13
Quality of Service, Security, and Privacy for Wearable Sensor Data
13.1 Introduction
A great deal of clinical data, including radiological images, physiological signals, impression reports by physicians, laboratory reports, and above all patients' identities, are spread around the local and public networks, large core memories, and the cloud. The major concerns in recording, analysis, and disseminating the patient data are quality of service (QoS), network and data security, and, most importantly, protecting patient privacy. The confidentiality, authenticity, integrity, and freshness of patient data are certainly the major body area network (BAN) requirements. The communication systems, techniques, and platforms necessitate having to establish security systems or implement one of the existing data and network security platforms.
Data confidentiality requires that the transmitted information remain strictly private and can only be accessed by authorised persons, for example the doctor who takes care of the patient. It is usually achieved by encrypting the information before sending it using a secret key. Data authenticity is needed to ensure that the information is sent by the right sender for the intended purpose to a recipient through a secure system environment. For this, often a message authentication code is calculated using a shared secret key. Data integrity makes sure that the received data have not been tampered with. However, this can be inspected by verifying the media access control (MAC) address within the computer network layer. Data freshness is required as the received data should be recent and not be a replayed old message for any reason such as disruption or impersonation. Commonly, a counter controlled technique is employed where the counter is increased every time a message is sent.
In this chapter there is no intention to go through all of the details of the various security methods and approaches. Instead, we focus on some practical applications for wireless BAN which aim at keeping patients' information safe and secure while maintaining the QoS.
There have been variety of approaches to wireless sensor network (WSN) security. Recent advances in wireless communications, embedded systems, and integrated circuit technologies have enabled the wireless BANs with their diverse applications to become a promising networking paradigm.
The patient's personal and clinical data collected or transmitted in BANs are very sensitive, crucially personal, and not only related to their clinical states but also to their entire personal and family status and circumstances. Generally and based on clinical ethics, biomedical data are highly confidential and should be handled, transmitted, and stored with care to prevent information misused, alteration, or leaks to unauthorised users. Therefore, authentication, data confidentiality, integrity, nonrepudiation, and privacy preservation should be guaranteed during all communications while maintaining a high QoS. The QoS requires minimum delay in transferring the patient's data to ensure that their situation will not be negatively affected because of such delays. To comply with these requirements, IEEE 802.15.6 has been proposed to provide an international standard for reliable wireless communication for wireless BANs which supports data rates ranging from 75.9 kb s−1 to 15.6 Mb s−1 [1]. Adopted international standards also recommend four elliptic curve-based security schemes to achieve those goals. Nevertheless, in some recent works it has been shown that these security protocols are vulnerable to some attacks [2, 3]. Therefore, in the past few years, several anonymous authentication schemes for wireless body area networks (WBANs) have been proposed to enhance the information security for protecting patients' identities and through the encryption of such sensitive information.
13.2 Threats to a BAN
As for various wired or wireless communication systems and scenarios, the local area network (LAN) including BANs are prone to attacks, eavesdroppers, impersonation, and all other popular breaches of security. For a wearable device, the received information includes private and sensitive information coming from wearable devices and sensors [4, 5]. This underscores the importance of establishing secure a mutual authentication between the mobile terminal, wearable devices, and sensors. Such a scheme allows one to establish the necessary session key for subsequent secure communications [6]. Similar to a wireless communication environment [7], a wearable communication network is suspected for several well-known attacks, such as man-in-the-middle, replay, impersonations, stolen wearable device or mobile terminal, and ephemeral secret leakage attacks [8].
Assuming that the BSNs and other LANs are prone to similar types of threats, the most common types of network and system attacks are listed below.
13.2.1 Denial-of-service
Denial-of-service (DoS) attacks are probably the most common security problem which affects many unprotected systems including BANs. DoS attack is a type of cyberattack during which a malicious actor attempts to make a computer or other device unavailable to its intended users, thereby interrupting the device's normal functioning. These attacks typically function by overwhelming or flooding a targeted machine with requests until normal traffic is unable to be processed, resulting in DoS to new users. A DoS attack is usually launched by a single computer/user. However, a distributed denial-of-service (DDoS) attack is a type of DoS attack that comes from many distributed sources. A popular example of this kind is a botnet DDoS attack. DoS attacks typically fall in two categories: (i) buffer overflow attacks in which a memory buffer overflow can cause a machine to consume all available hard disk space, memory, or CPU time (this form of exploitation often results in sluggish behaviour, system crashes, or other deleterious server behaviours, resulting in DoS); (ii) flood attacks, in which by saturating a targeted server with a large number of packets, a malicious actor is able to oversaturate the server capacity resulting in DoS. For successful DoS attacks, the malicious actor must have more available bandwidth capacity than the target.
13.2.2 Man-in-the-middle Attack
This occurs when a hacker inserts itself between the communications of a client and a server (by stealing personal information, such as login credentials, account details, or credit card numbers) and sniffs the information. Common types of man-in-the-middle attacks include session hijacking, IP spoofing, and replay. The aim of this attack is either to eavesdrop or to impersonate one of the parties, making it appear as if a normal exchange of information is underway. This is common in places where a login is necessary to start the communication.
13.2.3 Phishing and Spear Phishing Attacks
A phishing attack is the practice of sending emails that appear to be from trusted sources with the goal of gaining personal information or influencing users to do something. It could involve an attachment to an email that loads malware onto the user computer. It could also be a link to an illegitimate website that can trick the user into downloading malware or handing over their personal information. On the other hand, spear phishing is a very targeted type of phishing activity. Attackers take the time to conduct research into targets and create messages that are personal and relevant. Because of this, spear phishing can be very hard to identify and even harder to defend against. One of the simplest ways that a hacker can conduct a spear phishing attack is email spoofing, which is when the information in the ‘From’ section of the email is falsified, making it appear as if it is coming from someone known to the legitimate user. Another technique that scammers use to add credibility to their story is website cloning: they copy legitimate websites to fool the user into entering personally identifiable information or login credentials.
