Chapter 3
Risk Identification, Monitoring, and Analysis (Domain 3)
THIS CHAPTER COVERS THE FOLLOWING SSCP EXAM OBJECTIVES:
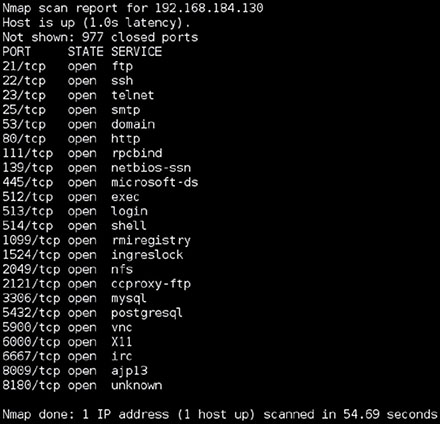
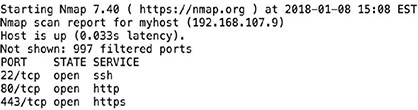
HAL Systems recently decided to stop offering public NTP services because of a fear that its NTP servers would be used in amplification DDoS attacks. What type of risk management strategy did HAL pursue with respect to its NTP services? Tom is responding to a recent security incident and is seeking information on the approval process for a recent modification to a system’s security settings. Where would he most likely find this information? Alex wants to use an automated tool to fill web application forms to test for format string vulnerabilities. What type of tool should he use? For questions 4–6, please refer to the following scenario. Henry is the risk manager for Atwood Landing, a resort community in the midwestern United States. The resort’s main data center is located in northern Indiana in an area that is prone to tornados. Henry recently undertook a replacement cost analysis and determined that rebuilding and reconfiguring the data center would cost $10 million. Henry consulted with tornado experts, data center specialists, and structural engineers. Together, they determined that a typical tornado would cause approximately $5 million of damage to the facility. The meteorologists determined that Atwood’s facility lies in an area where they are likely to experience a tornado once every 200 years. Based upon the information in this scenario, what is the exposure factor for the effect of a tornado on Atwood Landing’s data center? Based upon the information in this scenario, what is the annualized rate of occurrence for a tornado at Atwood Landing’s data center? Based upon the information in this scenario, what is the annualized loss expectancy for a tornado at Atwood Landing’s data center? Earlier this year, the information security team at Jim’s employer identified a vulnerability in the web server that Jim is responsible for maintaining. He immediately applied the patch and is sure that it installed properly, but the vulnerability scanner has continued to incorrectly flag the system as vulnerable because of the version number it is finding even though Jim is sure the patch is installed. Which of the following options is Jim’s best choice to deal with the issue? Which NIST special publication covers the assessment of security and privacy controls? Saria’s team is working to persuade their management that their network has extensive vulnerabilities that attackers could exploit. If she wants to conduct a realistic attack as part of a penetration test, what type of penetration test should she conduct? Tom enables an application firewall provided by his cloud infrastructure as a service provider that is designed to block many types of application attacks. When viewed from a risk management perspective, what metric is Tom attempting to lower? Jim uses a tool that scans a system for available services and then connects to them to collect banner information to determine what version of the service is running. It then provides a report detailing what it gathers, basing results on service fingerprinting, banner information, and similar details it gathers combined with CVE information. What type of tool is Jim using? What term describes software testing that is intended to uncover new bugs introduced by patches or configuration changes? Mike recently implemented an intrusion prevention system designed to block common network attacks from affecting his organization. What type of risk management strategy is Mike pursuing? During a port scan, Lauren found TCP port 443 open on a system. Which tool is best suited to scanning the service that is most likely running on that port? When developing a business impact analysis, the team should first create a list of assets. What should happen next? In this image, what issue may occur because of the log handling settings?
