Chapter 4. Acquiring Evidence in a Computer Forensics Lab
Learning Outcomes
After reading this chapter, you will be able to understand the following:
![]() What is needed to have a computer forensics laboratory certified;
What is needed to have a computer forensics laboratory certified;
![]() Good practices for managing and processing evidence in a computer forensics laboratory;
Good practices for managing and processing evidence in a computer forensics laboratory;
![]() How a computer forensics laboratory should be structured;
How a computer forensics laboratory should be structured;
![]() Computer forensics laboratory requirements for hardware and software;
Computer forensics laboratory requirements for hardware and software;
![]() Proper ways to acquire, handle, and analyze digital evidence;
Proper ways to acquire, handle, and analyze digital evidence;
![]() Methods for investigating financial fraud; and
Methods for investigating financial fraud; and
![]() How to use UNIX commands to scour files for particular information of interest.
How to use UNIX commands to scour files for particular information of interest.
Introduction
The process by which an investigator acquires evidence is just as important as the evidence itself. Remember that the term forensics means “to bring to court.” Evidence can only be brought to trial if it was legally obtained—through a search warrant approved by a court magistrate (or if consent to a search was granted). Certain forms are necessary when handling evidence, including the Chain of Custody form. Additionally, because forensics is a science, the process by which the evidence was acquired must be repeatable, with the same results.
Lab Requirements
The creation of a computer forensics laboratory, with all the necessary equipment, is an important part of evidence handling, acquisition, and analysis. Moreover, there are important management considerations to be aware of. Although notable differences might exist between one computer forensics laboratory and another, there are still similarities in basic requirements and guidelines for forensics laboratories. This ensures that certain standards are maintained in terms of equipment and the industry standards for utilizing that equipment. Many fields related to computer science are bereft of standards to guide us. However, in computer forensics, standard practices do exist, and they are assessed and certified by an independent body known as the American Society of Crime Laboratory Directors.
American Society of Crime Laboratory Directors
ASCLD is a nonprofit organization that provides a set of guidelines and standards for forensic labs. The organization not only promotes excellence in forensic practices, but also encourages innovation in the forensic practitioner community. ASCLD is not an accrediting body and should not be confused with ASCLD/LAB. More information can be found on their website at ascld.org.
American Society of Crime Laboratory Directors/Lab Accreditation Board (ASCLD/LAB)
ASCLD/LAB was originally a committee within ASCLD when it was created in 1981. Since 1982, however, it has been accrediting crime labs. In 1984, ASCLD/LAB became a separate nonprofit entity with its own board of directors. It currently certifies labs for federal, state, and local agencies, as well as some crime labs based outside the United States. The certification process of crime labs includes computer forensics labs. As an impartial entity, ASCLD/LAB strives to maintain certain standards for forensics labs, including standards that govern the behavior and practices of lab employees and their managers. In other words, those who work in a forensic lab must be always mindful of the law and continually adhere to proper scientific practices. Moreover, ASCLD/LAB also promotes a code of ethics for lab staff and management.
ASCLD/LAB Guidelines for Forensic Laboratory Management Practices
Laboratory managers are advised to act with integrity and create an environment of trust and honesty. A forensics laboratory should also have quality controls and maximize the use of laboratory resources in an efficient manner, to effectively manage the laboratory’s casework. A laboratory manager is also accountable for maintaining the health and safety of those who work in the lab. Moreover, maintaining the security of the laboratory, particularly with respect to access, is also a responsibility of the manager. The manager must also ensure that he hires highly qualified staff and also encourages research and continuous training, including staff certifications. The following list summarizes the proper laboratory management practices, as outlined by ASCLD/LAB at http://ascld.org/files/library/labmgtguide.pdf:
![]() Managerial competence
Managerial competence
![]() Integrity
Integrity
![]() Quality
Quality
![]() Efficiency
Efficiency
![]() Productivity
Productivity
![]() Meeting organizational expectations
Meeting organizational expectations
![]() Health and safety
Health and safety
![]() Security
Security
![]() Management information systems
Management information systems
![]() Qualifications
Qualifications
![]() Training
Training
![]() Maintaining employee competency
Maintaining employee competency
![]() Staff development
Staff development
![]() Environment
Environment
![]() Communication
Communication
![]() Supervision
Supervision
![]() Fiscal
Fiscal
![]() Conflict of interest
Conflict of interest
![]() Response to public needs
Response to public needs
![]() Professional staffing
Professional staffing
![]() Recommendations and references
Recommendations and references
![]() Legal compliance
Legal compliance
![]() Fiscal responsibility
Fiscal responsibility
![]() Accountability
Accountability
![]() Disclosure and discovery
Disclosure and discovery
![]() Work quality
Work quality
![]() Accreditation
Accreditation
![]() Peer organizations
Peer organizations
![]() Research
Research
![]() Ethics
Ethics
Many law enforcement agencies strive to attain ASCLD/LAB certification, but most never gain this certification. It might not always be necessary to realize this certification, but agencies should still try to adhere to many of the principles outlined by ASCLD/LAB, including maintaining best practices and industry protocols, proper documentation, and ongoing training for lab personnel.
Scientific Working Group on Digital Evidence (SWGDE)
The Scientific Working Group on Digital Evidence (SWGDE) is a committee dedicated to sharing research and setting standards for investigators working with digital and multimedia evidence. The group was formed in 1998 and subsequently began working with ASCLD/LAB in 2000. Later in 2003, the field of digital evidence was added to the ASCLD/LAB accreditation program.
Federal, state, and local law enforcement officers who do not have any commercial interests are invited to join as regular members. Additionally, educators and those from the private sector can join through associate memberships. SWDGE is a marvelous resource for computer forensics research on topics that range from investigations involving various operating systems to best practices in mobile phone examinations (www.swgde.org).
Private Sector Computer Forensics Laboratories
Computer forensics labs exist in the private sector for many reasons. Sometimes a lab is developed to make profit through client consulting services. Meanwhile, other large organizations maintain a lab to investigate internal fraud or fraud suffered by their customers. Banks and credit card companies often have their own internal computer forensics practitioners. All major accounting firms maintain sophisticated computer forensics laboratories that are primarily used to support investigations requested by their clients. Most of these investigations are not criminal investigations, but are electronic discovery (eDiscovery) investigations. eDiscovery is the detection of electronic data for the purposes of litigation. For example, when a company sues another company, the plaintiff may request certain electronically stored information. A plaintiff is the party that makes a claim against another party and initiates a lawsuit. Electronically stored information (ESI) can include email, Word documents, spreadsheets, databases, or any other type of digitally stored information. Under the Sarbanes–Oxley Act, publicly traded companies must maintain all electronic information, including emails, for a minimum of five years. Sometimes the Securities and Exchange Commission (SEC) will issue a 10-day notice to a publicly traded company. This notice directs a company to produce certain documents pertaining to an investigation within 10 days. For many companies, which may have tens of thousands of hard drives, finding specific historical information may be untenable given their limited IT resources and the imposed time constraint. Therefore, many companies will employ the services of accounting firms to quickly find the information requested by SEC investigators.
eDiscovery generally requires the expertise of computer forensics investigators, information technology (IT) staff, and corporate lawyers. The IT staff generally coordinates with computer forensics investigators to determine the location of the evidence (servers or employee computers), and the computer forensics investigators ensure that all evidence acquired is done so in a scientific manner and ultimately is available as court-admissible evidence. The lawyers will determine the value of the evidence extracted. In summary, the corporate IT staff members act as liaisons between the computer forensics examiners and the firm’s lawyers.
At large accounting firms, several different laboratories make up the computer forensics department. Although there are differences from company to company, the following is an outline of the different types of laboratories; the skills the staff members possess can differ according to the area in which they work.
Evidence Acquisition Laboratory
This first laboratory is responsible for extracting evidence from hard drives, flash drives, and other storage devices to create read-only forensic image files. The staff members in this laboratory need to be skilled in imaging software like FTK, EnCase, and X-Ways. Additionally, they will often have to crack passwords using tools like AccessData’s Password Recovery Toolkit (PRTK), perhaps with the addition of rainbow tables. Files, folders, and drives may also need to be decrypted. Laptop hard drives and associated removable flash memory or external drives often utilize an encryption tool such as Credant, and therefore a decryption key will be needed by the computer forensics examiners. Often, decryption is nearly impossible or impossible when a suspect has used Pretty Good Encryption (PGP) or has activated full-disk encryption using FileVault on a Mac.