13.2.4 Drive-by Attack
A drive-by download attack is a common method of spreading malware. Hackers look for insecure websites and plant a malicious script into HTTP (hypertext transfer protocol) or PHP (personal home page – hypertext processor) code on one of the pages. This script might install malware directly onto the computer of someone who visits the site, or it might redirect the victim to a site controlled by the hackers. Drive-by downloads can happen when visiting a website or viewing an email message or a pop-up window. Unlike many other types of cyber security attacks, a drive-by doesn't rely on a user to do anything to actively enable the attack, i.e. there is no need to click a download button or open a malicious email attachment to become infected. A drive-by download can take advantage of an app, operating system, or web browser that contains security flaws due to unsuccessful, or lack of, updates.
To protect a system or network from drive-by attacks, the browsers and operating systems need to be kept up to date and avoid websites that might contain malicious code. The users should stick to the sites they normally use, although even these sites can be hacked. Also, not too many unnecessary programs and apps should be keep on the system as the more plug-ins are active, the more vulnerabilities can be exploited by drive-by attacks.
13.2.5 Password Attack
Entering passwords are the most commonly used mechanism to authenticate users to an information system. Hence, obtaining passwords is a common and effective attack approach. Access to a person's password can be obtained by looking around the person's desk, ‘sniffing’ the connection to the network to acquire unencrypted passwords, using social engineering, gaining access to a password database, or outright guessing. The last approach can be done in either a random or a systematic manner.
13.2.6 SQL Injection Attack
SQL (structured query language) injection has become a common issue with database-driven websites. It occurs when a malefactor executes a SQL query to the database via the input data from the client to the server. SQL commands are inserted into data-plane input (for example instead of the login or password) in order to run predefined SQL commands. A successful SQL injection can read sensitive data from the database, modify (insert, update, or delete) database data, execute administration operations (such as shutdown) on the database, recover the content of a given file, and, in some cases, issue commands to the operating system.
13.2.7 Cross-site Scripting Attack
Cross-site scripting attack (XSS) attacks use third-party web resources to run scripts in the victim's web browser or scriptable application. Specifically, the attacker injects a payload with malicious JavaScript into a website's database. When the victim requests a page from the website, the website transmits the page, with the attacker's payload as part of the HTML body, to the victim's browser, executing the malicious script. For example, it might send the victim's cookie to the attacker's server, and the attacker can extract it and use it for session hijacking. The most dangerous consequences occur when XSS is used to exploit additional vulnerabilities. These vulnerabilities can enable an attacker to not only steal cookies but also log key strokes, capture screenshots, discover and collect network information, and remotely access and control the victim's machine.
13.2.8 Eavesdropping
Eavesdropping attacks occur through the interception of network traffic. By eavesdropping, an attacker can obtain passwords, credit card numbers, and other confidential information that a user might be sending over the network. Eavesdropping can be passive or active:
- Passive eavesdropping. A hacker detects the information by listening to the message transmission in the network.
- Active eavesdropping. A hacker actively grabs the information by disguising themselves as a friendly unit and by sending queries to the transmitters. This is called probing, scanning, or tampering.
Detecting passive eavesdropping attacks is often more important than spotting active ones, since active attacks require the attacker to gain knowledge of the friendly units by conducting passive eavesdropping before. Data encryption is the best countermeasure for eavesdropping.
13.2.9 Birthday Attack
Birthday attacks are made against hash algorithms that are used to verify the integrity of a message, software, or digital signature. A message processed by a hash function produces a message digest (MD) of fixed length, independent of the length of the input message. This MD uniquely characterises the message. The birthday attack stems from the probability of finding two random messages that generate the same MD when processed by a hash function. If an attacker calculates a similar MD for their message as that of the user, they can safely replace the user's message with their own message, and the receiver will not be able to detect the replacement even if it compares the MDs.
13.2.10 Malware Attack
Malicious software is an unwanted software installed in the system without the user's consent. It can attach itself to a legitimate code and propagate and lurk in useful applications or replicate itself across the Internet. There are a variety of factors and viruses affecting the system by performing this type of attack. Typical malware viruses and programs are macro viruses infecting applications such as Microsoft Word or Excel. Other file infectors attach themselves to executable codes such as.exe files. System or boot-recorded infectors (viruses) attach to the master boot record on hard disks and load into the memory when the system starts. Polymorphic viruses conceal themselves through varying cycles of encryption and decryption. Stealth viruses take over system functions to conceal themselves by compromising malware detection software so that the software will report an infected area as being uninfected. The popular Trojan virus hides in a useful program and usually has a malicious function and, unlike other viruses, does not self-replicate. A logic bomb is a type of malicious software appended to an application triggered by a specific occurrence, such as a logical condition or a specific date and time. Worms differ from viruses in that they do not attach to a host file but are self-contained programs that propagate across networks and computers through email attachments or such like. Droppers install viruses in computers. Finally, ransomware is a type of malware that blocks access to the victim's data and threatens to publish or delete it unless a ransom is paid.
Besides the above common network and system attacks, for BANs there should be a registration procedure built in the BAN security with authentication protocols to protect the wearable device or the mobile terminal against theft.
The protocols designed for BAN by different research groups aim to protect the system and the network against all these attacks. As an example, in the protocol designed by Des et al. [9] the BAN is protected against many attacks including stolen mobile terminal, replay, man-in-the-middle, stolen wearable device, impersonation, unanimity and untraceability, password change, and ephemeral secret leakage attacks. The network model, including a typical authentication model of wearable devices, and the threat model (widely used Dolev-Yao threat model [10]) have been set to test the system. In their scheme the endpoint entities (e.g. wearable devices and mobile terminals) have been considered as untrustworthy nodes.
