Chapter 3
Security Operations Scenarios
The CASP+ exam does enjoy scenario questions. Regarding threat actors and mitigation strategies in security operations, this chapter discusses all the topics you can expect to see in those scenario-formatted questions. Additional scenario topics are covered in subsequent chapters in this book. However, this chapter covers those topics revolving around security operations. You should then identify and analyze the vulnerabilities left open to those threats. And lastly in this chapter, you will understand the risk of those vulnerabilities being exploited and how to respond to them.
Threat Management
For the CASP+ exam you'll be expected to be familiar with the types of intelligence and how each factors into threat management. Not unlike with conventional warfare, cyber intelligence is important for knowing what threatens you, identifying your weaknesses before your threat does, managing all risk, and being ready to respond to whatever attacks first. This includes understanding the concepts of threat hunting and threat emulation.
Types of Intelligence
The types of intelligence can be categorized in three ways. They vary in how their value relates to the threats.
- Operational Operational intelligence strives to keep business going as planned. You are looking to identify the trends and systemic risks that threaten on an ongoing basis. Operational intelligence includes actively threat hunting for the malicious in your environment and working toward understanding those threats the best you can, before they create an incident, as well as using threat emulation to take new information about attacks and convert it into usable signatures. This gives an organization the ability to block those threats before they have an opportunity to do damage within an enterprise ecosystem.
- Tactical Tactical intelligence represents the “here and now” of needed information. You are looking to understand a specific discovery, perhaps a threat found in the course of incident response. For example, the security operations center (SOC) may have identified a common piece of commodity malware in your environment. Commodity malware is publicly available code that can be purchased but is not customized and used by many threat actors. If this type of threat is found within the organization, a high degree of tactical intelligence will help quickly identify and navigate the response to it.
- Strategic Strategic threat intelligence asks questions while looking further out. Who will be the threat the organization will soon face or can expect to face? What sort of targeted attacks can your industry or the organization come to expect? For example, an industrial espionage attack may target your organization because of specific value or product.
Threat Hunting
The concept of threat hunting means to search for and identify security threats and problems that have yet to be discovered in the environment. The act of threat hunting usually involves going well beyond the typical security technologies and safeguards. The potential reward is preferable to some undiscovered malware. The prize to be sought would be the capable insider threat or shadow IT which, until discovered, had been “flying under the radar.” Other potential discoveries can be bad configurations or outdated processes.
Remember that threat hunting is proactive, unlike most security appliances and technologies. Too often, security devices respond to a threat based on a matching signature. Threat hunting, on the other hand, is a practice or exercise that requires perseverance and creativity. Since human threats, especially ones already established on the inside, will be careful not to reveal their motives or reason, hunt teaming requires patience and vigilance to flush out the threats.
Threat Emulation
The value in carefully analyzing a threat is more than just research. When you can imitate how a threat works and interacts with the vulnerability, you understand more how to mitigate the risk of that threat. Threat emulation is the approach and activity of better understanding a threat for the sake of ultimately minimizing it.
Actor Types
To understand how and why various threats affect your operations, it's first necessary to cover the types of threat actors that threaten your operations. The FBI characterizes threat actors into three broad categories: organized crime, state-sponsored attacker, and cyberterrorist. Of these three groups, the FBI describes organized crime as the group we see most heavily involved in cybercrime today. A large portion of this activity originates from Eastern Europe and Russia. Originating from Russia or former Soviet states has been some of the most notorious malware that has targeted global consumers, banks, and retailers over the past few years: LoJax, Bad Rabbit, and NotPetya, to name just a few. Many of these organized crime groups have more than ample resources and skills to be a global threat. They have the sophistication, time, and money to leverage vulnerabilities to create new threats and new exploits (zero-day).
In 2021, Colonial Pipeline, an American oil pipeline system that originates in Houston, Texas, and carries gasoline and jet fuel mainly to the southeastern United States, suffered a ransomware cyberattack that impacted computerized equipment managing the pipeline. Also in 2021, work stopped at several U.S. meat processing plants after the world's largest meat producer was hit with a major cyberattack.
With all the confusion about the names of threat actors, the same might be said for the good guys. One term to describe an individual who tests the security of a network, application, or system is ethical hacker. An ethical hacker is an individual who performs authorized security tests and other vulnerability assessment activities to help organizations secure their infrastructures. Hackers are typically divided into different categories, which can include the following:
- Authorized These individuals perform ethical hacking to help secure companies and organizations. They work within the boundaries of the law and with the permission of the organization.
- Unauthorized These individuals are criminal attackers and may be driven by greed, revenge, or the challenge of breaking into a company.
- Semi-authorized
These individuals typically follow the law but sometimes venture over to the darker side of unauthorized hacking. You could think of them as Luke Skywalker from Star Wars. They cannot decide if they will join the Force or go with the Dark Side.
