2
Do You See What I See?
Remember that failure is an event, not a person.
—ZIG ZIGLAR
OSINT stands for Open Source Intelligence, and it's the life blood of social engineering. Information is the starting and supporting point of every engagement. Because OSINT is so important to us as social engineers, it is vital that you understand all the different ways you can go about obtaining intel on your targets.
Regardless of how you obtain OSINT, you need to have a clear idea in mind of what you are looking for. That might seem easy to do, but it's not as easy as it sounds. You can't simply say, “I want all info on the target.” Every type of information has a different value, and what is valuable can change with the type of attack you are looking to launch.
A Real-World Example of Collecting OSINT
Let me try to give you some perspective. According to the site www.worldwidewebsize.com, there are more than 4.48 billion indexed websites. This doesn't count anything that's not indexed, sites on the dark web or deep web, and so on. Annual worldwide Internet traffic reached 1.3 zettabytes (that is 1,300,000,000,000,000,000,000 bytes). One source even tells us that the Internet can contain up to 10 yottabytes of total data. (Writing 10 yottabytes looks like this: 10,000,000,000,000,000,000,000,000 bytes.)
Why is the amount of traffic on the Internet even remotely important to understand? Well, for example, if you are looking to send a spear-phish, your goal might be to look for personal hobbies, likes, dislikes, and things the target finds valuable. But if you are going to vish your target, then you might want to find details about the target's job, what role the person plays in the work organization, and what kinds of internal and external resources that person would expect calls from. If your goal is to get onsite, then you need to know whether the target would meet with people and who those people would be.
You have 4.48 billion potential websites to scrape through to look for data that can be helpful. So, before you start digging in, it is important to plan your OSINT engagement.
To help you establish some parameters for what you're looking for, use the lists of questions in Table 2-1.
Table 2-1 Sample OSINT questions
| Type of Organization | Questions to Ask |
| Corporation | How does the corporation use the Internet? How does the corporation use social media? Does the corporation have policies in place for what its people can put on the Internet? How many vendors does the corporation have? What vendors does the corporation use? How does the corporation accept payments? How does the corporation issue payments? Does the corporation have call centers? Where are headquarters, call centers, or other branches located? Does the corporation allow BYOD (bring your own device)? Is the corporation in one location or many locations? Is there an org chart available? |
| Individual | What social media accounts does the person use? What hobbies does the person have? Where does the person vacation? What are the person's favorite restaurants? What is the family history (sicknesses, businesses, and so on) of the person? What is the person's level of education? What did the person study? What is the person's job role, including whether people work from home, for themselves, and who they report to? Are there any other sites that mention the person (maybe they give speeches, post to forums, or are part of a club)? Does the person own a house? If yes, what are the property taxes, liens, and so on? What are the names of the person's family members (as well as any of the previously mentioned info on those people)? |
Of course, the questions in the table only touch the surface. You can add other items about types of computers used, employee schedules, what languages are used, type of antivirus protection used, and much more.
Here's a story ripped from the 2017 headlines. (You can read one account of it at https://gizmodo.com/this-is-almost-certainly-james-comey-s-twitter-account-1793843641.) It is centered on former Director of the FBI James Comey. An Internet blogger and researcher wanted to see if she could locate James Comey's social media accounts. Because Comey was the director of the FBI, it wasn't public knowledge whether he had social media accounts, let alone how to locate them. That is where this OSINT story starts.
The full outline of the steps the blogger used to get to the bottom of the story is shown in Figure 2-1. Take a look, and then I'll walk you through it step by step.
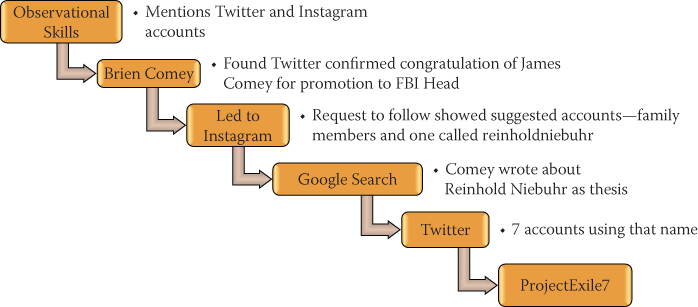
Figure 2-1 Amazing OSINT on a secure target
First, the researcher had to establish what she wanted to uncover: Did Director Comey have social media accounts? If so, where were they?
Researching this using only the Internet proved to be very hard. In 2016, one website listed “The Top 60 Social Media Platforms.” With that many platforms available—all with different rules and methods—it can be very hard to find one man.
Fortunately, one of the oldest forms of OSINT proved to be in the researcher's favor: listening. In one public appearance, Director Comey mentioned that he had Twitter and Instagram accounts.
That statement helped the researcher narrow the search from more than 60 social media platforms to just two. Two is a much easier number to manage in a search.
After not finding any accounts directly linked to Director Comey, the researcher located the Twitter account for Brien Comey, the director's son. The researcher was able to confirm the connection of Brien Comey to Director Comey when Brien congratulated Director Comey for his ascension to Director of the FBI.
One of the things a user can do is to link multiple social media accounts together. In this case, Brien had linked his Instagram account to his Twitter account. The researcher checked the Instagram account, but Brien had locked his account from the public, so only those who had been granted permission to the account could see what he posted.
The researcher decided to request to follow Brien. One of the features of Instagram is that while you wait for a user to accept your follow request, you're pointed to people in the same circle, in case you also want to follow any of those people. Instagram suggested a bunch of users who were Brien's family members (not including Director Comey) and one account for reinholdniebuhr.
If you do a few Internet searches for “Reinhold Niebuhr,” you quickly learn that he was an American theologian and political commentator. However, he died in 1971, so it's doubtful that he has an Instagram account. But with a little more investigation, the researcher learned that Comey wrote about Reinhold Niebuhr in his college thesis.
Armed with this information, the researcher searched Twitter and found seven accounts using that name. Out of all seven, there was one using that name publicly with the handle @ProjectExile7.
With a little more digging, the researcher found that Project Exile was the name of a program that Comey started when he was a U.S. attorney living in Richmond.
The researcher made her discoveries without accessing anything illegal, without hacking one single thing, and by looking only at open-source intelligence sources as she thought through the clues.
This is an excellent example of blending both nontechnical and technical OSINT, and it's a good lesson for all social engineers. That's the basis of the rest of this chapter: the different types of OSINT and how to utilize them as a social engineer. I've broken it down into two main sections: Nontechnical OSINT and Technical OSINT.
Nontechnical OSINT
I consider nontechnical OSINT to be anything that does not involve direct interaction between the social engineer and a computer. You might shoulder surf as a target uses a computer, but you (the SE) are not the one using the computer. It is information you gather using nontechnical means. There are a lot of specific methods I could go through here, but I can loosely define them all as observational skills, and in the following section, I give you some examples.
Observational Skills
Observational skills might seem like they're obvious and easy to use, but using them successfully is not a common skill—especially in the age of the firehose of digital media. If anything, today's marketing tactics have trained us to not pay attention to details. A 2015 study conducted by Emily Drago of Elon University (titled “The Effect of Technology on Face-to-Face Communication”) makes the point that the quality of face-to-face communications has declined due to technology. Sixty-two percent of individuals observed for the study used a mobile device while in conversation with others, despite knowing it would decrease the quality of that communication.
We are in a society that largely conveys messages of 280 characters and emojis, communicating through memes or social media posts. The advances that make these things possible are amazing, but they have created a situation in which people are less observant of those they are communicating with. It's also the reason that observational skills are at the top of my list in nontechnical OSINT.
You might be asking a few questions, such as these:
- What does the term observational skills encompass?
- What can you do to teach yourself these skills?
- What should you expect to reap?
Let's discuss each of these questions and see what you can observe and learn (see what I did there?).
What Do Observational Skills Encompass?
The following scenarios give you some examples of how observational skills can be used in the real world.
