Day 5. IDS/IPS Technologies
CCNA Security 210-260 IINS Exam Topics
![]() 6.2.a Rules/signatures
6.2.a Rules/signatures
![]() 6.2.b Detection/signature engines
6.2.b Detection/signature engines
![]() 6.2.c Trigger actions/responses (drop, reset, block, alert, monitor/log, shun)
6.2.c Trigger actions/responses (drop, reset, block, alert, monitor/log, shun)
![]() 6.2.d Blacklist (static and dynamic)
6.2.d Blacklist (static and dynamic)
Key Topics
Today we will review the important technological components behind IDS and IPS. We will look at how IDS and IPS sensors detect network threats using signatures, what actions sensors can take against malicious traffic, and how blacklisting can help protect corporate users against websites with a poor reputation rating. We will finish by discussing the advantages of Next-Generation IPS technology, in particular Cisco FirePOWER.
Detection Technologies
Multiple detection technologies are typically used to provide an effective intrusion detection or prevention architecture, including the following:
![]() Signature-based IDS/IPS: A signature-based approach is usually the starting point of an effective intrusion detection architecture. A signature is a set of rules that an IDS and an IPS use to detect typical intrusive activity, such as denial of service (DoS) attacks. Sensors allow you to modify existing signatures and define new ones. A signature-based IDS or IPS sensor looks for specific, predefined patterns (signatures) in network traffic. It compares the network traffic to a database of known attacks, and triggers an alarm or prevents communication if a match is found. The signature can be based on a single packet or a sequence of packets. New attacks that do not match a signature do not result in detection. For this reason, the signature database needs to be constantly updated.
Signature-based IDS/IPS: A signature-based approach is usually the starting point of an effective intrusion detection architecture. A signature is a set of rules that an IDS and an IPS use to detect typical intrusive activity, such as denial of service (DoS) attacks. Sensors allow you to modify existing signatures and define new ones. A signature-based IDS or IPS sensor looks for specific, predefined patterns (signatures) in network traffic. It compares the network traffic to a database of known attacks, and triggers an alarm or prevents communication if a match is found. The signature can be based on a single packet or a sequence of packets. New attacks that do not match a signature do not result in detection. For this reason, the signature database needs to be constantly updated.
![]() Policy-based IDS/IPS: In policy-based systems, the IDS or IPS sensor is configured based on the network security policy. You must create the policies used in a policy-based IDS or IPS. Any traffic detected outside the policy will generate an alarm or will be dropped. Creating a security policy requires detailed knowledge of the network traffic and is a time-consuming task.
Policy-based IDS/IPS: In policy-based systems, the IDS or IPS sensor is configured based on the network security policy. You must create the policies used in a policy-based IDS or IPS. Any traffic detected outside the policy will generate an alarm or will be dropped. Creating a security policy requires detailed knowledge of the network traffic and is a time-consuming task.
![]() Anomaly-based IDS/IPS: Anomaly-based (or profile-based) signatures typically look for network traffic that deviates from what is seen “normally.” The biggest issue with this methodology is that you first must define what normal is. If during the learning phase your network is the victim of an attack (or some other anomalous event takes place) and you fail to identify it, the anomaly-based IPS will interpret that malicious traffic as normal, and no alarm will be triggered the next time this same attack takes place. Some systems have hard-coded definitions of normal traffic patterns.
Anomaly-based IDS/IPS: Anomaly-based (or profile-based) signatures typically look for network traffic that deviates from what is seen “normally.” The biggest issue with this methodology is that you first must define what normal is. If during the learning phase your network is the victim of an attack (or some other anomalous event takes place) and you fail to identify it, the anomaly-based IPS will interpret that malicious traffic as normal, and no alarm will be triggered the next time this same attack takes place. Some systems have hard-coded definitions of normal traffic patterns.
![]() Reputation-based IPS: A more recent approach to intrusion detection is through the use of reputation-based IPS. This technique uses reputation analysis for various traffic descriptors, such as IP addresses, URLs, Domain Name System (DNS) domains, and others. This typically translates into reputation filters, sometimes known as whitelists or blacklists, that round up a signature-based system by filtering known malicious sources, destinations, or application components. Blacklisting is discussed in more detail in the next section.
Reputation-based IPS: A more recent approach to intrusion detection is through the use of reputation-based IPS. This technique uses reputation analysis for various traffic descriptors, such as IP addresses, URLs, Domain Name System (DNS) domains, and others. This typically translates into reputation filters, sometimes known as whitelists or blacklists, that round up a signature-based system by filtering known malicious sources, destinations, or application components. Blacklisting is discussed in more detail in the next section.