Criminal hacking has changed over the years, as has the source of emerging threats. Most of the hacking culture today grew out of the phone phreaking activities of the 1960s. These individuals hacked telecommunication and PBX systems to explore their capabilities and make free phone calls. Their activities included physical theft, stolen calling cards, access to telecommunication services, and the reprogramming of telecommunications equipment.
A wide range of threat actors exists. Some are individuals, while others are part of larger organizations. Each has its own goals and approaches. Some of the most common types of threat actors include the following:
- Nation-State Hackers and Cyberterrorists These individuals have some form of backing from a country or state and are typically focused on gathering intelligence, stealing data, and possessing advanced technology and knowledge that another nation or country may have. Several examples of alleged nation-state hacking are GhostNet, Stuxnet, and Shady RAT.
It is common for well-financed nation-state groups to place advanced persistent threats (APTs) in a compromised system. The APT serves to maintain accessibility to the “pwned” machine. Because APT malware can be advanced, the threat may stay even if the system administrators attempt to contain and eradicate it.
This category includes those individuals or groups of individuals seeking to engage in recruitment for the purpose of attacking and/or compromising critical infrastructures and industrial control systems (ICSs), such as nuclear power plants, power generation stations, and water treatment plants.
- Disgruntled Employees Disgruntled employees pose an insider threat as individuals who are upset with their current or former employers. These individuals may or may not have advanced hacking skills, but they do have access to and knowledge of the target that an outsider may not have. Proper human resource processes and good operational controls can go a long way toward preventing problems.
The insider threat is especially dangerous, since the insider already holds considerable trust with the organization. The insider knows internal policies, is familiar with the organizational structure, has awareness of business processes, and, most of all, has network access as a trusted employee.
- Organized Crime Today, a large portion of hacking activity is driven by monetary needs, and this type of threat continues to grow as the rewards get larger. These attackers are typically organized crime groups targeting banks, financial institutions, companies, and end users. Their goal is usually to obtain credit card numbers, personal information, steal identities, and perform other activities related to stealing money.
Further, given the strong drive for financial gain, the organized and well-funded hacker will persevere, no matter the time involved. Resources such as time and money are not in short supply!
- Competitors Don't forget that any company's intellectual property (IP) is regarded as the prime target for the competition.
- Script Kiddies This derogatory term is used to describe people who use hacking techniques but have limited skills. Often such attackers rely almost entirely on automated tools they download from the Internet. These attackers often have little knowledge of how their attacks actually work, and they are simply seeking out convenient targets of opportunity.
- Hacktivists These are individuals who hack for a cause. Groups such as Anonymous and LulzSec have been closely identified with this movement. Figure 3.1 shows the LulzSec Twitter page.
FIGURE 3.1 LulzSec
- Resources If I ask what sets bad actors apart from each other, the first answer is likely their skill set. Yes, having capability and perseverance is a big discriminator. Let's not forget how important things such as time and money are.
Most bad actors are doing their day jobs in addition to poking and probing at vulnerabilities. But what about those nation-state hackers and the for-hire or criminal hackers? Threatening your environment is their day job. When their reward, in all respects, is successfully ruining your day, you know they are highly motivated to do so.
-
Supply Chain Access Often the easier way to hurt an organization is not to hit them directly. Instead, a hacker may focus on supply chain access, opting to cripple or disrupt a different organization on which the target relies. This affects the company's reputation more than their own infrastructure. There is little in the way of technical controls for mitigating supply chain attacks. Mitigations could include the following:
- Knowing suppliers and looking upstream as well as downstream
- Conducting a risk assessment
- Utilizing third-party testing
- Regularly scanning and patching all vulnerable systems
- Using strong passwords
- Ensuring your staff has set up multifactor authentication everywhere possible
Intelligence Collection Methods
How is data collected? Where does it come from? When it comes to collecting intelligence regarding threat management, a range of tools and techniques exist, but they generally can be divided into two broad categories: open-source intelligence (OSINT) and human intelligence (HUMINT), which is related to social engineering.
Open-Source Intelligence
The open-source intelligence (OSINT) method allows required information to be delivered as highly relevant research results that can easily be validated and transformed into high-quality intelligence. The idea behind gathering OSINT originated in the military, but it was found to be of great value in the civilian domain as well. OSINT is broadly defined as using established intelligence tradecraft on open sources of information. Open sources range from foreign language translation to exploitation/analysis of multiple, independent, publicly available sources of information. OSINT sources include commercial, scientific, and technical databases; symposium proceedings; published strategies and doctrine; think-tank publications; patent information; and other open-source documents available to the general public. A variety of exploitation techniques are practiced in OSINT, including monitoring social media and gathering contact information from sites such as WHOIS, search engines, and other records.
It's important to note that information being readily available does not make that information free to use as we wish. Information accessibility has value and perhaps a cost associated with producing it. Information created by commercial research or effort can label that information as proprietary and protected. In threat research it is important to respect the difference between available and free to reuse. For example, threat intelligence research firms publish intelligence feeds to disseminate their findings. These intelligence feeds are highly valuable partly because of the vast effort behind making them.
