This appendix provides detailed information about the DNS standard resource records (RR) used to construct domain database files. This is primarily a reference to use in conjunction with the tutorial information in Chapter 6. This appendix is divided into three sections.
The first section covers the most commonly used resource records. It shows the DNS console dialog used to enter each commonly used record and the syntax of each standard resource record as it appears in the zone file.
The second section of the appendix covers the resource records that, while available in the DNS console, are less commonly used. In fact, a few of the records covered in this section should not be used because they are obsolete or potential security problems. Where that is the case, we note it. The zone file syntax of the less commonly used records is discussed.
The final section of the appendix covers the syntax of the optional boot file. This file can be used when transitioning a server from a Unix system running BIND 4 to a Windows Server 2003 system. The boot file has nothing to do with DNS resource records. However, it needs to be covered somewhere, so it has been added to this appendix.
Standard resource records define the domain data contained in the zone file. The format of standard resource records, sometimes called RRs, is defined in RFC 1033, the Domain Administrators Operations Guide. The format is:
[name] [ttl] INtype data
The individual fields in the standard resource record are:
nameThis is the name of the object affected by this resource record. The named object can be as specific as an individual host, or as general as an entire domain. The string entered for
nameis relative to the current domain unless a fully qualified domain name is used.[*] Certainnamevalues have special meaning:A blank name field denotes the current named object. The current name stays in force until a new name value is encountered in the name field. This permits multiple RRs to be applied to a single object without having to repeat the object’s name for each record.
..Two dots in the name field refer to the root domain. However, a single dot (the actual name of the root) also refers to the root domain, and is more commonly used.
@A single at sign (
@) in the name field refers to the current origin. The origin is the domain name associated with the current zone.*An asterisk in the name field is a wildcard character. It stands for a name composed of any string. It can be combined with a domain name or used alone. Used alone, an asterisk in the named field means that the resource record applies to objects with names composed of any string of characters plus the name of the current domain. Used with a domain name, the asterisk is relative to that domain. For example,
*.example.com.in the name field means any string plus the string .example.com.
ttlTime-to-live defines the length of time in seconds that the information in this resource record should be kept in the cache. The time is specified as a numeric value up to eight characters in length. If no value is set for
ttl, it defaults to the value defined for the entire zone file in the default TTL field of the SOA record.INThis field is the address class of the resource record. The Internet address class is
IN, which is the only address class supported by Windows Server 2003. Thus, all resource records used in this book have an address class ofIN.typeThis field indicates the type of data the record provides. For example, the A type RR provides the address of the host identified in the name field. All resource record types available in the DNS console are discussed in this appendix.
dataThis field contains the information specific to the resource record. The format and content of the data field vary according to the resource record type. The data field is the meat of the RR. For example, in an A record, the data field contains the IP address.
In addition to the special characters that have meaning in the name field, zone file records use these other special characters:
;The semicolon is the comment character. Use the semicolon to indicate that the remaining data on the line is a comment.
()Parentheses are the continuation characters. Use parentheses to continue data beyond a single line. After an opening parenthesis, all data on subsequent lines is considered part of the current line until a closing parenthesis.
xThe backslash is an escape character. A nonnumeric character following a backslash (
) is taken literally and any special meaning that the character may ordinarily have is ignored. For example,;means a semicolon—not a comment.dddThe backslash can also be followed by three decimal numbers. When the escape character is used in this manner the decimal numbers are interpreted as an absolute byte value. For example,
255means the byte value11111111.
The same general resource record format is used for all of the resource records in a zone file. Windows can read and process the same zone files as any other DNS server.
Most Windows administrators do not edit the zone files directly. Instead they use the DNS console to create resource records. We recommend that you do the same and that you never directly edit the zone files. Using the console is simpler, more intuitive, and less prone to error. Chapter 6 explains how to use the DNS console. The following sections examine the syntax for each of several key resource record types, and where appropriate, show the DNS console dialog boxes used to create those records.
The Start of Authority (SOA) record marks the beginning of a zone, and it is usually the first record in a zone file. Each zone has only one SOA record. All of the records that follow are part of the zone declared by the SOA. The SOA record defines parameters for the entire zone.
Unlike the other resource records, the SOA record cannot be created through the New Resource Record dialog. The New Zone Wizard creates the SOA record when a new primary zone is created. However, the values in the SOA record can be modified later through the Start of Authority (SOA) tab of the zone properties dialog, as described in Chapter 6.
The format of the SOA record is:
zone[ttl] IN SOAorigin contact(serial refresh retry expire minimum)
The components of the SOA record in the zone file are:
zoneThis is the name of the zone. Usually the SOA name field contains an at sign (
@). When used in an SOA record, the at sign refers back to the domain name declared in the New Zone Wizard when the zone was created.ttlThis is the time-to-live for the SOA record itself. This field is left blank on the SOA record unless the default value in the “TTL for this record” box of the Start of Authority (SOA) tab is changed, as described in Chapter 6.