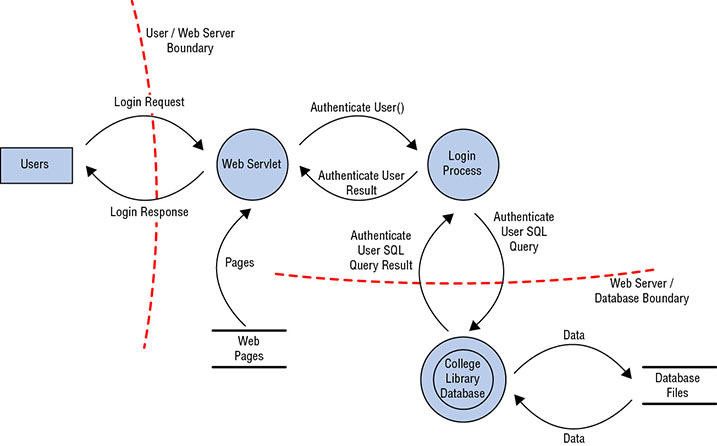
What message logging standard is commonly used by network devices, Linux and Unix systems, and many other enterprise devices? Ryan is a security risk analyst for an insurance company. He is currently examining a scenario in which a malicious hacker might use a SQL injection attack to deface a web server because of a missing patch in the company’s web application. In this scenario, what is the threat? Chris is responsible for his organization’s security standards and has guided the selection and implementation of a security baseline for Windows PCs in his organization. How can Chris most effectively make sure that the workstations he is responsible for are being checked for compliance and that settings are being applied as necessary? For questions 20–22, please refer to the following scenario. The company that Jennifer works for has implemented a central logging infrastructure, as shown in the following image. Use this diagram and your knowledge of logging systems to answer the following questions. Jennifer needs to ensure that all Windows systems provide identical logging information to the SIEM. How can she best ensure that all Windows desktops have the same log settings? During normal operations, Jennifer’s team uses the SIEM appliance to monitor for exceptions received via syslog. What system shown does not natively have support for syslog events? What technology should an organization use for each of the devices shown in the diagram to ensure that logs can be time sequenced across the entire infrastructure? Susan needs to predict high-risk areas for her organization and wants to use metrics to assess risk trends as they occur. What should she do to handle this? Tom is considering locating a business in the downtown area of Miami, Florida. He consults the FEMA flood plain map for the region, shown here, and determines that the area he is considering lies within a 100-year flood plain. What is the ARO of a flood in this area? Which of the following strategies is not a reasonable approach for remediating a vulnerability identified by a vulnerability scanner? Bruce is seeing quite a bit of suspicious activity on his network. It appears that an outside entity is attempting to connect to all of his systems using a TCP connection on port 22. What type of scanning is the outsider likely engaging in? Jim would like to identify compromised systems on his network that may be participating in a botnet. He plans to do this by watching for connections made to known command-and-control servers. Which one of the following techniques would be most likely to provide this information if Jim has access to a list of known servers? Susan needs to scan a system for vulnerabilities, and she wants to use an open source tool to test the system remotely. Which of the following tools will meet her requirements and allow vulnerability scanning? Jim is designing his organization’s log management systems and knows that he needs to carefully plan to handle the organization’s log data. Which of the following is not a factor that Jim should be concerned with? Kara used nmap to perform a scan of a system under her control and received the results shown here. Refer to these results to answer questions 30 and 31. If Kara’s primary concern is preventing eavesdropping attacks, which port should she block? If Kara’s primary concern is preventing administrative connections to the server, which port should she block? During a port scan, Susan discovers a system running services on TCP and UDP 137-139 and TCP 445, as well as TCP 1433. What type of system is she likely to find if she connects to the machine? After conducting a qualitative risk assessment of her organization, Sally recommends purchasing cybersecurity breach insurance. What type of risk response behavior is she recommending? What is the best way to provide accountability for the use of identities? Robin recently conducted a vulnerability scan and found a critical vulnerability on a server that handles sensitive information. What should Robin do next? Rolando is a risk manager with a large-scale enterprise. The firm recently evaluated the risk of California mudslides on its operations in the region and determined that the cost of responding outweighed the benefits of any controls it could implement. The company chose to take no action at this time. What risk management strategy did Rolando’s organization pursue? During a log review, Danielle discovers a series of logs that show login