As a developer, you will undoubtedly work with sensitive information such as passwords. How you handle this information during development is very important. In the past, I have received copies of a client's live database to use for testing. This does pose a very real security risk for your client.
Often, we keep settings in a web.config file (when working with web applications). For this example, though, I will be demonstrating a console application that uses an App.config file. The same logic can be applied to a web.config file too.
Creating a console application is the quickest way to demonstrate this recipe. If, however, you want to follow along using a web application (and securing a web.config file), you can do so.
- In the console application, locate the
App.configfile. This is the file that contains the sensitive data:
- If you open the
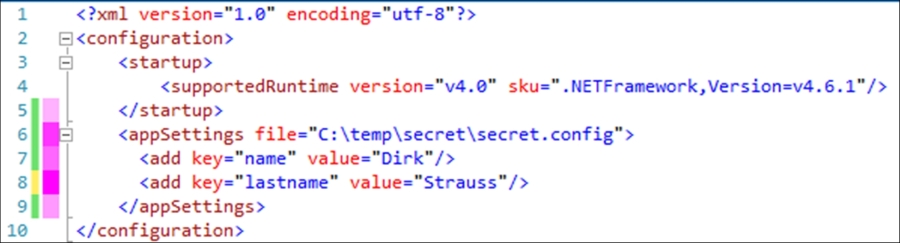
App.configfile, you will see that within theappSettingstag there is a key added calledSecret. This information should probably not be in theApp.configto start off with. The problem here is that it might be checked into your source control. Imagine that on GitHub?<?xml version="1.0" encoding="utf-8"?