Chapter 4
Offsite Profiling
What is Offsite Profiling?
Offsite profiling is, as the name suggests, is gathering as much information as possible prior to visiting the target site. As with many things, the more preparation that occurs prior to the project, the higher the likelihood of success. Much of the information that will be useful is public, whether intentionally or not, and the methods described in this chapter will help you find it. A few things to attempt to determine prior to going onsite include the lingo and codes used by any radio user within the target, the make, model, and type of equipment used by the target, the frequencies that they are likely to use, and whether the guard force, if there is one, is contracted or are employees of the target.
What to Look For
To start, simply search the Web for the company name and some keywords related to scanner and radios. During this process, pay special attention to search results from scanner hobbyist forums. It is not unusual to find a local hobbyist has mapped out a company’s radio system and even made notes about lingo, company culture, and other valuable information. Johnny Long’s Google Hacking for Penetration Testers has many great tips and techniques that will be helpful during the process.
Recommended Search Terms
While searching for information on the target, enter the company name combined with one of the following keywords:
Press releases are often a useful resource for determining the details of a contract guard force and the radio equipment in use. Often, marketing departments do not consider security when releasing information. When a radio manufacturer or outsourced guard company wins a contract, they will want the world to know. Take a look at a few press release aggregation sites, and it becomes immediately clear that there is a great deal of valuable information there for the taking. Announcing that large company has chosen a particular radio product is perhaps a useful marketing tool; when making a purchasing decision it is helpful to know that others have chosen the same product. If you own a smaller business, and can’t afford to spend the time of money researching multiple products, then choosing the same product as a larger company may make sense. This information, however, is also valuable to the penetration tester or attacker. These press releases will often include specific information as to the type of gear purchased as well as any special features of the gear.
Tip
In the United States, the top five commercial grade two-way radio manufacturers are Motorola, Midland, Kenwood, Icom, and Vertex.
Aside from press release aggregation sites, there are many other ways to find these press releases. Industry magazines, Web sites, and other publications will commonly print or post press releases. Many of the major equipment manufacturers will also post press releases on their corporate Web sites. Of course, as with any other information that is sought, search engines are a great place to start. When a press release is discovered, it is essential to review the details. Be sure that the press release is not so old that new equipment has likely been purchased, and for target organizations with multiple sites, see if the press release is location specific. It won’t necessarily be helpful the know the radio equipment used in the organization’s west coast location if you are targeting the east coast facility.
Keep in mind that much like other equipments, a large amount of radio hardware is sold by resellers. Find out if there are any resellers near the target organization and scour their Web sites for press releases related to the target.
Social engineering, when performed in an effective manner, can also provide a wealth of useful information. Calling the target organization and posing as a radio salesperson can result in release of valuable information. Commonly, the facilities department will manage radio equipment. If the target has a physical security department, they may be tasked with radio procurement. Remember, before calling, you must gather as much information as possible. If you aren’t able to speak intelligently about the equipment you purport to sell, the ruse will likely be discovered.
Tip
When posing as a salesperson for purposes of social engineering, let the target do the talking. Ask open-ended questions such as:
• How many radio users does your organization have?
• What type of special features do you use or are you considering?
The answers to these questions and others are helpful when selling radio equipment, and are also helpful when profiling a target organization.
With rare exception, legally broadcasting on a frequency within the United States requires a license from the Federal Communications Commission (FCC). In addition to many other functions, the FCC ensures that the radio spectrum is used in the most efficient manner, and that multiple organizations or stations do not fight over the same frequency. It should come as no surprise that to keep everything organized, the FCC maintains a database of the licenses issued to use specific frequencies. This database includes information such as the frequency information as well as the license, including their location and contact information. What may, however, come as a surprise, is that this FCC database is available to the public (Figure 4.1). The catch is, and of course there is a catch, that the database is cumbersome and difficult to search and retrieve specific information.
Tip
The following link can be used to access the FCC database Web site: http://wireless2.fcc.gov/UlsApp/UlsSearch/searchAdvanced.jsp. If this link does not work you can also search for “FCC ULS advanced license search” to find the site.