Social Media
Social media provides a treasure trove of open-source information for attackers. Visiting the personal social pages for an employee will yield their likes, passions, political leanings, and maybe even their thoughts about their employers. The opportunity for a social engineer to exploit the social media sites of a potential target is not just theory, as we all know from current events at the time of this writing.
Deep Web
The Deep Web has become popularized and mysterious to people who haven't gone there and woefully under-indexed for those who try. (That was a joke.) The Deep Web is a part of the Internet that is not indexed or searchable by conventional search engines. It can be treated as another source of information. However, like with many sources, enjoy it with a bit of skepticism. The Deep Web is different from the Dark Web, even though the words get used interchangeably. The Dark Web is also not indexed, but users of the Dark Web focus on anonymity and have access to illegal activities and information. It is in these illegal markets where you can purchase commodity malware.
WHOIS
If an attacker wants to learn more about the organization's technical contact or registration information about their domain, the site that provides both is WHOIS.
Routing Tables
Unlike social media rich with personal information, or record-keeping sites like WHOIS, open-source intelligence can also be more obscure but still empirical and highly valuable. Routing tables are found on any device aware of the network outside of the subnet, which can be any system, router, or layer 3 switch. The routing table is the set of “rules” or paths between routes. Obviously, this is valuable to anyone looking to learn about what network subnets or spaces a system has been or could be talking to.
DNS Records
Another publicly available repository of information about some of the organization's infrastructure is its DNS records. Through DNS records, an attacker can learn much about a company's domain, subdomains, and the blocks of IP addresses or services used by that system. Mitigation can include the following:
- Auditing DNS zones
- Keeping DNS servers patched and current
- Hiding the BIND version
- Restricting zone transfers
- Disabling DNS recursion to prevent DNS poisoning attacks
- Using isolated DNS servers
- Using a DDOS mitigation provider
- Using two-factor authentication
Human Intelligence and Social Engineering
No technology can build or betray confidentiality and trust like human interaction. If you agree with that, consider speaking with a trained professional. But seriously, humans do thrive on interaction and relationships. This can be for good or bad. For our purposes, we're talking about human interaction used for the sake of gathering information.
It's commonly said that the second-oldest profession is spying. Human intelligence (HUMINT) is the personal side of spying or collecting intelligence. While OSINT might involve dumpster diving and scouring social media, HUMINT involves building a genuine rapport and leveraging it for information or access.
HUMINT can be considered a portion of social engineering. Social engineering encompasses a spectrum of methods and devices, such as email, texts, and phone calls.
Speaking personally, social engineering is part of my job. More specifically, when a client asks my employer to perform social engineering, I am sent off for an onsite engagement. Phishing and other online social engineering gets done between myself and others.
My onsite work does not include breaking in after hours with specialized tools. I respect professionals who have that skill and practice. One of the penetration testers on my team is skillful at lock picking, but for now, such tools are outside our rules of engagement. We must stick to social engineering. Plus, unlike a door-opening tool, real people give you access and point you right where you need to be.
Instead, I gain access only by interacting with an employee. Naturally, that insider is not aware of my goal. In social engineering, the engagement is based on deceit, and time is needed to build a rapport. I do get in, but people do take more time than tools. And perhaps most importantly, I am ever careful to not put someone in a position of being embarrassed or being left feeling more vulnerable afterward. The goal is security awareness and team education. In almost every case, I am not forced to reveal the identity or insider who allowed me in.
Frameworks
This section discusses the frameworks promoted today regarding threat management and how attacks happen. You should familiarize yourself with the frameworks and related standard nomenclature.
MITRE Adversarial Tactics, Techniques and Common Knowledge
The MITRE Adversarial Tactics, Techniques and Common Knowledge (ATT&CK) framework is what happens when you take the brains of a well-schooled, methodical attacker and spray them on a highly organized matrix. Not a delicate picture, but neither is the ATT&CK matrix.
MITRE is the not-for-profit research organization that brought you the Common Vulnerabilities and Exposures (CVE), the leader in ranking and categorizing vulnerabilities. MITRE's ATT&CK framework by its full name is Adversarial Tactics, Techniques and Common Knowledge. So, yes, this means taking the brains of an attacker and categorizing them into methods and flow.
The MITRE ATT&CK Matrix for Enterprise is organized to identify top-level tactics that include hundreds of techniques that attackers use. In examining the ATT&CK Matrix, you are probably identifying techniques that seem to relate to only one operating system. Meanwhile, the overall structure and the majority of tactics and techniques can apply to any platform. The ATT&CK Matrix for Enterprise accommodates all OSs, but MITRE does have matrices specific to Windows, Linux, macOS, and mobile systems.
