This chapter and the following one present the protocols in the transport protocol group, from the radio up to and including L2CAP. In the Bluetooth specification, these protocols are detailed in over 600 pages. It is not within the scope of this book to recreate the algorithmic and implementation details of the specification. Instead, the key components of the protocols are highlighted. Readers who may want to learn about the protocols in more detail should supplement this reading with the study of the corresponding parts of the specification.
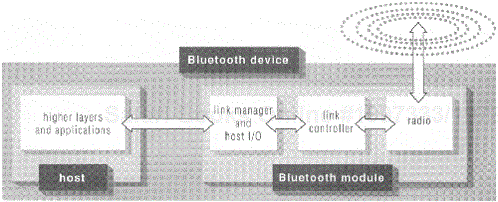
This chapter focuses on the lower-level functions (including the over-the-air protocols and information processing) in a Bluetooth system, which typically are performed within the Bluetooth hardware/firmware module as shown in Figure 6.1. The host I/O portion is covered in the next chapter in the presentation of the host controller interface.
As shown in Figure 6.1, a Bluetooth device [1] represents the complete physical entity (such as a notebook computer, a digital phone, an information appliance, and so on) that contains applications that can communicate using the Bluetooth wireless technology incorporated in that device. Here we assume that a device is associated with one and only one transport protocol group implementation and air-interface. However, as mentioned in the previous chapter and further elaborated in the next one, the L2CAP layer supports the multiplexing of several higher-layer protocols, like RFCOMM, SDP, and so on, and hence middleware protocol stacks and applications, as well.
The design point of the Bluetooth transport protocols is dictated primarily by low manufacturing complexity, associated low cost and fast time to market. For this reason, a low-cost, easy-to-implement, frequency-hopping spread-spectrum radio solution was selected. In addition, the selection of a master/slave architecture for the baseband transmission was dictated by the ad hoc nature of the systems considered. In particular, Bluetooth piconets can form spontaneously among disparate devices with vastly different power and computing capabilities, unlike wireless LAN systems which are designed primarily to support a wireless extension of LAN connectivity services to relatively "power-unconscious" personal computers.
To support ad hoc connectivity with minimal (if any) state maintained by the Bluetooth devices, piconets are dynamically formed in isolation without the support of third-party (infrastructure) control signaling. For as long as needed, the master of a piconet serves as the control point for the communications on the piconet. For the duration of the existence of a piconet, the operation of a master resembles that of a base station of a picocellular system. Thus, the Bluetooth technology permits the spontaneous creation of a temporary picocellular system, where traffic is regulated by a spontaneously created base station, the master, that regulates the traffic to and from the other member of the picocell, the slaves. Recall from previous chapters that the Bluetooth technology permits the creation of multiple, ad hoc picocellular systems that remain operational even in cases of temporal and spatial overlapping. The use of master and slaves reduces the complexity of the design and thus the cost of deploying the Bluetooth technologies.
The rest of this chapter highlights the Bluetooth radio; the link controller and the baseband functions it controls, like piconet creation and the medium access protocol; and the link manager that configures and manages the links between devices. In the reference implementation of a Bluetooth module, the radio and the link controller typically are implemented in hardware while the link manager is in firmware. As such, the radio and the link controller (with its baseband functions) were the first parts of the specification to mature, providing a stable enough hardware specification for chip designers to use in designing their early Bluetooth chipsets. The link manager specification originally was focused primarily on security-related transactions. The SIG's further work on the link manager specification has enriched it over time to take full advantage of the capabilities available in the baseband specification.
The Bluetooth system operates in the 2.4 GHz industrial, scientific, and medical (ISM) band. The ISM bands are license-free bands set aside for use by industrial, scientific and medical wireless equipment. Regulatory authorities around the world have opened the ISM bands for use by low-power systems that can be operated without the need for a license but nevertheless under strict regulations. In the United States, these regulations are set by the Federal Communications Commission (FCC) and are detailed in the Code of Federal Regulations part 15 [FCC99]; section 15.247 of the FCC regulations deals with the operational rules of intentional radiators operating in the various ISM bands including the 2.4 GHz band.
The 2.4 GHz ISM band is a globally available radio band, albeit not frequency harmonized. Table 6.1 shows the ISM frequency availability in the majority of countries around the globe.
The radio part of the specification consists mostly of a series of design specifications for Bluetooth transceivers, like in-band and out-of-band spurious emissions, frequency accuracy, co-channel and adjacent-channel interference, out-of-band blocking, intermodulation characteristics, and so on. The selection of the radio design specifications is driven by the requirement to allow the development of high-quality, low-cost transceivers that comply with the various 2.4 GHz ISM band regulations around the world.
The numerous design parameters plus the radio testing conditions are not repeated here. Readers interested in the Bluetooth radio design can find an abundance of information in the corresponding part of the specification. Since no new data-exchange protocols nor data-processing algorithms were developed for the Bluetooth radio, the radio part of the specification was the first to be completed. The errata to this portion of the specification are minimal, and the few that surface pertain mostly to the accommodation of new regulations or refinement of the radio testing procedures.
The Bluetooth transceiver is a frequency-hopping spread-spectrum (FHSS) radio system operating over a number m of 1 MHz-wide channels. While for the majority of countries m = 79, as shown in Table 6.1, regulations in certain countries may further constrain the license-free frequency spectrum for the 2.4 GHz ISM band. Thus, the Bluetooth radio (and the baseband described in the next section) design can accommodate two alternatives that operate over 79 or 23 channels, each one of which is 1 MHz wide. For frequency-hopping systems operating in the 2.4 GHz ISM band, the FCC part 15.247 regulations restrict the maximum peak output power of the radiator to no more than 1 watt (30 dBm). Moreover, at least 75 out of the 79 frequency channels must be used pseudo-randomly with a total residence time in each of the frequencies not to exceed 0.4 seconds within a 30-second period. A Bluetooth radio utilizes the maximum number of channels available, 79 in the United States, and it hops at a high rate, 1,600 hops per second, pseudo-randomly across all these frequencies to achieve high noise resilience. The use of direct-sequence spread-spectrum (DSSS) systems, which are also permitted in the 2.4 GHz ISM band, may be prohibitively costly for the low-cost requirement of Bluetooth radios.
Figure 6.2 summarizes the key operations in the Bluetooth radio. The figure also shows a pair of logical interfaces for carrying data and control information between the radio and the rest of the Bluetooth system. Here data relates to all information that is transmitted or received over the air. The control information controls the behavior of the radio. On the transmit side, this includes the carrier frequency to which the transmitter needs to tune prior to transmission of a bit stream of information over the air and the power level that is to be used for this transmission. On the receive side, this includes the carrier frequency to which the receiver must tune for receiving a bit stream of information and (optionally) the strength of the signal being received. Power-supply and time-signaling lines are not shown in the figure. A standardized set of interfaces for the data and control information is not provided in the specification. Thus, chip designers and manufacturers can choose to integrate the radio component with the rest of the components of a Bluetooth module in the way they believe is best for a low-cost, power-efficient system. Table 6.2 summarizes some of the key operational parameters of the Bluetooth radio.
Table 6.2. Key operational parameters of the Bluetooth radio specification.
|
Modulation |
Gaussian frequency-shift keying (GFSK) |
BT product[3] 0.5; modulation index: 0.28 – 0.35 |
|
Symbol rate |
1 Msymbol per second |
using the binary GFSK, this translates into 1 Mbps raw link speed;bit transmission time:1 μsec |
|
Frequency-hopping rate |
1,600 hops per second, typical |
residence time: 625 μsec per hop |
|
|
3,200 hops per second for inquiries and pages |
residence time: 312.5 μsec per hop |
|
Transmit power |
Class 3: 0 dBm (1 mW) |
a typical Bluetooth radio; optional power control to below –30 dBm |
|
|
Class 2: 4 dBm (2.5 mW) |
optional power control as above |
|
|
Class 1: 20 dBm (100 mW) |
required power control to at least 4 dBm; optional power control as above |
|
Receiver sensitivity |
a Bluetooth receiver must attain a raw bit error rate (BER)of 0.1% with an input signal level of –70 dBm or lower |
the –70 dBm sensitivity level shall be attained for any input signal generated by any compliant Bluetooth transmitter |
[3] The term "BT product" is not short for "Bluetooth product." It is a parameter describing the quality of transmitted waveforms expressed as the product of the bandwidth of the modulation filter and the bit time. | ||
The transmit power and receiver sensitivity values are examples of design decisions that were made to reduce cost and power requirements for the Bluetooth radio. An IEEE 802.11 wireless local area network (WLAN) may use up to 30 dBm (1000 mW) of transmit power in the United States (lower power-levels in other parts of the world) and not less than 0 dBm (1 mW). Hence, an 802.11 wireless solution may not be suitable for many power-constrained personal, portable devices. The sensitivity level is also much lower than that of an 802.11 radio receiver[2]. This means that a simpler Bluetooth radio can be built at a reduced cost as compared to an 802.11 radio.
As discussed in the previous section, the radio deals with the acts of sending and receiving data over the air. Outside the scope of the radio's responsibilities are considerations such as what data to transmit and when, what data to wait for and when, and which carrier frequency and transmit power to use. These are the responsibilities of the Bluetooth link controller, described later in this chapter, that executes the baseband communication protocol and related processes.
