From Legacy to Cloud: Risks and Benefits in Software Cloud Migration
Anastasija Efremovska; Patricia Lago Vrije Universiteit Amsterdam, The Netherlands
Abstract
Various factors need to be evaluated before moving on-premise software applications to the cloud. Considerations such as scale, legal constraints, and security play a key role in rearchitecting an application in a cloud-compliant way. However, the body of knowledge on relevant migration factors is mostly neglected in practice and scattered in the scientific literature. To make this knowledge accessible, we have conducted a systematic literature review. It identifies the relevant studies that describe measures and indicators for guiding software cloud migration. This chapter presents the results of the review, which include the collected factors, namely 40 benefits, 71 risks, and 72 general measures. All factors were classified into five categories: financial, organizational, technical, legal, and security-related. In Tables 9.7, 9.8 and 9.9 we present a selection (the complete list of factors is available online at http://tinyurl.com/h6rhhp6) of all factors (3 factors per category, if the category appears in the collected benefits, risks and general measures). The analysis of factors draws observations on the most relevant benefits, risks, and measures playing a role in contemporary cloud migration. Among them, security appears not to be the biggest inhibitor to cloud migration anymore thanks to matured Service Level Agreements (SLAs). In contrast, issues like post-migration costs and the potential impact of the migration on organization staff are gaining importance. These and similar findings, along with the list of factors, can help decision makers in assessing the risks and benefits of moving a software application to the cloud. The presented factors can also be used as a base for producing a more complete list of requirements for rearchitecting preexisting software and easing their migration to the cloud.
Keywords
Risks; Benefits; Software; Cloud migrations; Legacy applications
9.1 Introduction
The cloud has quickly become a disruptive technology, especially when it comes to the way enterprises run their IT. What began as a pioneering idea of companies such as Amazon and Google, quickly started to gain in popularity among enterprises. The main reason is the tremendous potential in cost savings that can be achieved. As Nati Shalom reports in her article “Moving Enterprise Workloads to the Cloud” [15], on a massive scale the cost savings that can be achieved reach 21% if only three mission-critical applications were moved to the cloud. Another driver towards migration is the maturing of cloud technology in areas that were considered as the biggest deal-breakers for migration such as security or complexity. Different degrees of SLAs and offerings in the form of IaaS, PaaS or SaaS seem to be able to accommodate the plethora of enterprise needs. Yet, all these benefits can be achieved only if the application is suitable for the cloud. This suitability, however, is not limited to the technical characteristics of the application – as many managers still think.
The aim of this chapter is to identify and classify the various factors that influence the success of enterprise application migration to the cloud. If known, addressing these factors can guide enterprises in deciding if a selected cloud environment is right for the considered software applications. The study also helps break the myth that migration is a one-time project.
In the rest of the chapter we first discuss how the literature review was designed and conducted, followed by an overview of the classified extracted data, including general measures and indicators, risks and benefits, and models that guide the migration process. Finally, we present the findings that emerged after examining the data.
9.2 Research Method
This study is based on the systematic literature review method described in [6,8,13]. The review method comprises: defining a research question, identifying keywords and defining a search query for different libraries, data extraction, data analysis and conclusion, containing the findings of the review. The method is tested by first running a pilot study.
9.2.1 Pilot Study
The pilot study aims to evaluate and revise the research method on one digital library, in terms of completeness and rigorousness. For this aim we used Google Scholar, which is one of the most voluminous and commonly used digital libraries. The initial research question is formed based on the pilot article “Decision support tools for cloud migration in the enterprise” [12]. The initial search proved to be too general, after which we reduced the context, for example, by explicitly defining “business application” or “enterprise application” instead of “business or enterprise” and “application”. In addition, the initial search revealed synonyms that are used in the final search strings. To make sure that the protocol was implemented correctly, we consulted a similar systematic research in the SOA migration field [14].
9.2.2 Search Strategy
After the pilot study identified the needed components for a complete review and helped us refine them, the systematic literature review was conducted. The following sections describe the strategy employed by this literature review study.
9.2.2.1 Research question
The purpose of this systematic review is to extract measures, indicators and/or models that can aid companies and individuals evaluate if migrating their enterprise (legacy) software applications to the cloud is feasible, and provide guidelines. Therefore we defined the following research question:
“What measures and indicators can be used by enterprises to predict if migrating their applications to the cloud is beneficial?”
9.2.2.2 Data sources
When conducting the systematic literature review we use the following digital libraries as primary resources: Google Scholar, ACM Digital Library, CiteSeerX, and IEEE Xplore. ACM Digital Library, CiteSeerX, and IEEE Xplore are included in addition to Google Scholar to see if there are any studies that are not retrieved by querying it and these are included in the final set of retrieved studies. CiteSeerX did not return any results so it was not used further.
9.2.2.3 Search query
From the research question defined in Section 9.2.2.1, the following keywords were extracted: “measure”, “indicator”, “enterprise”, “application”, “cloud”, and “migration”. To these search terms we add the keyword “model” in order to get all the enterprise application migration models defined, as they may already incorporate measures and indicators relevant for application migration and extract them when possible. We also wanted to see if there are models that can be used as a guideline framework for migration. Furthermore, for all search terms alternative spelling and synonyms were identified. Based on the search terms and their synonyms, we defined the following query string:
(Measure OR estimate OR evaluat⁎ OR indicator OR forecasting OR predicting OR prognosis) AND (enterprise OR business) AND (application OR software) AND model AND “cloud (transition OR migration)”
9.2.2.4 Search process
The first appearance of the term “cloud computing” is commonly connected to 2006 when companies like Google and Amazon started offering the new business model to customers. Antonio Regalado at MIT Technology Review traces it back to 1996 [19]. Other authors trace the initial conception of cloud computing back to the start of ARPANet in the late 1960s [18]. In order not to overlook relevant studies, the search was not limited to a starting year of publication; rather it dates from any article published on the topic until December 15th 2014, when the search was conducted. We applied the search string to the full text of papers, excluding patents, and checked if the pilot study was retrieved. The query in the form specified in Section 9.2.2.3 was suitable for Google Scholar and IEEE Xplore (using the advanced search option for IEEE Xplore) and returned the pilot study. In the case of ACM Digital Library, the query had to be decomposed into 64 separate queries. The resulting set of articles was obtained as an intersection of the sets returned by each separate query.
