While much of the focus of Bluetooth wireless communication is on the specification of the technology-which is explored in depth in Part 2 of this book-the specification is actually rooted in a set of usage models (sometimes also called usage scenarios or usage cases). Long before there was a specification, the official Bluetooth web site included descriptions of several of these usage models that the technology makes possible. The specification itself was preceded by a marketing requirements document(internal to the SIG); included in those marketing requirements were usage scenarios that were an integral part of the objectives that the initial specification was to address. These scenarios were not intended to cover all possible functions achievable with the technology but rather to set the initial focus for the version 1.0 specification.
Bluetooth usage models are formally specified in profiles, which are examined in Part 3. This chapter focuses on describing the usage models in a general fashion, emphasizing an end user's view of the scenarios and the benefits that Bluetooth wireless communication offers in those scenarios. Not all of the usage cases described in this chapter have a corresponding profile, although all of the scenarios have at one time or another been discussed, presented or published by the SIG, and they are representative of those usage cases that drove the development of the specification. If a usage model described here has no corresponding profile, it simply means that the SIG has not formally specified that scenario with version 1.0 of the specification. In many instances such usage scenarios could be realized with Bluetooth technology as defined in the current specification, but the SIG has not (yet) formalized an interoperable definition for doing so.
The usage models described here are just an initial set of scenarios that could be accomplished with Bluetooth wireless communication.[1] New applications of the technology will undoubtedly continue to be invented, and it is expected that new scenarios and new profiles will emerge from the SIG over time (Part 4 discusses some future possibilities).
At its heart, Bluetooth wireless communication is all about replacing cables. One place where many cables exist, and where these cables are sometimes unwieldy, is the typical desktop computer. The cordless computer usage model is not specifically addressed in version 1.0 of the specification, but it is expected that this scenario could be realized in a straightforward manner in the future. As depicted in Figure 3.1, many of the cables associated with computer peripherals could be replaced by wireless links. Keyboards, mice, joysticks, speakers, printers, scanners and the like might all employ Bluetooth wireless communications. While not shown in the figure, other computer-related wires such as personal digital assistant cradles, digital camera cables and network connection cables could also be replaced by wireless connections (these three examples are discussed below in "The Automatic Synchronizer," The Instant Postcard and The Internet Bridge usage models, respectively).
In addition to the directly evident benefits of not having to deal with cables during installation and operation of the computer, wireless devices offer more freedom in placement and use. Speakers, printers and scanners, for example, could be placed in the most appropriate location for the environment, unrestricted by connectors and cable length. User interface devices such as keyboards, mice and joysticks could be used wherever it is convenient to do so and could move with the user rather than being fixed in a certain location where they would be constrained by a cable.
Device sharing is much easier in this configuration than in a cabled environment. A joystick, for example, need not be used exclusively with the computer but might also be used with a video game. Even more important for many people, though, is the capability to share peripherals such as printers or scanners. Today sharing these devices often requires a networked environment where the computer that hosts the peripheral acts as a server; if other devices need to use the peripheral they do so via the hosting computer which is cabled to the peripheral. With the cordless computer, other devices using Bluetooth wireless communication could directly access peripherals in peer-to-peer fashion.
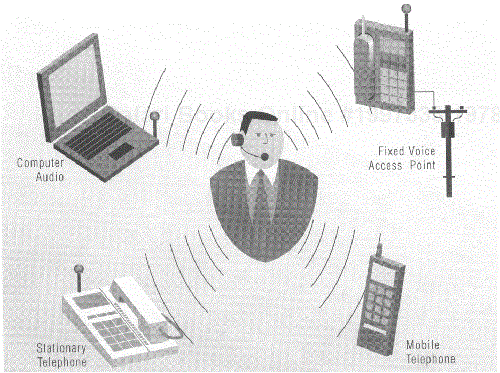
Support for voice in Bluetooth wireless communication fosters this usage model. Telephone headsets are increasingly common for use with both fixed and mobile telephones. In environments such as call centers (help desks, centralized reservations offices, and so on) headsets might be used with standard telephones to keep a person's hands free to use a computer. Headsets are also available for use with many mobile telephones, also for hands-free operation for situations such as driving or walking while carrying items. Bluetooth wireless communication removes the cable between the headset and the telephone. A call could be placed using the telephone keypad, with the audio portion of the call being carried through the headset's microphone and speaker. Figure 3.2 illustrates various instances of the ultimate headset usage model, including the use of the headset with nontelephony devices, described more fully below.
