Chapter 6
Cryptography and PKI
This chapter discusses cryptography, which can be defined as the art of protecting information by transforming it into an unreadable format. Everywhere you turn you see cryptography. It is used to protect sensitive information, prove the identity of a claimant, and verify the integrity of an application or program. As a security professional for your company, which of the following would you consider more critical if you could choose only one?
- Provide a locking cable for every laptop user in the organization.
- Enforce full disk encryption for every mobile device.
Our choice would be full disk encryption. Typically, the data will be worth more than the cost of a replacement laptop. If the data is lost or exposed, you'll incur additional costs such as client notification and reputation loss.
As a security professional, you should have a basic understanding of cryptographic functions. This chapter will include cryptographic types, explaining symmetric and asymmetric encryption, hashing, digital signatures, and public key infrastructure. These concepts are important as we move on to more advanced topics and begin to look at cryptographic applications. Understanding them will help you prepare for the CompTIA exam and to implement cryptographic solutions to protect your company's assets better.
The History of Cryptography
Encryption is not a new concept. The desire to keep secrets is as old as civilization. There are basic ways in which encryption is used: for data at rest, data in motion, and data in process/data in use. Data at rest might be information on a laptop hard drive or in cloud storage. Data in motion might be data being processed by SQL, a URL requested via HTTP, or information traveling over a VPN at the local coffee shop bound for the corporate network. Data in process/data in use is exactly what it sounds like: data being processed, changed, updated, read, or modified in any way. In each of these cases, protection must be sufficient. The following list includes some examples of early cryptographic systems:
- Scytale This system functioned by wrapping a strip of papyrus or leather, on which a message was written, around a rod of fixed diameter. The recipient used a rod of the same diameter to read the message. Although such systems seem basic today, it worked well in the time of the Spartans. Even if someone was to intercept the message, it appeared as a jumble of meaningless letters.
- Caesar's Cipher Julius Caesar is known for an early form of encryption, the Caesar cipher, which was used to transmit messages sent between Caesar and his generals. The cipher worked by means of a simple substitution. Before a message was sent, the plain text was rotated forward by three characters (ROT3). Using Caesar's cipher to encrypt the word cat would result in fdw. Decrypting required moving back three characters.
- Other Examples Substitution ciphers replace one character for another. The best example of a substitution cipher is the Vigenère polyalphabetic cipher. Other historical systems include a running key cipher and the Vernam cipher. The running key cipher is another way to generate the keystream for use with the tabula recta. The Vernam is also known as the onetime pad.
Cryptographic Goals and Requirements
Cryptography includes methods such as symmetric encryption, asymmetric encryption, hashing, and digital signatures. Each provides specific attributes and solutions. These cryptographic services include the following goals:
- Privacy This is also called confidentiality. What is private (confidential) should stay private, whether at rest or in transit.
- Authentication There should be proof that the message is from the person or entity you believe it to be from.
- Integrity Information should remain unaltered at the point at which it was produced, while it is in transmission, and during storage.
- Nonrepudiation The sender of data is provided with proof of delivery, and the recipient is assured of the sender's identity.
Consider how encryption can protect the privacy and confidentiality of information at rest or in transit. What if your CEO has been asked to travel to Asia for trade negotiations? Think about the CEO's laptop. If it is lost or compromised, how hard would it be for someone to remove unencrypted data? Strong encryption offers an easy way to protect that information should the equipment be lost, stolen, or accessed by unauthorized individuals. Applications such as CryptoForge and BitLocker offer the ability to encrypt a hard drive. PKWARE provides users with enterprise data security that persistently protects and manages data whenever it is used, shared, and stored, both inside and outside the organization. Sookasa transparently protects files across the Dropbox and Google Drive clouds as well as linked mobile devices while preserving the native user experience on the Windows, macOS, iOS, and Android operating systems.
Authentication is another key goal of cryptography. First, authentication is associated with digital signatures. Authentication provides a way to ensure that a message is from the person we believe it's from. In its basic form, authentication is used to determine identity. It is also part of the identification and authentication process.
Integrity is another cryptographic goal. Integrity is important while data is in transmission and in storage. Integrity means that information remains unaltered. Imagine the situation of needing to download a patch. Although the patch is available on the developer's site, you also have a copy on USB that was given to you by a colleague. Is the version on the USB the same as the one on the developer's website? Integrity verification programs that perform hashing such as MD5 or SHA can help you determine this. In this case specifically, the MD5 algorithm can be and is still used for integrity, but not confidentiality.
Nonrepudiation is assurance that an entity in a communication cannot deny authenticity. It is proof of the veracity of a claim. Nonrepudiation means that a sender of data receives proof of delivery and the recipient is assured of the sender's identity. Neither party should be able to deny having sent or received the data at a later date. This can be achieved with digital signatures. A digital signature provides authenticity, integrity, and nonrepudiation. In the days of face-to-face transactions, nonrepudiation was not as hard to prove. Today, the Internet makes many transactions faceless. We may never see the people we deal with; therefore, nonrepudiation becomes all the more critical. Nonrepudiation is achieved through digital signatures, digital certificates, and hash-based message authentication codes (HMACs).
When implementing a cryptographic system, there has to be consideration of strength versus performance versus feasibility to implement versus interoperability. Stronger systems typically require more process power and longer encryption/decryption times. Basically, you must consider how strong an encryption process should be. The strength of a cryptosystem relies on the strength of an algorithm and the complexity of the key generation process. The strength of the encryption mechanism also rests on the size and complexity of the key. If the cryptosystem uses a weak key generation process, then the entire process is weak. The key size goes a long way in determining the strength of the cryptosystem.
The designer of a cryptographic system must also understand the implications of cryptographic methods and design. As an example, Caesar might have thought his system of encryption was quite strong, but it would be seen as relativity insecure today. You need a sufficiently sized key to deter brute-force and other attacks. In the world of cryptography, key lengths are defined by the number of binary bits. So, for example, a 64-bit key has a keyspace of 2 to the power of 64, or 18,446,744,073,709,551,616.
Supporting Security Requirements
Knowing the basic goals discussed earlier can go a long way in helping you to understand that cryptography can be used as a tool to achieve confidentially, integrity, and availability (CIA). For example, let's consider the different types of requirements that might need to be met.
Compliance and Policy Requirements
One huge area of influence is compliance. Compliance can be defined as being in accordance with agreed-upon guidelines, specifications, legislation, or regulations. Auditors and audit findings play a huge role in maintaining compliance. Auditors typically report to the top of the organization and function by charter. Control Objectives for Information and Related Technology (COBIT) is one of the leading governance frameworks used by auditors to verify compliance. The U.S. federal government plays an active, large role in regulating the Internet, privacy, and corporate governance. This increased role is most visible in the upsurge in new laws and mandates that have been passed in the last 10 to 15 years.
Some of the major information security regulations facing organizations include the following:
- The Health Insurance Portability and Accountability Act (HIPAA) includes security and privacy rules that affect healthcare providers, health insurers, and health information clearinghouses in the United States.
- The Payment Card Industry Data Security Standard (PCI DSS) provides detailed rules about the storage, processing, and transmission of credit and debit card information. PCI DSS is not a law but rather a contractual obligation that applies to credit card merchants and service providers worldwide.
- The Gramm-Leach-Bliley Act (GLBA) covers U.S. financial institutions, broadly defined. It requires that those institutions have a formal security program and designate an individual as having overall responsibility for that program.
- The Sarbanes-Oxley (SOX) Act applies to the financial records of U.S. publicly traded companies and requires that those companies have a strong degree of assurance around the IT systems that store and process those records.
- The General Data Protection Regulation (GDPR) implements security and privacy requirements for the personal information of European Union residents worldwide.
- The Family Educational Rights and Privacy Act (FERPA) requires that U.S. educational institutions implement security and privacy controls for student educational records.
Privacy and Confidentiality Requirements
If you read about the major breaches in the last few years, most of them could have been avoided if the organization had subscribed to and executed controls. The Center for Internet Security (CIS) is a self-described forward-thinking, nonprofit entity dedicated to protecting private domains and public society from cyberthreats. The controls they publish are the global standard and are the recognized best practices for security. As our cyber worries evolve, so do these best practices.
The CISv8 controls have cross-compatibility or directly map to other cyber compliance and security standards like NIST 800-53, PCI DSS, and HIPAA. This translates to other organizations using these suggestions as regulations to aid in their respective compliance for privacy and confidentiality.
The NIST Cybersecurity Framework is another tool that organizations use to organize and strengthen their security posture using the CIS top controls as their baseline for several of their best practices. Let's look at these in more detail. Different nations have varying views of privacy, but most have some laws in place to protect the confidentiality of an individual's personally identifiable information (PII).
Integrity Requirements
In the United States, the banking and accounting failures of Lehman Brothers, Bear Stearns and AIG have long been analyzed and considered an example of how not to conduct business. Laws such as Sarbanes-Oxley, formed in the wake of the earlier Enron scandal, didn't adequately protect against such scandals from happening again.
While those laws might hold officers of publicly traded companies responsible and accountable for the accuracy of financial records, they could not protect against the deception and fraud demonstrated by Elizabeth Holmes, the founder and once-CEO of Theranos. Theranos, a blood-testing startup, was poised to become a major disruptor to the industry, but under Holmes, it instead became an example of how fleeting corporate integrity can be. Corporate integrity dictates that proper information security architecture be implemented.
Nonrepudiation
An important part of auditing and accounting is nonrepudiation. Nonrepudiation means that the person authenticated and authorized cannot deny the performance of an action. You do not want a situation where one person claims an action happened and another is in total opposition to the story. A traditional example of nonrepudiation is a signature you received in a document. In cybersecurity, nonrepudiation requires the creation of certain artifacts such as the following:
- An identity
- Authentication of that identity
- Evidence connecting that identity to an action
When you take a trip through an airport, you have to produce identification to authenticate you are who you say you are. Then you have to provide a ticket to an agent to access the boarding area. Your belongings are screened to make sure you're not bringing any malicious contraband with you into a secured area. When you board the plane, they scan your ticket to prove you gained access to the aircraft. Now the airline can track and audit if and when you traveled. This is fundamental access management. Now take the same concept and apply it to a networked environment.
With all these layers of access management, how often do we hear of people getting past security? What other layers of security are in place at an airport that you have not even considered? As a security professional, you become acutely aware of those layers of defense in depth. You always have to be thinking strategically and protectively and asking targeted questions. What if someone is impersonating another on my network? What if someone has too much access? What if someone does access the network but has brought ransomware along?
Diverse entities may very well be governed by different regulatory entities or regulations such as the Payment Card Industry Data Security Standard (PCI DSS) or Health Insurance Portability and Accountability Act (HIPAA). Other regulatory factors include export controls, such as use of encryption software. Companies dealing with controlled data types must meet the regulatory-imposed legal requirements, often related to storing, safeguarding, and reporting on that data.
Risks with Data
Data is the lifeblood of many organizations. Although the doctor's office of our childhood had a mountain of files, folders, and documents behind the receptionist's desk, today a computer holds the same information in a digital format. From the security professional's standpoint, there are several areas to consider: data at rest, data in transit, and data in process/data in use. Data at rest can be stored in hard drives, external physical storage, cloud storage, or even USB drives.
