Chapter 2. Windows Operating and File Systems
Learning Outcomes
After reading this chapter, you will be able to understand the following:
![]() What an operating system is;
What an operating system is;
![]() What binary, decimal, and hexadecimal are and how to convert from each notation;
What binary, decimal, and hexadecimal are and how to convert from each notation;
![]() The physical structure of a hard drive and how files are stored and retrieved;
The physical structure of a hard drive and how files are stored and retrieved;
![]() The booting process;
The booting process;
![]() The Windows file systems; and
The Windows file systems; and
![]() The different features of each Windows operating system and their implications on investigations.
The different features of each Windows operating system and their implications on investigations.
Introduction
A strong foundation in operating systems is an important building block in becoming a highly effective computer forensics investigator. The evidence that computer forensics investigators work with are files. The organization of these files, the data they contain, and their locations will vary according to the operating system and associated file system that exists on the suspect’s computer or digital device. Moreover, the type of operating system and file system will determine the way that digital evidence is acquired and analyzed in terms of both software and hardware. A file system is a hierarchy of files and their respective directories.
This chapter begins by outlining the important concept of logical versus physical storage, which is important when discussing how we all view files on our computers through File Explorer on a PC versus how files are actually physically stored on a hard drive. A file on a computer is merely a physical impression on a metal platter, as you will learn later in this chapter. Therefore, computer scientists represent the underlying data on the hard drive in a number of ways—sometimes in binary format or hexadecimal or decimal. This chapter explains these various numbering systems in detail and shows you how to translate from one numbering system to another. This is important because most computer forensics analysis tools give you a “natural” view of the file but also enable the investigator to view a hexadecimal view of the file, to reveal far more information about the file (the file header, metadata, and other helpful information).
An understanding of operating systems is also important because different types and versions of operating systems have different features, and knowing these features will assist the investigator in understanding where on the computer the most valuable evidence resides and what tools to use. Moreover, most computer forensics imaging tools give the investigator access to a variety of operating system files; the examiner must be familiar with them and be able to explain them.
When analyzing evidence from a hard disk drive, the computer forensics software displays files associated with the booting up process (when the computer is powered on). Therefore, the investigator should be familiar with these files. In fact, an investigator should be familiar with both system and user files and should be able to account for changes to these files. This is the case for all computing devices. For example, a defense attorney may state that some file changes occurred from when the suspect last used a computer, and the investigator must account for these changes.
The chapter continues by outlining all of the file systems that are supported by Windows operating systems. This is key because the type of file system impacts the value of the evidence and the investigator’s ability to view that evidence. For example, FAT12 files are not encrypted, whereas NTFS files can possess strong encryption and be unreadable. Nevertheless, a FAT12 file has a lot less valuable metadata than an NTFS file, and file backups are generally more probable than with FAT12. Therefore, understanding the characteristics of each file system is important for the investigator.
A recurring theme throughout this book is the importance of placing the suspect behind the keyboard and re-creating the events leading up to a crime. File Registry in Windows records any kind of configuration change to a system, which opens a tremendous wealth of information related to a user’s wireless connections and Internet activity. Therefore, we delve into Windows’ File Registry to see what information we can ascertain about a suspect or victim.
The chapter then discusses the file systems supported by Microsoft. The type of file system determines the way files are stored and retrieved in memory. Moreover, the file system defines the limits on file size. The evidentiary value of a file will differ from file system to file system. There are a multitude of reasons for this. For example, the longevity of a file can vary; deleting a file on a Macintosh computer is a different process than deleting a file on a Windows personal computer running NTFS. Metadata, or the attributes of a file, is often critical to associating a criminal with evidence, but the nature of this evidence differs from one file system to another. Encryption is yet another variable, and it generally becomes a more difficult proposition for forensic examiners to contend with as vendors continue to improve the quality of their file systems’ security.
A file system is also responsible for determining allocated and unallocated storage space. Allocated storage space is the area on a volume where a file or files are stored. When a file on a personal computer is deleted, it is not physically erased from the volume (disk) but now becomes available space. When a file is deleted, it is still physically stored on a volume. However, that space is now available to be overwritten. This available file storage space is referred to as unallocated storage space. Users can look to certain tools to securely delete a file. There are, however, search methods that a forensic examiner can use to check to see if a secure delete tool has been used. Unallocated storage space can generally be used to create a primary partition on a volume. A partition is a logical storage unit on a disk. In computer forensics, we often hear this notion of physical versus logical when it comes to file storage or files retrieved from a computer or media storage. Therefore, it is critical for an investigator to know the difference and be able to explain that difference to nontechnical people.
Physical and Logical Storage
Understanding the physical and logical storage aspects of file systems is important because computer forensics imaging software provides a very different view of the data stored on a computer. Forensic imaging software is also known as bit-stream imaging software because it captures every bit stored on a computer’s hard drive. Unlike Microsoft’s Windows File Explorer, forensic imaging software displays every file stored in a computer’s memory, including files from the operating system.
Physical versus logical can also refer to the difference between how the operating system refers to the location of a sector and the physical location of a sector on a disk relative to the storage media. Physical storage is discussed in greater detail later in this chapter.
File Storage
An investigator should understand how files on a computer are stored. With this understanding comes the realization that users cannot determine the physical location of where a file is stored and, therefore, cannot control the deletion of that file evidence from a hard drive. File storage and recording is largely controlled by the operating system.
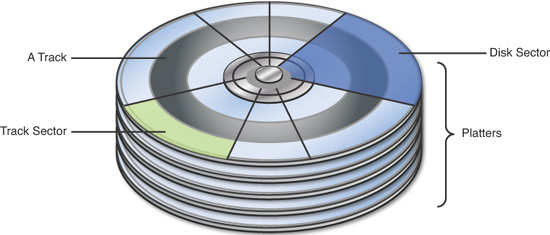
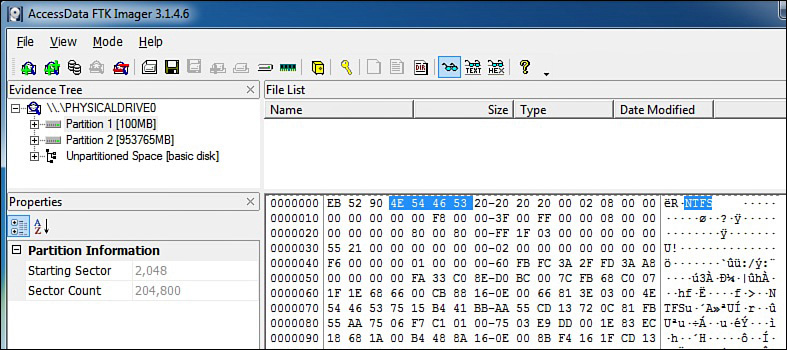
A byte is comprised of 8 bits and is the smallest addressable unit in memory. A sector on a magnetic hard disk represents 512 bytes, or 2048 bytes on optical disks. More recently, some hard drives contain 4096 byte sectors. Usually a disk has bad sectors, which computer forensics software can identify. A bad sector is an area of the disk that can no longer be used to store data. Bad sectors can be caused by viruses, corrupted boot records, physical disruptions, and a host of other disk errors. A cluster is a logical storage unit on a hard disk that contains contiguous sectors. When a disk volume is partitioned, the number of sectors in a cluster is defined. A cluster can contain 1 sector (512K) or even 128 sectors (65,536K). Tracks are thin, concentric bands on a disk that consist of sectors where data is stored. Computer forensic tools allow the investigator to easily navigate to specific sectors on a disk image, even if a sector is part of the operating system. Figure 2.1 shows the physical layout of a hard disk.
Because most files are comprised of 512-byte blocks, it is important to understand that an 800-byte file uses two 512-byte sectors on a magnetic disk. File slack refers to the remaining unused bytes in the last sector of a file. It is necessary to understand what file slack is because data can be hidden in this area. In our example of an 800-byte file, the physical size of the file is 1024 bytes (two sectors), whereas the logical size of the file is 800 bytes (or 800K). Windows File Explorer displays the logical file size. The physical file size is the actual disk space used by a file. The logical file size is the amount of data stored in a file. Table 2.1 is a diagram of an 800-byte file. To be more specific about slack, RAM slack is the slack at the end of the logical file or sector, and file slack refers to the remaining sectors at the end of the cluster.