Scenario 1
Your task is to gain entry to the mailroom of a large healthcare facility. You must do it in broad daylight. You can't pick locks, climb walls, or jump through windows. You're testing the front desk and security staff to see if they'll allow you into the secured area, so you must go through the part of the healthcare facility where those staff members work.
Here are just a few things you should have in your OSINT arsenal of observational skills:
- Clothing: This simple but sometimes overlooked piece of knowledge is important. In Chapter 1, “A Look into the New World of Professional Social Engineering,” I say the goal of the social engineer is to get you to decide without thinking. If you are breaking into a place where everyone dresses casually, and you're dressed in a three-piece suit, you're going to make people take notice of you. The reverse is also true, so you want to know how employees dress so that you can dress that way, too.
- Entries and exits: Before you enter the building, understand where your egress points are. Is there a door where the smokers hang out? Is one entrance more heavily guarded than another? Are there shift changes that leave a certain post unmanned, or less manned?
- Requirements for entry: What is required to gain entry to the facility or area? Do you see employees with badges? What kind of badges? Where do they wear them? Do they have to also know a code? Do visitors get escorts? Do visitors get badges? Is there a mantrap, turnstile, security desk, or other security setup when you walk in?
- Perimeter security: Check out what's happening outside the building. Are there security cameras? Are there guards roaming the grounds? Are the dumpsters locked up? Are there any alarms or motion-triggered defense systems?
- Security staff: Are they busy looking at their mobile devices or a computer screen, or are they alert and paying attention? Do they look bored beyond belief or interested?
- Lobby Setup: Are keypads or security devices set up where you can shoulder-surf for passwords? (In other words, can you get close enough to peek over someone's shoulder and capture the password as it is being typed?)
Of course, there can be many more things you will want to observe, but those are some of the basics.
To help you understand why these criteria are so important, here's a true story that involves clothing, entries and exits, requirements for entry, and perimeter security. Michele (who's the tech editor on this book) and I were tasked with the very scenario I outlined at the beginning of this subsection. We had to do a fair amount of technical OSINT, which I get into later in this chapter, but there was also a fair amount of nontechnical OSINT that led to our success.
We decided to use the pretext of a pest control company that was hired to quote out an emergency spider spraying. We called our company Big Blue Pest Control and came with full Big Blue outfits and spray bottles of custom blue “poison” to kill any spiders we saw during the quoting process. This poison was actually just some blue Gatorade in a spray bottle.
We started by driving around the perimeter and noticing entrances, exits, camera locations, hangouts for the smokers, and entrances that seemed the most crowded versus least crowded. We also took note of whether the employees coming in and out had badges and how they were dressed. We then picked our initial ingress point and started to do a slow walk toward the door. The reason for the slow walk was to observe what we could of how people were being let in.
We saw two security guards overseeing people as they pressed their badges against a metal stand and were allowed in. There was also a security desk to the right that had someone manning a sign-in sheet.
We decided to try to walk right past the guards and follow the crowd in. That did not work at all. We were stopped by a security guard who asked us what we were doing and why we were there. I looked down at his name badge and saw his name, and then I started to say, “Well Andrew, we were asked to come and give a proposal for some emergency spider spraying… .” The guard stopped me mid-sentence by saying, “Okay, go sign in at the desk.”
I thought we were in, but as we approached the desk, the man there asked for our names. As we gave our fake names, he scoured a list. When he didn't find us on the list, he said, “Sorry, you are not on our visitor list for today. You cannot come in without authorization.”
We tried to explain, influence, and even use pressure and a plea for help. Nada. Shut down. We exited the front door, walked around as we discussed what we would do, and saw a few smokers outside taking a break. I told Michele to follow me, and we walked toward the smokers, acting as if we belonged and were inspecting the outside of the building. I pretended to take notes on my clipboard.
We again did a slow walk, until we saw a few people moving toward the door, so we tailgated right in behind them. Now in the building, we followed this mass of people, and I quickly noticed we were heading straight toward the front where the security guards who just rejected us were located. I saw an elevator to my right, but there were no buttons. “Darn,” I thought to myself, “an elevator that is called by security.” Just as I finished my thought, an elevator door opened, and I immediately stepped inside, hoping that Michele would observe and follow my lead.
Fortunately for me, Michele is pretty amazing at this type of thing and was not lost or overstressed. There was a group of people in the elevator, and Michele promptly announced so all the people could hear, “Boss, can we finish this job soon? I'm starving, and you said we can't eat 'til we're done.”
I got a disapproving look from a woman on the elevator who said, “Feed the poor woman.” I replied, “I want to, but we just have one more floor to inspect. The quicker we get done the quicker she can eat.”
The woman sighed and said, “Well, then, let's get you where you are going… . ,” and I butted in midsentence with “to the mailroom.” The woman pulled out her badge, swiped the receiver in the elevator, hit a few buttons, and said, “Let me drop you off on the way.”
Whew! Thankfully, due to Michele's great observational skills and my quick movements, we had not been caught, and we even got a nice lady to badge us to that secure floor. (And Michele was only partially faking because, really, she is always hungry.)
On the floor with the mailroom, we got off the elevator and discovered that the mailroom door was locked. There was a bell with a label that said, “Ring for assistance.” We rang it and waited.
A woman came to the door and said, “How can I help you?” We spouted off our pretext about doing a quote and so on. The woman replied, “Well, I am going to have to call the security desk to get this approved.”
Our story would have been blown if she had called security, so I said, “Well, you can if you want, but Andrew is the one who sent us down here to get this done.”
She said, “Oh, Andrew sent you? Then come on in.” She let us into the mailroom and said, “Just don't touch the mail.” We were rummaging through ceilings by moving the ceiling tiles, network cable, and endless amounts of mail.
As you can see throughout this story, so much occurred because we made quick observations and cataloged that information for later use. (And this was just the beginning.)
I didn't know I would need Andrew's name, Michele didn't know we were going to meet a sympathetic woman on the elevator, and neither of us knew we would meet a group of disinterested smokers who didn't care that we tailgated in. But observations allowed us to use each of these for success.
Scenario 2
You are tasked to spear-phish a high-profile lawyer from a major American corporation. You're allowed to use any information you can find on her.
This story will unfold more when we get to the technical OSINT section, but to pinpoint a very valuable lesson, let me tell you how I failed miserably on this one.
Our OSINT led us to the fact that the lawyer handled some matters in Massachusetts. We discovered a recent tax law update in Massachusetts that might grab her interest and be very effective in getting her to click a link or open a malicious attachment.
I began crafting an email about the changes in the state of Massachusetts and planned every aspect of this spear. The email was written professionally, did not threaten, included the payload we wanted, gave a realistic deadline for reading and replying, and gave just enough detail to make sure she had to click to get more.
Within minutes of sending the email, we were caught and reported, and the campaign was totally blown. Did you pick out the flaw from the preceding paragraph? I will give you a few seconds to go back and look before I tell you.
Time's up!
Massachusetts is not a state but a commonwealth. This lawyer, whose attention to detail was her strong suit, received an email about changes to the State of Massachusetts tax law and said to herself, “Hey, they should know Massachusetts is not a state but a commonwealth!” That caused her to look at the “From” address and the URL, and to become suspicious enough that she reported it. And our cover was blown.
We did not observe the little detail in this story, and that lack of observation cost us.
The lesson of this scenario is that you need to observe everything you can. Think like the person you are social engineering. Try to understand what they would expect to see, and deliver that. Otherwise, little details can come back to bite you.
What Can You Do to Teach Yourself These Skills?
This topic is hard to cover in a short section in a book. Each person has natural ability as well as learned ability that can make learning these skills really easy or very difficult. Because I don't know you personally, all I can do here is tell you what I did to try and enhance my skills.
I would play a game that was along the lines of Capture the Flag. If I was entering a building—let's say a doctor's office—I would say to myself, “The flags are to remember the first two people I see, what color shirts they are wearing, and what magazine they are reading or what they are doing.”
I would set some boundaries like these:
- They can't be the service-related folks behind the counter.
