Smart cards present a variety of faces depending primarily on the type of integrated circuit chip (ICC) embedded in the plastic card and the physical form of the connection mechanism between the card and the reader. They can be very inexpensive tokens for financial transactions such as credit cards, telephone calling tokens, or loyalty tokens from a variety of businesses. They can be access tokens for getting through locked doors, for riding on a train, or driving an automobile on a toll road. They can function as identity tokens for logging in to a computer system or accessing a World Wide Web server with an authenticated identity. Of particular interest are several such variants, including cards with
surface contacts leading to a memory-only ICC
an electromagnetic connection to a microprocessor ICC
surface contacts leading to a microprocessor ICC
high-level physical network connections (e.g., Universal Serial Bus, or USB)
The very earliest smart cards were memory cards containing an ICC comprising only nonvolatile memory (NVM) and the necessary circuitry to read and write that memory. Today, such cards still constitute the largest number of smart cards in use. These cards are relatively inexpensive and provide modest security for a variety of applications, ranging from transportation fee tokens to telecommunications fee tokens (such as phone cards).
A memory card is used for storing information in a permanent or semipermanent fashion. The circuitry of the smart card exposes, through a standard electrical connector, the control lines for addressing selected memory locations as well as for reading and writing those memory locations through the electrical connectors on the face of the card. There is no on-board processor to support a high-level communications protocol between the reader and the card. Rather, memory cards use a synchronous communication mechanism between the reader and the card. Essentially, the communication channel is always under the direct control of the reader side and the card circuitry responds in a very direct (synchronous) way to the very low-level commands issued by the reader for addressing memory locations and for reading from or writing to the selected locations. In some recent memory cards, security enhancements have been incorporated through the provision of memory addressing circuitry within the chip that requires a shared secret between the terminal (which is writing to the card chip) and the chip itself.
A contactless card has an ICC embedded within the card; however, it makes use of an electromagnetic signal to facilitate communication between the card and the reader. With these cards, the power necessary to run the chip on the card is transmitted at microwave frequencies from the reader into the card. The separation allowed between the reader and the card is quite small—on the order of a few millimeters. However, these cards offer a greater ease of use than cards that must be inserted into a reader. This ease of use can be mitigated by other factors.
With the current state of the technology, the data transfer rate between the reader and the contactless card may be restricted by the power levels that can be achieved in the card; that is, for such cards without an internal power source (e.g., a battery) the power to run the on-card processor must be derived from a signal transmitted to the card from the reader. The power levels achieved typically allow only very small separation (a few millimeters) between the card and the reader. Further, a feedback mechanism from the reader to the card through which cardholder verification is done is a bit more awkward with the contactless card. Consequently, these cards are most popular for uses where the possession of the card is deemed to be adequate authorization for card use.
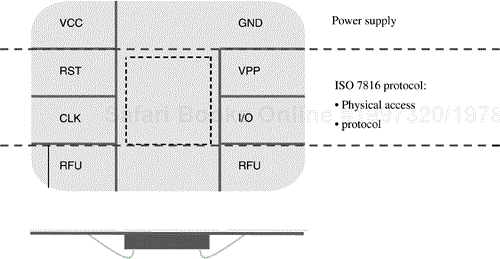
A smart card, that is, the card that is most commonly viewed as a “smart card,” is one that makes use of an electrical connection between the on-card ICC and the off-card computer. The physical connection is made through a contact plate on the face of the card; the contact plate providing eight distinct electrical connections to the embedded ICC as illustrated in Figure 2.1. The most common such physical connection makes use of two connectors on the face plate to effect a half-duplex input/output (I/O) channel to and from the card.
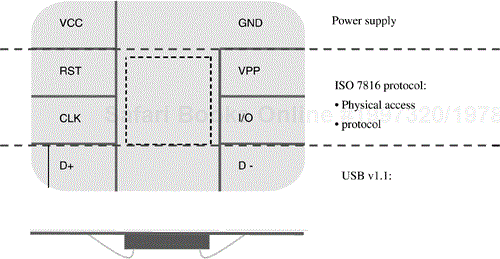
A second variant of such cards, which is just starting to come into being, makes use of two additional connectors on the face plate to effect a full-duplex channel through a USB connection. This is illustrated in Figure 2.2. This variant greatly simplifies the host computer connectivity in that a special smart card reader is no longer required; connectivity is achieved through the USB port to the host.