Email Preparation Laboratory
Email evidence is arguably the most important type of evidence that can be retrieved from a computer. Email often reveals our most innermost thoughts and the most incriminating evidence. Because of the tremendous importance of email in investigations, some computer forensics departments have a laboratory dedicated to email, where staff will parse email files to make them easier to view by attorneys involved in a case.
Inventory Control
Sometimes an investigation involves thousands of hard drives and storage media. Moreover, the sources can vary greatly, from magnetic tapes, to hard disk drives, to zip disks, to thumb drives. Therefore, proper management and control of this storage media is critical. A laboratory often is devoted to the managing and storage of evidence.
Large corporate investigations create vast amounts of evidentiary data. For example, the collapse of Enron due to corporate malfeasance necessitated the use of numerous computer forensics examiners, who sifted through thousands of emails and other digital data. The investigation generated 31 terabytes of data (1012 bytes), which is the equivalent of 15 academic libraries. More paper was generated for this one investigation than exists in the Library of Congress.
Web Hosting
When evidence has been extracted, analyzed, and parsed into a readable format, it needs to become available to a company’s lawyers. Simply emailing the evidence to legal counsel is often not feasible. Therefore, a computer forensics department or consulting firm provides a web hosting service, where authorized individuals can access the evidence for an investigation through a secure website. Discovery is the period leading up to a trial when each party involved in civil litigation can request evidence from the other party. Hence, web hosting can provide a safe and effective way to display evidence to the plaintiff and defense counsels. Of course, discovery can include not only evidence from a computer, but also evidence in the form of depositions or subpoenas from entities not party to a lawsuit.
The technical skills of staff members assigned to this area of a computer forensics department are certainly different than in other areas of the department. Website designers are required (at least, during the initial phase) to create the site, and web developers are needed to organize the information. Additionally, staff skilled in database design, development, and management are required to create a database that will not only contain searchable evidence and reporting features, but also will manage the secure access to the information. In addition, staff are needed to continually upload and maintain the evidence online for various investigations.
Computer Forensics Laboratory Requirements
Computer forensics labs vary greatly from region to region, but there are certain standards and requirements that every lab must maintain. This section details the basic layout, equipment, and standards that a legitimate computer forensics lab must adhere to.
Laboratory Layout
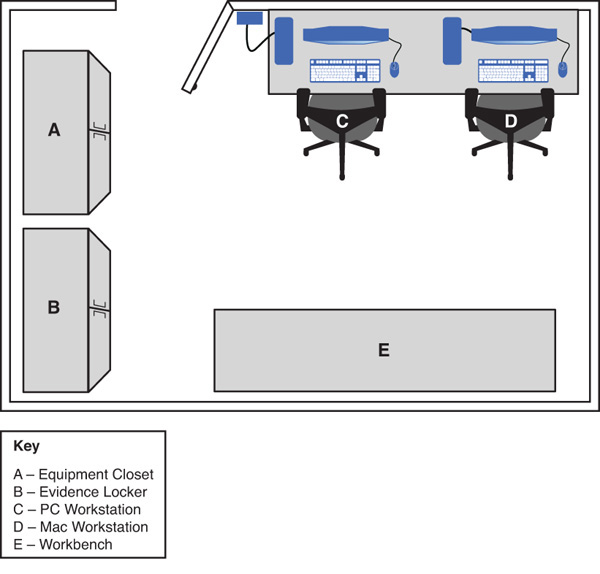
The layout of your laboratory will be determined by your investigative needs, the number of staff who will be involved in investigations, and the resources that you have available. Figure 4.1 is a diagram of a relatively small computer forensics laboratory.
Workstations
The workstations in a computer forensics laboratory are used for investigators to acquire evidence in the form of read-only image files. With the proliferation of Apple Macintosh machines, it is now more commonplace to find Macintosh workstations. All workstations should be password protected and should ideally use biometric authentication to gain access. All case files should be password protected.
Workbench
A workbench is used to prepare hardware devices for investigative analysis. When cloning a device, the computer’s case is opened to remove the hard drive. On the area where hard drives will be cloned, there should be rubber mats to ensure that no static electricity from a metal surface will interfere with the suspect’s drives. If an Apple iMac needs to be opened to retrieve the hard drive, a lot of space is required to ensure that the screen is dismantled safely (without damage). As with all electronic evidence, the area needs to be well lit—not only to work safely with evidence, but also for appropriate photography of all evidence.
Evidence Locker
An evidence locker is a metal cabinet with individual compartments that can be locked individually. These cabinets are often made of steel with tamper-resistant padlocks. A high-end door lock, like a Simplex lock, should be used with other physical security measures. Figure 4.2 shows an image of the door to an evidence room, and Figure 4.3 shows digital evidence stored in the evidence room.
Cabinets
When planning the development of a computer forensics lab, provision should be made for at least two large closets (cabinets). One cabinet is needed to store reference materials. These reference materials should include textbooks, professional journals, binders with articles, and training manuals. Reference materials should also include laboratory operating procedures, legal reference materials, and standard operating procedures for investigations.
Hardware
There are a number of hardware devices that must be budgeted for when developing a computer forensics laboratory. This section highlights the most important items that should be purchased.
Cloning Devices
Every computer forensics laboratory should have a forensic disk duplicator (cloning device) for forensically cloning hard disk drives at the crime scene or in the laboratory. Many different types of hard disk duplicators exist. They generally provide a feature to sanitize a harvest drive, which is an important process in preparing for an investigation. However, when purchasing a disk cloner, the purveyor should ensure that the device is a “forensic” device. Higher-end hard disk cloners have the ability to create multiple copies simultaneously. The investment is worthwhile if the laboratory handles large quantities of suspect hard drives. Disk cloners typically support both SATA and IDE hard disk drive connections.
Write-Blockers
As noted in Chapter 3, “Handling Computer Hardware,” a write-blocker is a hardware device that allows an individual to read data from a device, such as a hard drive, without writing to that device. Generally a write-blocking kit will include a number of different write-blockers; power adapters; and cables, which will connect to eSATA, SATA (see Figure 4.5), IDE, Serial Attached SCSI, USB (see Figure 4.7), and FireWire (see Figure 4.6) devices. A lab should also maintain a write-blocking card reader (see Figure 4.8) for Secure Digital cards, xD cards, Memory Sticks, and so on, as well as a ZIF hard drive adapter and cables. The latter is used for imaging or cloning 1.8-inch ZIF hard disk drives manufactured by Toshiba, Samsung, and Hitachi. These hard disk drives can be found in Dell Latitude D420 and D430 laptops. When the ZIF adapter (see Figure 4.4) and ZIF cable are connected between the suspect’s 1.8-inch ZIF hard disk drive and the IDE connection, cloning the drive can often fail, so be prepared to image the drive through the USB connection on the laptop (with a write-blocker of course). Any failure to clone or image a drive should be included in the investigator’s notes.
SIM Card Readers
Cellular telephones that operate on the Global System for Mobile Communications (GSM) network contain a subscriber identity module (SIM) card, which will need to be forensically examined using a SIM card reader (see Figure 4.9). Chapter 9, “Mobile Forensics,” has more information on this topic.
Harvest Drives
These drives are the hard disk drives that act as receptacles for evidence acquired from the suspect’s hard disk drive. A computer forensics laboratory often uses thousands of SATA drives annually. Remember, in most cases, two copies of each of the suspect’s hard drive are made. The same type of SATA hard disk drives can be used to clone the hard disk drives of both Macintosh computers (Macs) and personal computers (PCs), regardless of whether they are desktops or laptops. As previously noted, harvest drives should be sanitized (wiped clean) when purchased new. Naturally, a variety of sizes of hard disk drives should be purchased, and an investigator should always have hard drives with the latest capacities available to ensure that they can cope with the latest technologies. An investigator should also always carry extra harvest drives to an investigation because the cloning process can fail and there may be no time to sanitize the harvest drive (or destination drive) again and restart an acquisition. USB-powered hard disk drives (see Figure 4.10) should also be part of the investigator’s collection of harvest drives because direct drive-to-drive cloning may not be possible.
Toolkits
Every computer forensics examiner needs a computer toolkit similar to the one depicted in Figure 4.11. The tools are primarily screwdrivers used for removing hard drives from desktops, laptops, and the enclosures surrounding external hard drives. Other tools should also be considered, including a snips to remove cable fasteners and pliers to hold or bend wires and other objects.
Flashlights
An investigator sometimes requires the use of a good flashlight for locations where lighting is poor and inadequate. Moreover, there are times when a suspect may try to hide digital devices and therefore a flashlight is required.
