Chapter 5
Compliance and Vendor Risk
This chapter discusses securing shared cloud computing. Cloud computing has come a long way in the last 10 to 15 years, and it can be found everywhere today. Cloud computing is changing the concept of network boundaries.
In this chapter, we'll look at both the advantages and disadvantages of virtualization and cloud computing as well as the concerns that they raise for enterprise security. We will also discuss compliance frameworks and legal considerations that can impact your organization, such as contract and agreement types. These topics are the items that CompTIA expects you to know for the exam.
Shared Responsibility in Cloud Computing
One area that can have a huge impact on enterprise security is cloud computing—using a remote datacenter to manage access to applications and host data. Cloud computing can include virtual servers, services, or anything you consume over the Internet. It is a concept that seeks to redefine consumption and delivery models for IT services, but one of the biggest challenges of cloud computing is confusion over who has what responsibility. Many organizations have experienced an incident or event of some kind due to the confusion over shared responsibility in cloud computing.
There are many different ways to deploy in the cloud. In a cloud computing environment, the end user may not know the location or details of a specific technology; it is fully managed by the cloud service provider (CSP). Cloud computing offers users the ability to increase capacity or add services as needed without investing in new datacenters, training new personnel, or maybe even licensing new software. This on-demand, or elastic, service can be added to upgraded, and provided at any time. Some of the largest CSPs are Amazon Web Services (AWS), Google Cloud Provider (GCP), Microsoft Azure, and IBM Cloud. Their services and costs vary, but as a whole, their options include storing, processing, and analyzing data; protecting data at rest and in motion; and offering a variety of developer tools to create applications in the cloud.
Cloud Service/Infrastructure Models
Cloud computing architecture depends on the CSP and can include various models. Public use services are provided by an external provider. Private use services are implemented internally in a cloud design. A hybrid architecture offers a combination of public and private cloud services to accomplish an organization's goals.
A CSP has several cloud models that can be broken into several basic designs that include infrastructure as a service, monitoring as a service, software as a service, and platform as a service. Each design is described here:
- Software as a Service Software as a service (SaaS) is designed to provide a complete packaged solution. The software is rented out to the user. The service is usually provided through some type of front end or web portal. While the end user is free to use the service from anywhere, the company pays a per-use fee. As an example,
www.salesforce.comoffers this type of service. - Platform as a Service Platform as a service (PaaS) provides a platform for your use. Services provided by this model include all phases of the software development life cycle (SDLC) and can use application programming interfaces (APIs), website portals, or gateway software. These solutions tend to be proprietary, which can cause problems if the customer moves away from the provider's platform. An example of PaaS is the G Suite; see
gsuite.google.com. - Infrastructure as a Service Infrastructure as a service (IaaS) describes a cloud solution where you are buying infrastructure. You purchase virtual power to execute your software as needed. This is much like running a virtual server on your own equipment, except that you are now running a virtual server on a virtual disk. This model is similar to a utility company model, as you pay for what you use. An example of this model is Amazon Web Services; see
aws.amazon.com.
In Figure 5.1 you see how these different tiers build upon one another.
Cloud Computing Providers and Hosting Options
A wide range of companies provide cloud computing services. Some well-known examples include Amazon, Citrix, Dropbox, Google, IBM, iCloud, Microsoft, Rackspace, and VMware. These providers offer a range of services that include the following:
- Public Clouds Available to the general public. An example would be Google Drive.
- Private Clouds Operated for a single company or entity. An example would be a company's private cloud storage of travel expenses.
- Hybrid Clouds A combination of a public and private cloud. An example would be a company's cloud storage of projects with varied access for internal employees and vendors.
- Community Clouds Shared between several organizations. An example would be cloud storage for a group of schools.
- Multitenancy Used to host a single software application that hosts multiple customers. An example would be a collaborative workspace for several project contributors.
- Single Tenancy Hosts a single software application designed to support one customer. An example would be a specialized HR application for one organization.
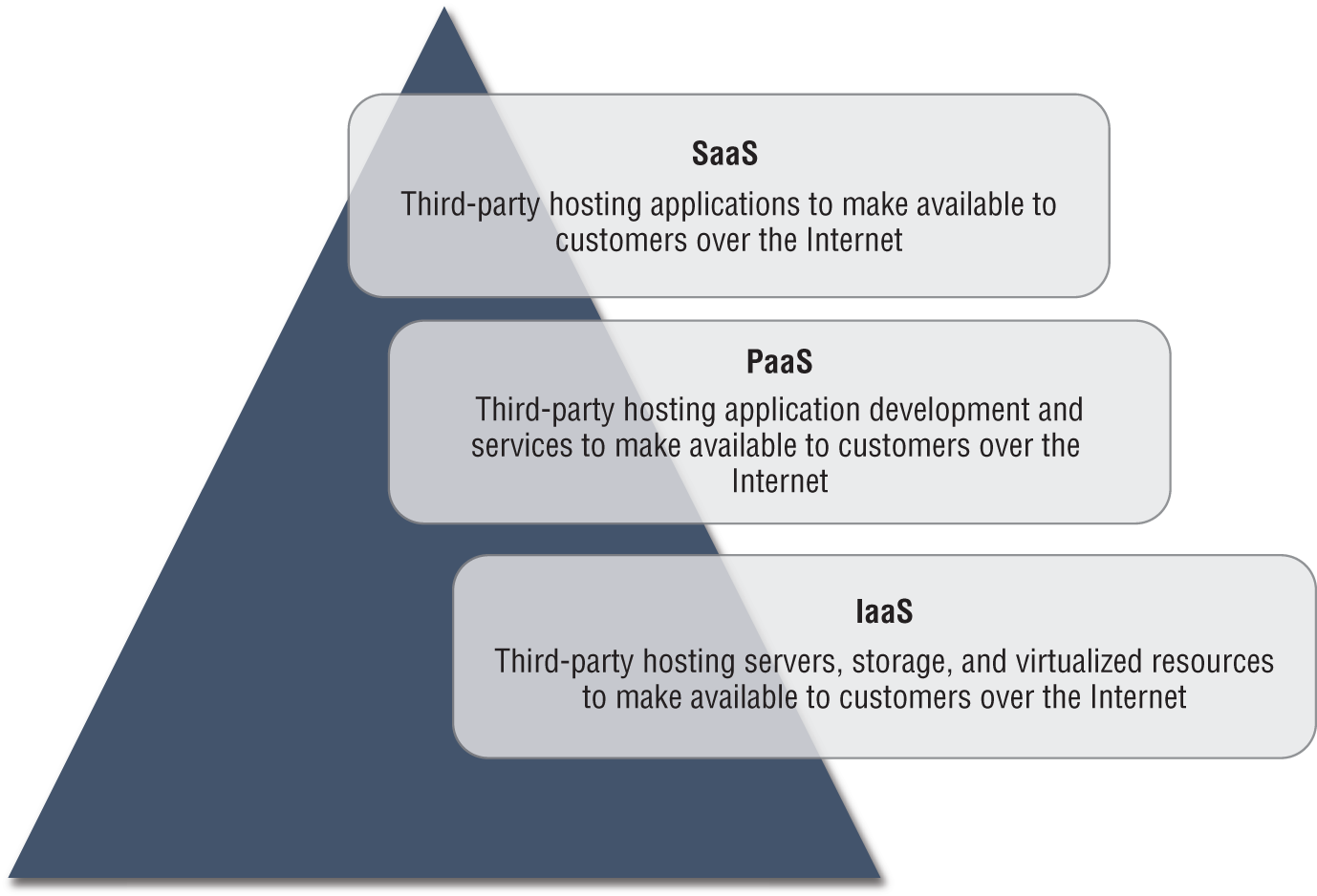
FIGURE 5.1 Layers of cloud computing
In Exercise 5.1 you will examine the benefits of cloud computing.