INThe address class is
INfor all resource records on a Windows DNS server.SOASOA is the resource record type. All the information that follows this is part of the data field and is specific to the SOA record.
originThis is the hostname of the master server for this domain. It is normally written as a fully qualified domain name. For example, komodo is the master server for example.com , so this field contains
komodo.example.com. in the SOA record for example.com . For this field, the New Zone Wizard uses the hostname defined on the Computer Name tab of the System Properties window of the system on which the zone file was created.contactThe email address of the person responsible for this domain is entered in this field. The address is modified slightly. The at sign (@) that usually appears in an Internet email address is replaced by a dot. Therefore, if [email protected] is the mailing address of the administrator of the example.com domain, the example.com SOA record contains
Administrator.example.com. in the contact field.serialThis is the version number of the zone file. It is an eight-digit numeric field usually entered as a simple number—for example,
9. Slave servers use the serial number to determine if the zone file has been updated. To make this determination, a slave server requests the SOA record from the master server and compares the serial number of the data the slave has stored to the serial number received from the master server. If the serial number has increased, the slave server requests a full zone transfer. Otherwise, it assumes that it has the most current zone data. The serial number must increase each time the zone data is updated for the new data to be disseminated in this manner. The DNS server automatically increases the serial number each time the zone data changes.refreshThis specifies the length of time that the slave server waits before checking with the master server to see if the zone has been updated. Every
refreshseconds the slave server checks the SOA serial number to see if the zone file needs to be reloaded. On their own, slave servers only check the serial numbers of their zones when they restart. Therefreshinterval provides a predictable cycle for reloading the zone that is controlled by the domain administrator. The process of retrieving the SOA record, evaluating the serial number and, if necessary, downloading the zone file is called a zone refresh. Thus the name “refresh” is used for this value. The value used inrefreshis a number, up to eight digits long, that is the maximum number of seconds that the masters’ and slave servers’ databases can be out of synch.A low
refreshvalue keeps the data on the servers closely synchronized, but a very lowrefreshvalue is not required. The master server alerts the slave whenever a zone update is made using a Notify message. DNS Notify keeps the servers tightly synchronized. The refresh timer is simply a “fail safe” mechanisms used to backup the DNS Notify mechanism. A value set lower than needed places an unnecessary burden on the network and the slave servers. The value used inrefreshshould reflect the reality of how long you can stand to have the servers out of synch. Most sites’ domain databases are very stable. Systems that must be accessed by name are added periodically, but not generally on an hourly basis. When you are adding a new system that must be accessed by name, you can assign the hostname and address of that system before the system is operational. You can then install this information in the name server database before it is actually needed, ensuring that it is disseminated to the secondary servers long before it has to be used. If extensive changes are planned, therefreshtime can be temporarily reduced while the changes are underway. Therefore, you can normally setrefreshtime high, reducing load on the network and servers.retryThis defines how long slave servers should wait before trying again if the master server fails to respond to a request for a zone refresh.
retryis specified in seconds and can be up to eight digits long. Do not set theretryvalue too low. If a master server fails to respond, the server or the network could be down. Quickly retrying a down system gains nothing and costs network resources. A slave server that backs up a large number of zones can have problems whenretryvalues are short. If the slave server cannot reach the primary servers for several of its zones, it can become stuck in a retry loop. The New Zone Wizard uses 10 minutes (600) as a default. Don’t setretryany lower than this.expireThis defines how long the zone’s data should be retained by the slave servers without receiving a zone refresh. The value is specified in seconds and is up to eight digits long. If after
expireseconds the slave server has been unable to refresh this zone, it should discard all of the data.expireis often a very large value. 3,600,000 seconds (about 42 days) is sometimes used. This says that if there has been no answer from the master server to refresh requests repeated everyretryseconds for the last 42 days, discard the data. Forty-two days is long, but commonly used. A week (604800) is adequate. However, one day (86400), which is the default provided by the New Zone Wizard, is much too short.minimumMicrosoft uses this value as the default TTL for any resource record that does not have an explicit TTL value. The value set for
minimumis also used by remote servers as the TTL value for negative cache information.
A sample SOA record for the example.com domain is:
@ IN SOA mandy.example.com. Administrator.example.com. (
9 ; serial
43200 ; refresh twice a day
1800 ; retry every half hour
604800 ; expire after one week
1800 ; default ttl half an hour )This SOA record says that mandy is the master server for this zone and that the person responsible for this zone can be reached at the email address [email protected]. The SOA serial number indicates the cached zone has been updated fewer than 10 times. The SOA tells the slave servers to check the zone for changes twice a day and to retry every half hour if they don’t get an answer. If they retry for a week and never get an answer, they should discard the data for this zone. Finally, if an RR in this zone does not have an explicit TTL, the TTL of the RR will default to 30 minutes.
Name Server (NS ) resource records identify the authoritative servers
for a zone. These records are the pointers that link the domain
hierarchy together. NS records in the top-level domains point to the
servers for the second-level domains, which in turn contain NS records
that point to the servers for their subdomains. Name server records
pointing to the servers for subordinate domains are required for those
domains to be accessible. Without NS records, the servers for a domain
would be unknown. NS records are so important that they are created by
the New Zone Wizard whenever a primary zone is created. However, the
list of NS records associated with the zone can be modified through
the Name Servers tab of the zone properties dialog, as described in
Chapter 6. The syntax of the
NS RR, as it appears in a zone file, is
domain [ttl]
IN NS
server, where:
domainIs the name of the domain for which the host specified in the
serverfield is an authoritative name server. Any one of the validnamefield formats described at the beginning of this appendix can be used in this field.ttlIs the explicit time-to-live for this record. Time-to-live is usually blank.
