Introduction
There’s a reason most Android geeks have such disdain for the other major smartphone operating system. The iPhone shackles the user, with its closed source code and ecosystem ruled with an iron fist. Android, on the other hand, frees developers to tear apart and rebuild nearly every aspect of the user’s experience with the operating system. Beyond the world of developer-created applications (apps), there is a vast universe of deeper customizations—custom kernels and ROMs, themes, CPU overclocks, and more.
In most cases, these tasks begin with gaining “root” access to your device. The goal of this book is to get you comfortable with the tools and vocabulary of Android hacking, to get you in the “root” mindset, and to point you towards the best online resources for expanding your knowledge even further.
First Things First: What Is XDA?
The XDA Developers (XDA) website, at http://www.xda-developers.com, is the largest smartphone community on the Internet. As the name implies, the site—launched in 2003—is a destination for developers. “XDA” was a line of phones based on Windows Mobile that were branded by O2 and developed by a small (at the time) Taiwanese manufacturer called High Tech Computer Corporation (HTC). According to XDA history:
It was these early O2 XDA devices that the founders of our site thought had much more potential than the sellers O2 and HTC were giving them credit for. With their geeky hats on they cracked them open and began to develop them beyond the standard fairly boring branded versions. To spread the word, they set up a small website and naturally called it xda- developers. In the early days they had less than a dozen members (2003).
As more and more phones were released, the XDA administrators launched a new forum for each one. The site was built around the spirit of community and cooperation. XDA itself is not an organization of developers. The site is merely a sandbox where developers congregate.
From those early few members, XDA became known as the go-to source for information on how to make phones do more great stuff and how to fix a phone that was otherwise broken. As more people were attracted to the site, enthusiasts were given a home to share the awesomeness of mobile device development. From that early core of a few dozen enthusiasts, geeks and developers, the XDA website now receives more than ten million visitors per month and thousands of informative posts every day.
The material in this book draws heavily on the work done by the fantastic community at XDA. The book combines the work of the XDA community, my technical teaching experience, and my work as an Android developer to provide a launching point for the budding Android hacker.
The XDA forums have become the foremost Internet destination for information about mobile devices: how to fix them, how to hack them and, generally, how to make them better than the manufacturers make them. http://forum.xda-developers.com is laid out in forums dedicated to individual devices. Each forum contains a core group of people who work with and love the device, as well as thousands of helpful individuals on the same journey as you. When you visit XDA, you can use the “Forums” link and navigate through the forums to find your specific device (see Figure 1).
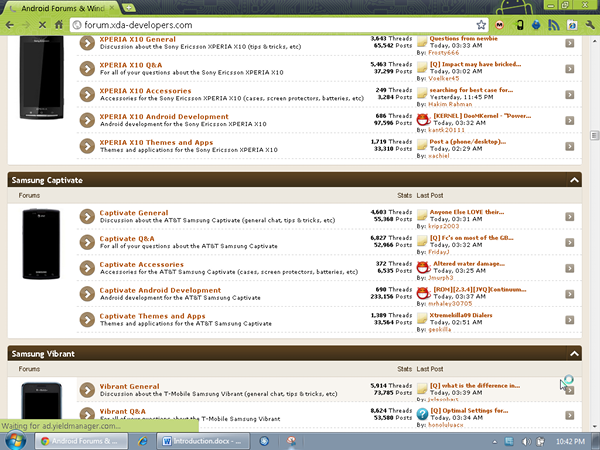
Figure 1: The device-specific forums at http://forum.xda-developers.com
The Dragons that Lie Ahead
The freedom offered to you when your device is rooted is liberating. It affords you such wonders as:
• complete backup of all applications and their data
• Google Apps, if they were not included with your device
• overclocking your device (speeding it up to run faster and better)
• fixing manufacturer issues, such as GPS errors or call dropping
• wireless tethering to create a quickie “hotspot”
• completely changing and customizing the device interface.
All of this and more is available to those who step out on a limb and root their Android device. However, there are two caveats to keep in mind before you get started.
You should know before you read any further that by even thinking about rooting your device you may have voided your warranty.
Not really, of course, but attempting any of the customizations that you read about in this book will void your manufacturer’s warranty and any insurance warranty you may have purchased. Manufacturers and mobile service carriers sell millions of devices every week. For every device they sell, they have to support a certain percentage of those devices that are defective. As far as your carrier and OEM are concerned, when you mess with the stuff they have spent millions on making, their responsibility to support you ends.
There are no exceptions to this rule. Most OEMs, carriers and support companies will instantly reject any sort of support or replacement request when they find the device has had its software, firmware or hardware altered outside normal parameters. Even so-called “developer” devices, such as the Nexus range, cease to be supported when you start developing on them.
The second big catch is that you can do permanent irreversible damage to your device. In the parlance of the mobile device hacker, this is known as “bricking” because it turns your $400 smartphone into something as useful as a brick. Some of the exploits that are used to gain “root” access are edge-of-the-knife procedures that can completely ruin a device if the tiniest mistake is made.
