An Ethernet bridge consists of two or more interfaces configured to forward Ethernet frames transparently, and which are not directly visible to the upper layers, such as the TCP/IP stack. In a filtering context, the bridge configuration is often considered attractive because it means that the filtering can be performed on a machine that does not have its own IP addresses. If the machine in question runs OpenBSD or a similarly capable operating system, it can still filter and redirect traffic.
The main advantage of such a setup is that attacking the firewall itself is more difficult.[28] The disadvantage is that all admin tasks must be performed at the firewall’s console, unless you configure a network interface that is reachable via a secured network of some kind, or even a serial console. It also follows that bridges with no IP address configured cannot be set as the gateway for a network and cannot run any services on the bridged interfaces. Rather, you can think of a bridge as an intelligent bulge on the network cable, which can filter and redirect.
A few general caveats apply to using firewalls implemented as bridges:
The interfaces are placed in promiscuous mode, which means that they will receive (and to some extent process) every packet on the network.
Bridges operate on the Ethernet level and, by default, forward all types of packets, not just TCP/IP.
The lack of IP addresses on the interfaces makes some of the more effective redundancy features, such as CARP, unavailable.
The method for configuring bridges differs in some details among operating systems. The following examples are very basic and do not cover all possible wrinkles, but should be enough to get you started.
The OpenBSD GENERIC kernel contains all the necessary code to configure bridges and filter on them. Unless you have compiled a custom kernel without the bridge code, the setup is quite straightforward.
Note
On OpenBSD 4.7 and newer, the brconfig command no longer exists. All bridge configuration and related functionality was merged into ifconfig for the OpenBSD 4.7 release.
To set up a bridge with two interfaces on the command line, you first create the bridge device. The first device of a kind is conventionally given the sequence number 0, so we create the bridge0 device with the following command:
$ sudo ifconfig bridge0 createBefore the next ifconfig command (brconfig on OpenBSD 4.6 and earlier), use ifconfig to check that the prospective member interfaces (in our case, ep0 and ep1) are up, but not assigned IP addresses. Next, configure the bridge by entering the following:
$ sudo ifconfig bridge0 add ep0 add ep1 blocknonip ep0 blocknonip ep1 upOn OpenBSD 4.6 and earlier, enter this:
$ sudo brconfig bridge0 add ep0 add ep1 blocknonip ep0 blocknonip ep1 upThe OpenBSD ifconfig command (brconfig on OpenBSD 4.6 and earlier) contains a fair bit of filtering code itself. In this example, we use the blocknonip option for each interface to block all non-IP traffic.
Note
The OpenBSD ifconfig command offers its own set of filtering options in addition to other configuration options. The bridge(4) and ifconfig(8) man pages provide further information. Since it operates on the Ethernet level, it is possible to use ifconfig to specify filtering rules that let the bridge filter on MAC addresses. Using these filtering capabilities, it is also possible to let the bridge tag packets for further processing in your PF rule set via the tagged keyword. For tagging purposes, a bridge with one member interface will do. This functionality and the keywords were also present in brconfig(4) on OpenBSD 4.6 and earlier.
To make the configuration permanent, create or edit /etc/hostname.ep0 and enter the following line:
up
For the other interface, /etc/hostname.ep1 should contain the same line:
up
Finally, enter the bridge setup in /etc/hostname.bridge0 (/etc/bridgename.bridge0 on OpenBSD 4.6 and earlier):
add ep0 add ep1 blocknonip ep0 blocknonip ep1 up
Your bridge should now be up, and you can go on to create the PF filter rules.
For FreeBSD, the procedure is a little more involved than on OpenBSD. In order to be able to use bridging, your running kernel must include the if_bridge module. The default kernel configurations build this module, so under ordinary circumstances, you can go directly to creating the interface. To compile the bridge device into the kernel, add the following line in the kernel configuration file:
device if_bridge
You can also load the device at boot time by putting the following line in the /etc/loader.conf file.
if_bridge_load="YES"
Create the bridge by entering this:
$ sudo ifconfig bridge0 createCreating the bridge0 interface also creates a set of bridge-related sysctl values:
$ sudo sysctl net.link.bridge
net.link.bridge.ipfw: 0
net.link.bridge.pfil_member: 1
net.link.bridge.pfil_bridge: 1
net.link.bridge.ipfw_arp: 0
net.link.bridge.pfil_onlyip: 1It is worth checking that these sysctl values are available. If they are, it is confirmation that the bridge has been enabled. If they are not, go back and see what went wrong and why.