Data at Rest
A wide variety of products are available to encrypt data in existing disk and media drive products. Data-at-rest encryption options include software encryption, such as encrypted file system (EFS) and VeraCrypt.
Failure to protect data at rest properly can lead to attacks such as the following:
- Pod slurping, a technique for illicitly downloading or copying data from a computer. This is typically used for data exfiltration.
- USB malware, such as USB Switchblade and Hacksaw.
- Malware such as viruses, worms, Trojans, and keyloggers.
Protection of data at rest is not just for equipment during its useful life. It's also required at end of life. All equipment that reaches end of life should be properly disposed of. Proper disposal methods can include the following:
- Drive wiping
- Zeroization
- Degaussing
- Physical destruction
Data in Transit
Another concern is when data is in transit. Anytime data is being processed or moved from one location to another, it requires proper controls. The basic problem is that many protocols and applications send information via clear text. Services such as email, web, and FTP are not designed with security in mind and send information with few security controls and no encryption. Here are some examples of insecure protocols:
- FTP Clear text username and password
- Telnet Clear text username and password
- HTTP Clear text
- SMTP Username and password, along with all data passed in the clear
For data in transit that is not being protected by some form of encryption, there are many dangers including these:
- Eavesdropping
- Sniffing
- Hijacking
- Data alteration
High-value data requires protection. One approach is for the security professional to break the data into categories. For example, the organization may require all email users to use some form of encryption such as S/MIME, OpenPGP, or GPG. Data-in-transit encryption works to protect the confidentiality of data in transmission. Mobile users should be required to use virtual private networks (VPNs). Individuals communicating with databases and web servers that hold sensitive information should use HTTPS, SSL, or TLS.
Data in Process/Data in Use
Data being sent over a network is data in motion. Data at rest is stored data that resides on hard drives, tapes, in the cloud, or on other storage media. Data in processing, or data in use, is data that is actively in use by a computer system. Data in use is data that is stored in the active memory of a computer system where it may be accessed by a process running on that system.
This type of data can be protected with technology such as smart cards. Smart cards are used in applications where security is of highest value such as credit cards, government identification cards, and e-documents like passports. They are often used with a personal identification number for multifactor authentication. When accessing, reading, or modifying data, smart cards can bring a stronger level of security.
Each of these data situations has risks that cryptography protects against. Data in motion may be susceptible to eavesdropping attacks, while data at rest is more susceptible to the theft of physical devices or misconfiguration in the cloud. Data in use may be accessed by unauthorized processes if the operating system does not implement process isolation.
Hashing
Hashing refers to a broad category of algorithms that are useful for their ability to provide integrity and authentication. Integrity ensures that the information remains unchanged and is in its true original form. Authentication provides the capability to ensure that messages were sent from those you believed sent them and that those messages are sent to their intended recipients.
Hashing is a method of translating a key into a code. It does this by assigning a random independent surrogate value that can still be identified as the original data. Hashing calculates a short, secret value from a dataset of any size but usually for an entire message. This value is recalculated independently on the receiving end and is compared to the submitted value to verify the sender's identity.
Hashing algorithms operate by taking a variable amount of data and compressing it into a fixed-length value referred to as a hash value. Hashing provides a fingerprint or message digest of the data. A well-designed hashing algorithm will not typically produce the same hash value or output for two different inputs. When this does occur, it is referred to as a collision.
Hashing can be used to meet the goals of integrity and nonrepudiation, depending on how the algorithm is implemented. Hashing is one of the primary means used to perform change monitoring. As an example, you might use a program such as Tripwire, a well-known change monitoring program, to verify that the contents of a specific folder remain unchanged over time. One of the advantages of hashing is its ability to verify that information has remained unchanged, but it is also used in authentication systems and digital signatures. Figure 6.1 gives an overview of the hashing process.

FIGURE 6.1 Hashing process
A hash is a one-way process and is not intended to be used to reproduce data. When a message or data file is hashed, the hashing algorithm examines every bit of the data while it is being processed. This means that if two files are close yet not exactly the same, their hashes will be different. For example, if we gave you a copy of a software program that had CASP+ exam study questions and you went to the Sybex website and downloaded the same software, hashing both files should result in the same value. Figure 6.2 shows an example of a cryptographic hash. It can be seen in the sha256sum column.
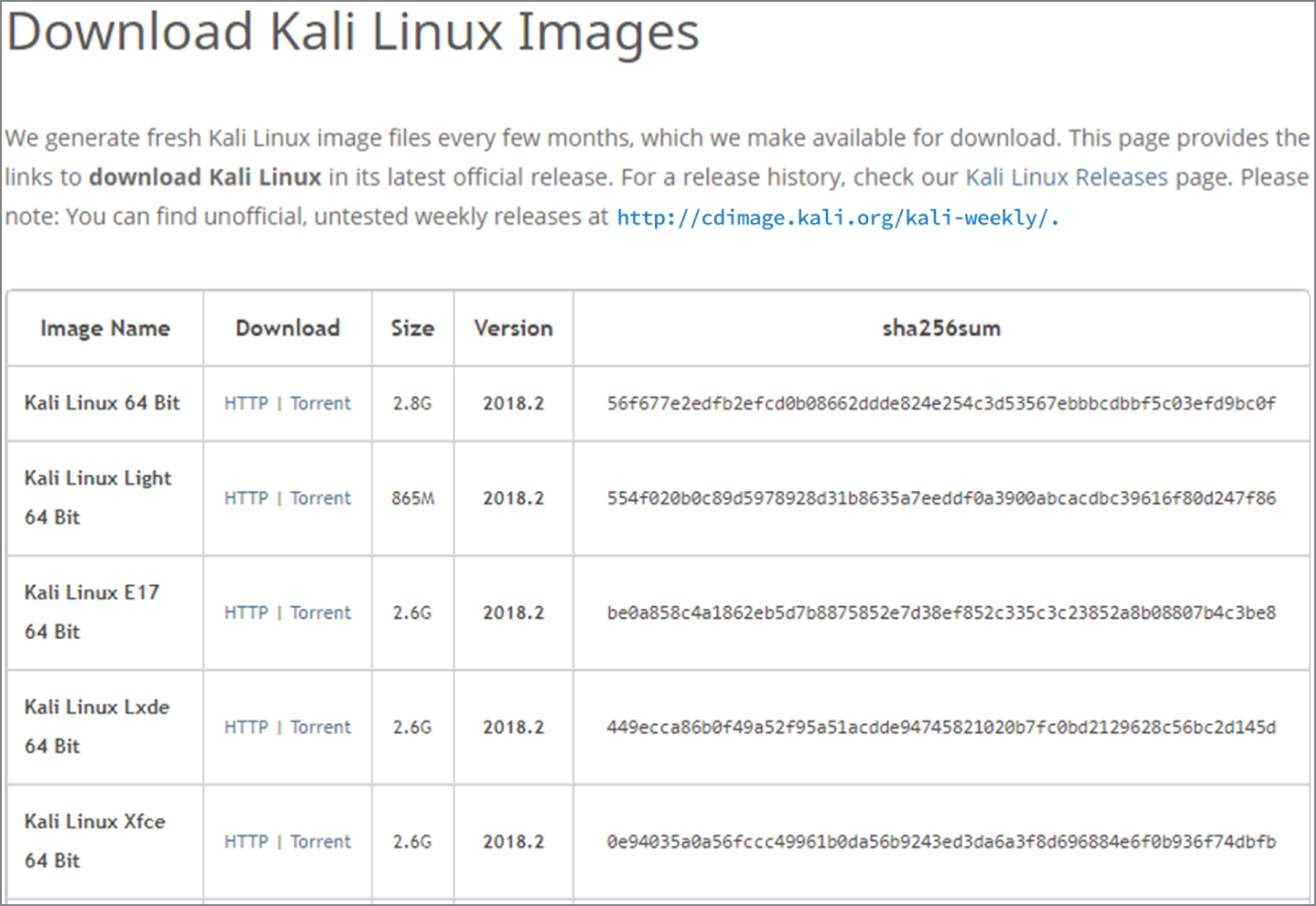
FIGURE 6.2 An example of a cryptographic hash on a software product
If there were even a slight difference between the two files, the hashed values would be different. Comparing the hashes for the two files would indicate that the software we gave you had been altered. This same process is how programs such as Tripwire, MD5sum, and Windows System File Checker (sfc.exe) work. These kinds of programs can be used to monitor a file, a folder, or an entire hard drive for unauthorized changes. You also see this process used for functions such as code signing. Code signing is the process of digitally signing executables and scripts to confirm the software author. Code signing also guarantees that the code has not been altered or corrupted since it was signed by use of a hash. Listed here are some examples of hashing algorithms:
- Message Digest (MD)
- Secure Hash Algorithm (SHA)
- Message Authentication Code (MAC)
- Hashed Message Authentication Code (HMAC)
- RACE Integrity Primitives Evaluation Message Digest (RIPEMD)
- Poly1305
The following sections explore these hashing algorithms further.
Message Digest
The MD algorithms are a series of cryptographic algorithms that were developed by Ron Rivest. These have progressed throughout the years as technology has advanced. The first algorithm was MD2, which is considered outdated. One reason for its demise is that it was prone to collisions. MD4 was the next algorithm in the series. MD4 processes data in 512-bit blocks. Like MD2, MD4 was found to be subject to collisions and could potentially be vulnerable to forced collisions. These issues helped lead to the development of MD5, which processes a variable-size input and produces a fixed 128-bit output. A common implementation of MD5 is MD5sum. It's widely used to verify the integrity of a program or file. Consider the following example: if we received a copy of snort.exe from a friend, we could hash it and verify that the MD5sum matches what is found on the Sourcefire website:
C: emp>md5sum snort.exed1bd4c6f099c4f0f26ea19e70f768d7f *snort.exe
Thus, a hash acts to prove the integrity of a file. Like MD4, MD5 processes the data in blocks of 512 bits. However, MD5 has also fallen from favor as it too has been shown to be vulnerable to collisions.
Secure Hash Algorithm
Secure Hash Algorithm (SHA) is similar to MD5. Some consider it a successor to MD5 because it produces a larger cryptographic hash. SHA outputs a 160-bit message digest. SHA-1 processes messages in 512-bit blocks and adds padding, if needed, to get the data to add up to the right number of bits. SHA-1 has only 111-bit effectiveness. SHA-1 is part of a family of SHA algorithms, including SHA-0, SHA-1, SHA-2, and SHA-3. SHA-0 is no longer considered secure, and SHA-1 is also now considered vulnerable to attacks. SHA-2 is the U.S. government's recommended replacement for the collision-vulnerable MD5. Some of the strongest versions currently available are SHA-256 and SHA-512. SHA-3 was released in 2012 and uses the Keccak algorithm.
Block cipher algorithms like AES and Triple DES in Electronic Code Book (ECB) and Cipher Block Chaining (CBC) mode require their input to be an exact multiple of the block size. If the plain text to be encrypted is not an exact multiple, you need to pad or extend the plain text before encrypting by adding a padding string. When decrypting, the receiving party needs to know how to remove the padding or extension.