One advantage of the ultimate headset is that it supports mobility. The user of the headset is not physically tied to the audio device and thus is free to roam about the area while keeping the connection intact. Another advantage is the ability to use the same headset with multiple devices. Because the specification offers a standard interface, the same headset used with a telephone might also be used with a fixed voice access point, such as a cordless telephone base station, and could also be used for audio interaction with computers. In the future it also may be possible to use such a headset with stereos, portable CD players and recording devices. As with the cordless computer, the ultimate headset allows devices to be placed wherever it may be convenient, which for mobile devices might be in a pocket or briefcase. With appropriate speech technologies it indeed may be possible, through the use of voice recognition, to place telephone calls using only the headset as the user interface.
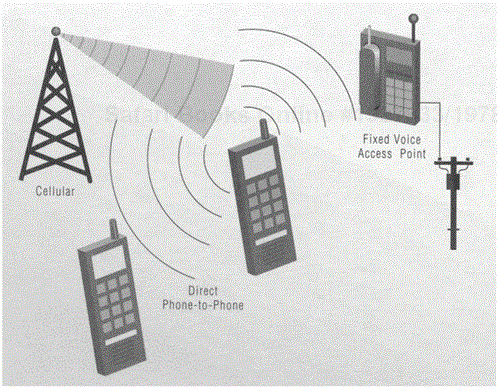
Today many people use multiple telephones: a phone in the office, one or more telephones at home (some wired, some cordless), a mobile (cellular) telephone, public telephones, and so on. A single phone using Bluetooth wireless communication could be used in place of many of these other telephones. The three-in-one phone usage model allows a mobile telephone to be used as a cellular phone in the standard manner, as a cordless phone connecting to a voice access point (cordless phone base station), and as an intercom or "walkie-talkie" for direct phone-to-phone communications with another device in proximity. Figure 3.3 shows all three uses of the three-in-one phone.
A key benefit of the three-in-one phone is that a single telephone could become the only one that a person needs. If multiple voice access points using Bluetooth wireless communication become available in environments such as the home, office and public areas, a single personal telephone that is usable almost anywhere becomes realistic. The need for separate telephones and separate telephone numbers in the office, at home and while traveling could be reduced. Another benefit that derives from the use of such voice access points is the possibility for reduced cellular airtime charges. When the handset is used as a cordless phone, communicating with a standard "landline" telephone service via an access point, no cellular airtime charges need be incurred.
The direct telephone-to-telephone, or "walkie-talkie" function of the three-in-one phone usage model is most useful with the 20 dBm power amplified radio, with its range of 100 meters. When two parties are within range of each other using standard Bluetooth radios (10 meters), it is likely that they could shout at each other rather than use telephone radio communication (aside from situations where a physical obstacle might separate the parties). Because a direct phone-to-phone communication scenario across only a 10-meter range might have limited utility, the SIG indeed debated whether or not this walkie-talkie function should be included in the usage model, since the focus of the version 1.0 specification is on a standard 0 dBm Bluetooth radio (there was some discussion of removing this use of the telephone and calling this usage model the two-in-one phone). However, even with the standard radio with its 10-meter range there are situations where the direct phone-to-phone communication might be useful. These might include cases such as people communicating across different floors of a building, from within confined spaces or when nonintrusive communication is desired even when both parties might be able to see each other (for example, video and sound control workers in a crowded auditorium).