Digital Cameras
An investigator’s notes are key to effectively documenting an investigation. Photographing devices that are seized is critical to properly documenting an investigation. An investigator should take photographs of where the devices are located. Additionally, the configuration of devices or how they are connected should be carefully photographed and documented. This is important because the investigator may need to re-create how a number of devices were connected, especially with an unusual setup which is unfamiliar to the investigator.
When photographing a computer, the investigator must photograph the computer, its drive bays (CD/DVD, etc.), ports (serial, USB, etc.), and the serial number of the computer. The serial number format varies on different computers; sometimes there will be “S/N” before the number, and on Dell computers, the serial number is called the Service Tag. When the cover on a desktop is removed to display the hard disk drive, be sure to look for multiple hard disk drives. The investigator should photograph the drives before they are removed and then note the order in which each hard disk drive was located. Each drive should be differentiated by the serial number of the hard disk drive. Each hard disk drive should be photographed, and the investigator should verify that the serial number in each photograph is clearly visible. Finally, it is always important to bring replacement batteries for the digital camera.
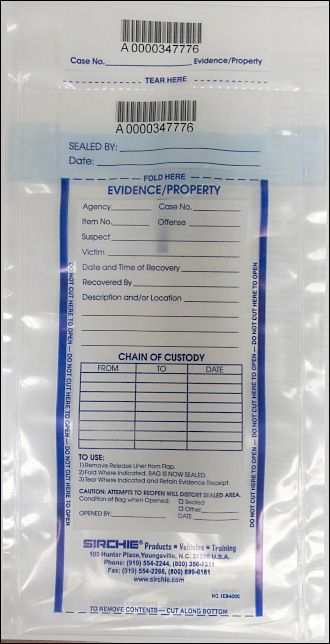
Evidence Bags
Evidence bags (see Figure 4.12) come in many shapes and sizes, but they all serve the same purpose: to prevent tampering of evidence and to record the chain of custody. This means that an evidence bag will have a tamper-resistant device, like an adhesive closure strip, so that the evidence cannot be accessed surreptitiously. Antistatic polyethylene evidence bags are designed to protect electronic devices from static electricity, and a computer forensics examiner should always have these when going on an investigation.
Evidence Labels
All drive bays should be sealed with an evidence label, and computers should be wrapped with tape to ensure that the evidence is not tampered with.
Software
A computer forensics laboratory should purchase and download different types of software. The laboratory should have computers running Windows and Mac operating systems. There should also be licenses for Microsoft Office and other applications that may be required to view files. A laboratory needs not only stream imaging tools, but must also have password-cracking software tools, an MD5 program for evidence verification, antivirus software, and virtual machine software. The list that follows illustrates the wide range of software requirements for a computer forensics laboratory. Chapter 9 covers the software requirements for mobile forensics.
Computer Forensic and Bit-stream Imaging Software
Many forensic imaging tools can be considered for use in a computer forensics laboratory. A combination of imaging tools is ideal because each tool has its own strengths in terms of recognizing partitions, the type and number of files recovered, filtering, and decryption. Using different tools on the same suspect drive frequently recovers varying amounts of evidence, and it is good practice to use multiple tools and log these differences in the case notes for the investigation.
Many of the tools discussed here have 30-day trials available, which make it easier to determine which tools are most suitable. The pricing of each of the tools listed varies, but discounts are often available for those in law enforcement, government agencies, and academia. The tools also have notable differences in features; and some companies, like Guidance Software, will build customized programs for their clients.
The following is a list of differences between computer forensic tools that should be noted when considering which tool to purchase:
![]() File systems supported
File systems supported
![]() Password cracking and decryption
Password cracking and decryption
![]() Hardware requirements to run the tool
Hardware requirements to run the tool
![]() Cost
Cost
![]() Customer support*
Customer support*
![]() File filtering
File filtering
![]() Evidence file backups
Evidence file backups
![]() GUI (user interface)
GUI (user interface)
![]() Reporting features
Reporting features
![]() Security of evidence files created.
Security of evidence files created.
(*Customer support can include software setup, hardware configuration, use of programmers for customized add-ons, and even the availability of an expert witness to testify in court.)
Some organizations purchase a tool like EnCase or FTK so that they can avail of an expert witness, from the vendor, should a case ultimately go to trial. Forensic tools that have been noted and accepted in court proceedings are arguably better to use in an investigation. To reiterate, there will often be differences in the level of evidence acquired by each tool, and therefore multiple tools should be used when gathering and analyzing the same devices and evidence.
![]() Sleuth Kit (TSK) and Autopsy Forensic Browser—Sleuth Kit is an open source computer forensics tool that is comprised of a group of command-line tools. The tool allows an investigator to examine file systems and a hard disk drive’s volume. This tool supports NTFS, FAT, UFS 1, UFS 2, Ext2, Ext3, Ext2FS, Ext3FS, and ISO 9660 file systems. Raw
Sleuth Kit (TSK) and Autopsy Forensic Browser—Sleuth Kit is an open source computer forensics tool that is comprised of a group of command-line tools. The tool allows an investigator to examine file systems and a hard disk drive’s volume. This tool supports NTFS, FAT, UFS 1, UFS 2, Ext2, Ext3, Ext2FS, Ext3FS, and ISO 9660 file systems. Raw dd images can also be analyzed using the tool. Autopsy is a graphical user interface (GUI) that is used in conjunction with Sleuth Kit. These tools can be used on either Windows or UNIX systems. Further information about this tool is available at www.sleuthkit.org.
![]() ILook—The ILook Investigator suite of tools was developed by Eliot Spencer in conjunction with the IRS Criminal Investigation Electronic Crimes Program. Further information about this tool can be found at www.ilook-forensics.org.
ILook—The ILook Investigator suite of tools was developed by Eliot Spencer in conjunction with the IRS Criminal Investigation Electronic Crimes Program. Further information about this tool can be found at www.ilook-forensics.org.
![]() DriveSpy—This forensic tool provides detailed information about a hard disk drive, including DOS and non-DOS partitions, slack space, allocated and unallocated disk space, and many other features. The tool logs when files are added or deleted from a location. More important, the tool allows the investigator to create a disk-to-disk forensic duplicate. The downside to using this tool is that it uses a DOS command-line interface instead of a nice user-friendly interface.
DriveSpy—This forensic tool provides detailed information about a hard disk drive, including DOS and non-DOS partitions, slack space, allocated and unallocated disk space, and many other features. The tool logs when files are added or deleted from a location. More important, the tool allows the investigator to create a disk-to-disk forensic duplicate. The downside to using this tool is that it uses a DOS command-line interface instead of a nice user-friendly interface.
![]() X-Ways Forensics—This tool is a well-recognized forensic imaging tool. It supports numerous file systems (FAT12, FAT16, FAT32, exFAT, TFAT, NTFS, Ext2, Ext3, Ext4, Next3, CDFS/ISO9660/Joliet, and UDF). The tool has a particularly effective file-filtering feature, which is important for culling through hundreds of thousands of files.
X-Ways Forensics—This tool is a well-recognized forensic imaging tool. It supports numerous file systems (FAT12, FAT16, FAT32, exFAT, TFAT, NTFS, Ext2, Ext3, Ext4, Next3, CDFS/ISO9660/Joliet, and UDF). The tool has a particularly effective file-filtering feature, which is important for culling through hundreds of thousands of files.
![]() WinHex—Like X-Ways Forensics, this software is produced by X-Ways Software Technology AG. This is not a forensic tool because it has write capabilities. Sometimes files are recovered by forensic tool but cannot be viewed in their natural format because the file is damaged or has been marked for deletion. WinHex comes with a hex editor that allows the user to recover files. In other words, editing a file with a hex editor might make an unreadable file viewable.
WinHex—Like X-Ways Forensics, this software is produced by X-Ways Software Technology AG. This is not a forensic tool because it has write capabilities. Sometimes files are recovered by forensic tool but cannot be viewed in their natural format because the file is damaged or has been marked for deletion. WinHex comes with a hex editor that allows the user to recover files. In other words, editing a file with a hex editor might make an unreadable file viewable.
![]() FTK—Forensic Toolkit (FTK) is bit-stream imaging software produced by AccessData. The software has been well documented in many court trials, including the Scott Peterson murder trial.
FTK—Forensic Toolkit (FTK) is bit-stream imaging software produced by AccessData. The software has been well documented in many court trials, including the Scott Peterson murder trial.
A free version of the software, called FTK Imager, is also available. It can be downloaded to a USB flash drive or burned to a CD. This tool allows the user to create a forensic image of a storage device and view the contents of the file system using the built-in hex editor. Beyond that, it has very few capabilities.