- I had to still go about my task of checking in and couldn't pause or deviate from that.
- I couldn't write anything down.
Then I would enter the building, observe what I saw, and try my hardest to remember it until I left the building. It would go something like this:
- Older woman sitting to left in blue shirt reading Woman's Day magazine
- Young child, male, striped T-shirt, playing with blocks on the floor
I would make a note of each of these things in my mind and try my hardest to remember them. I used little memory tricks, such as saying something to myself a couple times to try and embed it in my mind.
When I felt that I could make mental notes like this without having to think too hard, I would add some layers of complexity. Eventually, my flags list looked like this:
- Gender of X number of people
- What they were wearing
- What activities the people were engaged in when I first sighted them
- Perceived communication profile (more on this in Chapter 3, “Profiling People Through Communication”)
- Body-language tells
From this, I would try to build a story in my head of why they were at the location I was at, and use the details in the story to remember them.
Honestly, this worked so well—even with my bad memory—that I can remember one office I walked into three or four years ago where I saw two women in black skirts and white button-up tops reading something on an iPad. The woman on the left did not seem to like the woman on the right, but she tolerated her, or she had somewhere else to be. I could discern these things because the woman's hips were fully bladed away from the woman on the right.
There was a man behind a counter with a security suit on—black suit, white shirt, black tie. He had a gold watch on his right wrist, which indicated he was left-handed. His hair was neat, and he had a well-trimmed beard. He was writing on a notepad with a pen. He was observant of me as well as the lobby.
There was a young man waiting in chairs in front of the counter. He was looking at a newspaper, but it appeared to me that he was faking reading. He was staring into space, and the edges of the paper were shaking. I fabricated a story that he was there for an interview and was nervous but was trying to look calm and distract himself with a paper.
It is almost as if I can see that lobby now in my mind. These little observations go a long way toward helping you achieve your goals as a social engineer. My suggestion is to look for your own weaknesses, and then start small and build up. It is important to really get the point that you must practice. Too often, I see people wanting to achieve something 100% right away, but it takes time.
Failure can teach us way more than success if we let it—which is why I need to talk about expectations.
What Should You Expect to Reap?
In the book Unmasking the Social Engineer, which I coauthored with Dr. Paul Ekman, I focused solely on nonverbal cues: body language and facial expressions. When I started learning how to first notice and then decipher these expressions, I felt like some kind of mind-reading superhero. I could look at a face and see emotions that the person was trying to hide, and then I blended that with body language and other actions to almost predetermine how they would react to questions or situations. The crazy part is that I found that my predictions were right more than 50% of the time. Therein began the problem. Let's say I was right 75% of the time. That means I was wrong 25%. In addition to that, it affected my perceived ability, and I felt that I could see more, understand more, and therefore SE more than I really could.
One of my most humbling lessons came from working with Dr. Ekman, who has corrected me time and time again. He said, “Chris, just because you can see the what doesn't mean you know the why.”
Before I discuss expectations, I feel it's important for you to hear this repeatedly: Just because you can see the what doesn't mean that you automatically know the why. How can you make that connection between the what and the why? There are a few ways: questions, more information, and longer observation.
Here's an example: I was teaching a class, and I was talking about a social engineering story from my experience. One student suddenly got an angry look on his face. His body language shifted from being open to closed. With arms folded, he leaned back in his chair and his legs jutted out. I perceived that he was not believing what I was saying, and I began to give him more personal attention. Doing so did not seem to fix his lack of belief, and he drew back. After a few minutes, he excused himself and left the class.
I was dumbfounded. I did everything right. Why was he still mad at me?
Shortly after that, we took a break. I was walking toward the restroom, thinking about this and how I could “fix” it. The student approached me and said, “Hey, I'm really sorry I left. My boss texted me in the middle of class and said we have an emergency at work. I tried to tell him I couldn't do anything because I was in class, but he ordered me to leave and be on this ridiculous conference call. Can I make up the lesson I missed?”
I literally started laughing, which I had to explain quickly, but I told him how I misinterpreted all that I saw. I could hear Dr. Ekman in my head: “Chris, what have I told you before?” It was a great lesson for me in causality.
The same is true about OSINT and observation. Don't assume that the things I am about to show you are all the results of the “stupidity of humans.” I prefer to think that people simply are uneducated to the potential dangers rather than being blatantly stupid.
Take a quick look at the picture in Figure 2-2, and make a mental note of what you observe.

Figure 2-2 What do you see?
Thinking like a social engineer, what do you see in this picture that could help you profile the driver of this car? Figure 2-3 is a zoomed-in version that might help.

Figure 2-3 Is that easier to see?
The right side has a breast cancer support sticker. The left contains a Kids Wish Network Support sticker. Then there is a sticker that says “10-20-Life.” I had no clue what this was for, so I did a quick Internet search and found that it is a sticker supporting stricter sentences for those who commit crimes using firearms.
What do these stickers tell you about this person? That they support charities and which ones are important to them. Could this be because they or a family member suffered from cancer or childhood sickness? Also, they feel strongly about gun laws and gun crimes. Could this be because they were a victim or know a victim of gun crimes?
Armed with these pieces of information, do you think could strike up an elicitation conversation?
Be careful! Too many times I have students who will blurt out, “We will discuss gun laws and why they are wrong,” or something to that effect. But think about how hard it would be to convert you from one belief to another during a conversation. This person will be no different. Blend that with your goal—to have the target not thinking—and remember that you want to converse about their interests, not yours. I explain more about this in Chapter 7, “I Didn't Even Ask You for That,” when I discuss elicitation.
Now take a look at Figure 2-4.
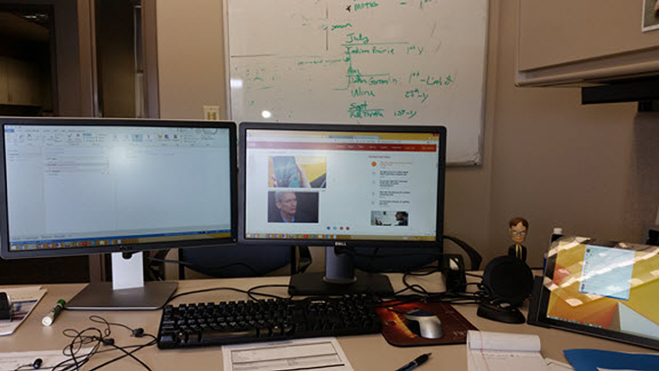
Figure 2-4 What can you tell from this picture?
What do you notice here? What could you observe as a social engineer? Think of the slight details in this one simple picture:
- You can see the type of work environment.
- You can see the operating system the person uses.
- You can notice what type of tablet the person has.
- You can see the person is a fan of a certain sitcom.
- Can you notice the browser they use and mail client, too?
- Do you notice a sign that might indicate some other details about the person?
- What other details can you pick out?
This is just a cursory list; there may be much more that you picked out. Based on this, could you develop enough of a profile to work up one or two phishing emails that would trigger an emotional response?
Sometimes, however, a picture or even an in-person interaction is not enough. This is where technical OSINT can bridge that gap.
Technical Open Source Intelligence
Before you start writing a terrible review, telling the world how bad I suck because this chapter did not contain an all-inclusive list of every tool known to man for OSINTers, let me make something very clear:
- This chapter does NOT contain a full list of every tool, every process, and every method of collecting OSINT from technical means.
Here is what I can tell you: This chapter touches on the tools and techniques I use every day in my business. There are some amazing minds out there in the OSINT world who you can delve miles deep with. Here are just a couple who I have been fortunate to come in contact with:
- Nick Furneaux: I flew to the UK to take Nick's four-day course and was blown away. It is truly eye-opening what can be done with APIs and an understanding of how social media applications work. Nick's website is at
www.csitech.co.uk. - Michael Bazzell: Michael is the man when it comes to disappearing from the web, but he's also developed an amazing set of tools for OSINT practitioners that can help them dig into social media sites and other search engines. You can find his website at
inteltechniques.com.