Except for the physical mechanism used to transfer information between the reader and the card, contactless and contact-based cards are very similar in overall architecture. This book focuses mainly on smart cards that make use of electrical connections between the cards and the readers. The two cards that we will review in some detail can actually be interfaced through a smart card reader or through a USB port, but this impacts only the physical interconnection. This type of microprocessor-based smart card combines all the necessary ingredients for an enhanced-security computing platform. It integrates both memory and a central processing unit (CPU) into a single ICC. This minimizes the opportunity to intercept well-defined electrical signal patterns moving between processor and memory elements. Keep in mind that the security resulting from this integrated packaging is not infallible. The smart card is tamper resistant, not tamper proof.
The impetus for creating smart cards was the need for secure tokens that could contain information and that could provide a secure platform for certain processing activities. These capabilities were greatly facilitated with an innovative packaging approach for the principal elements of a computer system, as illustrated in Figure 2.3. Specifically, all the basic components of a computer system are incorporated into a single ICC. This means that the physical connections between these components are embedded within a monolithic (silicon) structure. This, in turn, means that it is difficult for an observer to intercept signals passing between these components (within the chip). The net result is a more secure computer system than is normally achieved with macroscopic physical connections between components.
Central to the overall security architecture is the concept of physical security. The smart card figures very prominently in this. From the cardholder's standpoint, being able to have the smart card computer platform in physical possession is a large step toward overall security. In this case, attacks against the security of the overall system have to be made against the system components while in operation or through examination of information gained while the system was in operation. This means, for example, that attacking encryption algorithms used by the smart card must typically proceed from captured cyphertext, not from active examination of the card while in use.
Conversely, the overall security architecture of the smart card-enabled system must be such that if a card is no longer in the cardholder's possession, the damage to the system through a security attack can be limited through the knowledge that the card is no longer in the cardholder's possession. Further, the vulnerability to the entire system must be minimized if the information related to a single cardholder is compromised.
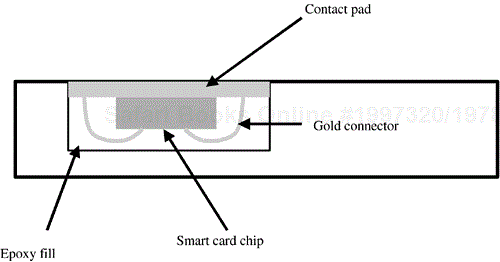
Complementing the concept of physical security is the concept of tamper resistance and tamper evidence on the part of smart cards and their constituent parts. Central to this concept is the packaging of the ICC and its connections into a module that is encased in an epoxy resin as illustrated in Figure 2.4. This packaging provides for both tamper resistance and tamper evidence. The epoxy is nontrivial to penetrate in a nondestructive fashion and to do so requires possession of the card. If the module packaging is penetrated, it requires destruction of the packaging, thus providing evidence of the tampering.
An adjunct to physical security, at least in the case of the smart card, is the enhanced security architecture of the microprocessor-based computer installed in the card and the tamper-resistant packaging of the card itself. This chapter examines the architecture of the smart card's computer. Packaging the processor, memory, and I/O support in a single ICC enhances the security of the entire configuration. It is difficult, though certainly not impossible, to connect electrical probes to lines internal to an ICC. The equipment to insert such probes is reasonably expensive. Consequently, for an attacker to extract information directly from a chip requires physical possession of the card, costly equipment, and detailed knowledge of both the hardware architecture of the chip and the software loaded onto the chip.
As we noted earlier, the ICC is packaged into a “module” which is then inserted into the card body. The module itself is a tamper-resistant and tamper-evident package. When the module is, in turn, embedded into the card body, it actually forms a second layer of tamper resistance and tamper evidence. Tamper resistant refers to the characteristic that, given physical possession of a smart card, it's a nontrivial task to get to the chip and even more nontrivial to extract information from the chip. Further, tamper apparent or tamper evident refers to the characteristic that, to do so, will typically leave an obvious trail that the card has been tampered with. Thus, it is difficult to learn the secrets contained within a smart card without the cardholder knowing that the card has been compromised.
The construction of a smart card is a nontrivial manufacturing problem, particularly given the volume of cards produced, the environmental conditions under which cards must operate, and the length of time they're expected to provide undiminished service. The details of card construction typically are a closely held secret of each manufacturing company. The general features of the process are, however, relatively standard.
The construction process proceeds from the beginning in two threads:
the manufacture and printing of the card body
the preparation of the ICC module and its insertion into the card body
The last stage in the preparation of the card itself is typically the final printing of information on the face and back of the card. This is the point in the process where the card is tied to a unique cardholder, and it generally entails both the printing operation and storing a set of information into the ICC of the card—information that uniquely identifies the cardholder.