One of the most fundamental and useful applications for any type of data networking, including simple point-to-point links (like those of Bluetooth wireless communication), is to exchange files and other data objects. File transfer using floppy disks or cables is common; wireless communication removes the need for cables, making it much easier to form temporary links between devices to quickly exchange files and other data objects. For example, as infrared data ports become more widely used with notebook computers, mobile telephones and personal digital assistants, it is not uncommon for users to establish a temporary infrared link to exchange electronic business cards and other data. This same sort of file and object transfer is possible with Bluetooth wireless communication. In an interactive conference room scenario, business cards and files could be exchanged among the participants of the meeting. Figure 3.4 illustrates the Bluetooth file transfer usage case; as shown, not only could files be transferred between two computers but objects also could be transferred between any two devices using Bluetooth wireless communications.Chapter 14 discusses the details of the various modes and types of file and object transfer.
A primary benefit of wireless file transfer is the convenience that it offers. Data could be exchanged easily between two or more devices without the use of cables (which, as pointed out in the introduction, are likely to be cumbersome, proprietary and incompatible between two given devices) and without the need to set up and configure a full-blown network among the devices. Files and other objects could be exchanged immediately in a conference room setting, rather than deferring the transmission of the files until after a meeting is over when a computer or other device can be connected to a network.
There are two similar yet different methods for using Bluetooth communication as a wireless "bridge"[2] to established networks like the Internet or campus or corporate intranets. The first method is dial-up networking using a telephone as a wireless data modem; the second is direct local area network (LAN) access using a data access point.
This form of the Internet bridge is no different from the method many people use to access the Internet today. A conventional arrangement involves connecting a computer to the Internet using a telephone to dial an Internet service provider through a modem. What Bluetooth communication adds to this scenario is the ability to accomplish this usage model entirely without wires. Today's usage models for dial-up networking typically require a cable between the computer and the telephone; even when a mobile telephone is used, a cable between the computer and the mobile telephone is usually required. With a computer and a telephone that both support the dial-up networking profile, the end-to-end connection to the Internet (or other network) could be wireless, as illustrated in Figure 3.5.
While dial-up networking is a popular way to access the Internet, especially from homes or other environments where telephone lines (or in some cases, cable or high-speed data connections) are the primary communications bridge, direct access to LANs is common in enterprises, on campuses, and in other similar environments. The directly accessed local area network often provides a gateway to the Internet, enabling the Internet to be accessed from the LAN without a dial-up connection.
Direct network access via Bluetooth wireless communication is possible using data access points. A data access point allows devices to connect to it wirelessly; the data access point in turn connects to the local area network. Once again this is not functionally different from the same sort of connection in a wired environment, such as a traditional Ethernet network where computers connect to network access points using cables. A data access point with Bluetooth wireless communication simply provides a "wireless plug" to connect to the network as illustrated in Figure 3.6.

Figure 3.6. The Bluetooth internet bridge usage case 2: direct local area network access through a data access point.
The Internet bridge is one case where Bluetooth wireless communication can be used to replace cables, making a common task easier and more convenient. Dial-up networking, for example, is common today with wired modems and telephones. Many business travelers have experienced searching a hotel room for the telephone jack so as to plug in their notebook computer's modem for dial-up networking. With Bluetooth wireless communication, no cable connection is required; a hotel room telephone or a person's own mobile phone could be used as a wireless data modem. The use of a mobile telephone as a wireless data modem is not uncommon today, but in most cases the mobile phone still needs to be cabled to the notebook computer; Bluetooth wireless communications could further improve upon this scenario by removing the cable between the computer and the phone.
Direct network access using Bluetooth wireless communication offers advantages over the equivalent wired scenario. In addition to obviating the need to provide an in-building wired infrastructure with endpoint connections at every access point, a wireless data access point also offers the possibility for devices to share the access point. Multiple devices in proximity of a single data access point could access the network wirelessly rather than requiring each device to have a separate cabled connection to its own access point. Moreover, data access points could be designed such that they could plug into existing network wiring infrastructure and thus allow "the last hop" to be wireless, with its associated conveniences, while making use of and protecting the investment in the existing wired network.