Message Authentication Code
A message authentication code (MAC) is similar to a digital signature except that it uses symmetric encryption. MACs are created and verified with the same secret (symmetric) key. There are four types of MACs that you may come across in your career as a security professional: unconditionally secure, hash function based, stream cipher based, and block cipher based.
Hashed Message Authentication Code
Sometimes hashing by itself is not enough, and in such situations a hashed message authentication code (HMAC) may be needed. This functionality was added by including a shared secret key. Basically, HMAC functions by using a hashing algorithm such as MD5 or SHA-1 and then alters the initial state by adding a password. Even if someone can intercept and modify the data, it's of little use if that person does not possess the secret key. There is no easy way for the person to re-create the hashed value without it.
RACE Integrity Primitives Evaluation Message Digest
RACE integrity primitives evaluation message digest (RIPEMD) is in the Cryptocurrency Bitcoins standard. RIPEMD is based on the MD4 hash function and was published in four strengthened variants: RIPEMD-128, RIPEMD-160, RIPEMD-256, and RIPEMD-320.
The first RIPEMD-128 was not considered a good hash function because of major security problems, including the size of output was too small and easy to break. RIPEMD-160 is the next version; it increases the output length to 160 bit and increases the security level of the hash function. This function is designed to work as a replacement for 128-bit hash functions MD4, MD5, and RIPEMD-128 and is used as one of the alternatives to SHA-256 in Bitcoin.
Poly1305
The Poly1305 is a cryptographic message authentication code created by Daniel J. Bernstein. It is used to verify the data integrity and the authenticity of a message. Poly1305 takes a secret key and a message and produces an identifier that is difficult to create unless you know the secret key. This identifier is small and can be produced very quickly. This will authenticate a message and make sure it hasn't been altered.
The Poly1305 algorithm is defined in RFC 8439. More information can be found here: https://datatracker.ietf.org/doc/html/rfc8439.
Symmetric Algorithms
Symmetric encryption uses a single shared key for encryption and decryption. These are known as dual-use keys, as they can be used to lock and unlock data. Symmetric encryption is the oldest form of encryption. Historical systems such as scytale and Caesar's cipher are types of symmetric encryption. Symmetric encryption offers users privacy by keeping individuals who do not have the key from having access to the true contents of the message. Figure 6.3 shows the symmetric encryption process.
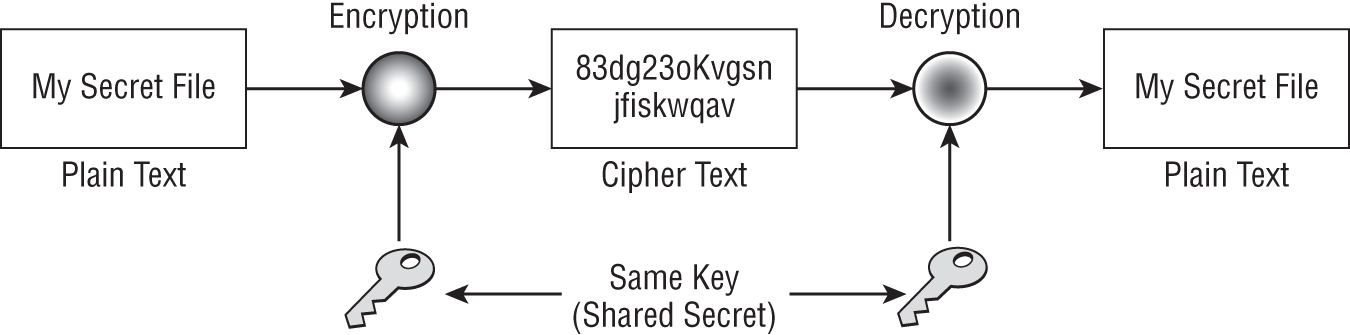
FIGURE 6.3 Symmetric encryption process
Notice how the plain text is encrypted with the single shared key and is then transmitted to the recipient of the message, who goes through the same process to decrypt the message. The dual use of keys is what makes this system so simple, but it also introduces weakness. Symmetric encryption is fast, and with a small key it can be used to encrypt bulk data quickly. It is also strong and difficult to break if the key is of sufficient size. However, symmetric encryption does have disadvantages.
The problem is key distribution. For symmetric encryption to be effective, there must be a secure method in place to transfer keys. In our modern world, there needs to be some type of out-of-band transmission. Out-of-band transmission means using a different means to transmit the key. As an example, if Bob wants to send Alice a secret message but is afraid that Mike can monitor their communication, how can he send the message? If the key is sent in clear text, Mike can intercept it. Bob could deliver the key in person, mail it, or even send a courier. All of these out-of-band methods are highly impractical in the world of e-commerce and electronic communications because they do not scale well.
Even if the problems of key exchange are overcome, there are still other concerns. Another problem is key management. If, for example, 10 people needed to communicate using symmetric encryption, the number of keys needed would be 45. As the number of people using symmetric encryption rises, so does the required number of keys. To determine the number of keys needed in symmetric encryption, the following formula is used:
which simplifies to
The third and final flaw with symmetric encryption is that it only provides confidentiality.
Some of the biggest challenges of key management across the enterprise can be made easier through security orchestration, automation, and response (SOAR). Public key infrastructure (PKI) isn't only about keeping keys stored securely. Through automation scripts and careful orchestration, the issuance and maintenance of keys can be done securely and with minimal risk of human error. PKI is discussed in more detail later in the “Public Key Infrastructure Hierarchy” section.
Although it is true that symmetric encryption is not perfect, it does offer some great features that make it an excellent choice for securing data and providing confidentiality. In the following sections, we will be discussing the following items (although not necessarily in this order):
- Modes of operation
- Galois/counter mode (GCM)
- Electronic codebook (ECB)
- Cipher block chaining (CBC)
- Counter (CTR)
- Output feedback (OFB)
- Stream and block
- Advanced Encryption Standard (AES)
- Triple digital encryption standard (3DES)
- ChaCha
- Salsa20
But first, let's look at some of the specifics of symmetric encryption for a moment. Symmetric encryption is fast. It can encrypt and decrypt very quickly, and it is considered strong. Symmetric encryption is hard to break if a large key is used. Here are some well-known symmetric algorithms:
- Data Encryption Standard The Data Encryption Standard (DES) was once the most common symmetric algorithm used. It has now been officially retired by the National Institute of Standards and Technology (NIST). Its short-term replacement was 3DES. Today, all versions of DES have been replaced by the Advanced Encryption Standard.
- Advanced Encryption Standard The Advanced Encryption Standard (AES) is the symmetric algorithm chosen as a replacement for DES. It was adopted from the Rijndael algorithm, and it is used for sensitive and secret data. Its key sizes are 128-, 192-, and 256-bit.
- Blowfish Blowfish is a general-purpose symmetric algorithm intended as a replacement for DES. Blowfish has a variable block size and up to a 448-bit key.
- Carlisle Adams/Stafford Tavares Carlisle Adams/Stafford Tavares (CAST) is a 128- or 256-bit block cipher that was a candidate for AES.
- International Data Encryption Algorithm The International Data Encryption Algorithm (IDEA) is a block cipher that uses a 128-bit key to encrypt 64-bit blocks of plain text. It is used by Pretty Good Privacy (PGP).
- Rivest Cipher 4 Rivest Cipher 4 (RC4) is a stream-based cipher. Stream ciphers treat the data as a stream of bits.
- Rivest Cipher 5 Rivest Cipher 5 (RC5) is a fast-block cipher. It is different from other symmetric algorithms in that it supports a variable block size, a variable key size, and a variable number of rounds. A round is a sequential repetition of a series of math functions. Allowable choices for the block size are 32, 64, and 128 bits. The key can range up to 2,040 bits.
- Secure and Fast Encryption Routine Secure and Fast Encryption Routine (SAFER) is a block-based cipher that processes data in blocks of 64 and 128 bits.
- Skipjack Promoted by the U.S. National Security Agency (NSA), Skipjack uses an 80-bit key and operates on 64-bit blocks of text. Skipjack faced opposition because the government would maintain a portion of the information required to reconstruct a Skipjack key so that legal authorities could decrypt communications between the affected parties when approved by a court.
- Twofish Twofish is a block cipher that operates on 128-bit blocks of data and is capable of using cryptographic keys up to 256 bits in length.
Now let's look at some of the popular symmetric encryption standards in more depth.
Data Encryption Standard
DES was originally developed by IBM and then modified by NIST. The NSA endorsed the revised standard. It was published in 1977, and it was released by the American National Standards Institute (ANSI) in 1981.
DES is a symmetric encryption standard that is based on a 64-bit block that processes 64 bits of plain text at a time. DES outputs 64-bit blocks of cipher text. The DES key size is 56 bits, and DES has four primary modes of operation:
- Electronic codebook (ECB) mode
- Cipher block chaining (CBC) mode
- Output feedback (OFB) mode
- Cipher feedback (CFB) mode
All four modes use the 56-bit key, and though the standard lists the key as 64 bits, 8 bits are used for parity checking, so the true key size is actually 56 bits. Parity checking is a simple form of error detection. Each 64-bit, plaintext block is separated into two 32-bit blocks and then processed by the 56-bit key. The plain text is processed by the key through 16 rounds of transposition and substitution.
Electronic Codebook Mode
Electronic codebook (ECB) mode is the default mode of encryption used by DES, ECB, CBC, OFB, and CFB and also applies to 3DES. If the last block is not a full 64 bits, padding is added. ECB produces the greatest throughput, but it is also the easiest implementation of DES encryption to crack. If used with large amounts of data, it is easily broken because the same plain text encrypted with the same key always produces the same cipher text. This is why if you use ECB, you should do so only on small amounts of data.
Cipher Block Chaining Mode
When DES is operating in cipher block chaining (CBC) mode, it is somewhat similar to ECB except that CBC inserts some of the cipher text created from the previous block into the next one. This process is called XORing. It makes the cipher text more secure and less susceptible to cracking. CBC is aptly named because data from one block is used in the next, and the blocks are chained together. This chaining produces dependency, but it also results in more random cipher text.
Output Feedback Mode
Output feedback (OFB) mode is implemented as a stream cipher and uses plain text to feed back into the stream of cipher text. Transmission errors do not propagate throughout the encryption process. An initialization vector is used to create the seed value for the first encrypted block. DES XORs the plain text with a seed value to be applied with subsequent data.
Cipher Feedback Mode
Cipher feedback (CFB) mode can be implemented as a stream cipher and used to encrypt individual characters. CFB is similar to OFB in that previously generated cipher text is added to subsequent streams. Because the cipher text is streamed together, errors and corruption can propagate through the encryption process. This mode could be referring to DES, 3DES, or AES.
Triple DES
Triple DES (3DES) was designed to be a stopgap solution. DES was initially certified for five years and was required to be recertified every five years. While easily passing these recertifications in the early years, DES began to encounter problems around the 1987 recertification. By 1993, NIST stated that DES was beginning to outlive its usefulness. It began looking for candidates to replace it. This new standard was to be referred to as the Advanced Encryption Standard (AES).