Computer forensics investigators typically spend most of their time examining hard disk drives. A platter is a circular disk made from aluminum, ceramic, or glass that stores data magnetically. A hard drive contains one or more platters, and data can usually be stored on both sides of this rigid disk. A spindle, at the center of the disk, is powered by a motor and is used to spin the platters. An arm sweeps across the rotating platter in an arc. This actuator arm contains a read/write head that modifies the magnetization of the disk when writing to it. There are generally two read/write heads for each platter because a platter usually contains data on both sides. The arm and head are nanometers from the platter. Therefore, hard drives must be handled very carefully: Any impact on the hard drive could render the read/write head useless. Additionally, the examiner must be very careful not to let any magnetic device near a hard drive. A cellular telephone, for example, contains a battery, and that battery contains a magnet. Sometimes hotel guests will deactivate their hotel room key when they place the key in their pocket with their cellular telephone. This is because the magnetic charge from the telephone corrupts the data on the key. Figure 2.2 shows the layout of a hard drive.
A cylinder is the same track number on each platter, spanning all platters in a hard drive. Disk geometry refers to the structure of a hard disk in terms of platters, tracks, and sectors. The capacity of a hard disk drive can be calculated using the following formula:
Number of cylinders × Number of heads × Number of sectors × Number of bytes per sector
Therefore, an HDD with 16,383 cylinders and 16 heads and 63 sectors (512 bytes per sector) is calculated thus:
= 16,383 × 16 × 63 × 512
= 8,455,200,768 bytes, or 8GB (8 gigabytes)
A gigabyte can be quantified as 109. See Table 2.2 for a byte conversion table.
File Conversion and Numbering Formats
As computer forensics investigators, we need to be able to convert from different formats because the forensics software that we use displays system and user data in different formats. Moreover, some files or data on a computer are in a format like binary, and we must convert that data before we can interpret it as information.
Conversion of Binary to Decimal
Binary is the language that computers understand. Binary is comprised of bits. Bits can only be one of two values, where a 1 is a positive charge and a 0 is a negative charge. Binary can be easily converted to decimal with a scientific calculator. However, we can use Table 2.3 to convert the following binary number: 1011 1111.
= (1 x 128) + (0 x 64) + (1 x 32) + (1 x 16) + (1 x 8) + (1 x 4) + (1 x 2) + (1 x 1)
= 128 + 0 + 32 + 16 + 8 + 4 + 2 + 1
= 191
Hexadecimal Numbering
Hexadecimal is yet another numbering system that can be found in forensics software tools, like FTK or X-Ways. An investigator also sometimes comes across binary files on a computer and may need to use a hex editor to read the content or may perhaps convert the file to an ASCII format. Some configuration files, for example, are in a binary format. As we mentioned, binary uses 2 symbols (0,1). Decimal uses 10 symbols (0 to 9). Hexadecimal is a numbering system that uses 16 symbols (base 16), which includes numbers 0 to 9 and letters A to F. It is necessary to understand hexadecimal because most computer forensics imaging software includes a hex editor. A hex editor enables a forensics examiner to view the entire contents of a file. Some hex editors, like WinHex, allow investigators to manipulate hex values, which can be helpful in making unreadable files readable. Table 2.4 illustrates the conversion from binary to decimal, to hexadecimal.
Conversion of Hexadecimal to Decimal
A nibble is one digit of a hexadecimal (hex) value, which represents 4 bits. Therefore, 7DA2 represents 2 bytes (4 bits × 4 bits = 16 bits, or 2 bytes). To differentiate hexadecimal numbers from other numbers, we use 0x before hex numbers. To convert 0x7DA2 to decimal, we can use Table 2.5.
= (7 x 4,096) + (13 x 256) + (10 x 16) + (2 x 1)
= 28,672 + 3,328 + 160 + 2
= 32,162
Conversion of Hexadecimal to ASCII (American Standard Code for Information Interchange)
Knowing how to convert hex to ASCII is more important than converting hex to decimal. Table 2.6 outlines the conversion of hexadecimal to ASCII.
Some of the symbols in Table 2.6 are not intuitive. For example, in Table 2.6, Hex 10 has a symbol of DLE, which stands for Data Link Escape. Data Link Escape is a communications control character that specifies that the proceeding character is not data, but rather a control code. A control character begins, modifies, or terminates a computer operation and is not a written or printable symbol. The first 32 codes in Table 2.6 are control characters. Another example from Table 2.6 is the symbol ACK (Hex: 06), which is a transmission control character affirmation (or acknowledgment) that a transmission was received.
Many free hex converters are available online. We use Table 2.7 here to convert the sentence Hi there!.
Unicode
Frequently, an investigator comes across the term Unicode and should understand what the term means. Unicode is an international encoding standard that supports various languages and scripts from across the world. For example, the Cyrillic alphabet, used by the Russian language, and Arabic script are supported by Unicode. This means that computers today have broader appeal because they support regional characters. Each letter, character, or digit is assigned a unique number. Unicode can be found in operating systems and in certain programming languages.
Operating Systems
An operating system is a set of programs used to control and manage a computer’s hardware and system resources. Forensic software tools display many different files from the operating system on a suspect’s or victim’s computer, so investigators must know how to recognize these files. Moreover, a user’s interaction with a computer often is evident through an examination of the operating system. When a user starts (also known as “boots”) a computer or inserts a CD, the computer’s operating system records these events.
The Boot Process
The kernel is at the core of the operating system and is responsible for communication between applications and hardware devices, including memory and disk management. When a computer is powered on, the computer executes code stored in ROM, referred to as the BIOS. The Basic Input/Output System (BIOS) starts an operating system by recognizing and initializing system devices, including the hard drive, CD-ROM drive, keyboard, mouse, video card, and other devices. Bootstrapping is the process of running a small piece of code to activate other parts of the operating system during the boot process. The bootstrap process is contained in the ROM chip. Read-only memory (ROM) is nonvolatile storage that is generally not modified and is used during the boot process.
In many examinations, a computer forensics investigation removes the suspect’s hard drive, and that hard drive is then cloned or imaged. It is important for the investigator to also document information about the system and its specifications. Therefore, the investigator starts the computer with the hard drive removed to prevent changes to the hard drive.
Remember that a user might have password-protected the BIOS, which can cause problems for the investigator. However, some solutions are available on the Internet to deal with BIOS passwords.
Master Boot Record (MBR)
The first sector on a hard disk (Sector 0) is known as the Master Boot Record. The Master Boot Record (MBR) is involved in the boot process and stores information about the partitions on a disk, including how many exist and their locations. A floppy disk has no MBR because the first sector on a floppy disk is the boot sector. When a computer is powered on and the BIOS initiates the boot process, the BIOS always looks at Sector 0 for instructions on how to load the operating system. The MBR is comprised of the Master Partition Table, Master Boot Code, and Disk Signature. The Master Partition Table contains descriptions about the partitions on a hard disk. There is only enough room in this table for four descriptions, so there are a maximum of four physical partitions on a hard drive. If a user wants to create an additional partition, then it must be a logical partition with a link to a primary partition (physical partition). The BIOS uses the Master Boot Code to start the boot process. The Disk Signature identifies the disk to the operating system. The End of Sector Marker is a two-byte structure found at the end of the MBR.
Windows File Systems
Windows is a series of operating systems with a graphical user interface (GUI), developed by Microsoft. This GUI was introduced in 1985 in response to the highly successful Macintosh (Mac) GUI, which was released in 1984. Although Apple’s Mac OS X continues to grow in market share, Windows is still the dominant operating system worldwide.
Surprisingly, Microsoft Windows supports only five file systems: NTFS, FAT64, FAT32, FAT16, and FAT12. FAT (File Allocation Table) is a file system developed by Microsoft that utilizes a table to store information about where files are stored, where file space is available, and where files cannot be stored. NTFS (New Technology File System) subsequently replaced FAT. NTFS was developed by Microsoft and introduced with Windows NT. NTFS is the primary file system that has been included with Windows since the advent of Windows 2000—Windows 2000 and subsequent Windows operating systems still support FAT.