Benefits of Cloud Computing
On-demand, or elastic, cloud computing changes the way information and services are consumed and provided. Users can consume services at a rate that is set by their particular needs. Cloud computing offers several benefits, including the following:
- Reduces Cost Cloud technology saves procurement and maintenance of a company's own infrastructure and/or applications. Additionally, a cloud service is paid for as needed.
- Increases Storage
Cloud providers have more storage capability that is elastic and has lower costs.
- Provides a High Degree of Automation Fewer employees are needed because local systems have been replaced with cloud-based solutions. The user does not need IT personnel to patch and update servers that have been outsourced to the cloud.
- Offers Flexibility Cloud computing offers much more flexibility than local-based solutions.
- Provides More Mobility One of the big marketing plugs is that users can access their data anywhere rather than having to remain at their desks.
- Allows the Company's IT Department to Shift Focus No hardware updates are required by the company—the cloud provider is now responsible. Companies are free to concentrate on innovation.
The benefits of cloud computing are many. One of the advantages of cloud computing is the ability to use someone else's storage. Another advantage is that when new resources are needed, the cloud can be leveraged, and the new resources may be implemented faster than if they were hosted locally at your company. With cloud computing, you pay as you go. Another benefit is the portability of the application. Users can access data from work, from home, or at client locations. There is also the ability of cloud computing to free up IT workers who may have been tied up performing updates, installing patches, or providing application support. The bottom line is that all of these reasons lead to reduced capital expense, which is what all companies are seeking.
When making decisions about selecting a cloud computing or software vendor, there are other considerations such as legal requirements, change management, employee churn, and configurations. Prior to looking at available vendors, it is best to define the organization's needs and what the application or platform would do for you. Many businesses have complex business processes and regulatory requirements. Key legal or compliance requirement questions for vendor assessment should include the following:
- Security
- What type of encryption is being used?
- How and where is information stored?
- What measures are taken to prevent a data breach?
- If you go out of business, what type of source code escrow or repository will you have access to?
- Infrastructure
- Are there redundant backups in multiple locations?
- What type of supply chain visibility do you have?
- Network
- What type of systems are they using?
- When are updates applied?
- What type of tiered technical support do they offer?
- Is support offered 24/7 or only during business hours?
- Data
- Who controls the data in the event you no longer decide to use the vendor?
- Who has access to the data?
- What process is in place when an employee leaves the organization that your data is still safe?
- Where is the data stored geographically?
- Incident management and disaster recovery services
- What is the vendor's responsibility to notify you in the event of data breach or data loss?
- Do they have a disaster recovery plan?
- Compliance requirements
- What is done to protect confidential information?
- Is data stored in compliance with regulations such as GDPR, HIPAA, PCI DSS, or SOX?
Security of On-Demand/Elastic Cloud Computing
Although cost and ease of use are two great benefits of cloud computing, there are significant security concerns when considering on-demand/elastic cloud computing. As a typical rule, the cloud service provider (CSP) is responsible for security of the cloud, while the client is responsible for security of their information while in the cloud. In Figure 5.2, you see the distribution of responsibility of security based on the layers of cloud computing mentioned earlier.