9.2.2.5 Selection of primary studies
The decision on which papers to include into the set of primary studies was done based on a set of inclusion and exclusion criteria. Studies that satisfied at least one of the exclusion criteria in Table 9.1 were excluded. Studies that met all the inclusion criteria in Table 9.2 were considered as primary studies.
Table 9.1
Exclusion criteria
Exclusion criteria
E1:The study does not contain (clear) measures or indicators that help estimate the success of enterprise application cloud migration. Rationale: The measures or indicators proposed are either absent or too general and don't include concrete measures or indicators but are based on poorly supported arguments. Example: A paper is concerned with the number of enterprise applications migrated so far, whether they have failed or succeeded, but does not include relevant measures or indicator that relate to the success/failure.
E2:The study does not relate to software migration to the cloud. Rationale: 1. The findings are relevant from the business perspective but do not touch upon any technical aspects of software or application migration to the cloud; 2. The study is related to hardware migration; 3. The study has nothing to do with software migration to the cloud. Example: 1. Business risk analysis according to specific business models; 2. Live migration of virtual machines; 3. “Review and Update of Standards for Marine Equipment”.
E3:The study is focused on cloud migration of applications for private customers or end-users and cannot be related to enterprise applications. Rationale: Such studies do not contain any aspects that capture concerns of enterprise applications and may lead to incorrect predictions if used for a large company's decision-making purposes. Example: 1. End user satisfaction levels' comparison before and after moving the end-user centered application to the cloud (e.g., moving Spotify application from dedicated servers to the cloud). 2. Video sharing user application popularity measured in percent of views after the application was moved to the cloud. (Measuring the percentage of views is important for this specific application to estimate its popularity between users but this cannot be used in enterprises.)
E4:The search result is a book, not a paper. Rationale: Restricted by the duration of this research, reading a whole book that matches the query is too time-consuming. Example: [BOOK] “The CIO's Guide to Oracle Products and Solutions”.
E5:The study is developed as part of a commercial research and it includes strong bias towards the commercial company it was developed for.Rationale: Renowned cloud providers already develop models or give customers guidelines whether their cloud platforms can best suit their company needs. Such commercial research that gives realistic and unbiased results can be used for extracting reliable measures and indicators for cloud migration. If, however, they are biased towards the company and do not give realistic results, they are not useful. Example: Analogous example from the pharmaceutical industry: “Drug companies now finance most clinical research on prescription drugs, and there is mounting evidence that they often skew the research they sponsor to make their drugs look better and safer.” (http://jama.jamanetwork.com/article.aspx?articleid=182478). A hypothetical example concerning our topic would be: Amazon sponsored research on AWS skews the results for performance, network speed, etc., in order to represent it as the predominant cloud technology on the market.
E6:The study is not written in English. Rationale: Because of the multilingual composition of the peer reviewers of the study and the study feasibility, we only focus on papers written in English. Example: “TEZĂ DE DOCTORAT”.
Table 9.2
Inclusion criteria
Inclusion criteria
I1:The study proposes either concrete quantitative and/or qualitative measures and indicators or a model that can be used to evaluate the success or failure of enterprise or end-user centered application software migration to the cloud. Rationale: We want to identify quantitative and qualitative measures and indicators that can be easily reused in a general context in an enterprise environment. These measures can be used as a template with which companies can estimate the feasibility of cloud migration of their IT products or as a basis for deriving an estimation model for cloud migration feasibility. If there are models that evaluate the benefits/risks of enterprise application software migration to the cloud, they should be based on qualitative or quantitative measures. We can extract these measures from the models to build our estimation of success template. Nonenterprise (or user) application software migration strategies may include general factors and indicators that are relevant for enterprise applications, too. Example: Quantitative measures: I/O and network data-transfer latency rates, CPU clock rate, cost (amount of money); Qualitative measures: security, interoperability issues, noncompliance with regulation, etc.
I2:The study includes risk and benefit factors recorded based on concrete examples of enterprises that have migrated their applications to the cloud. Rationale: Enterprise cloud migration is an already tried concept and as such has a few valuable success and failure stories. Based on these examples, quantitative and qualitative measurements can be derived to better estimate future cases. Examples may include: the enterprise size, the application dependencies, the application type, etc. Example: Company: R&D Division of a Media Corporation; Company size: 20000 employees worldwide; Division size: 40 employees; Benefits: ease of dealing with volatile number of customers; elastic compute power provisioning (i.e., on-demand extra servers provided and discarded when not needed); Risks: security of data; cloud company being sold to third party, etc.
I3:The study is developed by researchers and practitioners. Rationale: Both academic researchers and practitioners are relevant for this study. The academic papers may give the general guidelines, while the practitioners' results could be used to prove/disprove some of the theoretical guidelines proposed by researchers.
I4:The study is peer-reviewed. Rationale: Systematic research demands strict quality of content. Papers that are published by reliable sources, such as conference proceedings, journals in the domain, scientific libraries, etc., or peer-reviewed papers can be used for guaranteeing quality and proper information structure. Example: 1. “Recent Advances on Soft Computing and Data Mining.” Springer, pp. 633–645; 2. ICN 2011, The Tenth International Conference on Networks, pp. 353–358; 3. Example of a not peer-reviewed paper would be a Master's thesis.