The card construction operation, including its personalization for each individual cardholder, is done under the auspices of a “card management system” which controls and tracks the manufacturing and deployment operations on a population of cards. In Chapter 10, we will examine the characteristics of card management systems and smart card application infrastructures in a bit more detail.
Smart card bodies, according to international standards, must be composed of polyvinyl chloride (PVC) or an “equivalent material.” The physical requirements placed on the card body by its operating environment are quite rigorous. The smart card is generally carried on the person of the cardholder, either in a purse or perhaps in a pocket wallet. Consequently, the card is subjected to a large amount of bending and flexing. The material from which it is constructed must be sufficiently resilient to return to an essentially flat shape after it is flexed. This flat shape is required in order for the electrical contacts to be stable when the card is inserted into a reader or when it is swiped through a magnetic stripe reader.
The card body material must also be resistant to the effect of infrared or ultraviolet radiation, which is sometimes used as a fixing process in the printing operation. A recurring problem is an induced brittleness from the printing process, which makes cards crack during normal operations. Sometimes, this cracking can be so severe as to cause embedded ICC modules to be ejected from the card.
The most modern card construction sometimes makes use of the layering of dissimilar materials. The layering itself enhances the mechanical properties of the card against failure during flexing and bending. In addition, the layering diminishes the depth (into the card) of any failure induced by the printing operation. Finally, the layering process allows specially printed components (e.g., white light holograms) to be affixed to the card during the construction process. This greatly increases the difficulty of counterfeiting a card.
The computer on a smart card is a single ICC that includes the CPU, the memory system, and the I/O lines. A single chip is used in order to make tapping into information flows inside the computer more difficult. If more than one chip were used to implement the smart card computer, the connections between the chips would be obvious points of attack. Signals passing across these connections would typically not be protected (e.g., by encrypting information) from eavesdropping. Hence, extracting information from the card would likely be greatly enhanced.
Most smart card programming consists of writing programs on a host computer that sends commands to and receives results from predefined or application-specific smart cards. These applications read data from and write data to the smart card and perhaps make use of the modest computing powers of the processor on the smart card. Smart cards, in these applications, typically are secure stores for data pertaining to the individual bringing the card to the system, such as personal identification data.
In situations where no off-the-shelf card contains all the functionality needed by the application, the programmer may be able to extend the capabilities of an off-the-shelf card by writing software that runs on the card itself. This software may implement special-purpose or higher level function on the card that is a combination of existing operating system functions, or it may provide additional protections for the data stored on the card.
Finally, there may be situations where the operating system capabilities of an existing smart card need to be extended or where a wholly new and unique smart card needs to be manufactured. Examples of such situations include a closed system application where cost or a particularly high level of security is a critical factor or where a particular encryption algorithm is needed to connect the smart card to an existing host system. In these situations, smart card programmers write new operating system software for smart cards partially or completely in the assembly language of the processor on the smart card.
Regardless of the type of software being written, the smart card programmer must be constantly aware of the two central concerns of smart card software: data security and data integrity. The invocation of operations on the smart card must be allowed only by entities whose identities can be authenticated by the smart card. Conversely, the smart card's identity must be authenticated by the off-card (host computer) application. In some instances, the privacy of information flowing to and from the card must be guaranteed by encrypting the information.
An interesting problem that must be handled with the computer in a smart card is the integrity of information in the ICC in the midst of transaction computations. Power to the ICC is provided through the reader connections to a smart card. Because the smart card typically can be removed at any time, it is not unusual for the card to be removed in the midst of a computation (transaction). This particular error condition is actually given a name: tearing. When this happens, it is important that information not be left in an ambiguous state within the ICC. In particular, when some form of value is stored on the smart card, for example, in a cash purse, it is important that value not be “created” on the card during the conduct of a transaction operation. That is, no intermediate state of the purse should ever be greater than the final intended value of the purse at the completion of operations.
A number of antitearing mechanisms are used in smart cards. The most common is a mechanism similar to the transaction mechanisms of database systems. A “transaction flag” is set when the operation is started, and this flag is the last thing to be cleared at the completion of the operation. If, at the start of an operation, the transaction flag is noted to be set, it is an indication that a previous transaction was interrupted and not completed. When this state is identified, the transaction can be “rolled back” to the state at the beginning of the previous transaction. In later sections, we'll look at smart card transaction operations in much greater detail.
Most smart cards belong to a family of standardized cards referred to as Class I ID cards. We'll look at the specifications for these cards in a bit more detail in Chapter 3. Such cards have a well-defined size, including length, width, and thickness. These cards also have fixed positions for all the printing and information storage mechanisms typically used on cards. One such mechanism, which is quite prevalent on smart cards, is a magnetic stripe. This is a narrow strip of material affixed to the “back” of the smart card. The back of the card is the face of the card opposite the contact face plate.
