In this chapter, we will learn what HTML injection and SQL injection are. We will also learn how we can prevent them. HTML injection and SQL injection are different. Therefore, we will learn them separately. In the first half of this chapter we will talk about HTML injection, and in the second part we will talk about SQL injection.
What Is HTML Injection?
In this book, we have already learned about many types of attacks. We have seen that a web application may have many types of vulnerabilities that attackers can exploit using different types of attack. We have also learned that good security testing is a part of prevention. As a penetration tester, your job will be to find those vulnerabilities for your clients in a web application.
Let me tell you about the one key feature of HTML injection, in the very beginning. HTML injection is rare. And it is not considered as severe as Cross-site Scripting or XXE attacks. However, it could be disruptive because it could deface a web site. It could change the appearance of the web site. It cannot penetrate through the system and steal the data. It cannot even destroy the database. However, this part of security testing should not be missed because, as I have mentioned earlier, it could deface a web site’s appearance and that may cost your client’s reputation. In this section we will see how we can test it. We will also learn how to prevent it.
We should be aware of another risk. The HTML injection attackers may try to steal a user’s data by posting a fake login form. We will find such vulnerabilities in our virtual lab.
HTML injection is a rendering attack.
HTML injection code is injected into a web page.
A web site executes that HTML injection code and renders its contents.
It is often considered as a subsection of Cross-site Scripting (XSS) attack, since, in some cases, it leads to XSS attack and could be more dangerous.
In the next step, we will start our virtual lab and open Kali Linux and the OWASP broken web application. For the first test, we need the intentionally vulnerable bWAPP application.
Finding HTML Injection Vulnerabilities

The bWAPP vulnerable web page
In this page I have entered my first name in the first text box, but in the second text box I’ve entered this simple HTML code:

In the lower part of the web page of the bWAPP application, HTML injection code has done the damage.

We can read any data of the bWAPP login form that passes through Burp Suite.
Here is the output that shows everything about the POST data, including the cookie and session ID.
Next, we will demonstrate how an HTML injection occurs and how a web page is ripped from top to bottom by getting defaced. Since this type of attack deals with the appearance of the web application, a single page, it may be considered as less risky. As far as the valuable data of the system or the user is concerned, it is indeed less risky; still, it should not be skipped in the penetration testing. Why? It could lead to a bigger attack. A vulnerable web page also shows the user’s session cookie, as we have just seen in the Burp Suite output (code 10.2). An attacker can use it and launch an XSS attack, which could be more dangerous.
Next, in the bWAPP application, we will see how stored HTML injection works. It is stored in the database and then it gets reflected. The basic difference between reflected and stored HTML injection deals with the risk involved. The stored HTML injection is riskier and could be more unsafe. You will see why in a moment.

We have entered an HTML injection code in the bWAPP application’s stored blog page.
Granted, it is quite simple and there is nothing new in it, but what happens if we enter a form to submit some credentials there? There lies a great danger. Let us see how it works.
We are going to enter this simple HTML form that will only take a username.

We have successfully posted a login form in the bWAPP application.

The Burp Suite reads the submitted data in thebWAPP application.
Here is the little output that Burp Suite captured.
There are lots of vulnerabilities we have already detected in the application. If we go to the source code, we’ll find that the HTML form has not been encoded properly.
If it was encoded properly, it would look like this:
Another thing is very important here. You can read the data in clear text on the URL. It should have been encrypted. Therefore, Burp Suite also reads the data quite easily and captures everything that has been submitted through the form.

The form is no longer visible in the stored blog page of the bWAPP application.
Exploiting HTML Injection
Sometimes a web application gives users a separate interface to change the color or fonts. The problem is, as a developer you need to use the form to accept the requests from the users. If your form data is not properly validated, encoded, or the HTML scripts are not stripped off, an attacker might take a chance to deface the web site.

HTML injection code is used while changing the color of the web page using the mutillidae application.

The HTML injection code has changed and defaced the web page.
This time the code is tricky, as we need to add special characters so that it will reflect the HTML injection effect with the color.