FAT12
The FAT12 file system was introduced in 1980 as the first version of FAT and is the file system found on floppy disks. Initially. FAT12 was developed to support 5.25-inch floppy disks but was later used for the small 1.44MB floppy disks. Practically every operating system running on a personal computer today still supports FAT12.
FAT16
Introduced in 1987, FAT16 is a 16-bit file system that was developed for use with MS-DOS. Filenames in FAT16 are limited to eight characters, and the file extensions are three characters long. This file system supports disk partitions with a maximum storage of 2GB.
FAT32
FAT32 is a 32-bit version of FAT that uses smaller clusters, thereby allowing for more efficient utilization of space. The operating system determines the cluster sizes. This file system was introduced with Windows 95 and has a maximum file size of 4GB.
FAT64
The FAT64 file system, also referred to as exFAT (Extended File Allocation Table), was developed by Microsoft. This file system was introduced with Vista Windows Service Pack 1, Windows Embedded CE 6.0, and Windows 7 operating systems. Interestingly, Mac OS X Snow Leopard (10.6.5) can recognize exFAT partitions. Therefore, it is a practical file system to use when transferring files from a personal computer (running Windows) to a Mac. However, this file system does not possess the security or journaling features found in NTFS.
FATX
FATX is a file system developed for use on the hard drive of Microsoft’s Xbox video game console, as well as any associated memory cards. It is worth mentioning the FATX file system because computer forensics investigators have found incriminating evidence on video game consoles.
NTFS (New Technology File System)
NTFS is the latest file system developed by Microsoft for use with a Windows operating system. Unlike FAT, it supports advanced file encryption and compression. File compression allows the user to reduce the number of bits in a file, which allows for faster transmission of the file. It also supports a 16-bit Unicode character set for filenames and folders, which has more international appeal. File and folder names can also have spaces and use printable characters (except for “/:<>|”?). NTFS added security to its file system with the introduction of access control lists. An access control list is a list of permissions associated with a file and details the users and programs granted access to the file. A forensic examiner should know who has access to certain files. NTFS files also have potentially negative implications for an investigator because of the potential for encryption. NTFS files can be very large, with a maximum file size of 16EB (16 × 10246 bytes).
Unlike its predecessor FAT32, NTFS also utilizes journaling. Journaling is a form of file system record keeping that records changes made to files in a journal. The journal uses tracked changes to files for fast and efficient restoration of files when a system failure or power outage occurs. The NTFS log, with the filename $LogFile, records these changes.
NTFS also introduced alternate data streams into the file system. An alternate data stream (ADS) is a file’s set of attributes. NTFS allows files to have multiple data streams that can be viewed only by accessing the Master File Table. For example, Windows File Explorer details a music file’s logical path in a file system; however, the media provider might also use an additional data stream to update information about the album that the music file is derived from or associate the music file with an existing music download from the same artist. Hackers can use alternate data streams to hide data, including rootkits associated with viruses. Therefore, it is important for investigators to know about ADS.
Table 2.8 provides a summary of features for Windows file systems.
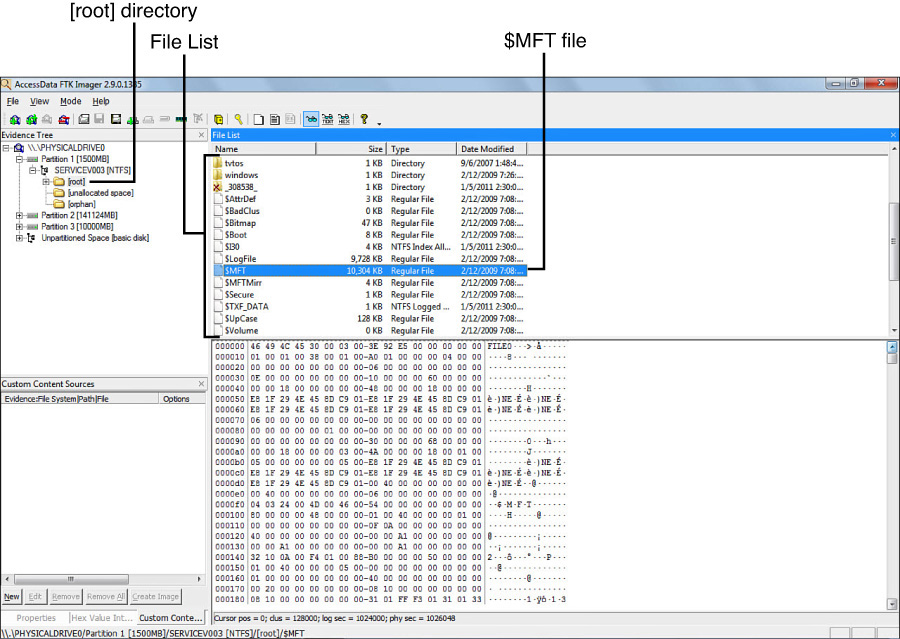
Master File Table
In NTFS, the Master File Table (MFT) maintains file and folder metadata in NTFS, including the filename, creation date, location, size, and permission for every file and folder. Other file properties, like compression or encryption, are found in the MFT. The MFT also tracks when files are deleted and indicates that the space can be reallocated.
Table 2.9 details the NTFS system filenames, functions, and locations.
Windows Registry
Windows Registry is a hierarchical database that stores system configuration information. It maintains files used to control the operating system’s hardware and software and keeps track of the system’s users. In terms of evidence, the Windows Registry can provide a wealth of information, including Internet searches, sites visited, passwords, and user activity.
The Registry is comprised of two elements: keys and values. Keys are akin to folders and are easily identified by noting the folder icon. Most keys contain subkeys (or folders). These subkeys can contain multiple subkeys. The Windows Registry has five basic hives, each of which plays an important role.
Do not make any changes to Windows File Registry. Changes may cause serious problems, which may require you to reinstall your operating system.
The following is a detailed explanation of the five major hives in the Registry:
![]()
HKEY_CLASSES_ROOT (HKCR)—Contains filename extension associations like .exe. Also contained in this hive are COM objects, Visual Basic programs, and other automation. The Component Object Model (COM) allows nonprogrammers to write scripts for managing Windows operating systems.
![]()
HKEY_CURRENT_USER (HKCU)—Contains the user profile for the current profile that is logged in to the system when viewed. This profile changes each time the user logs in to the system. A user profile includes desktop settings, network connections, printers, and personal groups. This hive contains very little data but acts as a pointer to HKEY_USERS.
![]()
HKEY_LOCAL_MACHINE (HKLM)—Contains information about the system’s settings, including information about the computer’s hardware and operating system.
![]()
HKEY_USERS (HKU)—Contains information about all the registered users on a system. Within this hive are a minimum of three keys. The first key is .DEFAULT, which contains a profile when no users are logged in. There is also a key containing the SID for the current local user, which could look something like S-1-5-18. There is also a key for the current user with _Classes at the end—for example, HKEY_USERSS-1-5-21-3794263289-4294853377-1685327589-1003_Classes.
![]()
HKEY_CURRENT_CONFIG (HKCC)—Contains information pertaining to the system’s hardware that is necessary during the startup process. Within this hive are screen settings, screen resolution, and fonts. Information about the plug-and-play BIOS is also found in this hive.
Registries are an important source of information for an investigator, and the user profile information is invaluable in linking a particular suspect to a machine.
Registry Data Types
The Registry uses a number of different data types. Figure 2.12 shows two data types. REG_SZ is a fixed-length text string. REG_DWORD is data represented by a 32-bit (4-byte) integer.
FTK Registry Viewer
Although the five primary keys are very similar in each version of the Windows operating system, the keys within each hive vary in location. Many forensic tools enable an examiner to export, search, and view the contents of the Registry. AccessData’s FTK includes a tool called Registry Viewer that enables the user to access the Registry’s encrypted Protected Storage System Provider, which can contain usernames and passwords, Internet searches, and Internet form data.
Microsoft Windows Features
The nature of evidence available does not differ from just one operating system to another, but it also changes with each version of that operating system. An investigator must understand these changes and how these changes will impact the investigation. When Microsoft introduced Windows Vista, it introduced a whole host of changes.