9.2.2.6 Included and excluded studies
From all three libraries, a total of 508 studies were found that matched the query strings (after eliminating multiple copies of the same studies found in more than one library). Table 9.3 provides an overview of the exact number and the percentage of studies found (hits) per digital library. Out of the 508 studies, 367 were eliminated based on reading the title, 99 based on the abstract, and 7 based on the full text. From the 28 studies left, which were taken as primary studies, 12 that contained general measures or models not connected to migrating only one part of an application (such as data, for example) were included in the study. The rest of the articles were not further considered. This decision was made in order to get an overall impression of factors that play a role in migrating any type of application. Studies that were a short version of a more detailed paper published at a later stage were combined in order not to bias the research results with the same model or measures appearing twice. Studies published by the same authors but with complementing findings were included. There was one example of the latter.
Table 9.3
Distribution of studies found in digital libraries
| Digital library | Number of studies | Percent (%) |
| Google scholar | 405 | 80% |
| IEEE Xplore | 59 | 12% |
| ACM digital library | 44 | 8% |
9.2.2.7 Search result management
For keeping track of the studies and their reference information we used the Zotero [20] desktop application as well as the browser add-on for Google Chrome. Zotero allows downloading the studies, if they are publicly available, and saving their reference information at the same time. For each digital library, a different Zotero folder was created. Exporting the reference information in a JabRef [21] database format is also possible.
9.2.2.8 Quality assessment of primary studies
The quality of the selected studies was measured according to six general quality criteria that should be satisfied for every well-written study and seven quality criteria that evaluate a study that deals with application cloud migration (see Table 9.4). The quality criteria were taken from the example quality criteria listed in [22] and adapted to fit the purposes of this review. The quality criteria evaluation is done in addition to the inclusion/exclusion criteria and serves as an internal metric. For each criterion, the studies were additionally scored on three levels: completely satisfies the criterion (1 point), partially satisfies the criterion (0.5 points), and does not satisfy the criterion (0 points). A study that completely satisfies a criterion has all the elements of that criterion present, and they are clearly described and defined. A study that has only a few elements of the criterion or that is not clearly defined is partially satisfied (e.g., statistical methods used for data aggregation are only listed but not described). Total absence of a criterion' elements (e.g., no data collection method described or defined) means that a particular criterion is not satisfied, resulting in a 0 points score. At the end the total score for the quality of a study was calculated as an average score of the applicable criteria. An average score of 0.7 or above represents high quality papers, a score between 0.3 and 0.7 represents papers of acceptable quality, whereas a score of 0.3 or below excludes the papers.
Table 9.4
Quality criteria
| Title | ||
| Author | ||
| ID | General quality criteria (G) | Score |
| G1 | Are the aims and objectives, as well as the motivation, of the study clearly described? | |
| G2 | Is the context in which the study was carried out adequately defined? | |
| G3 | Are the research methodology and its organization clearly stated? | |
| G4 | Is the reporting clear and coherent? | |
| G5 | Does the study provide clearly stated findings with credible results and justified conclusions? | |
| G6 | Do the findings answer the study question(s)? | |
| Specific quality criteria (S) | ||
| S1 | Have the identified measures and indicators or model for enterprise application cloud migration evaluated on a real world case study? | |
| S2 | If the research paper has a case study company is the size of the company and the choice of it presented and argumentatively supported? | |
| S3 | Are the quantitative measures and indicators identified in the study adequately measured? (Example database size, CPU clock rate, etc.) | |
| S4 | Are the data collection methods described? | |
| S5 | Are the qualitative measures (if any) clearly explained? | |
| S6 | If any statistical models were used in summarizing the results, are they explained and justified? | |
| S7 | Are the identified benefits and risks for enterprise cloud migration diverse (i.e., technical, legal, organizational, financial risks and benefits, etc.)? | |
9.2.3 Data Extraction
The data extraction from each of the primary studies was facilitated by the data extraction form given in Table 9.5. For each study we recorded the identified measures or indicators, benefits, risks, and models.
Table 9.5
Data extraction form
| Field | Description | |
| 1 | Study identifier | [A unique ID of the article in the set of all collected articles.] |
| 2 | Title | [Title of the study.] |
| 3 | Authors | [Authors of the study.] |
| 4 | Data source | [The name of the digital library in which the article was found (e.g., IEEE Xplore, Google Scholar, ACM Digital Library, etc.).] |
| 5 | Type of the article | [The type of the article (e.g., conference paper, journal article, book chapter, etc.).] |
| 6 | Measures or indicator identified | [For each measure or indicator identified, list all the characteristics of it (a, b, c, and d). If there are other characteristics mentioned list them too under e. |
| a) Name | a) Name of the measure; | |
| b) Type | b) Is it a qualitative or quantitative measure; | |
| c) Measuring unit (if quantitative) | c) Measuring unit (e.g., money unit or speed unit); | |
| d) Group | d) Hardware type of measure, Economical type of measure, etc.; | |
| e) Textual description | e) A short description of the measure; | |
| f) Other | f) Other characteristics not mentioned in a–d.] | |
| 7 | Model based on the measures (if any) | [Describe the models that are constructed from the measures or identifiers for supporting enterprise application cloud migration success evaluation.] |
| 8 | Risks and benefits identified | [List all the risks and benefits identified from the measures and case studies in general, for each list the specifics (a and b). If there are other characteristics list them too in c. |
| a) Description | a) Name of the risk or benefit, or a sentence that describes it; | |
| b) Type | b) Risk or a benefit; | |
| c) Group | c) Group of the risk or benefit: financial, legal, technical or other type of risk; | |
| d) Other | d) Other characteristics that may be important but are not mentioned.] | |
| 9 | Type of company and the application in the case study (if any) | [List the size of the case study company and the enterprise application on which the model or measures were tested, e.g., SME or Large company division and a web application.] |
| 10 | Study findings | [Describe the study findings for each of the case studies in which they were applied.] |
| 11 | Conclusions | [What is the study conclusion(s).] |
Many of the primary studies that were examined did not have the data we needed explicitly shown in the form it was expected in the data extraction form, such as benefits or risks. Therefore extra work was needed to extract or identify these types of measures. Many of the studies included implicit measures that aid migration in the models or frameworks they described, which required even deeper analysis.