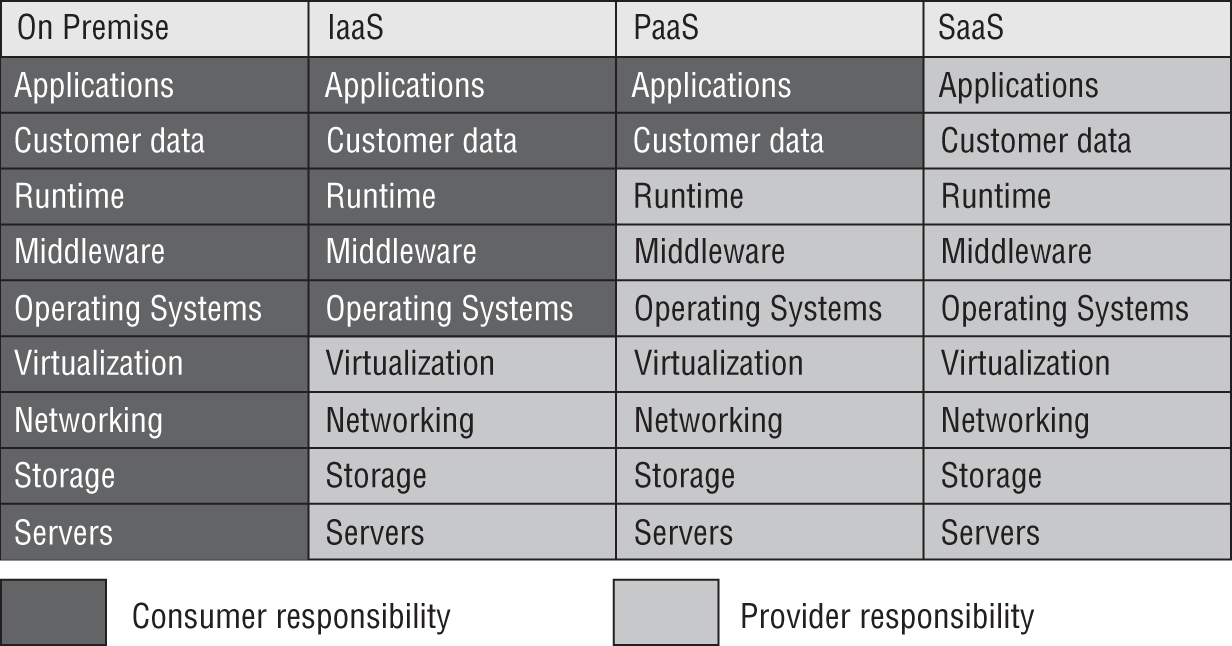
FIGURE 5.2 Distribution of security responsibility
Cloud computing is a big change from the way IT services have been delivered and managed in the past. One of the advantages is the elasticity of the cloud, which provides the online illusion of an infinite supply of computing power. Cloud computing places assets outside the owner's security boundary. Historically, items inside the security perimeter were trusted, whereas items outside were not. With cloud computing, an organization is being forced to place their trust in the cloud provider. The cloud provider must develop sufficient controls to provide the same level of security that the organization would have had if the cloud were not used—or a greater level.
You must be aware of the security concerns of moving to a cloud-based service. The pressures are great to make these changes, but there is always a trade-off between security and usability.
Geographic Location
The cloud exists on hard drives on individual servers found in datacenters and server farms globally. CSPs might be based in one country and their servers anywhere else on the globe. Nothing is stored locally on a machine. Cloud data is accessible from any location from many devices, anytime you need it. Security is of utmost importance, so much so that some organizations have compliance requirements or company policy specifying that data be hosted in datacenters that their country has legal control over.
Infrastructure
The cloud shared responsibility and security model varies from vendor to vendor. The confusion about how a CSP operates, as well as terminology used to describe service offerings across a diverse landscape, can be difficult when implementing a secure infrastructure built of hardware, software, and APIs. Hardware and software components include servers, storage, networking, and virtualization, and accessing these can be done a multitude of ways including IaaS, SaaS, and PaaS, all described in more detail earlier in the chapter.
Compute
As a rule, the CSP is responsible for the security of the cloud, and the customer is responsible for security in the cloud. The CSP is responsible for the physical security of the cloud servers, global infrastructure, and the virtualization layer, and the customer, depending on the platform and model, is responsible for the rest, including networking controls, access management, and customer data.
In cloud computing, the generic term compute describes the concepts related to software computation including processing power, memory, networking, and storage. In the case of the AWS shared responsibility model, compute falls under the purview of the CSP.
Storage
Shared responsibility requires excellent communication and understanding between the customer and the provider, especially when it comes to data storage. Storage in the cloud is ultimately the responsibility of the customer across all cloud models. Best practices for secure cloud storage include confirming there are no publicly accessible storage areas, data is in a life-cycle management program and being kept for the right amount of time, and encryption with customer-managed keys and object versioning is being enforced.
Networking
Many people are using the cloud in some way and some may be unaware they are doing so, which can put them at risk. Cybersecurity professionals use the confidentiality/integrity/availability (CIA) triad in the implementation of security controls within a cloud network. To secure cloud services, the first step is to use the strongest encryption available. Another best practice is to review the user agreements and understand how the service protects your information. When signing up for a cloud provider, configure the privacy settings to limit how long the service keeps data and what kind of information is stored. Privacy settings should be reviewed periodically because the cloud may update agreements, leaving a gap in security controls. Guides like CIS Benchmarks or the AWS Well-Architected Framework can help build the networking framework for a secure implementation.
These are other questions that a security professional should ask when considering cloud-based solutions:
- Does the data fall under regulatory requirements? Different countries have different requirements and controls placed on access. For example, organizations operating in the United States, Canada, or the European Union (EU) have many regulatory requirements. Examples of these include ISO 27002, Safe Harbor, Information Technology Infrastructure Library (ITIL), and Control Objectives for Information and Related Technology (COBIT). The CASP+ is responsible for ensuring that the cloud provider can meet these requirements and is willing to undergo certification, accreditation, and review as needed. The vendor's geographic location can be extremely important to compliance.
- Who can access the data? Defense in depth is built on the concept that every security control is vulnerable. Cloud computing places much of the control in someone else's hands. One big area that is handed over to the cloud provider is access. Authentication and authorization are real concerns. Because the information or service now resides in the cloud, there is a much greater opportunity for access by outsiders. Insiders might pose an additional risk.
Insiders, or those with access, have the means and opportunity to launch an attack and lack only a motive. Anyone considering using the cloud needs to look at who is managing their data and what types of security controls are applied to individuals who may have logical or physical access.
- Does the cloud provider use a data classification system? A CASP+ should know how the cloud provider classifies data. Classification of data can run the gamut from a fully deployed classification system with multiple levels to a simple system that separates sensitive and unclassified data. Consumers of cloud services should ask whether encryption is used and how one customer's data is separated from another customer's data. Is encryption being used for data in transit or just for data at rest? Consumers of cloud services will also want to know what kind of encryption is being used.
- What training does the cloud provider offer its employees? This is a rather important item in that people will always be the weakest link in security. Knowing how your provider trains their employees is an important item to review. Training helps employees know what the proper actions are and understand the security practices of the organization.
