After a heavy dose of learning and implementation in the last chapter, this chapter is a simple, straightforward breakdown of the elements that were presented in the last chapter, along with a use case.
Understanding cryptography and validations over blockchain transactions—encryption, validation
Data, stakes, and operations in a blockchain—distribution, security
Why is encryption so important?
Why is validation so crucial after a transaction is done?
Why does the undistributed, centralized system not suffice?
Information is an asset that, when not secured thoroughly, can mislead or divert business operations, economies, and humanity. So, let’s consider a famous person named XORO who did not store his personal data securely. XORO allowed access to his media storage on an unprotected website. All the hacker had to do was attack XORO’s machine or this poorly secured website to access information sitting there openly. The hacker shared this information on the internet. This information leak caused people to believe rumors generated by unknown sources without any validation of the news. Further, stocks of the brand attached to this famous figure dropped, thereby affecting other related elements and causing the pile of dominos to fall around the entire ecosystem.
Now, imagine this: XORO has used a blockchain platform to share personal information with his family members. The data is not stored on a single device. Even the private key can be encrypted, split, and distributed on a chain, thus making it difficult for the hacker to access the information. The hacker here would have to loop through the entire chain to retrieve a piece of information, which is encrypted differently at every node. Also, fake news origins can easily be discredited as it did not originate from the blockchain that stores XORO’s information. The blockchain provides immutability; i.e., it does not allow anyone to modify an existing data point—one must append and make an update. Thus, the creditability of the true information source is maintained. This control creates a trust with the brands XORO works with. The stakeholders can easily quantify trust based on such measures.
Encryption and Validation
Like XORO, we all share a lot of information digitally, be it bank details or movie preferences or the places we visit. Let’s study WhatsApp to understand end-to-end encryption and then explore various cryptographic options with blockchains.
Cryptography is an art that humans have long been using to store, share, and maintain secrets across traditions, cultures, and languages. This art got transformed to mathematical methods that are used to reword text, literature, and national secrets in the modern era, and now we have the usage of electronic key mechanisms.
We tend to share a lot of data with our peers, family, or co-workers in the form of images, audio, video, or text. These are further converted into a random set of alphanumeric characters known as hash functions to avoid plain-text readability on the part of developers or unauthorized users.
A hash function is a mathematical function that, when applied on the same message, will generate the same output. One such example of a hash function that is widely used is SHA256—it is used by Bitcoin. A 256-bit pattern can represent 2256 different messages. Breaking a 256-bit key by brute force requires 2128 times more computational power than a 128-bit key. Fifty supercomputers that could check a billion billion (10^18) AES keys per second would, in theory, requires about 3×1051 years to decode the key space. This makes it almost impossible for not just a human but also a supercomputer to determine the data communicated between two individuals.
One thing that makes us comfortable to chat freely is the simple indicator that the chat is end-to-end encrypted. That’s what made WhatsApp popular with such a large user base. Let’s see how they encrypt.
End-to-end encryption ensures that a message sent can only be read by the sender and the receiver and not by a third party, not even WhatsApp. A basic description given by WhatsApp states that the message being sent is secured with locks, and only the recipients and the sender have the key to these locks. Making it more complex for the third party to decrypt, every message has a unique set of lock and key.
- Public key types
Identity key pair – A long-term Curve25519 key pair, generated at install time
Signed pre-key – A medium-term Curve25519 key pair, generated at install time, signed by the identity key, and rotated on a periodic timed basis
One-time pre-keys – A queue of Curve25519 key pairs for one-time use, generated at install time, and replenished as needed
- Session Key Types
Root key – A 32-byte value that is used to create chain keys
Chain Key – A 32-byte value that is used to create message keys
Message Key – An 80-byte value that is used to encrypt message contents. 32 bytes are used for an AES-256 key, 32 bytes for a HMAC-SHA256 key, and 16 bytes for an IV.
WhatsApp not only encrypts the text messages inside the chat, but also includes encryption at every step, from the registration process, initiating sessions, receiving sessions, exchanging messages, transmitting media and other attachments to group messages, and statuses, to live locations.
Similarly, blockchain ensures similar security with encryption embedded at each step for every addition of blocks across the chain, across every node and every transaction. Cryptocurrencies are mined on solving cryptographic equations based on the fundamental principle or consensus the chain works on.
Bitcoin (₿) is a cryptocurrency, a form of electronic cash. It is a decentralized digital currency without a central bank or single administrator that can be sent from user-to-user on the peer-to-peer Bitcoin network without the need for intermediaries. Transactions are verified by network nodes through cryptography and recorded in a public distributed ledger called a blockchain. Bitcoins are created as a reward for a process known as mining. They can be exchanged for other currencies, products, and services.