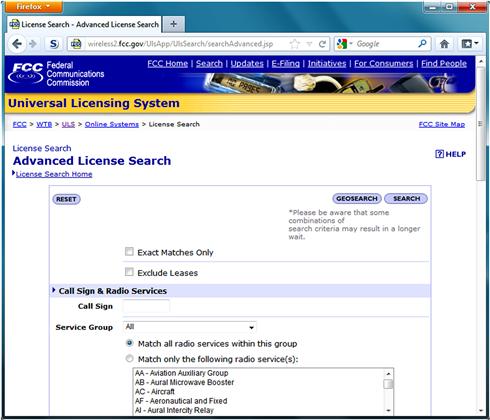
Figure 4.1 FCC Universal License Search (ULS) Advanced License Search Web Site
The private sector has come along and created resources to ease access to the information contained in the FCC database. Radioreference.com (Figure 4.2) and nationalradiodata.com (Figure 4.3) are two such resources.

Figure 4.2 The Radio Reference Web Site

Figure 4.3 The National Radio Data Web Site
Radio Reference, while a paid site, has many free areas which contain a wealth of information. National Radio Data offers a hobbyist rate which at the time of this writing is $29 per year.
Tip
When searching the FCC database or similar radio frequency databases, the authors often look up not only the current company name, but also any other names under which the company may have done business. This includes subsidiaries as well as partners and acquired companies, and also the names of companies from whom the target company may have acquired facilities. For example, if the target is the operation center of “Big Orange Bank” but the operation center used to be owned by “Big Green Bank,” search the sites for frequencies used by “Big Green Bank.” When one company acquires another company or their facilities, they rarely replace the radio equipment at that site. Oftentimes the same radio setup used by the previous company will continue to be used by the new company.
There are few things to keep in mind when searching for the frequencies in use by an organization. As discussed earlier, there are many radio equipment resellers. A large number of these resellers also provide maintenance for the equipment, and at times offer to provide frequencies to their Clients. In these cases, the frequency is licensed to the reseller and then leased to an organization.
Using RadioReference.com for Offsite Profiling
The following examples show how to use the RadioReference.com site to find information on the target. All of the following searches were performed using the free version of RadioReference.com.
For this example, we will assume you have been hired by Franklin County, in Ohio, to perform a physical penetration test of their data center. For this case Franklin County was chosen as an example as it is a county containing a large city in the state where authors live. To start off, go to frequency database on RadioReference.com, navigate to Ohio, and then Franklin County. Looking through the Franklin County section of the database you will see that Franklin County has two large trunked radio systems; one for public services and one for public safety. Studying both trunked systems will give you some interesting targets to monitor to gain information on the data center. Of specific interest are talk groups a17 and a19 on the public service trunked system (Figure 4.4). These talk groups are labeled “County Data Center Channel 1” and “County Data Center Channel 2,” and are likely, based solely on their names, to provide useful information regarding the data center. The page also contains all the information needed to program this trunked system into a trunking capable scanner and monitors these two talk groups for intelligence.
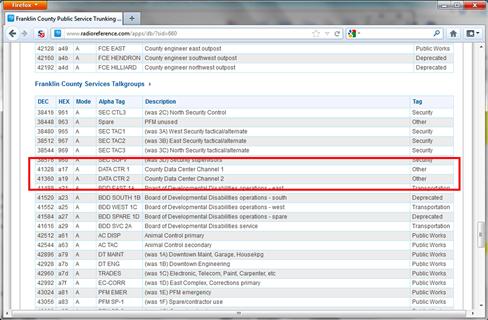
Figure 4.4 RadioReference.com Example
RadioReference.com and the FCC database have the ability to show which transmitters are in a given geographic area. The authors often use this feature when they cannot find the frequencies used by a target organization by searching for the company name. When performing geographic based searches, the authors prefer to use the RadioReference site because they have a functional tie in with Google Maps allowing you to visually see where the FCC licenses are located on a map. This feature can be located on the Radio Reference Frequency Databases page. At the time of writing, the search was under the Search FCC Database section of the page, with the specific search being labeled as “FCC License Proximity Search.” If you know the latitude and longitude of the target organiztion, or a point near the target organization, you can enter that directly into search function using the WGS84 GPS datum format (IE, 30.29128 −97.73858). Setting the search distance to two miles is a good starting point which can then be adjusted up or down depending on the number of transmitters in the area, size of the target property, and accuracy of the latitide and longitude data at hand. If the latitude and longitude of the site is unknown, click “Launch Location Tool Helper.” The link to the “Location Helper” tool icon is located next to the data entry boxes (shown in Figure 4.5) and can be a very helpful tool.