The magnetic stripe material is typically a ferrous alloy, which will retain a magnetic field imprinted on it by an electromagnetic write head such as is used in a tape recorder. Characters can be imprinted on this magnetic stripe according an ISO/IEC specification. The information is redundantly recorded in two or three tracks defined within the stripe. By swiping the card past a read head, the information recorded on the stripe can be extracted for use on an attached computer system.
Information is typically stored on a magnetic stripe in a redundant fashion; that is, information is stored more than once at various positions within the magnetic stripe. When the information is read off of a magnetic stripe, the redundant components can be checked for integrity (e.g., a checksum) and for consistency. This allows the retrieval of information even if the magnetic stripe is worn or damaged.
Embossing is a technique for printing characters on the surface of a card such that the characters are raised above the general level of the face of the card. By inserting such a card into a printing press-like mechanism, it is easy to print a copy of the characters found on the card onto a paper receipt. The characters printed on the card are usually an account number, which provides an unambiguous connection back to an account of the cardholder.
Other scanning techniques that can be used on other elements of the card (bar codes, magnetic stripe) are more reliable and provide better integration of the card information into host systems than does embossing. Consequently, embossing is perhaps not as important or used as routinely as in years past. Embossing is, however, perhaps the most straightforward and externally visible technique for monitoring information on the card. Thus, it is perhaps the preferred “method of last resort.”
The face (and back) of a card also can be printed in a “normal,” multicolor printed format. This printing may include uniquely identifying material related to the cardholder, for example, a picture of the cardholder. This provides a mechanism for connecting the cardholder to the card. Anyone presented with such a card can easily compare the picture to the actual person presenting the card.
Printing on the face and back of the card also can be used to identify other entities associated with the card. For example, the name of a bank that issued the card might be included, or the name and logo of a bank association responsible for the standards associated with the card.
The smart card is largely about security. In the construction of the card, security comes in several guises, in the
structure of the ICC and its modular packaging
embedding of the ICC module in the card body
techniques used to communicate with the card
techniques used to manipulate information within the ICC in the card
Much of the way that the smart card is constructed, programmed, and used is replete with measures designed to enhance the security of the system. We'll examine both directly and indirectly many of the attacks used to try to compromise the smart card. It should be noted that security measures for smart card systems are in a constant state of evolution in response to the constant evolution of attack mechanisms.
Historically, there are a variety of attacks against smart cards, which are facilitated by the external provision of power and programming (clock) control to the card. One such class of attack is termed “power analysis.” This approach makes use of knowing sequences of commands that are to be executed by the smart card processor and, by monitoring in very fine-grained steps the power consumed by the smart card processor, determining which commands are being executed; including determining the values of parameters used to trigger switching among processing pathways in the command sequences. This approach is particularly adept at isolating cryptographic operations involving the use of keys; that is, encryption and decryption operations. In some instances, the breaking of cryptographic keys can be greatly enhanced (speeded up) by power analysis.
The counter to this type of attack is to be cognizant of the attack mechanism while creating the on-card code which will effect the cryptographic operations. The cryptographic algorithms can be coded so that power analysis is greatly diminished as a viable attack. Of course, it should be remembered that to make use of such an attack means that the card must be in the hands of the attacker. This means that the cardholder should be able to detect the loss of the card and report it, allowing the information (e.g., keys) contained on the card to be invalidated.
Another attack, which is somewhat similar, is termed “differential fault analysis.” In this form of attack, a particular (usually cryptographic) operation is initiated and then an error is induced into the card operation causing an error response from the algorithm. If the error can be induced repeatedly, it is possible to glean information from the error responses that is useful in breaking the on-card keys. As we'll discover when we look at a couple of specific (commercial) smart cards in Chapter 6, this type of attack can be diminished by reducing the information returned by an error condition within the computation.
Attacks such as these are damaging to a system at large in the case where information from a single card can somehow be used to compromise a larger segment of the system in which it works. If the information gleaned from a single card can only impact that single cardholder, then the integrity of the overall system can generally be maintained. Specifically, if the attacker must have physical possession of the card in order to pursue a particular attack mechanism, then the cardholder has an opportunity to notice the missing card and report it to the system's administrators. In this case, strictly personal information, such as a (cryptographic) key used to establish the identity of the cardholder, can be invalidated and reissued.
