Chapter 2
Security Operations and Administration (Domain 2)
THIS CHAPTER COVERS THE FOLLOWING SSCP EXAM OBJECTIVES:
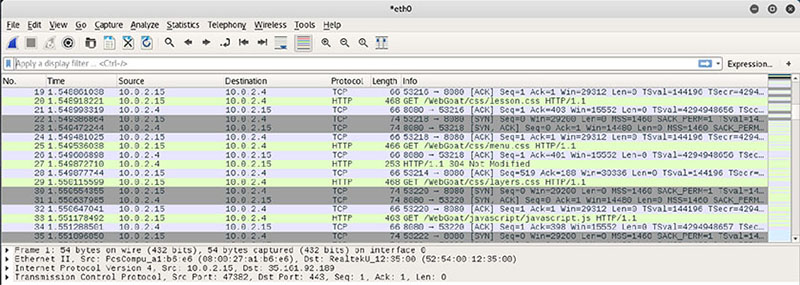
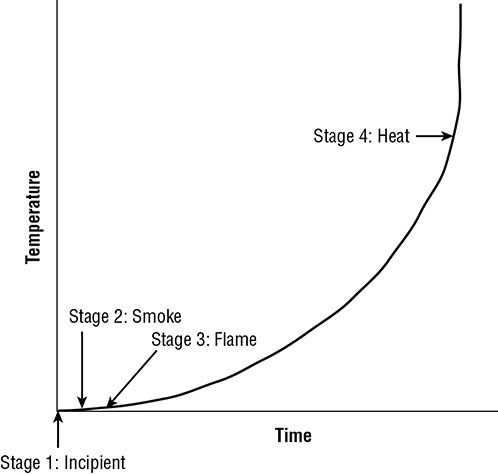
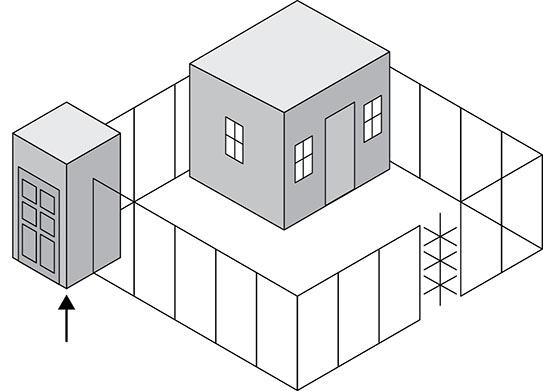
Maddox is conducting an information audit for his organization. Which one of the following elements that he discovered is least likely to be classified as PII when used in isolation? Carl recently assisted in the implementation of a new set of security controls designed to comply with legal requirements. He is concerned about the long-term maintenance of those controls. Which one of the following is a good way for Carl to ease his concerns? Darlene was recently offered a consulting opportunity as a side job. She is concerned that the opportunity might constitute a conflict of interest. Which one of the following sources is most likely to provide her with appropriate guidance? Which one of the following is an administrative control that can protect the confidentiality of information? Chris is worried that the laptops that his organization has recently acquired were modified by a third party to include keyloggers before they were delivered. Where should he focus his efforts to prevent this? The (ISC)2 code of ethics applies to all SSCP holders. Which of the following is not one of the four mandatory canons of the code? Which one of the following control categories does not accurately describe a fence around a facility? Which one of the following actions might be taken as part of a business continuity plan? Which one of the following is an example of physical infrastructure hardening? Mary is helping a computer user who sees the following message appear on his computer screen. What type of attack has occurred? The Acme Widgets Company is putting new controls in place for its accounting department. Management is concerned that a rogue accountant may be able to create a new false vendor and then issue checks to that vendor as payment for services that were never rendered. What security control can best help prevent this situation? Beth is the security administrator for a public school district. She is implementing a new student information system and is testing the code to ensure that students are not able to alter their own grades. What principle of information security is Beth enforcing? For questions 13–15, please refer to the following scenario. Juniper Content is a web content development company with 40 employees located in two offices: one in New York and a smaller office in the San Francisco Bay Area. Each office has a local area network protected by a perimeter firewall. The local area network (LAN) contains modern switch equipment connected to both wired and wireless networks. Each office has its own file server, and the information technology (IT) team runs software every hour to synchronize files between the two servers, distributing content between the offices. These servers are primarily used to store images and other files related to web content developed by the company. The team also uses a SaaS-based email and document collaboration solution for much of their work. You are the newly appointed IT manager for Juniper Content, and you are working to augment existing security controls to improve the organization’s security. Users in the two offices would like to access each other’s file servers over the Internet. What control would provide confidentiality for those communications? You are also concerned about the availability of data stored on each office’s server. You would like to add technology that would enable continued access to files located on the server even if a hard drive in a server fails. What integrity control allows you to add robustness without adding additional servers? Finally, there are historical records stored on the server that are extremely important to the business and should never be modified. You would like to add an integrity control that allows you to verify on a periodic basis that the files were not modified. What control can you add? An accounting employee at Doolittle Industries was recently arrested for participation in an embezzlement scheme. The employee transferred money to a personal account and then shifted funds around between other accounts every day to disguise the fraud for months. Which one of the following controls might have best allowed the earlier detection of this fraud? Yolanda is writing a document that will provide configuration information regarding the minimum level of security that every system in the organization must meet. What type of document is she preparing? Frank discovers a keylogger hidden on the laptop of his company’s chief executive officer. What information security principle is the keylogger most likely designed to disrupt? Susan is working with the management team in her company to classify data in an attempt to apply extra security controls that will limit the likelihood of a data