These fine chaps are both friends of mine, and I have personally taken training, advice, and help from them. I can wholeheartedly say they are masters in the OSINT game. (Shameless plug: They both have been guests on The Social-Engineer Podcast. Search for OSINT to find the episodes.)
My focus in the world of OSINT is on the daily practical uses for the work that I do, which can be broken out into four simple topics: social media, search engines, Google, and other tools. I will touch on each of these topics to give you a flavor of how I use them, and then you can use that knowledge as a foundation for further self-education.
Social Media
No chapter on OSINT would be complete without at least a cursory mention of the topic of social media. What is odd is that I can remember a time when reading your sister's diary would have resulted in multiple beatings. Now, personal diaries are not only online, but it's an insult if you don't read them, comment on them, and like them.
Social media is basically part of our everyday existence, and it is here to stay.
Here are some statistics that will put this into order for us, according to We Are Social (https://wearesocial.com/special-reports/digital-in-2017-global-overview). As of January 2017:
- The world population was 7.476 billion.
- Internet users totaled 3.773 billion.
- There were 2.789 billion active social media users.
- There were 4.917 billion unique mobile users.
- There were 2.549 billion active mobile social media users.
This is important for you, as a social engineer, to understand. Let's consider some of the top social media platforms:
- LinkedIn
With over 106 million users, LinkedIn tells a person the following things:
- Your job history
- Where you got your education
- Where you went to high school
- Clubs and academic achievements you're involved in
- People who endorse your skills
- Facebook
With its more than 1.8 billion users, Facebook tells a person the following things:
- Your favorite music
- Your favorite movies
- Clubs you belong to
- Your friends
- Your family
- Vacations you've taken
- Your favorite foods
- Places you've lived
- Much, much more
- Twitter
With its 317 million users, Twitter tells a person the following things:
- What you are doing right now
- Your eating habits
- Your geolocation
- Your emotional state (within 280 characters)
I could go on, but you get the idea. Just those three social media applications provide a ton of information for you to discover about your targets. I dare say you can build a pretty comprehensive profile on your target from this.
Evaluating a person based on social media should not be confused with developing an actual psychological profile. As the Fun Fact mentions, there are people who communicate one way online and another in person. Even though that is true, social media is still valuable for a social engineer because many attacks occur based on the “online” personality and learning how to communicate with that aspect of the target can lead to a breach.
With hundreds of social media platforms and billions of people using them, social media is a treasure trove of data for social engineers. One of the best ways to rip information from social media platforms is by using search engines, which is the topic of the next section.
Search Engines
The Internet is constantly changing, including new and improved ways of finding information in its yottabytes of cached data. Those constant changes can be a strength for most people, but they can also become a weakness for social engineers because a search engine that works today may not work tomorrow.
I remember when Spokeo first came out. I used it almost daily. It was an amazing source of great information. As its popularity grew, so did the number of ads. Then came the request to pay for information, and then information that was not as reliable seemed to pop up all too often.
Now, I'm not saying that Spokeo has nothing useful, but as a professional social engineer, my time is money. And if I must use another source to verify every fact I get, it can cost me a job.
In my first book, and many subsequent books after, I have found that including lists of tools is kind of useless to the reader. A few things often occur:
- The day the book is released, the tools are outdated and the ideas I gave the readers are old.
- New and better tools come along.
- A combination of the first two things.
Instead of giving you a list of websites and tools, I want to walk you through performing OSINT on a target. Yes, I will mention websites and tools that I use, but the focus will be more on how to think through this aspect of being a social engineer.
Our target is my good friend Nick Furneaux (let's hope he stays my good friend after this book comes out). It should be noted: there is no ill will toward Nick. I'm merely using him to show that even for a very aware, very alert, and very security-conscious person, the Internet holds secrets for those who know how to ask.
d0xing the Furneaux
So, what does it mean to d0x someone? The word d0x is a hacker term that means to work up a document on a target containing details about the target's personal life. Those details are often used to further attack the target, humiliate them, or perpetrate other crimes.
None of those are the goals here. I'm just showing you the power of OSINT and how it can be used. Often, I start at the doors of pipl.com.
Pipl (pronounced people) is a site I describe as what would happen if the White Pages and social media scraped sites and had a baby. What is great about this site is that you can search for a name, a user name, a nickname, or other details you may have about your target.
Just looking at the web quickly tells us that Nick's Twitter account is nickfx. Let's see what we can find by using pipl.com with that nickname. Take a look at Figure 2-5.
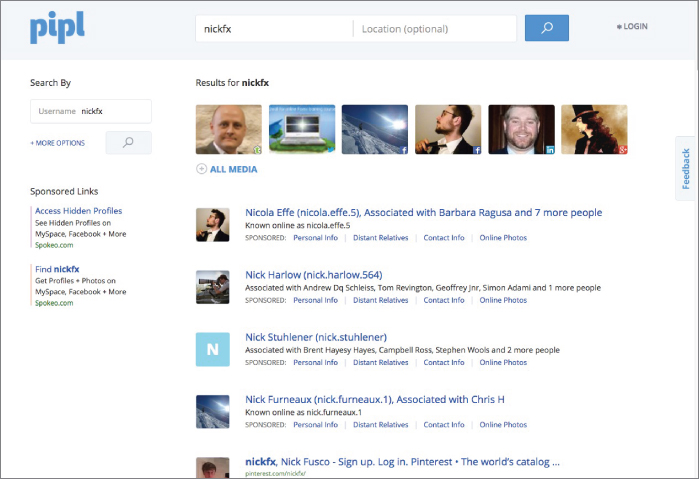
Figure 2-5 Do you see him?
With just a quick glance, we can see the first picture brought up the right “Nick,” and only four lines down, we see Nick Furneaux associated with Chris H (I wonder who that is) and a whole new user name.
Before we get to that, let's see what happens when I click the picture that we know to be Nick. The result is shown in Figure 2-6.
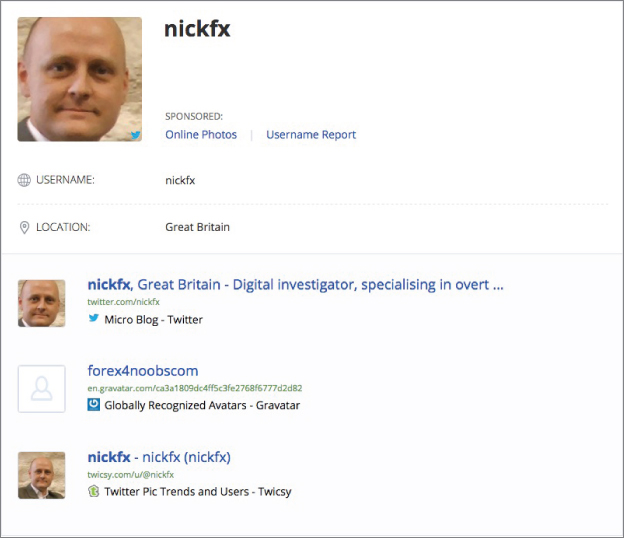
Figure 2-6 Confirmation
With one simple click, we can see confirmation that we have the right guy as well as his location. OSINT! We know where he lives.
Now, back up one page in the results, and click that fourth link down. What does that reveal? Take a look at Figure 2-7.
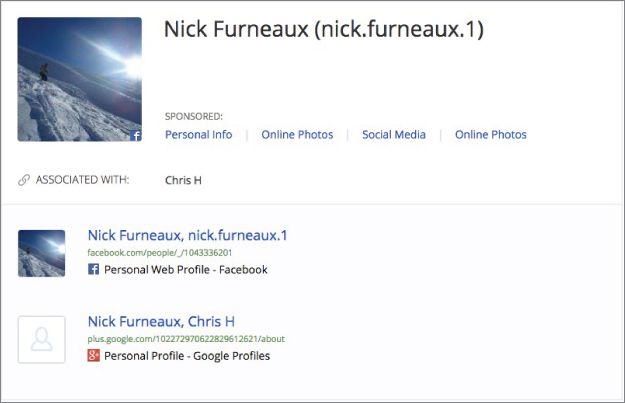
Figure 2-7 More OSINT!