Figure 6.3 summarizes the key functions of the Bluetooth baseband. These include piconet and device control functions like connection creation, frequency-hopping sequence selection and timing; modes of operation such as power control and secure operation; and medium access functions like polling, packet types, packet processing and link types. These items are detailed later in the chapter as we proceed through the operational phases of a Bluetooth device. The figure also shows a set of logical interfaces for carrying data and control information between the baseband and the rest of the Bluetooth system. For the same reasons mentioned in the radio section, the specification avoids specifying any standardized set of interfaces for the data and control information. Nevertheless, their presence, even on a "logical" plane, aids this presentation, since it allows us to concentrate on the baseband operations in isolation from the rest of the Bluetooth system.
Due to the vast and diverse areas covered by the baseband specification, the remainder of this section tries to combine the information flow in the specification with that of more traditional communication protocol standards and related articles. The discussion progresses stepwise, identifying the key components over which Bluetooth communications actually occur. We begin with the definition of a piconet over which Bluetooth devices can exchange information packets. We then describe fundamental helper elements that assist in the creation and maintenance of the piconet, such as the Bluetooth clock and frequency-hopping selection process. Using these helper elements, the presentation continues with the description of the procedures that Bluetooth devices follow to create and join a piconet. Finally, with a piconet in place, we focus on protocols and processes like medium access control, error control, security, power-saving operation and so on, that are exercised on the Bluetooth devices and on information packets sent and received over the piconet.
For devices to communicate with each other using Bluetooth wireless technology, they need to be part of a piconet. Simply stated, a piconet comprises a shared communications channel through which members of the piconet communicate. In the FHSS space in which Bluetooth radios operate, this communication channel consists of a well-defined sequence of frequency hops pseudo-randomly selected from the set of frequencies in Table 6.1 at a nominal rate of 1,600 hops per second. The members of the piconet are able to follow the successive hops of the frequency-hopping sequence in a synchronized manner. Piconets are formed as needed and endure for as long as participating devices need to communicate. The baseband operations define how a frequency-hopping sequence for a piconet is created, how devices learn how to follow it and hence join the piconet, and how to send and receive information packets communicated in a coordinated manner between devices in the piconet.
Bluetooth piconets are formed in a rather ad hoc manner. They are formed on demand among devices that want to communicate with each other without relying on the services of a dedicated support entity, such as a base station in a cellular network or a corporate or home WLAN. The baseband protocol establishes the rules according to which these ad hoc connections are established such that devices communicate in a coordinated and efficient manner.
The frequency-hopping sequences that define the communication channels in piconets are highly uncoordinated, or, to be more precise, they are created in a manner that makes them appear highly uncoordinated. Thus, owing to the frequency-hopping nature of transmissions in a piconet, multiple piconets may exist in time and space with minimal interference among themselves. Multiple piconets overlapping, at least partially, in time and space are referred to as scatternets. This opens the possibility of interpiconet communications when devices become members of multiple piconets.
Each piconet has one and only one master and one or more slaves. These roles are temporary ones and they are meaningful only while Bluetooth devices are members of a piconet. Certainly, Bluetooth devices may be built to operate only as masters or only as slaves, but this is a host application and usage scenario issue rather than a Bluetooth specification issue. The specification generally assumes that a Bluetooth device is capable of acting both as a master and as a slave, depending upon the role required to accomplish a given usage case. In the case of a scatternet, a device that participates in more than one piconet can be the master of at most one of these piconets, while it can be a slave in several of them. Through a detailed process, described later in this chapter, a master and a slave may exchange their roles. It is also possible for an "old" piconet based around an original master to be migrated to a new piconet with a new master. Piconet migration as well as communication across scatternets are not discussed in detail here, because they are not very mature processes in the version 1.0 specification, which does not define any usage scenarios that address communication across piconets. Nevertheless, the specification contains necessary considerations that could allow these processes to be accomplished.
The primary role of a master for a piconet is to define:
which frequency-hopping sequence the members of this piconet shall follow;
when frequency hops shall occur, thus defining the timing foundation for timed events in the piconet;
which particular frequency is the "current" frequency; and
which slave will be transmitted to and/or which slave will be permitted to transmit next (recall that transmission on the Bluetooth air-interface is through polling of the slaves).
The first three items are strongly associated with how a piconet is formed and maintained and how devices join it. The last item is associated with how transmissions occur in a piconet.
Figure 6.4 shows the operational states for a Bluetooth device. In the connected state, the device is a member of a piconet. On the other hand, when a device is not associated with any piconet or participates in no action that could result in its forming or joining a piconet, it is said to be in the standby state. The standby state is the default operational state for a Bluetooth device. In this state, a device typically idles with only its native clock operating in a low-power mode.
To move to the connected state, a device goes through the inquiry and page states, which are instantiated differently but in a complementary manner within a potential master and a potential slave. In the inquiry state, a device learns about the identity of other devices in its vicinity; these other devices must be in an inquiry scan state to listen for and subsequently respond to inquiries. In the page state, a device explicitly invites another device to join the piconet whose master is the inviting device; the other device must be in the page scan state to listen for and subsequently respond to pages. As Figure 6.4 shows, a device may bypass the inquiry state if the identity of a device to be paged is already known. The figure also implies that while a device is a member of a piconet, it may still perform inquiries and pages for additional devices to join this or some other piconet. In the latter case, a scatternet (multiple piconets overlapping in time and space as discussed in Chapter 2) eventually could be created.
To become a member of a piconet, a Bluetooth device needs to know how to recreate the frequency-hopping sequence that defines that piconet and which frequencies from this sequence will be visited and when. Also, to participate in communications over the piconet, the device needs to know how to formulate, read and write information packets on the piconet. All of these operations, as well as nearly every other operation in a Bluetooth device, are related to the following two fundamental elements:
the Bluetooth device address
the Bluetooth device (or native) clock
Any process in the Bluetooth baseband is intimately related to these two elements. Two baseband processes are notable and we refer to them as the fundamental processes, which are those that generate:
the frequency-hopping sequence, and
the access code.
These fundamental elements and fundamental processes are detailed below.
The Bluetooth device address (BD_ADDR)[3] is the most static entity of a Bluetooth device. The BD_ADDR is a single 48-bit address electronically "engraved" on each device. A device's BD_ADDR is globally unique among Bluetooth devices. To guarantee uniqueness, a numbering authority assigns BD_ADDRs. The BD_ADDR is an IEEE 48-bit address, similar to the medium access control (MAC) address of IEEE 802.xx LAN devices.
The 48-bit address field, shown in Figure 6.5 from the least significant bit (LSB) to the most significant bit (MSB), is partitioned into three parts: the lower address part (LAP), the upper address part (UAP), and the non-significant address part (NAP). The 24 bits of the UAP and the NAP constitute the organization unique identifier (OUI) part of the address that is assigned by the numbering authority to different organizations. The LAP is assigned internally by various organizations. The various parts of the BD_ADDR are involved in nearly every operation of the baseband from piconet identification, to packet header error checking, to authentication and encryption key generation. These items are discussed in more detail later in this chapter.
Each Bluetooth device has a free-running 28-bit (native) Bluetooth clock. The Bluetooth clock is never adjusted and is never turned off. The clock ticks 3,200 times per second or once every 312.5 μsec, representing a clock rate of 3.2 KHz. Notice that this is twice the nominal frequency-hopping rate of 1,600 hops per second. The clock has an accuracy of ± 20 ppm[4] In low-power modes like standby, hold, and park (introduced in Chapter 2 and detailed later in this chapter), lower power consumption can be achieved by using a low-power oscillator to drive the clock at a reduced accuracy of ±250 ppm. The Bluetooth clock is illustrated in Figure 6.6.
The Bluetooth clock wraps around just short of once per day. The Bluetooth clock plays a fundamental role in deciding when a device can or cannot transmit or listen for a transmission, and at which frequency and for what types of information packets it transmits or listens. A slave device uses the value of the Bluetooth clock of a master to accomplish piconet communications as discussed below. The significance of the time intervals shown in Figure 6.6 will become apparent as we proceed through the rest of this chapter.
For devices to communicate with each other, they must transmit and receive on the same frequency at the same time. The frequency-selection module (FSM) contains the procedure for selecting the next frequency to be used under various operating conditions. The algorithmic and implementation details of FSM are beyond the scope of this book. They are covered extensively in chapter 11 of the Baseband part of the specification.
In Figure 6.7, the notation (x∣y) means that there are two permissible alternatives, x or y, only one of which is entered into the module based upon the circumstances. The notation V[m:n], m ≤ n, denotes the use of bits m through n of the bit field V; m is the least significant bit (LSB) of the two.
Depending upon the country of use, the FSM is set by the manufacturer to operate in a 23- or 79-channel frequency hop mode as explained in the radio section of this chapter.
Given the country frequency-hop mode, the clock input determines which frequency from the current frequency-hopping sequence is to be used, and when. In other words, the clock input determines the phase of the frequency-hopping sequence. The actual frequency-hopping sequence is determined through the address input. In each of the three active operational states shown in Figure 6.4, a different combination of clock and address inputs is supplied to the FSM, as explained immediately below.
