Chapter 7
Systems and Application Security (Domain 7)
THIS CHAPTER COVERS THE FOLLOWING SSCP EXAM OBJECTIVES:
Lauren’s multinational company is planning a new cloud deployment and wants to ensure compliance with the EU GDPR. Which principle states that the individual should have the right to receive personal information concerning himself or herself and share it with another data controller? Tiffany needs to assess the patch level of a Windows 2012 server and wants to use a freely available tool to check the system for security issues. Which of the following tools will provide the most detail about specific patches installed or missing from her machine? Maria wants to deploy an anti-malware tool to detect zero-day malware. What type of detection method should she look for in her selected tool? Cameron is configuring his organization’s Internet router and would like to enable anti-spoofing technology. Which one of the following source IP addresses on an inbound packet should trigger anti-spoofing controls? As part of her malware analysis process, Caitlyn diagrams the high-level functions and processes that the malware uses to accomplish its goals. What is this process known as? The company that Lauren works for is making significant investments in infrastructure as a service hosting to replace its traditional data center. Members of her organization’s management have expressed concerns about data remanence when Lauren’s team moves from one virtual host to another in their cloud service provider’s environment. What should she instruct her team to do to avoid this concern? Lucca wants to prevent workstations on his network from attacking each other. If Lucca’s corporate network looks like the network shown here, what technology should he select to prevent laptop A from being able to attack workstation B?
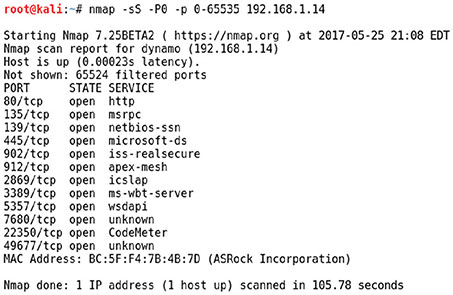
The company that Dan works for has recently migrated to a Service as a Service provider for its enterprise resource planning (ERP) software. In its traditional on-site ERP environment, Dan conducted regular port scans to help with security validation for the systems. What will Dan most likely have to do in this new environment? While investigating a malware infection, Lauren discovers that the hosts file for the system she is reviewing contains multiple entries as shown here: Why would the malware make this change? Geoff is responsible for hardening systems on his network and discovers that a number of network appliances have exposed services including telnet, FTP, and web servers. What is his best option to secure these systems? Tim needs to lock down a Windows workstation that has recently been scanned using nmap with the results shown here. He knows that the workstation needs to access websites and that the system is part of a Windows domain. What ports should he allow through the system’s firewall for externally initiated connections?
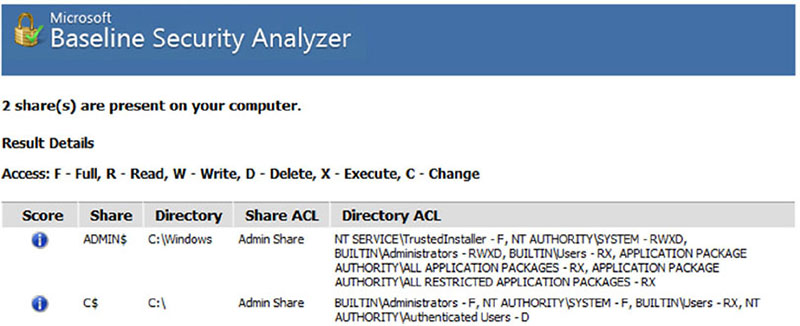
What major issue would Charles face if he relied on hashing malware packages to identify malware packages? As part of her system hardening process for a Windows 10 workstation, Lauren runs the Microsoft Baseline System Analyzer. She sees the following result after MBSA runs. What can she determine from this scan?
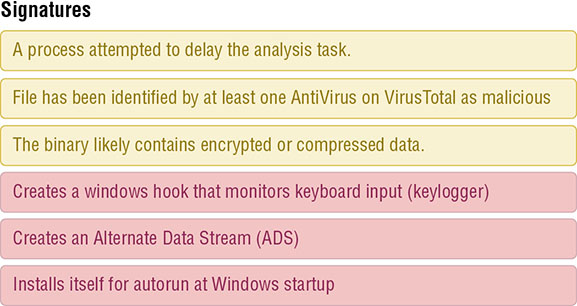
Susan is reviewing files on a Windows workstation and believes that cmd.exe has been replaced with a malware package. Which of the following is the best way to validate her theory? Chris wants to prevent users from running a popular game on Windows workstations he is responsible for. How can Chris accomplish this for Windows 10 Pro workstations? Ian’s company has an internal policy requiring that it perform regular port scans of all of its servers. Ian has been part of a recent effort to move his organization’s servers to an infrastructure as a service provider. What change will Ian most likely need to make to his scanning efforts? Isaac wants to prevent hosts from connecting to known malware distribution domains. What type of solution can he use to do this without deploying endpoint protection software or an IPS? Senior management in Adam’s company recently read a number of articles about massive ransomware attacks that successfully targeted organizations like the one that Adam is part of. Adam’s organization already uses layered security solutions including a border IPS, firewalls between network zones, local host firewalls, antivirus software, and a configuration management system that applies recommended operating system best practice settings to their workstations. What should Adam recommend to minimize the impact of a similar ransomware outbreak at his organization? Lauren’s screenshot shows behavioral analysis of the executed code. From this, we can determine that the tool she used is a dynamic analysis sandbox that runs the malware sample to determine what it does while also analyzing the file.