Windows Vista
Microsoft released Vista to the public in November 2006. It was not one of the more popular versions of Windows, given its hardware requirements. This RAM-intensive operating system has a slower response rate to commands than its predecessor, Windows XP.
Microsoft’s Vista is a dramatic departure from previous versions of the vendor’s operating systems in terms of security and file systems. Microsoft’s technical advances in security have created problems for law enforcement and other computer forensics investigators. The proceeding section details the major features introduced with this operating system and explores the implications for forensic investigators.
Vista comes in a 32-bit or 64-bit operating system version. The 32-bit version supports up to 4GB of RAM; the 64-bit version can support a maximum of 128GB.
As you begin using professional computer forensics software, you will notice that, in Vista, the first NTFS partition begins at Sector 2048. Previously, the first NTFS partition was located at Sector 63.
Defragmentation in Vista
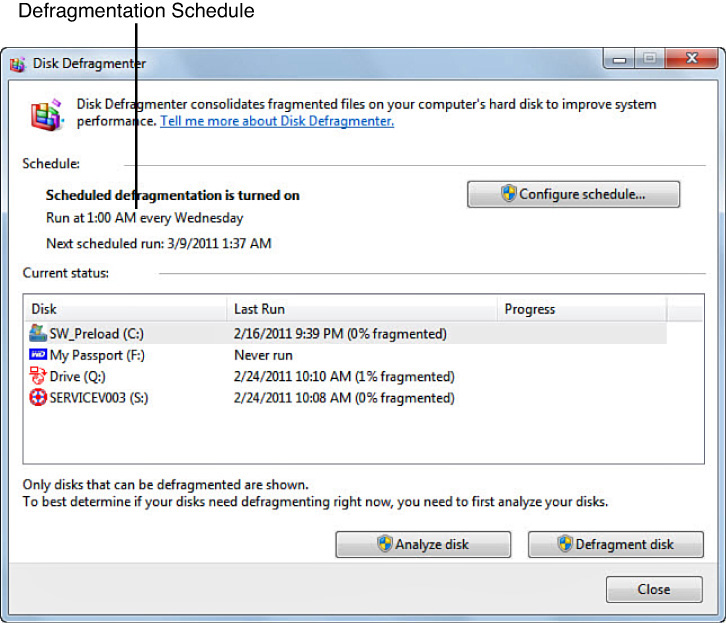
Defragmentation is the process of eliminating the amount of fragmentation in a file system to make file chunks (512K blocks) closer together and increase free space areas on a disk. Fragments of files are not always stored contiguously on a hard drive, but are often scattered. This defragmentation process can improve the read/write performance of the file system.
The defragmentation program on Vista is different than in previous versions of Windows. Most important, defragmentation in Vista is set to automatically run once a week. We know that some defragmentation occurs periodically in previous versions of Windows, unbeknownst to us. A defragmentation can also be executed manually in Vista, if necessary. Either way, it works in the background at a low priority without a graphical display. Defragmentation can also run from an administrative command prompt.
Why is this important? Its importance stems from the fact that, with the advent of automatic defragmentation, computer forensics investigators will face a significant decrease in evidentiary data.
Event Viewer in Vista
An investigator working the scene of the crime needs to re-create the events that led up to a crime being committed. Moreover, that investigator must prove that certain actions transpired, especially actions that involved the victim(s) and perpetrator(s). The same is true for a computer forensics investigator. One way in which an investigator can reconstruct events is by examining the event logs. An event is a communication between one application and another program or user on a computer. Event Viewer is a Windows application used to view event logs. An event can include the following occurrences: successful authentication and login of a user on a system, a defragmentation, an instant messaging chat session, or the download of an application. In certain cases, prosecutors have used event logs to demonstrate that a suspect installed an application to remove file registries or Internet activity in an effort to tamper with evidence after receiving a subpoena.
The Event Viewer in Vista is noticeably different from previous versions of the application. The GUI is different and includes a preview pane for the selected event located beneath the event list. Event logs now have the .evtx extension and are in an XML format. XML (Extensible Markup Language) is a standardized language that is compatible for use on the Internet. These event logs, found in C:WindowsSystem32winevtLogs, can be viewed by the Windows Vista Event Viewer. When you click the Start button on your Windows machine, simply type eventvwr to access the application. Because Vista event logs are XML based, an investigator can simplify searches of event logs using XPath (XML Path Language), a powerful query language used for searching XML documents. XPath queries can be executed through the Event Log command-line interface or through a user interface in Event Viewer.
Previous versions of Windows event logging had issues dealing with an expanding Event Log. More memory is now available in Vista. In fact, a greater array of attributes associated with each event log is available. Prior to Vista, only two attributes for each event were available: EventID and Category. Vista now provides the following attributes: event time, process ID, thread ID, computer name, and Security Identifier (SID) of the user, along with the EventID, Level, Task, Opcode, and Keywords properties. As mentioned in Chapter 1, “The Scope of Computer Forensics,” associating a user with actions on a computer is particularly important when demonstrating control; therefore, the SID is significant if multiple users, each using a different login and password, are using a system.
Event logging has been around since Windows NT. However, the structure of the event logs has undergone significant changes in Windows Vista. Not only has the file structure changed, but the actual event logging has also changed. For example, when the system clock is changed on a machine running XP, the event logs do not record the change. When the same experiment is carried out with a personal computer running Vista, Event Viewer notes the changes to the system clock. Therefore, it is important to understand that Windows operating systems will have major variations from version to version. Event logging is not just valuable on the client side, but it can provide important evidence on Windows Servers.
Windows Search Engine (Indexing) in Vista
The search engine and indexing feature in Vista has changed. Indexing has existed in Windows for more than a decade. Indexing in Windows Vista is now turned on by default, which is different than in previous versions. The indexing feature allows for searches of numerous file types and can locate files based on their metadata, text within a file, or even files within a file (for example, an attachment to an email). A user’s searches can be saved and could be of value later to the investigator.
Unlike many other aspects of Vista, the new default settings for indexing are an advantage to investigators trying to ascertain ownership, intent, and control by a suspect.
ReadyBoost and Physical Memory in Vista
ReadyBoost is a tool first introduced with Vista that allows a user to extend a system’s virtual memory through the use of a USB drive. The purpose of ReadyBoost is to make a computer and its processes run faster. When attaching a USB drive, the option to run ReadyBoost displays (see Figure 2.15).
Note that when ReadyBoost has been activated, any data stored on the USB device has been encrypted with AES-128 encryption. Advanced Encryption Standard (AES) is an encryption standard used by the U.S. government.
ReadyBoost is an important feature for an examiner to be cognizant of, especially because USB memory has become so pervasive in recent times, it can now be used as an extension of a system’s volatile memory, and the file footprint for a USB drive has changed with Vista.
File Metadata
As mentioned, file metadata is an important element of digital evidence. In Vista, when a file is opened, the last access date is not updated, which was the case with previous versions of Windows. As previously noted, dates are a significant source of information for investigators. For example, it is not enough to simply find contraband images stored on the computer of a suspect facing child endangerment charges. The prosecution must also demonstrate intent, with accurate information pertaining to file access times.
Volume Shadow Copy Service
Volume Shadow Copy Service is a backup infrastructure for volumes that was developed by Microsoft for Windows XP and Windows Server 2003. Two types of shadow copy exist: (1) a complete copy or clone of the volume and (2) copies only the changes to the volume. Two data images are created with the original volume, which has read-write capabilities, and the shadow copy volume, which is read-only. Changes at the block level are found in the System Volume Information folder.
Hyberfil.sys
The Hiberfil.sys is a file that contains a copy of the contents of RAM and is saved to a computer’s hard drive when the computer goes into hibernate mode. Because the Hyberfil.sys file is a mirror image of the contents of RAM, the size of this file is generally equal to the size of the computer’s RAM. When the computer is restarted, the contents of Hiberfil.sys are reloaded into RAM.
Remember that RAM can be of great importance to a forensics investigator because it often contains Internet searches, a history of websites visited, and other valuable evidence. This file is found in the root directory of the drive where the operating system is installed.