AES was to be the long-term replacement, but something else was needed to fill the gap before AES was ready to be deployed. Therefore, to extend the usefulness of the DES encryption standard, 3DES was adopted. It can use two or three keys to encrypt data, depending on how it is implemented. It has an effective key length of 112 or 168 bits, and it performs 48 rounds of transpositions and substitutions. Although it is much more secure, it is as slow as one-third the speed of 56-bit DES.
Rijndael and the Advanced Encryption Standard
Rijndael is a block cipher adopted by NIST as the AES to replace DES. In 2002, NIST chose Rijndael to replace DES. Its name is derived from its two developers, Vincent Rijmen and Joan Daemen. It is a fast, simple, robust encryption mechanism. Rijndael is also known to resist various types of attacks.
The Rijndael algorithm uses three layers of transformations to encrypt and decrypt blocks of message text:
- Linear mix transform
- Nonlinear transform
- Key addition transform
Rijndael uses a four-step, parallel series of rounds. Rijndael is an iterated block cipher that supports variable key and block lengths of 128, 192, or 256 bits:
- If both key and block size are 128 bits, there are 10 rounds.
- If both key and block size are 192 bits, there are 12 rounds.
- If both key and block size are 256 bits, there are 14 rounds.
Each of the following steps is performed during each round:
- Byte substitution: Each byte is replaced by an s-box substitution.
- Shift row: Bytes are arranged in a rectangle and shifted.
- Mix column: Matrix multiplication is performed based on the arranged rectangle.
- Add round key: Each byte of the state is combined with the round key.
On the last round, the fourth step is bypassed, and the first step is repeated.
ChaCha
ChaCha is a stream cipher developed by D.J. Bernstein in 2008. It is used as the core of the SHA-3 finalist, BLAKE. ChaCha20 consists of 20 rounds. ChaCha is used for improved mobile device browser performance while using the Internet. Engineers from Google needed a fast and secure stream cipher to add to TLS to provide a battery-friendly alternative to AES for mobile devices. ChaCha20-Poly1305 was included in Chrome 31 in November 2013, and Chrome for Android and iOS at the end of April 2014.
For more information, visit https://cr.yp.to/chacha/chacha-20080128.pdf.
Salsa20
Salsa20 is a stream cipher and was the precursor to ChaCha. Salsa can expand a 256-bit key into 264 randomly accessible streams of 264 randomly accessible 64-byte (512-bit) blocks.
International Data Encryption Algorithm
The International Data Encryption Algorithm (IDEA) is a 64-bit block cipher that uses a 128-bit key. It is different from others, as it avoids the use of s-boxes or lookup tables. Although IDEA is patented by a Swiss company, it is freely available for noncommercial use. It is considered a secure encryption standard, and there have been no known attacks against it. Like DES, it operates in four distinct modes. At one time, it was thought that IDEA might replace DES, but patent royalties made that impractical.
Rivest Cipher Algorithms
The RC cipher algorithm series is part of a family of ciphers designed by Ron Rivest. Rivest ciphers include RC2, RC3, RC4, RC5, and RC6. RC2 is an older algorithm that maintains a variable key size, 64-bit block cipher that can be used as a substitute for DES. RC3 was broken as a cipher as it was being developed. So, RC3 was never actually used. RC4 was implemented as a stream cipher. The 40-bit version is what was originally available in WEP. It is most commonly found in the 128-bit key version. RC5 is a block cipher in which the number of rounds can range from 0 to 255, and the key can range from 0 bits to 2,048 bits in size. Finally, there is RC6. It features variable key size and rounds, and it added two features not found in RC5: integer multiplication and 4-bit working registers.
Counter Mode
Counter mode uses an arbitrary number that changes with each individual block of text encrypted. The counter is encrypted with the cipher, and the result is XOR'd into ciphertext. The lack of interdependency also means that the CTR mode is tolerant to a loss in blocks. The CTR mode is considered to be very secure and efficient for most purposes. Two ways it can be used are as follows:
- Counter (CTR) mode is similar to OFB since it turns a block mode into a stream cipher. Unlike OFB, CTR can be a mode of operation for either DES or AES.
- Galois/Counter (GCM) mode is unique to AES (AES-GCM). GCM is an authenticated encrypted mode (meaning it offers confidentiality and authentication) with a block size of 128 bits.
Asymmetric Encryption
Symmetric encryption does offer speed, but if you're looking for a cryptographic system that provides easy key exchange, you will have to consider asymmetric encryption. Asymmetric encryption, or public key cryptography, is different from symmetric encryption. It overcomes one of the big barriers of symmetric encryption: key distribution. Asymmetric encryption uses two unique keys, as shown in Figure 6.4. What one key does, the other key undoes.
Here's how asymmetric encryption works: Imagine that you want to send a co-worker a message. You use your co-worker's public key to encrypt the message. Your co-worker receives the message and uses a private key to decrypt it.

FIGURE 6.4 Asymmetric encryption
Public key cryptography is made possible by the use of one-way functions. A one-way function, or trapdoor, is a math operation that is easy to compute in one direction, yet it is almost impossible to compute in the other direction. Depending on the type of asymmetric encryption used, this difficulty is based on either the discrete logarithm problem or the factoring of a large number into its prime factors. Although the math behind the encryption process is not needed to pass the CASP+ exam, in algebra, discrete logarithms are group-theoretic analogs of ordinary logarithms. For example, if you are given two large prime numbers, it is easy to multiply them. However, if you are given only their product, it is difficult or impossible to find the factors with today's processing power. Asymmetric systems may also make use of a zero-knowledge proof. This concept allows you to prove your knowledge without revealing the fact to a third party.
If the message is encrypted with the public key, only the matching private key will decrypt it. The private key is kept secret, whereas the public key can be given to anyone. If the algorithm is properly designed, it should not be possible for someone to easily deduce the private key of a pair if that person has only the public key.
Consider the following example of asymmetric encryption: given the prime numbers 397 and 823, it is easy to multiply them together and get 326,731. However, if you are given the number 326,731, it's quite difficult to extract the two prime numbers, 397 and 823. Anyone who knows the trapdoor can perform the function in both directions, but if you are lacking the trapdoor, you can perform the function in only one direction. Trapdoor functions can be used in the forward direction for encryption and signature verification, whereas the inverse direction is used for decryption and signature generation.
To help ensure your success on the CASP+ exam, Table 6.1 compares symmetric and asymmetric cryptographic systems.
TABLE 6.1 Attributes of symmetric and asymmetric encryption
| Symmetric | Asymmetric |
|---|---|
| Confidentiality | Confidentiality, integrity, authentication, and nonrepudiation |
| One single shared key | Two keys: public and private |
| Requires an out-of-band exchange | Useful for in-band exchange |
| Not scalable; too many keys needed | Scalable; works for e-commerce |
| Small key size and fast | Larger key size required, and slower to process |
| Useful for bulk encryption | Best for small amounts of data, digital signatures, digital envelopes, and digital certificates |
Diffie–Hellman
Dr. W. Diffie and Dr. M.E. Hellman released the first public key-exchange protocol in 1976. They developed it specifically for key exchange and not for data encryption or digital signatures. The Diffie–Hellman protocol was designed to allow two users to exchange a secret key over an insecure channel without any prior communication. The protocol functions with two system parameters: p and g. Both parameters are public and can be used by all of the system's users. Parameter p is a prime number, and parameter g, which is usually called a generator, is an integer less than p that has the following property: for every number n between 1 and p – 1 inclusive, there is a power k of g such that gk = n mod p. Diffie–Hellman is used in conjunction with several authentication methods, including the Internet Key Exchange (IKE) component of IPsec.
Diffie–Hellman was groundbreaking in its ability to allow two parties to exchange encryption keys securely, but it is not without its problems. It is vulnerable to on-path, formerly known as man-in-the-middle (MitM), attacks because the key exchange process does not authenticate the participants. You should use digital signatures to alleviate this vulnerability.
Elliptic-curve Diffie–Hellman (ECDH) works nearly the same but adds algebraic curves to generate keys to be used by the parties. Both participating parties have to previously agree on a specific elliptic curve. ECDH is much faster than using the large numbers required in normal DH, and the ECDH discrete logarithm problem is harder to solve than the normal discrete logarithm problem. This means smaller keys can be used with ECDH.
RSA
The RSA algorithm is named after its inventors. Ron Rivest, Adi Shamir, and Len Adleman developed RSA in 1977. Although RSA, like other asymmetric algorithms, is slower than symmetric encryption systems, it offers secure key exchange and is considered very secure. RSA supports a key size up to 3,072 bits. The design of RSA is such that it has to use prime numbers whose product is much larger than 129 digits for security; 129-digit decimal numbers are factored using a number field sieve algorithm. RSA public and private keys are generated as follows:
- Choose two large prime numbers, p and q, of equal length and compute p × q = n, which is the public modulus.
- Choose a random public key, e, so that e and (p – 1)(q – 1) are relatively prime.
- Compute e × d = 1 mod [(p – 1)(q – 1)], where d is the private key.
- Thus, d = e–1 mod [(p – 1)(q – 1)].
From these calculations, (d, n) is the private key, and (e, n) is the public key. The plain text, P, is encrypted to generate cipher text, C, as follows:
and is decrypted to recover the plain text, P, as follows:
RSA functions by breaking the plain text into equal-length blocks, with each block having fewer digits than n. Each block is encrypted and decrypted separately. Anyone attempting to crack RSA would be left with a tough challenge because of the difficulty of factoring a large integer into its two factors. Cracking an RSA key would require an extraordinary amount of computer processing power and time. The RSA algorithm has become the de facto standard for industrial-strength encryption, especially since the patent expired in 2000. It is built into many protocols, such as PGP; software products; and systems such as Mozilla Firefox, Google Chrome, and Microsoft Edge.
Elliptic Curve Cryptography
In 1985, two mathematicians, Neal Koblitz from the University of Washington and Victor Miller from IBM, independently proposed the application of elliptic curve cryptography (ECC) theory to develop secure cryptographic systems.
ECC can be found in smaller, less powerful devices such as smartphones and handheld devices. ECC is considered more secure than some of the other asymmetric algorithms because elliptic curve systems are harder to crack than those based on discrete log problems. Elliptic curves are usually defined over finite fields such as real and rational numbers, and they implement an analog to the discrete logarithm problem.
The strengths of various key lengths also vary greatly according to the cryptosystem you're using. For example, a 1,024-bit RSA key offers approximately the same degree of security as a 160-bit ECC key. ECC using a 256-bit key would require a 3,072-bit RSA key to achieve equivalent protection.
By increasing the bit key to 384, the security ECC would give is very strong. Longer keys are certainly more secure, but they also require more computational overhead. It's the classic trade-off of resources versus security constraints.
Any elliptic curve can be defined by the following equation:
In this equation, x, y, a, and b are all real numbers. Each elliptic curve has a corresponding elliptic curve group made up of the points on the elliptic curve along with the point O, located at infinity. Two points within the same elliptic curve group (P and Q) can be added together with an elliptic curve addition algorithm. This operation is expressed as follows:
This problem can be extended to involve multiplication by assuming that Q is a multiple of P, meaning the following:
Computer scientists and mathematicians believe that it is extremely hard to find x, even if P and Q are already known. This difficult problem, known as the elliptic curve discrete logarithm problem, forms the basis of elliptic curve cryptography.