Probably the greater risk to the individual cardholder are attacks aimed at intercepting information as it flows between the card and the terminal configuration. If an attacker can access this information stream and extract useful information without the knowledge of the cardholder, then damage might well be done to the cardholder. We will look at a number of such attack mechanisms and the defenses against them throughout the remainder of this book.
Again, the bottom line is that new attacks are being discovered or refined all the time. Then, defenses of those attacks are developed and made part of the smart card methodology. Continuing vigilance of attacks and defenses is necessary on the part of those who develop and deploy smart card-based systems.
Printing or other preparation of a smart card can contain a variety of elements that guard against the card being counterfeited. One such mechanism is a white light hologram affixed to the face of a card. Such holograms cannot be directly copied with normal electrostatic copying machines. Further, it is typically quite expensive to create a copy hologram. Consequently, it is difficult, if not impossible for a counterfeiter to correctly reproduce the physical appearance of a specific smart card.
Just as with currency, certain printing elements may be included on the face of a card that are difficult or impossible to copy with normal copying machines. One such mechanism is extremely fine-line artwork. If line widths much finer than the resolution of copying machines are used, then running a copy of the card will result in fuzzy areas on the face of the card.
Perhaps the best anti-counterfeiting mechanism provided by a smart card is the ability of the ICC on the card to support complex identification protocols. Such protocols, generally based on the sharing of secret information between the on-card and off-card computers, are very difficult (and expensive) to crack. This means that it can be virtually impossible for an attacker to get a card to communicate (with an attacking system) long enough to extract any useful information from the card.
Contactless smart cards are a variant which makes use of a wireless communication mechanism between the card and the card reader. A contactless card contains an embedded ICC but does not require a contact face plate on the front of the card. Rather, an antenna is embedded within the plastic body of the card. This antenna is connected to the ICC. The card, or more correctly the card antenna, must be brought into physical proximity to a card reader, which also includes an antenna. Power, in the form of electromagnetic radiation, is transmitted from the reader antenna and is received by the card's antenna. The power received is quite small, but it is sufficient to power the on-card ICC.
Once power is received by the card and applied to the on-card ICC, a communication protocol is initiated between the card and the host computer. Most contactless cards make use of two distinct frequencies for this communication channel, which allows a full duplex channel to be created. Data is transferred between the card and the host at approximately 100 Kbps.
Contactless cards are most useful for transactions where it is reasonable to assume that possession of the card is adequate authorization for participation in the transaction(s) that the card supports. Paying a toll at a tollbooth, or opening a door that many people use are good examples of such transactions. In such systems, the cardholder is not authenticated to the card as a prelude to the transaction.
During the course of this book, we will, from time to time, discuss the ramifications of using contactless smart cards. However, our main thrust will always be contact-based cards.
Another variant of the smart card features a card with both a contactless ICC and a contact-based ICC. These two processors may be interconnected on the card or they may operate autonomously. This type of card is of particular use for supporting operations that require specific cardholder authentication and other operations that only require possession of the card. The latter is typical of transportation systems, while the former is typical of credit or debit card operations.
While combi-cards have some very useful applications, it should be remembered that having two processors on the card, particularly if they are interconnected, goes against one of the main tenets of smart cards; that is, the monolithic processor and memory combination of the smart card ICC makes it harder to effect a physical attack against the card.
The generally recognized (most secure) smart card packaging approach consists of putting the CPU, all the memory, and the I/O electronics into the same ICC, rather than presenting them in the form of various chips, which are then tied together through electrical connections of some type. Why is this simple packaging approach so profound? Because it provides all the necessary capabilities in a very small physical package and it conceals the interconnections between the various computer elements inside the chip itself, thereby enhancing the security of what's going on (or what's stored) in the computer.
Once the elements of the computer are integrated into a single chip, it becomes very difficult for an outside observer to intercept signals flowing among the various elements and to subsequently discern the information content of those signals. The connection to the outside world through which information flows is a simple I/O port that can be guarded to a large extent by the processor included within the chip. This is done through the use of high-level telecommunications protocols through which the chip's processor element filters all information passed to or from the other components of the chip. Through these protocols, it is possible to require authentication of the identity of the reader-side program that is communicating with the computer on the smart card. In this manner, the smart card can protect itself by communicating only with entities that can prove who they are and that the smart card's computer trusts.