Vista Summary
Windows Vista can be viewed as more problematic for investigations involving the use of digital evidence. The problems encountered are mainly a result of enhancements made to encryption, through Vista’s Encrypted File System (EFS), BitLocker Drive Encryption with Trusted Platform Module (TPM), and electronic mail encryption in Windows Mail. It appears evident that Microsoft has sought to remove the user from many housekeeping tasks associated with operating systems, such as file restoration and defragmentation. On one hand, shadow copy and file restoration features are beneficial to examiners. On the other hand, the introduction of automatic defragmentation poses new problems for data recovery.
Windows 7
Windows 7 was released to the public in July 2009. The 32-bit version requires a minimum of 1GB of RAM, and the 64-bit version requires a minimum of 2GB of RAM. For most 32-bit versions of Windows 7, there is a physical memory (RAM) limit of 4GB.
The changes in Windows 7 are not as great as the changes that emerged with Windows Vista. Nevertheless, Microsoft has embraced changes in our technical environment that are manifested through advances in biometric authentication, file backups, and consumer growth in removable memory and touch-screen computing. Arguably, the greatest challenges Windows 7 poses include file backups to networks, encryption of USB devices using BitLocker To Go, and touch-screen computing. Changes to the operating system’s registries are also noteworthy to computer forensics examiners because the locations for many of these files have changed.
Biometrics
Connecting a criminal suspect with incriminating evidence is a challenge in computer forensics. The investigator must be able to prove that a suspect had control of a computer when files were created, accessed, modified, or deleted. The use of biometric authentication when accessing a system is one way in which a prosecutor can link a suspect to a series of events and the associated digital footprint left by him. Biometric authentication is different in Windows 7 with the introduction of Windows Biometric Framework (WBF). Previous versions of the Windows operating system worked with fingerprint devices; the vendor was required to provide its own drivers, software development kits (SDKs), and applications. Windows 7 provides native support for fingerprint biometric devices through WBF, which was not a feature of its predecessor, Microsoft Vista.
Backup and Restore Center
It is well documented that bit-stream imaging tools like Helix, FTK, EnCase, and X-Ways can retrieve files that have been marked for deletion. If a file cannot be recovered or can be only partially recovered, a computer forensics investigator might resort to searching for backup copies of files. Therefore, it is important to understand changes to the backup and restoration of files in Windows 7. Most importantly, this operating system supports backups to a shared network space or to an external drive.
The Windows Backup and Restore Center (see Figure 2.16) can be accessed through the Start menu search feature or through the Control Panel. The Backup and Restore Center displays the drive selected to be your backup, available memory, the space being utilized by Windows Backup, and whether a backup is currently running. You can view the breakdown of space utilization by choosing Manage Space from the main Backup and Restore window. Windows 7 backup gives you access to previous system image files marked for deletion and shows exactly how much space each of its backup components is using. After the first backup, the tool copies only the changed bits in files. The tool also provides a comprehensive view of the space required to make available for the backup.
Windows Vista replaced the tape-oriented Windows NT Backup Wizard with a new backup system optimized for external hard disks; some editions also included disaster recovery. However, Vista’s Backup and Restore Center was missing some functionality, including the inability to create a recovery environment disc to boot your system. File and folder backup, in addition to system image backup, were performed with different programs. Moreover, Home Premium users who needed an image backup were required to purchase a third-party program. Windows 7 builds on features developed in Windows Vista’s backup and addresses the aforementioned shortcomings.
Microsoft’s goal with Windows 7 Backup and Restore was to provide usable image and file backup services for users of external hard disks, DVD drives, and network shares without third-party solutions. Unlike Windows Vista, Windows 7 uses a single backup operation to perform both file and image backup. Every edition of Windows 7 includes file and image backup support. Unlike Windows XP, Windows 7 provides disaster recovery, without requiring the reinstallation of the operating system first.
Windows 7 Backup is designed to use the advanced features of NTFS the default file system used by Windows XP, Vista, and Windows 7. When you use an NTFS-formatted drive as a backup target, you can create scheduled backups that record changes to the system image and changes to individual files. Moreover, Windows 7 Backup backs up only NTFS-formatted drives. Windows 7 does not include the Removable Storage Service (RSS) used by NTBackup, the backup tool used in Windows 2000 and XP. However, if the backup does not reside on tape or removable media, the user can copy NTBackup files to the Windows 7 system and run NTBackup to restore files directly to Windows 7.
It is important for computer forensics investigators to understand how files are being backed up because attached devices could contain important evidence and permission to access backup servers. A court-issued warrant could be critical.
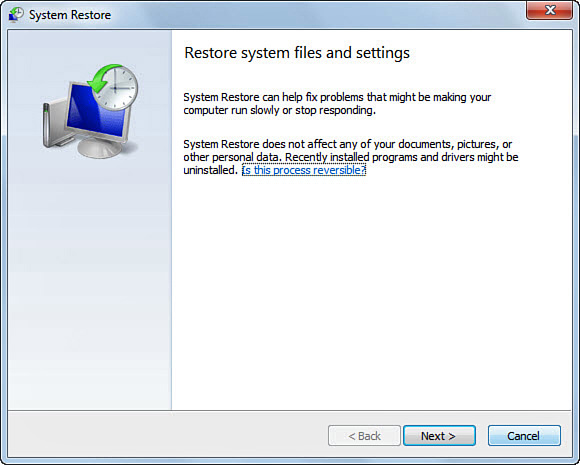
Restoration Points
Restoration points have been a feature of Window’s operating systems for a number of years. However, there are some changes to this tool in Windows 7. Unlike Windows Vista, Windows 7 provides a few options for configuring the System Restore option. For example, the user can prevent System Restore (see Figure 2.17) from backing up the Registry, meaning that restore points will not consume as much disk space. This has implications for forensic investigators because registries are often an important source of evidentiary data in investigations. Furthermore, the user can eliminate all the restore points by pressing the Delete button, which has the potential to reduce the amount of data available for forensic investigators.
Backing Up to a Network
A computer forensics investigator not only needs to be concerned about backups to external devices, but also needs to be cognizant of a system’s ability to back up to a network. Windows 7 Starter, Home Basic, and Home Premium editions support backups to only local drives, whereas Windows 7 Professional, Ultimate, and Enterprise editions also support backups to network locations. Therefore, an investigator must also consider that a system’s imaging and analysis could also include external devices and a network. This will certainly impact the scope of an investigator’s search warrant.
BitLocker To Go
BitLocker was a tool introduced with Windows Vista. The tool was developed to encrypt at the file and folder level, or even encrypt an entire hard drive. BitLocker To Go is a more advanced tool that debuted in Windows 7. What sets this tool apart from its predecessor is that the encryption tool encrypts removable USB storage devices. Files written to USB devices that are AES encrypted can be decrypted in previous versions of Windows (XP and Vista). XP and Vista provide read-only access until the files are copied to another drive. The application BitLocker To Go Reader (bitlockertogo.exe) allows the investigator to view the files from a USB drive using XP or Vista. Simply removing the USB device activates the encryption, so an examiner needs to be cognizant of this fact. This has serious implications for computer forensics examiners because the perpetrator of a crime might not have used BitLocker To Go simply to encrypt the hard drive; she also might have encrypted associated removable memory with the same encryption algorithm. The user who wants to encrypt a drive is required to either enter a “strong password” or use a smart card. Windows 7 provides the option to save the recovery key to a file or to print it, which is of note to an investigator.
COFEE (Computer Online Forensic Evidence Extractor) is a tool developed by Microsoft that is made available exclusively to law enforcement to work on systems running BitLocker. According to Microsoft, this “fully customizable tool allows your on-the-scene agents to run more than 150 commands on a live computer system.” Microsoft also states that it “provides reports in a simple format for later interpretation by experts or as supportive evidence for subsequent investigation and prosecution.” COFEE has also been developed for Windows 7 and is used by law enforcement when working with a system running BitLocker To Go. The major disadvantage with using the tool is that the system must be live and will not work if the suspect has powered down the computer.