> <configuration> <startup> <supportedRuntime version="v4.0" sku=".NETFramework,Version=v4.6.1"/> </startup> <appSettings> <add key="name" value="Dirk"/> <add key="lastname" value="Strauss"/> <add key="Secret" value="letMeIn"/> </appSettings> </configuration> - To overcome this vulnerability, we need to move the sensitive data out of the
App.configfile into another file. To do this, we specify a path to a file that will contain the sensitive data we want to remove from theApp.configfile:<appSettings file="C: empsecretsecret.config">
Note
You might be wondering, why not simply just encrypt the information? Well, that is a given really. The reason this value is in plain text is just to demonstrate a concept here. You would probably encrypt this value anyway in a real-world situation. You would not, however, want this sensitive information sitting on a server in a code repository somewhere, even if it is encrypted. Be safe, move it out of your solution.
- When you have added the path to the secure file, remove the key containing the sensitive information:
- Navigate to the path you specified in the
App.configfile property. Create yoursecret.configfile and open it up for editing:
- Inside this file, repeat the
appSettingssection and add theSecretkey to it. What happens now is that when your console application runs, it reads theappSettingssection in your solution and finds the reference to the secret file. It then looks for the secret file and merges it with theApp.configin your solution: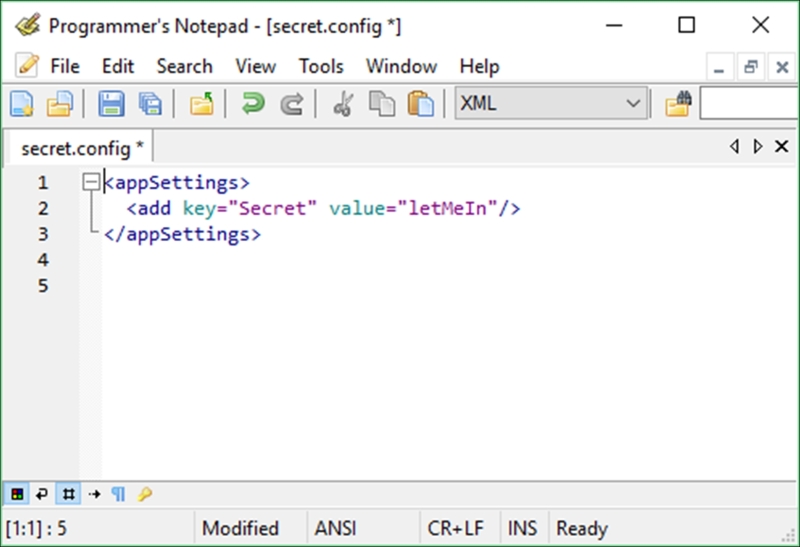
- To see that this merge works, add a reference to your console application:
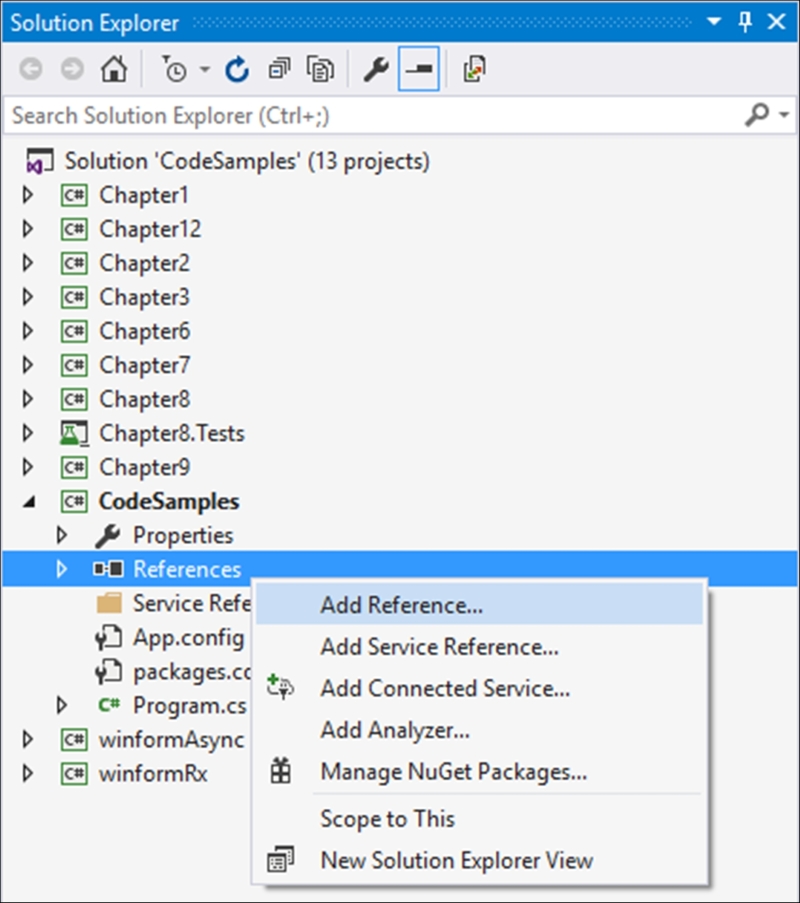
- Search for and add
System.Configurationto your references: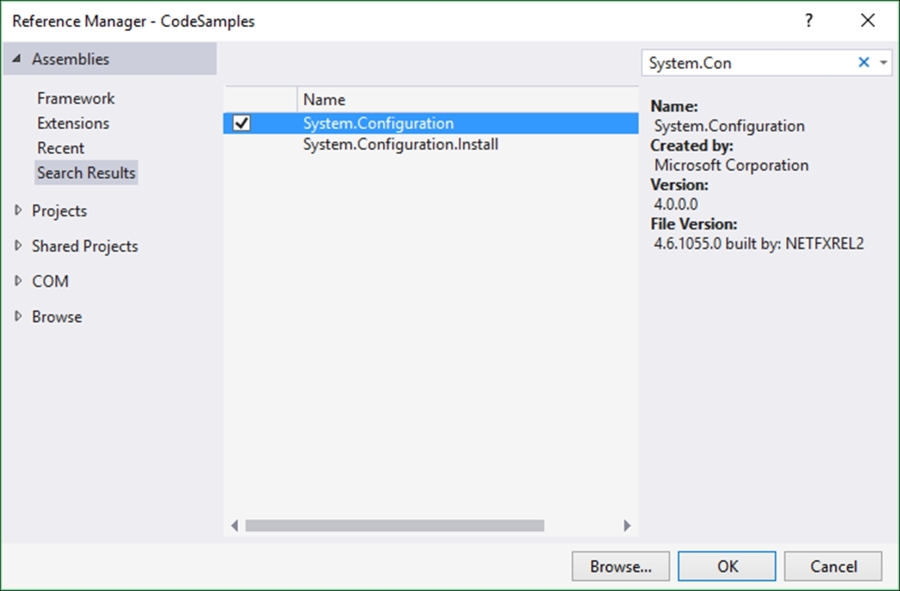
- When you have added the reference, your solution references should look something like this:
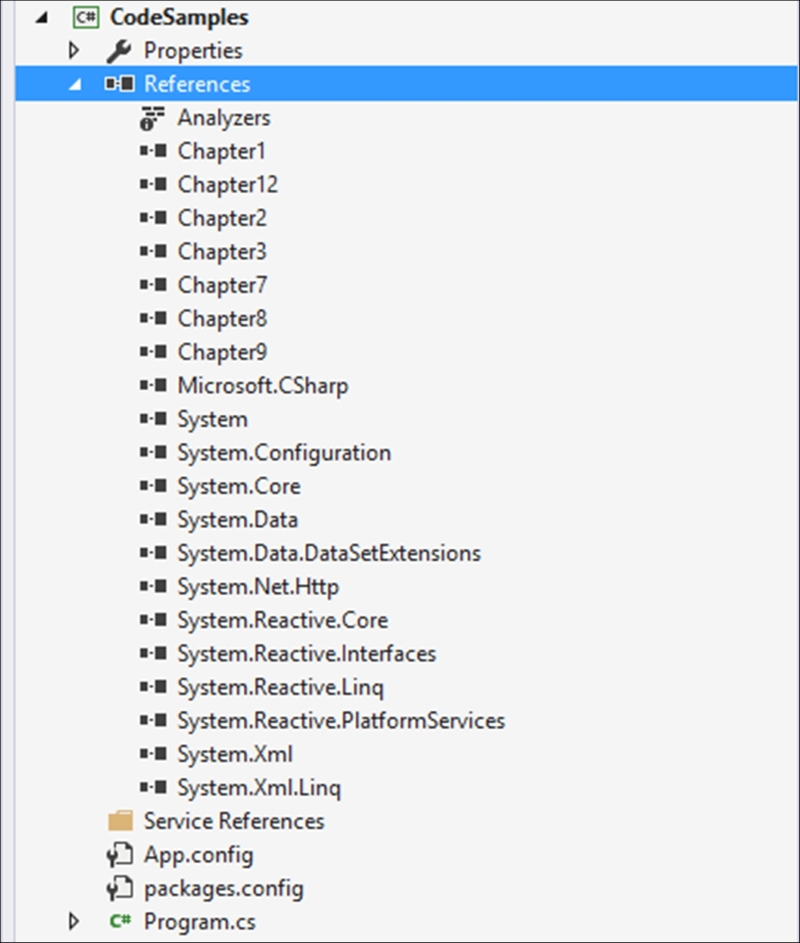
- To the top of your
Program.csfile, add the followingusingstatement:using System.Configuration;
- Add the following code to read the
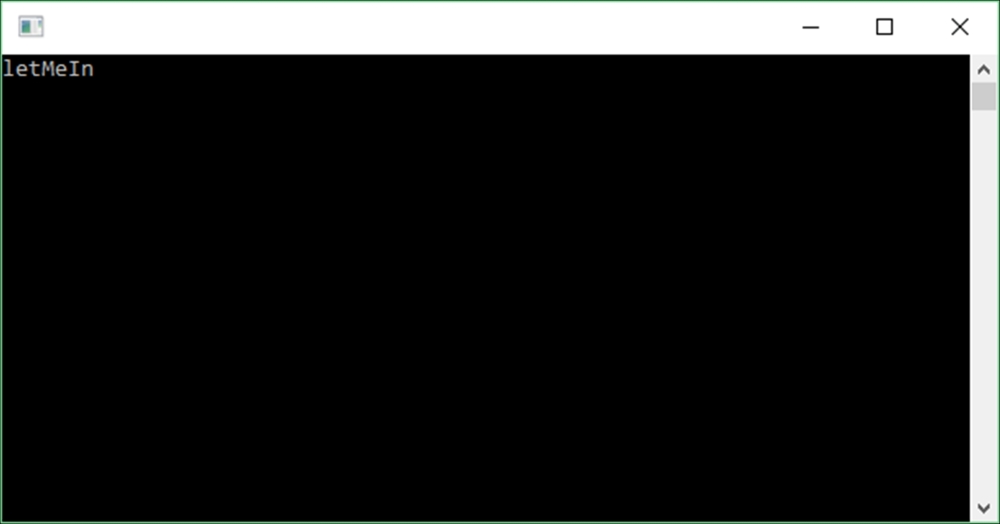
Secretkey setting from yourApp.configfile. Only this time, it will read the merged file, which is made up of yourApp.configand yoursecret.configfile:string sSecret = ConfigurationManager.AppSettings["Secret"]; Console.WriteLine(sSecret); Console.ReadLine();
- Run your console application and you will see that the sensitive data has been read from the
secret.configfile, which was merged with theApp.configfile at runtime: