properties necessary for public carrier use.
With the growth of the Internet, cable operators have begun thinking of their HFC networks as a logical vehicle for improved data service. Internet access is an inherently asymmetric service, meaning that more data comes from the head end than to the head end, a characteristic that matches the bandwidth capabilities of low-split cable networks. Furthermore, cable networks have the ubiquity to quickly offer service to large segments of the population. Finally, the convergence of Internet access with digital TV made it necessary for cable operators to offer data service and to prevent cannibalization of their video service.
For these reasons, cable has significant leverage and motivation to deploy residential data service. Various research groups are predicting big things for broadband data service. The following are variables affecting the sales of cable modems:
How many systems are two-way-enabled
How well operators can recruit and train field engineering talent and keep their plants clean enough to offer high-bit rate services
How well Web servers can deliver significantly faster service to showcase the speed of cable networks when compared with their telco counterparts
How popular competitive technologies will become, including ISDN and 56 Kbps modems and new phone company services called xDSL
Pricing of high-speed services by Internet service providers
Data services are expected to generate roughly $500 per subscriber per year. This yields annual revenues on the order of $2 billion per year by 2001, by some projections. Though this is far less than U.S. cable's current revenue of $28 billion per year, it does represent a significant new revenue stream and has the added benefit of reducing customer churn for video services.
Fairchild long ago exited from the data/cable business, but the company was supplanted by a number of companies that developed proprietary technologies. Among these were Motorola and Applitek. Applitek became LanCity, which was acquired by Bay Networks, which was in turn acquired by Northern Telecom (NYSE: NT) .
In 1995, the cable industry began exploring the possibility of standardized cable modems. By standardizing, a critical mass of equipment could be developed through common development to provide lower-cost modems. A group of cable operators in North America formed a partnership called the Multimedia Cable Network System Partners Ltd. (MCNS) partnership, whose objective was to develop a purchasing specification for its members so that a critical mass of buying commitment and development could lower costs and improve functionality. Accordingly, MCNS joined with CableLabs , the research and development group supported by the cable industry, to develop the Data-Over-Cable Service Interface Specification (DOCSIS). Motorola and other companies, such as Terayon (Nasdaq-TERN) continue to sell their proprietary systems, but the interest here is to explicate the DOCSIS specification.
The DOCSIS 1.0 specification has been adopted for standardization by the Society of Cable Television Engineers (SCTE), the American National Standards Institute (ANSI), and the International Telecommunications Union (ITU).
Principles of Operation
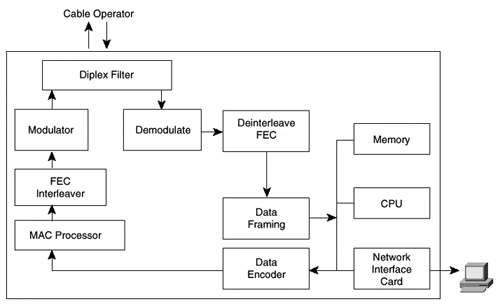
The components for a cable modem are shown in Figure 3-5. These are similar to the components of a digital set top, but without the MPEG elements. Because the cable does not include MPEG elements, it is cheaper than a digital set-top box.
Figure 3.5. Cable Modem Schematic
The operations of data services over HFC will be demonstrated by explicating the DOCSIS specification, version 1.1, which is the most current specification as of this writing. The discussion is segmented into three parts:
Channelization and modulation— Spectrum allocation, modulation, and symbol rates
Startup— What happens when a new modem is attached to the network?
Continuing operations— How a modem sends and receives data after startup
Channelization and Modulation
For data services to operate, the cable plant must provide minimum levels of quality. Therefore, DOCSIS specifies requirements for noise characteristics. Some examples are carrier-to-noise ratio (not less than 35 dB) and burst noise (not longer than 25 microseconds). Cable plants failing to meet minimum quality requirements cannot be expected to support DOCSIS traffic.