We have some great OSINT here, don't we? A Facebook page and a hobby we didn't previously know that Nick had. He is a snowboarder. And he must really like that Chris H character; he seems to be everywhere.
When I click the Facebook link, I'm greeted with even more OSINT!
- He lives in Bristol, UK.
- I can see a list of friends.
- I've found a new username: nick.furneaux.1.
When I head back to pipl.com and enter just his name and his known location of Bristol, England, I get even more details about him:
- Previous employment
- LinkedIn profile
- Yet another username
- Where he went to school
With a handful of clicks, I have a decent amount of information on Nick that would definitely be useful in developing a profile on him. Can I get more information?
Next, I jump over to a site called webmii.com. The whole goal of WebMii is to help you see people's online visibility. Running a search there for “Nick Furneaux” returns the results you see in Figure 2-8.
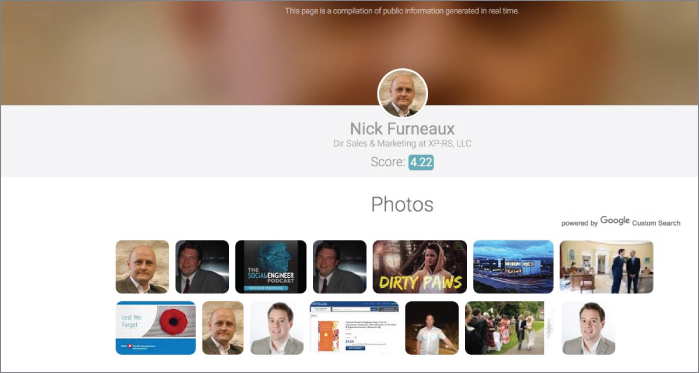
Figure 2-8 A lot more info on Nick
Right away, I notice a few things: Nick's visibility score is 4.22 (which isn't that high because it's out of 10). But clicking on that shows us when in time he was most visible (see Figure 2-9). As an OSINTer, the times when Nick was most popular would pique my interest—I want to find out what was going on in his life at those times.
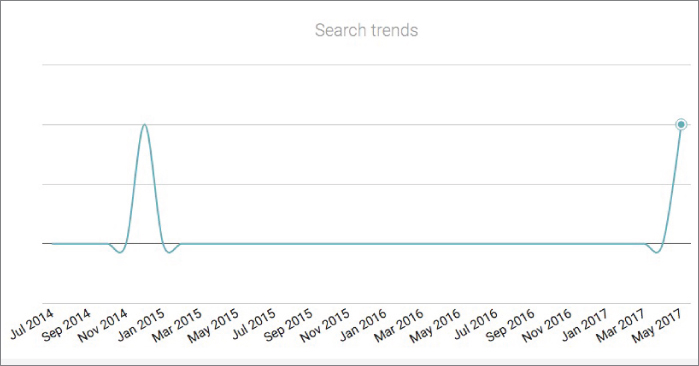
Figure 2-9 When was Nick popular?
Going back to the image shown in Figure 2-8, there are some other pieces of data to be gleaned:
- The first image links to Twitter.
- The third image links to a podcast where Nick was interviewed. It is The Social-Engineer Podcast, and I hear it is really amazing (another shameless plug).
- Many of the other images link to Canadian LinkedIn pages that don't pertain to the Nick Furneaux we're interested in.
- The fifth image is weird: a young man in some kind of animal onesie. What is that?
Clicking that fifth link takes me to a music video made by a company called AFB Productions. When I click the More button, I see what's shown in Figure 2-10.

Figure 2-10 Even more OSINT!
The video appears to have been made by a chap named Toby Furneaux (same last name!), and the driver in the video is none other than Nick Furneaux. Of course, this discovery opens another rabbit hole of digging into who this Toby is and what AFB is all about. It doesn't take long (just two or three clicks) to realize that Toby is Nick's son, and he runs a small production company called Any Future Box (AFB for short).
A good OSINTer would include all of this detail in their info because family members (especially a target's children) are often great resources for attack vectors.
Refer to Figure 2-8 again. That picture of Nick has been in a few places that I stumbled upon. This picture might lead to more resources, so I grab the actual URL of that picture and load it into a reverse image search, which you can do by following these steps:
- Right-click on the image.
- Click View the Image.
- Right-click again, and then click Copy Image Location.
- Go to
www.google.comand click Images. - Click Paste Image by URL, and paste in the URL of the image that you copied in step 3.
You should see a page that looks like Figure 2-11.
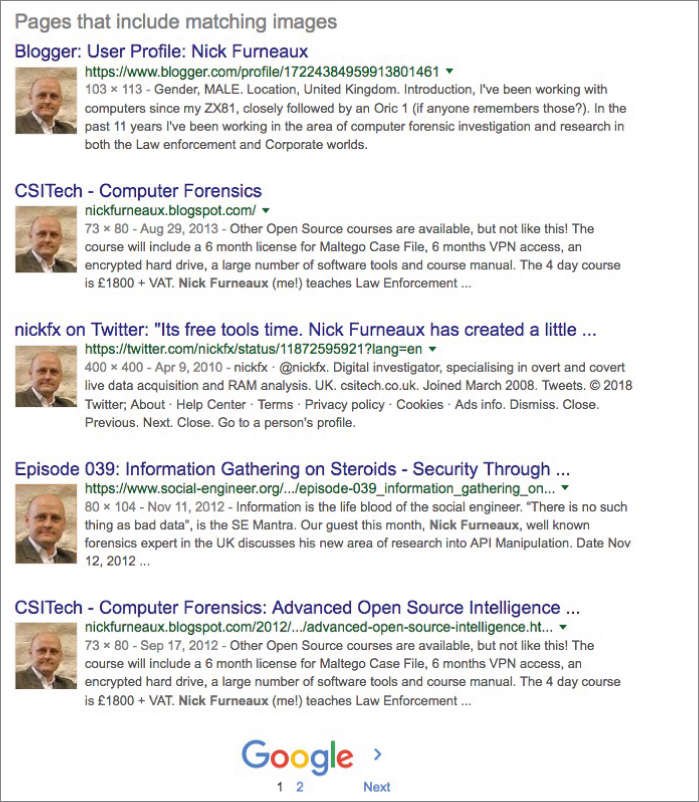
Figure 2-11 That's a whole lotta Nick.
In addition to seeing that he uses this same headshot a lot, I uncovered that Nick has a Blogspot page and wrote on a forensics page too. When I follow the link for the forensics page, I find an interview of Nick from a few years ago, and that interview ends with his email and his website URL.
When I do a quick WHOIS lookup of Nick's website domain name, it reveals what you see in Figure 2-12.

Figure 2-12 Who is you?
Nick has had this website for a long time, and it's not expiring any time soon. Interestingly (and intelligently), Nick has his domain privatized. That means there is no info on the record; just his company name, which we already know, and that he is an individual in the UK.
The type of information-gathering I just walked you through is very common in the world of a social engineer. Think about why this is so. With very few clicks, I was able to uncover quite a bit of useful information on a target.
Granted, I didn't find a link to all of Nick's passwords or his private photos (thank God for that), but I did find enough information to really help if I wanted to attack Nick with a phishing or vishing attack.
Is that it, though? Absolutely not. Entering the ring is the heavy-weight champion of the world when it comes to OSINT.
Enter the Google
Google. The word alone should make a social engineer giggle with happiness. Okay, okay—that mental picture is pretty disturbing. So maybe put the idea of giggling aside and think of it more like a silent smirk of knowledge-filled happiness.
Why? Google is like an all-knowing oracle. She knows all the things you ever did, stores them, and even caches them if you try to delete them (you know, for safekeeping).
With all this power, and trillions of indexed web pages, how can one little ol' social engineer find the tiny bits of data he or she needs? Before I can answer that, I need to give you a quick explanation of how Google (or any search engine, really) works.