breach. What principle of information security is Susan trying to enforce? Gary is implementing a new website architecture that uses multiple small web servers behind a load balancer. What principle of information security is Gary seeking to enforce? Which one of the following is not an example of a technical control? For questions 22–25, please refer to the following scenario. Jasper Diamonds is a jewelry manufacturer that markets and sells custom jewelry through their website. Bethany is the manager of Jasper’s software development organization, and she is working to bring the company into line with industry standard practices. She is developing a new change management process for the organization and wants to follow commonly accepted approaches. Jasper would like to establish a governing body for the organization’s change management efforts. What individual or group within an organization is typically responsible for reviewing the impact of proposed changes? During what phase of the change management process does the organization conduct peer review of the change for accuracy and completeness? Who should the organization appoint to manage the policies and procedures surrounding change management? Which one of the following elements is not a crucial component of a change request? Ben is designing a messaging system for a bank and would like to include a feature that allows the recipient of a message to prove to a third party that the message did indeed come from the purported originator. What goal is Ben trying to achieve? What principle of information security states that an organization should implement overlapping security controls whenever possible? Which one of the following is not a goal of a formal change management program? Ben is responsible for the security of payment card information stored in a database. Policy directs that he remove the information from the database, but he cannot do this for operational reasons. He obtained an exception to policy and is seeking an appropriate compensating control to mitigate the risk. What would be his best option? You discover that a user on your network has been using the Wireshark tool, as shown here. Further investigation revealed that he was using it for illicit purposes. What pillar of information security has most likely been violated? Which one of the following is the first step in developing an organization’s vital records program? Which one of the following security programs is designed to provide employees with the knowledge they need to perform their specific work tasks? Which one of the following security programs is designed to establish a minimum standard common denominator of security understanding? Chris is responsible for workstations throughout his company and knows that some of the company’s workstations are used to handle proprietary information. Which option best describes what should happen at the end of their lifecycle for workstations he is responsible for? What term is used to describe a set of common security configurations, often provided by a third party? Which one of the following administrative processes assists organizations in assigning appropriate levels of security control to sensitive information? Ben is following the National Institute of Standards and Technology (NIST) Special Publication 800-88 guidelines for sanitization and disposition as shown here. He is handling information that his organization classified as sensitive, which is a moderate security categorization in the NIST model. If the media is going to be sold as surplus, what process does Ben need to follow? Source: NIST SP 800-88 Ben has been tasked with identifying security controls for systems covered by his organization’s information classification system. Why might Ben choose to use a security baseline? Retaining and maintaining information for as long as it is needed is known as what? Referring to the figure shown here, what is the earliest stage of a fire where it is possible to use detection technology to identify it? Image reprinted from CISSP (ISC)2 Certified Information Systems Security Professional Official Study Guide, 7th Edition © John Wiley & Sons 2015, reprinted with permission. What type of fire suppression system fills with water when the initial stages of a fire are detected and then requires a sprinkler head heat activation before dispensing water? Ralph is designing a physical security infrastructure for a new computing facility that will remain largely unstaffed. He plans to implement motion detectors in the facility but would also like to include a secondary verification control for physical presence. Which one of the following would best meet his needs? Referring to the figure shown here, what is the name of the security control indicated by the arrow? Image reprinted from CISSP (ISC)2 Certified Information Systems Security Professional Official Study Guide, 7th Edition © John Wiley & Sons 2015, reprinted with permission.