The speaking laptop is one of the usage models that is not advertised in version 1.0 of the specification, perhaps because it could be considered a straightforward extension of the headset profile already described.[3] The concept behind it is that a laptop (or notebook) computer's microphone and speaker could be used as the audio input and output for a voice call placed on a mobile telephone. As an example, suppose someone places a call on a mobile phone during a meeting. As the conversation progresses, it becomes evident that others in the meeting would benefit from taking part in the call. Bluetooth wireless communication could be used to route the voice traffic to a notebook computer in the conference room, allowing the computer to be used as a speakerphone. The call is still being carried over the mobile phone's wide area voice network but the audio source and sink are now at the notebook computer. Figure 3.7 illustrates the speaking laptop scenario.
The speaking laptop usage model is an example of extending the functions of one device by allowing it to "borrow" the capabilities of some other device. Speakerphone capability becomes available, using the speaker and microphone of the notebook computer, even if the mobile phone does not have its own speakerphone capability. Extensions to the speaking laptop scenario might enable other similar usage models where existing audio input and output could be used to supplement that of a mobile telephone. For example, the audio portion of a call could also be routed to a car's audio system in a vehicle with Bluetooth wireless communications.
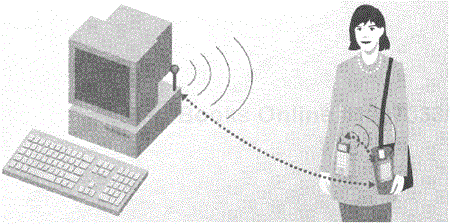
The automatic synchronizer is an example of using proximity networking to add value by making an existing task easier to do. Personal portable devices empower people to have quick and easy access to information they can use in their daily lives. For that information to be most useful it needs to be kept up to date, but this personal information management data might be distributed across the many devices that a person could use. For example, new calendar entries or to-do list items might be entered on any of a notebook computer, personal digital assistant or smart phone; or these entries might be entered on a desktop computer and stored on a server in a network. Synchronization is the process of merging the data from two different sources based upon some set of rules such that the resulting data sets are identical (or at least reflect identical information). A common example is synchronizing a personal digital assistant with a desktop or notebook computer. Today this often is performed using special serial cables and software that may be unique to the device. Standard protocols and object formats in the specification allow data on one device to be synchronized with data on any other device, whether they be PDAs, notebook computers, smart phones or even networked data accessed through a data access point.
The "automatic" part of this usage model is enabled by proximity networking. Today synchronization is almost always a conscious effort-it involves connecting a serial cable and pushing a button, or pointing two infrared-capable devices at each other and launching an application. With Bluetooth wireless communications it is possible for two devices to automatically synchronize whenever they come within range of each other. For example, a personal digital assistant carried in a person's pocket could automatically synchronize with that person's desktop computer whenever she walked into her office. Clearly it should be possible to configure the devices as to when and how to automatically synchronize, and to ensure that devices synchronize only with other known devices and data sources and not with just any random device; the specification does offer mechanisms that could be used to do this. Figure 3.8 shows examples of the automatic synchronizer. The figure illustrates how different devices in a personal area network (such as the mobile telephone and PDA shown) might automatically synchronize. The figure also shows how one of those devices (here, the PDA in the briefcase) might also synchronize with a desktop computer when those devices come within range of each other (in this case, when the PDA's owner walks into her office).
In addition to the convenience afforded by automatic synchronization, Bluetooth wireless communication removes the requirement for cables. By specifying a standard protocol and object formats for synchronization (these are adopted from IrDA, as detailed in Chapters 9 and 14), Bluetooth wireless communication makes it easier for any device to synchronize with any other device. This multidevice synchronization enables a person to use any convenient device to enter new appointments, to-do list items or other data.
The instant postcard is another usage model that was discussed early in the development of the specification but is not formally part of the version 1.0 profiles. This is one of the few scenarios that involves a device other than a mobile phone or computing platform, although it is expected that over time many new usage models and profiles will be developed for additional device classes. The underlying concept is that of having a digital camera which can wirelessly transfer a photo image to some other device which could then e-mail the image to a recipient, thus creating a digital "postcard." Today many digital cameras use a serial cable to transfer photo images to a computer where they can be stored, catalogued, manipulated and distributed. As with the other version 1.0 usage models, Bluetooth wireless communication removes the need for a cable which in turn presents new ways to use a device, as pointed out below. Figure 3.9 shows how the instant postcard might be realized.