During normal piconet operation, the channel-hopping sequence is used. For the channel-hopping sequence, the address input to the FSM for all devices in the piconet consists of the 28 least significant bits, BD_ADDR[0:27], of the master's Bluetooth device address. The channel-hopping sequence has a very long period, but the (23 or 79) hop frequencies are distributed equally over short periods of time to satisfy the regulatory requirements for the frequency-hopping sequence described earlier in this chapter.
During normal piconet operation, a new frequency from the channel-hopping sequence is selected every 625 μsec. This interval is the period for bit c 1 of the Bluetooth clock shown in Figure 6.6; in this case, the LSB of the clock, c 0, is not used. The time, 625 μsec, between two successive ticks of bit c1 of the clock is referred to as a slot. For devices in the connected state, the slot boundaries coincide with the ticks of bit c1 of the master's clock. Furthermore, all the devices in the piconet utilize the current value of the master's clock to drive their FSMs.
During the residence time at a frequency, a device may transmit a single packetized piece of information, referred to as a baseband packet data unit (BB_PDU)[5] BB_PDUs are strictly constrained within the residence time at a frequency. However, the residence time at a frequency may occupy multiple slots, thus permitting multi-slot BB_PDU transmissions to occur as discussed below. Following a multi-slot transmission, the next frequency selected is the one that would have been used if single-slot transmissions had occurred instead. That is, the frequencies from the channel-hopping sequence are selected on a slot basis, although the frequency hops themselves occur on a BB_PDU basis.
One device "invites" another device to join its piconet through the use of a page. The device issuing the page is called a paging device, and the device listening (or scanning) for pages is called the paged device. A paging device selects a new frequency at which to transmit a page every 312.5 μsec, which is the period of bit c0 of a Bluetooth clock. During page scans, when a device listens for transmitted pages, a new listening frequency is selected every 1.28 seconds, which is the period of bit c12 of the clock. Note that a paging device changes frequencies at a much higher rate than a paged device. While the paged device uses its own clock to drive its FSM, the paging device uses its best estimate of the clock of the paged device to drive its own FSM. The paging device estimates the clock value of the paged device based upon the most recent communication between the devices. In the worst case, the paging device could use its own clock.
During the page operation, the page-hopping sequence is used. To generate this sequence, the paging and paged devices use the 28 least significant bits of the address of the paged device—that is, the LAP and part of the UAP of the address shown in Figure 6.5—as the address input to their respective FSMs. For each device, its page-hopping sequence is a well-defined, periodic sequence composed of 32 (resp.[6] 16) frequencies uniformly distributed over the 79 (resp. 23) frequency channels permissible in the 2.4 GHz band in various countries. The period of the page-hopping sequence is 32 (resp. 16) hops.
Through inquiries a device "searches" for other devices in its vicinity. Just as in page operation, an inquiring device selects a new frequency at which to transmit an inquiry every 312.5 μsec. Inquired devices, executing inquiry scans, select a new listening frequency every 1.28 seconds. Note that an inquiring device changes frequencies at a much higher rate than an inquired device. Both the inquiring and inquired devices use their own clock to drive their FSMs.
During the inquiry operation, the inquiry-hopping sequence is used. To generate this sequence, the inquiring and inquired devices use the 28 least significant bits of the "inquiry address," referred to as the general inquiry access code (GIAC) LAP, as the address input to their respective FSMs. The inquiry address is a known, reserved 24-bit field equivalent to the 24-bit LAP of a Bluetooth address. The remaining four bits of the inquiry address (UAP[0:3]) are equal to hexadecimal '0x0'. The GIAC LAP is '0x9E8B33' and no Bluetooth device is allowed to have an address whose LAP coincides with the GIAC LAP. The inquiry-hopping sequence is a well-defined periodic sequence composed of 32 (resp. 16) frequencies uniformly distributed over the 79 (resp. 23) frequency channels permissible in the 2.4 GHz band in various countries. The period of the inquiry-hopping sequence is 32 (resp. 16) hops.
The access code is a 68- or 72-bit field prepended to each BB_PDU prior to its transmission over the Bluetooth air-interface. The access code serves a multitude of purposes including identifying the piconet, synchronizing on the incoming bit stream, aiding in establishing the proper DC-offset, and others. The focus here is the role of the access codes in identifying the state classification (inquiry, page, or connected) of transmitted BB_PDUs. The algorithmic and implementation details of the access code generator are beyond scope of this book. They are covered extensively in chapter 13 of the Baseband part of the specification. Figure 6.8 depicts an overview of the functions related to the access code.
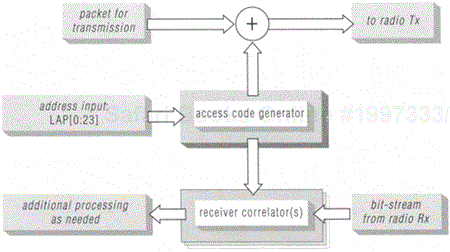
Figure 6.8. The access code functions; the "+" symbol above implies the prefixing of the access code in front of the transmitted packet.
To receive a transmission, a device uses a correlator, as shown in Figure 6.8, at its receiving end. The correlator can be tuned to particular access codes. If the correlator matches the access code of an incoming transmission sufficiently well, the receiver will continue receiving the incoming bit stream and pass it to higher layers for processing. Note that to conserve power, these higher layers may not be fully powered until the correlator informs them of an incoming message that has the proper access code prefixed to it.
As before, there are three classes of access codes that the device utilizes; each is described below.
During normal piconet operation, each transmission on a given frequency of the channel-hopping sequence is preceded by the channel access code (CAC) generated using the LAP of the address of the piconet master. Only transmissions that contain the proper channel access code are received by a device.
During page operation, each paging transmission on a given frequency of the page-hopping sequence and each response to it are preceded by the device access code(DAC) generated using the LAP of the paged device's address.
During inquiry operation, each inquiry transmission on a given frequency of the inquiry-hopping sequence and each response to it are preceded by an inquiry access code(IAC). There are 64 IACs, including the GIAC, associated with 64 reserved LAPs. Excluding the GIAC, the remaining 63 IACs are referred to as dedicated IACs (DIACs). The IAC LAPs belong to the set {'0x9E8B00', …, '0x9E8B3F'}. No device can have an address whose LAP matches any of these reserved LAPs. Note that no matter which IAC is used, the inquiry-hopping sequence over which this IAC is transmitted is generated using the GIAC. This is done to allow devices with multiple receiver correlators, as highlighted in Figure 6.8, to follow a single inquiry-hopping sequence but still be able to listen to multiple classes of inquiries simultaneously.
While the specification does not define how IACs are to be used, they are intended to be used primarily as a filtering mechanism for identifying well-defined subsets of the devices that may receive inquiries. While all devices that execute inquiry scans use the GIAC to generate the inquiry-hopping frequency, only those devices whose receiver correlators are tuned to a particular IAC will receive and respond to inquiries that contain that particular IAC.
Table 6.3 summarizes the various parameters related to the fundamental processes for each of the three operational states of a Bluetooth device.
Table 6.3. The FSM inputs and the access codes used during the various active states of a device.
|
Device state |
Frequency-hop module |
Access code |
|---|---|---|
|
Connected |
clock: master's; address: master's |
channel access code (CAC); it coincides with the master's device access code (DAC) |
|
Inquiry |
clock: own; address: GIAC |
general or dedicated inquiry access code (GIAC or DIAC) |
|
Page |
clock: (estimate of) paged device's; address: paged device's |
paged device's device access code (DAC) |
As discussed earlier, the Bluetooth clock and the BD_ADDR of the master of a piconet fully identify the frequency-hopping sequence and phase of the channel used in the piconet. Since communication between a slave and a master can occur only within a piconet, it follows that each slave in a piconet must know the master's clock and BD_ADDR. Alternatively, for a potential master to efficiently invite a potential slave, it needs to know the slave's clock and address. The exchange of address and clock information between devices occurs during inquiries, when the master collects operational information about the prospective slaves, and during pages, when the master communicates to a slave its own operational information. The operational information of a device, which includes its BD_ADDR and clock value, is sent in a frequency-hopping sequence (FHS) BB_PDU described in detail later in this chapter.
Assuming that the fundamental elements (address and clock) of the devices involved are known, the connected state is highlighted first in the next section. The inquiry and page states are presented afterward.
While in the connected state, devices can exchange data under the control of the master that defines which device transmits when. To maintain piconet synchronization, each slave adds an offset to its native clock that accounts for the difference of its own clock from that of the master. Thus, the clock of the master becomes the regulator of timed events in the piconet. In addition, the LAP of the master is used for the access code generation.
With a common clock reference among all devices in a piconet, the transmission time on the piconet is divided into master and slave transmission slots. A master starts its transmissions on even-numbered slots (c 1 = 0) exclusively. Likewise, a slave starts its transmissions on odd-numbered slots (c 1 = 1) exclusively. A particular slave transmits if and only if the last master transmission was destined exclusively to this slave. Thus, the medium access protocol for Bluetooth communications is a packet-based, time-division duplex (TDD)[7] polling scheme. Typically, master and slave transmit slots alternate every 625 μsec, the residence time at a frequency, although as mentioned earlier, multi-slot transmissions are possible. However, multi-slot transmissions are limited to an odd number of slots (one, three or five), which guarantees that master transmissions always start on even slots and slave transmissions on odd slots.