HTML injection in the blog page of the mutillidae application
This time we are going to add some moving text on the blog page. The code is like this:

Adding HTML injection in the blog page of the mutillidae application

Over the other texts, the “marquee” element moves the text.

The “marquee” text is disappearing over the other texts.
Preventing HTML Injection
I have said earlier, HTML injection is not as risky as SQL injection, which we will learn in the next section. However, a penetration tester should have a good knowledge of web structure, especially how the HTML language works.
The request and response cycle often depends on form inputs. Therefore, every input should be checked if it contains any script code or any HTML code. Hence, proper validation is the best solution. Every programming language has its stripping-tags functions. In any case, no code should contain any special characters or HTML brackets—<script></script>, <html></html>. The selection of checking functions depends on the programming language, which is the developer’s job. However, a penetration tester should point it out in the proof of concept.
In the proof of concept, a penetration tester also should mention these unavoidable steps that would prevent HTML injection. Include all types of escaping characters that I have mentioned earlier. This “escape” includes HTML, JavaScript, CSS, JSON, and URLs. The rule is never to trust user input. The HTML escape should be used before inserting user inputs into HTML element content. This rule is applied for attribute escaping in HTML common attributes.
Sanitizing HTML markup with a proper library and implementing content security policy are two important factors that should be maintained for HTML injection prevention.
What Is SQL Injection?
A web application usually makes queries to the database when it is requested to respond. An attacker may interfere with these queries if this web application is vulnerable. Therefore, we can say that SQL injection (SQLi) is a web security vulnerability that allows an attacker to interfere with the queries that an application makes to its database.
To prevent SQL injection, data segmentation by using routines such as stored procedures and user-defined functions are necessary. Otherwise, these vulnerabilities allow an attacker to view data that is not normally available for general users. This data may belong to other users. It may belong to the application data category. An application is supposed to access this data. However, these particular web security vulnerabilities open the floodgate, and an attacker may access them all through the back door. In many cases, an attacker may modify or delete the data, causing persistent changes to the application’s behavior.
SQL injection attacks may cause serious damage to the application when the attacker compromises the underlying server. The attacker may interfere with the back-end infrastructure by using SQL injection to perform a denial-of-service attack, which could be more damaging to the application.
We can test a web application in our virtual lab to see whether it has SQL injection vulnerabilities; to do that, we need the intentionally vulnerable web application mutillidae and Burp Suite.
Bypassing Authentication by SQL Injection

User info (SQL) page in mutillidae
We need to register here as a new user, and I have created a new user account. The user name is “sanjib.” The password is “123456,” and the signature is “I am Sanjib” (Figure 10-15).

Creating a new user account in mutillidae
As a general user, I am not supposed to view other user accounts’ details and I should not be able to log in as other users, say as admin. If the database is protected, and the web application has no vulnerabilities, a user’s movement is restricted. This is because the SQL query selects only one user when they are logged in. Let us see the code:
Let us study this code minutely. It is a logical statement. The user name and the password should match. It is only true when both statements are true. However, this is an injection point. We can write one statement like this in the input field of the form:
This means we close the single quote of the user name and then pass two hyphens, meaning the rest of the SQL statement is commented out. The vulnerable web application will read this statement as the following:
In such a case, it does not require the password anymore. When the rest is commented out, it conveys the message that the rest is not required. In that case, it gives the accounts detail of that particular user. Now we can build up our query in a manner where the statement is true all the time.
Our query will look like this:

Getting all the records by SQL injection
Because the application has vulnerabilities, we get all the records of the user accounts due to this malicious SQL injection.
The output is shortened for brevity. We have 23 records altogether.
A statement that is true by necessity or by its logical form is known as a tautology. In SQL injection, the tautology plays a vital role. Let’s return to our original starting point:
Here the word SELECT is known as the projection or the subject of the statement. It selects a field from a table or a group of tables joined together by a union. The word WHERE stands for the predicate of the statement. In the predicate part, we need a series of conditions, because after that it checks whether the statement is true. When we write, SELECT * FROM accounts WHERE username='sanjib OR 1=1 -- ;, it checks the condition at runtime and the query is formed.