Staff turnover is very high in the technology industry. Training done well can reduce the likelihood of turnover while increasing the performance of an IT employee. Supervision can also be a major factor in staff leaving an organization. Training senior staff on how to lead teams more effectively and manage conflict is extremely beneficial.
- What are the service level agreement (SLA) terms? The SLA serves as a contracted level of guaranteed service between the cloud provider and the customer. An SLA is a contract that provides a certain level of protection. For a fee, the vendor agrees to repair, replace, or provide service within a contracted period of time. An SLA is usually based on what the customer specifies as the minimum level of services that will be provided.
- Is there a right to audit? This particular item is no small matter in that the cloud provider should agree in writing to the terms of audit. Where and how is your data stored? What controls are used? Do you have the right to perform a site visit or review records related to access control or storage?
- Does the cloud provider have long-term viability? Regardless of what service or application is being migrated to a cloud provider, you need to have confidence in the provider's long-term viability. There are costs not only to provision services but also for deprovisioning should the service no longer be available. If they were to go out of business, what would happen to your data? How long has the cloud provider been in business, and what is their track record? Will your data be returned if the company fails and, if so, in what format?
- Could we experience vendor lock-in or lock-out? Vendor lock-in can be difficult to plan for. Vendor lock-in happens when consumers become so integrated with a specific vendor or single cloud provider that they cannot easily move to another vendor without spending huge amounts of money, getting attorneys involved, or technical incompatibility; then the organization is at the mercy of the cloud provider. A related problem is vendor lock-out, when a consumer wants to leave a vendor but will have trouble transferring their data, services, and files. (In daily practice, you'll see that a lot of people use the terms vendor lock-in and vendor lock-out interchangeably.) The best way to avoid vendor lock-in and vendor lock-out is to understand the complex dependencies and commonalities of your technology stack as well as making apps portable, ensuring portability once migrated, and, as always, doing your due diligence.
- How will the cloud provider respond if there is a security breach?
Cloud-based services are an attractive target to computer criminals. If a security incident occurs, what support will you receive from the cloud provider? To reduce the amount of damage that these individuals can cause, cloud providers need to have incident response and handling policies in place. These policies should dictate how the organization handles various types of incidents. Cloud providers must have a computer security incident response team (CSIRT) that is tied into customer notification policies for law enforcement involvement.
- What is the disaster recovery and business continuity plan (DR/BCP)? Although you may not know the physical location of your services, they are physically located somewhere. All physical locations face threats, such as fire, storms, natural disasters, and loss of power. In the case of any of these events, the CASP+ will need to know how the cloud provider responds and what guarantee of continued services they are promising. There is also the issue of retired, replaced, or damaged equipment. Items such as hard drives need to be decommissioned properly. Should sensitive data be held on discarded hard drives, data remanence is a real issue. Data remanence is the remaining data, or remnants, that remain on the media after formatting or drive wiping. The only way to ensure there are no data remnants is through physical destruction of the media.
Cloud outages are not uncommon occurrences, and when they hit, they hit hard. In November 2021, Google Cloud, Snapchat, and Spotify experienced an outage for about an hour. More than 50,000 users reported the outage on
downdetector.com. Many companies were affected, from Pokémon GO to Home Depot. In Figure 5.3, you see the Google Dashboard reporting the outage.
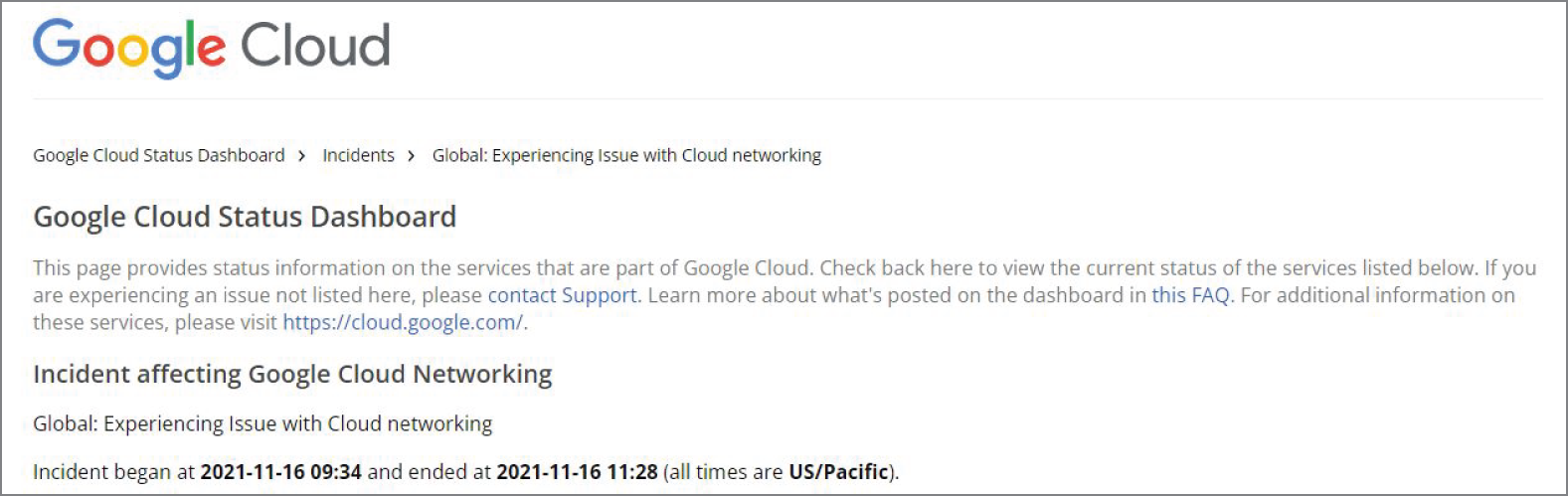
FIGURE 5.3 Google Cloud Status Dashboard
In Exercise 5.2, you will examine some common risks and issues associated with cloud computing as they would affect your organization.
Change Management
Change management is a formalized process that is implemented to control modifications made to systems and programs, whether in a cloud environment on premises. Change management provides a controlled process for change, and it is typically handled by a change review board. It also provides stakeholders with an opportunity to voice their concerns before changes are implemented. Before changes are made, the change management request should list specific items about the requested change. Items to record include change number, change type and description, change requestor name and time/date, change source, problem or reason for the change, and dates of the proposed change.