Downstream traffic is modulated with QAM-64 or QAM-256, selectable by the cable operator over the U.S. standard of 6 MHz increments anywhere from 50 to 860 MHz. QAM-64 yields 5.057 million symbols per second, or 30.3 Mbps, and QAM-256 yields 5.361 million symbols per second, or 42.9 Mbps. To make data service as compatible as possible with digital TV service, DOCSIS specifies MPEG-2 Transport Frames as the framing protocol; that is, IP data packets are placed in the payload section of MPEG-2 frames. This allows data and video to be multiplexed on a common 6 MHz channel. Interleaving is applied to the forward channel. Depending on the amount of burst protection, latency of 0.22 to 4.0 milliseconds is induced.
While the forward path operates within 6 MHz channels, DOCSIS return paths vary according to the bandwidth. The bandwidths supported by DOCSIS are shown in Table 3-3. Return paths occur anywhere in the range of 5 MHz through 42 MHz. The center frequencies are located with 32 kHz precision. The upstream channel can have either QPSK or QAM-16 modulation over one of five bandwidth options. The gross bit rates available under DOCSIS upstream channels are a function of bandwidth and modulation scheme.
| Bandwidth | Symbol Rate (ksymbols/second) | Bit Rate Using QPSK | Bit Rate Using QAM-16 |
|---|---|---|---|
| 200 kHz | 160 | 320 Kbps | 640 Kbps |
| 400 kHz | 320 | 640 Kbps | 1.28 Mbps |
| 800 kHz | 640 | 1.28 Mbps | 2.56 Mbps |
| 1.6 MHz | 1280 | 2.56 Mbps | 5.12 Mbps |
| 3.2 MHz | 2560 | 5.12 Mbps | 10.24 Mbps |
The bandwidth, placement, and modulation schemes are selected by the cable operator and are a function of line quality. Cleaner return paths can entertain higher symbol rates. As of this writing, the most common bandwidths are 800 kHz and 1.6 MHz with QPSK modulation. As cable plants improve noise characteristics, there will be greater use of QAM-16.
The use of the cable return path is shared among all active transmitters. Thus, the 10.24 Mb in the best case is shared among whomever is transmitting back to the head end at any given moment. Also, there is significant overhead that is to be subtracted from these bit rates. Therefore, a single individual user can experience much less than the stated bit rates but generally will have faster service than current telephone or ISDN-based services.
DOCSIS can be modified for Europe with the following changes to the U.S. specification:
8 MHz-wide channel instead of 6 MHz
European standard Intermediate Frequency (37 MHz instead of 45 MHz)
Return path capability up to 65 MHz instead of 42 MHz
DVB Forward Error Correction (ITU J.83 Annex A instead of Annex B)
Startup
When a new cable modem is installed on a cable network, there must be a very user-friendly installation process. Basically, everything needs to happen automatically. The modem needs to know which frequencies to listen to and on which frequency to transmit for downstream and upstream data, respectively. It needs networking information as well, such as an IP address and packet filters.
The basic steps at startup are listed here:
Obtain physical-layer information, such as which downstream to use, which upstream frequencies to use, modulation scheme, and symbol rate
Obtain network-layer information, such as an IP address and access list filters
Authenticate the cable modem and establish an encryption key
Obtain Physical-Layer Information
When a customer's cable modem is taken out of its cardboard box, it has no idea on which frequencies it will be receiving data from the head end, nor does it know which frequencies it will use to transmit to the head end. So, the first order of business is to learn these frequencies and obtain other physical-layer information.
The modem does so by scanning downstream frequencies for standard control packets. These packets contain messages, called upstream channel descriptors, that are broadcast downstream expressly for newly attached modems from the Cable Modem Terminal Server (CMTS). Among other information, the upstream channel descriptor contains the following:
Frequency on which the cable modem is to transmit on the return path
Symbol rate used to transmit
Maximum number of bytes that can be transmitted the next time permission to send is granted
Modulation technique, either QPSK or QAM-16
The cable modem tunes to a relatively low frequency and ascertains whether that frequency is an analog TV channel or a digital TV channel. If analog, it tunes to the next higher frequency and continues to look for a digital channel.