The full version of FTK is not free, but it has many other features, including comprehensive reporting, file decryption, and file carving. File carving is the process of identifying a file by certain characteristics, like a file header or footer, rather than by the file extension or metadata. For example, a suspect could try to hide images from investigators by changing the file extension of a picture from .jpg to .dll. When conducting a search using Windows File Explorer, you will not be able to find the file, and even trying to open the file will be unsuccessful because the association between the file and the appropriate application has been broken. Nevertheless, in our example, the file is still a picture. The file header for the picture will not have changed. A JPEG file generally shows “JFIF” in the file header, which is the equivalent of “4A 46 49 46” in the hex editor (see Figure 4.14). Tools like FTK have the ability to identify what a file actually is and classify it as a picture. The file carving option also extracts files embedded within other files; for example, a picture sent with an email can be viewed within the email using FTK and also as a picture listed with other pictures listed under that category. FTK also facilitates drive indexing. This is the process of taking categories of files, like emails, and creating a list of words found in each file. These words can then be used for keyword searches or even used for password cracking. As you can imagine, this indexing function means that the investigator does not have to spend valuable time performing keyword searches by opening one file at a time.
This pay-per-license version also contains a tool called Password Recovery Toolkit (PRTK), which has the ability to recover passwords from applications. These passwords can then be used to access to files, folders, and drives that a user password-protected.
More recently, FTK provides a Windows-based tool for examining Macintosh computers.
AccessData provides training at various locations throughout the United States and internationally, as well as online. The company also provides the opportunity to become certified with the tool by successfully completing a proficiency test to become an AccessData Certified Examiner (ACE):
![]() EnCase—This forensic software was developed by Guidance Software and is comparable to FTK in terms of functionality, reputation, and expert witnesses. Customers can request that Guidance Software create special add-on programs. EnScript is a programming language developed by Guidance Software that then allows EnCase users to create their own customized functions and features in EnCase. There are a number of websites where EnCase users make EnScripts freely available to other users.
EnCase—This forensic software was developed by Guidance Software and is comparable to FTK in terms of functionality, reputation, and expert witnesses. Customers can request that Guidance Software create special add-on programs. EnScript is a programming language developed by Guidance Software that then allows EnCase users to create their own customized functions and features in EnCase. There are a number of websites where EnCase users make EnScripts freely available to other users.
Guidance Software also has created its own proprietary file type: E01, a forensic disk image file format. Interestingly, many competitors also offer this file format as an option in their software. The three primary forensic image file formats are E01 and dd (or RAW). Computer forensics examiners also sometimes use the SMART file format. SMART files are forensic disk image files (compressed or uncompressed) originally developed by ASRData’s Expert Witness. Advanced Forensics Format (AFF) is an open source format, which was developed by Simson Garfinkel, and is supported by Autopsy and Sleuthkit forensics software. There are many other forensic image file formats that can be used by computer forensics investigators. Guidance Software also markets a tool called EnCase Enterprise that companies can use for network-based investigations, including investigations on internal computers and incident handling involving network attacks external to the organization. EnCase Enterprise allows for remote imaging of host computers; servers; and, with Version 7, smartphones and tablets on a network. The software also facilitates the imaging of multiple drives simultaneously.
![]() Mac Marshal—Developed by ATC-NY, Mac Marshal is a Mac OS X forensic imaging software. Mac Marshal Forensic Edition is used by the investigator on a Mac workstation to retrieve evidence from Mac machines. The software is currently available to law enforcement in the United States for free. Outside the United States, law enforcement and private-sector agencies can purchase the software.
Mac Marshal—Developed by ATC-NY, Mac Marshal is a Mac OS X forensic imaging software. Mac Marshal Forensic Edition is used by the investigator on a Mac workstation to retrieve evidence from Mac machines. The software is currently available to law enforcement in the United States for free. Outside the United States, law enforcement and private-sector agencies can purchase the software.
![]() BlackLight—This tool, produced by BlackBag Technologies, is available to the general public. It is used to image Apple Macintosh computers, iPhones, and iPads. More specifically, the tool can image computers running Mac OS X and Mac 9 operating systems.
BlackLight—This tool, produced by BlackBag Technologies, is available to the general public. It is used to image Apple Macintosh computers, iPhones, and iPads. More specifically, the tool can image computers running Mac OS X and Mac 9 operating systems.
Chapter 9 documents the necessary hardware and software for forensically examining cellular telephones.
Virtual Machine Software
Sometimes investigators need to use virtual machine software in an investigation, especially if they think there could be malware on a suspect’s machine. A virtual machine is a computer running software that allows for an instance of an operating system, or multiple operating systems, without making any changes to the user’s computer. In other words, after the user terminates a virtual machine session, the computer’s configuration remains unchanged. If a criminal uses virtual machine software to perpetrate criminal activities, this makes the work of the computer forensics examiner difficult because little or no evidence relating to the suspect’s activities then can be found on the computer.
VMware is well-known virtual machine software that an investigator can use to reverse-engineer malware. This software is ideal for examining malware because the investigator’s computer’s settings will remain unaffected by the malware. Examining the malware code is helpful because the programming code for viruses can be compared to identify whether malware code found on victims’ computers was authored by the same hacker. Additionally, the virus code may include the IP address of the hacker’s computer, which was used for command and control (C&C), so reverse-engineering malware can be extremely helpful in solving a crime. Many malware programs can, however, detect the presence of a virtual machine and in such an instance would not execute.
Antivirus Software
When examining a suspect’s machine, an examiner should recognize that viruses could be present on the machine. Having antivirus software running on the investigator’s computer should help mitigate the threat of malware.
Password-Cracking Software
A computer forensics examiner commonly encounters computers that are password protected. The entire system may require a password to access the desktop, files, and folders. A separate password may be required for administrator access, which allows for certain access, like installing software. A computer may also have a separate firmware password. Firmware refers to programs that control electronic devices like hard disk drives, game consoles, or mobile telephones. Therefore, with the proliferation of numerous types of passwords, good password-cracking software is necessary.
As previously noted, AccessData’s fee-based version of FTK comes with a tool called Password Recovery Toolkit (PRTK). Many law enforcement agencies purchase rainbow tables that contain thousands of different hash values to try to crack passwords. Other notable password-cracking tools include John the Ripper and Cain and Abel. John the Ripper is a free tool that works with Windows, UNIX, and many other operating systems. Cain and Abel is also free and works with Windows to execute brute-force, dictionary, and cryptanalysis attacks. A brute force attack checks all possible keys to decrypt data. A dictionary attack uses a predetermined list of words to decrypt data or authenticate a user. Cryptanalysis attempts to target weaknesses in protocols and cryptographic algorithms to try to break a system or gain access to data. Passware and Elcomsoft are other companies that provide popular commercial password-cracking tools.
It is important to note, however, that sometimes password-cracking software is not needed because investigators have techniques to circumvent the password system or locate a file containing a system’s password.
Photo Forensics
The importance of photos to investigations is clear because they are so personal and they are so prevalent. To give you an example of their importance, an estimated 2.5 billion photos are uploaded to Facebook every month. Photos can be used in all types of investigations, but child abuse is certainly the most important in terms of relying on evidence to convict a suspect. Photos are also quite important to cases involving intellectual property and copyright issues.
Photo File Formats
JPEG is the most popular picture file format and is supported by most systems and photo-enabled devices. Many other picture file formats exist, however. Websites can contain JPEG, GIF, and PNG picture formats; cameras use JPEG and RAW formats. The Adobe Digital Negative (DNG) format also is used, and Microsoft has its proprietary BMP format. All these images are raster-based graphics that are rectangular pictures based on pixels.
Photo files are sometimes compressed. There are two types of compression: (i) lossy compression where the picture is made smaller with some image quality compromise and loss of data and (ii) lossless compression where unneeded data is eliminated from a file without loss of original data. JPEG photos used lossy compression.
Photo Metadata
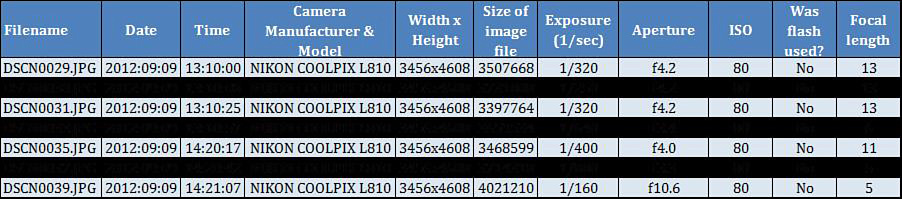
As previously noted, EXIF data (see Figure 4.19) is the metadata found in images that can contain the date and time a photo was taken, the make and model of the camera that took the picture, and an embedded thumbnail of the image. EXIF data can also contain the geographic location (longitude and latitude) of where the photograph was taken. Sometimes the serial number of the camera may also be stored in a photograph. The user may of course also add a personalized description to an image.