INThe address class is always
INon Microsoft servers.NSThe Name Server resource record type is NS.
serverIs the hostname of a computer that provides authoritative name service for this domain. Usually domains have at least one server that is located outside the local domain. That server name cannot be specified relative to the local domain; it must be specified as a fully qualified domain name.
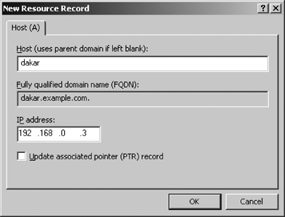
The majority of the resource records in a forward lookup zone file are address records . Address records are used to convert hostnames to IP addresses, which is the most common use of the DNS database. Figure C-1 shows the address record dialog box used to create A records via the DNS console.
Enter the hostname and the IP address in the dialog box to add
an address record to the zone. The A record added to the zone file
contains the following fields (host
[ttl] IN
A address):
hostThe name of the host whose address is provided in the data field of this record. If the host is a member of the current zone, the hostname can be written relative to the current domain. If the host is external to the current zone, the name must be a fully qualified domain name.
ttlThe explicit time-to-live field is usually blank. The dialog box used to create this record does not provide a means to input an explicit TTL.
INThe address class is always
IN.AThe Address resource record type is A.
addressThe IP address of the host is written here in dotted decimal form, for example,
192.168.0.3.
A glue record is a special type of address record. Most address records refer to hosts within the zone, but sometimes an address record needs to refer to a host in a subordinate zone. Recall that the NS record for a subdomain server identifies the server by name. An address is needed to communicate with that server, so an A record must also be provided when a subdomain is delegated its own zone. The address record and the name server record combine to link the domains together—thus the term glue record. Chapter 6 describes glue records in the discussion of how to delegate a subdomain.
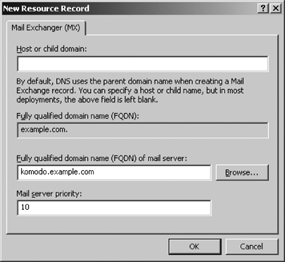
The mail exchanger (MX ) record redirects mail to a mail server. It can redirect mail for an individual computer or an entire domain. MX records are extremely useful because most domains contain many systems that don’t run mail server software and many systems that are offline for part of every day. MX records redirect mail addressed to those systems to reliable servers that run mail server software. Figure C-2 shows the dialog used to add an MX record to the zone.
Use the dialog box to define the name, preference, and server
fields of the MX record. The mail server name and the priority
assigned to that server are filled in Figure C-2, but the name
field, which is taken from the “Host or child domain” box, is left
blank. A blank name field means that this MX record is being defined
for the current zone. In effect, this defines a mail server for the
entire domain. The format of the MX RR in the zone file is
[name] [ttl]
IN MX preference
server:
nameThe name of a host or domain to which the mail is addressed, which is taken from the “Host or child domain box” of the dialog shown in Figure C-2. Think of this as the value that occurs after the @ in a mailing address. Mail addressed to this name is sent to the mail server specified by the MX record’s
serverfield.ttlTime-to-live is usually blank.
INThe address class is always
IN.MXThe Mail Exchanger resource record type is MX.
preferenceA host or domain may have more than one MX record associated with it. The
preferencefield specifies the order in which the mail servers are tried. The server with the lowestpreferencenumber is tried first. Preference values are usually assigned in increments of 5 or 10, so that new servers can be inserted between existing servers without editing the old MX records. The preference value is defined using the “Mail server priority” box of the dialog shown in Figure C-2.serverThe name of the mail server to which mail is delivered when it is addressed to the host or domain identified in the
namefield. The name of the server is defined in the “Fully qualified domain name (FQDN) of mail server” box in the dialogue.
Here is how MX records work. If a remote system has mail to send to a host, it requests the host’s MX records. DNS returns all of the MX records for the specified host. The remote server chooses the MX with the lowest preference value and attempts to deliver the mail to that server. If it cannot connect to that server, it tries each of the remaining servers in preference order until it can deliver the mail. If no MX records are returned by DNS, the remote server delivers the mail directly to the host to which the mail is addressed. MX records only define how to redirect mail. The remote system and the mail server perform all of the processing that actually delivers the mail.
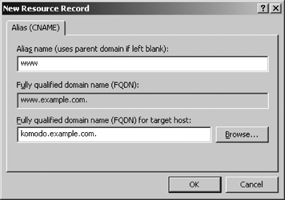
The Canonical Name (CNAME ) resource record defines an alias for the official name of a host. The CNAME record provides a facility similar to nicknames in the host table. The facility provides alternate hostnames for the convenience of users, such as www for web servers, ns for name servers, and smtp for email servers. Figure C-3 shows the dialog box used to add CNAME records to the zone file.
Use the dialog box to enter the alias of the host as well as the
canonical name of the host. The format of the CNAME record that the
dialog inserts into the zone file is alias
[ttl] IN
CNAME hostname:
aliasThis hostname is an alias for the official hostname that is defined in the
hostnamefield.ttlTime-to-live is usually blank, and it cannot be explicitly set using the dialog box.
INThe address class is IN.