Following the work in [9], the group designed a remote user authentication scheme through which a user (a doctor) and a controller node can mutually authenticate each other and establish a session key for their future secure communication [11]. Apart from that, the pairwise key establishment between a controller node and its implantable medical devices is also provided in the proposed scheme for secure communication between them. In terms of computational cost, their scheme is comparable with the existing related schemes while it provides better security and more functionality features.
Liu and Chung [12] proposed a user authentication scheme through bilinear pairing and a trusted authority for authenticating the user. In addition, they established a secure communication between a node (sensor) and the user. In some other proposals the authors tested the vulnerability of Liu and Chung's system [13] and proved that it was not sensitive enough to some attacks. Then, they proposed a secure three-factor authentication and key agreement approach suitable for BANs.
13.3 Data Security and Most Common Encryption Methods
The IEEE 802.15.6 security hierarchy is illustrated in Figure 13.1. There are three security levels that the BAN sensors and hubs can comply with: level 0 for unsecured communication, level 1 for authenticated but not encrypted messages, and level 2 for the authenticated and encrypted cases. In a unicast communication, a pre-shared or a new master key (MK) is activated. A pairwise temporal key (PTK) is then generated which is utilised only once per session. In a multicast communication, on the other hand, a group temporal key (GTK) is generated that is shared with the corresponding group [1].
In a data security process, to keep the identities and messages secure, the information is encrypted just before propagating it into a network and decrypted in the receiver. The encryption key is somehow known by both transmitter and receiver. There are a variety of encryption/decryption algorithms, and to better protect the message against unlocking a more sophisticated encryption algorithm has to be used.
Although encryption of the information is good enough for many BAN communication scenarios, in many other cases using both encryption and authentication together becomes necessary to validate both the user's identity as well as the data.
Data encryption standard (DES), triple DES, Rivest–Shamir–Adleman (RSA), advanced encryption standard (AES), and Twofish are probably the most popular encryption methods. It is also common for different suppliers, users, and applications to have their own (but often very close to one of these five) algorithms.

Figure 13.1 IEEE 802.15.6 security hierarchy [1].
Source: Courtesy of IEEE.
13.3.1 Data Encryption Standard (DES)
This well-established encryption technique uses a symmetric-key block cipher published by the National Institute of Standards and Technology (NIST) [14]. DES implements a Feistel cipher and uses 16 round Feistel structure. The block size is 64-bit. Despite having the key length of 64-bit, DES has an effective key length of 56 bits, since 8 of the 64 bits in the key are not used by the encryption algorithm and are used as check bits only. The general structure of DES is depicted in Figure 13.2.
13.3.2 Triple DES
It is a type of computerised cryptography, introduced by IBM, where block cipher algorithms are applied three times to each data block. The key size is increased in triple DES to ensure additional security through encryption capabilities. Each block contains 64 bits of data [15].
13.3.3 Rivest–Shamir–Adleman (RSA)
This is an asymmetric cryptography algorithm which works on two different keys, namely a public key and a private key. As the name describes, the public key is given to everyone and the private key is kept private. Since this is asymmetric, nobody else except the browser can decrypt the data even if a third party has the browser's public key.
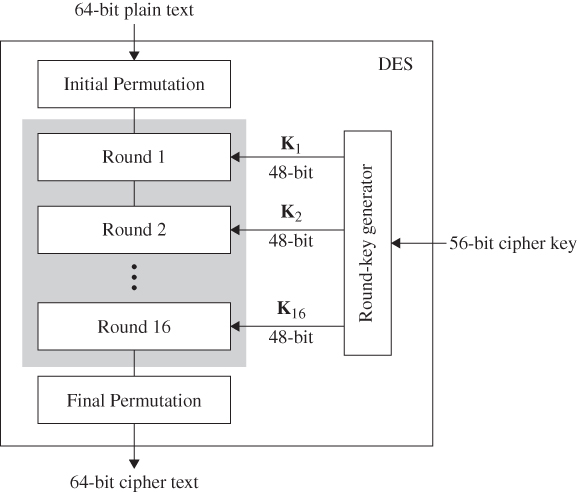
Figure 13.2 A DES structure.
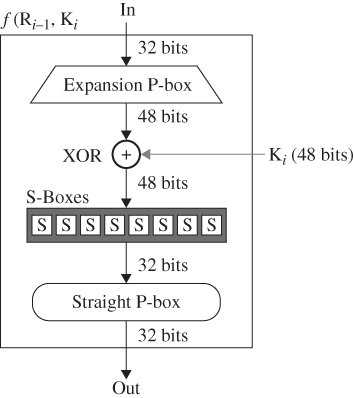
Figure 13.3 A DES round function.
The RSA user generates a public key using two large prime numbers along with an auxiliary value. The prime numbers must be kept secret. Anyone can use the public key to encrypt a message, but with currently published methods, and if the public key is large enough, only someone with knowledge of the prime numbers can decode the message feasibly [16]. RSA decryption is as difficult as the factorisation problem and is an open question.
RSA is a relatively slow algorithm, and because of this it is less commonly used to directly encrypt the user's data. More often, RSA passes encrypted shared keys for symmetric key cryptography which in turn can perform bulk encryption-decryption operations at much higher speed.
The Round function is the heart of DES which can be summarised, as in Figure 13.3. The DES function applies a 48-bit key to the rightmost 32 bits to produce a 32-bit output. This is then extend to 48 bits using an expansion permutation box (P-box). The aim of S-boxes is to use the input as an address for a table look-up to generate the output. Finally, the round-key generator creates sixteen 48-bit keys out of a 56-bit cipher key.