Eventually, the modem will find a digital channel. Because digital channels are above 350 MHz, modems will normally begin scanning above that frequency. The cable modem then needs to discern whether the digital channel is used for TV or DOCSIS. To do so, it waits for a well-known PID of "1111111111110," which has the hexadecimal notation of "1FFE." This PID is specified by DOCSIS to contain control information. Naturally, that PID cannot be used by the operator to indicate TV program information.
Having found the well-known PID, the cable modem can decode the MPEG packets, recover the data, and obtain the upstream channel descriptor. Because the downstream can be anywhere from 50 to 860 MHz, there are potentially hundreds of channels for the cable modem to scan. Each must be scanned serially, and each channel may have multiple PIDs to decode. Therefore, the process of hunting for the upstream channel descriptor can take seconds or even minutes. This process can be especially time-consuming if there is a system-wide outage and all cable modems in a neighborhood must go through startup at roughly the same time.
Because the process can be lengthy, some cable modems start scanning from frequencies above 350 MHz because frequencies below 350 MHz are presumed to be analog. Also, if there has been a reset, most cable modems can remember startup parameters by retaining them in nonvolatile memory. That is, if a cable modem went through initialization at one point, parameters such as frequency and symbol rate are retained. When reinitialization is required, the cable modem will attempt to use these retained parameters first.
After the upstream channel descriptor is read, the cable modem waits for timing information (in a separate synchronization message) and an indication of when to transmit in a message called the bandwidth allocation map.
Control packets from the CMTS are not encrypted; it would be impossible for an uninitialized modem to sign on to the system without prior knowledge of the encryption keys.
After the modem knows which downstream and upstream frequencies it will use and has permission to transmit, it announces to the head end that it is here and begins ranging. Ranging is the process by which a cable modem learns its distance from the head end. This is required to synchronize the boundaries of the time slots on which to send. Ranging is accomplished by the cable modem sending a short message to the head end and measuring the response time interval. Ranging is a continual process because of thermal changes that cause the cable to expand and contract during the day.
During the ranging process, the CMTS also manages the transmit power of the cable modem. The problem is that if a single cable modem is transmitting with insufficient power, it cannot be heard reliably by the CMTS. On the other hand, if the cable modem transmits with excess power, it could drown out other cable modems on the same cable plant. During initialization, the cable modem transmits at low power. Often the CMTS will not hear the cable modem and a timer will expire. The cable modem will transmit at a higher level, and the process is repeated until the CMTS is happy with the power level it receives.
Obtain Network Information (IP Address Acquisition)
After the ranging process, the cable modem is ready to obtain an IP address and other network parameters. It would be customer-unfriendly and would create security problems if the customer were to configure his own IP address.
The modem obtains an address by using the Dynamic Host Configuration Protocol (DHCP). DHCP is the standard Internet protocol for dynamic assignment of IP addresses. When a subscriber requires an address, the cable modem launches a particular type of broadcast packet, called a DHCP Discover, onto the return path. The CMTS router at the head end receives the DHCP Discover and authenticates the cable modem. It then returns the IP address of the server to the cable modem, and the cable modem sends a DHCP request to the DHCP server. The DHCP server returns an IP address to the router, which caches it and relays the information to the subscriber cable modem. The router will identify and store the MAC address of the modem. Thus, the router keeps a database of all necessary address bindings for a particular user.
In addition, the initialization process provides other information to the cable modem by use of a trivial file transfer (TFTP). The DHCP address server can be linked with a subscriber management database to provide bandwidth guarantee parameters (semantics to be determined), packet filters (semantics to be determined), graphical user interfaces (customized per user), and the time of the day from the head end. The time of day is needed to timestamp error messages.
Security
The controlling document on security is the Baseline Privacy Plus (BPI+) Interface Specification (BPIv1.1-IO1-990316), available at www.cablemodem.com .
Inasmuch as HFC is a shared medium, user data encryption is required for privacy. Without that, is possible for excessively clever customers who have proper network analysis equipment to snoop on the data traffic of their neighbors. Baseline privacy not only protects the customer from intrusion, but, perhaps more importantly from the MSO's point of view, it protects the cable company against unauthorized use.