MySQL Boolean literal page
Here SELECT TRUE OR true equals 1, always. The constants, true and false , are always evaluated as 1 and 0. Therefore, how about this query?
In the input field we can put this value:

The user logged in as admin and sees the accounts record.
How can we make that possible? Well, if we examine the statement minutely, we can get our answer. We don’t need tautology here. Rather, we should concentrate on the user name. In many applications, the administrator uses the name admin as the user name. We can target that, and in the input box we can place this statement:
In an application full of vulnerabilities, the query is formed like this:

Logged in as admin
Discovering the Database
One of the key features of SQL injection involves knowledge of the database. You need to know which database is working as the back-end infrastructure. You cannot use the same fuzzing of the MySQL database in Microsoft SQL Server. We can use the Burp Suite tools to discover that information.

The HTTP history in Burp Suite
We have kept the intercept on in our Burp Suite tool and get the HTTP history as the following output:
Watch the last line; we have typed in the random string sadldfjfkg as our user name and tried to log in. The password field was empty.
Now select the random string and add the special fuzzing character by clicking the “Add§” button on the right-hand side. We need to configure our Payloads position at that point so that we can start the attack from there.

Checking the Payloads position
Click the Payloads button and add all payloads that we will need to inject. We have seen before how to add payloads individually: just keep these characters /, ', "", %.