Search Engine Mysteries Revealed!
There really is no mystery revealed in this section. The title is misleading. You probably already understand how search engines work, but on the off chance that you don't, here is a very quick and easy explanation of it.
Search engines use little pieces of code called spiders. Spiders “crawl” (I don't make this stuff up) through every web page on the open web and cache what they are allowed to access. There are certain files, like robots.txt
That cache is put into a database, which, when you enter a search term in the search box, provides results like you see in Figure 2-13.
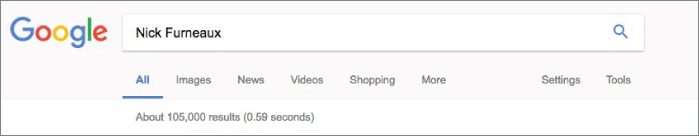
Figure 2-13 He's baaacccckkk.
Let me point out a few key things in Figure 2-13. First, the search returned 105,000 results in .59 seconds. How can it search 30 trillion web pages in .59 seconds? Remember, these pages have been cached in a database, which allows for blazing-fast speeds in searching.
Scraping 105,000 web pages would be not only improbable but, most likely, impossible. So, let me tell you about operators.
Enter the Operators
Google has created a set of search terms called operators that limit what Google looks for. Think of it as being the difference between using a magnifying glass and a microscope. Both get you closer to an object you want to inspect, but if you really want to home in on the details, a microscope is the way to go. These operators are the microscope of searching.
The following two websites list all the useful operators for Google (and even some for Yahoo! and Bing):
https://support.google.com/websearch/answer/2466433?hl=en&ref_topic=3081620www.googleguide.com/advanced_operators_reference.html
For your convenience, here is a list of the operators I find the most useful:
intextintext:csitechsite:site:csitech.co.ukinurl:siteinurl:csitech.co.ukccistech.co.ukforensicsmag.com/csitech.co.uk/interviewssitefiletype:cache:info:
Like most things involving software, there are rules. Google searching is no different.
- The search term follows the operator, a colon, and no space. If you search for
site:whitehouse.govwhitehouse.govsite: whitehouse.gov: - You can use a hyphen (
-).cominurl:csitech.co.uk –site.com - If you have a search term that is more than one word, and you want all of the words included in the search, you must use quotation marks. For example, if I want to search for Nick Furneaux, I could try
intext:"Nick Furneaux"intext - According to Google (
https://support.google.com/gsa/answer/4411411#requests), there is a limit to the number of search terms allowed. The default is 50, and the upper limit is 150. (But honestly, if you are searching with upward of 100 search terms, you might need help.)
Believe me, there are a lot more search terms and other goodies than what I listed here. Google is a powerful tool, and I could spend volumes delving into every little corner of it. But we need to get back to our OSINT. Let's work through some examples and see what we can find.
Limiting for the Win
When I interrupted my search for info about Nick Furneaux earlier in this chapter, I was on my way to creating a nice little profile about him. Can Google either reconfirm my findings or give even more information?
I had found some information like his name and a nickname he uses on at least one social media outlet. What if I search for those two together to see what could be found? Typing intext:"Nick Furneaux" intext:nickfx

Figure 2-14 0 to 206 in .82 seconds flat
In less than one second, I have a solid 206 results on the target. One of the features of searching on Google is being able to see images related to your search. Clicking the More Images For link can show you some interesting results. In this case, the images can take me to pages that talk about Nick.
But I already know a lot of this information about Nick, so let's see what else I can find. I change the search term to intext:"Nick Furneaux" intext:UK
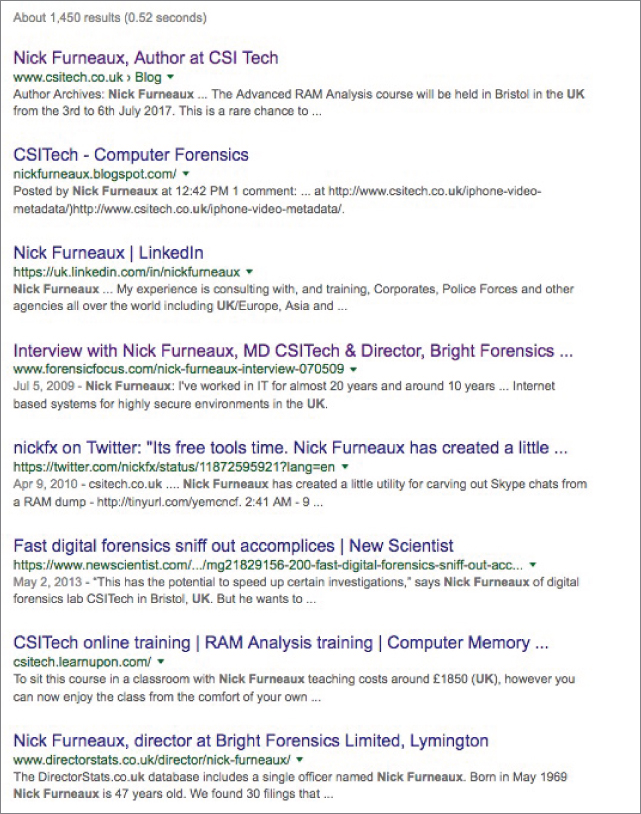
Figure 2-15 Are we getting warm yet, Nick?
The first result tells me he is training in a town called Bristol. The last result provides the name of a company that Nick might still be a part as well as his full date of birth and even an address in—you guessed it—Bristol.
The page also includes a list of family or friends that he might be working with at that company. It's a treasure trove of information.
Changing the “UKBristol
Here's one last example before I move on. What do you think would be the first result if you performed the following Google search?
intext:"Nick Furneaux" site:linkedin.com intext:Bristol
The first result I got when I did this search was Nick's LinkedIn page. Using the Google operators, you can add little bits of information you get from your previous searches to keep homing in until you find the exact piece you need.
I want to show you more about the power of Google, but since Nick is still my friend (or at least he was the last time I checked), I'm going to move the focus away from him and on to general searches.
But It Says “Private” Right in the Title
Have you heard of RSA private keys? An RSA key is a key that is based on a proprietary algorithm. It comes in two parts: the public key, which helps identify it, and the private key, which unlocks the kingdom.
According to this definition, RSA private keys are used to establish a secure connection.
So, you would think that if you searched for RSA private keys, you would find none, right? But using the following search
BEGIN (CERTIFICATE|DSA|RSA) filetype:keygives you more than 3,000 results, as shown in Figure 2-16.
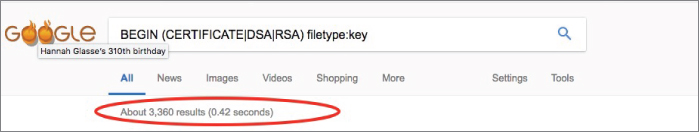
Figure 2-16 Why did you call it private?
But It's Marked Confidential
Often, government entities mark documents with certain classifications to indicate whether the general public should see them. Markings like “CLASSIFIED” and “TOP SECRET” usually indicate that the documents aren't for general consumption. You would assume that you can't find any of those online. (You know what they say about people who assume …)
But since I like living life outside prison walls, let's say we just want to see if there are any documents with passwords, which should be confidential, right?
What if I searched for site:gov.ir intext:password filetype:xls? This should limit my search to any gov.ir domain and look for only XLS files with the word password in them. The results are shown in Figure 2-17.
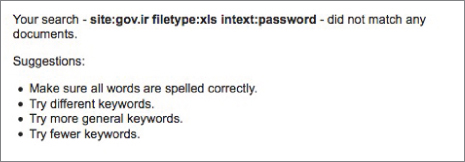
Figure 2-17 What went wrong?
Hmm, that doesn't seem right. Why would a document in an Iraqi government server have the English word password in it? Ah, but what if I use the translate.google.com site to translate the word password into Persian? Does it help? Figure 2-18 shows the result.