Let's take a quick look at the top-level tactics from the ATT&CK framework. Later, with other frameworks, you can compare and contrast the length and flow. The tactics from the MITRE ATT&CK Matrix for Enterprise include the following:
- Reconnaissance
- Resource development
- Initial access
- Execution
- Persistence
- Privilege escalation
- Defense evasion
- Credential access
- Discovery
- Lateral movement
- Collection
- Command and control
- Exfiltration
- Impact
ATT&CK for Industrial Control Systems
There is an ATT&CK matrix tailored for industrial control systems (ICSs). Recall that ICS refers to operational technology systems that monitor and control industrial operations, such as wastewater and other utilities, manufacturing, and so on. This also applies to supervisory control and data acquisition (SCADA) systems.
There is something important to understand here about ATT&CK for ICS. The ICS matrix does not seek to replace the more generic “IT” version of ATT&CK. Obviously, industry control systems also include the enterprise IT, so a replacement would just result in 90 percent duplication. The ATT&CK for ICS spotlights the attack techniques and tactics particular to the industry control components.
The MITRE ATT&CK for ICS tactics include the following:
- Collection
- Command and control
- Discovery
- Evasion
- Execution
- Impact
- Impair process control
- Inhibit response function
- Initial access
- Lateral movement
- Persistence
There is some overlap but even at the highest level you notice the shifted focus. Dig into the techniques, and you'll see how ATT&CK for ICS is quite different from IT systems. A good resource for exploring this is collaborate.mitre.org/attackics/index.php/Main_Page.
Cyber Kill Chain
The Cyber Kill Chain is similar to MITRE's ATT&CK framework, since both describe how an attacker goes about compromising a system or network. A noticeable difference is that the Cyber Kill Chain is shorter and more concise. Another difference is the ATT&CK framework is fixed in terms of naming those top-level tactics. The Cyber Kill Chain can be found in a few different iterations. Lockheed Martin started it, evolving it from a military model. Now Gartner has its version, which is not too different but Gartner claims it as its own. For the CASP+ exam, it's best if you remember the terms of the Lockheed Martin model. The Cyber Kill Chain tactics follow these steps:
- Reconnaissance
- Weaponization
- Delivery
- Exploitation
- Installation
- Command & control (C2)
- Actions on objectives
To learn more about the Cyber Kill Chain, see lockheedmartin.com/en-us/capabilities/cyber/cyber-kill-chain.html.
Diamond Model of Intrusion Analysis
An altogether different concept is the Diamond Model of Intrusion Analysis, which is presented as a simple diamond shape. Each corner of the diamond is labeled like this:
- Left corner: Infrastructure
- Top corner: Adversary
- Right corner: Capability
- Bottom corner: Victim
Far from the linear progression of steps of the other two models, the Diamond Model of Intrusion Analysis aims to help threat intelligence analysts organize large amounts of data. Every incident connects these labels to insight and knowledge as well as exposes knowledge gaps. Using this model, an intelligence analyst can show with precision how an adversary uses their capability within an infrastructure against the victim.
The CASP+ exam does not require that you have experience using the model, or even know how to work with it. However, it's a good idea to know at least how to label it. I suggest you watch a 10-minute YouTube video called Diamond Model of Intrusion Analysis: An Overview (youtube.com/watch?v=3PoQLOJr5WI).
Indicators of Compromise
Indicators of compromise (IoCs) are evidence that a security incident occurred and more investigation is needed to reveal the consequences. IoCs can be subtle or blatantly obvious. Using a house as an analogy, an IoC might be as subtle as fingerprints on the window or as obvious as broken glass on the floor. In the security space, IoCs can come from a variety of sources. They range from log entries, alerts and notifications, or detecting activity or traffic that seems out of the ordinary. In any event, IoCs can become foreshadowing for the incident response team.
Reading the Logs
Logs are the greatest source of IoCs. As great as logs are, they are a double-edged sword. The more you log, the more detailed information you're gathering, at your disposal, ready for your review. And the more you log, the more there is to review. Logs provide evidence that will prove useful in any forensic audit after a security breach. Some compliance requirements will state how long logs must be kept.
Intelligent log management goes a long way toward watching for indicators of compromise. Let's review the types of logs proving to be a good source for IoCs.
- Network Logs Network devices are the eyes and ears of the network. Network switches and routers can monitor for abnormal traffic, odd levels of traffic, unusual sources or destinations, triggered rules, and signatures. Use this capability to watch the perimeter as well as interior networks. When the time comes to investigate indicators of compromise, your network logs can provide breadcrumbs to follow.
- Vulnerability Logs Identifying and assessing vulnerabilities is a key part of risk management. After scanning a system for vulnerabilities, keep those logs as your baseline. Those vulnerability logs are a valuable resource when trying to understand or validate an indicator of compromise.
- Operating System Logs OS logs are your one-stop shop to tons of information related to the host system, the server's interfaces, OS errors, and failures. As with other logs, you get out of operating system logs only as much as you allow the operating system to record.