Note
These values apply to filtering on the bridge interface itself. You do not need to touch them, since IP-level filtering on the member interfaces (the ends of the pipe) is enabled by default.
Before the next ifconfig command, check that the prospective member interfaces (in our case, ep0 and ep1) are up but have not been assigned IP addresses, and then configure the bridge by entering this:
$ sudo ifconfig bridge0 addm ep0 addm ep1 upTo make the configuration permanent, add the following lines to /etc/rc.conf:
ifconfig_ep0="up" ifconfig_ep1="up" cloned_interfaces="bridge0" ifconfig_bridge0="addm ep0 addm ep1 up"
This means your bridge is up, and you can go on to creating the PF filter rules. See the if_bridge(4) man page for further FreeBSD-specific bridge information.
On NetBSD, the default kernel configuration does not have the filtering bridge support compiled in. You need to compile a custom kernel with the following option added to the kernel configuration file. Once you have the new kernel with the bridge code in place, the setup is straightforward.
options BRIDGE_IPF # bridge uses IP/IPv6 pfil hooks too
To create a bridge with two interfaces on the command line, first create the bridge0 device:
$ sudo ifconfig bridge0 createBefore the next brconfig command, use ifconfig to check that the prospective member interfaces (in our case, ep0 and ep1) are up but have not been assigned IP addresses. Then configure the bridge by entering this:
$ sudo brconfig bridge0 add ep0 add ep1 upNext, enable the filtering on the bridge0 device:
$ sudo brconfig bridge0 ipfTo make the configuration permanent, create or edit /etc/ifconfig.ep0 and enter the following line.
up
For the other interface, /etc/ifconfig.ep1 should contain the same line:
up
Finally, enter the bridge setup in /etc/ifconfig.bridge0:
create !add ep0 add ep1 up
Your bridge should now be up, and you can go on to create the PF filter rules. For further information, see the PF on NetBSD documentation at http://www.netbsd.org/Documentation/network/pf.html.
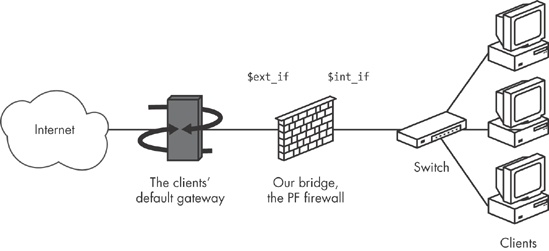
Here is the pf.conf file for a bulge-in-the-wire version of the baseline rule set we started with in this chapter. The network changes slightly, as shown in Figure 5-3.
The machines in the local network share a common default gateway, which is not the bridge, but could be placed either inside or outside the bridge.
ext_if = ep0
int_if = ep1
localnet= "192.0.2.0/24"
webserver = "192.0.2.227"
webports = "{ http, https }"
emailserver = "192.0.2.225"
email = "{ smtp, pop3, imap, imap3, imaps, pop3s }"
nameservers = "{ 192.0.2.221, 192.0.2.223 }"
client_out = "{ ssh, domain, pop3, auth, nntp, http, https,
446, cvspserver, 2628, 5999, 8000, 8080 }"
udp_services = "{ domain, ntp }"
icmp_types = "{ echoreq, unreach }"
set skip on $int_if
block all
pass quick on $ext_if inet proto { tcp, udp } from $localnet
to port $udp_services
pass log on $ext_if inet proto icmp all icmp-type $icmp_types
pass on $ext_if inet proto tcp from $localnet to port $client_out
pass on $ext_if inet proto { tcp, udp } to $nameservers port domain
pass on $ext_if proto tcp to $webserver port $webports
pass log on $ext_if proto tcp to $emailserver port $email
pass log on $ext_if proto tcp from $emailserver to port smtpSignificantly more complicated setups are possible. But remember that while redirections will work, you will not be able to run services on any of the interfaces without IP addresses.
[28] How much security this actually adds is a matter of occasional heated debate on mailing lists such as openbsd-misc and other networking-oriented lists. Reading up on the pros and cons as perceived by core OpenBSD developers can be entertaining as well as enlightening.