13.3.4 Advanced Encryption Standard (AES)
The AES is a fast algorithm which uses three cryptographic keys to encrypt and decrypt electronic data. AES is an iterative rather than Feistel cipher (which is block-based and symmetric). It is based on ‘substitution–permutation network’. It includes a series of linked operations, some of which involve replacing inputs by specific outputs (substitutions) and others shuffle bits around (permutations) [15].
AES performs all its computations on bytes rather than bits. Hence, AES treats the 128 bits of a plaintext block as 16 bytes. These 16 bytes are arranged in four columns and four rows so they can be processed as a matrix.
Unlike DES, the number of rounds in AES is variable and depends on the key length. AES uses 10 rounds for 128-bit keys, 12 rounds for 192-bit keys, and 14 rounds for 256-bit keys. Each of these rounds uses a different 128-bit round key, which is calculated from the original AES key. Figure 13.4 presents a block diagram of the AES structure.
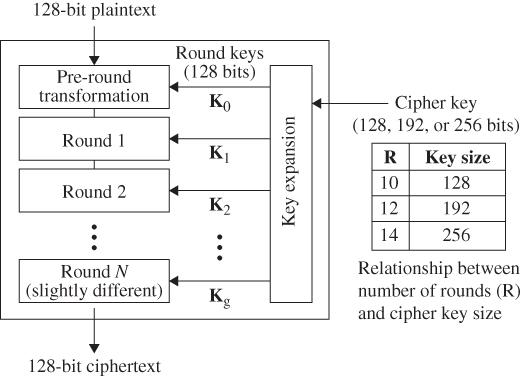
Figure 13.4 An AES structure.
Each round comprises four subprocesses. The first-round process is depicted in Figure 13.5.
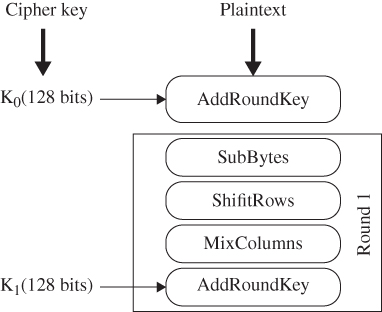
Figure 13.5 The process steps of the first round.
The blocks in Figure 13.5 are defined as follows:
- Byte Substitution (SubBytes): The 16 input bytes are substituted by looking up a fixed table (S-box) given in the design. The result is in a square matrix form including four rows and columns.
- Shiftrows: Each of the four rows of the matrix is shifted to the left. Any entry that ‘fall off’ is re-inserted onto the right side of the row. The shift operation is carried out as follows: first row is not shifted, second row is shifted one (byte) position to the left, third row is shifted two positions to the left, and the fourth row is shifted three positions to the left. The result is a new matrix consisting of the same 16 bytes but shifted with respect to each other.
- MixColumns: Each column of the four bytes is now transformed using a particular mathematical function. This function takes the four bytes of one column as input and produces four completely new bytes as the outputs, which replace the original column. The result is another new matrix consisting of 16 new bytes. This step is not carried out in the last round.
- Addroundkey: The 16 bytes of the matrix are now considered as 128 bits and are XORed to the 128 bits of the round key. If this is the last round then the output is the ciphertext. Otherwise, the resulting 128 bits are interpreted as 16 bytes and another similar round begins.
- Decryption process: The decryption process for an AES ciphertext is similar to the encryption process in the reverse order. Each round consists of four processes conducted in the reverse order, i.e. add round key, mix columns, shift rows, and byte substitution.
Since the subprocesses in each round are in reverse order, unlike for the Feistel cipher, the encryption and decryption algorithms, although closely related, need to be separately implemented.
13.3.5 Twofish
Twofish is a symmetric key block cipher with a block size of 128 bits and key sizes up to 256 bits. A single key is used for encryption and decryption. Twofish accepts a key of any length up to 256 bits. (NIST requires the algorithm to work with 128-, 192-, and 256-bit keys.) It is fast on both 32-bit and 8-bit CPUs (such as smart cards and embedded chips), and in hardware. Owing to its high flexibility, it can be used in network applications where the keys change frequently and in applications where there is little or no RAM and ROM available [17].
There are many other encryption techniques with some similarities to the above five methods. These include but are not limited to block ciphers such as AES SHARK, Square, Anubis, Blowfish, KHAZAD, Manta, Hierocrypt, Kalyna, and Camellia, as well as stream ciphers such as MUGI.
13.4 Quality of Service (QoS)
Monitoring BAN applications is real time and life critical and requires a strict guarantee of QoS in terms of timeliness, reliability, security, power requirement, noise, and many other issues. Recently, there have been a number of proposals describing diverse approaches or frameworks to achieve QoS in BANs (i.e. for different layers or tiers and different protocols). The QoS also reflects the ability to set different priorities to different applications, users, or data flows.
These priorities directly depend on the BAN major characteristics. These characteristics include resource-constrained (mainly related to embedded computing and sensors, dynamic traffic patterns, network dynamics, data redundancy, heterogeneous traffic, criticality, as the patient data are life-related), dynamic pathloss, and environmental and user's context (which correspond to type of measurement, location, frequency range, number of channels, error rate that can be tolerated, etc.). Owing to all these characteristics, eventually there should be a measure of quality of information as the baseline for QoS quantification bearing in mind that there is no QoS support solution that can satisfy every application's requirements.
13.4.1 Quantification of QoS
As mentioned above, QoS is very application-specific and an inclusive measure for BAN QoS is difficult to achieve. However, the major requirements and the related metrics are discussed below [18].
13.4.1.1 Data Quality Metrics
The quality of data and the metrics for measuring them concern:
- Accuracy: which refers to how clear and accurate the data are measured, processed, transmitted, or presented.
- Reliability and believability: to ensure that the data collected by the sensors are trustable, meaningful, and can be analysed.