In addition to enhancing the security of the smart card, the ICC packaging also provides a small unit that is amenable to being embedded in a credit card-sized card, which can be carried on the person of the card bearer. When embedded in the plastic card and carried, for example, in a person's wallet, the chip is subject to a variety of physical forces. The card is bent and flexed and might be subjected to sudden shocks. In typical electronic equipment, in which components are tied together through macroscopic electrical wiring or even conducting lines on a printed circuit board, this physical environment is an excellent recipe for many failures. When all the elements are packaged in a single chip, however, the stresses tend to be applied to all the elements equally. So, if the chip itself can hold together, then the components will tend to operate successfully. Empirical evidence indicates that when chips are reduced to a size of approximately 25 square millimeters (in roughly a square configuration) they are able to withstand the day-to-day stresses encountered through normal credit card-type uses.
Achieving these small sizes for the chip to be embedded in a smart card is dependent on several criteria:
the resolution of the technology used for the chip, which is often characterized by “feature size” (e.g., the size of a single transistor element within the chip) in microns
the width of the internal bus of the processor (i.e., is it 8 bits, 16 bits, 32 bits, or 64 bits?)
the type of memory utilized
auxiliary elements (such as power line frequency, voltage filters, and memory-mapping registers) included in the chip for security or functionality reasons
The small size needed for chip features requires leading-edge technology. However, in order for chips to be inexpensive and reliable, we often need to turn to older, more mature technologies. The makeup of memory, that is the amount of ROM, EEPROM, and RAM is a design decision based on the amounts of each memory necessary to address particular problem areas. To meet the constraints of the physical environment, ICCs generally do not exceed 25 mm2. At the same time, the amount of chip area required to implement the various types of memory varies significantly, as shown in Figure 2.5.
The width of the internal bus structure indicates the number of memory address lines running between components within a chip; that is, width is generally indicative of the number of bits in individually addressable sections of memory. Minimizing chip size generally tends to call for selection of fewer address lines; therefore, most smart card chips are currently based on 8-bit microprocessors. These microprocessors also tend to be the older and more mature technologies.
With higher resolution manufacturing techniques becoming more mature, we can expect to see significantly larger memory sizes in coming years; sizes in the 500-kB to 1-MB range are predicted in some quarters. If this evolution does occur, then the smart card will surely become more of a general-purpose computing element in future systems.
The CPU in a smart card chip is typically an 8-bit microcontroller typically using the Motorola 6805 or Intel 8051 instruction set. Hitachi's H8 smart card chip is a notable exception. These instruction sets have the usual complement of memory and register manipulations, addressing modes, and I/O operations. Some chip manufacturers have extended these basic instruction sets with additional instructions that are of particular use on smart cards. Smart card CPUs execute machine instructions at the rate of about 400,000 instructions per second (400KIP) although speeds of up to 1 million instructions per second (1MIP) are becoming available on the latest chips.
In the next few years, 32-bit processors will likely become the norm. This enhancement, coupled with much larger memory sizes, will open up whole new classes of problems that can be addressed by the smart card as a secure and truly personal computing system.
The I/O channel on a smart card is a unidirectional serial channel. This means that it passes data 1 bit and subsequently 1 byte at a time and that data can flow in only one direction at a time. The smart card hardware can handle data at up to 115,200 bps, but smart card readers typically communicate with the card at speeds far below this.
The communication protocol between the host and the smart card is based on a master (host) and slave (smart card) relationship. The host sends commands to the card and listens for a reply. The smart card never sends data to the host except in response to a command from the host.
Smart card operating systems support either character or block transfers, but usually this level of detail is hidden from the smart card programmer.
As was indicated earlier, two smart cards to be discussed in some detail later in this book will allow the direct use of a USB channel. This channel offers both full-duplex operation and higher speed operation. Higher speeds can be exploited with existing smart card O/S architectures. However, some architectural changes will be required to take advantage of full-duplex and essentially peer-to-peer communication protocols. Word is proceeding in this direction, but it will likely be a few years before it makes its way to commercial viability.
Power is supplied from the reader to the card. Virtually all smart cards in use today operate at 5 volts. Some ICCs are able to operate at a lower voltage, nominally 3 volts. In this case, the reader will typically power the card to 5 volts and then the ICC and the reader negotiate a lower voltage as part of the protocol negotiation sequence.
Two interface lines are used to carry I/O traffic between the reader and the card. One line, the I/O line, carries the data bits. This line is found in one of two states, which nominally represent a “0” in one position and a “1” in the other position. The second line, the clock, indicates when the I/O line is to be sampled in order to determine a data bit.
For the USB interface that we've mentioned, two additional lines are used to carry a second I/O channel. Thus a full-duplex connection can be achieved.