Establishing Ownership of a USB Device
Establishing ownership of a USB flash memory device can be critical for a computer forensics investigator. Interestingly, these devices leave a time stamp and other metadata when attached to a system running Windows 7. The metadata includes the unique serial number or identification code originally assigned to the USB device. A record of when the device was last connected to a computer is also recorded in the metadata. However, not all of these devices leave a signature behind. For those that do leave a signature, law enforcement can link the usage of those devices to the suspect’s computer. The information about USB devices is stored in the Registry key called HKEY_LOCAL_MACHINESystemCurrentControllerSetEnumUSB. Figure 2.18 displays the contents of this hive.
The contents of this Registry can be parsed using a freeware utility called USBDeview, which was created by NirSoft (www.nirsoft.net). The examiner can generally determine the device manufacturer through the VendorID, a unique identifier with the serial number displayed along with the ProductID, which identifies the make and model of the device. The tool can also provide information about when the device was last attached to the computer. Figure 2.19 illustrates the various types of USB devices that were connected to a computer using the USBDeview application.
Touch-Screen Computing in Windows 7
Demand for touch-screen computing has clearly been very strong, and the supply for touch-screen devices will continue to grow. From smartphones to the Apple iPod Touch, touch screens are pervasive. Interestingly, in April 2007, Microsoft CEO Steve Ballmer stated, “There’s no chance that the iPhone is going to get any significant market share.” Ballmer had a change of heart in 2009 when he stated, “We believe in touch.” This belief was followed by conviction when Microsoft released Windows 7 with integrated touch-screen technology. Previously, touch-screen operating systems in the personal computer market were associated with tablet PCs. Windows 7 operating system supports touch-screen computing natively, allowing the user to move and size application windows, for example, with the use of a touch-enabled screen. The user also now has the ability to use an onscreen keyboard to type Internet searches or URLs, or even draw the letters. There is no question that evidence pertaining to Internet communications is extremely important to criminal investigations, but integrating new touch-screen features into Windows 7 has noteworthy implications for forensic examiners and prosecutors. Potentially, an investigator will not be able to use a traditional keystroke logger, which relies on keyboard input, for the same method of evidence capture. Computer forensics tools will, of course, be able to track sites visited, but login and password information, often captured with a keystroke logger, could be problematic. Notorious hackers Alexey Ivanov and Vasili Gorshkov were convicted based on evidence attained by the FBI using a keystroke logger. The user can use fingers or a pen to write, which implies that handwriting analysis might need to be carried out and the computer screen may need to be dusted for fingerprints to find corroborating evidence to prove ownership of the computer system.
Sticky Notes
Sticky Notes (see Figure 2.20) are a feature of Windows 7, and the application comes with Home Premium, Professional, and Ultimate editions of the operating system.
Sticky Notes were available in Vista, but these notes now have more advanced features, including the ability to format text, resize, and flip through open Sticky Notes. Sticky Notes support pen and touch input if the user is using a pen or a touchscreen. Sticky notes may contain important evidence for a case, but more importantly may assist the investigator in placing the suspect in front of the computer and prove ownership and control. This argument is further strengthened if the suspect used a pen with the Sticky Notes. A handwriting analyst could potentially be asked to testify with the computer forensics examiner. Sticky Notes files have an .snt file extension and, by default, are saved to the following location: C:UsersYourNameAppDataRoamingMicrosoftSticky Notes.
An .snt file can be viewed in Microsoft Word. However, the commercial tool Structured Storage Extractor allows for a forensic examination.
Registry Analysis in Windows 7
As mentioned earlier, Windows Registry lies at the core of the operating system and can be a tremendous resource for evidence for a computer forensics investigator. It stores the settings and options for the entire system and therefore can provide a wealth of information.
Although the Registry viewed by standard Registry Editor (regedit.exe) appears to be a single database, it is in fact a highly integrated collection of files. The following list details the Registry hives and associated file paths found in Windows 7.
HKLMSystem
File path: C:WindowsSystem32configSYSTEMHKLMSAM
File path: C:WindowsSystem32configSAMHKLMSecurity
File path: C:WindowsSystem32configSECURITYHKLMSoftware
File path: C:WindowsSystem32configSOFTWAREHKUUser SID
File path: C:Users<username>NTUSER.DATHKUDefault
File path: C:WindowsSystem32configDEFAULTHKLMComponents*
File path: C:WindowsSystem32configCOMPONENTSUsrclass.dat*
File path: C:Users<username>AppDataLocalMicrosoftWindowsusrclass.dat
As with Vista, Windows 7 does not automatically record the Last Access time on the NTFS volume. By default, Microsoft disabled the update to reduce performance overhead, which in turn caused examiners to lose a very important source of evidence. The value accountable for that setting is found in the following location:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControl
FileSystem>NtfsDisableLastAccesUpdate
Registry Paths and Corresponding Files in Windows 7
Establishing the sequence of events to create a timeline using the operating system is crucial to a computer forensic investigation. Registry keys contain information pertaining to events and the associated system’s time.
In addition to establishing the system’s time, registries can provide an examiner with the LastWrite time for a particular key. Although the time stamp for each value is not recorded, it can still be helpful to know that the key was changed, especially when a Registry key has a single value. Moreover, the time stamp from the Registry key can be compared against other time stamps on a system.
Event Viewer in Windows 7
When a computer running Windows 7 is shut down unexpectedly, an event is automatically created. That event is subsequently escalated to the category of Error. Moreover, when the metadata of the event log is observed, it provides the time when the system was shut down. An additional event log, with a new event ID, is created when the system is restarted; the system documents that an unexpected system shutdown occurred due to a possible loss of power. This event creates a unique Power Button Time Stamp.
When the system date and time are changed, an instant log, with the event ID and a designation of Security State Change, is created. Moreover, the previous date and time and the changed date and time are recorded. This metadata is stored in XML format, and the event viewer GUI provides an option to view this content in either an XML format or in a user-friendly text format.
Understanding how system time changes are recorded is important because an attorney might question an examiner’s methods of reconstructing events. Events differ from one operating system to another, as will file metadata.
Web Browser
The U.S. version of Windows 7 is bundled with Internet Explorer 8. This browser introduces a new way to display HTML pages on the Web. It is important to note that there are substantial changes in Internet Explorer 8, which provides new challenges for forensics investigators.
InPrivate Browsing, a feature of Windows Internet Explorer 8 (see Figure 2.21), helps to protect data and privacy by preventing the browsing history, temporary Internet files, form data, cookies, and usernames/passwords from being stored or retained locally by the browser, leaving virtually no evidence of the user’s browsing or search history. During an InPrivate Browsing session, files that are saved to the hard disk and websites that are added to the user’s Favorites are preserved. The most successful retrieval of Internet forensics always comes from a live system because Internet files and search information often reside in RAM, which is volatile memory.
InPrivate Browsing has an impact on forensics analysis because the investigator will potentially lose more evidence relating to the suspect’s online activities. Internet activity is especially important in child pornography and online fraud cases. An InPrivate Browsing session in Internet Explorer 8 can be initiated from the new Safety menu by selecting Start InPrivate Browsing from a New Tab page. Once initiated, a new Internet Explorer 8 window opens with an InPrivate indicator displayed to the left of the address bar. Behavior of the browser changes only for the InPrivate session. Therefore, if the user had the standard window open, the browser history would be stored as normal, whereas the activity within the InPrivate mode window would be discarded. Other competing browsers, like Firefox and Chrome, have a similar privacy mode.
When searching for Internet activity, it is not only necessary to check for multiple users, but to also recognize that a user may use multiple web browsers, which could also include Tor. Nowhere is this more evident than in the investigation of Casey Anthony. Apparently, investigators retrieved 17 vague searches related to Internet Explorer but failed to recover more than 1,200 Google searches performed using Firefox, including searches for “fool-proof suffication”. The defense attorneys knew about the Firefox browser evidence and were surprised that they never came to light during the trial.