9.2.4 Data Analysis Method
The aim of this review is to identify and categorize different factors that can aid companies evaluate if migrating their legacy application to the cloud is beneficial. In order to achieve this, a method of analyzing the studies was needed. Given that most of the measures we found are qualitative, manual analysis and synthesis was inevitable.
We differentiate benefits and risks as a special kind of factors because they represent an explicit indicator of the possible gains or losses of a migration approach. In this work we use the following definitions of benefits and risks: a benefit is an advantage or profit gained from migrating an (enterprise) application to the cloud, whereas a risk is an undesirable event that may happen if you migrate your application to the cloud. These measures are typically qualitative in nature. Therefore they do not have any measuring units specified and are characterized only by category.
The risks and benefits categories identified in the pilot study [12] were used as classification categories of all types of measures (including identified benefits and risks), which include the following: financial, technical, organizational, legal, and security. The studies that categorized their measures either had the same or similar categories or had a more fine-grained technical category. Technical subcategories were translated simply into technical as we were interested in the type of the categorization of measures rather than their subcategories. The description of a measure, if identified in multiple studies, was taken from the one that had the most descriptive name or best explanation. If a measure in a study did not specify any category, the most logical category of the set of starting categories identified was chosen. When we encountered a specific category that was not present in the list of categories, it was replaced with the most logical one.
The found measures and indicators are summarized in a tabular form, augmented with the corresponding narrative description. The description is taken from the source articles, unchanged (if it was present) or reported as a combination of the definitions (if found in multiple articles). A mapping of the measures in one study to the same or similar measures found in other studies was reported in these tables.
The models found in the studies were also evaluated and compared by looking at the proposed steps and the stage of the migration they cover. An evaluation of models for cloud migration is given in [7], which presents a descriptive summary of models/frameworks of migration and an evaluation of their missing features. However, our analysis of the models is not based on model completeness – as [7] suggest – but on the perspective they consider for migration and when a certain perspective starts to appear or becomes predominant.
9.3 Results
The analysis of the primary studies identified a set of factors, both general and related to risks and benefits, as well as many models or frameworks designed especially for application migration to the cloud. The analysis also revealed the gaps and quality of the studies. In the next two sections we present an overview of the included studies and their quality, followed by the identified measures and models. While Tables 9.7, 9.8 and 9.9 present only a selection of the identified factors (3 factors for each subcategory), the complete list of factors is also available online at http://tinyurl.com/h6rhhp6.
9.3.1 Overview of Primary Studies and Quality Evaluation
An interesting fact found when analyzing the included studies is that 3 out of the 12 studies (also quite detailed and high in quality) share a coauthor, Khajeh-Hosseini (Table 9.6). Most of the primary studies are from 2012 and 2013, whereas the earliest study dates from 2010.
Table 9.6
Overview of included studies
| Study | Year |
| Khajeh-Hosseini et al. [11] | 2010 |
| Varia [16] | 2010 |
| Khajeh-Hosseini et al. [12] | 2011 |
| Banerjee [4] | 2012 |
| Beserra et al. [5] | 2012 |
| Khajeh-Hosseini et al. [10] | 2012 |
| Vu and Asal [17] | 2012 |
| Aggarwal et al. [1] | 2013 |
| Alonso et al. [2] | 2013 |
| Azarnik et al. [3] | 2013 |
| Erfan [9] | 2013 |
From the 12 initially selected articles, one more was eliminated and further used as a reference. Namely, the article “A Survey of Cloud Computing Migration Issues and Frameworks” [7] is a summary of the quality and completeness of 11 models or frameworks for application migration. The article includes a summary of models that were not evaluated by the authors themselves but were taken from other articles and analyzed as defined or were not available. Therefore we used this article exclusively as an example for evaluating other models found in the rest of the primary studies. Three of the models identified in [7] were also found in separate studies and were used to extract measures and indicators from their original articles.
Two articles [2] and [10] do not report on any benefits or risks identified and because of that do not completely satisfy inclusion criterion 2. However, these articles have very detailed models and general measures which have been evaluated on real-world case studies. Therefore, they were included as primary studies.
A shortcoming in most of the articles is that their findings were not evaluated on real-world case studies (or case studies that mimic real applications in general). There were six such articles, and one in particular, even though it states that it is based on the migration of applications in the Iranian telecommunications industry [9], does not specify any details of the company, staff size and composition or characteristics of the migrated applications. Eight of the included studies presented models or frameworks for migration. As can be seen in Fig. 9.1, the average quality of the studies is around 0.8, based on the quality criteria point system (see Section 9.2.2.8).