So, let’s understand where encryption is used for a Bitcoin, in contrast with the WhatsApp example that we just saw. Bitcoin does not use encryption of the data throughout the transaction directly. It ensures that the user’s wallet is secured by digital signatures . Users using the Bitcoin network to transfer simply validate with their digital signatures. However, the mining process is different from a transaction—mining yields Bitcoins upon validation of the transaction on the network. Not all users may be miners. The ones who validate or take the effort to authenticate a transaction are the ones who earn.
A digital signature offered by a Bitcoin user proves their ownership over the authorization of a transfer in a way that can be validated by everyone on the network. A digital signature such as ECDSA (Elliptic Curve Digital Signature Algorithm) with variations of the elliptic curve are used. Imagine this like XORO walking to his bank safety deposit box with his private key, where the bank manager has a public key. The combination of both authorizes the opening of the locker. However, in the case of a Bitcoin, the private key is not provided by any central authority, but rather is generated privately in its true form, and the bank manager is the entire peer network rather than one person. This makes it way more reliable and inaccessible to anyone else.
To dive deeper into the cryptography used by Bitcoin, the elliptic curve defined over SHA256 is secp256k1.
The definition of the elliptic curve in secp256k1 is as follows:
y2 = x3 + 7
Looks like gibberish? Let’s see how XORO uses all of this. XORO and the bank manager generate their own private keys. They agree on a public key based on an equation and factors of the curve. The formulation of this public key is a combination of the private key and the curve that satisfies at two ends. The public key formulation is based on six variables, thereby making any third-party guess nearly impossible.
- 1.We’ve used the Azure Jupyter notebook to implement the following (Figure 3-1).
 Figure 3-1
Figure 3-1implementing the SHA256 encryption in Python
- 2.
We want to apply the elliptic curve secp256k1 used in Bitcoin’s public-key cryptography for “hello”: Install secp256k1 on pip by typing:
!pip install secp256k1 - 3.
Implement as follows (Figure 3-2).

Using SECP256k1 in Python
Distribution and Security
Now that we have learned about the methods used to encrypt and validate, let us see how distribution and security are maintained on the blockchain. Different blockchain applications run for different purposes.
For example, the Bitcoin network runs for its cryptocurrencies and the proof of work. Hyperledger allows users to decentralize application processes, data, and authority based on the principle of design over the network. There are several such distribution-based networks known as DLT (decentralized ledger technology) that allow the platform to decentralize.
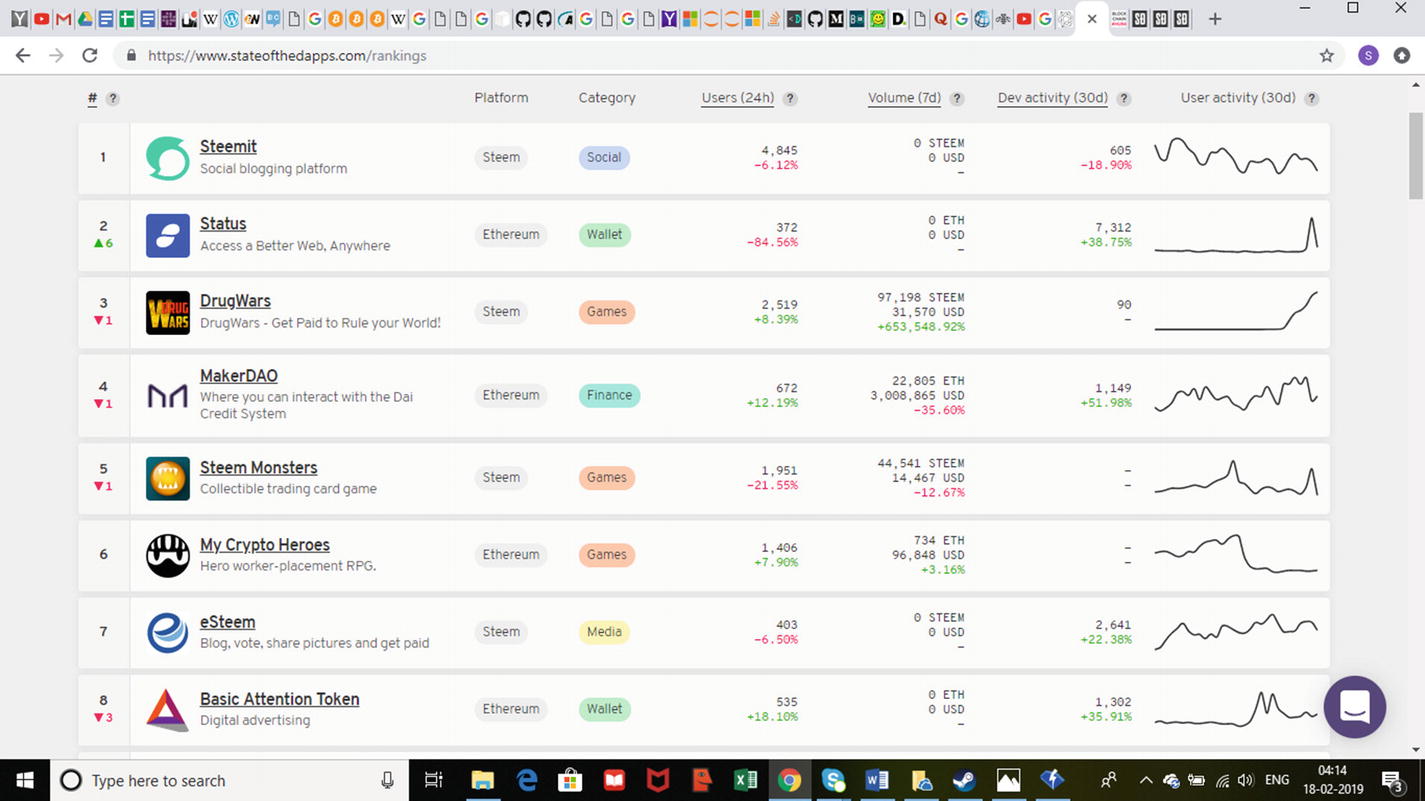
Top eight DApps based on number of active users, trends, value, etc.