Windows Event Viewer Application, Security, and System logs can be critical in a forensic investigation. Windows Event logs are stored locally in
%SystemRoot%System32WinevtLogs.Most Linux log files are stored in a plain ASCII text file and are in the
/var/logdirectory and subdirectory. Logs are generated by the Linux system daemon log, syslogd, or rsyslogd. -
Access Logs Want to know who signed in to what, when, and from where? Access logs can answer all those questions. Depending on whether sufficient logging is done, an access log can either confirm suspicions or instill doubt.
- NetFlow Logs In case you're not familiar with network monitoring protocol NetFlow, Cisco created it to assist in collecting statistics on IP traffic as it traverses the network. There are a variety of commercial tools to gather and make pretty graphs from what NetFlow monitors. Those NetFlow logs might be a gold mine to you when reviewed in conjunction with network device logs.
NetFlow collects packets via a router interface. They are then provided to a NetFlow collector. A NetFlow application can then analyze the data, which is useful for incident investigations for intrusion analysis. An alternative to NetFlow is sFlow (sampled flow), which is also used for network monitoring. sFlow samples packets and provides analysis to identify unauthorized network activity and investigate DDoS attacks.
Intrusion Detection and Prevention
Intrusion detection has come a long way since the concept was created in the 1980s. Early intrusion detection and prevention systems (IDPSs) were clearly divided into two broad types: network intrusion detection systems (NIDSs) and host-based intrusion detection systems (HIDSs). These can be further divided into categories based on the internal engine or approach to detecting anomalies and unusual process activity. They typically include the following:
- Signature: Seeks to match based on known signature rules
- Anomaly: Examines traffic and looks for activity that is abnormal, based on behavior rules
- Protocol: Examines data and compares it to a database of known protocols and their activity
The IT security industry has grown to require more from these devices. This is how intrusion prevention systems (IPSs) were born. The IPS was designed to move beyond IDSs and provide the capability to enforce computer security policies, acceptable use policies, or standard security practices. Today, this technology has continued to evolve into what is known as intrusion detection and prevention (IDP). IDPs can record information related to observed events, generate notifications, generate IDS/IPS alerts, and create reports. Many IDPs can also respond to a detected threat by attempting to prevent it from succeeding. They use several response techniques, which involve the IDPs stopping the attack itself, changing the security environment through alteration of a firewall setting, or changing the attack's content.
Many IDPs exist, and some are community based and therefore free. Snort is one of the most popular and has been around for several years now. A more recent addition to the community is Suricata. It is offered by the Open Information Security Foundation (OISF) with funding from the U.S. Department of Homeland Security (DHS) and the U.S. Navy's Space and Warfare Command (SPAWAR) as well as the Open Information Security Foundation (OISF) Consortium. More information about Suricata is available at suricata-ids.org.
Threat intelligence sources may also provide IoCs. These are the telltale signs that an attack has taken place and may include file signatures, log patterns, and other evidence left behind by attackers. IoC may also be found in file and code repositories that offer threat intelligence information.
Exercise 3.1 will demonstrate how to perform a basic packet capture with WinDump and how this technology can be used to monitor and detect anomalies as well as look for indicators of compromise.
Notifications and Responses to IoCs
When we first recognize an indicator of compromise and our minds ask 100 questions at once, the panicked reaction is to respond. We want to respond immediately. The superior approach is to avoid panic and dig deeper for more information to make a more informed response. Tools that are monitoring and digesting information from our network can alert us when human hands are needed.
- FIM Alerts Would you know if the master price list was changed? Imagine the scenario where the master price list is updated every Monday morning. However, on Thursday, your service responsible for file integrity monitoring alerts you that a change was made by someone not in the appropriate department.
File integrity monitoring (FIM) will monitor for changes in the file. FIM alerts can tell you practically in real time, permitting you to immediately investigate. This wouldn't include end-user files, which we can safely expect to change constantly.
- Antivirus Alerts On end devices, commonly on an end-user workstation or production server, the antivirus software is working quietly in the background. However, when it does float an antivirus alert to the workstation user, it is an immediate indicator of compromise warranting further research.
- IPS/IDS Rules and Alerts Alerts from intrusion detection systems and intrusion prevention systems prove a significant indicator of suspect activity on the network. IDS or IPS alerts come when activity might get triggered when the activity matches the signature.
Depending how the organization manages alerts, the notification may feed into a security information and event management (SIEM) system. SIEM alerts provide security analysts a more centralized view compared to receiving alerts directly from individual systems.
- Scripts/Regular Expressions In earlier years, intrusion detection and antivirus systems had a processing technique using regular expressions (regex) and scripts to identify a match between a known signature and what was seen on the wire. Regex or regular expression matching was the default approach, but regex matching does take considerable overhead in memory. With the speed and volume of traffic today, regex matching is not quite fast enough, and other methods have met the need.