CNAMEThe Canonical Name resource record type is CNAME.
hostnameThe Canonical Name of the host is provided here. The
hostnamemust be the official hostname; it cannot be an alias.
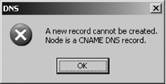
One important thing to remember about the CNAME record is that all other resource records must be associated with the official hostname, and not with the alias. This means that the alias cannot appear in the name field of any other resource record. For example:
www IN MX 5 jamis.example.com.
Assume that www is an alias assign, as shown in Figure C-3. In that case, the MX record in this example is illegal because it contains an alias in the name field. The DNS console will not let you make this mistake. Trying to create the MX record shown above using the DNS console generates the error shown in Figure C-4.
The Domain Name Pointer (PTR ) resource record is used to convert a numeric IP address to a hostname. This is the opposite of what is done by the address record, which converts a hostname to an address. PTR records are used to construct the in-addr.arpa reverse domain files.
Don’t ignore the reverse domain even if name service appears to run fine without it. Programs use the reverse domain to map IP addresses to hostnames when displaying information messages that include IP addresses. Some service providers use reverse domains to track who is using their service, and if they cannot map an IP address back to a hostname, they reject the connection.
The DNS console lets you keep the reverse domain updated automatically. Notice the “Update associated pointer (PTR) record” checkbox on the address dialog shown in Figure C-1. When that box is checked, the DNS console adds a PTR record to the reverse lookup zone when the A record is added to the forward lookup file. PTR records can also be added to the reverse lookup zone using the Pointer (PTR) dialog shown in Figure C-5.
Use the dialog box to define the IP address that appears in the
name field of the PTR record and the hostname that appears in the data
field. The format of the PTR record in the zone file is
name [ttl]
IN PTR
hostname:
nameThe
namespecified here is actually a number. The number is defined relative to the current in-addr.arpa domain. Names in an in-addr.arpa domain are IP addresses specified in reverse order. If the current domain is 0.168.192.in-addr.arpa, then thenamefield for dakar.example.com (192.168.0.3) is3. The digit 3 is added to the current domain 0.168.192.in-addr.arpa to make the name 3.0.168.192.in-addr.arpa.ttlTime-to-live is left blank to use the zone default. While not explicitly shown in Figure C-3, turning on Advanced in the DNS management console will display the TTL for each record.
INThe address class is IN.
PTRThe Domain Name Pointer resource record type is PTR.
hostnameThis is the fully qualified domain name of the computer whose address is specified in the
namefield. The host must be specified as a fully qualified name because the name cannot be relative to the current in-addr.arpa domain.
The Service Location record, which is defined in RFC 2052, provides a standardized way to locate network servers. Generic names such as www.example.org and ftp.example.org are widely used to locate network servers, but these names are not really a standard. The SRV record provides a standard convention for creating generic server names and it adds features for server selection and load balancing. SRV records are used extensively in AD integrated DNS, which is covered in Chapter 7. The format of the SRV record is:
_service._protocol.name[ttl] IN SRVpriority weight port server
The name field of the SRV record has a unique _ service
._
protocol . name format.
Dots are used to separate the components in the name field just as
there are in any domain name. The underscore characters (_) are used to prevent the service name and
the protocol name from colliding with real domain names.
service is the name of the offered service
as listed in the
%SystemRoot%system32etcservices file.
protocol is either _tcp or _udp depending on which transport protocol
is associated with the specified service.
name is a standard host or domain name that
would be found in any name field. Using these criteria, the name that
could be used to find the FTP servers for the example.org domain would
be _ftp._tcp.example.org. A correctly formatted
name is built by selecting a service from the Service drop-down list
and a protocol from the Protocol drop-down list in the Service
Location (SRV) dialog box.
The data field of the SRV record contains four values:
priorityA number used to select the most preferred server when multiple SRV records exist for the same service. The servers are sorted by preference number, so the server with the lowest number is the most preferred. All traffic is sent to the most preferred servers; servers with a higher preference number are only used if the preferred server is not available.
weightUsed to balance the load among servers with the same preference number.
weightis a number that defines the share of traffic sent to a server, with 1 being the base number. If server A has a weight of1and server B has a weight of2, B gets twice as much traffic as A.portThe port number used for the service. The standard port number for the service selected from the Service drop-down list appears automatically in the “Port number” box. But it is possible to enter a nonstandard port number in the box if the services has been configured to use a nonstandard number.
serverThe canonical hostname of the computer running the requested service.
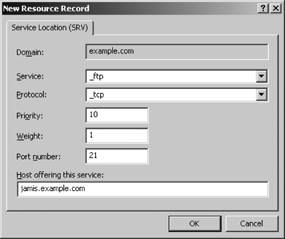
Figure C-6 shows the dialog box used to add a SRV record to the zone.
The SRV service and
protocol values are selected from drop-down
lists. When a service value is selected, the correct
port value for that service appears in the
“Port number” box. In this example, a
priority of 10 was selected to simplify adding other FTP
servers in the future. (10 allows
for future servers to be easily added with lower or higher priority
numbers.) A base weight value of 1 was used even though there are no other
FTP servers defined at this time. These values can be easily changed
in the future if necessary.
The dialog shown in Figure C-6 creates the following zone file entry:
_ftp._tcp SRV 10 1 21 jamis.example.com.