Photo Evidence
Most forensic imaging tools, like FTK, EnCase, and X-Ways, can efficiently find and display photo images in a separate category. More photo images can be found by carving pictures that are embedded in other files, like emails for example. Photo files have now become so large that they are often fragmented across a hard disk drive. When fragmentation occurs, reconstructing these images can be problematic. If a fragment is overwritten, then the reconstruction is virtually impossible, which is in contrast to many other file types.
Adroit Forensics
Adroit Forensics is a photo forensics tool developed and distributed by Digital Assembly. Adroit uses a process called SmartCarving, which enables the investigator to reconstruct a photograph when file fragments of the picture are located in noncontiguous sectors on a hard disk. The tool can also categorize photographs by date and by camera. Filters can be applied to search for skin tones and, more specifically, child faces.
Energy Requirements
Computer forensics investigators require more electricity to complete their work than the average employee. This is because an investigator may be cloning, or sanitizing, hard drives while also using a workstation to image a hard drive, while simultaneously using his workstation for build case files. Moreover, some forensic imaging software is optimally run using a duo core processor, and a lot of RAM and is attached to a RAID. Therefore, the workstation alone will utilize more energy than the average workstation. Additionally, large hard drives are often imaged overnight because of the time the process takes to complete, which makes this occupation different. Many organizations that create computer forensics laboratories fail to understand that the energy utilization is very different from other departments: A licensed electrician may be needed to upgrade the electric box and connections to facilitation greater power consumption. Labs also need an uninterruptible power supply (UPS), a power supply that contains a battery that will maintain power in the event of a power outage. Some UPS for computers are designed so that a backup will automatically be triggered if there is a power outage.
Laboratory Safety
An increase in energy requirements for a computer forensics laboratory introduces an increased risk of electrical fire. Dry chemical fire extinguishers should be strategically placed inside and outside the laboratory. An ABC fire extinguisher is probably the most appropriate for a laboratory. An ABC fire extinguisher uses a dry chemical extinguishing solution called monoammonium phosphate powder and ammonium sulfate and is suitable for electrical fires. It is called an ABC extinguisher because it can be used on Class A fires (standard combustibles), Class B fires (flammable liquids), and Class C fires (electrical equipment).
Budget
Developing a fully functional computer crime laboratory is expensive. For many local law enforcement agencies, it is cost prohibitive. This is why the growth of Regional Computer Forensics Laboratories (RCFLs) across the United States, managed by the FBI and staffed by local law enforcement, has become so important. In January 2011, an RCFL was opened in Orange County, California, at a cost of $7 million.
Setup costs for a computer forensics laboratory are high. Nevertheless, maintenance costs are also very high for a crime lab. Apart from staff salaries, the costs for maintaining software licenses must be calculated. Continuous education for laboratory staff must also be included in the budget. A computer forensics investigator will also go through an inordinate number of hard disk drives (harvest drives) during criminal investigations. Finally, new electronic devices must be continually purchased and tested with forensic software. For example, new versions of the iPhone, iPad, BlackBerry, and other devices need to be purchased and benchmark tested before suspect devices arrive at the laboratory. Remember, benchmark testing involves the scientific testing of tools on different devices to determine the effectiveness of that forensic tool.
An effective method for budgeting in a computer forensics laboratory is to keep copious notes about each criminal investigation. The primary points to document are as follows:
1. Crime category—e.g. identity theft, child pornography or murder.
2. Investigative hours—i.e. crime scene investigation, lab hours, and report writing.
3. Resources utilized—i.e. software to retrieve the evidence and hardware used to store the evidence, e.g. harvest drives and server space.
4. Suspect devices—detail the types of devices seized and examined. This is necessary to justify forensic software and hardware purchases and maintenance fees.
Laboratory Management
The American Society of Crime Laboratory Directors Laboratory Accreditation Board (ASCLD/LAB) provides extensive guidelines on best practices for managing a forensic laboratory. Many people view the ASCLD/LAB certification as the ultimate approval of a forensics laboratory. Most laboratories will never be ASCLD/LAB certified, but many labs still adhere to the principles outlined by ASCLD/LAB. Some forensics laboratory managers believe that attaining this certification will benefit their standing in the courtroom as experts who follow proper protocols. Thus, it is important to outline some of these guiding principles.
Laboratory Access
Restricting access to a computer forensics laboratory is extremely important and should be part of your physical security plan. Ideally, only those who handle evidence and manage the laboratory should have access to the room or building where your equipment and evidence are held. Access to a laboratory can be controlled using the following methods:
![]() Picture identification card
Picture identification card
![]() Biometric authentication
Biometric authentication
![]() Security guard
Security guard
![]() Closed-circuit television (CCTV)
Closed-circuit television (CCTV)
![]() Keypad with access code
Keypad with access code
To prevent unauthorized access, other precautions should be put in place. The laboratory manager can perform a background check, with the assistance of the human resources department, to make sure that employees have nothing in their background, such as a criminal record, that would preclude employment in the laboratory. Naturally, the laboratory manager should also undergo a background check before employees are assigned to the laboratory. Unfortunately, many employers do not continue to monitor the activities of their laboratory employees after they are hired.
Data Access
When making an assessment of access, it is critical to also review access to the laboratory’s data. Strict controls should govern who has access to certain workstations and who has access to particular cases under investigation. Forensic software, like AccessData’s FTK, has effective ways to password-protect certain cases and can allow an investigator to view only certain files in an investigation. Access to files varies because both an investigator and his or her supervisor need access to the case. Additionally, prosecutors may require access, as do defense attorneys upon request.
Access to data also includes access to the server rooms where the evidence is backed up. Restricting access to these servers by other employees is vital.
Data access in an organization can also occur through Wireless Fidelity (WiFi) connections. Ideally, there should be no wireless accessibility in a computer forensics laboratory, but it should used intermittently for software updates and patches. Removal of wireless connectivity should not be limited to Internet access but should also include removing access to other radio frequencies, including cellular frequencies. Cellular telephone jammers are devices that prevent cellular telephone users from connecting with other cellular telephones. These are necessary to ensure that seized cellular telephones will not be able to connect with their assigned network, which is good practice to preventing evidence from changing when an organization has authorization. The Federal Communications Commission (FCC) has recently warned many organizations about the illegal use of signal jammers, and some computer forensics laboratories have stopped using these devices.
Physical Security
In terms of physical security, there should be no openings in any of the walls; for example, the walls should reach the ceilings. If there is a drop-down ceiling, you should ensure that the walls of the laboratory go all the way up to the true ceiling so that access cannot occur from an adjacent room. A laboratory should not have any windows because they are a potential access point.
Laboratory Access Auditing
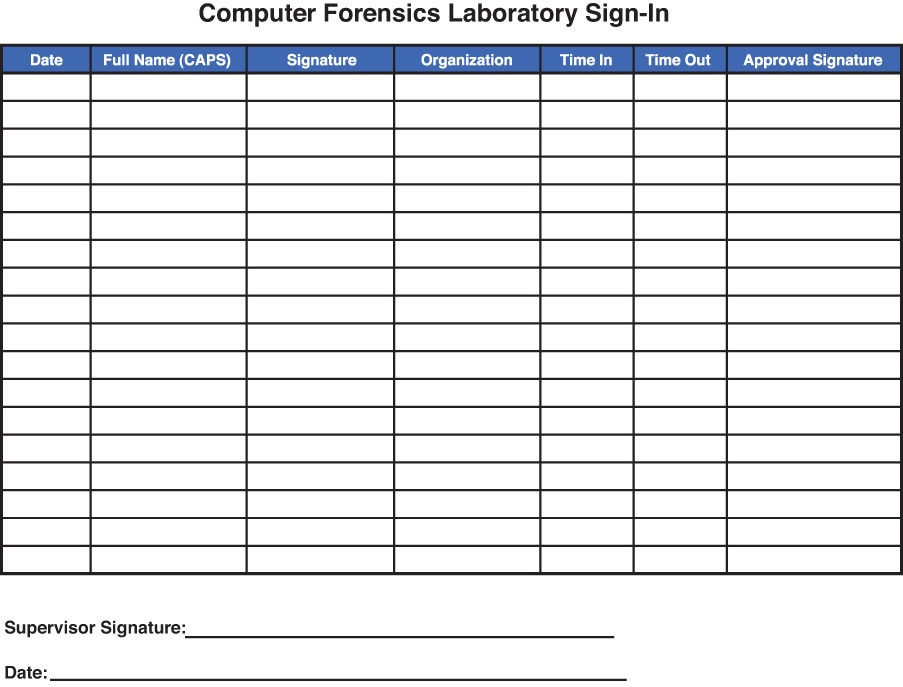
An audit of those who access the computer forensics laboratory is necessary. Preferably, a system is in place that can automatically record anyone who enters the laboratory, possibly by recording entry automatically when a person uses his or her identification card to enter the laboratory. This audit could hopefully be backed up with CCTV surveillance. At a minimum, there should be a clipboard by the entry point where staff and visitors are required to sign in and out of the laboratory with the date and time. Figure 4.20 shows a sample sign-in sheet.