Blockchain brings in the shared ledger aspect when DLT is considered. How does XORO benefit from the distributed network of data, processes, and authority? Let’s find out.
Distributed Data
As mentioned earlier, storage of XORO’s complete encrypted data is spread across a couple of servers. To decrypt or read that data, XORO needs to go through the entire network. However, what happens when one of the servers gets corrupted? Will XORO lose his data? That’s why the blockchain must be fault tolerant. Shared ledgers make multiple copies of the data. When one entry is to be changed, all the nodes must have the change replicated to allow the data change in a true sense. This may or may not require permission to modify the data based on whether the DLT is permissioned or permissionless.
Consider the example of the Interplanetary File System—XORO has created a video album that is to go on the ledger. Every node stores 256kb of data chunked onto different servers. When XORO accesses the file, he goes through all the nodes. When XORO wants to modify info, until all nodes reflect the change, the info is not changed.
FileCoin uses the IPFS protocol to decentralize storage on a blockchain platform. XORO can safely use FileCoin and enjoy its benefits of credible data storage, immutability, and security.
SiaCoin leverages underutilized hard-drive capacity around the world to create a data storage marketplace that is more efficient and cheaper than current solutions. It’s like an AirBnb of space on a decentralized platform.
Distributed Processes
Blockchain Name | Protocol | Decentralized Aspect |
|---|---|---|
Ripple | XRP Ledger Consensus Protocol | Decentralizes trust, settlement, and validation of transactions |
NEM | Proof of Importance | Decentralizes authority of transactions by calculating importance of a node/user |
Stellar | Federated Byzantine Agreement | Decentralizes cross-border currency conversions |
The distribution of processes can be done for decentralized authority, decentralized ownership, and several such processes. Let’s take the use case from trade finance (Figure 3-4). The importer must present its paying capacity to the exporter to initiate the deal. Thus the importer has to produce a bank guarantee. The bank that the importer visits may or may not be biased to the importer’s situation, allowing leniency. This also allows the possibility of creating fake bank guarantees.
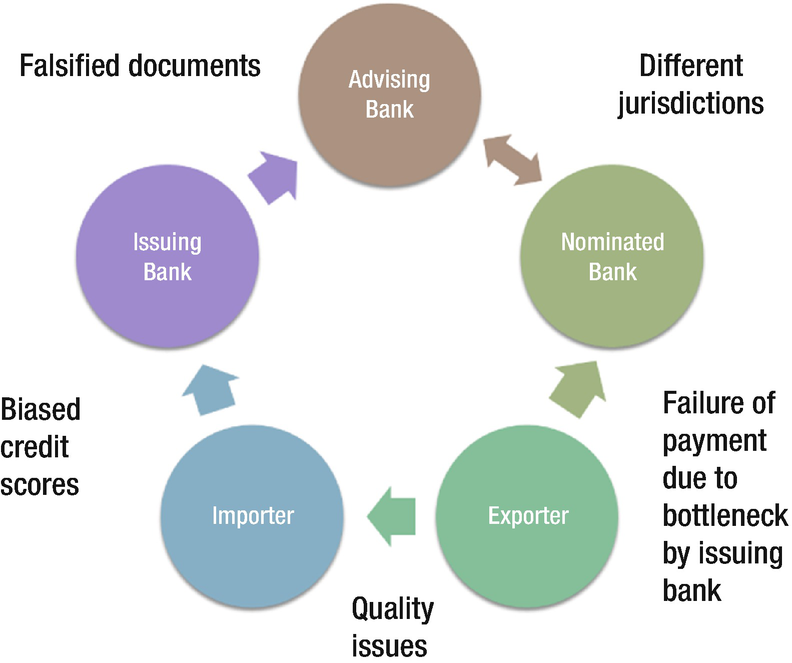
Trade Finance Process in a centralized environment, and its problems