File Grouping
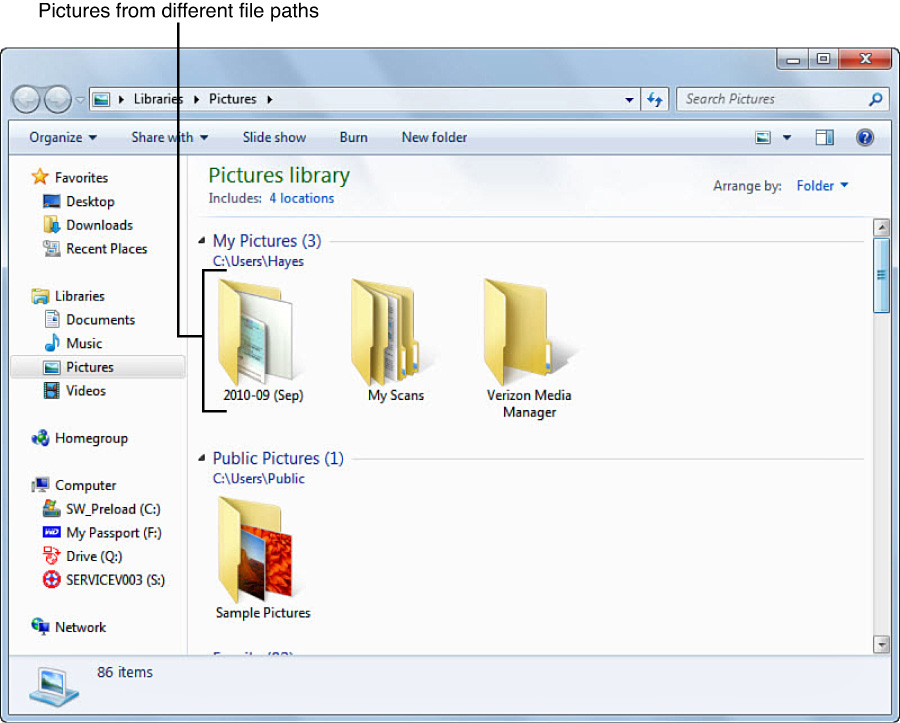
Windows 7 introduced more advanced “library” functionality, which allows users to view all their files in one logical location, nevertheless, the actual files physically distributed randomly across a PC or even across a network. Figure 2.22 shows the Pictures Library.
The folder that is added to the library has an index attached to it, so it allows for faster searching, which can be particularly helpful to investigators as they can use FTK to look for any file mapped to a particular index. A parole officer making a house call to a sex offender on probation may also want to use this feature to view picture files expeditiously, although this cannot be considered a forensic search.
Indexing is a prerequisite for a folder to be added to the library. Indexed locations can be investigated to determine user-specified places. They are recorded in the following Registry key:
HKLMSoftwareMicrosoftWindows SearchCrawlScopeManagerWindows
SystemIndexWorkingSetRules
Windows Federated Search
Windows Search 4.0 was introduced with Windows Vista as an update. However, the introduction of the libraries feature extended the usefulness of this search feature. The libraries can be accessed based on different metadata criteria encapsulated within the files. Microsoft introduced Windows Federated Search, which allows a user to query external data sources, including databases and even content from the Web, if they support OpenSearch technology. Search connector files exist for many popular websites and services, like YouTube and Picasa. The most important field in the XML file is the <domain> tag because it displays a suspect’s website searches. A computer forensics examiner needs to understand that a suspect may have retrieved information from the Internet without a web browser by utilizing the search features of Federated Search. With Windows 7, the computer forensics examiner has to observe these new *.osdx search connector files for web searches. There is arguably less intent by the suspect to access web content. Here is an example of the XML content output from a connector file:
<?xml version="1.0" encoding="UTF-8"?>
<searchConnectorDescription xmlns="http://schemas.microsoft.com/windows/2009/
searchConnector">
<description>Search deviations on DeviantArt.com</description>
<isSearchOnlyItem>true</isSearchOnlyItem>
<domain>http://backend.deviantart.com</domain>
<supportsAdvancedQuerySyntax>false</supportsAdvancedQuerySyntax>
<templateInfo>
<folderType>{8FAF9629-1980-46FF-8023-9DCEAB9C3EE3}</folderType>
</templateInfo>
<locationProvider clsid="{48E277F6-4E74-4cd6-BA6F-FA4F42898223}">
<propertyBag>
<property name="LinkIsFilePath" type="boolean"><![CDATA[true]]></property>
<property name="OpenSearchShortName"><![CDATA[DeviantArt]]></property>
<property name="OpenSearchQueryTemplate"><![CDATA[http://backend.deviantart. com/rss.xml?q=boost%3Apopular+{searchTerms}&offset={startIndex}]]></property>
<property name="MaximumResultCount" type="uint32"><![CDATA[100]]></property>
</propertyBag>
</locationProvider>
</searchConnectorDescription>
Windows 8.1
The first thing that you notice about Windows 8 and 8.1 is the change in the user interface. By default, you are brought to the Start screen, which has a series of tiles and each tile represents an application, as shown in Figure 2.23.
This is a departure from the user desktop being the default landing place after the computer’s initial bootup. You can quickly access the desktop from the Start screen by clicking the Desktop tile. As you can see in Figure 2.24, the most notable change is that there is no Windows Start button on the lower left of the screen.
To access applications and programs or to change the computer’s settings, you need to use the Start screen. The Windows interface on the PC is similar to a tablet running Windows 8 and has a similar look to a smartphone running this operating systems (as does the Xbox One). All these devices create a Windows ecosystem, and a Windows Live account can seamlessly join the user experience across various devices. This is a similar strategy to what Apple has already successfully created.
New Applications
Some new applications come standard with Windows 8. Mail enables the user to combine all email accounts into one app. Videos is an app that enables the user to browse and watch movies on their PC or play them on their television. The People app enables to user to communicate with their contacts on email, Twitter, Facebook, and other apps. Other apps on Windows 8 include Maps, Games, Food + Drink, Weather, Sports, Health + Fitness, Travel, and News. Many of the changes to Windows 8 reflect its focus on its support of touchscreen.
Gathering Evidence
The Recycle bin has no major changes, although the interface has changed slightly. Deleted files are found in the $Recycle.Bin folder. If the investigator wishes to find information about connected USB devices, not much has changed—this information can be retrieved from the Registry Editor at HKEY_CURRENT_CONFIGSystemCurrentControlSetEnumUSB, as in Figure 2.25.
Of course, the application, USBDeview, and other forensics software such as EnCase will also recover this information.
Security in Windows 8.1
A major change is Picture Password. This feature allows the user to select a photo to lock the computer. The computer is then unlocked with a series of gestures on the screen. For example, a user may decide to draw two circles on a specific portion of a photo.
Summary
An operating system is responsible for managing a computer’s resources, which includes the computer’s hardware. It is important to understand how an operating system works because much of the interaction between a user and a computer can be viewed through changes to the operating system. A computer forensics examiner will also encounter a variety of different file systems on computers and storage media. Each file system will vary in terms of file size, metadata, encryption, and permissions. The type of evidence, the weight of evidence, and the accessibility and location of the evidence all differ based on the type of operating system and file system running on a suspect’s computer. Professional computer forensics tools generally include a view of files in hexadecimal format, and therefore it is important for a computer examiner to understand how to read hexadecimal code. These tools also display a physical view of files stored on a hard drive, so it is helpful to understand the physical layout of a hard drive. Windows Registry can provide a treasure trove of evidence for a forensic investigator. Much of the user’s activity, such as installing an application or logging on to the system, can be ascertained through an examination of the registries. Registries are particularly important when multiple users are utilizing a computer and you need to differentiate each user’s activity.
Microsoft’s Windows Vista introduced many notable changes and was a dramatic departure from previous versions of the operating system. Of note was the new XML file format for system events and also the robust querying abilities through the use of XPath. Sometimes an investigator will rely on file backups for evidence, and Volume Shadow Copy in Vista means that the nature of file backups has changed. The biggest challenge for a forensic examiner encountering a system running Vista is BitLocker, a tool used to encrypt at the file, folder, or drive level. Windows 7 added to this challenge by enabling USB devices to be encrypted. Windows 7 introduced new features, which will surely impact investigations; the operating system now natively supports biometric authentication and also allows for the use of a touch screen monitor without downloading any additional drivers. Windows 7 enables a user to back up the system and files to a network, and this feature provides an indication of future issues for investigators to deal with: cloud computing.
Key Terms
access control list: A list of permissions associated with a file and details the users and programs granted access to the file.
actuator arm: Contains a read/write head that modifies the magnetization of the disk when writing to it.