Location of Laboratory
A computer forensics laboratory should be located in a secure area that is monitored continuously. Often a laboratory is located in the basement of the building. If this is the case, provision should be made to keep the area dry and cool. The laboratory should also allow for server scalability. In other words, evidence files should be backed up every evening on the laboratory’s servers. Over time, more servers will need to be added, and room will need to be allocated to these. When possible, a backup site should be maintained in case the computer forensics laboratory needs to be evacuated. This backup can be planned for in the organization’s Disaster Recovery Plan. On 9/11, valuable evidence acquired by law enforcement and stored at the World Trade Center as part of ongoing investigations was destroyed.
Extracting Evidence from a Device
Investigators use three primary methods to extract evidence from a device. The first method involves using a hardware device such as a Talon forensic hard disk drive duplicator. The second method involves using vendor software, such as FTK or EnCase. Finally, another method involves using a line-command interface. This third method involves running Linux commands both to acquire evidence and to search and filter evidence. The Talon and other professional tools, such as EnCase, are expensive, so in the next section, we explain the dd utility, which is a free and accepted tool in the courtroom.
Using the dd Utility
As previously noted, dd is a UNIX command utility used to copy data from a source location to a destination. From a computer forensics perspective, dd is important because it is an accepted file format for forensic imagining and because of its versatility. It is versatile because the command can be used to image very specific data, the user can verify also images with the MD5 algorithm, and images can be sourced from a specific computer on a network and that image sent to a network location.
The basic format of a dd command follows:
dd if=<source> of=<destination> bs=<byte size>
In the example above, if is short for input file and of is short for output file. The byte size is often set at 512 bytes but differs according to the file system you are working with and how quickly you want to copy the source data.
As noted earlier, a destination drive should be sanitized before acquiring data. dd can be used to forensically clean a drive using the following command:
dd if=/dev/zero of=/dev/
In the example above, dev is short for device. When executed, the drive will have zeros written to it. This command confirms that the drive now just contains zeros:
dd if=/dev/sda | hexdump -C | head
In the previous example, sda refers to the hard disk, which is the source of data we want to copy. Here is a list of other devices we might want to copy from:
sr0: CD-ROM
fd0: Floppy disk
sdb1: USB volume
The following command would then create a copy of the source file:
dd if=/dev/ of=/dev/ bs=512 conv=noerror
In the previous expression, conv=noerror is used to skip blocks with bad data.
A major benefit of using the dd utility is the ability to image a file across a network. In UNIX, we can use a utility called netcat to copy files over a network. We use the command nc, which is used for netcat. Following is the structure of dd over a network:
dd if (input file) | nc (NetCat) <Target-IP Address> <Port>
Here is an example of a netcat command:
dd if=/dev/hda bs=512 | nc 192.166.2.1 8888
In the previous example, 192.166.2.1 is the IP address of the target computer and 8888 is an arbitrary port number that we will send the file through.
It is also possible to conduct remote imaging of a hard drive over a network using SSH, which can prevent sniffing by a third party (https://www.linode.com/docs/migrate-to-linode/disk-images/copying-a-disk-image-over-ssh/).
Using Global Regular Expressions Print (GREP)
Many computer forensics tools today have become so user-friendly that some people have termed them “pushbutton forensics.” Although using these tools can be nice, relying on them too much could mean that an investigator fails to understand the science behind these tools. This is problematic when an investigator is called on to be an expert witness and must explain how these tools work. Additionally, when we have a better understanding of concepts such as Global Regular Expressions Print (GREP) and know Linux commands, we gain more control over how we conduct an investigation and become more competent.
Most of the computer forensics imaging tools available contains advanced search features, one of which is GREP. Global Regular Expressions Print (GREP) is a powerful set of UNIX expressions used for pattern matching. When using GREP, each line from a file is copied to the buffer; is compared against a search string (or expression); and then, if there is a match, outputs the result to the screen. GREP can be used not only to search through files, but also to search through the output of a program. GREP allows an investigator to search evidence files for key terms or numbers using specialized expressions.
Amazingly, very few computer forensics books cover GREP, even though this powerful search feature can be found in forensic tools like EnCase. Similarly, GREP provides tremendous search capabilities from the command line.
Here is a list of commands used in GREP:
![]()
-c does not print the keyword, but instead details the number of times the keyword displays.
![]()
-f searches for a particular file for a keyword.
![]()
-i is not case sensitive, meaning that it ignores the case of the search term.
![]()
-l outputs the filenames of the matches.
![]()
-n provides details about which lines in a file contain a match.
![]()
-v displays the lines that do not contain the keyword.
![]()
-x outputs only exact matches.
![]()
$ is used to search lines that end in a certain character.
Imagine a file containing the following data:
Secluded
Sector
Sect
Sects
$ect
The following simple GREP expression searches each line for any word containing Sect in the file test.txt:
# grep "Sect" test.txt
The following result then prints onscreen:
Sector
Sect
Sects
To specify the line when the match was made, you use the following:
# grep -n "Sect" test.txt
The following result then prints onscreen:
2:Sector
3:Sect
4:Sects
To search for an exact match, use the following command:
# grep -x "sect" test.txt
The following result prints onscreen:
Nothing is printed to the screen because Sect in the file is not an exact match with sect.
To find keywords that end with the letter r, you use the following expression:
# grep "r$" test.txt
The following result prints onscreen:
Sector
Extended Global Regular Expressions Print (EGREP) allows for the additional use of operators not found in basic GREP. The following shows EGREP notation:
Union/or |
Kleene star *
Kleene plus +
May or might not appear ?
The use of ? means that the previous character may or not be in the keyword. Take a look at this example:
# grep "Sects?" test.txt
The following result prints onscreen:
Sect
Sects
In EGREP, a | is known as a pipe. On the PC keyboard, hold down the Shift key and then press the key above the Enter key. A pipe functions as an “or” command. Here is an example of an EGREP expression using a pipe:
# egrep "Sect|Sects" test.txt
The following result prints onscreen:
Sect
Sects
The same result prints to the screen. Thus, you should remember that GREP and EGREP will often provide multiple expression connotations to produce the same output.
Finally, there is FGREP. Fast Global Regular Expressions Print (FGREP) is a UNIX search utility that does not use regular expressions but interprets characters literally and is therefore faster than GREP. Consider an FGREP expression:
# fgrep "$ect" test.txt
The following result prints onscreen:
$ect
We can now take a look at a more practical example of how an investigator might use GREP. In this example, a detective has been tipped off about a Word document on a suspect’s machine. The file is called bank.docx. The investigator doesn’t know the name of the file or its contents, but we do:
Dave,
Here's the stolen credit card details that I told you about.
Have fun!
J-Man
1. James Colgan
Card# 6011-0001-0001-0001-0001
CVV: 444
Expiration: 12/14
Telephone: (212) 555-0879
SS# 123-45-6789
2. Francis Bolger
Card# 53690001000100010001
CVV: 444
Expiration: 0113
Telephone: 6095551111
An informant told the detective that the suspect had accessed the Word document (.docx) within the past three days. The following GREP expression can find all Word documents accessed in the past three days:
# find . -name '*.docx' -atime -3
Here is a breakdown of that command:
![]()
# is automatically added in UNIX and indicates that this is the root user.
![]()
find is the search function in FGREP.
![]()
. refers to all files being searched.
![]()
-name refers to a search for a filename.
![]()
* is the Kleene star, which means that anything can display before the proceeding file extension.
![]()
.docx refers to the file extension we are searching for.
![]()
-atime refers to the days.
![]()
-3 refers to three—in this case, three days.
If the detective knew the approximate modify date, then –mtime (Modified Date) could have been used instead of –atime (Access Date).
The following are some additional helpful GREP expressions for investigators.
City, State, Zip Code
'[a-zA-Z]*, [A-Z][A-Z][0-9][0-9][0-9][0-9][0-9]'
Email Address
'[a-z0-9.]*@[a-z0-9.]*.[a-z][a-z][a-z]+'
The + indicates that there could be either two or three letters at the end of the email address.