failures. What type of attack has Danielle discovered? During a third-party audit, Jim’s company receives a finding that states, “The administrator should review backup success and failure logs on a daily basis, and take action in a timely manner to resolve reported exceptions.” What is the biggest issue that is likely to result if Jim’s IT staff need to restore from a backup? For questions 39–41, please refer to the following scenario. Ben’s organization has begun to use STRIDE to assess its software and has identified threat agents and the business impacts that these threats could have. Now they are working to identify appropriate controls for the issues they have identified. Ben’s development team needs to address an authorization issue, resulting in an elevation of privilege threat. Which of the following controls is most appropriate to this type of issue? Ben’s team is attempting to categorize a transaction identification issue that is caused by use of a symmetric key shared by multiple servers. What STRIDE category should this fall into? Ben wants to prevent or detect tampering with data. Which of the following is not an appropriate solution? During a port scan of his network, Alex finds that a number of hosts respond on TCP ports 80, 443, 515, and 9100 in offices throughout his organization. What type of devices is Alex likely discovering? Alan is performing threat modeling and decides that it would be useful to decompose the system into the key elements shown here. What tool is he using? Image reprinted from CISSP (ISC)2 Certified Information Systems Security Professional Official Study Guide, 7th Edition © John Wiley & Sons 2015, reprinted with permission.
Which of the following is not a hazard associated with penetration testing? Nmap is an example of what type of tool? Which of the following is a method used to design new software tests and to ensure the quality of tests? When a Windows system is rebooted, what type of log is generated? What is the first step that should occur before a penetration test is performed? Bobbi is investigating a security incident and discovers that an attacker began with a normal user account but managed to exploit a system vulnerability to provide that account with administrative rights. What type of attack took place under the STRIDE threat model? For questions 50–53, please refer to the following scenario. Ann is a security professional for a midsize business and typically handles log analysis and security monitoring tasks for her organization. One of her roles is to monitor alerts originating from the organization’s intrusion detection system. The system typically generates several dozen alerts each day, and many of those alerts turn out to be false alarms after her investigation. This morning, the intrusion detection system alerted because the network began to receive an unusually high volume of inbound traffic. Ann received this alert and began looking into the origin of the traffic. At this point in the incident response process, what term best describes what has occurred in Ann’s organization? Ann continues her investigation and realizes that the traffic generating the alert is abnormally high volumes of inbound UDP traffic on port 53. What service typically uses this port? As Ann analyzes the traffic further, she realizes that the traffic is coming from many different sources and has overwhelmed the network, preventing legitimate uses. The inbound packets are responses to queries that she does not see in outbound traffic. The responses are abnormally large for their type. What type of attack should Ann suspect? Now that Ann understands that an attack has taken place that violates her organization’s security policy, what term best describes what has occurred in Ann’s organization? During a log review, Saria discovers a series of logs that show login failures, as shown here: What type of attack has Saria discovered? Ben is seeking a control objective framework that is widely accepted around the world and focuses specifically on information security controls. Which one of the following frameworks would best meet his needs? Alex is using nmap to perform port scanning of a system, and he receives three different port status messages in the results. Match each of the numbered status messages with the appropriate lettered description. You should use each item exactly once. Tony is developing a business continuity plan and is having difficulty prioritizing resources because of the difficulty of combining information about