Figure 6.9 depicts the general format of a BB_PDU transmitted on a piconet. No frequency hops occur during a BB_PDU transmission and at most one BB_PDU is transmitted during the residence time at a frequency. Over-the-air transmissions start with the LSB and proceed to the MSB (little-endian transmission ordering). Every BB_PDU transmitted starts with the access code that, for the discussion here, serves as the piconet identifier, thus filtering out transmissions that might be received from other piconets (see Figure 6.8). The access code typically is 72 bits long, which includes a 4-bit trailer field. If the BB_PDU does not contain a header (and hence a payload), the trailer is not used and the BB_PDU consists of the 68-bit access code only. The 68-bit BB_PDUs are used exclusively for transmitting inquiries or pages as described in the corresponding sections later in this chapter.
The header of the BB_PDU contains link control data to aid medium access control. The header contains a mere 18 bits of information for low overhead, but it is encoded with a forward error-correcting(FEC) code with rate 1/3 for high transmission reliability. In particular, every bit of the header is transmitted three times in sequence. Table 6.4 summarizes the fields of BB_PDU header.
Table 6.4. The baseband BB_PDU header.
|
Field name |
Size |
Comments |
|---|---|---|
|
AM_ADDR |
3 bits |
active member address assigned to an active slave when devices exchange paging information, such as during the paging of a device |
|
TYPE |
4 bits |
defines 16 BB_PDU/payload types |
|
FLOW |
1 bit |
stop/go flow control switch set by a receiving device in its response to the sender |
|
ARQN |
1 bit |
used for acknowledging successfully transmitted BB_PDUs; BB_PDUs for which an acknowledgement is not received are retransmitted |
|
SEQN |
1 bit |
simple (odd/even) sequence number for filtering duplicate transmissions |
|
HEC |
8 bits |
header error check (HEC) generated by the generator polynomial G HEC(x) = x 8 + x 7 + x 5 + x 2 + x + 1 |
During the paging process, the master assigns a 3-bit active member address (AM_ADDR) to the new slave. AM_ADDR takes on the values 1 through 7 and it is unique for each active slave in a piconet. The reserved value of AM_ADDR = 'b000' is used to signify broadcast transmissions from the master to all the slaves in a piconet.[8] The AM_ADDR is included in the same FHS BB_PDU sent by the master to the slave that also contains the master's address and clock information.
The various BB_PDU types are distinguished by their roles: purely signaling or payload-carrying packets; their link designation: asynchronous connectionless (ACL) data or synchronous connection-oriented (SCO) data; their size: 1, 3 or 5 slots; and their FEC encoding: no FEC, 2/3 rate FEC encoding, and 1/3 rate FEC encoding. The 2/3 rate FEC is a (15,10) shortened Hamming code generated by the generator polynomial G FEC(x) = x 5 + x 4 + x 2 + 1.
The HEC is implemented through an 8-bit linear feedback shift register (LFSR) circuit whose initial value is UAP[0:7] of the master of the piconet. Hence, even in the case where transmissions from multiple masters with overlapping LAPs (thus generating the identical access code as shown in Figure 6.8) were accepted, the corresponding BB_PDU would be rejected because the BB_PDU header would fail its header error check. In other words, both the LAP and the UAP of the master of a piconet are needed to fully identify and accept a BB_PDU transmission on the piconet.
The link control packets include:
the ID packet, used in inquiries and pages, that consists of only the access code;
the NULL packet that is used primarily for slave acknowledgment and flow control information transmission when the slave does not have anything else to transmit (NULL packets themselves are not acknowledged);
the POLL packet that is sent from a master to a slave to poll it for a transmission when the master does not have any payload information to send to the slave (the POLL packet requires a response); and
the FHS packet used in inquiries and pages.
The ACL packets are designated as D(M∣H)(1∣3∣5), where "DM" stands for medium speed data that use a 2/3 FEC encoding for the payload; "DH" stands for high speed data where no FEC is used for the payload. The size qualifier 1, 3 or 5 refers to the number of slots occupied by the packet. For multi-slot packets, the frequency does not change until the packet finishes its transmission. The next frequency to be used is the one that would have been used if single-slot transmissions were used in the meantime instead. Note that the size of an ACL packet is odd because a master's transmission must always start at even-numbered slots while slave transmissions must start at odd-numbered slots. Using five-slot packets in one direction and one-slot packets in the opposing direction, the maximum achievable rate for ACL traffic is 723.2 Kbps in the first direction and 57.6 Kbps in the opposite direction.
Knowledge of the type of a BB_PDU and hence its size facilitates power conservation in a slave. In particular, as a slave in a piconet inspects an incoming transmission and finds that the transmission is not intended for that slave (that is, its AM_ADDR does not match the address in the BB_PDU header), the slave could go to "sleep" for a duration of time dictated by the packet type field.
The SCO packets are one slot long and are designated as HV(1∣2∣3). All three variants can support 64 Kbps in each direction over periodically reserved slots using different encoding for the payload data. In particular, HV stands for high-quality voice, and the encoding qualifier 1, 2 or 3 refers to the encoding used for the payload data:
1 is for 1/3 rate FEC; a device transmits a single-slot packet every 2 slots
2 is for 2/3 rate FEC; a device transmits a single-slot packet every 4 slots
3 is for no FEC; a device transmits a single-slot packet every 6 slots
In addition to the above packet types there is a DV packet that combines both ACL, with 2/3 FEC, and SCO, with no FEC, data in a single-slot packet. A device could transmit a DV packet every 2 slots.
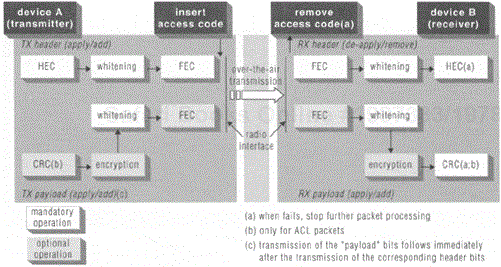
Figure 6.10 depicts the low-level baseband operations that occur during the transmission and reception of baseband packets. Note that different operations take place for the packet header versus the payload; the operations for the header and the payload occur serially rather than in parallel as the figure might imply. In the figure, whitening refers to the process of scrambling the transmitted data to randomize them and to reduce the DC bias in the transmitted data. The data are whitened through the use of the whitening word generated by the polynomial G WHITE (x) = x 7 + x 4+1. Security features in Bluetooth piconets, including device authentication and link encryption, are discussed in the following LMP section. The CRC operation pertains only to ACL packets, detailed immediately below.
The payload portion of the DM packets and the ACL portion of a DV packet is further structured with its own ACL packet header and payload along with a two-byte cyclic redundancy check(CRC) field. Table 6.5 summarizes the fields of the ACL packets, from the LSB to MSB.
Table 6.5. The ACL packet format.
|
Field name |
Size |
Comments | |
|---|---|---|---|
|
L_CH (logical channel) |
2 bits |
'b00': not defined | |
|
|
|
'b01': continuation segment of an L2CAP PDU | |
|
|
|
'b10': start of an L2CAP PDU | |
|
|
|
'b11': LMP PDU | |
|
FLOW |
1 bit |
for flow control on the ACL link | |
|
LENGTH |
(5∣9) bits |
length of ACL payload in octets (excludes header and CRC) for either single- or multi-slot packets in the case of a 9-bit length field, a 4-bit undefined padding is used to make the header an integer multiple of bytes (2 bytes total) | |
|
Payload |
0–339 bytes |
ACL packet payload spanning 1 to 5 slots | |
|
CRC |
2 bytes |
the cyclic redundancy check protects the payload and is generated by the CRC-CCITT generator polynomial G CRC(x) = x 16 + x 12 + x 5 +1 |
There is one extra one-slot ACL packet, AUX1, which does not contain a CRC. The use of this packet is not defined in the specification. Possibly, it could be used for testing and development purposes; however, it is outside the scope of the version 1.0 specification and this discussion.
As mentioned earlier, the Bluetooth baseband supports two types of links over a piconet. ACL links are used for carrying asynchronous data. The master schedules asynchronous transmissions in slots not already reserved for synchronous (SCO) transmissions. In other words, SCO traffic is of high priority and cannot be preempted for asynchronous transmissions. For each and every slave in its piconet, a master establishes exactly one ACL link that represents a physical pipe between the master-slave pair over which ACL data are exchanged. Point-to-point ACL BB_PDU exchanges are all acknowledged and retransmitted as appropriate. Broadcast (AM_ADDR = 'b000') ACL transmissions from a master to its slaves are not acknowledged but may be repeated several, N BC, times for increased reliability. Note that, since it is impossible for multiple slaves to acknowledge a transmission simultaneously, it is also impossible to acknowledge a broadcast transmission. In particular, there exists no simple and reliable method to dynamically designate a single slave to acknowledge on behalf of all slaves in the piconet that the broadcast transmission has been successfully received by all slaves.
SCO links carry telephony-grade voice audio through a priori periodically reserved pairs of slots. In a piconet, following a request from a slave or the master, a master may establish up to three SCO links in total between it and all of its slaves. Each SCO link represents a physical pipe between the master and one of its slaves over which SCO data are exchanged. To maintain the high quality of service expected for SCO traffic, the length of the baseband slot, 625 µsec, is selected to minimize the packetization delay for audio traffic and the effects of noise interference. For example, an HV1 BB_PDU carries the equivalent of 10 bytes of audio information, which at 8,000 samples per second and 8 bits per sample takes 1.25 msec (=2*625 µsec) to accumulate. This is the same as the period of transmissions of HV1 BB_PDUs from a device. Unlike ACL transmissions, SCO BB_PDUs are not acknowledged. Note that prior to establishing an SCO link, an ACL link must already exist to carry, at a minimum, the SCO connection control information.