ISO 20000 defines change management as a needed process to “ensure all changes are assessed, approved, implemented and reviewed in a controlled manner.” NIST 800-64 describes change management as a method to ensure that changes are approved, tested, reviewed, and implemented in a controlled way. Regardless of what guidelines or standards you follow, the change management process can be used to control change and to help ensure that security does not fall to a lower state. A typical change management process includes the following:
- Change request
- Change request approval
- Planned review
- A test of the change
- Scheduled rollout of the change
- Communication to those affected by the planned change
- Implementation of the change
- Documentation of all changes that occurred
- Post-change review
- Method to roll back the change if needed
Also, what is and is not covered by the policy should be specified. For example, some small changes, like an update to antivirus programs, may not be covered in the change control process, whereas larger institutional changes that have lasting effects on the company are included. The change control policy should also list how emergency changes are to occur, because a situation could arise in which changes must take place quickly without the normal reviews being completed before implementation. In such a situation, all of the steps should still be completed, but they may not be completed before implementation of the emergency change. Change management must be able to address any of the potential changes that can occur, including the following:
- Changes to policies, procedures, and standards
- Updates to requirements and new regulations
- Modified network, altered system settings, or fixes implemented
- Alterations to network configurations
- New networking devices or equipment
- Changes in company structure caused by acquisition, merger, or spinoff
- New computers, laptops, smartphones, or tablets installed
- New or updated applications
- Patches and updates installed
- New technologies integrated
Validation and Acceptance Testing
Before products are released, they must typically go through some type of validation and acceptance testing. The idea is to conduct tests to verify that the product or application meets the requirements laid out in the specification documents.
For some entities, validation is also performed. The U.S. federal government specifies this process as certification and accreditation. Federal agencies are required by law to have their IT systems and infrastructures certified and accredited. Certification is the process of validating that implemented systems are configured and operating as expected. If management agrees with the findings of the certification, the report is formally approved. When comparing products, all products must be validated with identical tests. The formal approval of the certification is the accreditation process and authorization to operate in a given environment.
Testing and Evaluation
An important phase of cloud computing or any vendor/product acquisition is the testing and evaluation of systems. Before a system or service can be accepted, or deemed to reach a milestone in its development, that system must be evaluated against the expected criteria for that phase or project. If the system is tested against its specification requirements and passes, then its owners and users gain the assurance that the system will function as needed.
Testing spans cloud adoption, hardware, and software development, but the goal is to raise the assurance that the system will operate as expected. Further, testing may seek to verify that undesired aspects do not exist. For example, during the course of software development, an application might be evaluated for forbidden coding techniques.
Managing and Mitigating Risk
Companies must be aware of current and emerging threats and security trends to be able to adapt quickly. An example is the rise of advanced persistent threats (APTs). It is so important to remind users not to click unknown or suspicious links, even if they appear to be from someone they trust on a social networking site.
The need for proper controls is more critical when involving critical devices and technical configuration. Industrial control systems (ICSs) include Supervisory Control and Data Acquisition (SCADA), such as a system for managing a water or gas pipeline. When malware affects industrial control systems, it's conceivable that it could have disastrous consequences. If not causing imminent danger or widespread interruption to a community, ICS outages could at least produce costly results. Recall that the ICS malware Stuxnet targeted Iranian nuclear centrifuges. Their outage included permanent self-destruction of the industrial machinery.
A large number of emerging threats are driven by people out for financial gain, hacktivists, and nation-state hackers. Some believe that out of these three categories, the nation-state hackers are the most serious threat, both to corporations and to governments. To deal with emerging threats, companies should be prepared with a plan that lays out the key steps and resources to deploy immediately when a breach is detected.
Although many companies state financial issues as one of the items that are preventing better controls in dealing with security issues, the real question is when the company would prefer to spend the funds. Having a team come in after the security breach to fix the problem and figure out what occurred can be very costly. Implementing preventive controls before the event is more cost effective.
There is also the issue that money isn't always the solution. A big part of the solution in dealing with emerging threats is training and education. IT security policies need to be created, and employees must be educated on the value of the company's assets and how to protect them. At a minimum, the security awareness and training program should be documented in the enterprise-level policy and should include the following:
- Definition of security roles and responsibilities
- Development of program strategy and a program plan
- Implementation of the program plan
- Maintenance of the security awareness and training program
Geographical Considerations
Advances in technology now make it possible for device-tracking technologies to monitor assets and manage inventory to a much greater degree than ever before. As the Internet has grown, businesses have allowed customer access to data to, for example, track orders and find out where things are at any given time. Customer service expectations have also increased as consumers want to track packages in real time. Asset management is not just about tracking packages—it is also concerned with products being sold at retail, the tracking of patients in a hospital, and products in warehousing and distribution systems.
Geolocation technologies give individuals the ability to track the real-world location of an item. This technology includes the ability to geotag the location of photographs, but it can also be used by mobile applications to identify a user's exact location. The idea is that you can identify a user by their location for service or revenue. Examples include coupons from nearby coffee shops and restaurants. However, the security concern is that hackers or others potentially have the ability to track the location of specific individuals.
Third-Party Dependencies
Rapid growth in third-party dependencies (including hardware, software, open-source libraries, code, modules, packages, and container images, etc.) has considerably changed the contemporary software development method. Most applications are developed on a blend of in-house and external code, and most computer hardware made of multiple components has a long list of suppliers.
Third-party hardware refers to the computing components that are developed outside of the original manufacturer. An organization may purchase hardware from Dell, but a specific hard drive could be made by Seagate or Kingston, and the video card could be made by NVIDIA or ZOTAC and the CPU made by AMD or Intel. These third-party components are supported by the company that made them, not Dell.
With the evolution of the Internet of Things (IoT) there are many hardware security issues with attackers concentrating on vulnerabilities on physical devices. Common hardware security issues include devices having default passwords, outdated firmware, and unprotected local access.