Advanced Encryption Standard (AES): An encryption standard used by the U.S. government.
allocated storage space: The area on a volume where a file or files are stored.
alternate data stream (ADS): A file’s set of attributes.
bad sector: An area of the disk that can no longer be used to store data.
Basic Input/Output System (BIOS): Starts an operating system by recognizing and initializing system devices, including the hard drive, CD-ROM drive, keyboard, mouse, video card, and other devices.
binary: The language that computers understand.
bits: Can only be one of two values, where a 1 is a positive charge and a 0 is a negative charge.
bootstrapping: The process of running a small piece of code to activate other parts of the operating system during the boot process. The bootstrap process is contained in the ROM chip.
byte: Comprised of eight bits and is the smallest addressable unit in memory.
COFEE (Computer Online Forensic Evidence Extractor): A tool developed by Microsoft that is made available exclusively to law enforcement to work on systems running BitLocker.
cluster: A logical storage unit on a hard disk that contains contiguous sectors.
Component Object Model (COM): Allows nonprogrammers to write scripts for managing Windows operating systems.
control character: Begins, modifies, or terminates a computer operation and is not a written or printable symbol.
cylinder: The same track number on each platter, spanning all platters in a hard drive.
Data Link Escape: A communications control character that specifies that the proceeding character is not data, but rather a control code.
defragmentation: The process of eliminating the amount of fragmentation in a file system to make file chunks (512K blocks) closer together and increase free space areas on a disk.
disk geometry: Refers to the structure of a hard disk in terms of platters, tracks, and sectors.
disk signature: Identifies the disk to the operating system.
End of Sector Marker: A two-byte structure found at the end of the MBR.
event: A communication between one application and another program or user on a computer.
Event Viewer: A Windows application used to view event logs.
FAT (File Allocation Table): A file system developed by Microsoft that utilizes a table to store information about where files are stored, where file space is available, and where files cannot be stored.
FAT12: Introduced in 1980 as the first version of FAT. It is the file system found on floppy disks.
FAT16: A 16-bit file system that was developed for use with MS-DOS.
FAT32: A 32-bit version of FAT that uses smaller clusters, allowing for more efficient utilization of space.
FAT64: A file system, also referred to as exFAT (Extended File Allocation Table), that was developed by Microsoft.
FATX: A file system developed for use on the hard drive of Microsoft’s Xbox video game console, as well as associated memory cards.
file compression: Allows the user to reduce the number of bits in a file, which allows for faster transmission of the file.
file slack: Refers to the remaining unused bytes in the last sector of a file.
file system: A hierarchy of files and their respective directories.
FTK Imager: A professional computer forensics bit-stream imaging tool that is available for free.
hex editor: Enables a forensics examiner to view the entire contents of a file.
hexadecimal: A numbering system that uses 16 symbols (base 16), which includes the numbers 0 to 9 and letters A to F.
journal: Tracks changes to files for fast and efficient restoration of files when there is a system failure or power outage.
journaling: A file system record keeping feature that records changes made to files in a journal.
kernel: At the core of the operating system. It is responsible for communication between applications and hardware devices, including memory and disk management.
logical file size: The amount of data stored in a file.
Master Boot Code: Code used by the BIOS to start the boot process.
Master Boot Record (MBR): Involved in the boot process and stores information about the partitions on a disk, including how many exist and their location.
Master File Table (MFT): Maintains file and folder metadata in NTFS, including the filename, creation date, location, size, and permission for every file and folder.
Master Partition Table: Contains descriptions about the partitions on a hard disk.
nibble: One digit of a hexadecimal (hex) value, which represents 4 bits.
NTFS (New Technology File System): Developed by Microsoft and introduced with Windows NT.
operating system: A set of programs used to control and manage a computer’s hardware and system resources.
partition: A logical storage unit on a disk.
physical file size: The actual disk space used by a file.
read-only memory (ROM): Nonvolatile storage that is generally not modified and is used during the boot process.
ReadyBoost: A tool first introduced with Vista that allows a user to extend a system’s virtual memory through the use of a USB drive.
sector: On a magnetic hard disk, represents 512 bytes; on an optical disk, represents 2048 bytes.
spindle: Found at the center of the disk, this is powered by a motor and used to spin the platters.
tracks: Thin, concentric bands on a disk that are comprised of sectors, where data is stored.
unallocated storage space: Available file storage space.
Unicode: An international encoding standard that supports various languages and scripts from across the world.
Volume Shadow Copy Service: A backup infrastructure for volumes developed by Microsoft for Windows XP and Windows Server 2003.
Windows: A series of operating systems with a graphical user interface (GUI), developed by Microsoft.
Windows Registry: A hierarchical database that stores system configuration information.
XML (Extensible Markup Language): A standardized language that is compatible for use on the Internet.
XPath (XML Path Language): A powerful query language used for searching XML documents.
Assessment
Classroom Discussions
1. Why is it important to learn about hexadecimal?
2. How can the type of operating system influence the work of a computer forensics examiner?
Multiple Choice Questions
1. Which of the following values are found in binary?
A. 0 or 1
B. 0–9 and A–F
C. 0–9
D. A–F
2. Which of the following values are found in hexadecimal?
A. 0 or 1
B. 0–9 and A–F
C. 0–9
D. A–F
3. A nibble represents how many bits?
A. 2
B. 4
C. 8
D. 16
4. Which of the following best describes an actuator arm on a hard disk?
A. It is an area of the disk that can no longer be used to store data.
B. It is a circular disk made from aluminum, ceramic, or glass where data is stored magnetically.
C. It is found at the center of the disk, is powered by a motor, and is used to spin the platters.
D. It contains a read/write head that modifies the magnetization of the disk.
5. What is the name of the nonvolatile storage that can generally not be modified and is involved in the boot process?
A. RAM
B. Flash memory
C. Partition
D. ROM
6. Which of the following refers to the rigid disk where files are stored magnetically?
A. Cylinder
B. Actuator
C. Spindle
D. Platter
7. Which of the following file systems was developed for use on the Xbox?
A. FAT12
B. FAT16
C. FAT32
D. FATX
8. Which of the following contains the permissions associated with files?
A. Journal
B. Alternate data stream
C. Access control list
D. BIOS
9. Which of the following best describes the information contained in the MFT?
A. File and folder metadata
B. File compression and encryption
C. File permissions
D. All of the above
10. Which of the following Windows features allows the user to extend virtual memory using a removable flash device?
A. BitLocker
B. Volume Shadow Copy
C. ReadyBoost
D. Backup and Restore
Fill in the Blanks
1. A(n) ________ can possess one of two values: 1 or 0.
2. ________ is the base 16 numbering system, which includes numbers 0 to 9 and letters A to F.
3. A(n) ________ is comprised of eight bits and is the smallest addressable unit in memory.
4. The Master Boot ________ is used by the BIOS to start the boot process.
5. ________ ________ refers to the structure of a hard disk in terms of platters, tracks, and sectors.
6. ________ file system was introduced in 1980 as the first version of FAT and is the file system found on floppy disks.
7. The ________ uses tracked changes to files for fast and efficient restoration of files when there is a system failure or power outage.
8. ________ ________ is a hierarchical database that stores system configuration information. The Registry is comprised of two elements, keys and values.
9. ________ is the process of eliminating the amount of fragmentation in a file system to make file chunks (512KB blocks) closer together and increase free space areas on a disk.
10. ________ ________ is a Windows application used to view event logs.
Projects
Create a Guide to Navigating the Registry
Choose a Windows operating system and then create an investigator’s guide to navigating through the Registry for that system. Highlight in a table what you believe to be the most important keys for the investigator to focus on.
Explain the Boot Process
Detail the process that occurs when the power button on a personal computer is pressed to start a system.
Use Event Viewer
Find a computer running Windows XP or above. Using that computer’s Event Viewer, document the events that occurred in an investigator’s notes.
Explain File Storage
Explain the process that occurs when saving a Word document that is 1500 bytes in size. Include how the computer physically stores the file, and also detail how the operating system keeps track of the new file being created.
Submit USB Evidence
Download the free USBDeview program to a computer running Windows Vista or Windows 7. Run the application to determine the types of USB devices that were attached to the computer. Submit your report as directed by your instructor.