The key elements of BPI+ are an encryption protocol and a key management protocol.
Encryption
User data is encrypted with the U.S. Data Encryption Standard (DES), which has varying levels of strength. To make DOCSIS an exportable product, the encryption must go with it. However, due to national security concerns, the federal government places limits of the strength of encryption algorithms that can be used domestically or exported commercially. The DES used in DOCSIS provides relatively light encryption strength.
DES works simply by having the sender and receiver share a secret before data is transmitted. The shared secret, or key, is an integer that is used by the sender to scramble data and by the receiver to descramble data to render the original data, within the safe confines of the customer or carrier premises.
Key Management
Obviously, it is necessary that there be a key exchange protocol before data can be exchanged. Because the keys contain important information, their exchange is also encrypted. The encryption for key exchange uses a triple DES, a relatively strong form of encryption. The algorithm for exchanges uses public key exchange.
Authenticate the Cable Modem
For the service provider to be protected with proper conditional access, it is necessary to authenticate the user cable modem. Otherwise, it would be possible for an intruder to impersonate a legitimate cable modem and thereby obtain keys and access.
The method to authenticate the cable modem uses a relatively recent innovation in cryptography called digital certificates. When a cable modem is manufactured, the following information is installed into the cable modem permanently:
A serial number
A cryptographic public key
An Ethernet MAC address
The manufacturer's identification
The union of all these data elements is referred to as an X.509 digital certificate.
When a customer signs onto the network, his cable modem sends the embedded X.509 certificate information to the head end. The head end validates the certificate and then uses the customer's public key to encrypt subsequent data packets.
Special precautions are taken in the event that the cable modem is a member of a multicast group or has preferred quality of service. In both cases, the cable modem is assigned to a class of users. That class is determined by multicast group membership or membership in a group of cable modems enjoying higher quality of service. In these two cases, the key exchange is processed by the group.
These measures are in addition to any application-level end-to-end security. Security is the subject of discussions in various standards organizations and remains an open issue.
Security vulnerabilities are specific to user environments. For example, Windows 95 users on cable data systems have been advised to disable file sharing in the Networking menu of the Windows 95 Control Panel file. Otherwise, it is possible for others on the cable system to peer into the disk drives of the exposed user. However, turning off file sharing creates problems for users who have local-area networks. Additional software is needed to provide security on cable systems while enabling file and print sharing.
It should be observed that security measures for data are fundamentally different from security measures for digital video or analog scrambling. Security for data relies on unique descrambling or de-encryption per user session. Broadcast security cannot be done this way because all viewers receive a common program. Therefore, common descrambling or de-encryption is required. This means that data security is structurally different from broadcast security, and dual security mechanisms are required.
Continuing Operations
After determining upstream and downstream frequencies, ranging, acquiring an IP address, and obtaining security, the cable modem is finally ready to exchange data. Figure 3-6 shows a schematic of the path and process the data follows.
Figure 3.6. Data and Cable Schematic
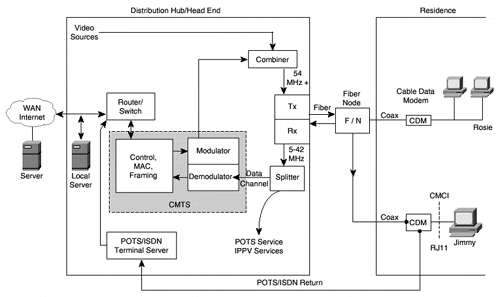
In the forward path, data is received at the Cable Modem Terminal Server (CMTS) from the Internet or private intranets. It is modulated, upconverted to the proper forward frequency, multiplexed with standard video traffic in the analog domain (in the combiner), and transmitted through the distribution plant.
In the return path, traffic is received at the head end. Some of the upstream traffic is split off for other purposes, such as pay-per-view, telephony, and monitoring. The splitting is performed in the analog domain using diplex filters. The remaining data traffic is sent to a QPSK or QAM-16 demodulator, which then sends bits to a terminal server, indicated as the CMTS in Figure 3-6. Traffic is then sent to a local router or switch for transmission to a local server, the Internet, or another cable subscriber. If the cable plant is not capable of two-way service, telephone return can be used. Jimmy's cable modem in Figure 3-6, for example, has an internal telephone modem and an RJ-11 jack for this purpose.