Bluetooth links between devices can be authenticated, encrypted, operated in low-power mode, and in general, qualified based upon application or user requirements. The operation of the baseband in these cases is highlighted in the following link manager protocol section since it is link manager involvement that initiates these sorts of changes in link behavior.
For communication in a piconet to occur, a slave needs to know its master's clock and address. The following sections discuss the inquiry and page mechanisms by which this information is acquired. As Figure 6.4 shows, this two-step process can be trimmed to one step when connecting to known devices.
The purpose of device inquiries is to collect information about other Bluetooth devices in proximity. This primarily involves obtaining their fundamental elements: BD_ADDR and clock value. The inquiry state is composed of several substates executed by "potential" masters and slaves. These are the inquiry substate executed by a potential master and the inquiry scan and inquiry response substates executed by a potential slave. In the inquiry substate, a master[9] transmits inquiry packets, which are received by slaves in the inquiry scan substate. The latter devices then enter the inquiry response substate and schedule the transmission of their fundamental elements to the master.
While in the various inquiry substates, devices utilize the inquiry-hopping sequence to transmit and receive packets. The inquiry packet sent by an inquiring master is a BB_PDU that contains only an appropriate IAC, typically the GIAC, as described in the preceding section on access codes. This packet is referred to as the inquiry ID packet. The inquiry ID packet simply notifies slaves that a master is looking for slaves.
In responding to an inquiry, a slave transmits an FHS packet containing, among other information, the slave's BD_ADDR and clock value at the time of transmission of the FHS packet. Table 6.6 depicts the contents of the FHS packet. Since either a master or a slave can send an FHS packet,[10] the fields in the FHS packet are interpreted with respect to the device that sent the packet. The fields and the bits within them are provided in the transmission order from the LSB to the MSB.
Table 6.6. The FHS packet.
|
Field name |
Size |
Comments |
|---|---|---|
|
parity bits |
34 bits |
used for building the device access code (DAC) for paging the device sending this packet |
|
LAP |
24 bits |
the lower address part of the BD_ADDR of the device sending this packet |
|
Reserved |
2 bits |
set to 'b00' |
|
Paging interval parameters |
4 bits |
two 2-bit subfields defining the period of the successive page scans and the duration of the mandatory page scan period for the device sending this packet |
|
UAP |
8 bits |
the upper address part of the BD_ADDR of the device sending this packet |
|
NAP |
16 bits |
the non-significant address part of the BD_ADDR of the device sending this packet |
|
CoD |
24 bits |
class of device field containing information regarding the device sending this packet |
|
AM_ADDR |
3 bits |
for inquiry responses, it is set to 'b000'; for a master response following a page response by a (potential) slave, it is set to the active member address assigned to the new active slave |
|
CLOCK[2:27] |
26 bits |
the current time (updated with each retransmission of the packet) of the Bluetooth clock of the device sending this packet |
|
Page scan mode |
3 bits |
the default page scan mode of the device; one mandatory page scan mode and up to three optional ones are supported in version 1.0 |
The header of the BB_PDU carrying the FHS packet as payload has the AM_ADDR field set to 'b000' without meaning that this is a broadcast packet. The FHS packet is protected by a 2-byte CRC and encoded with an FEC with rate 2/3. The size of the FHS packet is 240 bits of payload and 126 bits of packet header and access code.
The operations of a master, the inquiring device, and a slave, the listening device, are highlighted in Figure 6.11. The numbers shown in the figure are typical numbers, which can be changed through intervention from applications as needed.
In summary, a master transmits its inquiry ID packets on different frequencies of the inquiry-hopping sequence, changing the transmission frequency rapidly in the hope of transmitting as soon as possible on one of the frequencies that slaves are listening to. This would ultimately happen, given enough time, as slaves performing inquiry scans change their listening frequency from the inquiry-hopping sequence at a much slower rate. Since a master does not know when a slave listens for inquiries, the master repeats its inquiry transmissions a number of times. When "contact" finally occurs, the slave responds with its FHS packet that includes vital paging information. SCO transmissions scheduled in any of the inquiring or listening devices take precedence over the inquiry procedures. A device will forego an inquiry action to transmit and receive scheduled SCO packets.
The inquiry-hopping rate is 3,200 hops per second, double the nominal frequency-hopping rate. The master will transmit and listen for responses over 16 different frequencies of the inquiry-hopping sequence (train A in Figure 6.11) over a period of 10 msec (8 transmit and 8 receive slots alternating with each other). If an insufficient number of responses is gathered, the master will repeat the same process over the same set of 16 frequencies at least 256 times, or 2.56 seconds. Following this interval and assuming operation in a 79 channel country, the master may also search through the remaining 16 frequencies of the inquiry-hopping sequence (train B in Figure 6.11) an additional 256 times. The whole inquiry process may then be repeated from the beginning.
![Fast frequency scanning for inquiries in a 79 channel country; f t[.]I denotes the master transmit frequencies from the inquiry-hopping sequence.](http://imgdetail.ebookreading.net/hardware/1/0130902942/0130902942__bluetooth-revealed__0130902942__graphics__06fig11.gif)
Figure 6.11. Fast frequency scanning for inquiries in a 79 channel country; f t[.]I denotes the master transmit frequencies from the inquiry-hopping sequence.
To avoid collisions from multiple slaves responding to the same inquiry ID packet, a rare event in its own right, a back-off mechanism is used and it works as follows. Upon receipt of an inquiry ID packet, the slave enters the inquiry response substate. It then randomly selects a number RN (≤ 1,023) and suspends its inquiry response operations for at least that many slots; the slave may move into the standby, connected or page states as necessary. When the slave resumes the inquiry response substate, it will respond with an FHS packet following the first inquiry ID packet it receives again. The detailed description of the inquiry procedures can be found in section 10.7 of the Baseband part of the specification.
Responding immediately after receiving an inquiry ID packet is not prudent, as the master may not have switched to the mode in which it listens for responses. To guarantee that this does not occur, the slave responds with its FHS packet 625 μsec after the receipt of the inquiry ID packet, as shown in Figure 6.12. The figure shows two slaves, noted as i and j, responding to inquiry ID packets. Slave I heard the inquiry ID packet in the first half of a master transmit slot. Slave j heard the inquiry ID packet in the second half of a transmit slot from the master. In either case, even though the slave is unaware exactly when the master will switch to the proper listening frequency, it is guaranteed that the corresponding FHS packet from a slave is sent at the right transmit frequency at the time that the master is listening at that same frequency.
![Inquiry transmission sequences; f r[.]I denotes the master receive frequencies from the inquiry-hopping sequence corresponding to f t[.]I.](http://imgdetail.ebookreading.net/hardware/1/0130902942/0130902942__bluetooth-revealed__0130902942__graphics__06fig12.gif)
Figure 6.12. Inquiry transmission sequences; f r[.]I denotes the master receive frequencies from the inquiry-hopping sequence corresponding to f t[.]I.
Note that the inquiry ID packet is 68 μsec long and it is transmitted twice over two different frequencies within a 625 μsec time interval. Therefore, closely observing the figure, one may deduce that the transmit frequency synthesizer has 244.5 μsec in which to switch to a new frequency. Actually, accounting for a ±10 μsec tolerance for clock drift, the synthesizer must settle to a new transmit frequency within 224.5 μsec. Admittedly this number is large compared to state-of-the-art synthesizer design. However, it allows the use of less complex and less precise circuitry that results in the desired low cost system design point. For more information on this subject, see [Haartsen00].
The purpose of a device page is to invite a specific paged device to join a piconet whose master is the paging device. The paging device uses the paged device's BD_ADDR and clock estimate to send its pages as discussed earlier. The page state is composed of several substates executed by potential masters and slaves. These are the page and master response substates executed by a master and the page scan and slave response substates executed by a slave.
In the page substate, a master transmits page BB_PDUs, which are received by the slave when it is in the page scan substate. The paging transmission contains only the slave's DAC. This BB_PDU is referred to as the slave ID packet. In its page response, the slave also sends the slave ID packet that simply notifies the master that the slave has received the page. Finally, the master enters the master response substate during which the master transmits to the slave its fundamental elements and the slave's AM_ADDR, which allows the slave to join and participate in communications in the master's piconet. These fundamental elements and AM_ADDR are transmitted within an FHS packet (see Table 6.6). The slave responds with one more slave ID packets, and then enters the connected state and readies itself to start piconet communications.
The operation of the master and the slave in the page and page scan substates, respectively, is quite similar to that of the inquiry and inquiry scan operations discussed earlier. In particular, the illustration of Figure 6.11 for inquiries can also be used for pages as well by replacing the terms related to inquiries with corresponding terms related to pages. The typical value for TpageScan is 1.28 seconds; subsequently, the typical value for Npage is 128. These typical values correspond to the so-called R1 paging mode. The paging mode, and hence the corresponding parameters TpageScan and Npage, are communicated to the master during the slave FHS transmission in an inquiry, or during link manager information exchange during regular communications.