Questions 20 through 22 refer to the bare-metal virtualization environment shown here. What component is identified by A in the image? What component is identified by B in the image? What component is identified by C in the image? Frank discovers a missing Windows security patch during a vulnerability scan of a server in his organization’s data center. Upon further investigation, he discovers that the system is virtualized. Where should he apply the patch? Mike runs a vulnerability scan against his company’s virtualization environment and finds the vulnerability shown here in several of the virtual hosts. What action should Mike take?
During a recent vulnerability scan, Ed discovered that a web server running on his network has access to a database server that should be restricted. Both servers are running on his organization’s VMware virtualization platform. Where should Ed look first to configure a security control to restrict this access? Which one of the following protocols might be used within a virtualization platform for monitoring and managing the network? Don completed a vulnerability scan of his organization’s virtualization platform from an external host and discovered the vulnerability shown here. How should Don react?
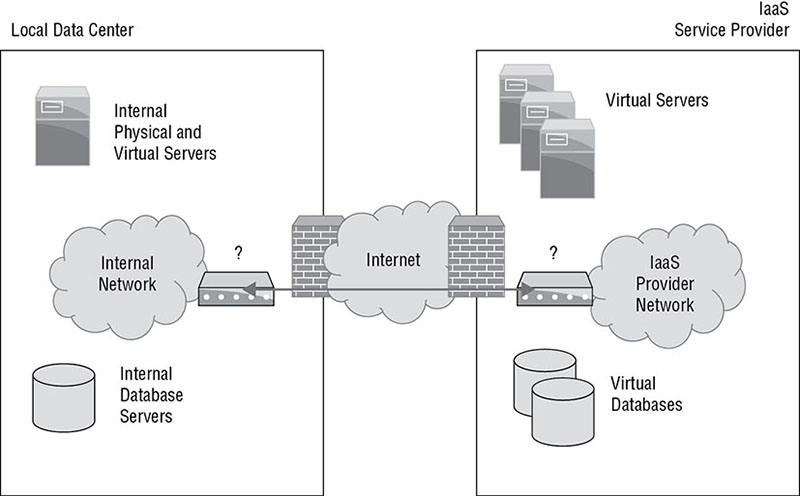
While conducting a vulnerability scan of his organization’s data center, Renee discovers that the management interface for the organization’s virtualization platform is exposed to the scanner. In typical operating circumstances, what is the proper exposure for this interface? Angela wants to understand what a malware package does and executes it in a virtual machine that is instrumented using tools that will track what the program does, what changes it makes, and what network traffic it sends while allowing her to make changes on the system or to click on files as needed. What type of analysis has Angela performed? Derek sets up a series of virtual machines that are automatically created in a completely isolated environment. Once created, the systems are used to run potentially malicious software and files. The actions taken by those files and programs are recorded and then reported. What technique is Derek using? Ian is reviewing the security architecture shown here. This architecture is designed to connect his local data center with an IaaS service provider that his company is using to provide overflow services. What component can be used at the points marked by question marks to provide a secure encrypted network connection?