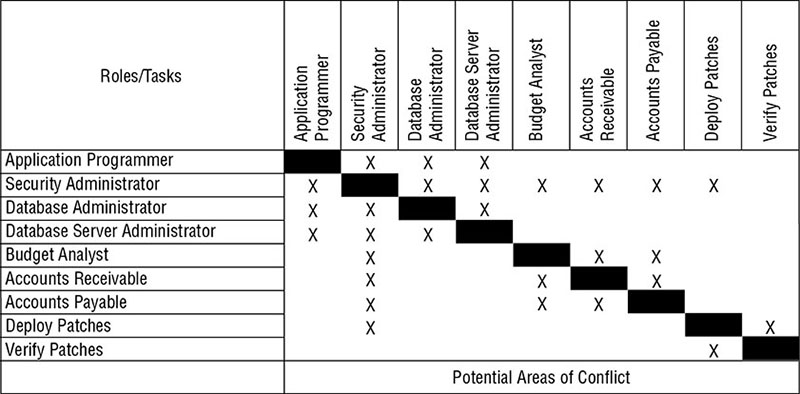
Which one of the following does not describe a standard physical security requirement for wiring closets? Betty is concerned about the use of buffer overflow attacks against a custom application developed for use in her organization. What security control would provide the strongest defense against these attacks? Juan is retrofitting an existing door to his facility to include a lock with automation capabilities. Which one of the following types of lock is easiest to install as a retrofit to the existing door? Rhonda is considering the use of new identification cards for physical access control in her organization. She comes across a military system that uses the card shown here. What type of card is this? Which one of the following facilities would have the highest level of physical security requirements? Glenda is investigating a potential privacy violation within her organization. The organization notified users that it was collecting data for product research that would last for six months and then disposed of the data at the end of that period. During the time that they had the data, they also used it to target a marketing campaign. Which principle of data privacy was most directly violated? What type of access control is composed of policies and procedures that support regulations, requirements, and the organization’s own policies? Match each of the numbered security controls listed with exactly one of the lettered categories shown. Choose the category that best describes each control. You may use each control category once, more than once, or not at all. Which of the following access control categories would not include a door lock? For questions 53–54, please refer to the following scenario. Gary was recently hired as the first chief information security officer (CISO) for a local government agency. The agency recently suffered a security breach and is attempting to build a new information security program. Gary would like to apply some best practices for security operations as he is designing this program. As Gary decides what access permissions he should grant to each user, what principle should guide his decisions about default permissions? As Gary designs the program, he uses the matrix shown here. What principle of information security does this matrix most directly help enforce? Lydia is processing access control requests for her organization. She comes across a request where the user does have the required security clearance, but there is no business justification for the access. Lydia denies this request. What security principle is she following? Helen is implementing a new security mechanism for granting employees administrative privileges in the accounting system. She designs the process so that both the employee’s manager and the accounting manager must approve the request before the access is granted. What information security principle is Helen enforcing? Which of the following is not true about the (ISC)2 code of ethics? Javier is verifying that only IT system administrators have the ability to log on to servers used for administrative purposes. What principle of information security is he enforcing? Connor’s company recently experienced a denial-of-service attack that Connor believes came from an inside source. If true, what type of event has the company experienced? Which one of the following is not a canon of the (ISC)2 code of ethics? When designing an access control scheme, Hilda set up roles so that the same person does not have the ability to provision a new user account and assign superuser privileges to an account. What information security principle is Hilda following? Which one of the following tools helps system administrators by providing a standard, secure template of configuration settings for operating systems and applications? Tracy is preparing to apply a patch to her organization’s enterprise resource planning system. She is concerned that the patch may introduce flaws that did not exist in prior versions, so she plans to conduct a test that will compare previous responses to input with those produced by the newly patched application. What type of testing is Tracy planning? Which one of the following security practices suggests that an organization should deploy multiple, overlapping security controls to meet security objectives? What technology asset management practice would an organization use to ensure that systems meet baseline security standards?
![]() 2.1 Comply with codes of ethics
2.1 Comply with codes of ethics
![]() 2.2 Understand security concepts
2.2 Understand security concepts
![]() 2.3 Document, implement, and maintain functional security controls
2.3 Document, implement, and maintain functional security controls
![]() 2.4 Participate in asset management
2.4 Participate in asset management
![]() 2.5 Implement security controls and assess compliance
2.5 Implement security controls and assess compliance
![]() 2.6 Participate in change management
2.6 Participate in change management
![]() 2.7 Participate in security awareness and training
2.7 Participate in security awareness and training![]() 2.8 Participate in physical security operations (e.g., data center assessment, badging)
2.8 Participate in physical security operations (e.g., data center assessment, badging)



Controls
Categories