IP Address
'[0-9]*.[0-9]*.[0-9]*.[0-9]*'
This regular expression is for IPv4 addresses. The *looks for any number of characters between 0 and 9 digits long. The . indicates that a period follows.
FTK and EnCase tools have their own versions of GREP, so understanding the GREP commands listed previously is extremely helpful.
Financial Fraud
The criminal investigation noted above involved financial fraud and, more specifically, credit card theft. Before continuing with GREP searches of the file listed previously, it is prudent to understand some basic information about credit cards to make your GREP searches more efficient. Moreover, credit card fraud is a huge problem in the Western world.
There are distinctive groups of bank and credit cards. Certain cards, like American Express, MasterCard, and Visa are issued through banks. These can be in the form of credit, debit, or prepaid (or gift) cards. Other cards, like Discover, are issued direct to the customer without a secondary bank. Capital One is in a separate category; it is a bank that issues its own credit cards.
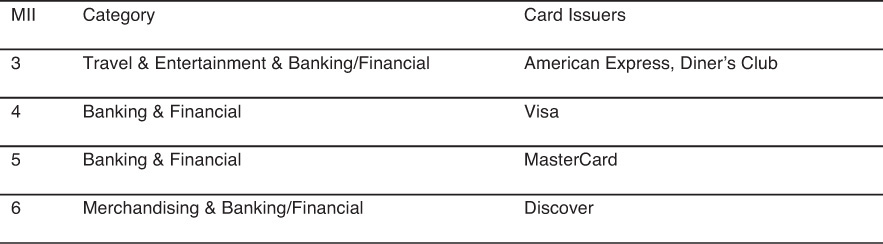
When searching for credit card numbers on a computer, it is helpful to know how the numbering system works. The Major Industry Identifier (MII) refers to the first digit of a credit card number. Figure 4.21 shows some issuer categories.
The Issuer Identification Number (IIN) refers to the first six digits of a credit card number. A credit card number can range from 12 digits to 19 digits. Figure 4.22 shows a list of some of the major credit card issuers and their IINs.
*Diners Club International operates on the Discover Network.
Based on the information in the matrices above and the data in the bank.docx file, it is clear that the credit card belonging to James Colgan is a Discover card, whereas Francis Bolger owns a MasterCard. This is helpful because if we wanted to search for MasterCards on a computer, we know that the first two digits range between 51 and 54 and that the credit card has a total of 16 digits.
A simple GREP search for a 16-digit credit card with five groups of four digits and dashes could be written as follows:
# grep "[[:digit:]]{4}-[[:digit:]]{4}-[[:digit:]]{4}-[[:digit:]{4}-
[[:digit:]]{4}" bank.docx
Result(s): 6011-0001-0001-0001-0001
However, we can see from the bank.docx file that Bolger’s credit card number is listed without dashes. Therefore, to find both matches, an EGREP command can be used:
# egrep "[[:digit:]]{4}-?[[:digit:]]{4}-?[[:digit:]]{4}-?[[:digit:]{4}-
?[[:digit:]]{4}" bank.docx
The ? in the previous command denotes that the dash may or may not appear for it to be a positive match and print to the screen.
Result(s): 53690001000100010001 and 6011-0001-0001-0001-0001
The following GREP search on bank.docx finds numbers with 20 digits and no dashes:
# grep "[[:digit:]]{20}" bank.docx
Result(s): 53690001000100010001
The following GREP command finds credit cards that begin with a 4 or 5 or 6. In other words, a Visa card, MasterCard, or Discover card could be a match, but an American Express would not be a match because it begins with a 3.
# egrep [[:digit:]][456]{3}-?[[:digit:]]{4}-?[[:digit:]]{4}-?[[:digit:]{4}-
?[[:digit:]]{4}" bank.docx
Result(s): 53690001000100010001 and 6011-0001-0001-0001-0001
With the previous expression run on the bank.docx file, both credit cards would be a match and would be output to the screen. [456] in GREP is the equivalent of the series {4,5,6}.
The bank.docx file also contains telephone numbers that might be of interest to us. The following GREP search looks for a 10-digit telephone number with no spaces:
# grep "^[0-9][0-9][0-9][0-9][0-9][0-9][0-9][0-9][0-9][0-9]$"
Result: 6095551111
It is important to note that, as with Word, Microsoft Office documents are actually a file bundle; therefore, another program needs to be run before a GREP search can be performed. Likewise, a direct GREP search cannot be performed on an entire hard drive, although FTK and EnCase make the GREP search process easier.
One cannot underestimate the importance of knowing Linux as a computer forensics investigator. The importance of knowing Linux becomes even more apparent when we cover Android forensics later in this book. There are numerous wonderful resources available online, including the following for Bash Shell Scripting (http://www.tldp.org/LDP/abs/html/).
Check Fraud
Another important type of investigation is check fraud. An investigator might want to run a GREP search to find ABA numbers. An American Bankers Association (ABA) number is found on checks and indicates how this financial instrument is to be routed through the banking system. The first two digits of the ABA relate to a corresponding Federal Reserve Bank. Figure 4.23 lists these banks.
An investigator can quickly ascertain the exact bank and branch for a check by checking online websites like Bank Routing Numbers (www.routingnumbers.com).
GREP and EGREP searches can be used for any alphanumeric search, including searches for IP addresses, Social Security numbers, email addresses, picture files, and many other important searches.
Skimmers
A skimmer is an electronic device used to capture the data from the magnetic stripe on a debit, credit, or prepaid card. These devices will often be examined in a computer forensics laboratory. Skimmers have reached epidemic proportions and are used by identity thieves worldwide. They are generally battery operated, and although they are illegal in the United States, they can be easily purchased in Canada. They are also available on the Internet. For a comprehensive report on skimmer fraud, see www.accaglobal.com/content/dam/acca/global/PDF-technical/other-PDFs/skimming-surface.pdf.
Criminals use various types of skimmers. A parasite is a point-of-sale skimmer. In 2011, Michael’s Stores discovered that skimmers had been installed in many of their point-of-sale (POS) terminals and ended up replacing 7,200 terminals. Criminals also use different types of parasites. With one type, a terminal is compromised. With another type, a phony terminal is installed; this type merely captures the data from the customer’s credit or debit card but does not function as a payment system. Some POS skimmers are homemade. The last type of skimmer is a do-it-yourself (DIY) kit used to modify an existing POS. These DIY kits work with POS terminals produced by VeriFone, Ingenico, Xyrun, and TechTrex. POS skimmers can have a Bluetooth board installed, which enables the criminal to download consumer POS data using a Bluetooth-enabled computer or cellphone. This has the added benefit of enabling the criminal to inconspicuously capture the data wirelessly. Typically, the device has a fake, paper-thin keypad that sits under the legitimate keypad on the POS and is used to capture PINs.
An ATM skimmer is used to capture data from the magnetic stripe on credit cards or ATM cards. The ATM has a false front to capture this data (as shown in Figures 4.24 and 4.25); in other words, a false card reader is place over the real one. A tiny camera is then usually hidden close to the ATM to capture the PIN number. The camera is sometimes hidden in a false leaflet box attached to the ATM or is placed in other areas like a false smoke detector. Sometimes a false PIN pad can added instead of using a camera.
IBM created the magnetic stripe (or magstripe) in 1960. Data is stored in magnetized iron particles. Whereas skimmers are illegal in the United States, magstripe encoders are not. A magstripe encoder is a device used to transfer data onto a plastic card with a magnetic stripe (see Figure 4.26).
There are sophisticated technologists/programmers who have the ability to manufacture credit cards that look legitimate and work just like the original card. A computer programmer typically downloads consumer card information from the skimmer by connecting it to a computer. The data is acquired through a computer port or by connecting pins to the EEPROM. Many skimmers are password protected, and cooperation from a criminal suspect may be required to bypass this protection. Interestingly, sometimes these devices will be password-protected or contain encrypted skimmed data—not to evade law enforcement, but to prevent their own criminals from taking and using the credit card data. After a criminal technologist has his or her henchmen gather the skimmer devices and he or she downloads the data, the technologist can create fake credit cards using a special printer to make the blank white cards look like real credit cards. The magstripe encoder is then used to add the customer data to the cards. After the credit cards have been prepared, a number of “shoppers” are sent out to make purchases with the fraudulent cards. These purchased goods might end being sold on websites such as eBay.