DOCSIS uses an entire 6 MHz channel for the forward path. This enables the MSO to use the same RF multiplexing equipment for data used for video. Six MHz of bandwidth on the forward allows 27 Mb of data per channel, using QAM-64 modulation and RS FEC (net of overhead). The 27 Mb is shared among all subscribers in a system. For example, if there are 27 subscribers online at any instant, each can expect to receive 1 Mb of forward path service, far exceeding the capability of telephone modem and ISDN service.
DOCSIS cable modems are required to operate in bridged mode and run the IEEE 802.1d spanning tree algorithm. Loops are not permitted on the customer premises local-area network.
There is also a provision for the cable modem to join a multicast group using standard Internet Group Management Protocol (IGMP) messages. Multicast is particularly well suited to the cable environment because cable is a natural broadcast medium. When cable modems join multicast groups, the replication problem is simplified and the cable modem is left with the work of retaining packets bound for the multicast group.
Return Path Bandwidth Arbitration
Because only a single source of data is in the forward path, data is transmitted in broadcast mode from the head end to one or more subscribers in the cluster. On the return path, multiple customers may request use of the return bandwidth simultaneously. Therefore, there needs to be a bandwidth arbitration mechanism on the return path. This mechanism is bandwidth arbitration or the Media Access Control (MAC) protocol. If Junior and Rosie decide to transmit at nearly the same time, their bits will collide, rendering both transmissions indecipherable when they reach the head end. There must be a way for them to decide which one goes first and for how long before relinquishing the upstream to the other, or to someone else.
The objectives of any MAC are to do the following:
Support the maximum number of possible users per cluster
Minimize latency on data transfer
Provide fairness so that all users get some access
Achieve maximum bandwidth utilization of the return path
Support multiple classes of service
Well-known LAN schemes such as Ethernet and Token Ring were not considered in the cable environment, due in part to their distance limitations. If Rosie was 10 miles from the head end, a round trip would take 120 microseconds. At 10 Mbps, that would mean that 1200 bits would be in flight before a collision could be detected. A short message could be sent by another user in the interim. Instead, in Ethernet or Token Ring setups, Rosie and everyone else would have to wait for the packet to pass. Polling techniques, such as Token Ring, consume excessive amounts of time for the polling sequence, so polling has never been considered by data and cable vendors.
Instead of using standard Ethernet techniques, DOCSIS opted for a collision-avoidance or credit-allocation scheme built largely on the lines of the original LanCity cable modem system. In fact, substantial parts of the DOCSIS protocol were authored by LanCity (now Nortel) engineers.
With credit schemes, the CMTS sends credits to the subscriber modems, granting them access to the upstream for a specified period of time. The time interval at which cable modems are allowed to transmit is limited by their grants. After grants are exhausted, the cable modems must stop transmission. The CMTS controls the amount of data transmitted per request.
The key features of the DOCSIS return path arbitration mechanism are as follows:
User data and requests to transmit user data are sent in fixed-length increments, or time slots.
Variable-length packets may be sent by obtaining multiple time slots per request.
Mechanisms exists to provide for quality of service.
CRC checksums are used to detect errored packets, but there is no means to correct errors at the MAC layer.
Requests to transmit occur in special packets or may be "piggybacked" inside user data packets, thereby reducing the need for special request packets and reducing bandwidth use.
Credit mechanisms must ensure that the CMTS can provide grants fast enough to keep bandwidth utilization high. If grants from the head end come to the subscribers too slowly, the subscriber modems stop transmitting. The result is that the return path is underutilized. Because the return path contains acknowledgments that permit forward path traffic, the forward path might become underutilized as well.
Normally, only one request may be outstanding from a single subscriber at a time. With a 4 ms interleaving delay on the forward path, a 1.6 ms round trip propagation delay, and processing time, it can take more than 6 ms from the time a request is made by the subscriber to the time the grant is received. Efficient MAC algorithms are required to ensure that grant requests are expedited.