For a 79-channel country, trains A and B contain 16 frequencies each from the page-hopping sequence, while for 23-channel countries there is only one train containing all 16 frequencies. In the former case, train A contains the 16 frequencies closest to the frequency on which the slave listens for pages as estimated by the master using its knowledge of (the estimate of) the slave's native clock. Train B contains the remaining frequencies from the page-hopping sequence. Yet, since train B is used 1.28 seconds after transmitting pages on frequencies from train A, the master knows that the frequency on which the slave listens will also move by one. Hence, trains A and B have one common frequency. For example, if train A contains frequencies f t[0]P through f t[15]P, then when train B is used, it will contain frequencies f t[17]P through f t[0]P, in that order. A device that performs page scans in the R1 paging mode can be located within no more than 1.28 seconds most of the time. When the estimate of the slave's native clock deviates more than –8*1.28 seconds or +7*1.28 seconds from the actual value of the slave's clock, the search time can be as much as twice the nominal value, or 2.56 seconds.
The sequence of transmissions during paging operations is summarized in Figure 6.13, where a master pages a slave denoted as i. Following the paging operation, the slave shall be able to participate in piconet communications. Hence, the slave not only needs to learn about the master's BD_ADDR and clock value but also must have an AM_ADDR assigned to it and must know exactly when a master transmit slot starts. The AM_ADDR is included in the FHS packet transmission to slave i. The time of transmission of this packet is used to identify the start of the master transmit slots in the piconet. The master transmits its FHS packet to slave i at the beginning of its transmit slot, regardless of whether the slave sends its previous slave ID packet in the first or second half of the slot during which the master listens for the slave response to its pages. In the example of Figure 6.13, since the master receives the slave response to the master's pages in the second half of the master's receive slot, the master transmits the FHS packet 312.5 μsec after it receives the slave ID packet. Thus, by the time that the slave receives and processes the FHS packet, the slave has all the information needed to participate in the piconet communications, starting with a master transmission 1.25 msec from the start of reception of the FHS packet.
![Page transmission sequence. f t[.]P and f r[.]Pdenote the corresponding master transmit and receive frequencies, respectively, from the page-hopping sequence and f t[.]C denotes a master transmission frequency from the channel-hopping sequence.](http://imgdetail.ebookreading.net/hardware/1/0130902942/0130902942__bluetooth-revealed__0130902942__graphics__06fig13.gif)
Figure 6.13. Page transmission sequence. f t[.]P and f r[.]Pdenote the corresponding master transmit and receive frequencies, respectively, from the page-hopping sequence and f t[.]C denotes a master transmission frequency from the channel-hopping sequence.
As with inquiries, SCO transmissions scheduled in any of the paging or paged devices take precedence over the paging procedures. A device will forego a page action to transmit and receive scheduled SCO packets. This case is not elaborated further here. The detailed description of the page procedures can be found in section 10.6 of the Baseband part of the specification.
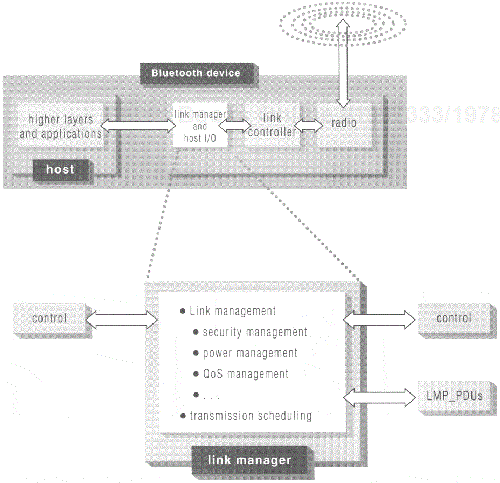
Link manager entities, or simply link managers, in communicating devices exchange messages to control the Bluetooth link between those devices. The communication protocol between link managers is called the link manager protocol(LMP) and the messages exchanged between communicating link managers are noted as LMP_PDUs. Figure 6.14 summarizes the functions of a link manager. LMP does not carry application data. Based upon control data it receives from higher layers, LMP either communicates with the link manager in another device using LMP_PDUs or it sends control signals to its own device's baseband and radio layers. It should be noted that, contrary to baseband processes that are executed in real time, link manager interactions are not. Albeit infrequently, communicating link managers may take up to 30 seconds to react to each other's requests.
As discussed earlier (see Table 6.5), LMP_PDUs are carried in the payload of ACL packets whose header has an L_CH field with the value 'b11'. LMP_PDUs are transmitted on single-slot DM1 packets or on DV packets. LMP_PDUs have very high priority and, if needed, they can preempt even an SCO transmission to transmit control information to another device. Table 6.7 summarizes the LMP_PDU packet format; note that LMP_PDU packet format.
Table 6.7. The LMP_PDU format.
|
Field name |
Size |
Comments | |
|---|---|---|---|
|
transactionID |
1 bit |
'b0': identifies link manager transaction initiated by the master | |
|
|
|
'b1': identifies link manager transaction initiated by a slave | |
|
OpCode |
7 bits |
identifies the LMP_PDU and the type of contents it carries | |
|
payload |
0–17 bytes |
the LMP_PDU fits in DM1 BB_PDU; if the LMP_PDU payload is less than 9 bytes then, when supported, DV BB_PDUs may also be used |
When a link manager in a device initiates an LMP_PDU transaction with the link manager in another device, the latter link manager will respond with the next LMP_PDU in the transaction sequence (for example, respond with the requested information). Alternatively, the receiving link manager responds with an LMP_accepted or LMP_not_accepted PDU that signifies whether the link manager request from the transaction initiator is or is not accepted, respectively. When an LMP_not_accepted PDU is sent, the reason for not accepting the transaction is provided.
Figure 6.15 shows two typical types of LMP_PDU transactions. In the first, either one of the communicating link managers initiates a transaction with a request. The receiving link manager either will accept the request and act accordingly (perhaps providing the requested information) or will reject the request with an LMP_not_accepted PDU. It might also send its own corresponding request LMP_PDU initiating a negotiation phase for the original request. In the second transaction type, the master sends a command to be executed by the slave in an LMP_PDU, without the opportunity for the slave to reject the command or negotiate its parameters. An example of the latter case is forcing a slave to go into a power-saving mode, like the hold mode, or requesting a link detachment, which is the only operation that a slave may also force on a master.
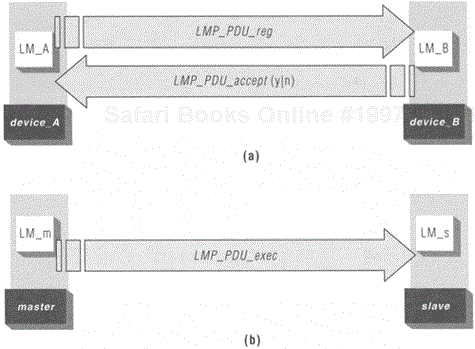
Figure 6.15. Typical LMP_PDU transactions: (a) a request/response transaction and negotiation; (b) master demands link adjustment.
There are many link manager transactions from a simple device name exchange to elaborate authentication and encryption transactions, but not all of them are mandatory. However, the receiving link manager must be able to respond to all link manager transaction requests, even if the response is an LMP_not_accepted PDU, with the reason for non-acceptance being "feature not supported." The following sections focus on a few of the more important link manager transactions. The interested reader can find a more detailed presentation in the LMP part of the specification.
Security has been part of the specification from the outset of its development. It was recognized early on that in ad hoc, wireless, and especially RF environments security is of paramount importance.
The baseband defines security algorithms and procedures needed to authenticate devices, and if needed to encrypt the data flowing on the link between them. Section 14 of the baseband part of the specification includes algorithms for the generation of authentication and encryption keys and the operations for verifying the authenticity of a device. Even though security is presented mostly in the baseband part of the specification, it is discussed here in the link manager section, since it ultimately relates to the configuration of a link between devices, the responsibility for which lies with the link managers.
Device authentication is a mandatory feature supported by all Bluetooth devices. Link encryption is optional.
Authentication of Bluetooth devices is based on a challenge-response transaction. In this transaction, a verifier challenges a claimant by sending to the latter a 16-byte random number in an LMP_au_rand PDU. The claimant operates on the random number and returns the result of the operation to the verifier in an LMP_sres PDU. If the result is the one expected by the verifier, the verifier considers the claimant an authenticated device. Optionally, the two devices may then exchange their roles as verifier and claimant and perform authentication in the opposite direction.
The above procedure occurs when the two devices have a common link key, which is used to operate on the random number. A device may maintain identical or separate link keys for every other device that it wants to authenticate. If a link key does not exist for a device, when an LMP_au_rand PDU is sent, the claimant will respond with an LMP_not_accepted PDU, giving the reason that the key is missing.
When a link key is missing, the devices need to be paired first. With the pairing process, an initialization key is generated and used to authenticate the devices and eventually to create a permanent link key for them. The initialization key is generated by entering a common personal identification number (PIN) in both of the pairing devices, which generates a temporary key. Note that neither keys nor the PINs that generate them are ever sent in clear form over the air. Using the temporary key generated by the PIN, the two devices may proceed with the authentication process as if they had a link key. The only difference is that pairing is initiated using an LMP_in_rand PDU instead of the LMP_au_rand PDU. Certain devices without a user interface may have a fixed, non-changeable PIN. In this case, the PIN entered in a device with a user interface must match this fixed PIN; otherwise authentication is not possible.