It is easy to see how the values in the dialog box map to the finished resource record.
This concludes our short tour of the basic resource records. There are several more resource records that can be defined in the DNS console than those already covered. Those other RRs are described in the next section However, the few resource records described in this section make up the bulk of most zone files.
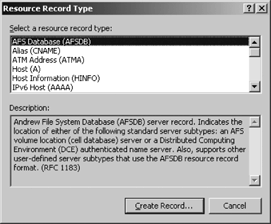
The basic resource records covered in the previous section are all either created by the New Zone Wizard or through their own entries in the DNS console Action menu. To create the less commonly used resource records described in this section, select the Other New Records item from the Action menu to open the Resource Record Type dialog shown in Figure C-7.
Highlighting a record type in the “Select a resource record type” list box and then clicking Create Record opens a dialog specific to the type of record selected, where you can then enter the data required by the record type. The records available through this dialog box that have not already been covered in this appendix are described here in the order they appear in the list box. The purpose of each record and the type of data the record requires are covered.
The experimental AFSDB record points to the server for an AFS or DCE cell. AFS, originally called the Andrew File System, is a distributed filesystem that is optimized for use over wide area networks (WANs). DCE, the Distributed Computing Environment, is just that, a standard that describes the interactions between computers in a distributed computing environment. AFS and DCE systems use DNS to point to their servers. They do this by using cell names that are compatible with DNS domain names. The AFSDB record maps the cell name to the correct server. The format of an AFSDB record is:
cell_name[ttl] IN AFSDBtype server
The cell_name looks just like a
domain name and, in fact, is often the name of the current domain. The
Microsoft DNS server defaults to using the current domain name unless
a specific name is entered in the AFS Database
(AFSDB) dialog. The type field,
which is correctly set in the dialog by simply clicking a button,
contains a 1 if the server is an
AFS server or a 2 if it is a DCE
server. The server field contains the DNS
domain name of the AFS or DCE server. The AFSDB record is defined in
RFC 1183.
The ATMA record maps a hostname to an Asynchronous Transfer Mode (ATM) address. ATM is a high-speed fiber optic network technology. It transmits small chunks of information that are only 53 bytes long to make it easier to optimize support for real-time traffic such as voice or video. The ATMA record was not standardized in an RFC. Instead, it is standardized by the ATM Forum in ATM Name System Specification Version 1.0. The format of the ATMA record is:
name[ttl] IN ATMAatm_address
name is the hostname to which the ATM
address is assigned; atm_address is the ATM
address written in either the E.164 international telephone standard
format or in the ISO NSAP (network service access point) standard
format. When the hostname and ATM address are entered in the ATM
Address (ATMA) dialog box, either the E.164 address button or the NSAP
address button must be selected to indicate the format you used to
enter the address.
The Host Information record provides a short description of the hardware and operating system used by a host. RFC 1035 defines the HINFO record. The format of the HINFO record is:
host[ttl] IN HINFOhardware software
Originally, the hardware and software items in the data field were supposed to come from an official list of hardware and software registered in RFC 1700, Assigned Numbers. That might have worked in the days of mainframes when computer models changed slowly, but it wouldn’t work today. Administrators who use this record simply make up descriptive entries for the hardware and software and enter those in the “CPU type” box and the “Operating system” box of the Host Information (HINFO) dialog.
Adding this record to the zone file is generally discouraged because it can provide information to network intruders and has no particular use.
The AAAA record maps a domain name to an Internet Protocol Version 6 (IPv6) address. The AAAA record is defined in RFC 3596, DNS Extensions to Support IP Version 6. The format of the AAAA record is:
name[ttl] IN AAAAipv6_address
The format is the same as an A record except that the address provided in the data field is a 128-bit IPv6 address instead of a 32-bit IPv4 address. Instead of the dotted decimal notation used to write an IPv4 address, an IPv6 address is written as eight, 16-bit hexadecimal numbers separated by colons, as follows:
big6 IN AAAA 1234:a:b:c:d:e:f:9876
The traditional PTR record is used to map IPv6 addresses back to domain names. A new top-level reverse-mapping domain was created called ip6.int. When IPv6 addresses are converted to names in the reverse-mapping domain, they are reversed and written out as 32, four-bit nibbles separated by dots. Thus, the IPv6 address 1234:a:b:c:d:e:f:9876 becomes:
6.7.8.9.f.0.0.0.e.0.0.0.d.0.0.0.c.0.0.0.b.0.0.0.a.0.0.0.4.3.2.1.ip6.int.
Only systems that use IPv6 are assigned IPv6 addresses, and only systems that run the IPv6 protocol stack need to lookup AAAA records. Unless you run IPv6 on your network you won’t use this record.
The experimental ISDN record maps a domain name to an ISDN address. Integrated Services Digital Network (ISDN) is a digital telephone service that can carry voice and data. Poor price/performance has limited the number of ISDN users in the United States, but it is popular in many other countries. The format of the ISDN record is:
name[ttl] IN ISDNISDN_address subaddress
The ISDN record is rarely used because most IP-to-ISDN bridges have internal mechanisms to map from IP addresses to ISDN addresses. The ISDN record is defined in RFC 1183.