Public open-source code repositories present a place for developers to use and share software libraries, packages, container images, and other works with many useful and well-developed features. The use of third-party dependencies does increase development efficiency and value, but the security risks of malicious code and vulnerabilities has created a backdoor for supply chain attacks.
Typosquatting and dependency confusion are two ways that attackers trick developers to download their malicious code. Typosquatting relies on the typos from the content supplied by threat actors. The malicious codes will be brought into the project and deployed to the production systems. Malicious packages conceal their contents by misspellings, commonly using a capital I in place of a lowercase l. In certain fonts, it is extremely difficult to tell the difference.
Dependency confusion happens when an attacker takes advantage of the default configuration of a package manager to force the download of a package they have tampered with by keeping the same name but with a higher version number.
Technical Considerations
As a CASP+, you must consider several technical security considerations. These include network segmentation, technical testing, transmission control, and shared credentials. Testing is discussed throughout this chapter and this book, but let's take a look these other considerations.
Network segmentation is the practice of taking a large computer network and dividing it into several smaller, isolated subnetworks. Network segmentation using a screened subnet, also known as a DMZ, is a key part of compliance with PCI DSS. If a point-of-sale (POS) system is breached, cardholder data could still be secure because the database holding that information is in another subnet. If there was no network segmentation, the attacker could move around freely and steal the keys to the kingdom.
When looking at transmission control in the form of TCP/IP, information is broken up into packets, and the IP source generates a listing of the routes that packets must take to reach their intended destination. This listing may in turn be used by the recipient to send information back to the sender. At this time, threat actors can gain access to the source path and modify the options in the route for a data packet, which is called a source route attack. The attacker may also be able to read the data packets and gain access to confidential information or intellectual property. This security risk may be offset to some extent by dropping or forwarding any data packets that carry the source route option.
Other technical security considerations are shared and generic accounts or credentials. These accounts are often prohibited by security policies. While shared accounts can be useful, many organizations build delegation capabilities to allow multiple users to act in the same way or with the same rights to avoid shared account issues, like the inability to determine who was logged in to the shared account or what actions each user who shares the account took. All administrator or root account/credentials should not be shared with third-party vendors and should be monitored and audited on a schedule.
Security Concerns of Integrating Diverse Industries
Many substantial security risks arise when merging enterprises or hiring third-party organizations. These risks may be the result of a vendor relationship that starts somewhere along the organization's supply chain, or they may be the result of other business partnerships or conflicts within the merged entity.
A security professional can learn a great deal about an organization by reviewing the strategic plan and examining the company's policies and procedures. In the best-managed companies, high-level documents such as policies reflect management's view of the company. Policies should exist to cover most aspects of organizational control, since companies have legal and business requirements to have policies and procedures in place. One example of this is the Sarbanes-Oxley Act (SOX), a federal law that mandates financial record-keeping and reporting. This mandate places strict controls on companies and requires them to have policies and procedures in place. For those that are not compliant, there are fines and possible imprisonment of up to 20 years for those responsible. Policy should dictate who is responsible and what standards must be upheld to meet minimum corporate governance requirements.
Management is responsible for defining the structure of the organization and therefore must divide the company into smaller subgroups that control specific functions. Policies and procedures are the controlling documents that dictate how activities occur in each of the general functional areas. A security professional should always look to see what documents are in place, with what frequency they are updated, and what activities they cover. You may find that companies don't have security policies in place. In some cases, it may be that technology has moved so fast that the company has not yet adapted. In other situations, it may be that the company just doesn't see the need for a policy or hasn't made policy development a priority.
As a security professional responsible for any type of acquisition or vendor agreement, you should keep in mind that documents such as policies and procedures are living documents that need to be reviewed periodically. Processes and procedures may have to change or be updated in light of policy, regulatory, environment, and business changes. Timing for this review will vary depending on the company and the business sector in which it operates. Although many companies review policies at least once a year, intervals can range from six months to five years. During the review, the following questions should be asked:
- Have procedures or processes changed?
- Is the policy relevant?
- Have the relevant laws changed?
- Does the change management process incorporate documentation change?
- Have industry best practices changed?
- Have periodic audit findings indicated a problem with documentation, such as policies and procedures?
When reviewing documentation, consider documents that address internal practices as well as the company's interactions with external entities, business partners, and contractors. A company may have contracts with vendors or suppliers for an array of products and services. During the review process of policies, procedures, and documentation, any of the following conditions may indicate potential problems:
- Negative audit findings
- Lack of documentation
- Out-of-date documentation
- Unsupported hardware changes or unauthorized purchases
- Employees who are unaware of or not knowledgeable about documentation
The CASP+ should support legal compliance and advocacy by partnering with HR, legal, management, and other entities to make sure that all stakeholders are involved. For items like employee concerns, HR should be involved. For items like compliance or Payment Card Industry Data Security Standard (PCI DSS), the legal department should be involved since these individuals will know the requirements under which the company must work.
Regulations, Accreditations, and Standards
Legislators and regulators around the world take an interest in cybersecurity due to the potential impact of cybersecurity shortcomings on individuals, government, and society. While the European Union (EU) has a broad-ranging data protection regulation, cybersecurity analysts in the United States are forced to deal with a patchwork of security regulations covering different industries and information categories.
Privacy and protection of sensitive information touch the organization in a way that no other items do. As a security professional, you may be asked to help build an effective privacy governance program or work with one that has already been developed. How such a program is managed will affect not only the customer's opinion of the firm but also the firm's financial status.
With mandates such as the Sarbanes-Oxley Act (SOX), the Health Insurance Portability and Accountability Act (HIPAA), and the Payment Card Industry Data Security Standard (PCI DSS), companies face a huge amount of regulation and monetary exposure should private policy violations occur and sensitive information be exposed. It's not just monetary losses a company could suffer if they fail to protect certain types of data; there is also the issue of lawsuits, bad publicity, and government investigations.
One of the reasons we see so many more laws governing sensitive information today than in the past is that the way information is stored, moved, and processed has changed. There was a time when credit card machines were manual. These mechanical devices required the operator to swipe the card and make a carbon copy duplicate of the card number and signature of the purchaser. Security rested in the physical protection of credit card information. People were sometimes told to tear up the credit card carbon copy so criminals could not steal the numbers.