Authentication of Bluetooth devices depends upon a shared secret. Commonly used public key and certificate schemes are not appropriate for ad hoc networks of personal devices. These other schemes require the support of trusted authentication agencies and other third-party means of communication that cannot be assumed to be available in ad hoc networks. Authentication keys are 128 bits long and are constructed using the PIN (only for the initial authentication), a 128-bit random number, and a device's BD_ADDR.
Bluetooth devices may store link keys for future authentication without the need to enter a PIN each time. The two primary types of link keys are the unit keys and the combination keys. The former are derived from input parameters available in only one device, while the latter are derived by combining input parameters available in each of the two devices. The use of combination keys is preferred, as it provides for a stronger "bonding" between pairs of devices; a device must store a separate combination key for each other device it wants to authenticate using a stored link key. However, devices of limited storage capacity may store and use just a single link key for authentication of other devices.
To protect the privacy of the data flowing over a Bluetooth link, the link can be encrypted. Encryption in Bluetooth wireless technology is based on a 1-bit stream cipher, whose implementation is included in the specification. The size of the encryption key, which changes with each BB_PDU transmission, is negotiable to match application requirements.
The encryption key is derived from the link key used to authenticate the communicating devices. This implies that prior to using encryption two devices must have authenticated themselves at least once. The maximum key size is 128 bits, but regulatory authorities in various countries may limit the permissible maximum key size. Encryption applies only to the payload of BB_PDUs and it is symmetric, in that both directions of communication are encrypted. Encryption is a link property in that both SCO and ACL packets over this link are encrypted.
A request for encryption starts with the LMP_encryption_mode_req PDU with an encryption mode parameter that distinguishes encryption of a link between two devices (point-to-point encryption), or encryption of broadcast packets as well. In the latter case, a master key is created that is to be used for encryption by multiple devices in the piconet. If the request for encryption is accepted, the devices then negotiate the size of the encryption key exchanging LMP_encryption_key_size_req PDUs. If the negotiation succeeds, the devices can initiate encryption by sending an LMP_start_encryption PDU. Encryption starts by: (a) the master becoming ready to receive encrypted data; (b) a slave becoming ready to transmit and receive encrypted data; and (c) the master becoming ready to transmit encrypted data.
Devices in a connected state can regulate their association with the piconet(s) to which they are connected to preserve power or to attend to other business such as participation in a scatternet. There are three low-power modes: sniff, hold, and park; all are optional.
Apart from modifying the property of the link between devices, a device optionally may request its communicating partner to adjust its transmission power depending on the quality of the link, as measured by the received signal strength of incoming transmissions. Power control for this case is discussed in Chapter 2 and is not discussed further here.
Typically a slave must listen at the beginning of each even-numbered slot to see whether the master will transmit to the device. In the sniff mode, a slave may relax this requirement for its ACL link. The master will transmit to the slave at a reduced duty cycle by starting its transmissions every T sniff slave listening opportunities (master transmit slots). In particular every, say, T sniff[j] listening opportunities, slave j will listen for N sniffAttempt [j] slots for a transmission to it. If data is received, the slave will continue listening until the transmissions stop. The slave will continue listening for an additional N sniffTimeout [j] listening opportunities for additional transmissions to it. While a slave is in the sniff mode, any ongoing SCO transmissions will still occur as scheduled.
A master may force a slave into sniff mode with an LMP_sniff PDU. Alternatively, a master or a slave may request that the slave enter into sniff mode with an LMP_sniff_req PDU. Both of these LMP_PDUs carry the timing parameters defining the slave operation in sniff mode. These LMP_PDUs also carry an offset parameter D sniff that determines the time of the first sniff instance. Subsequent sniff instances are separated by the period T sniff. In the case of a request to enter the sniff mode, the master and the slave may negotiate the timing parameters for this mode.
While sniff mode communications are periodic, in hold mode ACL communications with a slave are suspended in single installments for a time interval referred to as the hold time. While a slave is in hold mode, any ongoing SCO transmissions will still occur as scheduled.
A master may force a slave into hold mode with an LMP_hold PDU. Alternatively, a master or a slave may request that the slave enter into hold mode with an LMP_hold_req PDU. Both of these LMP_PDUs carry the initial value of the hold time. In the case of a request to enter the hold mode, the master and the slave may negotiate the timing parameters for this mode.
In the sniff and hold modes, a slave is still considered a fully qualified active member of the piconet and as such it maintains its AM_ADDR that was assigned to it when it joined the piconet. Note that while in these two modes, SCO transmissions with the slave are not interrupted.
To further reduce power consumption during periods of no activity, a slave may enter the park mode during which it disassociates itself from the piconet, while still maintaining timing synchronization with the piconet. By doing so, it can rejoin the piconet relatively quickly without having to perform inquiry and paging procedures.
A slave that enters the park mode gives up its AM_ADDR. On the other hand, to manage its fast and orderly readmission to the piconet, the master assigns to the slave two temporary 8-bit addresses, the parked member address (PM_ADDR) and the access request address (AR_ADDR). PM_ADDR is used to distinguish up to 255 parked devices (actually, slaves); the address '0x00' is a reserved PM_ADDR. Parked devices could be recalled using their 48-bit BD_ADDR if needed, but the use of the much shorter PM_ADDR allows for increased efficiency in recalling multiple parked devices.[11] AR_ADDR is used in scheduling the order of readmission of parked devices in a way that minimizes the possibility of collisions.
To maintain synchronization with the piconet and to facilitate the readmission of parked devices in the piconet, the master defines a low-bandwidth beacon channel, which consists of the periodic transmission of broadcast packets. Prior to entering park mode, slaves are notified of the timing parameters of the beacon transmissions, and thus they know when they can wake to receive possible transmissions from the master. Beacon transmissions destined to the parked stations are broadcast transmissions (BB_PDUs with AM_ADDR = 'b000'), for the simple reason that parked devices don't have an AM_ADDR and thus they cannot be addressed explicitly.
The timing parameters for beacon intervals are numerous. They include an offset parameter denoting the time of the first beacon transmission and the period of the beacon instances. They also include the broadcast repetition parameter, the interval following a beacon instant before the master gives the opportunity to parked devices to request to rejoin the piconet, the length of time that the master will continue giving this opportunity, and so on.
Just as in the sniff and hold modes, the master may force a slave into park mode with an LMP_park PDU. Alternatively, a master or a slave may request that the slave enter into park mode with an LMP_park_req PDU. When a slave is to rejoin the piconet, the master broadcasts in the beacon slots an LMP_unpark_BD_ADDR_req or an LMP_unpark_PM_ADDR_req PDU, depending upon whether the parked device is addressed with its 48-bit BD_ADDR or its 8-bit PM_ADDR. Multiple parked devices can be invited with a single unpark LMP_PDU. In the unpark LMP_PDUs, the master also includes the new AM_ADDR to be assigned to the parked device when it rejoins the piconet as a slave. Note that a parked device cannot be invited to rejoin a piconet when there are already seven active slaves in the piconet. In the latter case, the master may have to park some active devices and free the corresponding AM_ADDRs prior to unparking a parked device.
Bluetooth devices have several options available for managing the bandwidth that is allocated between them. As mentioned earlier, devices may use SCO links whose high-priority periodic transmissions provide for telephony-quality voice communications. Transmissions on ACL links can also be provided with bandwidth guarantees through polling interval restrictions. Support for SCO links is optional, while support for ACL polling interval transactions is mandatory.
Furthermore, to increase the efficiency of the transmission and thus increase the bandwidth supported on an ACL link, link managers may negotiate the use of larger BB_PDUs. Support for this link manager transaction is mandatory; the actual use of larger BB_PDUs needs to be coordinated with additional LMP transactions described below. Finally, devices may dynamically change the encoding schemes of the transmissions to take better advantage of the link quality conditions. Support for this link manager transaction is optional. The latter two transactions are not discussed further.
A piconet supports up to three SCO links for telephony-quality (64 Kbps) voice communications. SCO packets transmitted on the SCO links are of high priority and can preempt any other activity that the device may be involved with, like pages and inquiries, holds, and so on. A device requests the establishment of an SCO link with an LMP_SCO_link_req PDU. This LMP_PDU contains the audio parameters like the period T SCO, the SCO BB_PDU type and the air-mode, which represents the voice codec type. Supported codec types are: 64 Kbps μ-law or A-law PCM format, or 64 Kbps CVSD (continuous variable slope delta) modulation format. With such a high resolution of voice traffic, cellular phone conversations carried to, say, a headset that is connected with a cellular phone over a Bluetooth SCO link should not degrade in quality.
When the master responds positively to a slave's LMP_SCO_link_req PDU or sends its own LMP_SCO_link_req PDU, it supplies the offset DSCO that identifies the time of the first transmission for the new SCO link, and an SCO link unique identifier, or handle. Either the master or the slave can subsequently request to change the parameters of the SCO link, using the LMP_SCO_link_req PDU again, or to remove the link altogether, using an LMP_remove_SCO_link_req PDU. The latter transactions make use of the SCO link handle to identify the particular SCO link whose parameters or status is to be changed.