Some devices are more robust than others and are less likely to be bricked. The original Motorola Droid from Verizon, for instance, was known for being almost impossible to permanently brick. But even the venerable Droid has been bricked by hasty or extremely adventurous hackers.
Many of this book’s tutorials, whether to achieve root or other customizations, require you to be familiar with a command prompt window, such as the one shown in Figure 2. If you are a typical Windows user, you probably do not have much experience with the command line. Although you can find shortcuts, scripts, and workarounds, I still recommend you get comfortable with the command line. By the time you make it through Chapter 4, you’ll be a command prompt pro.
Figure 2: The command prompt window
Most of the steps in this book assume that you have the ability to connect your device to your computer and that your computer has all the drivers it needs to communicate with your device. If you are unsure of this, you may need to read through Appendix A to get your phone connected to your computer. Your best shot at getting your particular device connected to your computer is to do a quick search of the XDA forums to locate the drivers. Don’t do all the hard work of locating the right drivers if one of the wonderful people at XDA has already located them.
The other dragon that can gobble up the new hacker is that most Android device hacking requires the Software Development Kit (SDK) to be installed on your computer. In Appendix A, I walk you through setting up the Android SDK and point out the few pieces that you actually need for hacking your Android device.
For many devices, much of the risk has been removed by developers and hackers who have created scripts, one-click methods, and helper tools to root and customize your device. The XDA forums are an awesome community of curious and extremely intelligent people that can get you out of most dead ends when hacking your phone.
In order to access the wealth of information undoubtedly available for your device, you must first navigate to your device-specific forum. Finding the dedicated forum for your device is a simple task that can be accomplished several ways. While you could comb through the forum index and find your device manually, this can become quite frustrating given the extremely large number of device forums.
An easier method to find your device-specific forum is to use the “Find Your Device” box in the upper-right hand corner of the screen, see Figure 3 (top). Simply type the name of your device, or even a few letters, and you will be presented with a list of all matching device forums. Alternatively, you can jump to devices from a particular manufacturer by using the “Devices by OS or Manufacturer” drop-down menu at the top center of the page, see Figure 3 (bottom).
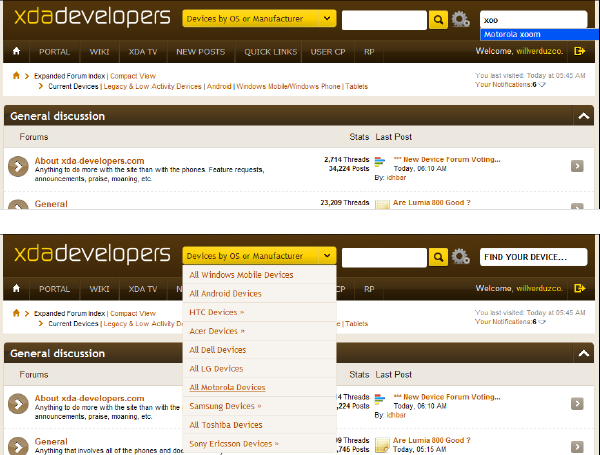
Figure 3: Searching for your device by name (top) or by manufacturer (bottom)
If you decide to continue to root your device, customize it and slip the surly bonds of OEM tyranny, you must proceed at your own risk. You have to accept the very real possibility that you could do your device permanent harm or even brick it. John Wiley & Sons, XDA Developers and I are not responsible if you turn a beautiful shiny Android device into the most expensive paperweight ever.
You have been warned.
Who This Book Is For
This book is for the Android user who wants to get started with hacking Android devices. If you have heard of “rooting” an Android device and wonder what it means and how it is done, then this book is for you. This book is also for the user who wants to get more out of their Android device and increase its life and functionality.
What This Book Covers
This book covers general Android knowledge and mobile device concepts. It also includes chapters that give the reader the skills necessary to begin hacking and exploring on their own. It covers installing the tools needed, such as the Android SDK. Later chapters cover the rooting procedures for specific devices. Although devices, and Android itself, change very quickly, reading a walkthrough can prepare you for what you can expect in rooting your device.
How This Book Is Structured
This book is divided into two parts. The first part gives a basic overview of Android and the shell. Shell command skills will be the core of your Android-hacking career. The second part gives example walkthroughs on representative devices, from the very tightly locked to the wide open. Some devices from major manufacturers are given a detailed walkthrough to demonstrate how the skills learned earlier can be applied. The appendix walks you through getting your computing environment set up to hack Android.
What You Need to Use This Book
You need a PC with Windows (XP or later), a free USB port (USB hubs are not generally recommended), and an Internet connection. You need to be familiar with navigating the XDA forums in order to access the latest updates and information. Android hacking can be done very well from computers running Mac or Linux but this book focuses on the PC user. You need an Android device if you wish to follow along with the examples and tutorial walkthroughs.