ElGamal
ElGamal was released in 1985, and its security rests in part on the difficulty of solving discrete logarithm problems. It is an extension of the Diffie–Hellman key exchange. ElGamal consists of three discrete components: a key generator, an encryption algorithm, and a decryption algorithm. It can be used for digital signatures, key exchange, and encryption.
Hybrid Encryption and Electronic Data Exchange (EDI)
Sometimes mixing two things together makes good sense. Do you remember the commercial, “You got your chocolate in my peanut butter?” While you may not consider cryptography as tasty as chocolate, there is a real benefit to combining symmetric and asymmetric encryption. Symmetric encryption is fast, but key distribution is a problem. Asymmetric encryption offers easy key distribution, but it's not suited for large amounts of data. Combining the two into hybrid encryption uses the advantages of each and results in a truly powerful system. Public key cryptography is used as a key encapsulation scheme, and the private key cryptography is used as a data encapsulation scheme. Here is how the system works. If Bob wants to send a message to Alice, the following occurs:
- Bob generates a random private key for a data encapsulation scheme. This session key is a symmetric key.
- The data encapsulation happens when Bob encrypts the message using the symmetric key that was generated in step 1.
- The key encapsulation happens when Bob encrypts the symmetric key using Alice's public key.
- Bob sends both of these items, the encrypted message and the encrypted key, to Alice.
- Alice uses her private key to decrypt the symmetric key and then uses the symmetric key to decrypt the message.
Almost all modern cryptographic systems make use of hybrid encryption. This method works well because it uses the strength of symmetric encryption and the key exchange capabilities of asymmetric encryption. Some good examples of hybrid cryptographic systems are IPsec, Secure Shell, Secure Electronic Transaction, Secure Sockets Layer, PGP, and Transport Layer Security. With hybrid systems, can we achieve perfect secrecy? This depends on items such as the algorithm, how the key is used, and how well keys are protected. The concept of perfect forward secrecy (PFS) refers to the goal of ensuring that the exposure of a single key will permit an attacker access only to data protected by a single key. To achieve PFS, the key used to protect transmission of data cannot be used to create any additional keys. Also, if the key being used to protect transmission of data is derived from some other keying material, that material cannot be used to create any additional keys.
For data in transit, Electronic Data Interchange (EDI) may be used. However, EDI is losing ground and being replaced with Transaction Processing over XML (TPoX). EDI was designed specifically for security and to bridge the gap between dissimilar systems. EDI is used to exchange data in a format that both the sending and receiving systems can understand. ANSI X12 is the most common of the formats used. EDI offers real benefits for organizations, as it reduces paperwork and results in fewer errors because all information is transmitted electronically.
Although EDI eases communication, it must be implemented with the proper security controls. Luckily, EDI has controls that address the issue of security as well as lost or duplicate transactions and confidentiality. The following list includes some common EDI controls:
- Transmission controls to validate sender and receiver
- Manipulation controls to prevent unauthorized changes to data
- Authorization controls to authenticate communication partners
- Encryption controls to protect the confidentiality of information
EDI adds a new level of concern to organizations because documents are processed electronically. One major concern with EDI is authorization. This means that EDI processes should have an additional layer of application control.
Public Key Infrastructure Hierarchy
Public key infrastructure (PKI) allows two parties to communicate even if they were previously unknown to each other. PKI makes use of users, systems, and applications. It allows users that are previously unknown to each other to communicate over an insecure medium such as the Internet. The most common system of using PKI is that of a centralized certificate authority. Applications that make use of PKI commonly use X.509 certificates.
PKI facilitates e-commerce. Consider how different dealing with brick-and-mortar businesses is from transactions over the Internet. Dealing with brick-and-mortar businesses gives you plenty of opportunity to develop trust. After all, you can see who you are dealing with, talk to the employees, and get a good look at how they do business.
In the modern world of e-commerce, transactions are much less transparent. You may not be able to see with whom you are dealing, yet you might have full trust in them. PKI addresses these concerns and brings trust, integrity, and security to electronic transactions.
One nontechnical issue with key distribution is controlling access to keys. Any PKI system has to be carefully controlled to ensure that the wrong individuals don't get access to secret keys.
From a user's perspective, PKI may look seamless, yet in reality it is made up of many components. PKI consists of hardware, software, and policies that manage, create, store, and distribute keys and digital certificates. The basic components of PKI are as follows:
- The certificate authority (CA)
- The registration authority (RA)
- The certificate revocation list (CRL)
- Digital certificates
- A certificate distribution system
Certificate Authority
The certificate authority (CA) is like a passport office. The passport office is responsible for issuing passports, and passports are a standard for identification for anyone wanting to leave the country. Like passport offices, CAs vouch for your identity in a digital world. VeriSign, Thawte, and Entrust are some of the companies, or trusted providers, which perform CA services. The most commonly used model is the hierarchical trust model. Figure 6.5 shows an example of this model. In small organizations, a single trust model may be used. Its advantage is that it's not as complex and has less overhead than the hierarchical trust model.
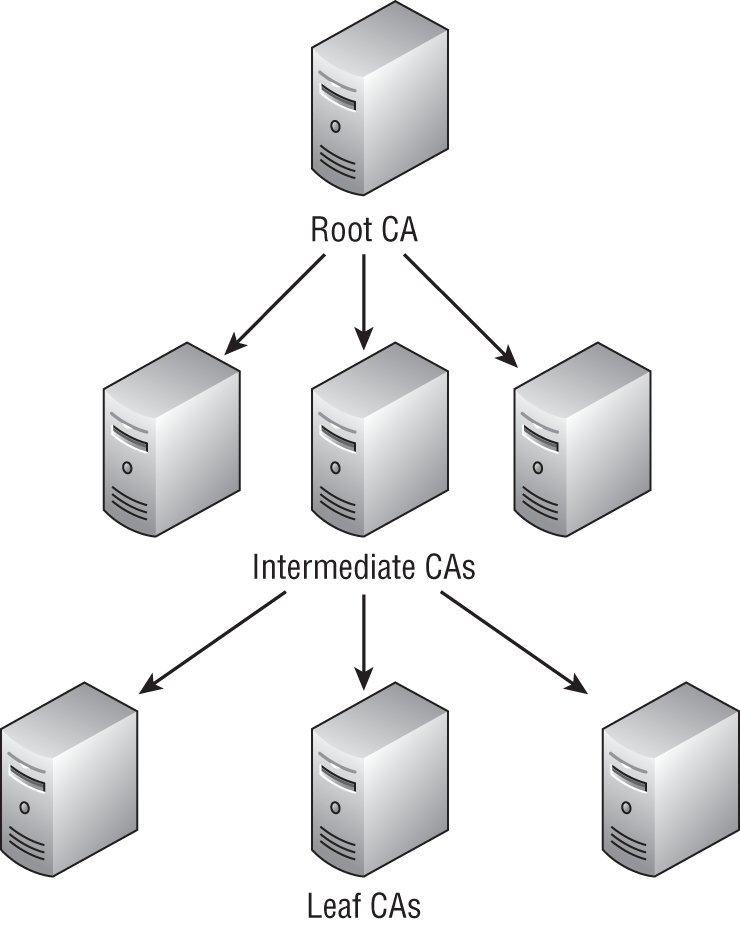
FIGURE 6.5 Hierarchical trust model
Although the companies mentioned are external CAs, some organizations may also decide to tackle these responsibilities by themselves. Regardless of who performs the services, the following steps are required:
- The CA verifies the request for a certificate with the help of the registration authority.
- The individual's identification is validated.
- A certificate is created by the CA, which verifies that the person matches the public key that is being offered.
Certificate profiles can offer end devices the certificates to avoid having to manually install the certificates. The end device may be a client workstation or server in order to expedite server authentication or client authentication.
Subordinate and Intermediate Certificate Authorities
As the name implies, a subordinate certification authority is one step lower in the CA hierarchy. In terms of the hierarchy, the top-level CA is also called the root CA. The root CA is at the highest level, while a certificate authority that requests and authorizes certificates from the root CA is called the subordinate CA. While there is only one root CA in the hierarchy, there may be several subordinate CAs. Beneath the subordinate CA would be the certificate issued to services, users, or devices.
One more type of certificate authority is the intermediate CA. An intermediate CA is a subordinate CA that may have one or more subordinate CAs beneath it.
Cross-Certification
Let's use the example of an enterprise organization, where it may include multiple PKI solutions. This may be the case for scalability or efficiency reasons. With multiple PKI implementations, it can be beneficial for a CA of one PKI to trust the certificates from the second PKI. Cross-certification is used for CAs to trust the issued certificates across PKIs. In the real world, cross-certification is in effect an example of federation, chaining together multiple PKI implementations. Federation certainly helps with efficiency and ease of use, but the reliability of the trust is dependent on every chain, every PKI. Any compromise of one PKI solution could cause a domino effect of damage across multiple PKIs.
Registration Authority
If the CA is like a passport authority, the registration authority (RA) is like a middleman. Think of it as one of the rush services that you can use when you need to get your passport right away. The RA is positioned between the client and the CA. Although the RA cannot generate a certificate, it can accept requests, verify a person's identity, and pass along the information to the CA for certificate generation.
RAs play a key role when certificate services are expanded to cover large geographic areas. One central private or corporate CA can delegate its responsibilities to regional RAs; for example, there might be one RA in the United States, another in Canada, another in Europe, and another in India.
Digital Certificates
Digital certificates are critical to the PKI process. The digital certificate serves two roles. First, it ensures the integrity of the public key and makes sure that the key remains unchanged and in a valid state. Second, it validates that the public key is tied to the stated owner and that all associated information is true and correct. The information needed to accomplish these goals is added to the digital certificate.
Digital certificates are formatted to the X.509 standard. The most current version of X.509 is version 3. One of the main developments in version 3 was the addition of extensions. This version includes the flexibility to support other topologies such as bridges and meshes. It can operate as a web of trust, much like PGP. An X.509 certificate includes the following elements:
- Version
- Serial number
- Algorithm ID
- Issuer
- Validity
- Not before (a specified date)
- Not after (a specified date)
- Subject
- Subject public key information
- Public key algorithm
- Subject public key
- Issuer-unique identifier (optional)
- Subject-unique identifier (optional)
- Extensions (optional)
Different entities can use a certificate. Issuance to entities identifies to whom the CA issues certificates. The certificate might be issued to a user, a system, or an application. The CA not only issues the certificate, but it also vouches for the authenticity of entities. It is not mandatory that you use an external CA to issue certificates, but they are widely used. An organization may decide to have itself act as a CA. Regardless of whether a third party handles the duties or your company performs them, digital certificates will typically contain the following critical pieces of information:
- Identification information that includes username, serial number, and validity dates of the certificates.
- The public key of the certificate holder.
- The digital signature of the signature authority. This piece is critical since it validates the entire package.
If you decide to use a third party to issue a certificate, there is a cost. These organizations are generally for-profit and will charge fees for you to maintain your certificate in good standing.