Figure 4.5 Launch Location Tool Helper Icon
Figure 4.6 shows the results of a geographic search in downtown Cleveland, Ohio. If, using this method, a licensee on the target property is found, the name of the licensee should be used to run additional name-based searches. This will often turn up additional frequency information for remote site or licenses that are registered at a different address.
Note
The addresses in the search can be the licensee’s address or the location of the antenna tower licensed to use the frequency. Always try to use a database that shows the antenna location when looking for the frequencies used at a specific site. This is especially helpful for multi-location businesses as often multiple transmitters over a 75 mile area are covered with a single, variably placed license.
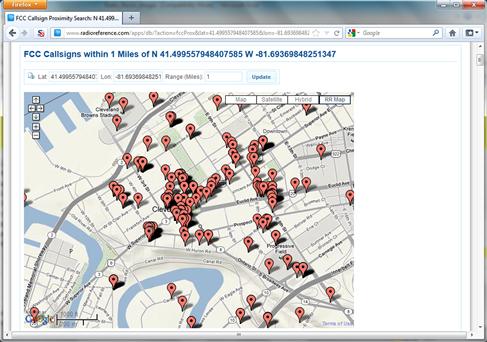
Figure 4.6 Example FCC License Proximity Search Results for Downtown Cleveland, Ohio
Case Study: Offsite Profiling
Physical penetration test at a ship dock.
The following story is, well, mostly true. Because we are professional security people, we cannot disclose details of our Clients’ systems nor their names. All the events in this case study happened, however we drew from events from multiple penetration assessments to create this scenario.
The penetration team’s goal was to gain access to the ship dock, specifically the high-security area where the ships docked, and deliver a special package to prove we were there—a loaf of bread. In addition to the usual gates around the perimeter of the property, the actual docks had additional security controls: a second fence, gates, cameras, automated ID card reader checkpoints, and guards, to prevent people from moving undetected between the ships and the mainland. We noted that the ID card readers had no controls in place to prevent tailgating, so it would be possible to sneak in if security wasn’t watching the gates.
We began offsite profiling by Google searching the name of the company and common radio terms. This turned up nothing of interest. Next, we searched for the company name on Radio Reference (www.radioreference.com), and still turned up nothing. Next we navigated to the state and county inside the Radio Reference Frequency Database (Figure 4.7).
Figure 4.7 Radio Reference Frequency Database Page for King County Washington
From here we opened the Businesses link under Other Agencies and reviewed the companies to see if any matched our Client (Figure 4.8). Sometimes by manually reviewing the businesses in the area, we will find a business whose name is close to or related to the target business.

Figure 4.8 Radio Reference Frequency Database Businesses Listings
After reviewing this page, the Client’s name, or a related name, still did not show up. It’s important to note that the Businesses listing in this section mostly includes only large business and attractions. Next we searched all the FCC licenses for businesses in the area, and again turned up nothing related to our target.
Searching for FCC Licenses for Businesses
To search all the FCC licenses for businesses in the area, it’s necessary to navigate back to the County level in the database and open the FCC Licensees tab. From here select Display All FCC Licenses for XXX County. This will open up a page displaying all FCC licenses in the area. By default this view only shows the public safety licenses in the area. To display the businesses in the county turn on the Business Conv and Business Trunked filters at the top of the page. If you want to only see the businesses, turn disable showing the public safety entries by turning off the Public Safety Conv and Public Safety Trunked filters (Figure 4.9). This will usually create a very long list. If you have a subscription to Radio Reference you can download this data to Excel using the Downloads and Reports tab. Next you can use Excel, of other spreadsheet or database tools, to search the information. In the downloaded file, GB, GJ, GS, GO, GU, GX, IG, IK, LN, LR, QT, YB, YG, YI, YJ, YK, YS, and YX are the tags used for Business licenses. By far analyzing this data offline is the recommended approach to take. If you do not have a subscription, you will need to search the information online. Licenses are listed alphabetically, start by navigating to the page where the company name should appear to see if a close name can be found.