9.3.2 Benefits and Risks
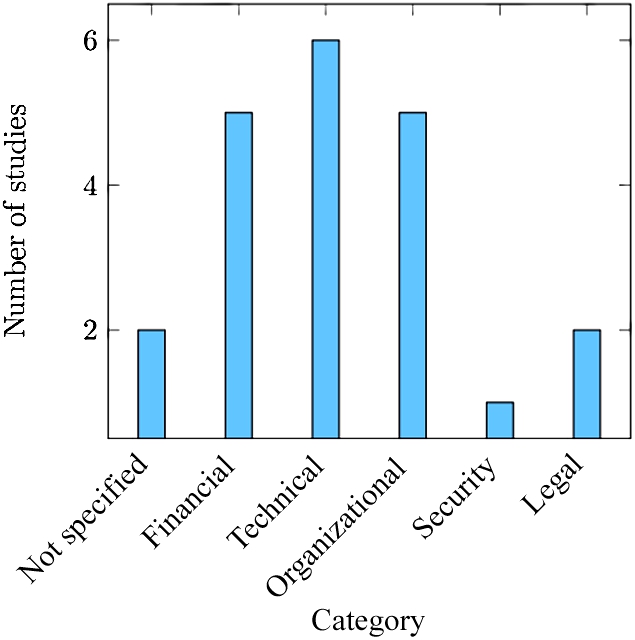
Benefits and risks, as a special type of qualitative measures, are classified according to the five categories defined in Section 9.2.4. Five of the studies that were chosen did not have a category specified for their risks and benefits. Not defining a category for the risks and benefits is more common than in the case of general measures. The reason for this may be the opinion of authors that specifying something as a risk or benefit is self-sufficient and does not need any other classification information.
Beserra et al. [5] have much more detailed technical subcategories for the risks and benefits such as communication, performance, availability, and suitability, which can be useful if the accent is put on the technical aspects of migration.
Especially interesting categorizations were given by Azarnik et al. [3], who use cost category in the equivalent sense as the financial category. One particularly interesting category of risks they identify is the outsourcing opportunism risk (see Table 9.8), which takes into account the risks that may emerge from using cloud providers without (clearly defined) SLAs. If a risk or benefit does not fit any of the four previously mentioned categories, they simply categorize it as other.
In general, many of the articles had specific subcategories defined for the categories we use. The list of subcategories for the technical benefits and risks category include: communication, availability, suitability, performance, operational, and agility. In contrast, Azarnik et al. [3] also use super categories for some of the classification categories. Such is the outsourcing opportunism risk category, which integrates the technical, legal, and organizational categories. The distribution of our categories in the studies is given in Fig. 9.2.

Besides the defined super- and subcategories for measures, the following category synonyms were encountered: cost or economic for the financial category, operational or functionality as technical subcategories, and political as a synonym for organizational. Selected lists of benefits and risks, along with their original and assigned classification categories, can be found in Tables 9.7 and 9.8, respectively.
Table 9.7
Benefits
| ID | Classification category |
Source category |
Benefit |
| 1 | Technical | Technical [12] | Fast access to additional computational resources and specialized skills (e.g., IT specialists who build and maintain clouds). Results in quicker system deployment times. |
| 4 | Technical | Technical [12] | Anywhere/anytime/any device (desktop, laptop, mobile, etc.) access to computational resources and applications can be setup without too much effort. This in turn simplifies collaboration amongst users and simplifies application support and maintenance. |
| 5 | Technical | Technical [12]; Not specified [9] | Increased system security due to more investment into security by cloud providers (e.g., specialized security teams, greater resilience, protection against network attacks, and quicker disaster recovery procedures). |
| 18 | Financial | Financial [5,12] | Reduced costs due to more efficient operations and less infrastructure maintenance costs but also due to economies of scale that can be achieved by cloud providers. |
| 19 | Financial | Financial [12]; Unknown [9]; Other [3] | Reduced energy consumption, leads to greener organizations. |
| 26 | Financial | Cost [3] | Lower cost of entry as cloud computing does not require heavy investment in physical infrastructure. |
| 28 | Organizational | Organizational [12]; Agility [3] | Ability to focus on core business activities and free-up management and IT personnel from mundane tasks (such as hardware support activities) so that they can focus on value-added activities. |
| 30 | Organizational | Organizational [12]; Other [3]; Not specified [4] | Opportunity to offer new products or services or trial products to gauge the level of interest from customers. |
| 32 | Organizational | Organizational [12] | Reduced risks of technological obsolescence as cloud providers update the infrastructure. |