Certificate Revocation List
Let's compare Online Certificate Status Protocol (OCSP) with the certificate revocation list (CRL). Like passports, digital certificates do not stay valid for a lifetime. Certificates become invalid for many reasons, such as someone leaving the company, information changing, or a private key being compromised. For these reasons, the certificate revocation list (CRL) must be maintained.
The CRL is maintained by the CA, which signs the list to maintain its accuracy. Whenever problems are reported with digital certificates, the digital certificates are considered invalid and the CA has the serial number added to the CRL. Anyone requesting a digital certificate can check the CRL to verify the certificate's integrity. There are many reasons a certificate may become corrupted, including the following:
- The certificate expired.
- The DNS name or the IP address of the server changed.
- The server crashed and corrupted the certificate.
Certificate Types
There is the option for a browser or device to verify that a certificate hasn't been revoked. That revocation checking as an option, though, is changed to a strict requirement in the case of one type of certificate, the validation certificate.
Some organizations may choose to use wildcard certificates to cut costs. A wildcard certificate allows the purchaser to secure an unlimited number of subdomain certificates on a domain name. The advantage is that you buy and maintain only one certificate. The drawback, however, is that you are using just one certificate and private key on multiple websites and private servers. If just one of these servers or websites is compromised, all of the others under the wildcard certificate will be exposed.
A similarly beneficial option for secure multiple domains is the multidomain certificate. Unlike the wildcard, which secures multiple subdomains, the multidomain certificate will secure multiple websites. For example, a multidomain certificate could secure example.net, example.com, and example.org. The wildcard certificate could secure sub1.example.org, sub2.example.org, and sub3.example.org.
If a private key is exposed or another situation arises where a certificate must be revoked, PKI has a way to deal with such situations, that is, when a CRL is used. These lists can be checked via the Online Certificate Status Protocol (OCSP), an Internet protocol used for obtaining the revocation status of an X.509 digital certificate. This process is much the same as maintaining a driver's license. Mike may have a driver's license, yet if he gets stopped by a police officer, the officer may still decide to run a check on Mike's license; he's checking on the status of Mike's license in the same way that the OCSP is used to check on the status of an X.509 certificate.
Certificate Distribution
Certificates can be distributed by a centralized service or by means of a public authority. The use of a CA is an example of centralized distribution: a trusted CA distributes a public key to another party. The certificate is signed by means of a digital signature of the CA to prove it is valid. The certificates can be passed from one CA to another by using a chain of trust. A chain of trust provides a trust relationship between entities. See Figure 6.6 for an example.

FIGURE 6.6 An example of a chain of trust
A second way to distribute keys is directly through a third party. This is called a web of trust. For example, if you email us with a question about the book, our return emails will include our public key. It's an easy way to distribute keys, but it does not offer the level of trust that would be obtained from a third-party CA such as VeriSign or Thawte. PGP and GPG are examples of systems that provide encryption and can use web-of-trust certificate distribution.
- Tokens PKI tokens provide secure storage for digital certificates and private keys. They allow public-key cryptography and digital signatures to be leveraged securely without the risk of leaking the private key information. PKI tokens are hardware devices that store digital certificates and private keys securely. When you need to encrypt, decrypt, or sign something, the token does this internally in a secure chip, meaning that the keys are never at risk of being stolen.
- Stapling Online Certificate Status Protocol (OCSP) stapling or certificate stapling enhances performance of the website and privacy of the client. Prior to OCSP stapling, the OCSP request originates from a client to the CA server in order to validate an SSL certificate. OCSP stapling allows the certificate presenter to query the OCSP responder directly and then let them cache the response. This allows for a securely cached response, which is then delivered (“stapled”) with a TLS/SSL handshake via the Certificate Status Request extension response. This helps to ensure that the browser gets the same response performance for the certificate status as it does for the website content.
OCSP stapling also addresses a privacy concern with OCSP that the certificate authority no longer receives the revocation requests directly from the client (browser). OCSP stapling further addresses the concerns about OCSP SSL negotiation delays by removing the need for a separate network connection to a certification authority's responder.
- Pinning Certificate pinning is the technique of telling your browser of choice that only certificates with a specific public key somewhere in the certificate chain are to be trusted. Current implementations are based on trust on first use (TOFU), which means that your browser of choice will have to trust the connection the first time you use a site. This is because the pinning info is sent via an HTTP header by the web server. In the future, this can ideally be retrieved via DNSSEC-signed DNS records.
You pin the public key of a certificate. There are at least three certificates per site (site cert, intermediate cert, and root cert) that give you a few options on what to pin. Your site certificate will be replaced in the near future, commonly within three years, but it will most likely be replaced even before that due to reissues. You have no control over what intermediate certificate the CA will use on a reissue, so don't pin that. Certificate authorities have multiple root certs in trust stores, and you simply can't control which one they will use on reissues. You must rely on what you can control—your own public key in the certificate chain—so that is what you want to pin.
HTTP Public Key Pinning (HPKP) doesn't just let you provide a backup public key; it requires you to do so. This is useful when your private key gets compromised. Your backup key will then be used to generate a new certificate. The backup key should, of course, never be stored on the same infrastructure as your primary key, and it will never be used for anything else.
The Client's Role in PKI
Although the CA is responsible for a large portion of the work, in the world of PKI the client also has some duties. Clients are responsible for requesting digital certificates and for maintaining the security of their private key.
And even though certificates are issued, a client may still attempt to establish the connection insecurely. For example, if the user's browser were to initiate using HTTP instead of HTTPS. One solution is to redirect the browser to switch to HTTPS. This is done by setting up a 301 redirect directive on the server.
However, a malicious user would be able to capture traffic leading up to the redirect. The optimal solution would be to utilize HTTP Strict Transport Security (HSTS). When a web server directs the web browser to implement HSTS to only (strictly) utilize a secure connection starting with the browser, then this potential insecure capture is avoided.
Loss, compromise, or exposure of the private key would mean that communications are no longer secure. Protecting the private key is an important issue because for the attacker, it may be easier to target the key rather than to try to brute-force or crack the certificate service. Organizations should concern themselves with eight key management issues:
- Generation
- Distribution
- Installation
- Storage
- Recovery
- Change
- Control
- Disposal
Key recovery and control is an important issue that must be addressed. One basic recovery and control method is the m of n control method of access. This method is designed to ensure that no one person can have total control; it is closely related to dual control. If n administrators have the ability to perform a process, m of those administrators must authenticate for access to occur. M of n control should require physical presence for access.
Here is an example. Let's say that a typical m of n control method requires that four people have access to the archive server and that at least two of them must be present to accomplish access. In this situation, m = 2 and n = 4. This would ensure that no one person could compromise the security system or gain access.
Implementation of Cryptographic Solutions
Has this chapter got you thinking about all of the ways cryptography can be used and how valuable it is to a security professional? We hope that it has. The real question is, now that you're armed with some specific cryptographic solutions, how strong should the encryption be and where might you apply cryptographic solutions?
Encryption can be applied at the disk, block, file, record, and port:
- Disk Encryption Disk encryption can use either hardware or software to encrypt an entire hard drive or volume. Such technology is incredibly important today. Mobile security is especially enhanced by encryption, considering how much sensitive information individuals have stored on mobile devices and tablets. Such items are easily lost or stolen. Common disk encryption products include BitLocker and AxCrypt.
- Block Encryption Block encryption secures data in fixed-size groups of bits. An example of a block cipher that we have previously discussed is DES ECB. DES encrypts data in 64-bit blocks.
- File Encryption You don't have to encrypt an entire hard drive or volume. In some situations, you may simply need to encrypt specific files. Examples of products that can be used for file encryption include AxCrypt and PGP.
- Record Encryption Databases are a common area of attack. If you are storing sensitive information in a database, you may want to encrypt the entire database or just specific records. As an example of record encryption, in a medical facility you may want to protect records that hold Social Security numbers or other personal information, leaving only medical IDs and medical records open to the hospital staff.
- Port Encryption Some services are just more secure than others. As an example of port encryption, Telnet, TCP port 23, sends data in the clear, whereas Secure Shell, port 22, uses encryption. Another example is HTTP, as port 80 is clear text, whereas HTTPS uses port 443.
These examples demonstrate that cryptography is one of the most valuable tools that a security professional can use, but the trade-offs between strength, performance, and usability must be considered. Each cryptographic solution has strengths and limitations. Organizations must perform a proper risk assessment to determine the level of threat and the amount of protection that each asset requires. That assessment will go a long way in determining the type of technology used. Is the data something that is useful for only the next few minutes, like orders to buy or sell stock? Is the information top-secret data on the next generation of fighter jets that have yet to start production? Where is the data being stored? How valuable is it to someone else? How long is it likely to remain valuable?
Even if the information does not require cryptographic solutions to provide privacy, you may still need controls that can help safeguard the information. One such technology is digital rights management (DRM). DRM is an entire suite of technology designed to protect digital content. As an example, you may be reading a copy of this book on your tablet, yet that does not mean the publisher wants to provide free copies to 100 of your closest friends! That is the situation for which DRM is designed: it helps prevent copyright infringement online and thus helps the copyright holder maintain control of the information.
Next, you need to consider where to build in the protection. Cryptography can be used in many different situations to build a true defense in depth. If you think of cryptography in reference to the TCP/IP model, you can see where cryptographic solutions can be applied, from the application layer all the way down to the physical frame. Let's start at the top of the TCP/IP stack and work down through the layers, highlighting a few cryptographic solutions.
Application Layer Encryption
The following application layer protocols are just a few examples that can be used to add confidentiality, integrity, or nonrepudiation:
- Secure Shell Secure Shell (SSH) is an Internet application that provides secure remote access. It serves as a replacement for FTP, Telnet, and the Berkeley “r” utilities. SSH defaults to TCP port 22.
- Secure Hypertext Transfer Protocol
Secure Hypertext Transfer Protocol (S-HTTP) is a superset of HTTP that was developed to provide secure communication with a web server. S-HTTP is a connectionless protocol designed to send individual messages securely.
- Pretty Good Privacy Pretty Good Privacy (PGP) was developed in 1991 by Phil Zimmermann to provide privacy and authentication. Over time, it evolved into open standards such as OpenPGP and GnuPGP. PGP builds a web of trust that is developed as users sign and issue their own keys. The goal of PGP was for it to become the “everyman's encryption.” Popular programs such as HushMail, CounterMail, and K-9 Mail are based on PGP, providing end-to-end encryption.
- GNU Privacy Guard Does free sound good? If you are like many of us, the answer is yes, and that is where GNU Privacy Guard (GPG) comes into the equation. It is a licensed, free version of PGP. The idea was to provide a free version of PGP that everyone can use. Like PGP, GPG makes use of hybrid encryption and uses the best of both symmetric and asymmetric encryption. The symmetric portion is used for encryption and decryption, and the asymmetric portion is used for key exchange.
- S/MIME For those who prefer not to use PGP or GPG, there is another option for the security of email. That solution is S/MIME (Secure/Multipurpose Internet Mail Extensions). S/MIME is a standard for public key encryption and signing of MIME data. S/MIME provides two basic services: digital signatures and message encryption. S/MIME is a popular solution for securing email, and it is built into most email software programs, such as Microsoft Outlook and Mozilla Thunderbird.