The obsolete Mail Group record defines mail delivery instructions for mailing lists using a scheme in which the list name and the mailboxes of the individual recipients in the list are defined in DNS. In actuality, mailing lists are processed by mail servers and are defined in the configuration of those servers, not in DNS. This record is no longer used. It is, however, documented in RFC 1035 and thus listed in the Resource Record Type dialog.
The obsolete Mailbox record defines mail delivery information for an individual user. As originally envisioned, every user in the domain would be given a unique MB record. This record has been obsolete for many years. The mail server, not DNS, handles mail delivery to individuals. The MB record is documented in RFC 1035 and is therefore listed in the Resource Record Type dialog. However, you should not use this record.
The obsolete Mailbox Information record defines control information for MG mailing lists by defining both the email address of the email administrator and an email address where error messages should be sent. This record is directly related to the obsolete Mail Group record. Mailing lists and the administrative information about mailing lists are defined in the mail server configuration, not in DNS. The MINFO record is documented in RFC 1035 and is therefore listed in the Resource Record Type dialog. However, this record is no longer used.
The Next Domain record provides a way to formally document and authenticate nonexistent domain information. The SIG record, described later, is used to authenticate domain database records. However, a digital signature can only be calculated against an existing record. By its very nature, the information involved in negative caching has no database record to be authenticated. If the information returned by the authoritative name server states that no MX record exists for a given domain name, how is that information authenticated before being added to the cache? The NXT record is the solution. The format of the NXT record is:
name[ttl] IN NXTnext_name type_list
The type_list is a list of the types
of resource records that do not exist for the object identified by
name. Thus, if no MX record existed for the
domain name parrot.example.org
, you might have the following NXT record:
parrot.example.org. IN NXT puffin.example.org. MX
The function of the next_name field
is a little more obscure. This field contains the next domain name in
canonical order as defined by RFC 2535. A simple way to think of
canonical ordering is as if each label in the names were sorted
without regard to case. The next_name field
is used to provide evidence that a name does not exist.
The NXT record is only needed when strong authentication is used. By default, all data from an authoritative server is cached, whether it is a positive response that provides the requested resource records or a negative response that indicates that the requested information does not exist. In the default situation, there is no need to document nonexisting data with the NXT record.
The Public Key record provides the public key for a given domain name. The KEY record is defined in RFC 2535. The format of the KEY record is:
name[ttl] IN KEYflags protocol algorithm public_key
The public_key is an encryption key,
written in base 64 encoding, that is to be used for public key
cryptography when communicating with the object identified by
name. The value for the
public_key field is entered in the “Key
(base 64)” box of the Key (KEY) dialog box when the Key record is
created.
The value of the algorithm field can
be 1 for RSA/MD5, 2 for Diffie-Hellman or for DSA, 4 for Elliptic Curve, or 252 for indirect key. Set the
algorithm value by making a selection from
the Algorithm drop-down list of the Key (KEY) dialog box.
The protocol field defines the
protocol that will use the public key. The key is limited specifically
to DNS security by RFC 3445. When the record was originally designed,
however, it was to be accessible to other protocols that might want to
use the key. Therefore, multiple protocol values were defined, and are
supported by the DNS console. Select DNSSEC from the Protocol
drop-down list to set the correct value. The full list of
protocol field values is:
1TLS is no longer valid and is now officially referred to as “reserved.”
2Email is no longer valid and is now officially referred to as “reserved.”
3DNSSEC is the only valid setting for
protocol.4IPSEC is no longer valid and is now officially referred to as “reserved.”
255All is no longer valid and is now officially referred to as “reserved.”
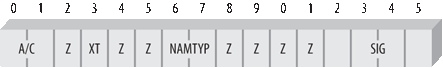
The flags field is a binary bit mask
that contains several different subfields. The “Bit field
representation” box of the Key (KEY) dialog shows the changing bit
values as you configure the KEY record. Figure C-8 shows how each
bit in the flags field is defined by RFC 2535.
Every bit marked with a Z in
Figure C-8 is reserved
for future use and must be set to 0. That leaves four active subfields:
- A/C
These two bits define whether the key is used for authentication or for confidentiality. If the first bit is
1(10), the key cannot be used for authentication. If the second bit is1(01), the key cannot be used for confidentiality. Thus,00means the key can be used for either task, and11means that the zone is not secured. To set these bits make a selection from the “Key type” drop-down list.- XT
This bit is reserved for the future when more than one flags field may be required. If set to
1, it means that the flags are extended to a second 16-bit word. Currently, the value must be0because there are no valid extensions.- NAMTYP
These two bits identify what type of domain name is found in the name field. (Use the “Name type” drop-down list to set this field.) Bits
00means that the name is a username such as would be found on an RP or SOA record. Bits01means that the name is the domain name of the zone. Bits10means that the name is the name of an object, such as a host or subdomain, contained within the zone. Bits11is reserved for future use.- SIG
These four bits indicate whether or not the key can be used to sign updates for dynamic DNS. If the field is nonzero, the key can be used to sign dynamic DNS updates. (The “Signatory field” checkboxes set values in this field.) If the field is 0, the key can still be used to sign a dynamic DNS update, but only if the name type is “zone” and the update is for the specified zone, i.e., the NAMTYP field contains 01 and the dynamic update is for the zone identified in the
namefield.