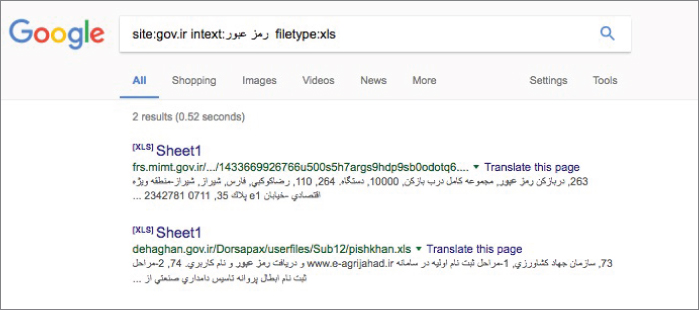
Figure 2-18 Multilingual Google searches
The power of Google is truly shown here. I didn't need to know Persian or even search in Persian. I just had to tell it to look for that word, and I was able to find documents.
Webcams: It's Time to Stop Dancing in Your Underwear
There was a boom in the desire for people to have webcams hooked up in their homes. People used them for monitoring their children, babysitters, and pets; for security; and more.
Many of these cameras were sold with default settings that left them vulnerable and wide open. Sometimes the software sold with the cameras also left a lot to be desired. Easy for the user? Yes. But also easy for attackers.
One such software was webcamXP. As indicated by its name, it was made to run on Windows XP, Vista, 7, 8, 9, 10, Server 2003, 2008, and 2012. According to its website, the software's last update was in 2016. With that in mind it should not be too popular today, so you would imagine that searching for these now would not give you too much, right?
Right?!
So, I searched for intitle:"Webcam 7" inurl:8080 -intext:8080
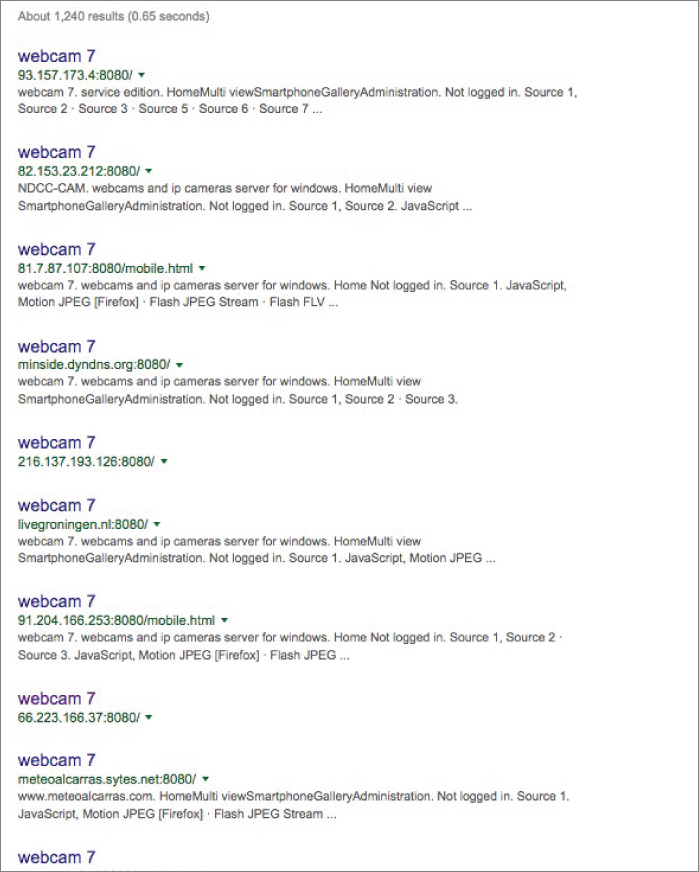
Figure 2-19 Webcams galore!
Granted, many of these webcams are intended to be online and are meant for the public to see. They're streaming traffic scenes or waterfronts and other areas. But there are people who set up webcams for personal use and leave them open in their yards or homes. The point is that if these webcams are not properly secured, any person with a little skill may be watching you, and you won’t even know.
Other Sources of Intel
Usually when I get to this point, people react with a mixture of horror and curiosity about what else you can turn up with a Google search. I don't want to list every Google search I have done, but I can tell you some of the things that I have easily uncovered using only Google searches:
- A webcam of some guy watching his marijuana plants grow
- People's private photos from their phones
- People's shared music and movie directories
- Documents containing full passwords, dates of birth, and Social Security numbers
- Thousands of credit card numbers in files
- Fully open SQL databases loaded with info
- Open access to traffic cams
- Open access to power grids and control systems
- A number of child pornography drop spots
The list can go on and on.
Two Other Things
This section alone could be its own book. But before I move on and wrap up this chapter, I would be remiss if I didn't mention two other things.
Robots Are Cool
When I was a kid, I wanted a robot so bad. I thought R2D2 would be my best friend if I could get one. In this case, I'm not talking about that type of robots. I'm referring to robots.txt
What is a robots.txtDisallowrobots.txtrobots.txtwhitehouse.gov.

Figure 2-20 That's a lot of disallowance!
Now think like a social engineer for a second. What does the file in Figure 2-20 tell you?
You can see what directories exist, but you can also see which directories they don't want you to access—or that they don't want Google to cache.
In addition, files like mysqlpgpsql
Now, if this was an actual target (which it is not—I repeat, it is not), we would go to each of those directories to make sure it was appropriately configured and not allowing us in without authorization. We would check out those logs and files, if they're accessible, to see if there was anything misconfigured in the servers.
I once did a job for a medium-sized company. It was the rare “do all you can do and see what you can find, then attack us with no gloves on” type of test. I started with a bit of OSINT and some Google searching, and I found in their robots.txtDisallowadmin
Just to check it, I typed www.company.com/admin, and to my shock, I was let in with no credentials! The directory contained the CEO's private file repository, and it appeared that he used this to share files he would need when traveling. It contained included contracts, banking data, a picture of his passport, and numerous other sensitive details.
I found a contract that had been signed within the past couple of days. I bought a domain that was one or two characters off of the real company name, set up an email for the person who signed the contract, and phished the CEO with a malicious file and an email that stated: “I am not sure if I replied with the fully signed contract, but there is a question on section 14.1a. Can you please see it inside and let me know?”
Within 15 minutes, the CEO had the email, opened it, and was compromised. He was then emailing the fake address, saying that the contract would not open, and it just kept crashing. The penetration test (aka pen test), which was supposed to take a week, was over in about three hours.
I called the CEO, and our conversation went something like this:
| CEO: | Hello |
| Me: | Hey, Paul. This is Chris over at Social-Engineer. I wanted to talk to you about the pen test… . |
| CEO: | Ha! Giving up so soon, Chris? I knew we were a hard nut to crack. |
| Me: | Well, Paul, we already have your passport, date of birth, credit cards, access to your banks, and a remote shell with admin credentials on the network. I thought I should call and see if you really want me to continue for the week? |
| CEO: | Come on! You're making this up!! It just started a couple hours ago. Tell me, who is the loser that clicked and gave shell? I want words with him. |
| Me | Well, Paul… . (I gulped hard, not sure if I could make the joke that was in my head.) I wouldn't go too harsh on him; he is a pretty cool guy. |
| CEO: | Oh yeah? Who? |
| Me: | Paul, it's you. |
I then explained every detail to him, and he realized quickly what had occurred. This particular pen test was won largely due to a robots.txt
It's All About the Meta, Baby
According to the Oxford Dictionary, meta is defined as “referring to itself or to the conventions of its genre; self-referential.” So, metadata is literally data about data. Very inception-esque, no?
Let me explain it more simply. Metadata is information about an artifact that you find in a search. Many times, that data provides some pretty interesting facts—many that might not have been put there intentionally.
Let's say I do a very benign Google search to find .docFinalPasswordPolicy

Figure 2-21 “What's-a meta you?!” (See what I did there?)
This metadata gives us the date and time it was made, the last person who saved it, the author's name/title, how many revisions the file has been through, and some other information I'm not mentioning here. You might be thinking, “So what?”