The United States Secret Service and the FBI are very active with skimmer investigations in the United States. These investigations generally have the cooperation of the affected financial institutions and assistance from local law enforcement. Software is available for examining these skimmers—primarily Exeba-COMM Law Enforcement Version, which can forensically analyze and decode skimmers and their skimmed data. Laws have now been adopted to deal with the skimmer epidemic; the New York State Penal Code now contains a law pertaining to the unlawful possession of a skimmer device.
Summary
The development and maintenance of a computer forensics laboratory plays a critical role in both the discovery of evidence and the ability to process that evidence in a way that makes it admissible in court. The American Society of Crime Laboratory Directors/Lab Accreditation Board (ASCLD/LAB) is an independent, nonprofit organization that provides guidelines on lab management and also certifies labs. A computer forensics lab must contain equipment that will be used in the field, as well as equipment that will be used in the lab. The tremendous range of digital devices, especially mobile devices, means that the hardware and software used for evidence acquisition has become greater and the costs for these solutions has increased over the past few years. Creating a lab budget is important when creating and maintaining a computer forensics lab; there are energy requirements, there are safety and security concerns; and general management of the lab must be addressed.
A computer forensics lab is not just used for criminal investigations. In the private sector, these labs are used for eDiscovery and can find data associated with civil litigation. All large accounting firms typically have a computer forensics lab and provide eDiscovery services to their clients.
Photo forensics is important because these images can provide information about where the suspect was at a particular point in time. The importance of photos can be seen with how prolific they are on the Web, especially on social networking sites. Photos are particularly important when it comes to child pornography cases. Chapter 10, “Photograph Forensics,” discusses photo forensics in depth.
Numerous computer forensics tools are available today, but not all are expensive. dd is a UNIX command utility that can create a forensic image-even remotely on a network. Global Regular Expressions Print (GREP) is a set of UNIX expressions used to search for key terms or for patterns, like numbers that may be credit card or Social Security numbers.
Finally, skimmers are devices used to capture personal and financial data from the magnetic strip of credit, debit, prepaid, and gift cards. Law enforcement is often called upon to examine and retrieve evidence from these devices in a computer forensics laboratory.
Key Terms
ABC fire extinguisher: Extinguisher that uses a dry chemical extinguishing solution called monoammonium phosphate powder and ammonium sulfate and is suitable for electrical fires.
Advanced Forensics Format (AFF): An open source format developed by Simson Garfinkel and supported by Autopsy and Sleuthkit forensics software.
American Bankers Association (ABA) number: Number found on checks that denotes how this financial instrument is to be routed through the banking system.
antistatic polyethylene evidence bags: Designed to protect electronic devices from static electricity.
ASCLD: A nonprofit organization that provides a set of guidelines and standards for forensic labs.
ASCLD/LAB: Originally, a committee within ASCLD that was created in 1981.
ATM skimmer: Used to capture data from the magnetic stripe on credit cards or ATM cards.
brute-force attack: Checks all possible keys to decrypt data.
cellular telephone jammer: Device that prevents cellular telephone users from connecting with other cellular telephones.
cryptanalysis: Attempts to target weaknesses in protocols and cryptographic algorithms to try to break a system or gain access to data.
dictionary attack: Uses a predetermined list of words to decrypt data or authenticate a user.
discovery: The period leading up to a trial during which each party involved in civil litigation can request evidence from the other party.
E01: A forensic disk image file format developed by Guidance Software.
eDiscovery: The detection of electronic data for the purposes of litigation.
electronically stored information (ESI): Can include email, Word documents, spreadsheets, databases, and any other type of digitally stored information.
EnScript: A programming language developed by Guidance Software that allows EnCase users to create their own customized functions and features in EnCase.
evidence locker: A metal cabinet with individual compartments that can be locked individually.
Extended Global Regular Expressions Print (EGREP): Allows for the additional use of operators not found in basic GREP.
Fast Global Regular Expressions Print (FGREP): A UNIX search utility that does not use regular expressions, but interprets characters literally and is therefore faster than GREP.
file carving: The process of identifying a file by certain characteristics, like a file header or footer, rather than by the file extension or metadata.
Firmware: Programs that control electronic devices like hard disk drives, game consoles, or mobile telephones.
Global Regular Expressions Print (GREP): A powerful UNIX set of expressions used for pattern matching.
Issuer Identification Number (IIN): Refers to the first six digits of a credit card number.
lossless compression: Eliminates unneeded data from a file without loss of the original data.
lossy compression: Makes the picture smaller, with some image quality compromise and loss of data.
magstripe encoder: A device used to transfer data onto a plastic card with a magnetic stripe.
Major Industry Identifier (MII): Refers to the first digit of a credit card number.
parasite: A point-of-sale skimmer.
plaintiff: The party that makes a claim against another party and initiates a lawsuit.
raster-based graphics: Rectangular pictures that are based on pixels.
Scientific Working Group on Digital Evidence (SWGDE): A committee dedicated to sharing research and setting standards for investigators working with digital and multimedia evidence.
SMART files: Forensic disk image files (compressed or uncompressed) originally developed by ASRData’s Expert Witness.
uninterruptible power supply (UPS): A power supply containing a battery that will maintain power in the event of a power outage.
virtual machine: A computer running software that allows for an instance of an operating system, or multiple operating systems, without making any changes to the user’s computer.
workbench: Used to prepare hardware devices for investigative analysis.
Assessment
Classroom Discussions
1. Explain the process by which you would plan, create, and maintain a successful computer forensics lab.
2. How can GREP be used in computer forensics investigations?
3. Detail the type of equipment that a computer forensics examiner in law enforcement would need to bring to a crime scene.
4. Why have skimmers become such a huge problem worldwide?
Multiple-Choice Questions
1. Which of the following fire extinguishers are suitable for electrical fires?
A. AFF
B. FAC
C. DBA
D. ABC
2. Which of the following indicates the routing information for a bank branch?
A. ABC
B. AFF
C. ABA
D. ESI
3. Which UNIX search utility does not use regular expressions, but interprets characters literally and is therefore faster than GREP?
A. FGREP
B. GREP
C. EGREP
D. XGREP
4. Which of the following best describes using a predetermined list of words to decrypt data or authenticate a user?
A. Dictionary attack
C. EGREP
D. Cryptanalysis
5. Which of the following formats is the forensic disk image file format developed by Guidance Software?
A. AFF
B. dd
C. AD1
D. E01
6. Which of the following formats is the forensic disk image file format developed by ASRData’s Expert Witness?
A. AFF
B. E01
C. SMART
D. RAW
7. Which of the following best describes what electronically stored information (ESI) can include?
A. Email
B. Spreadsheets
C. Databases
D. All of the above
8. Which of the following organizations is an independent body that provides forensic lab guidelines and certification?
A. ASCLD
B. ASCLD/LAB
C. ESI
D. SWGDE
9. Which of the following refers to the first six digits of a credit card number?
A. Issuer Identification Number
B. Major Industry Identifier
C. Electronically stored information
D. Sequential identification number
10. Which of the following is not a forensic file image format?
A. dd
B. E01
C. SMART
D. UPS
Fill in the Blanks
1. The open source file format, developed by Simson Garfinkel and supported by Autopsy and Sleuthkit forensics software, is called ________ Forensics Format.
2. An ATM ________ is used to capture data from the magnetic strip on credit cards or ATM cards.
3. A cellphone ________ is a device that prevents cellular telephone users from connecting with other cellular telephones by blocking all radio signals.
4. The programming language developed by Guidance Software that allows EnCase users to create their own customized function and features in EnCase is called ________.
5. File ________ is the process of identifying a file by certain characteristics, such as a file header or footer, rather than by the file extension or metadata.
6. When unneeded data is eliminated from a photo, this is referred to as ________ compression.
7. A(n) ________ machine is a computer running software that allows for an instance of an operating system, or multiple operating systems, without making any changes to the user’s computer.
8. ________ power supply is a power supply containing a battery that will maintain power in the event of a power outage.
9. A(n) ________ is a point-of-sale skimmer.
10. An evidence ________ is a metal cabinet with individual compartments that can be locked individually.
Projects
Design the Ultimate Lab
You have been tasked with designing a computer forensics laboratory for a local law enforcement agency. Imagine that you have a $1 million budget for your new laboratory. Create a graphical layout of the laboratory and, based on what you have learned in this chapter, draw up a list of the items (software, hardware, and so on) that you would like to purchase for the laboratory.
Create a Plan for a Forensics Lab
Using both NIST publications and ASCLD/LAB guidelines related to best practices in computer forensics, create a plan for a new computer forensics laboratory. Be sure to include important concepts such as physical security, auditing, benchmarking testing tools, management, and ongoing training.