The obsolete Mail Rename record defines a mail alias. A mail alias is a nickname for a user that permits mail addressed to the nickname to be delivered to the real user. For example, [email protected] might be an alias for [email protected]. In that case, mail addressed to postmaster would really be delivered to david. The mail server handles aliases; this function is not handled by DNS. The MR record is documented in RFC 1035 and is therefore listed in the Resource Record Type dialog. However, this record is no longer used.
The Responsible Person record, which is defined in RFC 1183, identifies the point of contact for a host or domain. The format of the RP record is:
name[ttl] IN RPmail_address text_pointer
The mail_address is the email address
of the responsible person. The @ usually included in an email address
is replaced with a dot. Thus, [email protected] becomes
craig.example.org .
The text_pointer is the domain name of a
TXT record that contains additional information about the responsible
person. Here’s an example of how an RP record is used with a TXT
record:
ibis.example.org. IN RP craig.example.org. ibisRP ibisRP.example.org. IN TXT "Craig Hunt (301)555-1234 X237"
The RP record states that the person responsible for ibis.example.org can be reached via email at [email protected] and that additional information about the person can be obtained in the TXT records for ibisRP.example.org. The TXT record in this example provides the contact person’s name and phone number, but it could provide any information you wish.
RP records could make it easier for system administrators to contact each other when things go wrong. However, most domains don’t use RP records because these records can expose internal email addresses to the outside world.
The experimental Route Through record points to a gateway that can be used to route packets to networks that are not part of the Internet. The X.25 and ISDN networks mentioned in the description of other resource record are good examples of such networks. The RT record is defined in RFC 1183. The format of the RT record is:
name[ttl] IN RTpreference gateway
The preference value in the RT record
is similar to the preference value of an MX record. It is a numeric
value and the lower the number, the more preferred the gateway.
preference permits DNS to define multiple
gateways to the remote host allowing applications that use the RT
records to select the best route. When a server returns an RT record
as the response to a query, it also includes all A, X25, and ISDN
records that define addresses for the gateway. This allows
applications on various types of networks to find addressing and
routing information from DNS.
The RT record is rarely used. There are no widely available applications designed to use it. Routing protocols handle the distribution of routing information. RT was primarily of interest as a possible technique for integrating dissimilar networks.
The Signature record provides a digital signature to authenticate a set of resource records. The format of the SIG records is:
name[ttl] IN SIGtype_list(algorithm labels original_ttl signature_expiration signature_ inception key_tag signer_name signature)
The fields for the SIG record are as follows:
type_listA list of the resource record types for the specified domain name that are digitally signed by this SIG record. Set the value for this field using the “Type covered” drop-down list in the Signature (SIG) dialog box.
algorithmThe encryption algorithm used to produce the digital signature. There are five algorithm values available from the Algorithm drop-down list of the dialog box. They are:
1For the RSA/MD5 algorithm defined in RFC 2537
2For the Diffie-Hellman algorithm defined in RFC 2539
3For the DSA algorithm defined in RFC 2536
4For the Elliptic Curve algorithm described in RFC 3278
252For indirect key
labelsSpecifies the number of parts in the domain name. For example, example.org has two parts, example and org, so it has a
labelsvalue of2. terns.example.org has three parts and thus alabelsvalue of3. Use the Labels box to set thelabelsvalue.orginal_ttlThe TTL value from the original resource record that was used when the digital signature was calculated. Because the TTL is decremented by servers that hold records in their caches, the
orginal_ttlis needed to recalculate the signature when verifying the record. The “Original time to live” box sets this value.signature_expirationDefines the date that the signature becomes invalid. The date is defined as the number of seconds from January 1, 1970. The DNS console correctly calculates this value based on the date you enter in the “Signature expiration (GMT)” box.
signature_inceptionDefines the date on which the signature was created. The date is defined as the number of seconds from January 1, 1970. The DNS console correctly calculates this value based on the date you enter in the “Signature inception (GMT)” box.
key_tagWhen used with the RSA/MD5 algorithm, is a 16-bit piece of the key that is used to select the correct key when multiple possible keys are involved. For all other algorithms, the
key_tagfield holds a checksum of the SIG resource record. Only use the “Key tag” box to enter this value when using RSA/MD5 with multiple keys.signer_nameThe domain name of the entity that created the digital signature. It is usually the domain name of the zone that contains the signed records, and it is entered in the “Signer’s name” box.
signatureThe digital signature that authenticates the resource records. This value is entered in the “Signature (base 64)” box as a base-64 encoded string.
RFC 2535 defines the SIG record.
The Text record is used to define free-form information about the named object. RFC 1035 defines the TXT record. The format is simple:
name[ttl] IN TXTstring
The TXT record can be used to provide information useful for supporting a host. The following example illustrates this use:
buzzard IN TXT "Accounting Department server in room B152"
Because of its free-form nature, the TXT record has been used over time for special purposes, such as providing input to locally developed programs that collect domain information. As noted previously, the TXT record is also used with the RP record.
A Well Known Services record advertises the network services offered by a host. The format of the WKS record is:
host[ttl] IN WKSaddress protocol services
The data field of the WKS record contains three fields:
addressThe IP address of the host advertising the services. The address must be one of the addresses that are valid for the computer identified by the
hostfield.protocolEither UDP or TCP. To advertise services for both transport protocols, use one WKS record for UDP and one for TCP for each host.
servicesThe list of advertised services. The services should be identified using the names found in the %SystemRoot%system32etcservices file.