This scenario is useful not only for sending "postcard" type pictures to friends and relatives but also for commercial applications, such as real estate (transferring photos of newly listed homes to a central database), law enforcement (transferring photos of suspects or stolen vehicles, for example) and insurance (transferring photos of automobile damage resulting from accidents). In addition to replacing cables, Bluetooth technology also could change the way a digital camera is used, since photos need not necessarily be transferred to a computer. Many photos might be transferred directly from the camera to a mobile phone and then sent as an e-mail attachment without using a computer as an intermediary. In addition, the transfer of photos from the camera to a database or library could be accomplished in more of a real-time fashion, since no cabling is required.
This usage model could be considered to be an extension of the interactive conference (file transfer) scenario. It is not specifically addressed in the version 1.0 specification but it does provide an illustration of usage cases that could be enabled in the future. Ad hoc networks are networks that form spontaneously; Bluetooth wireless communication is an enabling technology for these sorts of applications. The interactive conference usage model showed how objects such as electronic business cards or files could be exchanged in a conference room setting. When ad hoc networks can be formed among the meeting participants, additional applications become possible. Among these are collaborative applications such as real-time viewing and group editing of presentations and instant messaging among the meeting participants.
Ad hoc networks consisting of diverse types of devices present many new and exciting possibilities for usage scenarios. While more work is required to establish interoperable methods for general networking,[4] Bluetooth wireless communication is positioned to be an enabling technology for ad hoc networking scenarios.
Hidden computing (sometimes called unconscious computing) is one of the most exciting future applications for Bluetooth technology. While not directly addressed in the version 1.0 specification, hidden computing has been discussed at SIG events in the past and is an area ripe for future exploration. The fundamental elements required for some forms of hidden computing already exist in the current specification, although the SIG has not developed profiles that describe how the various hidden computing applications might be accomplished in a standard and interoperable manner.
Hidden computing involves a class of applications in which devices that are not overtly being used by a person can still perform tasks on that person's behalf. We have already seen one example that could be considered a hidden computing application: the automatic synchronizer. In that usage model, a PDA "hidden" in a pocket or purse could synchronize with another device without user intervention. Several other examples have been described in the context of Bluetooth wireless communication. Among these are:
A notebook computer "hidden" in a briefcase in a "sleeping" mode could be configured to awake periodically, receive new e-mail and send information such as new e-mail alerts (and possibly a short clip of the e-mail content) to a mobile phone. The user might then decide to browse e-mail using the mobile phone or process e-mail on the notebook computer.
A mobile telephone "hidden" in a pocket or purse could be used by an appropriately configured notebook computer "hidden" in a briefcase to access a network in the manner described for the Internet bridge (dial-up networking) scenario. Once the computer is connected to a network in this fashion, network synchronization or transmission and reception of e-mail could be initiated, all without conscious user interaction with either device.
In early stages of the development of the specification, such applications were called "the briefcase trick." With proximity networking enabled by Bluetooth wireless communication, hidden computing applications abound. Other future possibilities might include the use of a hidden device that controls environmental settings (such as home climate and lighting, music, automobile driver's seat and mirror adjustments and so on) based upon the personal preferences of the user, automatic customer discounts applied at points of sale based upon a device tucked away in a pocket or suitcase, and automated identification and authentication when a person checks in with an airline or a hotel.
These sorts of scenarios are almost limitless. While hidden computing applications may not be fully realized for some time, the Bluetooth technology does offer a basis upon which industry innovators could build them.
[1] Some scenarios could also be accomplished with other technologies, and the usage models are not necessarily unique to Bluetooth wireless communication.
[2] The term bridge is used here since it is consistent with the nomenclature used by the SIG. The function described here is similar to a traditional network bridge, which is distinct from a router. While no Bluetooth "Internet router" usage case exists in version 1.0, such a function is not beyond the realm of possibility.
[3] The technical underpinnings of routing voice traffic between a telephone and another device are similar, although the speaking laptop has some distinct end-user considerations that merit its independent discussion here.