Figure 4.9 FCC Licenses Issued to Businesses in King County Washington
Tip
If you do not find the target listed in the FCC database, you can also set up the database to display expired FCC licenses by turning on the Expired/Canceled Licenses filter. The authors have encountered a couple of occasions where companies are still operating on expired licenses. If this is discovered, be sure to notify the Client because they are illegally transmitting on those frequencies.
Widening our Radio Reference search to the general area turned up about two dozen shipping companies and dock names, but none of them matched the Client name. We started searching press releases to see if there was any evidence of a relationship between any of the companies we found and our Client. When we look for press release information, our first tool is Google, but we also make use of the Client’s Web site, and any affiliated companies we know they work with. If we know of any integrators in the area, we also search their Web sites for press releases about business dealings they may have with the Client company.
For this Client, these basic searches did not turn up anything. This was very odd, because large sites with lots of logistical needs invariably employ a radio system to help coordinate activities.
Unable to identify a relationship between the Client and the companies in the area, we used the map feature on Radio Reference. We used this feature to find transmitters in the area, and located a transmitter tower on the Client site. But the licensee did not match the name of our Client. Doing further research turned up information that established the connection we were looking for: the FCC license was still in the original name of the company, which had changed as the result of a buyout. The parent company, our Client, had never bothered to change the name on the license. This is not an uncommon situation to run into.
Once we had established the connections, we now had useful information that we could act on. Thanks to Radio Reference, we knew they had a conventional four-channel radio system. In the Radio Reference database, Channel 4 was labeled “security.” The other three channels were used for operations.
Armed with this information, we arrived onsite and programmed all four channels into our scanner and started listening. Before long, we were able to confirm that Channel 4 was in use by security. We monitored this channel. Radio chatter confirmed that there were guards stationed at the main gate, but we never heard any transmissions from the second gate.
Using Google Maps, we got an aerial view of the property, which showed two roads leading into the property. Both roads were gated at the perimeter. One clearly had a guard booth; the other, we couldn’t tell.
Security appeared to have one mobile unit, which used an SUV to cover the grounds. This unit did rounds when ships were not at dock. However, when a ship was at the dock, we were able to infer from the radio chatter that it parked and watched the “high-security gate” leading to the dock. Additionally, we heard two or three guards on foot, depending on the time of day.
From the map, we knew that the property also had a number of train tracks leading into it. From what we could tell, the rail yard area was patrolled by the mobile unit when it was doing rounds. So, when a ship was docked, the train track entrance was not patrolled. Furthermore, while we were at the site, we could see that the train tracks were not gated. Our reconnaissance found that the mobile unit patrolled this area as part of its rounds. This meant that when a ship was docked, the train tracks were not patrolled. And although the dockyard had a fence around it, most of the dockyard was open via the train entrance, which did not have a fence or gate.
While doing onsite reconnaissance, we saw security cameras, and the area was lit with flood lights and street lights, but coverage appeared to be mainly focused at the gates and water. On our map, we noted the areas that had camera coverage, as well as blind spots, for later debriefing with our Client. After the test, we would provide the Client with recommendations on where to place additional cameras to fill in these gaps.
By monitoring the other channels, we could also hear the operations side of the dock and learn when ships were coming and going. We could also learn when ship crew where leaving for shore leave, and when they were supposed to report back. All of these activities were coordinated, so usually we started hearing radio chatter well before the ship crews would go ashore. By monitoring the guards at the perimeter gate, we could learn when ship crews were coming back. Once they passed through the perimeter, the gate guards would notify the mobile unit of the inbound arrivals heading to the docks, so that there would be someone at the inner gate to get them through.