- Consistency: to ensure that the information collected over time remains consistent and, therefore, the overall system is stable.
- Ubiquitous access: the patient's information should be accessible to those authorised (doctors, caregivers, etc.) whenever necessary.
- Access security: which is discussed in other sections of this chapter and is a measure for QoS. It also includes data freshness, ensuring that the available data are the most recent ones.
- Accessibility of data: it is important to ensure that the data are accessible, particularly at critical times, with no, or only a limited, delay.
- Interpretability: those involved in a patient's care have to be able to find and understand the patient's data.
13.4.1.2 Network Quality Related Metrics
These metrics are related to the network function. The most popular metrics to measure the network quality are:
- Delay: queueing, processing, measurement, communication, and propagation delays for wireless BAN should be small in order to ensure freshness, timeliness, and correctness of the patient information.
- Delay jitter: it is important to measure and minimise the variation in delay, namely jitter, to ensure an in-order delivery of the data packets.
- Throughput: there is need to have a good match between the channel capacity for different segments of the communication channel to enable accommodating a high rate of information transmission.
- Packet error rate: most new systems can adapt to having low packet error rate, which is a measure of network quality when the system is prone to noise, multipath, and traffic.
- Energy efficiency: energy suppliers and harvesters such as batteries, solar cells, and motion-based harvesters have to be evaluated and remain at a consistent level throughout the measurement and the BAN functioning.
- Interoperability: the BAN system should be compatible with heterogeneous devices and applications without much change in the networking structure. Therefore, there won't be any need for changing, coding, or decoding the data to make them suitable for other networking systems.
In addition to the above, the devices within a BAN should be comfortable and easy to use, wearable, and safe.
A BAN, depending on the structure of its sensors, follows the hierarchy of computer networking layering system, though most of the design efforts are made for building and connecting the sensors. Most data quality measures such as accuracy, precision, completeness, consistency, and noise level are derived in relation to a physical layer and are dependent on the devices within this layer, and the technologies and standards of the BAN. Unlike other BAN parts, sensors are very different from one application to another and therefore a general-purpose BAN should be flexible enough to cater for such variabilities. The QoS is then evaluated based on the overall performance.
Nevertheless, for the network quality, the network standards and systems (Bluetooth, ZigBee, etc.) have their own QoS requirements. Most importantly, they use different frequency bands. Therefore, an acceptable QoS is often achieved by adhering to these standards and protocols.
On the other hand, data link layer, involving MAC protocols, has a crucial role in data framing, error detection, and recovery. As such, the MAC protocols become important. In particular, due to the clinical environment, through body or near-body communication channels, most of the QoS for BANs has to be arranged and conducted within the link layer rather than in the upper layers.
The last networking layer effective in QoS is the network layer. This is the layer where all the addressing actions and processing take place and therefore IP generation and identification followed by routing the packets from source to destination through several routers take place in this layer. Hence, developing an efficient and QoS-aware routing, including table look up by routers (address calculation) and forwarding in BANs, is a nontrivial task.
Some studies have shown that from a QoS perspective (requiring timeliness, reliability, and energy efficiency) multihop communications are preferable to single-hop ones. This is mainly to avoid shadowing caused by obstacles. Some examples of multihop routing can be found in [19, 20].
In [21] the authors focus on QoS-based routing protocols in BANs. They have classified the existing solutions into two main approaches: (i) multisink approach-based architecture and (ii) single-sink approach-based architecture. The latter category may be further divided into two subcategories to illustrate the different communication modes of the ensemble of solutions. The protocols are presented in a way to highlight many different approaches to QoS routing in WBANs. In order to assess the performance of QoS routing process in WBANs, a Markov chain has been used to evaluate the delivery process in terms of success/failure transmission probabilities under the probability of route rupture, followed by a comparison and analytical discussion of each category. They also studied the adaptability of the surveyed protocols related to the healthcare sector. The single-sink approach receives success in many aspects. However, the reliability and the transmission delay are deemed the most important requirement in WBANs scenarios. Therefore, this approach does not always provide the best results. In this context, the trend is to switch from a single-sink to a multisink approach with the main aim of further improving the reliability and transmission delay. In a general communication system multihop and single-hop transmission may be combined. The multihop approach may not be the optimal solution to guarantee some critical levels of QoS and may limit the required potential improvements. However, by combining these approaches the performance can be better tested for various QoS levels.
Finally, employing transmission control protocol (TCP) rather than user datagram protocol (UDP) in the transport layer allows a three-way hand-shaking in one hand and end-to-end acknowledgement (ACK) communication. This avoids both packet loss and transmission error up to a great extent. This, however, follows the standard transport layer design and is hardly changed by the BAN designers.
13.5 System Security
To guarantee secure communication in wireless BANs, Poon et al. [22] used physiological values (such as electrocardiogram, iris, and fingerprint) to design an authentication scheme. By measuring and comparing these values, a means of authentication can be achieved. To improve the performance, several improved schemes [23–25] based on physiological values have been proposed. However, the physiological value-based schemes [22–25] suffer from the DoS attack because there are differences between any two measured physiological signals recorded from the same person that may not be suitable enough for practical applications.
The received signal strength (RSS) in WBANs varies according to mobility and the channel state and variation. Therefore, channel-based authentication schemes [26–28] are also considered to implement mutual authentication in WBANs. Zeng et al. [26] used temporal RSS variation lists to deal with the identity-based attack. However, their scheme focuses on identification and cannot provide anonymity. Cai et al. [27] proposed a device pairing scheme using differential RSS involving at least two receiver antennas.