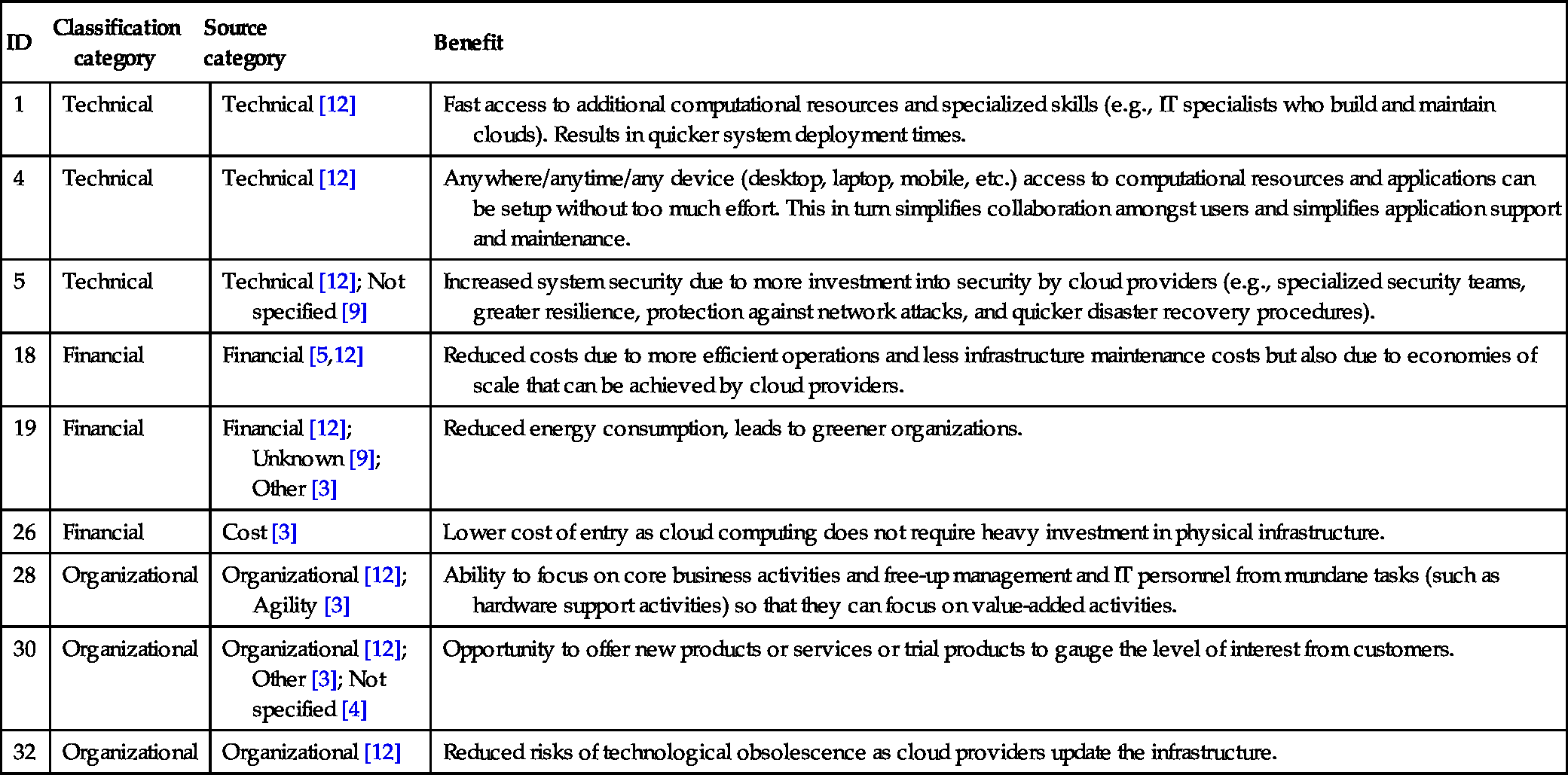
Table 9.8
Risks
| ID | Classification category |
Source category |
Risk |
| 9 | Technical | Application [5] | Application users are located in a region with unreliable Internet connection, which may affect their capacity to communicate reliably with application components deployed on remote cloud servers. |
| 13 | Technical | Not specified [17] | Applications processing data streams. Cloud providers rarely support data streams as it can drastically increase costs because of data-intensive remote/intra-cloud communication. |
| 21 | Technical | Technical [12]; Outsourcing opportunism risks [3] | Data lock-in for SaaS/PaaS and system lock-in for IaaS. |
| 29 | Financial | Financial [5] | Cost to operate the application after migration to the cloud. |
| 31 | Financial | Financial [12] | Actual costs may be different from estimates, this can be caused by inaccurate resource estimates, cloud providers changing their prices, or inferior performance (e.g., due to over-utilized servers) resulting in the need for more computation resources than expected. |
| 33 | Financial | Financial [12] | Increased costs due to complex system integration problems between existing systems and cloud-based systems. Inability to reduce costs due to unrealizable reductions in the number of system support staff (e.g., due to their knowledge of existing systems). |
| 34 | Organizational | Organizational [12] | Private data being exposed due to a change of responsibility for users who have a lack of awareness about where to put different types of data. |
| 35 | Organizational | Organizational [12] | Mismatch between existing incident handling procedures and cloud providers' procedures. Lack of information or no access to a cloud's vulnerability information or incident report data. Leads to limited responses from an organization in case of incidents. |
| 37 | Organizational | Not specified [11] | Decrease in satisfaction – Support engineers risk decreasing job satisfaction as work may shift from a hands-on technical role to reporting and chasing up issues with third party service providers. Sales and marketing staff risk of decreasing job satisfaction if they are set unrealistic goals regarding the selling of the new cloud based services. Customer care staff also risk decreasing job satisfaction because their ability to perform their job will be dependent upon third parties out of their control resulting in a greater lag between customer queries and resolution. |
| 54 | Legal | Legal [12]; Suitability [5] | Unusable software license on the cloud due to the license using traditional per-seat or per-CPU licensing agreements, etc. |
| 56 | Legal | Not specified [17] | Applications contain sensitive or important data that cannot be exported to outside the organization or outside the country where the organization is situated. |
| 65 | Legal | Legal [12] | Private data stored on the cloud can be accessed by foreign governments due to differences in jurisdictions. |
| 66 | Security | Security [12] | Denial of service attacks. Leads to unavailability of resources and increases cloud usage bills. |
| 67 | Security | Security [5] | Level of encryption implemented by the provider for communication both within and outside the cloud infrastructure. |
| 70 | Security | Security [12] | Insecure or ineffective deletion of data when scaling down resource usage or when changing providers. |

9.3.3 General Measures
General measures and indicators are those measures that, depending on the values they take and the context in which they are measured, can be seen either as benefits or risks in the process of migration. Without their values, it is difficult to say if they describe an upside or downside of migration. For example, let us consider network bandwidth as a measure. Low bandwidth values are a hindering factor towards the migration decision, if we want to migrate an application that has large bandwidth demands. If the bandwidth values are high enough for the application needs, then bandwidth is a beneficial factor towards migration.