We also observed the type of equipment and outfits being worn by the workers and dock hands so we could get similar gear. The company we were working for is very concerned about safety, so before we arrived onsite we were required to purchase extra safety gear and required to wear it while on property. Coincidently, we had been required to wear this same type of safety gear while doing a physical penetration test at another site so it was already dirty and broken in. This helped us to blend in. We would have purchased similar looking gear locally had we needed.
Armed with this information, we were able to plan an approach to gain access to the facility. We waited for a ship to come into port. By listening to their radio chatter, we could hear them preparing for the arrival of a ship several hours in advance. Initial chatter would begin to happen about 12–24 h before a ship’s arrival in port. Chatter on the operations channels increased as the time of arrival drew near. Had we needed, we could have learned everything about their procedures for loading and unloading this way, as well as kept tabs on where they were in the process. Anticipating the ship’s arrival, the guard in the mobile unit had a habit of parking in a position where they could observe the inner gate a short time before the ship docked. When in this position, they were not able to monitor the perimeter at the train tracks. This was the time when we would be able to penetrate the perimeter by following the rail lines. Once inside the perimeter, we found a hiding spot where we could watch traffic going in and out of the higher security area, and waited for an opportunity to enter ourselves.
Given the attention on this area we didn’t feel a technical attack (lock picking, fencing climbing, etc.) would be the best way to go. So we decided to try to use a stealth approach, augmented with social engineering (our costumes and equipment, to allow us to blend in and look like employees, and knowledge of their processes and terminology that we had gained through radio surveillance) in case we were detected or needed to reveal ourselves. We had heard on the operations channel that they were going to bring the cargo onto the ship in an hour. From listening, we learned the cargo was a mix of shipping containers and smaller items inside semi-trailers.
We went to the cargo area, and found an unlocked trailer. This part of the property didn’t seem to have guard coverage at the moment. We entered through a side door in the trailer, which was fortuitous because that door happened to have an interior handle which allowed us to open the door from the inside. The rear cargo doors did not appear to have a way to unlock them from the inside.
We hid out in the cargo area and waited. Around 90 min later, they started moving the cargo.
We could verify this by the radio traffic (using headphones to keep our noise down) and noises heard in the cargo waiting area. After a while, our truck started up. It drove for about 5 min, then stopped. Once it stopped we waited several minutes until it was quiet. Once we felt safe, we carefully opened the side door, looked around to make sure no one was in the area, and exited the trailer. At this point, we proceeded to obtain evidence that we were inside the target area by taking pictures. We also found a place to leave the loaf of bread.
Having accomplished our objective, we exited the area. This was accomplished by simply walking out the gate. The guards assumed that we were dock hands, and did not check our IDs. We learned later that they were supposed to perform an ID check, but had fallen out of this habit when the ship crew wasn’t present and only “trusted” dock hands were present. With the number of personnel employed at the dock, and turnover in the workforce, it was easy to pass by without raising suspicion.
Remediation and Lessons Learned
As a result of our successful penetration, the dock company became far more diligent about having people scan ID cards to get in and out of the secure area. The benefit that really sold them here is a matter of life safety in an emergency response situation. Knowing how many people are in an area, in the event an accident occurred is very beneficial information. If you send first responders into a fire, it’s great if you can tell them we have X number of people unaccounted for, instead of “a few” people.
We recommended the Client install turn styles or other anti-tail gating devices to prevent multiple persons from entering or exiting on one card swipe.
The Client made changes so the mobile patrol remained mobile even when ships where in dock.
The Client set up a video system that could monitor the secure dock entrance, so the mobile unit was no longer required to monitor that gate.
Additionally, we recommended the Client install a smart video system to watch the train tracks and automatically notify the guards if the system sees people. This was also a life safety issue. In the past, there had been incidents with unauthorized persons wondering onto the tracks, and getting into the facility. While preventing their entry into the facility was obviously desirable, it was also important to remove them from the train tracks as fast as possible to avoid being hit by a train.
Lessons:
![]() Perimeter security. If there is an area that is impractical to fence and gate, it diminishes the security provided by whatever perimeter fencing you do have. Unsecured perimeter areas should be subject to increased monitoring.