To control the minimum bandwidth assignment for ACL traffic between two devices, or equivalently the maximum access delay of ACL BB_PDUs, the maximum polling interval [12] for a slave can be adjusted as needed. A master can enforce a new maximum polling interval using an LMP_quality_of_service PDU. In this case, the slave cannot reject the adjustment of the polling interval determined by the master. On the other hand, a master or a slave may request a change in the polling interval with an LMP_quality_of_service_req PDU. In this case, the request can be either accepted or rejected by the other party.
Both of these LMP_PDUs also carry the number of times, N BC, that each broadcast packet is to be repeated. Since this parameter relates to the operation of the entire piconet, and not just to the ACL link between a slave and the master, N BC is meaningful only when it is sent from the master. When this parameter is included in a request LMP_PDU from a slave, it is ignored.
The transactions in this section apply to negotiation of parameters related to the link controller and the baseband protocols, such as negotiation of the paging scheme, timing accuracy, master-slave role switch and so on.
When two devices have already communicated with each other, they may subsequently reconnect with each other more rapidly, since they can bypass the inquiry process. However, during an inquiry response, a slave provides paging information to the master in an FHS packet. When bypassing the inquiry process, this FHS packet is also bypassed. Thus, if a device has modified its paging parameters, perhaps to switch to an optional paging scheme or to change its T pageScan interval, the master will not become aware of the change.
With the paging scheme LMP_PDU transaction, devices can announce or even negotiate the paging scheme to be used the next time these devices page each other. With an LMP_page_mode_req PDU, the requesting link manager suggests to the other link manager the paging scheme to be used when the requesting device pages the other. Likewise, with an LMP_page_scan_mode_req PDU, the requesting link manager suggests to the other link manager the paging scheme to be used when the other device pages the requesting device. Rejecting any of these request LMP_PDUs implies that the current paging scheme is not to be changed. However, a request to change to the mandatory paging scheme cannot be rejected. Support for this transaction is optional.
A paging device becomes the default master of the resulting piconet, although circumstances may necessitate that the roles of the master and the slave be exchanged. For example, such an exchange is needed to implement the LAN access profile using PPP (described in Chapter 15). To initiate the process of master-slave role switch, a device sends an LMP_switch_req PDU, which upon acceptance will initialize the role switch. The switch basically comprises the process of migrating from the master/slave transmit timing sequence in the piconet of the old master (the new slave) to the master/slave transmit timing sequence in the piconet of the new master (the old slave). Support for a master-slave role switch is optional.
A device can request updated clock information from another device to optimize various link controller operations.
An LMP_clock_offset_req [13] PDU sent by a master results in a slave returning the most current offset between the native clocks of the slave and the master as registered by the slave. This information can be used to optimize the paging time when the master pages the slave again in the future. Support for this transaction is mandatory.
An LMP_slot_offset PDU carries with it the slot offset, in microseconds, between the start of the time of a transmit slot from the master and the corresponding transmit slot from the slave, if the slave were to be a master. This information is used to optimize a master-slave role switch. Support for this LMP_PDU is optional.
An LMP_timing_accuracy_req PDU results in returning the long-term jitter, in microseconds, and drift, in parts per million (ppm), of the receiving device's clock. This information is used to optimize the wake time for a device after a long period of inactivity while still being associated with a piconet, such as waking after hold mode, or waking prior to a master's transmission at a sniff slot or a beacon slot for a parked device. Support for this LMP_PDU is optional; when it is not supported the jitter and accuracy are assumed to be at their maximum value of 10 μsec and 250 ppm, respectively.
An LMP_supervision_timeout PDU sent by a master includes the link supervision timeout value used by a link controller to detect the loss of a Bluetooth link between the master and a slave. Support for this LMP_PDU is mandatory.
Link managers typically exchange information about each other to better coordinate their interaction. The LMP_version_req PDU contains the LMP version supported by the sender of this PDU. The receiver of this LMP_PDU returns the LMP_version_res PDU which contains its own supported LMP version. The version number is provided as a triplet [versionNo:companyID:subVersionNo]. The version number part of the triplet is a version of LMP as defined by the SIG. The subversion number is relative to a company that may have its own particular implementation of the protocol. Support for this LMP_PDU transaction is mandatory.
The LMP_features_req PDU contains the optional radio, baseband, and link manager features supported by the sender of this LMP_PDU. The receiver of this LMP_PDU returns the LMP_features_res PDU, which contains its own supported features. These features include the supported packet types, other than the mandatory FHS, NULL, POLL, DM1 and DH1; supported power control modes, voice codecs, encryption, role switch, optional paging schemes and so on. Support for this LMP_PDU transaction is mandatory.
With the LMP_name_req PDU, the requesting link manager requests the user-friendly name of the device that receives this LMP_PDU. The user-friendly name is the name that a user of a device assigns to it. Within a device a name is encoded in UTF-8 and it can be up to 248 bytes long. Since the name of a device can be longer than a single DM1 packet, when a device requests the user-friendly name of another device it also provides an offset parameter that the responding device can use to transmit the proper segment of its name, using the LMP_name_res PDU.
The UTF-8 encoding [IETF96] for device names has been selected for its support of international languages because the Bluetooth wireless technology is targeted for worldwide use. UTF-8 characters are encoded using sequences of 1 to 6 bytes. For compatibility with the widely used ASCII character set, ASCII characters are encoded using a one-byte UTF-8 character, which has the same value as the corresponding ASCII character. Hence, the user-friendly name of a Bluetooth device can be up to 248 ASCII characters long.
LMP is a transport protocol for control information between link managers in devices. LMP does not encapsulate PDUs of any higher communication layer. As such, LMP transactions may occur without involvement of any higher layer, such as L2CAP or the host itself. When a host application in a device wants to communicate with one in another device, the first device sends an LMP_host_connection_req PDU which the receiving device will either accept or not. If the connection request is accepted, the two link managers will negotiate the parameters of the link, like authentication and QoS. When link managers finish negotiating, each sends an LMP_setup_complete PDU. Only after both link managers have issued the LMP_setup_complete PDU can communication that does not involve LMP_PDUs commence between the devices.
When any device wants to terminate its link with another device, it issues an LMP_detach PDU with a reason parameter explaining why the link is to be terminated. The LMP_detach PDU cannot be contested and the link between the two devices will be terminated immediately.
Support for the LMP_PDUs in this section is mandatory.
In this chapter we have highlighted the lower Bluetooth transport protocols: radio, baseband, and link manager. These protocols define the operational characteristics of the Bluetooth wireless technology and instantiate the Bluetooth air-interface. Bluetooth devices use relatively high rate frequency-hopping spread-spectrum transceivers operating over 79 (or 23) 1 MHz channels in the 2.4 GHz ISM RF band. Devices find others in their vicinity using inquiries and request connections to those devices by explicitly paging them. Communicating devices are organized in piconets composed of a master and one or more slave devices. Device transmissions are organized over a TDD transmission time axis, with the slaves transmitting only when they have been first addressed by the master. Bluetooth links between devices can support both asynchronous and synchronous transmissions, and they can be authenticated, encrypted, and conditioned based on QoS demands.
The next chapter presents the upper transport protocols, which aim to conceal the details of the lower transport protocols from higher layers and applications. This allows the higher layers to use the Bluetooth links in a manner that is agnostic of the way that connections and transmissions between devices are organized and managed over the Bluetooth air-interface.
[1] The terms unit, node, station, and so on may (and have) also been used instead of the term device. Insofar as possible, however, the use of these other terms is avoided. The reason for this choice will become apparent later.
[2] The receiver sensitivity for an IEEE 802.11b radio receiver, which uses DSSS, is specified to be –80 dBm for a frame error rate of 8% for a 1024-byte MAC protocol data unit when a 2 Mbps DQPSK modulation is used. For more information on the IEEE 802.11 WLANs see [IEEE99]
[3] The use of the notation BD_ADDR in the specification is the main reason for choosing the term "device" in Figure 6.1 over any of the other legitimate alternatives identified in footnote 1 of this chapter.
[4] The abbreviation "ppm" stands for "parts per million" and it is a metric of clock accuracy, where the smaller the value the more accurate the clock.
[5] The specification refers to the baseband PDUs as such or simply as packets. The BB_PDU nomenclature is introduced here for consistency with use of the terms PDU and packet elsewhere. Nevertheless, the term packet is used whenever appropriate for ease of reading.
[6] The abbreviation "resp." stands for "respectively."
[7] TDD refers to a time-division multiplexing technique where the transmission time on a single communication channel is divided into successive, non-overlapping intervals, every other of which is used for transmissions in one of two opposing directions. The transmission direction alternates between the two directions with each successive interval.
[8] Due to the TDD polling scheme used for medium access control in a piconet, only the master can directly broadcast data to the other piconet members (its slaves). Slaves in a piconet can only unicast (a point-to-point transmission) to the master of the piconet.
[9] For brevity, the qualifier "potential" for masters and slaves will be omitted unless it is required for clarifying the context.
[10] A master sends an FHS packet during a page operation as described in the following section.
[11] When the value of PM_ADDR = '0x00'; is assigned to a device, this device can only be unparked using its BD_ADDR. This could be the case when there are at least 255 parked devices in a single piconet, which is a rather exceptional case.
[12] Recall that a master polls a slave either explicitly through the use of a POLL BB_PDU or implicitly by simply transmitting any payload carrying BB_PDU.
[13] The name of this LMP_PDU is actually LMP_clkoffset_req.