When subscribers collide, they are unaware of the event unless informed by the head end. The head end detects the collision and informs the cable modem that the collision occurred. When informed of a collision, the cable modem performs a backoff and tries again.
MAC design on shared media with large propagation delays remains an interesting research topic and the subject of intense competition.
Apart from normal data exchange, continuing operations require a high level of management. Some of the key ongoing management functions are listed here:
Power management— The head end continually monitors power levels of each cable modem and orders them to decrease or increase transmit levels as needed, in a process very similar to the original ranging process.
Changing upstream channels— If there are significant levels of narrowband interference on the upstream, the head end will command the cable modems using that impaired return path to hop to another frequency. This information is sent in the upstream channel descriptor.
Changing upstream parameters— On the other hand, if the return path is performing well, the head end may elect to increase the use of the existing return path. For example, the head end can command the cable modem to increase the symbol rate.
Alternative Approaches
This review of data services concentrated on the DOCSIS approach. It should be mentioned that other proprietary approaches from companies such as Terayon (Nasdaq: TERN) and Motorola (NYSE: MOT) have found market acceptance. Com21 (Nasdaq: CMTO) has a DOCSIS product as well, but it also has an ATM-based alternative. However, these products have not been explored here because of the relative lack of available sources and because DOCSIS presents the design issues and concepts completely for explanatory purposes.
Table 3-4 summarizes DOCSIS channelization characteristics.
| Characteristic | Return Path | Forward Path |
|---|---|---|
| Also known as | Reverse path, upstream | Downstream |
| Channelization | 200 kHz, 400 kHz, 800 kHz, 1600 kHz, 3200 kHz | 6 MHz |
| Modulation scheme | QPSK, QAM 16 | QAM 64 |
| Access | Via MAC protocol | Broadcast |
| Shared bandwidth | 320 Kbps to 10 Mbps, depending on symbol rate and modulation | 27 Mb |
Challenges to Data over Cable
Widespread industry development of cable for data depends on resolving several technical challenges:
Competition from xDSL and other services
Return path noise problems
Problem isolation
Scaling techniques
The next sections explore these issues in greater detail.
Competition
The lucrative market for high-speed data services will attract service providers using other technologies. Among the key competitors will be the big telephone companies that will offer various forms of digital subscriber loop services (discussed in Chapter 4); new generation carriers, offering fiber access to multiple dwelling units (discussed in Chapter 5); and wireless carriers using various technologies (discussed in Chapter 6). Cable is particularly well suited to broadcast applications, such as TV distribution. But data services, especially for commercial purposes, often require a symmetric bandwidth capability—that is, as much bandwidth coming from the client as going to the client. Cable is not well suited to this profile.
Return Path Problems
The return path is enabled in the frequency range of 5 to 42 MHz. This is low frequency that has good attenuation properties. On the other hand, because there is heavy use of those frequencies by other services, ingress noise is a problem.
More importantly, the shared nature of the return path creates a funneling effect. Impairments are received by coaxial wires (which act as giant antennas) in the home and are sent upstream. These impairments are funneled together as the signals move upstream because of cable's tree and branch topology. This means that noise gets increasingly louder as you go upstream, rendering the signal potentially indecipherable. (For a summary of issues of return path problems, see [Prodan].)
Sources of Ingress
Ingress noise is picked up by the cable from outside sources, through leakage and bridged taps. Here's a partial list of problems that result in ingress noise:
HAM radio and citizen's band (CB) radio. Both are allocated frequency by the FCC within the 5 to 42 MHz passband. Also, there is a business band radio service near the CB band.
Poorly insulated equipment in the home, such as microwave ovens, televisions, radios, and electric motors (vacuum cleaners and so on). If these are operating near a loose F-connector, the noise will be picked up on the cable and sent upstream.
Emissions from outside the home, such as lightning, neon lights, vehicle ignitions, and powerline interference.