- DLP Rules and Alerts Detecting and blocking data exfiltration requires the use of security event management solutions that can closely monitor outbound data transmissions. Data loss prevention (DLP) requires the analysis of egress network traffic for anomalies and the use of better outbound firewall controls that perform deep packet inspection. Deep packet inspection normally occurs by a device at a network boundary, for example by a web application firewall at the trusted network's perimeter. To select where such a device should be placed in any organization, it's important to have a data flow diagram, depicting where and how data flows throughout the network. On this device, DLP rules establish what and how data flows will trigger DLP alerts. A DLP alert warns the security analyst or administrator of the likelihood of data being exfiltrated out of the network.
More notification types and rules to trigger are discussed in the following section through other situations. However, here we can already understand how valuable an alert or notification is to kick off our training in reviewing IoCs and possibly moving onto incident response.
Response
Firewalls can be hardware, software, or a combination of both. They are usually located at the demarcation line between trusted and untrusted network elements. Firewalls play a critical role in the separation of important assets. Figure 3.2 shows an example of the placement of a typical firewall.
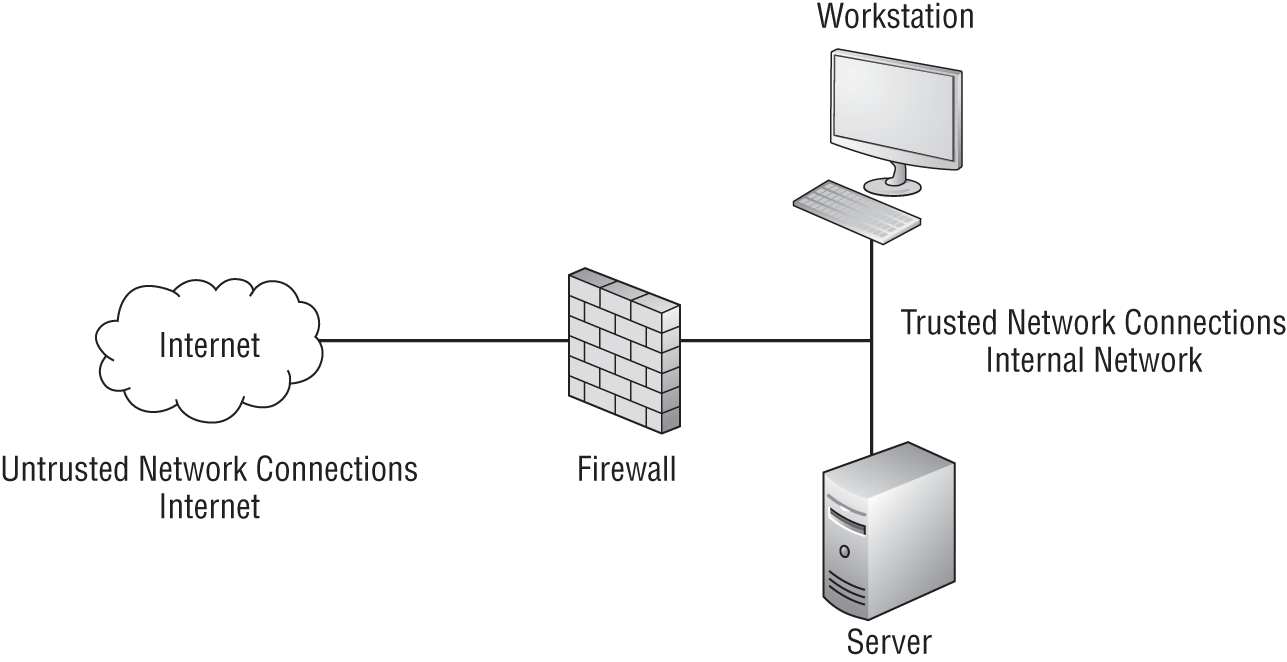
FIGURE 3.2 Firewall placement and design
Firewall rules determine what type of traffic is inspected, what is allowed to pass, and what is blocked. The most basic way to configure firewall rules is by means of an access control list (ACL). An ACL is used for packet filtering and for selecting the types of traffic to be analyzed, forwarded, or influenced in some way by the firewall or device. ACLs are a basic example of data flow enforcement. Simple firewalls, and more specifically ACL configuration, may block traffic based on the source and destination address. However, more advanced configurations may deny traffic based on interface, port, protocol, thresholds, and various other criteria. Before implementing ACLs, be sure to perform secure configuration and baselining of networking and security components. Rules placed in an ACL can be used for more than just allowing or blocking traffic. For example, rules may also log activity for later inspection or to record an alarm. Table 3.1 shows an example rule set.