Signatures
As explained earlier, a signature is a set of rules that an IDS and an IPS use to detect typical intrusive activity, such as DoS attacks. IPS signatures are dynamically updated and posted to Cisco.com on a regular basis so that customers can access signatures that help protect their network from the latest known network attacks. The updates take the form of signature files, also known as signature packages or simply signature updates. Manual updates are also possible.
Cisco IPS devices use signature engines to load the signature files and scan signatures. Signatures that are contained within the signature packages are managed by various signature engines. The packages typically contain signature definitions for multiple engines.
Signature engines typically correspond to the protocol in which the signature occurs and look for malicious activity in that protocol. Each signature engine provides a common set of signature parameters that can be used to tune the sensitivity, scope, and actions of that particular signature engine, instead of making changes to individual signatures.
Table 5-1 summarizes the types of signature engines available.
Trigger Actions
The distinction between IDS and IPS is based on whether the sensor interacts with traffic passively, limited to detective capabilities, or the sensor interacts with traffic actively, providing protective services. Regarding IDS and IPS, the terms “action” and “response” are used synonymously for the reactions a sensor can be configured to perform in response to suspicious events.
The following terms define passive actions or responses that are commonly available in IDS and IPS technology:
![]() Alerts: Generation of a loggable message upon detection of potentially malicious traffic flows. How alerts are used is dependent on the size and complexity of the deployment. Alerts should always be stored in a database so records can be reviewed later for forensic analysis. They are often sent to real-time event viewers that are monitored by IT staff in a Network Operations Center (NOC). Larger deployments will incorporate the alerts into a Security Information and Event Management (SIEM) system. The term “alarm” is often used interchangeably with “alert.”
Alerts: Generation of a loggable message upon detection of potentially malicious traffic flows. How alerts are used is dependent on the size and complexity of the deployment. Alerts should always be stored in a database so records can be reviewed later for forensic analysis. They are often sent to real-time event viewers that are monitored by IT staff in a Network Operations Center (NOC). Larger deployments will incorporate the alerts into a Security Information and Event Management (SIEM) system. The term “alarm” is often used interchangeably with “alert.”
![]() Monitor: An IDS may react to suspicious events by concentrating more resources on traffic that is associated with a particular host or between a pair of hosts. For example, it may include a packet capture in the data that is logged.
Monitor: An IDS may react to suspicious events by concentrating more resources on traffic that is associated with a particular host or between a pair of hosts. For example, it may include a packet capture in the data that is logged.
The following terms define active actions or responses that are commonly available in IPS technology only:
![]() Drop: Packets that are determined to have suspicious payload may be dropped by the sensor, preventing the payload from reaching the destination.
Drop: Packets that are determined to have suspicious payload may be dropped by the sensor, preventing the payload from reaching the destination.
![]() Reset: When a suspicious payload is detected with a TCP connection, the sensor may inject TCP resets to cause the offending TCP connection to be terminated.
Reset: When a suspicious payload is detected with a TCP connection, the sensor may inject TCP resets to cause the offending TCP connection to be terminated.
![]() Block: A reset only functions with TCP. Attacks may be carried out using other protocols, such as UDP and ICMP. Also, it is possible for an attacking system and a compromised host to break the normal rules of TCP and ignore the TCP reset to counter the IPS reaction. Additional protection can be provided by blocking further traffic. A block may be implemented for a particular session, or between a particular pair of hosts, or for all traffic that is associated with a single host.
Block: A reset only functions with TCP. Attacks may be carried out using other protocols, such as UDP and ICMP. Also, it is possible for an attacking system and a compromised host to break the normal rules of TCP and ignore the TCP reset to counter the IPS reaction. Additional protection can be provided by blocking further traffic. A block may be implemented for a particular session, or between a particular pair of hosts, or for all traffic that is associated with a single host.
![]() Shun: Some IPSs have the ability to request that blocking be performed by other devices in the network. In some deployments, this dynamic blocking between security zones within a network is controlled by the SIEM. This action is often referred to as shunning. The term originates from the Cisco ASA security appliance command that is used to initiate the requested block.
Shun: Some IPSs have the ability to request that blocking be performed by other devices in the network. In some deployments, this dynamic blocking between security zones within a network is controlled by the SIEM. This action is often referred to as shunning. The term originates from the Cisco ASA security appliance command that is used to initiate the requested block.
Blacklisting
Some of the capabilities or features of an IPS sensor are intended to protect the network before an attack by controlling access to resources, enforcing policies, and generally hardening network devices.