The typical link-level protocols that are used between the reader and the card are half-duplex protocols. That is, data is either written to the I/O line by the reader and read by the card or data is written by the card and read by the reader. Thus, each end of the communication line keeps track of whether it is in a talking state or a listening state. The protocols are not terribly sophisticated, so it is possible to get into a sequence of error conditions that may leave one or both of the ends of the channel in an ambiguous state. When this happens, it is the responsibility of the reader to reset the entire protocol sequence, which it can do with the reset line.
Physical security of information stored in a smart card starts with the combination of computer memory and processor in the same small package. It is difficult, though not impossible, to physically examine the contents of memory cells within the chip. It is also difficult, though not impossible, to intercept the electrical signals passing between the processor and memory or between processor elements during selected computations. To examine or intercept such information requires the use of fairly expensive equipment and unfettered access to the smart card itself, usually without the smart card's owner being aware of it.
Security features are sometimes enhanced by randomizing the sequence of memory cells to be accessed by the processor. That is, the address lines for various memory cells don't proceed in a linear sequence, but rather are varied from one cell to the next through some complex algorithm. The net result is that an external observer is less likely to be able to discern any information about where data is stored or how it is being used by simply watching the sequencing of access to individual memory cells.
As the use of smart cards has grown, the number of attempts to thwart the security features of smart cards has grown. Several techniques to coax information out of a card have been identified. Some of these involve manipulation of the power supplied to a card. Defenses against these techniques have been developed as well. Some chips have additional sensors that monitor characteristics of the power supplied to the chip. This information can be used by programs within the chip and allow it to lock down the card when it detects that it is under attack. In extreme circumstances, the card can destroy sensitive information in such cases in order to prevent it from being extracted by the attacker.
Smart cards have a memory architecture that will be unfamiliar—if not downright bizarre—to most mainstream programmers. Programmers typically think in terms of having available large amounts of homogeneous random access memory (RAM) that is freely available for reading and writing. This is definitely not the case on a smart card. There are, in fact, three kinds of memory on a smart card: read-only memory (ROM), nonvolatile memory (NVM), and a relatively tiny amount of RAM.
ROM is where the smart card operating system is stored and is of interest only to assembly language programmers. General-purpose smart cards have between 8 KB and 96 KB of ROM. Here one finds various utility routines such as those for doing communication and for maintaining an on-card file system along with encryption routines and special-purpose arithmetic routines. Code and data are placed in read-only memory when the card is manufactured and cannot be changed; this information is hard-wired into the card.
NVM is where the card's variable data—such as account numbers, number of loyalty points, or amount of e-cash—is stored. NVM can be read and written by application programs, but it doesn't act like and cannot be used like RAM. NVM gets its name from the fact that it happily retains its contents when power is removed from the card; data written to NVM, if not overwritten, will last 10 years. NVM presents two problems:
Slowness. It generally takes 3 to 10 milliseconds to write data into NVM.
Data loss. NVM wears out after it has been written to a number of times (around 100,000 times).
The typical programmer is not familiar with either of these two problems, but must take them into account when writing smart card software.
There is some familiar RAM on a smart card, but not very much—usually only 2,000 bytes or less. This is unquestionably the most precious resource on the smart card from the card software developer's point of view. Even when using a high-level language on the smart card, the programmer is acutely aware of the need to economize on the use of temporary variables. Furthermore, the RAM is not only used by the programmer's application, but also by all the utility routines, so a programmer has to be aware not only of how much RAM he or she is using, but also how much is needed by the routines he or she calls.
A smart card CPU will not necessarily execute code from all parts of the smart card memory system. Most smart card chips, for example, will not execute code stored in RAM. Furthermore, some chips make it possible to reconfigure sections of NVM so that a program loaded into NVM cannot be overwritten (essentially turning the NVM into ROM) or so that the CPU won't take instructions and therefore execute code from this part of memory.
These various types of memory used in smart card chips bring in a very interesting wrinkle with respect to the chip design for smart card ICCs. The implementation technologies used for chip memories vary greatly in the size of individual memory cells as we saw illustrated in Figure 2.5. The smallest memory element is read-only memory. This type of memory, as the name implies, can be read by typical computer elements, but it requires very special equipment in order to write information into the memory. In fact, the writing of ROM can be incorporated very early into the chip fabrication process itself; this technique tends to enhance the security of the chip because it is difficult to examine the contents of the ROM without destroying the chip, even with very expensive probing equipment. So this type of memory is very useful for permanently encoding stored programs for the smart card, but it is useless for storage of dynamic information that needs to be changed during the normal use of the card.