Today credit card information is stored and processed electronically. Many of these electronic systems are connected to the Internet and make an attractive target for hackers. Just consider the process of paying for a meal with your credit card. From the point you hand your credit card to the server to the time the credit card bill arrives at your home, the data has passed many points at which a hacker can attempt to steal the information. Companies can be held liable if personal data is disclosed to an unauthorized person. The potential losses can be huge.
PCI DSS
The Payment Card Industry Data Security Standard (PCI DSS) provides detailed rules about the storage, processing, and transmission of credit and debit card information. PCI DSS is not a law but rather a contractual obligation that applies to credit card merchants and service providers worldwide.
If your organization accepts credit cards, debit cards, or any other type of electronic payment, you connect to a multifaceted and complicated structure of networks, banking, and credit card institutions. In this digital age when many attackers are looking to monetize their processes, fraud must be defended against, and every organization connecting to this structure must meet a minimum set of standards to protect this sensitive financial data. This is the PCI DSS. Companies that process and handle any amount of credit card information must implement specific controls including policies, procedures, network architecture, and software design to protect cardholder data. Failure to meet PCI DSS compliance mandates can suffer negative impact including fees, fines, and lost business.
Visa and MasterCard between 1988 and 1998 lost more than $750 million due to credit card fraud. PCI was established in 2004 with PCI DSS version 1.0 Security Architecture with a basic yet comprehensive list of security controls for merchants accepting credit cards. PCI DSS outlines best practices for companies handling payment card information and was developed collectively by American Express, Discover Financial Services, JDB International, MasterCard, and Visa. These best practices are used to improve security and outline the policies used to safeguard security systems that carry sensitive cardholder information. The most current version of PCI DSS is version 3.2.1, released May 31, 2018. PCI DSS standards are based on 12 requirements that involve network security and internal controls:
- Installing/maintaining a firewall configuration for networks and systems
- Avoiding using vendor-supplied defaults for passwords and other security procedures
- Protecting cardholder data during storage
- Using encryption during cardholder data transmissions in open and public networks
- Using and updating antivirus software
- Developing and maintaining secure network systems and applications
- Restricting user access to cardholder data
- Creating a unique ID for users who need to access cardholder data
- Restricting any physical access to cardholder information
- Tracking and monitoring all access to network systems and data
- Testing security processes and systems
- Maintaining information security policies
PCI DSS helps sellers to protect their vital cardholder data that contains personally identifiable information (PII). PII is any data that could potentially identify a specific individual. TechTarget defines PII as “any data about an individual that could potentially identify that person, such as a name, fingerprints or other biometric data, email address, street address, telephone number or social security number.”
Protecting PII is essential for personal and data privacy as well as data and information security. Information that can uniquely identify someone as an individual, separate from everyone else, is PII and includes the following:
- Name
- Address
- Telephone number
- Date of birth
- Passport number
- Fingerprint
- Driver's license number
- Credit or debit card number
- Social Security number
Unfortunately, some companies have the preconceived notion that security controls will reduce the efficiency or speed of business processes. According to securitymagazine.com, the number of data breaches through September 30, 2021, has exceeded the total number of events in 2020 by 17 percent, with 1,291 breaches in 2021 compared to 1,108 breaches in 2020. These breaches affected millions of Americans. These companies did not have sufficient controls in place to protect personally identifiable information.
Your job as a security professional is to work with managers to help them see the importance of strong security controls. Good security practices are something that most managers or users do not instinctively know. They require education. A key component of the process is training and awareness for users. Part of the educational process is increasing the awareness of the costs involved if sensitive information is lost.
Here are some general privacy principles for PII:
- The PII data will be collected fairly and lawfully.
- The PII data will be used only for the purposes for which it was collected.
- The PII data will be kept secure while in storage and in transit.
- The PII data will be held only for a reasonable time.
Two areas of protection that a company's policy must address are protecting credit card data while it is at rest and while it is in transit. If your company deals with credit cards, PCI standards dictate that the stored cardholder data must be rendered unreadable or encrypted to protect customer privacy. To meet this requirement, your company must implement security controls that provide for encryption methods while the credit card data is being stored and while the credit card data moves across open, public networks. Companies that must comply with PCI standards state that documentation is one of the most tedious aspects of attaining and maintaining PCI compliance and is one area that typically needs more work.
A big component of providing the proper protection for PII is to make sure that there is a way to track privacy policy violations and measure their impact. One way to measure the impact is to verify that company policy has been based on a privacy impact assessment (PIA). A PIA should determine the risks and effects of collecting, maintaining, and distributing PII in electronic-based systems. The PIA should be used to evaluate privacy risks and ensure that appropriate privacy controls exist. Existing controls should be examined to verify that accountability is present and that compliance is built in every time new projects or processes are scheduled to come online.
You can read more about PCI DSS and the best practices surrounding payment card information at www.pcicomplianceguide.org/category/best-practices.
GDPR
Sweeping data privacy laws like the General Data Protection Regulation (GDPR) implement strict security and privacy requirements for the personal information of European Union (EU) residents worldwide. GDPR significantly restricts how certain types of information may be stored and used by organizations and will be used to enforce these regulations with stiff fines and penalties. This 88-page regulation was put into effect on May 25, 2018. The GDPR will levy punitive penalties against those who breach its privacy and security standards, with fines reaching into the tens of millions of euros.
The GDPR defines an array of legal terms at length. Here are some of the most important ones:
- Personal data: Personal data is any information that relates to an individual who can be directly or indirectly identified (PII).
Pseudonymousdata can also fall under the definition if it's easy to ID someone from it. - Data processing: Any action performed on data, whether automated or manual. The examples cited on
gdpr.euinclude collecting, recording, organizing, structuring, storing, using, and erasing. - Data subject: The person whose data is processed. These are customers or site visitors.
- Data controller: The person who decides why and how personal data will be processed. If you're an owner or employee in your organization who handles data, this is you.
- Data processor: A third party that processes personal data on behalf of a data controller.