Well, just the name and the type of document that something is can be huge pieces of intel for a social engineer. Think of this: What if a social engineer were to find a new HR policy you just released? The metadata reveals when the policy was last revised (in this case, it wasn't even a month old), who wrote it, and when it was released. Of course, the policy info is in the document, too. Do you think a phishing email that seems to come from the person who wrote the policy and seemingly includes an update to the policy would get a few clicks?
Have a look at Figure 2-22.

Figure 2-22 “No, really. What's-a meta you?!”
At first, you again might be thinking, “Okay. So, are we gonna phish this guy with a coupon for hot sauce?” No. But take a look at the metadata, which is shown in Figure 2-23.
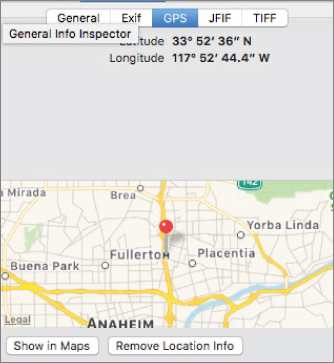
Figure 2-23 The answer is …
When you find a seemingly innocuous photo online, the metadata gives you information on the type of camera, the date, the time, and the GPS coordinates of where it was taken. When you put those coordinates into Google Maps … well, look at Figure 2-24.

Figure 2-24 That's pretty saucy, if you ask me.
The map shows the parking lot of Pepe's restaurant, which just happens to be a pretty large user of that brand of hot sauce.
So, a guy used his smartphone to take a picture. His smartphone had GPS turned on and did not block the camera app from embedding all that metadata in the back end of the photo file. When he uploaded the picture to his social media, the file contained all this information, so it was also released to the world.
Can you see the implications yet? Imagine it's not your buddy you're eating dinner with, but one of the following:
- The CEO of a large utility company who is being targeted by a nation-state attack
- The secretary of a billionaire who has information on his banks and transfer authority
- Your 15-year-old daughter taking naughty pictures of herself
Now can you see the implications? No matter which scenario you thought of, this easily accessible information gets dangerous quickly.
I worked one job with my team in which we had been tasked to perform OSINT and then attack a high-level target in the defense space. The goal was not to compromise the man, but to test his level of willingness to take an action he should not take. For educational purposes, we were to record any calls made and any click-throughs.
Light OSINT led us to his social media pages. We hit pay dirt when we found out he was a prolific tweeter, and he loved to use his brand-new iPhone with GPS turned on. Why is this so important? Twitter allowed us to graph out his location throughout the day as he tweeted from every location he went to. In a matter of a few hours, we knew the following things:
- His favorite place to stop for coffee every morning
- The gym he went to before he went home
- Two of his favorite restaurants
- His home address
- How much he hated city traffic
There was much more OSINT, but the info in the preceding list came to be crucial in our attacks. First, we found a domain that was basically one letter different from his gym's domain. We set up a quick email that told him we were updating all accounts, and his credit card info was no longer valid. We asked him to “log in to enter his credit card info now,” which prompted him to click through very quickly.
Knowing the page was going to 404 out, we waited until we saw the click, and then we called him on the phone. The conversation went something like this:
| Caller: | Hello. Is this Mr. Smith?” |
| Target: | Yes, it is. Who is this? |
| Caller: | This is Sarah over at Cold's Gym. We sent an email out earlier today about our system upgrade. Well, the email had a bad URL, so we are calling our customers to apologize. I can send you out a new link or take your credit card and update it for you. What is easier for you? |
| Target: | No problem, Sarah, here is my card number. |
| Caller: | Thank you, Mr. Smith! See you tonight! |
This attack worked because it hit topics familiar to him, and it was believable. With just a little OSINT, one phish, and one call, we had a click, a credit card number, and another five vectors prepared in case we needed them.
Metadata is powerful and very useful to a social engineer, so I suggest that you make sure to check it on every file you obtain during OSINT.
This can be daunting, especially when you're dealing with a large number of files. I personally like to use tools like FOCA (www.elevenpaths.com/labstools/foca/index.html) and Maltego (www.paterva.com/web7) to make this job easier.
Although I promised to not get too deep into any tools in this book, I feel it is imperative to at least briefly cover these and two other useful tools, which I will do in the next section.
Tools of the Trade
As I say in Chapter 1, I decided not to focus too much on tools in this book, because tools change often.
However, there are four tools that have remained in my tool chest for the last 5 to 10 years, and I felt it would be wrong of me to not even mention them. Although these tools have stayed around for a long time, they have had interface and functionality changes. If I were to spend a ton of time going through each feature, the information would be outdated by the time you get this book. Instead, I will point you to the tools' websites where you can get tutorials and keep abreast of the latest and greatest developments. I promise, this tour will be quick, but it's an essential piece of the puzzle you won't want to miss.
SET
I can remember chatting with my good friend David Kennedy. I was telling him about my desire to have a tool that allowed me to phish someone and automatically feed them a payload, grab credentials, or clone any webpage. Dave's response was, “I think I can do that.”
Not even a full 24 hours later, he had a prototype. From that moment on, Dave ran with what was called SET, or the Social Engineers Toolkit, like it was a life's mission.
He issues updates all the time—it seems like every day—and he has built-in features that make my original little ideas seem really lame. It's an amazing tool that has over two million downloads.
You can get the tool as well as instructions from www.trustedsec.com/social-engineer-toolkit.
IntelTechniques
Okay, this one is not really a “tool” per se as much as it's a collection of amazing search engines that my good friend Michael Bazzell has put together.
Michael is an expert at a few things, but there are two of them that he truly eats, breathes, and sleeps: finding people on the Internet and hiding from people who are looking for you on the Internet. Honestly, once Michael told me that to buy things from Amazon, I should set up a dummy company in Mexico, so I can get credit cards that don't tie back to me.
Michael has set up an amazing collection of tools that search everything from social media, phone numbers, IP addresses, and even reverse images. You can find these tools at https://inteltechniques.com/menu.html, and I suggest you spend some considerable time at that site.
FOCA
FOCA stands for Fingerprinting Organizations with Collected Archives. Way back at DEF CON 18 in 2010, a small group of Brazilian hackers released the tool and took the Internet by storm.
To date, there is nothing else like FOCA in the world. It's a Windows-only tool that has gone through some serious ups and downs over the years. At one point, I stopped using it because there had been no updates for some time, and there was no way to contact any person running it (and the tool wasn't open source).
Then the folks at ElevenPaths took over the project. They did an update and released it on their website at https://www.elevenpaths.com/labstools/foca/index.html. Sadly, FOCA is still Windows-only, but if you're not on Windows, it's worth setting up a virtual machine.
The speed at which FOCA grabs files and rips out useful metadata is amazing. Check it out.
Maltego: The Granddaddy of Them All
At the risk of sounding like an infomercial for Maltego, I love this tool. I really do. The folks at Paterva do something you rarely see: They make an amazing tool, release a smaller free version (that is just as amazing), and keep the commercial version updated, so it's always moving forward and very usable.
What is Maltego, you ask? It is a tool that helps you collect data from online sources and then gives you an interactive graph to display it. It can help you catalog, footprint, investigate, and make connections with public sources of intelligence.
Maltego makes my work much easier than it would otherwise be, and the tool is easy and fun to use. In addition, the guys at Paterva (the company that makes Maltego) offer amazing training videos and courses. Finally, Maltego is made for every platform.
You can check it out and download it right from the Paterva website at www.paterva.com/web7/downloads.php#tab-2. I suggest you start with Maltego Classic.
Summary
Knowledge is certainly power, and there may be no better source of knowledge of your targets than OSINT. If you follow the principles in this chapter, practice, and hone those skills you can become a master and finding even the minute details hidden all over the Internet.
You have done all the OSINT. You have cataloged, collected, and documented every piece articulately. You think you have found the piece that will be your vector, and you need to start preparing your pretext. How will analyzing the data you found and looking for key indicators about the target's communication style help? That is the topic of the next chapter.