- Secure Remote Access A variety of applications can be used for secure remote access, such as SSH, Remote Desktop Protocol (RDP), and Virtual Network Computing (VNC). RDP is a proprietary protocol developed by Microsoft. It provides the remote user with a graphical interface to the remote computer. VNC is like RDP in that it allows graphic access to a remote computer. VNC makes use of the Remote Frame Buffer (RFB) protocol to control another computer remotely.
Transport Layer Encryption
The transport layer of the TCP/IP stack can also be used to add cryptographic solutions to data communications. Some common examples follow:
- Secure Sockets Layer Netscape developed Secure Sockets Layer (SSL) for transmitting private documents over the Internet. SSL is application independent and cryptographically independent since the protocol itself is merely a framework for communicating certificates, encrypted keys, and data.
- Transport Layer Security The improved Transport Layer Security (TLS) is the successor protocol to SSL. It works in much the same way as the SSL, using encryption to protect the transfer of data and information. The two terms are often used interchangeably in the industry although SSL is still used.
Transport Layer Security (TLS) encrypts the communication between a host and a client. TLS consists of two layers: the Record Protocol and the TLS Handshake Protocol. Although TLS and SSL are functionally different, they provide the same services, and the terms are sometimes used interchangeably.
- Wireless Transport Layer Security Wireless Transport Layer Security (WTLS) encrypts the communication between a wireless host and a client. WTLS is a security protocol, and it is part of the Wireless Application Protocol (WAP) stack. WTLS was developed to address the problems, specifically the relatively low bandwidth and processing power, of mobile network devices. These issues will become increasingly important in the next few years as mobile banking is being widely used on smartphones.
Internet Layer Controls
The Internet layer is home to IPsec, a well-known cryptographic solution. IPsec was developed to address the shortcomings of IPv4. It is an add-on for IPv4. IPsec can be used to encrypt just the data or the data and the header. With the depletion of IPv4 addresses, look for more attention to be paid to IPsec as it is built into IPv6. IPsec includes the following components:
- Encapsulated Secure Payload (ESP) Encapsulated Secure Payload (ESP) provides confidentiality by encrypting the data packet. The encrypted data is hidden, so its confidentiality is ensured.
- Authentication Header (AH) The Authentication Header (AH) provides integrity and authentication. The AH uses a hashing algorithm and symmetric key to calculate a message authentication code. This message authentication code is known as the integrity check value (ICV). When the AH is received, an ICV is calculated and checked against the received value to verify integrity.
- Security Association (SA) For AH and ESP to work, some information must be exchanged to set up the secure session. This job is the responsibility of the Security Association (SA). The SA is a one-way connection between the two parties. If both AH and ESP are used, a total of four connections are required. SAs use a symmetric key to encrypt communication. The Diffie–Hellman algorithm is used to generate this shared key.
- Transport and Tunnel Mode AH and ESP can work in one of two modes: transport mode or tunnel mode. Transport mode encrypts the data that is sent between peers. Tunnel mode encapsulates the entire packet and adds a new IP header. Tunnel mode is widely used with VPNs. The AH and the ESP can be used together or independently of each other.
- Hardware Security Module (HSM) Actually a physical control rather than an Internet layer control, but many organizations use Hardware Security Modules (HSMs) to store and retrieve escrowed keys securely. Key escrow or key management allows another trusted party to hold a copy of a key. They need to be managed at the same security level as the original key. HSM systems can be used to protect enterprise storage and data, and they can detect and prevent tampering by destroying the key material if unauthorized access is detected.
Additional Authentication Protocols
While the following protocols are not on this CASP+ exam revision, they are all worth mentioning as many of us will, or have, come across them in our careers.
- Password Authentication Protocol (PAP) We have included Password Authentication Protocol (PAP) here, but it should not be used. It is weak at best. PAP is not secure because the username and password are transmitted in clear text.
- Challenge Handshake Authentication Protocol (CHAP) Challenge Handshake Authentication Protocol (CHAP) is a more suitable option than PAP because it sends the client a random value that is used only once. Both the client and the server know the predefined secret password. The client uses the random value, nonce, and the secret password, and it calculates a one-way hash. The handshake process for CHAP is as follows:
- The user sends a logon request from the client to the server.
- The server sends a challenge back to the client.
- The challenge is encrypted and then sent back to the server.
- The server compares the value from the client and, if the information matches, grants authorization.
- Extensible Authentication Protocol (EAP) The Extensible Authentication Protocol (EAP) is an authentication framework that is commonly used for wireless networks. Many different implementations exist that use the EAP framework, including vendor-specific and open methods like EAP-TLS, LEAP, and EAP-TTLS. Each of these protocols implements EAP messages using that protocol's messaging standards. EAP is commonly used for wireless network authentication.
Authentication is a critical component and is used as a first line of defense to keep hackers off your network. Systems such as federated ID, AD, and single sign-on can be used to manage this process more securely.
- Point-to-Point Tunneling Protocol (PPTP) Point-to-Point Tunneling Protocol (PPTP) consists of two components: the transport that maintains the virtual connection and the encryption that ensures confidentiality. It can operate at a 40-bit or a 128-bit length.
- Layer 2 Tunneling Protocol (L2TP)
Layer 2 Tunneling Protocol (L2TP) was created by Cisco and Microsoft to replace Layer 2 Forwarding (L2F) and PPTP. L2TP merged the capabilities of both L2F and PPTP into one tunneling protocol.
Cryptocurrency
Cryptocurrency is the medium of exchange similar to the U.S. dollar (USD) but designed for the purpose of exchanging digital information through a process made possible by certain principles of cryptography. Cryptocurrency uses cryptography to secure the digital transactions along with the ability to control the creation of new cryptocurrency coins. Cryptocurrency was first introduced as Bitcoin in 2009. Currently, there are hundreds of other known alternative cryptocurrencies, which are referred to as digital altcoins.
Cryptocurrency security is broken into two parts. The first part comes from the difficulty in finding the hash set intersection. This task is conducted by miners. The second and most common of the two cases is known as the 51 percent attack. Within this scenario, a miner has the power to mine more than 51 percent of the network. The miner can take control of the global blockchain ledger along with generating an alternative blockchain. At this point, the attacker is limited by the capabilities of their resources. The attack can also reverse the attacker's own transaction or even block other transactions.
The advantage of cryptocurrencies is that they are less susceptible to seizure by law enforcement or even the transaction holds placed on them from acquirers such as PayPal. Cryptocurrencies are all pseudo-anonymous, and some coins have added features to assist in creating true anonymity.
Digital Signatures
Digital signatures are a category of algorithms based on public key cryptography. They are used for verifying the authenticity and integrity of a message. To create a digital signature, the message is passed through a hashing algorithm. The resulting hashed value is then encrypted with the sender's private key. Upon receiving the message, the recipient decrypts the encrypted sum and then recalculates the expected message hash using the sender's public key. The values must match to prove the validity of the message and verify that it was sent by the party believed to have sent it. Digital signatures work because only that party has access to the private key. Let's break this process out step-by-step to help detail the operation:
- Bob produces a message digest by passing a message through a hashing algorithm.
- The message digest is then encrypted using Bob's private key.
- The message is forwarded to the recipient, Alice.
- Alice creates a message digest from the message with the same hashing algorithm that Bob used. Alice then decrypts Bob's signature digest by using Bob's public key.
- Finally, Alice compares the two message digests: the one originally created by Bob and the other one that she created. If the two values match, Alice can rest assured that the message is unaltered.
Figure 6.7 illustrates the creation process. It shows how the hashing function ensures integrity and how the signing of the hash value provides authentication and nonrepudiation.
FIGURE 6.7 Digital signature creation
To help ensure your success on the CASP+ exam, integrity verification methods are reviewed in Table 6.2.
TABLE 6.2 Integrity verification methods
| Method | Description |
|---|---|
| Parity | Simple error detection code |
| Hashing | Integrity |
| Digital signature | Integrity, authentication, and nonrepudiation |
| Hashed MAC | Integrity and data origin authentication |
| CBC MAC | Integrity and data origin authentication |
| Checksum | Redundancy check, weak integrity |
Recognizing Cryptographic Attacks
As long as there have been secrets, there have been people trying to uncover them. Attacks on cryptographic systems are nothing new. The formal name for this activity is cryptanalysis, which is the study of analyzing cryptography and attempting to determine the key value of a cryptographic system. Depending on which key is targeted by the attacker, it's possible that success may mean that someone could gain access to confidential information or pretend to be an authenticated party to a communication.
There are many ways an attacker can target a system for attack, such as a brute-force attack. A brute-force attack tries all possible solutions. One technique to make the attacker work longer and harder to perform a brute-force attack is key stretching. Key stretching refers to cryptographic techniques used to make a possibly weak cryptographic system, such as password generation, more secure. This technique hashes a password along with a random value known as a salt. This process can be repeated many times to produce a derived key. Typically, this might be a thousand or more iterations. This approach makes brute-force attacks time-consuming for an attacker. However, remember the previous discussion about the trade-off between strength, performance, and usability? Although it is more secure, the increased number of iterations will require more CPU power and time.
Password-based key derivation 2 (PBKDF2) is defined in RFC 2898. PBKDF2 is a specific key derivation function (KDF). A KDF is way to take a password and turn it into a symmetric key for cryptographic operations such as AES. AES can use any value as its input that meets certain length and entropy requirements. PBKDF2 can produce a hash of any length that meets those requirements for entropy.
PBKDF2 takes a password, a salt, an integer defining how many rounds of the hash function to undergo, and another integer describing the desired key length for the output. By increasing the number of rounds, you make the resulting output more computationally expensive. A use case of PBKDF2 is a means of hashing a password to avoid storing a plaintext password in a database.
The Bcrypt algorithm is based on the Blowfish cipher. Bcrypt helps in preventing the brute-force search attacks by increasing the number of rounds. The computation cost of the algorithm depends on parameterized rounds, so it can be increased as computers evolve. Just like PBKDF2, this method uses a salt to protect against rainbow table attacks.
Many countries seek to control cryptographic algorithms and place controls on their use. These controls fall under the Wassenaar Arrangement on Export Controls for Conventional Arms and Dual-Use Goods and Technologies (see www.wassenaar.org). The goal of the agreement is to promote transparency in transfers of conventional arms and dual-use goods and technologies while also promoting greater responsibility in such transfers. The idea is to keep strong cryptography out of the hands of criminals and terrorists.
Troubleshooting Cryptographic Implementations
There will be problems to troubleshoot. Guaranteed you've browsed to a website only to get the warning “Your connection is not private,” offering you a Back to Safety button.
Sometimes the evidence points to one of the configuration problems, but in reality, the issue is much simpler. Keep in mind the troubleshooting acronym KISS, which stands for “keep it simple, stupid.” For example, an incorrect certificate name error may just be caused by a browser cache or a bad browser plug-in. Try simple troubleshooting first, such as clearing the cache or testing in incognito mode, before immediately reconfiguring the corporate certificate authority.
Figure 6.8 is the warning screen expected when there is a certificate error.

FIGURE 6.8 “Your connection is not private” error
Let's start by recognizing some of the more common certificate issues.