Several proximity-based authentication schemes [29–31] have been proposed for BAN applications. Varshavsky et al. [29] extended the Diffie–Hellman key exchange with the verification of device colocation and proposed an authentication method for WBANs. By monitoring the radio environment and generating a signature (including its RSS), the device could detect a similarity. With pairing devices transmitting and the trusted body-worn personal devices receiving, Kalamandeen et al. [30] proposed an authentication method by monitoring the transmissions. Later, Mathur et al. [31] developed a colocation-based pairing scheme by exploiting environmental signals. The main weakness of proximity-based authentication methods is that the devices have to be within half of the wavelength distance from each other, which can be restrictive for medical sensors deployed in a BAN. Shi et al. [32, 33] established that an off-body attacker has distinct RSS variation behaviour with an on-body sensor. Hence, they proposed a channel-based and a proximity-based authentication scheme for WBANs.
Unlike the physiological value-based schemes [22–25], the channel-based schemes [26–28], and the proximity-based schemes [29–31], the cryptography-based schemes require fewer restrictions (such as channel, distance, and location) from the applications' environments. Consequently, cryptography-based authentication schemes, as discussed in Section 13.3, have attracted increasing attention recently. These approaches may be implemented using the traditional public key cryptography (TPKC) [16, 34]. For example, Li et al. [35, 36] proposed a key management method and used the TPKC to implement mutual authentication. In the TPKC, the complex modular exponentiation operation is needed. However, the client device in WBANs has very limited computing capability and battery capacity. Therefore, the authentication schemes based on the TPKC are not suitable for WBAN applications. To avoid the modular exponentiation operation, several authentication schemes [37–39] based on the elliptic curve cryptography (ECC) have been proposed.
The concept of ECC was first introduced by Miller [40] and Koblitz [41] separately. Compared to TPKC, ECC is able to provide the same security with a much smaller key size [42]. Therefore, ECC is more suitable for environments with limited computing capabilities and battery capacity. However, a public key infrastructure is needed for the practical implementation of the ECC. With public key cryptography (PKC), every user has a certificate, generated by the certificate authority, to bind their identity and public key. The management of certificates becomes more tedious as the number of users grows. Therefore, the authentication schemes [37–39] based on ECC are not suitable for WBANs.
The idea of identity-based public key cryptography (ID-based PKC) was proposed by Shamir [43]. In the ID-based PKC, the key generation centre (KGC) uses its secret key to calculate the user's secret key according to their identity, and this identity plays the role of public key. Therefore, the ID-based PKC could address the problem of certificates management in the TCP. Yang and Chang [44] proposed an effective authentication scheme based on the ID-PKC. However, Yoon and Yoo [45] demonstrated that the scheme had serious security vulnerability by proposing an impersonation attack. Based on the ID-PKC, He et al. [46] used ECC to design a new provably secure authentication scheme. Unfortunately, Wang and Ma [47] found that the scheme [46] could not resist the reflection attack. They also pointed out that He et al.'s proposed method could not provide mutual authentication. Later, Islam and Biswas [48] used ECC to construct another authentication to solve security vulnerability in Yoon and Yoo's scheme. Unfortunately, Truong et al. [49] pointed out that this scheme could not resist the DoS attack. Although the above ID-based authentication schemes [44–49] perform better than previous schemes, they are not suitable for WBAN applications because they are designed for the client–server environment. To ensure secure communication in WBANs, Liu et al. [50] used the bilinear pairing defined on the elliptic curve to design a new certificateless signature scheme. Then, they presented a preliminary version authentication scheme for WBANs using their signature scheme. However, the scheme provides nontraceability because the user's identity is a constant value and the adversary could trace the client by observing the constant value. To enhance security, they also presented a security enhanced authentication method using their signature scheme and demonstrated that it could withstand various attacks.
However, in most of the practical applications, there is a privileged insider of the system, who is responsible for ensuring the device's normal functions. This insider can access the database of the system and modify the entries if necessary. Besides, a powerful adversary can actually penetrate into the system and modify the database. In other words, it is realistic and reasonable to assume that there is such an adversary who has the ability to modify the database of the system.
In the WBAN environment, the client and the application provider communicate wirelessly. Therefore, the authentication scheme for WBANs is susceptible to many attacks. To guarantee secure communication in WBANs, the authentication scheme should be able to withstand various attacks. In [51] a new anonymous authentication scheme for WBANs with provable security is proposed. The authors showed that the IEEE 802.15.6 is not secure against impersonation attacks. Then, they demonstrated that their own scheme not only overcomes the weakness in previous schemes but also reduces the computation burden for the clients. Finally, they argued that their system is secure and can meet the security requirements of BANs particularly for clinical applications.
13.6 Privacy
It is believed that, by establishing a secure system, network security as well as patient privacy are preserved. Although most of the techniques in security (such as network security and encryption) focus on data transmission, recently much attention has been paid towards data mining and archiving. Most importantly, cloud computing has become central to e-health. This requires an extra measure in securing patient privacy. The use of the cloud is becoming even more important nowadays due to the possibility of running very computationally costly algorithms, such as deep neural networks, over the cloud.
Vora et al. [52] have reviewed the privacy methods and looked at the privacy issues over the cloud as a low-cost data archiving and retrieval resource for e-health. To ensure that when two parties communicate a patient's data the traceability and identification of patients are achieved and the patients get access using anonymous credentials without revealing their identity or authentication credentials, an authentication scheme for e-health users using anonymous, adaptive authentication services has been proposed [52]. A level of confidentiality of the data has been achieved by adding a layer of anonymity. This layer follows the simple principle that the presence of a health record implies the retrieval of healthcare services for a particular condition, which violates patient privacy instead of maintaining patient confidentiality. Anonymous tickets work as the additional scheme of anonymity by offering consumption of the services, which allows the system not to depend on ‘trust’. The ‘trust’ concept demands a baseline of confidence for assuring the user's anonymity. The access control layer blocks any unauthorised access to patient data while complying with the tasks of providing the necessary measures to ensure security and privacy of patient data.