TABLE 3.1 Basic rule set
| Rule number | Action | Protocol | Port | Direction | Comment |
|---|---|---|---|---|---|
| Rule 20 | Allow | DNS | 53 UDP | Outbound | None |
| Rule 50 | Allow | HTTP, HTTPS | 80, 443 | Outbound | None |
| Rule 100 | Allow | SMTP | 25 | Inbound | To mail server |
| Rule 101 | Allow | SMTP | 25 | Outbound | From mail server |
| Rule 255 | Deny | ALL | — | Bidirectional | None |
For the CASP+ exam, you will need to have a basic understanding of ACLs and their format. The command syntax format of a standard ACL in a Cisco IOS environment is as follows:
access-list access-list-number {permit|deny}{host|source source-wildcard|any}
There are also extended ACLs. These rules have the ability to look more closely at the traffic and inspect for more items, such as the following:
- Protocol
- Port numbers
- Differentiated services code point (DSCP) value
- Precedence value
- State of the synchronize sequence number (SYN) bit
The command syntax formats of extended IP, ICMP, TCP, and UDP ACLs are shown here:
IP trafficaccess-list access-list-number[dynamic dynamic-name [timeout minutes]]{deny|permit} protocol source source-wildcarddestination destination-wildcard [precedence precedence][tos tos] [log|log-input] [time-range time-range-name]ICMP trafficaccess-list access-list-number[dynamic dynamic-name [timeout minutes]]{ deny|permit } icmp source source-wildcarddestination destination-wildcard[icmp-type [icmp-code] |icmp-message][precedence precedence] [tos tos] [log|log-input][time-range time-range-name]TCP trafficaccess-list access-list-number[dynamic dynamic-name [timeout minutes]]{ deny|permit } tcp source source-wildcard [operator [port]]destination destination-wildcard [operator [port]][established] [precedence precedence] [tos tos][log|log-input] [time-range time-range-name]UDP trafficaccess-list access-list-number[dynamic dynamic-name [timeout minutes]]{ deny|permit } udp source source-wildcard [operator [port]]destination destination-wildcard [operator [port]][precedence precedence] [tos tos] [log|log-input][time-range time-range-name]
Let's review how basic rules work. Figure 3.3 shows a basic network configuration with two segments of the network separated by a router and a common connection to the Internet.
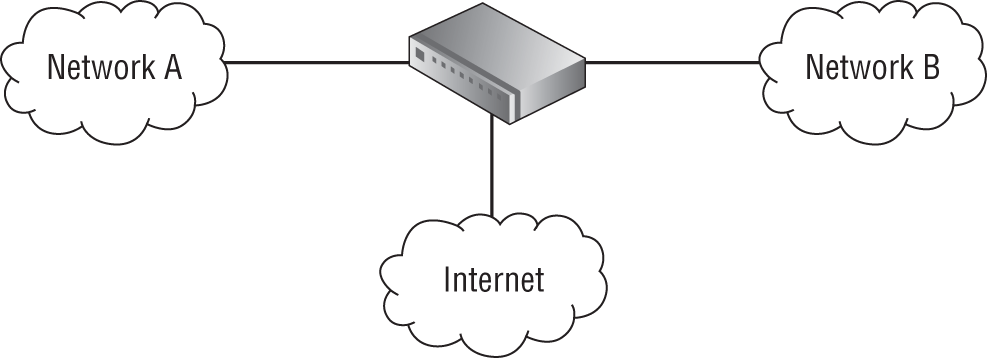
FIGURE 3.3 Basic network with firewall
In our first example, assume that the decision has been made to block all Telnet traffic. Telnet sends information via clear text, and it is not considered a secure protocol.
hostname R1!interface ethernet0ip access-group 102 in!access-list 102 deny tcp any any eq 23access-list 102 permit ip any any
In this configuration, all TCP traffic bound for port 23 is blocked by the firewall. All other traffic is permitted.
For this example, Telnet to ports other than TCP/23 would still be allowed. If you want to block Telnet to any TCP port, you need other controls. It is also good to know that standard ACLs are often used to restrict Telnet, or ideally SSH access to a device such as a router, by limiting that access to specific IP addresses. Extended ACLs are used for many more tasks. Also note that the previous example is for demonstration purposes only. As stated earlier, it is generally considered best practice to permit only that which is required and deny everything else, following the principle of least privilege.
Exercise 3.2 shows you how to review a basic ACL.
Host-based firewalls are devices that run directly on a network host or device. A host-based firewall is deployed for the purpose of protecting the device on which it's installed from an attack. A host-based firewall usually has predefined rules to protect the host against specific attack patterns.
Some host-based firewalls can also prevent malicious software from attacking other devices on a network. Adding a host-based firewall builds on the concept of defense in depth.
Host-based firewalls work by inspecting and controlling inbound and outbound traffic from the host on which the firewall is placed. Although there are many kinds of firewalls, only a host-based firewall is designed to reside on the end host and to protect it from an attack. Like all firewalls, a host-based firewall works by inspecting traffic as it passes through the interface. It works in much the same way as do border guards and customs agents. The host layer adds to other devices on the network and perimeter.
As people and products pass over the border of one country and go to another, they are inspected. All firewalls work by using predefined rule sets. Higher-level and application-layer firewalls can make determinations on traffic based on behavior as well. Firewalls and other network inspection devices add to defense in depth by adding another layer of control.