- Validity Dates This is an easy one. Did the certificate expire? Was it post-dated like the rent check? Check the dates. If the valid dates of the certificate are outside the server's date and time, then the certificate is considered invalid. Of course, the real issue could be the server's date and time is wrongly set.
These are some basic ways to troubleshoot invalid SSL/TLS errors:
- Check the date on your computer. First you should check if the date and time on your computer is correct.
- Check for configuration errors.
- Check for domain mismatch.
- Get your certificate from a reliable CA.
- Check the certificate structure.
- Check for revocation.
- Wrong Certificate Type It goes beyond the CASP+ exam to differentiate between these validation levels of SSL certificates: domain validated (DV), organization validated (OV), and extended validation (EV).
However, if, for example, a single domain certificate were issued when a multidomain certificate was required, then this would fall under the blanket error category of “wrong type.”
- Revoked Certificates Illegally purchased or wrongly issued certificates can and will be revoked eventually. The same can happen if the private key is compromised. A CRL is a list of CA certificates that have been revoked before expiration, and these certificates should never be trusted.
- Incorrect Name “NET::ERR_CERT_COMMON_NAME_INVALID” is the error that does actually happen too often when the certificate is for a different domain. If the name on the SSL certificate isn't the same as in the browser address bar, prepare for the browser to point that out to every visitor.
Even something as innocuous as leaving off the “www.” when the certificate includes it can cause a name mismatch error.
- Chain Issues If the subordinate CA cannot reach the root CA, then the chain is broken. This issue may be fairly easy to spot, given the warnings, but may require online resources to troubleshoot. Free online services are the fastest way to test and validate the chain of trust.
- Invalid Root or Intermediate CAs If a certificate is installed without a valid chain of trust, the result is that the untrusted certificate's validity cannot be verified.
- Self-Signed If a certificate is installed without a valid chain of trust, the result is that the untrusted certificate's validity cannot be verified. In the case of a self-signed certificate, the chain of trust stops at the server.
Other issues will be more centered around the keys:
- Embedded Keys Some devices have the certificate embedded in the device. Maybe its processing power is limited, and maybe it's forced to rely on an outdated algorithm. These are issues to consider for embedded keys.
- Rekeying In PKI, rekeying is simply issuing a new certificate, but with all the old information as with the replaced certificate. This is not a renewal, which essentially extends the validity period of an old certificate (and the private key).
- Exposed Private Keys and Improper Key Handling Once the secret key is out, all confidentiality and integrity are compromised. It's safe to say that proper key handling is a critical element to maintaining a PKI implementation.
- Crypto Shredding Crypto shredding is intentionally deleting an encryption key. The consequence is effectively permanently encrypting the data. In practice, this can be useful when a client wants their data “erased” or inaccessible forever. This brings up the challenge of maintaining unique keys to enable every possible such request.
But the risk is, deleting the encryption key doesn't mean the encrypted data is not available. Encrypted data doesn't stay unencrypted when attacked with enough brute force.
- Cryptographic Obfuscation Unlike encryption that renders something entirely unreadable, obfuscation is the method of masking the data's value by mixing it or modifying it with nonsensical data. This scrambles the input into something too challenging to understand or recover. This is not the same as the poor practice of “security by obscurity.” Obfuscation works best when the data is already fairly complex or not easily recovered. For instance, source code is unrecoverable with minimal obfuscation.
- Key Rotation Knowing when to rotate keys and certificates is based on their validity period. Interestingly enough, the maximum validity period has been contested and changed in recent years. In 2022, the maximum period is 825 days, but there is growing momentum to reduce it to 398 days.
In any case, key rotation must happen within those periods to maintain valid certificates and keys. And rotation can and should happen sooner if any compromise is detected.
- Compromised Keys The real danger of compromised keys is a malicious actor can now impersonate the intended source of the compromised certificate. The consequences of a malicious actor acting as the legitimate source can range from certified malware, decrypted communication, setting up on-path (formerly known as man-in-the-middle) attacks, forged traffic, and sniffing encrypted traffic. It's a bad thing.
Summary
This chapter focused on cryptography, a relatively deep component of the CASP+ content. While cryptography is on the CASP+ exam, it is also one of the most powerful tools of a security professional. It offers you the ability to protect sensitive information through the use of encryption. It can also offer you the ability to verify the integrity of patches, files, and important data. In addition, cryptography makes e-commerce possible. With cryptographic solutions such as PKI, you can trust that a third party is who they claim to be. These are but a few of the solutions cryptography offers.
As a security professional, you need to able to communicate with others about cryptographic solutions and services. You don't have to be able to write your own cryptographic algorithms. You do need to be able to offer solutions to real problems. There is not a week that goes by without a news report that lists stolen or lost media that contained personal information. As a security professional, you may be in a position to suggest that your company use full disk encryption (FDE) for all laptops. You may also have the opportunity to promote PGP as a standard to encrypt all email being used to discuss sensitive business matters. You may even be on a team preparing to roll out a new e-commerce site and be asked to offer your opinion on PKI. These are the types of solutions that security professionals offer every day.
Exam Essentials
Be able to describe which cryptographic solution is appropriate for a given situation. Cryptographic solutions can be broadly divided into symmetric encryption, asymmetric encryption, hybrid encryption, and hashing. Each offers specific solutions such as privacy, authentication, integrity, and nonrepudiation.
Be able to describe the basic operation of PKI and understand advanced PKI concepts. PKI allows two parties that are previously unknown to each other to communicate over an insecure public network. Such communications can then be used to exchange data securely and privately or for e-commerce. PKI systems make use of public and private keys. Keys are shared through a trusted certificate authority.
Know what terms such as wildcard mean when applied to PKI. A wildcard certificate allows the purchaser to secure an unlimited number of subdomain certificates on a domain name. The advantage is that you buy and maintain only one certificate. The drawback, however, is that you are using just one certificate and private key on multiple websites and private servers.
Be able to describe transport encryption. Transport encryption is one of the two modes in which IPsec can operate. When IPsec transport encryption is used, only the data portion or payload of each IP packet is encrypted. This leaves the IP header untouched and sent in the clear.
Be able to describe a digital signature. A digital signature is a hash value that has been encrypted with the private key of the sender. It is used for authentication and integrity.
Be able to describe hashing. Hashing refers to a broad category of algorithms that are useful for their ability to provide integrity and authentication. Hashing algorithms operate by taking a variable amount of data and compressing it into a fixed-length value referred to as a hash value.
Be able to describe code signing. Code signing is the process of digitally signing executables and scripts to confirm the software author. Code signing also guarantees that the code has not been altered or corrupted since it was signed by use of a hash.
Know how nonrepudiation works. Nonrepudiation is the ability to verify proof of identity. It is used to ensure that a sender of data is provided with proof of delivery and that the recipient is assured of the sender's identity.
Be able to define certificate authority hierarchy. Understand the relationship between the root, subordinate, and intermediate CAs. Understand the importance of the chain of trust.
Be able to explain perfect forward secrecy. Perfect forward secrecy is based on the concept that the exposure of a single key will permit an attacker access only to data protected by a single key.
Recognize and understand PKI implementation issues. There are several configuration problems that can arise from poorly implemented PKI. Recognize the errors you might encounter and how to decipher them. Remember that troubleshooting begins with verifying the simple issues first.
Review Questions
You can find the answers in Appendix.
- You have been asked by a member of senior management to explain the importance of encryption and define what symmetric encryption offers. Which of the following offers the best explanation?
- Nonrepudiation
- Confidentiality
- Hashing
- Privacy and authentication
- As the security administrator for your organization, you must be aware of all types of hashing algorithms. Which fast-block algorithm was developed by Ron Rivest and offers a 128-bit output?
- Salsa20
- 3DES
- CHACHA
- RC5
- A co-worker is concerned about the veracity of a claim because the sender of an email denies sending it. The co-worker wants a way to prove the authenticity of an email. Which would you recommend?
- Hashing
- Digital signature
- Symmetric encryption
- Asymmetric encryption
- A junior administrator at a sister company called to report a possible exposed private key that is used for PKI transactions. The administrator would like to know the easiest way to check whether the lost key has been flagged by the system. What are you going to recommend to the administrator?
- Hashing
- Issuance to entities
- Adding to RA
- Wildcard verification
- You've discovered that an expired certificate is being used repeatedly to gain logon privileges. To what list should the certificate have been added?
- Wildcard verification
- Expired key revocation list
- Online Certificate Status Department
- Certificate revocation list (CRL)
- A junior administrator comes to you in a panic after seeing the cost for certificates. She would like to know if there is a way to get one certificate to cover all domains and subdomains for the organization. What solution can you offer?
- Wildcards
- Blanket certificates
- Distributed certificates
- No such solution exists
- Which of the following is not an advantage of symmetric encryption?
- It's powerful.
- A small key works well for bulk encryption.
- It offers confidentiality.
- Key exchange is easy.
- Most authentication systems make use of a one-way encryption process. Which of the following offers the best example of one-way encryption?
- Asymmetric encryption
- Symmetric encryption
- Hashing
- PKI
- Which of the following algorithms would serve to prove the integrity of a file?
- RSA
- Diffie–Hellman
- SHA-256
- ECC
- Which type of encryption offers the easiest key exchange and key management?
- Symmetric
- Asymmetric
- Hashing
- Digital signatures
- SSL and TLS can best be categorized as which of the following?
- Symmetric encryption systems
- Asymmetric encryption systems
- Hashing systems
- Hybrid encryption systems
- Which is the type of certificate to use for securing these example domains:
snakes.pets.com,budgies.pets.com, andchinchillas.pets.com?- Wildcard
- Multidomain
- Validation
- CRL
- Which of the following is not a hashing algorithm?
- SHA-512
- ECDH
- Skipjack
- IDEA
- A mobile user calls you from the road and informs you that he has been asked to travel to China on business. He wants suggestions for securing his hard drive. What do you recommend he use?
- S/MIME
- BitLocker
- Secure SMTP
- PKI
- You were given a disk full of applications by a friend but are unsure about installing a couple of the applications on your company laptop. Is there an easy way to verify if the programs are original or if they have been tampered with?
- Verify with a hashing algorithm.
- Submit to a certificate authority.
- Scan with symmetric encryption.
- Check the programs against the CRL.
- What is the correct term for when two different files are hashed and produce the same hashed output?
- Session key
- Digital signature
- Message digest
- Collision
- You have been asked to suggest a simple trust system for distribution of encryption keys. Your client is a three-person company and wants a low-cost or free solution. Which of the following would you suggest?
- Single authority trust
- Hierarchical trust
- Spoke/hub trust
- Web of trust
- Which of the following would properly describe a system that uses a symmetric key distributed by an asymmetric process?
- Digital signature
- Hybrid encryption
- HMAC
- Message digest
- A CASP+ must understand the importance of encryption and cryptography. It is one of the key concepts used for the protection of data in transit, while being processed, or while at rest. With that in mind, 3DES ECB is an example of which of the following?
- Disk encryption
- Block encryption
- Port encryption
- Record encryption
- Which of the following can be used to describe a physical security component that is used for cryptoprocessing and can be used to store digital keys securely?
- HSM
- TPM
- HMAC
- OCSP