Which one of the following statements is true about virtualized operating systems? While reviewing output from netstat, John sees the following output. What should his next action be? As Lauren prepares her organization’s security practices and policies, she wants to address as many threat vectors as she can using an awareness program. Which of the following threats can be most effectively dealt with via awareness? Which one of the following mobile device strategies is most likely to result in the introduction of vulnerable devices to a network? Jarett needs to protect an application server against resource exhaustion attacks. Which of the following techniques is best suited to surviving a large-scale DDoS attack? Jennifer is an Active Directory domain administrator for her company and knows that a quickly spreading botnet relies on a series of domain names for command and control and that preventing access to those domain names will cause the malware infection that connects to the botnet to fail to take further action. Which of the following actions is her best option if she wants to prevent off-site Windows users from connecting to botnet command-and-control systems? Several employees will need to travel with sensitive information on their laptops. Martin is concerned that one of those laptops may be lost or stolen. Which one of the following controls would best protect the data on stolen devices? For questions 39–41, please refer to the following scenario. Ben is an information security professional at an organization that is replacing its physical servers with virtual machines. As the organization builds its virtual environment, it is decreasing the number of physical servers it uses while purchasing more powerful servers to act as the virtualization platforms. The IDS Ben is responsible for is used to monitor communications in the data center using a mirrored port on the data center switch. What traffic will Ben see once the majority of servers in the data center have been virtualized? The VM administrators recommend enabling cut and paste between virtual machines. What security concern should Ben raise about this practice? Ben is concerned about exploits that allow VM escape. What option should Ben suggest to help limit the impact of VM escape exploits? Michael is responsible for forensic investigations and is investigating a medium-severity security incident that involved the defacement of a corporate website. The web server in question ran on a virtualization platform, and the marketing team would like to get the website up and running as quickly as possible. What would be the most reasonable next step for Michael to take? Sonia recently removed an encrypted hard drive from a laptop and moved it to a new device because of a hardware failure. She is having difficulty accessing encrypted content on the drive despite that she knows the user’s password. What hardware security feature is likely causing this problem? In an infrastructure as a service (IaaS) environment where a vendor supplies a customer with access to storage services, who is normally responsible for removing sensitive data from drives that are taken out of service? Gary is concerned about applying consistent security settings to the many mobile devices used throughout his organization. What technology would best assist with this challenge? In a software as a service cloud computing environment, who is normally responsible for ensuring that appropriate firewall controls are in place to protect the application? Grace would like to implement application control technology in her organization. Users often need to install new applications for research and testing purposes, and she does not want to interfere with that process. At the same time, she would like to block the use of known malicious software. What type of application control would be appropriate in this situation? In a virtualized computing environment, what component is responsible for enforcing separation between guest machines? During a third-party vulnerability scan and security test, Danielle’s employer recently discovered that the embedded systems that were installed to manage her company’s new buildings have a severe remote access vulnerability. The manufacturer has gone out of business, and there is no patch or update for the devices. What should Danielle recommend that her employer do about the hundreds of devices that are vulnerable? Lauren’s networking team has been asked to identify a technology that will allow them to dynamically change the organization’s network by treating the network like code. What type of architecture should she recommend? Ben’s organization has had an issue with unauthorized access to applications and workstations during the lunch hour when employees aren’t at their desk. What are the best types of session management solutions for Ben to recommend to help prevent this type of access? Harold recently added an input validation routine to a web application that is designed to remove any instances of the <SCRIPT> tag in user input. What type of attack is Harold attempting to mitigate? Under what virtualization model does the virtualization platform separate the network control plane from the data plane and replace complex network devices with simpler devices that simply receive instructions from the controller? Which one of the following terms is often used to describe a collection of unrelated patches released in a large collection? Brian recently joined an organization that runs the majority of its services on a virtualization platform located in its own data center but also leverages an IaaS provider for hosting its web services and an SaaS email system. What term best describes the type of cloud environment this organization uses? Mark is considering replacing his organization’s customer relationship management (CRM) solution with a new product that is available in the cloud. This new solution is completely managed by the vendor, and Mark’s company will not have to write any code or manage any physical resources. What type of cloud solution is Mark considering? Which one of the following statements best describes a zero-day vulnerability? Melanie suspects that someone is using malicious software to steal computing cycles from her company. Which one of the following security tools would be in the best position to detect this type of incident? Brandon observes that an authorized user of a system on his network recently misused his account to exploit a system vulnerability against a shared server that allowed him to gain root access to that server. What type of attack took place? Roger recently accepted a new position as a security professional at a company that runs its entire IT infrastructure within an IaaS environment. Which one of the following would most likely be the responsibility of Roger’s firm? Renee is a software developer who writes code in Node.js for her organization. The company is considering moving from a self-hosted Node.js environment to one where Renee will run her code on application servers managed by a cloud vendor. What type of cloud solution is Renee’s company considering? Lauren wants to ensure that her users run only the software that her organization has approved. What technology should she deploy? Which one of the following files is most likely to contain a macro virus? What type of malware is characterized by spreading from system to system under its own power by exploiting vulnerabilities that do not require user intervention? Martin is inspecting a system where the user reported unusual activity, including disk activity when the system is idle, and abnormal CPU and network usage. He suspects that the machine is infected by a virus but scans come up clean. What malware technique might be in use here that would explain the clean scan results? TJ is inspecting a system where the user reported a strange error message and the inability to access files. He sees the window shown here. What type of malware should TJ suspect?
![]() 7.1 Identify and analyze malicious code and activity
7.1 Identify and analyze malicious code and activity
![]() 7.2 Implement and operate endpoint device security
7.2 Implement and operate endpoint device security
![]() 7.3 Operate and configure cloud security
7.3 Operate and configure cloud security
![]() 7.4 Operate and secure virtual environments
7.4 Operate and secure virtual environments

0.0.0.0
symantec.com
0.0.0.0
mcafee.com
0.0.0.0
microsoft.com
0.0.0.0
kapersky.com



[minesweeper.exe] TCP 127.0.0.1:62522 dynamo:0 LISTENING
[minesweeper.exe] TCP 192.168.1.100 151.101.2.69:https ESTABLISHED