13.7 Conclusions
Extra measures need to be undertaken for patient data as well as other human-body-related information. In addition, to enable efficient healthcare and timely medication, the QoS for BANs has to be high enough to secure, preserve, and speed up the flow of information whenever and wherever necessary. This becomes even more critical where more patients are connected to the WSN through their wearable networks. Therefore, the design of new protocols and conventions may become necessary after the expansion of personalised medicine.
References
- 1 IEEE Std 802.15.6-2012 (2012). IEEE standard for local and metropolitan area networks – Part 15.6: Wireless body area networks. New York: IEEE.
- 2 Toorani, M. (2015) On vulnerabilities of the security association in the IEEE 802.15. 6 Standard. arXiv preprint arXiv:1501.02601.
- 3 Toorani, M. (2015). Cryptanalysis of two PAKE protocols for body area networks and smart environments. International Journal of Network Security 17 (5): 629–636.
- 4 He, D., Kumar, N., Wang, H. et al. (2018). A provably-secure cross-domain handshake scheme with symptoms matching for mobile healthcare social network. IEEE Transactions on Dependable and Secure Computing 15 (4): 633–645.
- 5 Meng, W., Li, W., Xiang, Y., and Choo, K.-K.R. (2017). A Bayesian inference-based detection mechanism to defend medical smartphone networks against insider attacks. Journal of Network and Computer Applications 78: 162–169.
- 6 Choo, K.-K.R. (2009). Secure Key Establishment (Advances in Information Security 41). New York: Springer.
- 7 Fang, H., Xu, L., Li, J., and Choo, K.-K.R. (2017). An adaptive trust-Stackelberg game model for security and energy efficiency in dynamic cognitive radio networks. Computer Communications 105: 124–132.
- 8 Lindstrom, J. (2007). Security challenges for wearable computing – a case study. In: Proceedings of 4th International Forum on Applied Wearable Computing, 1–8. IEEE.
- 9 Das, A.K., Wazid, M., Kumar, N. et al. (2018). Design of secure and lightweight authentication protocol for wearable devices environment. IEEE Journal of Biomedical and Health Informatics 22 (4): 1310–1322.
- 10 Dolev, D. and Yao, A. (1983). On the security of public key protocols. IEEE Transactions on Information Theory 29 (2): 198–208.
- 11 Wazid, M., Das, A.K., Kumar, N. et al. (2018). A novel authentication and key agreement scheme for implantable medical devices deployment. IEEE Journal of Biomedical and Health Informatics 22 (4): 1299–1309.
- 12 Liu, C.H. and Chung, Y.F. (2017). Secure user authentication scheme for wireless healthcare sensor networks. Computers & Electronic Engineering 59: 250–261.
- 13 Challa, S., Das, A.K., Odelu, V. et al. (2018). An efficient EEC based provably secure three-factor user authentication and key agreement protocol for wireless healthcare sensor networks. Computers & Electronic Engineering 69: 534–554.
- 14 Federal Information Processing Standards Publication, FIPS Pub 46-3, reaffirmed 25 October 1992. US Department of Commerce, National Institute of Standards and Technology.
- 15 Daemen, J. and Rijmen, V. (2002). The Design of Rijndael: AES – The Advanced Encryption Standard. Springer.
- 16 Rivest, R., Shamir, A., and Adleman, L. (1978). A method for obtaining digital signatures and public key cryptosystems. Communications of the ACM 21 (2): 120–126.
- 17 Schneier, B., Kelsey, J., Whiting, D., Wagner, D., Hall, C., and Ferguson, N. (1998) Twofish: A 128-Bit Block Cipher. in First Advanced Encryption Standard (AES) Conference. National Institute of Standards and Technology, 104.
- 18 Razzaque, M.A., Hira, M.T., and Dira, M. (2017). QoS in body area networks: a survey. ACM Transactions on Sensor Networks 13 (3) https://doi.org/10.1145/3085580.
- 19 Bangash, J.I., Khan, A.W., and Abdullah, A.H. (2015). Data-centric routing for intra wireless body sensor networks. Journal of Medical Systems 39 (9): 1–13.
- 20 Ababneh, N., Timmons, N., and Morrison, J. (2015). A cross-layer QoS-aware optimization protocol for guaranteed data streaming over wireless body area networks. Telecommunication Systems 58 (2): 179–191.
- 21 Yessad, N., Omar, M., Tari, A., and Bouabdallah, A. (2018). QoS-based routing in wireless body area networks: a survey and taxonomy. Computing 100 (3): 245–275.
- 22 Poon, C., Zhang, Y., and Bao, S. (2006). A novel biometrics method to secure wireless body area sensor networks for telemedicine and m-health. IEEE Communications Magazine 44 (4): 73–81.
- 23 Singh, K. and Muthukkumarasamy, V. (2007). Authenticated key establishment protocols for a home health care system. In: Proceedings of 3rd International Conference on Intelligent Sensor, Sensor Network and Information (ISSNIP'07), 353–358. ACM.
- 24 Venkatasubramanian, K. and Gupta, S. (2010). Physiological value-based efficient usable security solutions for body sensor networks. ACM Transactions on Sensor Networks 6 (4): 1–36.
- 25 Venkatasubramanian, K., Banerjee, A., and Gupta, S. (2010). PSKA: usable and secure key agreement scheme for body area networks. IEEE Transactions on Information Technology in Biomedicine 14 (1): 60–68.
- 26 Zeng, K., Govindan, K., and Mohapatra, P. (2010). Non-cryptographic authentication and identification in wireless networks [Security and Privacy in Emerging Wireless Networks]. IEEE Wireless Communications 17 (5): 56–62.