Examples of features that play a role in protecting the network before an attack actually occurs include the following:
![]() Blacklisting: You can blacklist (deny traffic to and from) specific IP addresses that might pose a danger to your network. To help you build blacklists, the IPS can dynamically download, at configurable intervals, a collection of IP addresses that have been determined by the Cisco Collective Security Intelligence team (Talos, http://www.talosintel.com/) to have a poor reputation. Blacklisting will block matching traffic regardless of any other characteristics of the traffic. Entries on a blacklist can be manually defined, created dynamically as a response to a rule violation, and maintained dynamically based on a security intelligence service. The opposite of blacklisting is whitelisting. When whitelists are implemented, matching traffic is permitted, regardless of whether the IP address in question is blacklisted. Blacklisting and whitelisting can be used in various security solutions, including IPS, email security, web security, and firewall.
Blacklisting: You can blacklist (deny traffic to and from) specific IP addresses that might pose a danger to your network. To help you build blacklists, the IPS can dynamically download, at configurable intervals, a collection of IP addresses that have been determined by the Cisco Collective Security Intelligence team (Talos, http://www.talosintel.com/) to have a poor reputation. Blacklisting will block matching traffic regardless of any other characteristics of the traffic. Entries on a blacklist can be manually defined, created dynamically as a response to a rule violation, and maintained dynamically based on a security intelligence service. The opposite of blacklisting is whitelisting. When whitelists are implemented, matching traffic is permitted, regardless of whether the IP address in question is blacklisted. Blacklisting and whitelisting can be used in various security solutions, including IPS, email security, web security, and firewall.
![]() Cisco Advanced Malware Protection (AMP) for Networks: This network-based component uses FirePOWER-based appliances to detect malware in transit over network connections. It, too, can communicate with the cloud to get instant access to the most current information that the cloud stores about file disposition and known malware. Network-based AMP allows the system to inspect network traffic for malware in several types of files.
Cisco Advanced Malware Protection (AMP) for Networks: This network-based component uses FirePOWER-based appliances to detect malware in transit over network connections. It, too, can communicate with the cloud to get instant access to the most current information that the cloud stores about file disposition and known malware. Network-based AMP allows the system to inspect network traffic for malware in several types of files.
Next-Generation IPS with FirePOWER
Cisco Next-Generation IPS (NGIPS) solutions build on typical IPS technologies by providing contextual awareness during an attack to promptly assess threats, and ensure a consistent and appropriate response. Not only does the IPS report the event, but it also provides information about network activity, systems, applications, locations, and people related to the attack.
NGIPS filtering analyzes network traffic in real time, comparing the traffic contents against known threats. Cisco Collective Security Intelligence (Talos) develops signatures that identify threats. Multiple signatures can map to a single threat. New threats and signature sets are updated by default every hour.
With NGIPS, threats are the focus instead of signatures. If a connection or traffic flow matches a threat, the NGIPS can drop the connection to block the threat.
The FirePOWER NGIPS solution also includes Cisco FireSIGHT Management Center, which centrally manages network security and operational functions for Cisco FirePOWER appliances, legacy non-FirePOWER appliances, and virtual appliances. The Cisco FireSIGHT Management Center, which aggregates and correlates the information that is gathered by managed devices, is a separate application that can be hosted on a separate FireSIGHT Management Center appliance or as a virtual appliance running on a VMware server.
 Video: IDS and IPS Technologies
Video: IDS and IPS Technologies
Refer to the Digital Study Guide to view this video.
 Activity: Compare IPS Alarm Characteristics
Activity: Compare IPS Alarm Characteristics
Refer to the Digital Study Guide to complete this activity.
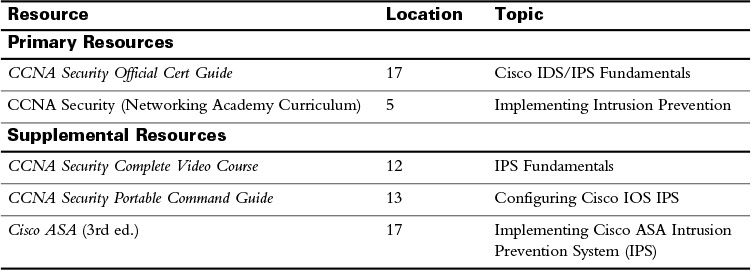
Study Resources
For today’s exam topics, refer to the following resources for more study.
![]() Check Your Understanding
Check Your Understanding
Refer to the Digital Study Guide to take a ten-question quiz covering the content of this day.