These two WKS records are an example of advertising UDP and TCP services for the host crow:
crow IN WKS 172.20.5.5 TCP ftp telnet crow IN WKS 172.20.5.5 UDP domain smtp
The WKS record is rarely used. There are no widely distributed programs that take advantage of WKS record, and there is the threat that network intruders will use the information in the WKS record to exploit the advertised system.
The experimental X25 record maps a domain name to an X.25 address, called an X.121 address. X.25 is an international standard for public packet-switched networks. X.25 networks have not been widely used in the United States for many years. The advent of personal computers and the Internet made them largely obsolete, though some countries still use X.25. The X25 record is defined in RFC 1183. The format of the X25 records is:
name[ttl] IN X25X.121_address
The X25 record is rarely used because most X.25 networks provide their own mapping to IP addresses. The scale of the Internet makes it impossible for X.25 networks, or any other network for that matter, to ignore IP. In fact, implementations of IP that run directly over X.25 have long been available.
There is one DNS configuration file that is not built of standard resource records. The boot file defines the name server configuration and tells the name server where to obtain database information. If the server is configured using the DNS console, the boot file is not used. However, the Microsoft DNS server can use a boot file for compatibility with BIND 4 servers and to simplify the transition from a BIND 4 server to a Windows Server 2003 DNS server. Windows Server 2003 supports the following types of boot file records :
primarydomain-name file-nameThe
primarycommand declares the local name server as the master server for the domain specified bydomain-name. As a master server, the system loads the name server database from the local disk file specified by name in thefile-namefield.secondarydomain-name server-address-list file-nameThe
secondarycommand makes the local server a slave server for the domain identified bydomain-name. Theserver-address-listcontains the IP address of at least one other authoritative server for this domain. Multiple addresses can be provided in the list, but at least the master server’s address should be provided. The local server will try each server in the list until it successfully loads the name server database. The local server transfers the entire zone file and stores all of the data it receives in a local file identified byfile-name. After completing the transfer, the local server answers all queries for information about the domain with complete authority.cache .file-nameThe
cachecommand points to the file used to initialize the name server cache with a list of root servers. This command starts with the keywordcache, followed by the name of the root domain (.), and ends with the name of the file that contains the root server list. This file is usually named cache.dns on systems running the Microsoft DNS server software.BindSecondaries|NoBindSecondariesThis command provides zone transfer compatibility with Unix BIND 4 DNS servers. If any of the secondary servers for the Microsoft DNS Server are BIND 4 servers, use the
BindSecondariescommand for compatibility. If none of the secondary servers are BIND 4 servers, useNoBindSecondariesfor more efficient zone transfers.
A sample boot file is located in the %SystemRoot%system32dnssamples directory. That file, named BOOT, explains the syntax of the boot file commands as if you might build your own boot file. While that is possible, it is unlikely. The primary reason to use a boot file is to rapidly migrate an old BIND 4 Unix server to Windows Server 2003. In that case, you would start with an existing BIND 4 boot file such as the following one:
; ; BIND 4 boot file ; directory /etc/named primary example.com example.com.hosts primary 0.168.192.IN-ADDR.ARPA 192.168.0.rev secondary example.net 172.16.12.6 example.net.hosts secondary 16.172.IN-ADDR.ARPA 172.16.12.6 172.16.rev secondary example.org 172.22.1.3 example.org.hosts secondary 22.172.IN-ADDR.ARPA 172.22.1.3 172.22.rev primary 0.0.127.IN-ADDR.ARPA named.local cache . named.ca
Lines that begin with a semicolon are comments. Use a semicolon to
“comment out” unneeded lines and unsupported commands, such as the
directory command in this sample
file. (On a Windows DNS system the zone files are always located in the
%SystemRoot%system32dns directory. Therefore, the
directory command is not needed or
supported.) On the other hand, the BIND 4 file will not contain the
BindSecondaries or NoBindSecondaries command. If you need one of
those commands, you must manually add it to the file.
Most of the primary command
lines in the BIND 4 files can be used as is. Simply copy the zone files
from the old Unix server to the
%SystemRoot%system32dns directory and ensure that
the filename specified on each primary command is the name used for the
corresponding file copy. One exception to this is the primary command for the 0.0.127.IN-ADDR.ARPA
reverse zone, which is found in many BIND 4 boot files. That primary command is not needed for Windows
Server 2003 and should be commented out. The second to last line in the
sample file shows an example of this unneeded primary command.
BIND 4 secondary command lines
also require very little editing. Check that the address of the master
server specified in each secondary
command is still valid. Often, more than one server is migrated from
Unix to Windows at approximately the same time. Therefore, all server
addresses should be double-checked. If addresses have not changed, the
secondary commands can often be used
as is.
Finally, edit the cache command
to change the filename field to cache.dns. When the
boot file is to your liking, copy it to the
%SystemRoot%system32dns directory and give it the
filename boot.
These instructions assume that you are migrating from an existing BIND 4 server to a new Windows server and that you have decided to use the boot file. Generally, the boot file is not used and the configuration is built directly through the DNS console.