Perimeter security. If there is an area that is impractical to fence and gate, it diminishes the security provided by whatever perimeter fencing you do have. Unsecured perimeter areas should be subject to increased monitoring.
![]() Cameras and lighting. We noted on our map the locations and coverage areas of all the cameras and lights, and made recommendations to the Client to cover blind areas, particularly in the vicinity of the train yard, where the exposed perimeter allowed us to enter the site undetected.
Cameras and lighting. We noted on our map the locations and coverage areas of all the cameras and lights, and made recommendations to the Client to cover blind areas, particularly in the vicinity of the train yard, where the exposed perimeter allowed us to enter the site undetected.
![]() Lax security posture. Security staffs need to establish and follow procedures closely, particularly at gates and other checkpoints. This is a constant battle to keep people following process. Without external reinforcement of process, it is simply human nature for people to relax as the job becomes routine, and this leads to taking shortcuts. First, we recommend to automate process where possible, because machines are much more reliable than people when it comes to following a process exactly the same way every time. When a person is required to follow a process repeatedly, it becomes routine, and soon the person stops thinking. We find it preferable for the human elements in the security chain to think, and so we recommend reserving them for tasks that require thinking and judgment, which are domains currently still better suited to human beings. To the extent that people do need to adhere to process, spot checks and audits are helpful. For Clients that are concerned about this, we help them establish re-occurring physical penetration tests every quarter or so to test the security force. If they know they are being tested they tend to maintain a more ready posture. Finally, we recommend regular training and drills. When we run into cases of a laxed guard force the first thing we recommend is more training, and not firing the guards. Firing the guards and bringing in new ones who will also not be trained doesn’t fix the problem.
Lax security posture. Security staffs need to establish and follow procedures closely, particularly at gates and other checkpoints. This is a constant battle to keep people following process. Without external reinforcement of process, it is simply human nature for people to relax as the job becomes routine, and this leads to taking shortcuts. First, we recommend to automate process where possible, because machines are much more reliable than people when it comes to following a process exactly the same way every time. When a person is required to follow a process repeatedly, it becomes routine, and soon the person stops thinking. We find it preferable for the human elements in the security chain to think, and so we recommend reserving them for tasks that require thinking and judgment, which are domains currently still better suited to human beings. To the extent that people do need to adhere to process, spot checks and audits are helpful. For Clients that are concerned about this, we help them establish re-occurring physical penetration tests every quarter or so to test the security force. If they know they are being tested they tend to maintain a more ready posture. Finally, we recommend regular training and drills. When we run into cases of a laxed guard force the first thing we recommend is more training, and not firing the guards. Firing the guards and bringing in new ones who will also not be trained doesn’t fix the problem.
![]() Inadequate guard coverage. The mobile unit performing double duty at the inner dock gate was a cost-saving measure that left the Client vulnerable. When the mobile unit needed to be at the gate, it left the train yard unguarded. Better coordination with the foot patrol potentially could have helped remediate this hole. Additional lighting and cameras would have provided additional layers of security, further strengthening the perimeter hole. We recommended a smart video system, which can detect humans over other items automatically, which eliminates the need for a human to monitor the cameras. Even the best trained person will tune out after watching a video screen for a while. This frees the human to perform more valuable duties. Wherever possible, we like to recommend replacing humans performing non-thinking tasks with technology that is more reliable, while allowing that person to do something more rewarding.
Inadequate guard coverage. The mobile unit performing double duty at the inner dock gate was a cost-saving measure that left the Client vulnerable. When the mobile unit needed to be at the gate, it left the train yard unguarded. Better coordination with the foot patrol potentially could have helped remediate this hole. Additional lighting and cameras would have provided additional layers of security, further strengthening the perimeter hole. We recommended a smart video system, which can detect humans over other items automatically, which eliminates the need for a human to monitor the cameras. Even the best trained person will tune out after watching a video screen for a while. This frees the human to perform more valuable duties. Wherever possible, we like to recommend replacing humans performing non-thinking tasks with technology that is more reliable, while allowing that person to do something more rewarding.