Simple String Grep – Match in Payloads options
This will enable us to get all the errors and syntax-errors, from where we will get an idea about the database used in the application. Here we added the escape sequences individually, assuming that the mutillidae application has used MySQL database.
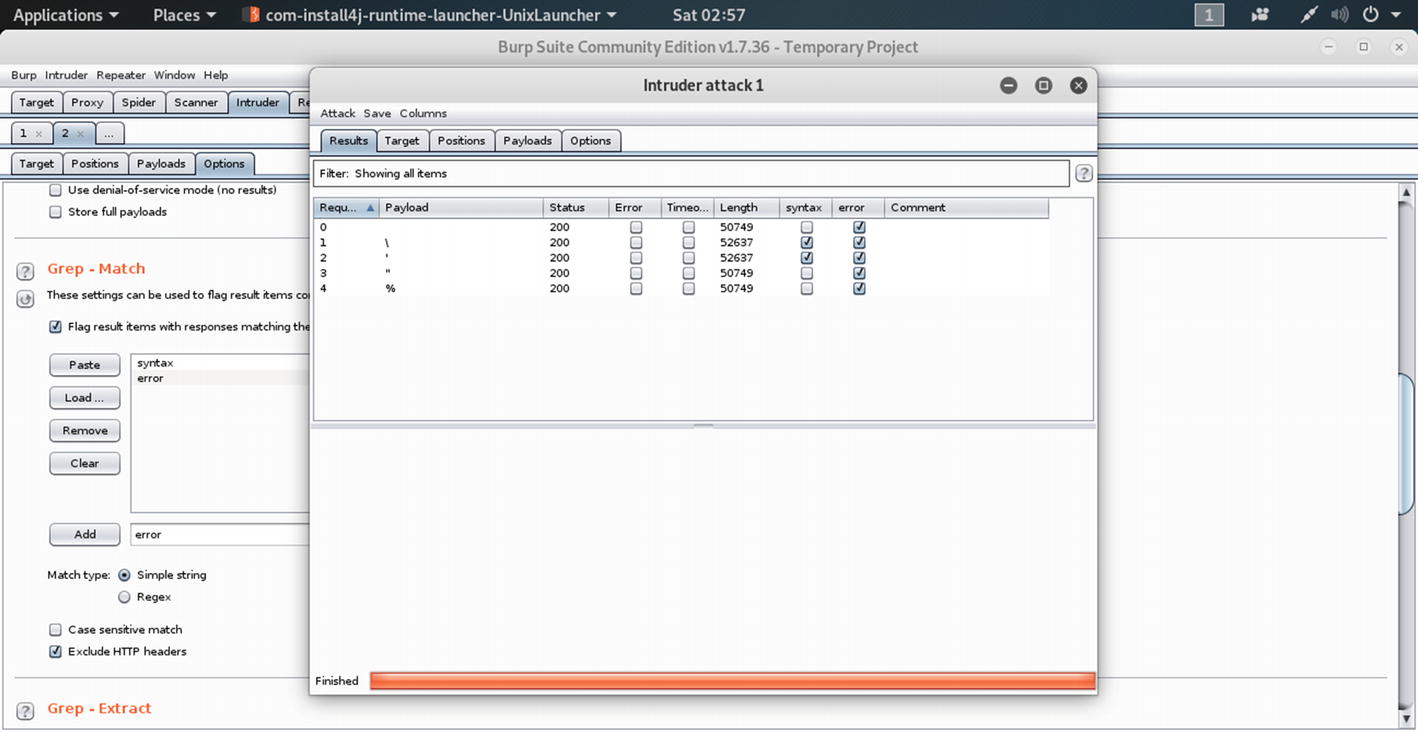
Highlighting the Intruder attacks in Burp Suite
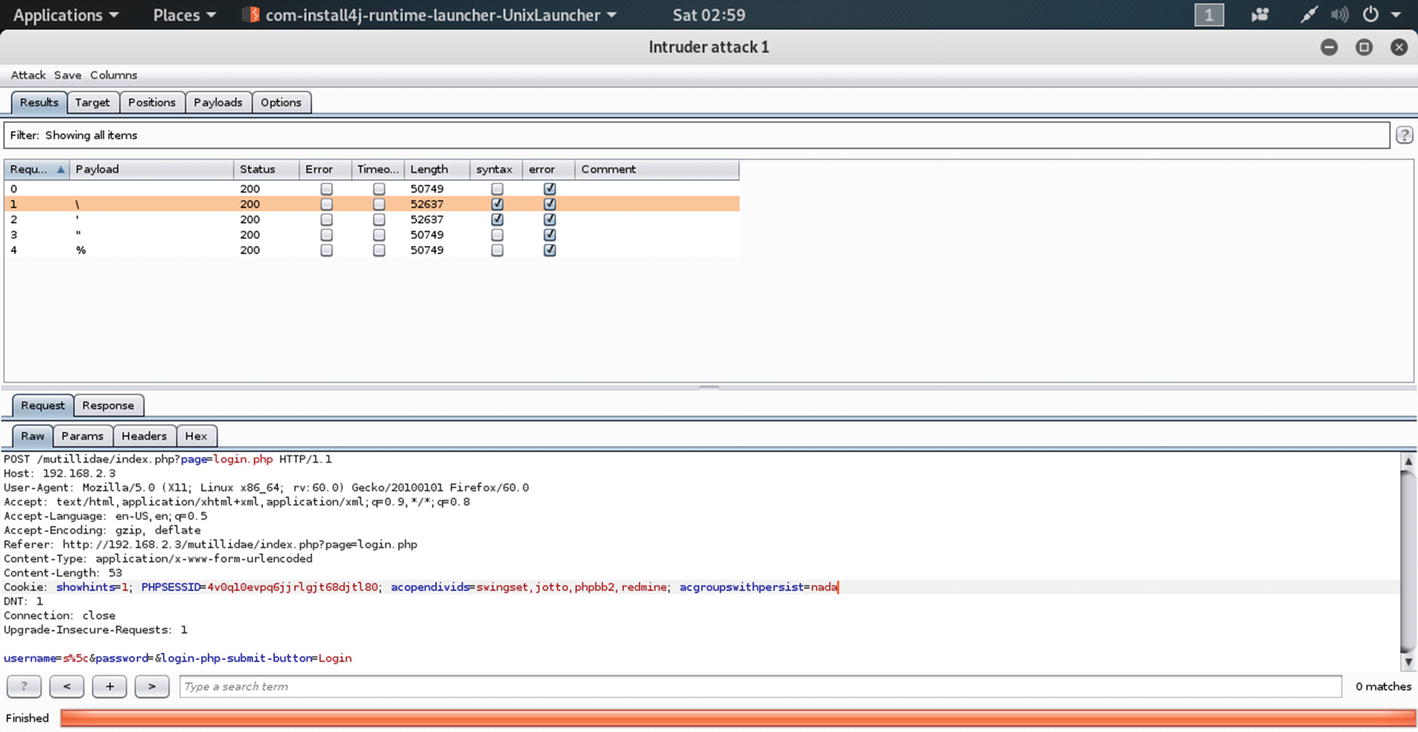
The Request highlighting the syntax-errors
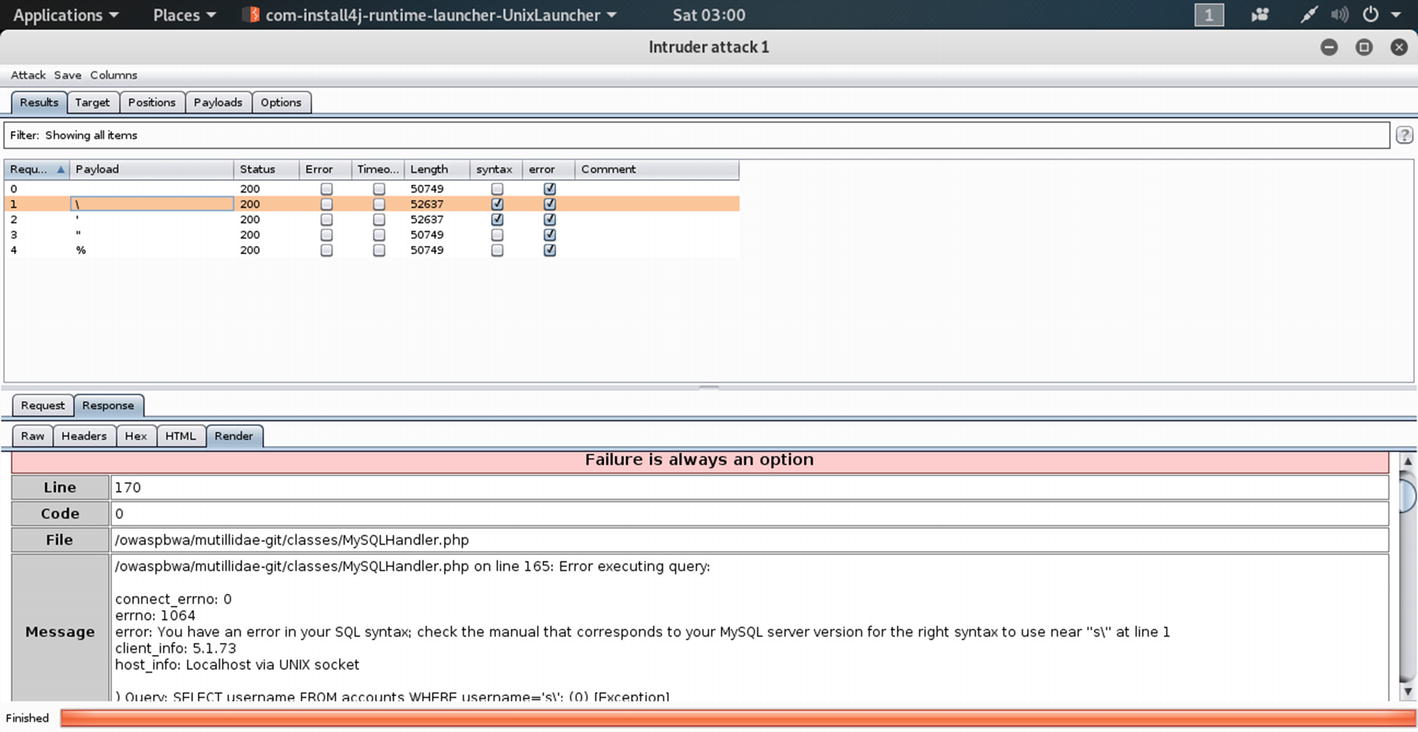
The message about the database in the Response section of Intruder
In this section, I have tried to give you an idea of how SQL injection works, by describing some common examples. I have also tried to explain the basic logical statements and tautology on which the SQL injection attacks are mainly based. There are a few good free resources available over the Internet where you can get more ideas about SQL injection. In Appendix, I will talk about other bug hunting tools and free resources that may help you.