tangible and intangible assets. What would be the most effective risk assessment approach for him to use? Angela wants to test a web browser’s handling of unexpected data using an automated tool. What tool should she choose? Saria wants to log and review traffic information between parts of her network. What type of network logging should she enable on her routers to allow her to perform this analysis? Jim is working with a penetration testing contractor who proposes using Metasploit as part of her penetration testing effort. What should Jim expect to occur when Metasploit is used? You are completing your business continuity planning effort and have decided that you wish to accept one of the risks. What should you do next? For questions 62–64, please refer to the following scenario. During a port scan, Ben uses nmap’s default settings and sees the following results. If Ben is conducting a penetration test, what should his next step be after receiving these results? Based on the scan results, what operating system (OS) was the system that was scanned most likely running? Ben’s manager expresses concern about the coverage of his scan. Why might his manager have this concern? What is the formula used to determine risk? A zero-day vulnerability is announced for the popular Apache web server in the middle of a workday. In Jacob’s role as an information security analyst, he needs to quickly scan his network to determine what servers are vulnerable to the issue. What is Jacob’s best route to quickly identify vulnerable systems? During a review of access logs, Alex notices that Danielle logged into her workstation in New York at 8 a.m. daily but that she was recorded as logging into her department’s main web application shortly after 3 a.m. daily. What common logging issue has Alex likely encountered? What is the final step of a quantitative risk analysis? Carrie is analyzing the application logs for her web-based application and comes across the following string: ../../../../../../../../../etc/passwd What type of attack was likely attempted against Carrie’s application? Allie is responsible for reviewing authentication logs on her organization’s network. She does not have the time to review all logs, so she decides to choose only records where there have been four or more invalid authentication attempts. What technique is Allie using to reduce the size of the pool? During a penetration test of her organization, Kathleen’s IPS detects a port scan that has the URG, FIN, and PSH flags set and produces an alarm. What type of scan is the penetration tester attempting? Which type of business impact assessment tool is most appropriate when attempting to evaluate the impact of a failure on customer confidence? What type of vulnerabilities will not be found by a vulnerability scanner? Which of the following vulnerabilities is unlikely to be found by a web vulnerability scanner? Jim has been contracted to conduct a gray box penetration test, and his clients have provided him with the following information about their networks so that he can scan them: What problem will Jim encounter if he is contracted to conduct a scan from offsite?
![]() 3.1 Understand the risk management process
3.1 Understand the risk management process
![]() 3.2 Perform security assessment activities
3.2 Perform security assessment activities
![]() 3.3 Operate and maintain monitoring systems (e.g., continuous monitoring)
3.3 Operate and maintain monitoring systems (e.g., continuous monitoring)
![]() 3.4 Analyze monitoring results
3.4 Analyze monitoring results



Jan 31 11:39:12 ip-10-0-0-2 sshd[29092]: Invalid user admin from remotehost passwd=aaaaaaaa
Jan 31 11:39:20 ip-10-0-0-2 sshd[29098]: Invalid user admin from remotehost passwd=aaaaaaab
Jan 31 11:39:23 ip-10-0-0-2 sshd[29100]: Invalid user admin from remotehost passwd=aaaaaaac
Jan 31 11:39:31 ip-10-0-0-2 sshd[29106]: Invalid user admin from remotehost passwd=aaaaaaad
Jan 31 20:40:53 ip-10-0-0-254 sshd[30520]: Invalid user admin from remotehost passwd=aaaaaaae
Jan 31 11:39:12 ip-10-0-0-2 sshd[29092]: Invalid user admin from remotehost passwd=orange
Jan 31 11:39:20 ip-10-0-0-2 sshd[29098]: Invalid user admin from remotehost passwd=Orang3
Jan 31 11:39:23 ip-10-0-0-2 sshd[29100]: Invalid user admin from remotehost passwd=Orange93
Jan 31 11:39:31 ip-10-0-0-2 sshd[29106]: Invalid user admin from remotehost passwd=Orangutan1
Jan 31 20:40:53 ip-10-0-0-254 sshd[30520]: Invalid user admin from remotehost passwd=Orangemonkey
Status message
Description