The measures and indicators in the studies were less frequently explicitly listed as measures compared to the risks and benefits. Yet, the classification of measure and indicators was much more easily extracted and more often explicitly specified. There is also a bigger overlap in identified measures and indicators across the studies compared to risks and benefits.
There is an overlap in some of the risks and benefits and the general measures identified. A typical example would be the “bandwidth” general measure which prescribes examining the bandwidth available in the cloud and if it is sufficient for the concrete application. The equivalent risk is “low bandwidth”, which describes the unwanted effects of migration if bandwidth was not taken into account.
The classification of general measures is similar to the risks and benefits across the papers (Table 9.9). The technical category had the most subcategories: operational, computational, application-usage characteristics,1 application-technical characteristics,2 application and monitoring, user management and security, IaaS, PaaS, monitoring, and multitenancy. The financial category has only one subcategory – billing, whereas organizational has the migration strategy characteristics, provisioning, user interaction, and SLA subcategories. Beserra et al. [5] use the cloud provider characteristics super category which includes the security, organizational, financial, and technical categories. Alonso et al. [2], on the other hand, use the business supercategory to classify measures in the financial, organizational, and legal categories. An overview of the general measures and their original categories is shown in Table 9.9, and the categorization across studies is presented in Fig. 9.3.
Table 9.9
General measures and indicators
| ID | Classification category |
Source category |
Measure/indicator |
| 1 | Financial | Economical [1] | Existing investments in IT – For migrating into the cloud, Small and Medium Enterprises (SMEs) are at an advantage over large organizations because they have a limited installed IT base. They may be able to directly move into the cloud. In comparison large organizations huge investments and complexity of hardware, network, application support, administration, customization and integration make it difficult for them to migrate to cloud easily. |
| 6 | Financial | Business [2] | Type of elements for billing. |
| 7 | Financial | Cloud provider characteristic [5] | Cost and price models for the resources – What are the costs and price models (e.g., per hour on demand, per hour reserved, market bidding) for each type of resource. |
| 8 | Security | Technical [1,10] | Data security – Organizations resist sending sensitive applications and confidential information behind the corporate firewall. Data with greater security tolerance however could be ported onto the cloud. Security of data is still the top most inhibiter of cloud adoption. |
| 9 | Security | Technical [4,10]; Cloud provider characteristic [5] | Security mechanisms offered by provider – What are the security mechanisms put in place by the provider? |
| 10 | Legal | Organizational [1]; Business [2]; Technical [10] | Regulations – Geopolitical issues especially for Governments and financial institutions should be carefully evaluated before making the transition to the cloud. In the Indian context this is especially relevant as most cloud data centers are not located within the country. It is also important to ensure that local regulations relevant to each organization should be adhered to before deciding to move to the cloud. |
| 11 | Legal | Business [2]; Organizational [5] | Fulfilment of data privacy laws |
| 12 | Organizational | Technical [1]; Organizational [5] | IT skills – Migration to cloud requires IT team with updated skills like virtualization, Web 2.0, etc. These types of challenges need to be addressed prior to deciding the migration to the cloud. |
| 13 | Organizational | Organizational [1]; Technical [2,10]; Cloud provider characteristic [5] | Service Level Agreements (SLAs) – Another key aspect to consider before migrating to the cloud is whether cloud service providers are able to provide SLAs that the business needs. It should clearly outline service provider responsibilities and penalties for failure to meet agreed service levels. |
| 15 | Organizational | Business [2] | More than one business model. |
| 41 | Technical | Technical [1]; Application and programming [2]; Application, technical characteristic [5]; Not specified [16] | Architecture and architecture complexity – Simple applications can be easily migrated to the cloud and the amount of effort required moving such applications may not be not too significant. Migration of complex applications however, needs elaborate planning and testing prior to implementation. Legacy applications and existing enterprise applications could require code changes to work on the cloud. |
| 47 | Technical | Technical [2,4,10]; Application, technical characteristic [5] | Specific or minimal hardware needs – What is the minimum or specific hardware configuration necessary to run the application? |
| 57 | Technical | Application, usage characteristic [5] | Number of users and users' location – How many users access the application and from which locations? |

9.3.4 Models and Frameworks for Cloud Migration
The analysis of the models and frameworks of migration revealed four distinct types of models, based on the extent to which they cover the migration process:
• Type 1: Models that focus only on one aspect of migration
This is the simplest type of model found, and can be seen more as guidelines. Examples are the Cost modeling framework [12] that deals with the financial infrastructure costs and the Informal migration feasibility assessment framework [11] that deals with the organizational impact of migration.
• Type 2: Models that support migration decision making from multiple perspectives
These models can be seen as an extension of the type 1 models, which take the diverse nature of factors of migration into account. The factors match the categorization of measures and indicators and comprise of technical, organizational, financial, etc., feasibility assessment. For instance, the Cloud Adoption Toolkit [10] includes the Cost Modeling framework [12] and augments it with technical feasibility, energy consumption, stakeholder and responsibility analysis. Another example of this type of model is the ARTIST cloud modernization framework [2], which in the analyzed study only describes the premigration phase. The full ARTIST framework can be seen as type 4 model, but the paper that describes it only presents the internal tools working rather than the migration and evaluation phases.
• Type 3: Incremental migration support models
The incremental migration support model type can be seen as composed of three general stages: premigration, migration and validation/testing. In the premigration stage the technical characteristics and requirements of the application are determined and profiles of the cloud providers are made. The application characteristics are compared to the profiles and the most suitable one is chosen. The migration phase encompasses the actual moving of the application and data, which is done in two separate steps: either first migrating the application then the data or vice versa. In the validation phase performance tests and optimization of the cloud environment are done. The following frameworks can be classified as type 3 migration models: AWS cloud migration framework [16], The five step methodology to cloud migration [4], and the Incremental data-application cloud migration model [1].