- 27 Cai, L., Zeng, K., Chen, H., and Mohapatra, P. (2011). Good neighbor: ad hoc pairing of nearby wireless devices by multiple antennas. In: Proceedings of the Network and Distributed System Security Symposium. San Diego, California (6–9 February 2011), 1–15. The Internet Society.
- 28 Shi, L., Yuan, J., Yu, S., and Li, M. (2013). ASK-BAN: authenticated secret key extraction utilizing channel characteristics for body area networks. In: Proceedings of the 6th ACM Conference on Security Privacy Wireless Mobile Networks, 155–166. ACM.
- 29 Varshavsky, A., Scannell, A., LaMarca, A., and De Lara, E. (2007). Amigo: proximity-based authentication of mobile devices. In: Proceedings of 9th International Conference on Ubiquitous Computating, 253–270. Berlin: Springer-Verlag.
- 30 Kalamandeen, A., Scannell, A., De Lara, E. et al. (2010). Ensemble: cooperative proximity-based authentication. In: Proceedings of the 8th International Conference on Mobile Systems, Applications, Services, 331–344. New York: ACM.
- 31 Mathur, S., Miller, R., Varshavsky, A. et al. (2011). Proximate: proximity-based secure pairing using ambient wireless signals. In: Proceedings of the 9th International Conference on Mobile Systems, Applications, and Services, 211–224. ACM.
- 32 Shi, L., Li, M., Yu, S., and Yuan, J. (2012). BANA: body area network authentication exploiting channel characteristics. In: Proceedings of the 5th ACM Conference Security and Privacy in Wireless Mobile Networks, 1–12. Tucson, AZ: ACM.
- 33 Shi, L., Li, M., Yu, S., and Yuan, J. (2013). BANA: body area network authentication exploiting channel characteristics. IEEE Journal on Selected Areas in Communications 31 (9): 1803–1816.
- 34 Elgamal, T. (1985). A public key cryptosystem and a signature protocol based on discrete logarithms. IEEE Transactions on Information Theory 31 (4): 469–472.
- 35 Li, M., Yu, S., Lou, W., and Ren, K. (2010). Group device pairing based secure sensor association and key management for body area networks. In: Proceedings IEEE INFOCOM, 1–9.
- 36 Li, M., Yu, S., Guttman, J. et al. (2013). Secure ad hoc trust initialization and key management in wireless body area networks. ACM Transactions on Sensor Networks 9 (2): 1–35.
- 37 Jiang, C., Li, B., and Xu, H. (2007). An efficient scheme for user authentication in wireless sensor networks. In: Proceedings of the 21st International Conference on Advanced Information Networking and Applications Workshops, 438–442. IEEE.
- 38 Guo, P., Wang, J., Li, B., and Lee, S. (2014). A variable threshold-value authentication architecture for wireless mesh networks. Journal of Internet Technology 15 (6): 929–936.
- 39 Shen, J., Tan, H., Wang, J. et al. (2015). A novel routing protocol providing good transmission reliability in underwater sensor networks. Journal of Internet Technology 16 (1): 171–178.
- 40 Miller, V. (1985). Use of elliptic curves in cryptography. In: Proceedings of Advance in Cryptology (CRYPTO'85), 417–426. Springer.
- 41 Koblitz, N. (1987). Elliptic curve cryptosystem. Mathematics of Computation 48: 203–209.
- 42 Hankerson, D., Menezes, A., and Vanstone, S. (2004). Guide to Elliptic Curve Cryptography. Berlin: Springer-Verlag.
- 43 Shamir, A. (1984). Identity based cryptosystems and signature schemes. In: Proceedings of Advance in Cryptology (CRYPTO'84), 47–53. Berlin: Springer-Verlag.
- 44 Yang, J. and Chang, C. (2009). An ID-based remote mutual authentication with key agreement scheme for mobile devices on elliptic curve crypto system. Computers & Security 28 (3–4): 138–143.
- 45 Yoon, E. and Yoo, K. (2009). Robust ID-based remote mutual authentication with key agreement protocol for mobile devices on ECC. In: Proceedings of the International Conference on Computational Science and Engineering, 633–640. Vancouver, Canada: IEEE.
- 46 He, D., Chen, J., and Hu, J. (2012). An ID-based client authentication with key agreement protocol for mobile client-server environment on ECC with provable security. Information Fusion 13 (3): 223–230.
- 47 Wang, D. and Ma, C. (2013). Cryptanalysis of a remote user authentication scheme for mobile client-server environment with provable security based on ECC. Information Fusion 41 (4): 498–503.
- 48 Islam, S. and Biswas, G. (2011). A more efficient and secure ID-based remote mutual authentication with key agreement scheme for mobile devices on elliptic curve cryptosystem. Journal of Systems and Software 84 (11): 1892–1898.
- 49 Truong, T., Tran, M., and Duong, A. (2012). Improvement of the more efficient and secure ID-based remote mutual authentication with key agreement scheme for mobile devices on ECC. In: Proceedings of 26th International Conference on Advanced Information Networking and Applications Workshops. Fukuoka, Japan (26–29 March 2012), 698–703. IEEE.
- 50 Liu, J., Zhang, Z., Chen, X., and Kwak, K. (2014). Certificateless remote anonymous authentication schemes for wireless body area networks. IEEE Transactions on Parallel and Distributed Systems 25 (2): 332–342.
- 51 He, D., Zeadally, S., Kumar, N., and Lee, J.-H. (2017). Anonymous authentication for wireless body area networks with provable security. IEEE Systems Journal 11 (4): 2590–2601.
- 52 Vora, J., DevMurari, P., Tanwar, S. et al. (2018). Blind signatures based secured E-healthcare system. In: International Conference on Computer, Information and Telecommunication Systems (CITS). Colmar, France (11–13 July 2018), 1–5. IEEE.