The output of digital signals from the home terminal. Sometimes the source of noise could be the cable modem or the digital set top itself.
Tampering and malice.
Loose or poor quality F-connectors and bad cable quality and installation in the home
Corrosion. The design life of taps is 15 years, but in reality, street taps don't last longer than 5 years.
Despite the miles of cable owned by the operator, noise characterization studies have determined that most ingress noise on return path cable plants comes from inside consumer's homes, which is out of the control of the cable operator.
Scaling Techniques
Because cable is a shared medium, care must be taken to avoid congestion as the number of users grows and the usage of each user grows. In both cases, there needs to be a plan for how to manage scaling for video and ATM for data services and control functions.
Multiple Return Paths per Forward Channel
In the event that path traffic grows, collisions might increase without a corresponding increase in forward traffic. In this event, it might be necessary to add an additional return path to complement the forward channel. Now there are two return paths, each with its own port.
In Figure 3-2, for example, Jimmy and Rosie share a common fiber node on the return path. Because the return is used heavily, the cable operator could assign Jimmy and Rosie to different frequencies for the return path, even though they use the same forward channel. Control messages from the CMTS must instruct the respective modems to use their assigned frequencies. Management processes at the head end are responsible for load balancing across the return paths.
Having multiple return paths potentially complicates the MAC design process. Data received on two different ports at the same time is not a collision, but the MAC will still consider it a MAC collision unless proper care is taken.
Additional Forward Channels
A single forward channel provides a shared 27-Mb service to a neighborhood. When take rates and individual utilization permit, another forward channel can be allocated to data service. This means one less channel for analog data or multiple digital TV channels. The tradeoff of bandwidth between data and broadcast use is strictly an economic tradeoff.
Smaller Clusters
A final scaling technique is to extend fiber farther into the neighborhood. Initial rollouts of two-way services may be limited to clusters of 2000 homes passed. In response to congestion, it might be necessary to reduce clusters to 1000 or even 500 homes passed. Unlike using multiple return channels or additional forward channels, this step requires capital expenditures. So, for those MSOs that don't commit to small clusters early, this is likely to be the last resort.
Equal Access
In the current telephone regulation environment in the United States, local telephone companies are required to offer equal access to any long-distance telephone service provider. This is because telephone service has been referred to as a common carrier bearer service, much like railroads, highways, and other public infrastructures. At the time of this writing, MSOs have no similar regulatory requirement at the federal level; that is, MSOs offering data service are not required to offer equal access to ISPs. Thus, in the current environment, a cable operator such as AT&T can offer @Home service exclusively. While it is possible to connect to other ISPs, such as America OnLine (NYSE: AOL) , that are not affiliated with AT&T, one must be an @Home customer to get to AOL. This is like saying that a Bell Atlantic telephone customer can get to a Sprint customer but must be, say, an MCI customer, to get any long-distance service.
America OnLine, Mindspring (Nasdaq: MSPG) , and other ISPs want direct access to cable infrastructure on an equal access basis—that is, on an equal footing with @Home. A number of municipalities seeking to have a competitive local data/cable environment have required equal access for cable franchises in their respective localities. Portland, Oregon, was the first city to require equal access in late 1998. AT&T claimed that the city had no jurisdiction to require equal access without a federal mandate. In January 1999, the case was taken to Federal Court, and Portland won. Other cities, such as Los Angeles, are pursuing an open access policy. On another legal front, Internet Ventures, a small ISP in Redondo Beach, California, sought similar access to cable using a different legal argument. In this case, Internet Ventures argued that they must be given carriage on a Must Carry basis. As of this writing, this case is winding its way through the legal system.
For their part, the cable operators argue that allowing competitors to use its cable networks removes the incentive to invest in DOCSIS and the upgrades necessary for high-speed two-way transmission. This is precisely the same argument that local telephone companies have used to argue that they should not be required to resell high-speed services that they develop and offer.
The argument for equal access will become more acute when cable operators begin to offer telephone service, as they intend. In that case, AT&T, with its direct access to 25 million subscribers, will offer its long-distance service. No doubt MCI, Sprint, and others will have something to say about that.