• Type 4: Multiple perspective integration migration support models
The type 4 models can be seen as a synthesis of the type 2 and type 3 models. This model explores the multiple perspectives of migration in the pre-migration stage as described in the type 3 model. A representative example is the Cloudstep [5] model.
9.4 Discussion
In the following we extract the main findings and lessons learned, followed by the threats to validity that should be kept in mind in the interpretation of the results.
9.4.1 Findings and Lessons Learned
• The shortage of migration specialist to perform the migration increases.
The analysis of measures and indicators revealed a comparable number of organizational and technical risks. One of the risks gaining importance over time is the need of migration specialists in the staff to both perform the migration and be able to monitor the life cycle of the application once it is migrated. This risk was first mentioned in 2010 in the works of [11]. After that it gained popularity from 2013. This risk is important to be pointed out as it defies the belief, common at the time, that outsourcing an application to the cloud is sufficient and does not require further effort.
• Employees' resistance to migration is a prominent organizational obstacle towards migration to the cloud.
Another prominent organizational obstacle is the staff's resistance to migration, motivated by fear of losing their job. As a result, possible risks include loss of valuable and experienced engineers and a decrease in the productivity and morale of the rest of the staff. This risk also appears as early as 2010 and has been the most often identified risk.
• Legal restrictions on data location may prohibit migration.
From a legal standpoint, migration is most often not possible because of the strict requirements of data location. Namely, many countries' laws require that private and sensitive data of the country and their citizens be kept within the country borders. As cloud providers expand and open more data centers, this risk is slowly, but certainly starting to disappear, at least for the larger Western countries. The appearance of this risk is evident in 2011 and 2012 and slowly disappears in 2013, just to be replaced with the general measure of the type of SLA offered by the cloud providers. The reason lies in the fact that nowadays cloud providers offer the option of keeping certain types of data within country borders and guarantee it through their SLAs. This trend explains the low number of legal risks and measures identified in the studies.
• Better SLAs offered by cloud providers eliminate many security risks.
The low amount of security risks can also be explained by the more detailed SLAs offered by cloud providers. Risks such as interception of infrastructure management messages in transit or private data accesses by other customers sharing the same infrastructure are explicitly engineered against by cloud providers and guaranteed in the SLAs they offer. Risks such as Denial of Service attacks cannot be avoided by cloud providers and can happen even if the application does not reside in the cloud.
• Nowadays software license migration is done along with the migration of software.
Another advancement, which is visible from the cloud providers' side, is the offering of easy migration of software licenses alongside the application. Cloud providers in cooperation with third party software suppliers offer cloud licenses for a small additional fee for the most commonly used support services, such as Oracle database. So if a company already has a license for a software product, it can easily move to the cloud by extending its existing license.
• Green computing is an important additional benefit of the migration to the cloud.
An important benefit emerging from the literature is green computing, which authors relate to energy savings. In [12], the authors enlist, among the additional resources for their study, reduced energy consumption as a benefit that leads to greener organizations. Erfan goes a step further by characterizing cloud computing as a “green IT tool for the 21st century” [9, p. 4], [3, p. 5] identify green computing as a benefit of cloud computing because cloud providers, according to them, are better at managing voltage conversions and cooling as compared to on-premise computing centers, and consequently are more energy-efficient. Furthermore, because cloud providers use virtualization of their servers, they reach better resource utilization that leads to lower energy consumption. Azarnik et al. [3] also believe that businesses today care more about the environment and run companies in a greener way, therefore it is plausible that in the near future they will turn to using cloud computing because of its (promised) green benefits.
• Migration models vary in the focus and detail of the migration phases.
As far as the different types of model are concerned, we could not spot any trend across different years. This may be a result of the relatively small number of primary studies. Apparently the depth in which cloud migration is considered in these models is diverse and models of all types are equally appearing in 2010, 2013, and 2014. Our suggestion, based on the primary studies, is to turn the focus to technical, financial, and organizational factors when considering cloud migration. Special care should be taken when calculating the postmigration costs from the financial aspect and the staff impact the migration may have from organizational aspect. A detailed SLA can eliminate the majority of legal and organizational risks and as such is a mandatory ingredient of any migration process. If a migration model or framework is to be used, in the initial phase (considering whether to migrate or not) models of type 1 and 2 are more suitable. When planning the migration itself, however, models of type 4 are preferable as they cover all migration phases.
9.4.2 Threats to Validity
Even though this review was performed based on the systematic literature review guidelines provided in scientific literature (Section 9.2), there may still be some threats to its validity. In particular, the following threat to validity was identified: most studies do not have the same classification of measures and indicators or have no explicit classification at all. Therefore most of the classification done in this paper is done based on the context in which the measures are mentioned. The classification is naturally influenced by the specific context reported in the primary study. However, the authors could have defined the measures/indicators for more generic applications.
9.5 Conclusion
This study shows that cloud migration factors and models for software applications haven't matured, yet. However, the literature shows clear signs of the increased need for these techniques.
Multiple factors need to be considered when migrating to the cloud, which include financial, legal, security, organizational, and technical risks and benefits, as well as general measures. The field of cloud computing is maturing, and SLA offerings eliminate most security and legal concerns that were noticeable in previous years. However, these risks may still appear depending on the chosen cloud provider or the legal constraints that concern its geographical location. Migration that was once considered a one-time task has now become a long term project. This impacts the organization in multiple aspects in terms of needed technology and knowledge, financial considerations and the effect the potential migration may have on the employees.
There are four types of model for migration that either deal with the initial stage of migration and consider only one or a few aspects, or are designed to guide the whole migration, from the planning phase to postmigration management.