Summary
Threat management is a full-time job. Managing threats requires resources such as time, money, and intelligence. It requires a firm grasp of the actors involved, including their sophistication and techniques. And threat management should involve actively hunting and proactively mitigating against those threats.
Luckily, there are resources for the good guys, such as intelligence feeds, tools, and frameworks to help you. The CASP+ exam candidate should understand the properties and methods of various threat actors. Candidates should recognize the frameworks available and the concepts within. Lastly, the CASP+ candidate must be able to recognize indicators of compromise, know where to find more, and appreciate how to respond with the appropriate tools and rules.
Exam Essentials
Know the various ways someone can gather information. Getting open-source information from online and offline resources makes for a massive list of sources. Understand where to look for the type of information you want. Understand how HUMINT differs from OSINT.
Be able to name specific indicators of compromise. Understand what an indicator of compromise is. Know where to search for more information and the significance of what you find.
Know what kinds of actors threaten you. Bad actor types come with all manner of financial backing, skills, and available resources.
Know how and when to apply ACLs. Access control lists are a valuable commodity when it comes to network access control. Learn how to read, write, and understand them.
Review Questions
You can find the answers in Appendix.
- What term describes the search for an insider threat or shadow IT, which, until discovered, had been “flying under the radar?”
- Threat hunting
- Threat emulation
- Intelligence
- Targeted attacks
- LoJax, Bad Rabbit, and NotPetya are three examples of what?
- Zero-day threats
- Malware
- APTs
- Competitors
- You discover log entries that raise suspicion that a security incident might have occurred. You decide more investigation is needed. What describes what you found?
- Vulnerabilities
- ACLs
- Threat intelligence types
- Indicators of compromise
- What is a key strength the disgruntled employee has over an outsider?
- Trust
- Time
- Money
- Signature
- Your manager asks if you've noticed any abnormal volumes of network traffic or other network issues. What logs might help you answer those concerns?
- FIM logs
- NetFlow logs
- Firewall logs
- Access logs
- Which of the following alerts warns the security analyst or administrator of the likelihood that data was exfiltrated out of the network?
- IoC
- FIM
- DLP
- ICE
- What intrusion detection processing technique is common for identifying a positive match but struggles to keep up with today's traffic speeds and volumes?
- SIEM
- Regular expressions
- Signature-based
- Anomaly or behavior
- Which of the following can block traffic based on the source and destination address?
- The Deep Web
- Script kiddie
- ICS
- ACL
- In the following example of an access control list, which of the following answers is true?
hostname R1!Interface ethernet0Ip access-group 102 in!access-list 102 deny tcp any any eq 23access-list 102 permit ip any any- TCP traffic bound for port 102 is permitted.
- TCP traffic bound for port 23 is blocked.
- TCP traffic bound for port 102 is blocked.
- TCP traffic bound for port 23 is permitted.
- You got an alert that unusual changes were made to files in a customer directory. What type of alert was this?
- DLP
- IDS
- FIM
- IPS
- Which of the following is not a label for the conceptual Diamond Model of Intrusion Analysis?
- Capability
- Attacks
- Victim
- Infrastructure
- For the purpose of better understanding a company, an employee is tasked with browsing social media, listening to recorded speeches, and reading patents. What type of intelligence gathering is this employee performing?
- HUMINT
- APT
- OSINT
- ATT&CK
- A determined security analyst discovered some evidence on a system that warranted more investigation. Ultimately, the analyst identified that advanced malware was resident and difficult to remove. The security analyst recommended the system be rebuilt from scratch. What is it the analyst had discovered?
- IoC
- ACL
- DLP
- APT
- What intelligence collection method is described as the personal side of spying or collecting intelligence?
- Lessons learned report
- Deep Web
- HUMINT
- OSINT
- If you needed to find out an organization's technical contact or registration information about their domain, what OSINT resource might be helpful?
- DNS records
- Deep Web
- TRA
- WHOIS
- Whether following the Cyber Kill Chain or the ATT&CK framework, which of the following tactics would occur first?
- Reconnaissance
- Command and control
- Exfiltration
- Discovery
- In the ATT&CK framework, which of the following tactics occurs last?
- Initial access
- Persistence
- Discovery
- Defense evasion
- For the purpose of gaining access to a competitor's property, you are tasked with befriending the competitor's employees, using social media, conversations, and empathy to build personal trust. What type of intelligence gathering are you performing?
- HUMINT
- APT
- OSINT
- ATT&CK
- Which dangerous category of bad actors describes those seeking to compromise critical infrastructures such as nuclear power plants, power generation stations, and water treatment plants?
- Script kiddie
- Organized crime
- Insider threat
- Nation-state
- A few months after the legal firm Dewey, Cheatem, and Howe outsourced their accounts receivable department, the law firm suffered from hacked bank accounts. They are growing suspicious of an attack. Which of the following terms describes what likely happened?
- Denial-of-service attack
- SYN flood attack
- Disgruntled employee
- Supply chain attack