Significantly larger is the electrically erasable and programmable read-only memory (EEPROM). The contents of this type of memory in a smart card chip can actually be modified during normal use of the card. Hence, programs or data can be stored in EEPROM during normal operation of the card and then read back by applications that are using the card. The electrical characteristics of EEPROM memory are such that it can only be erased and then reprogrammed a finite (but reasonably large) number of times, generally around 100,000 times. While somewhat limited, techniques have evolved which make this type of memory quite useful for typical smart card uses. EEPROM memory cells tend to be about a factor of four larger than ROM memory cells. EEPROM, like ROM, does have the nice characteristic of being nonvolatile memory; that is, the information content of the memory is unchanged when the power to the memory is turned off. So information content is preserved across power-up and power-down cycles on the smart card chip.
Larger still is a memory type known as RAM. This is the type of memory used in typical computer systems such as a desktop PC. Information can be written and erased in this type of memory a very large number of times. In the smart card chip, however, a RAM memory cell is approximately four times larger than an EEPROM memory cell. RAM is also volatile memory; that is, the contents of the memory are lost when power is removed from the memory cell. So information in RAM is not preserved across a power-down and power-up cycle on a smart card. RAM is, nevertheless, essential for certain operations in smart card applications; in particular, it requires much less time for RAM locations to be read or written by the chip's processor unit. This can be extremely important when the smart card is interacting with a PC application in which the timing of responses from the card to the PC are important; this is often the case in the mobile telecommunications area (i.e., smart card-based cellular telephones).
The net result is that smart card chips tend to make use of varying amounts of each memory type depending on the specific application for which the smart card is intended to be used. The most powerful chips used in smart cards today have RAM sizes in the 1-kB to 2-kB range, ROM sizes in the 16-kB to 96-kB range, and EEPROM sizes in the 8-kB to 64-kB range.
The demand for stronger encryption in smart cards has outstripped the ability of software for these modest computers to generate results in a reasonable amount of time. Typically, 1 to 3 seconds is all that a transaction involving a smart card should take; however, a 1024-bit key RSA encryption can take 10 or more seconds on a typical smart card processor. As a result, some smart card chips include coprocessors to accelerate specifically the computations done in strong encryption.
A typical smart card processor is an 8-bit microprocessor. Such a processor is capable of manipulating only 1 byte of information at a time. This manifests itself in the support of 8-bit integer arithmetic as the primary computational facility of the computer. Handling larger integer arithmetic or floating-point arithmetic operations requires significant additional programming beyond the basic instruction set of the processor. This presents something of a problem when you need to support public key cryptography on a smart card chip.
Public key cryptography is predicated on the use of integer arithmetic on a scale that severely taxes the capabilities of a typical smart card processor. Performing encryption or decryption operations can be extremely time-consuming, taking several seconds or even minutes. Because these delays are not acceptable given the time it should take to conduct a typical transaction, enhancements to smart card processors are needed. This enhancement has been accomplished by adding to the chip a second processor that is capable of enhanced performance for selected integer arithmetic operations, such as fast integer multiply operations. This greatly speeds up the public key cryptography operations; however, it affects the overall size of the chip (slightly) and the cost of the chip (more significantly).
One of the security threats to smart cards is the ability of an attacker to probe the ICC with high-powered magnification devices such as scanning electron microscopes (SEM). This form of attack is essentially destructive of the smart card. That is, one must disassemble the card in order to extract the ICC from it. One must then chemically (and perhaps physically) remove layers of the chip and then examine the constituent layers with an SEM. Through this technique, however, one can extract much about the software and information stored on the card if one is willing to invest the time, energy, and money. Given the knowledge that can be gained when it is combined with other forms of attack (e.g., power analysis), it is conceivable that multipronged attacks could be devised which would threaten an individual cardholder's personal card.
One approach to mitigating such a physical attack is to harden the ICC itself. That is, as part of the manufacturing process, a hardened shell is deposited over the top surface of the chip. This shell is difficult for a probe to penetrate and is very brittle. This means that if some physical means is used to remove the shell, there is a high probability that the ICC will fracture. This will greatly increase the difficulty in this type of attack.
Smart cards have a very uniform physical footprint. Standardization has been accomplished through a number of international standards. This approach was taken in order to standardize the worldwide infrastructure needed to support the use of smart cards, and allows equipment vendors in all parts of the world to create cards and equipment to use cards that are interchangeable throughout the world.
The construction of smart cards and their internal structure are also highly standardized, which allows them to be used in large-scale systems without having to resort to single source providers. This much standardization, of course, offers the prospect of uniform methods of attacking smart cards and their constituent systems in an attempt to extract the value they represent.
Our review in this chapter of the physical characteristics of smart cards gives us a good grounding from which to begin to examine the software systems contained within smart cards. We'll delve into these aspects in the coming chapters.