- Data classification: Identifying the types of data that an organization stores and processes and the sensitivity of that data, based on a set of rules. Data will fall into four categories:
- Public
- Internal Only
- Confidential
- Restricted
Here is a rundown of data subjects’ privacy rights:
- The right to be informed
- The right of access
- The right to rectification
- The right to erasure
- The right to restrict processing
- The right to data portability
- The right to object
- Rights in relation to automated decision-making and profiling
With various countries imposing so many different requirements, organizations face a regulatory patchwork of inconsistent, unclear, and often contradictory demands. The implications for multinational companies are substantial: threats of regulatory action, disruptions to established business processes, and requirements to tighten controls for handling and processing information that crosses national boundaries. The overturning of the Safe Harbor agreement, governing how data is moved between EU countries and the United States, forced many companies to reexamine their own legal and policy frameworks for protecting personally identifiable data.
To address the challenges emerging from new and pending data privacy regulations, business and technology leaders need to work collectively with their compliance, legal, and technology teams to understand the impact regulations have on their businesses.
Data sovereignty is the concept that information that has been converted and stored in binary digital form is subject to the laws of the country in which it is located. With data theft and breaches dramatically on the rise, national governments around the globe are strengthening laws to protect their citizens’ data, preserve national security, and, in some cases, protect local business interests.
Data sovereignty is different from data ownership. Data ownership is both the possession of the data and responsibility for the information. According to GDPR, data ownership refers to the explicit assignment of responsibility to every data element. A data owner can be a team or individual who has the right to access and edit the data and decide how it is used. Data ownership is important because it creates accountability. A data owner has a vested interest in the protection and integrity of their data and will create policies to ensure they are GDPR compliant. The data steward's role essentially is to support the user community. This individual is responsible for collecting, collating, and evaluating issues and problems with data. Typically, data stewards are assigned either based on subject areas or within line-of-business responsibilities. The main difference between a data owner and a data steward is that the latter is responsible for the quality of a defined dataset on day-to-day basis.
As regulations are drafted in a particular nation or region, even when they affect data and users around the globe, the question of jurisdictions is debated. Companies seek to minimize how a regulation affects their infrastructure and users. There is ongoing debate, but it seems that most data privacy regulation is tilted toward the user's benefit.
One side effect of GDPR is the resulting impact on cloud computing. Under GDPR, a company is considered the data controller and is responsible for keeping all the data safe, regardless of where that data is being stored. Key steps to take for geographical decisions regarding compliance in the cloud are strict privacy policies, terms of use, server location, security features, encryption, and legal guarantees for data protection.
ISO
The International Organization for Standardization (ISO) describes itself as “a network of the national standards institutes of 162 countries, one member per country, with a Central Secretariat in Geneva, Switzerland, that coordinates the system that forms a bridge between the public and private sectors.”
An important ISO document for cybersecurity that is definitely worth reviewing is ISO 27002. This standard is considered a code of best practice for information security management. It grew out of ISO 17799 and British Standard 7799. ISO 27002 is considered a management guideline, not a technical document. You can learn more at www.27000.org/iso-27002.htm. ISO 27002 provides best-practice recommendations on information security management for use by those responsible for leading, planning, implementing, or maintaining security. The ISO 27017 was created to include additional security controls for cloud computing.
The latest ISO 27002:2022 contains 93 controls; 11 are new, 24 have merged, and 58 are updated for guidance. The standard contains 14 control domains spread across four categories including organizational, physical, technological, and people. The 11 new controls are as follows:
- Threat intelligence: Understanding attackers and their methods in the context of your IT landscape
- Information security for the use of cloud services: Considering the introduction through operation to exit strategy regarding cloud initiatives
- ICT readiness for business continuity: Deriving the requirements for the IT landscape from the overall business processes and the ability to recover operational capabilities
- Physical security monitoring: Using alarm and monitoring systems to prevent unauthorized physical access
- Configuration management: Hardening and secure configuration of IT systems
- Information deletion: Compliance with external requirements, such as data protection deletion concepts
- Data masking: Using techniques that mask data, such as anonymization and pseudonymization, to bolster your data protection
- Data leakage prevention: Taking steps to help prevent sensitive data from being leaked
- Monitoring activities: Monitoring network security and application behavior to detect any network anomalies
- Web filtering: Helping prevent users from viewing specific URLs containing malicious code
- Secure coding: Using tools, commenting, tracking changes, and avoiding insecure programming methods to ensure secure coding
Another ISO document for cybersecurity professionals to be acquainted with is the ISO 15408, which was finalized after years of drafts and was initially published in 1997. It is currently in version 3.1, and it is more widely known as the Common Criteria. The purpose of the Common Criteria is to provide a common structure and language for expressing product and system IT security requirements. It's a way for vendors to describe what their products are capable of and for buyers to test such products to be sure they meet specific requirements. The Common Criteria provides assurance that the process of specification, implementation, and evaluation of a computer security product has been conducted in a rigorous and standard manner. As such, the Common Criteria can be used on a worldwide basis and is meaningful to a much larger audience.
CMMI
The Capability Maturity Model Integration (CMMI) was created by the Software Engineering Institute at Carnegie Mellon University as a method improvement tool for projects, divisions, or organizations. The DoD and U.S. government helped build the CMMI, which is a common requirement for DoD and U.S. government software development contracts. The CMMI is presently administered by the CMMI Institute, which was acquired by the ISACA in 2016. CMMI is a process and behavioral model that helps groups reorganize or restructure processes for improvement that decrease risk in software, product, and service development.
The CMMI model breaks down organizational maturity into five levels. While CMMI has its beginnings in software engineering, it has been generalized to incorporate other areas. There are three areas, all of which use the same five-level model:
- Product and Service Development: CMMI for Development (CMMI-DEV)
- Service Establishment and Management: CMMI for Services (CMMI-SVC)
- Product and Service Acquisition: CMMI for Acquisition (CMMI-ACQ)
For cybersecurity businesses that use CMMI, the aim is to raise the organization up to level 5, the “optimizing” maturity level. In Figure 5.4, you see the difference between the levels of CMMI from level 1 to level 5.
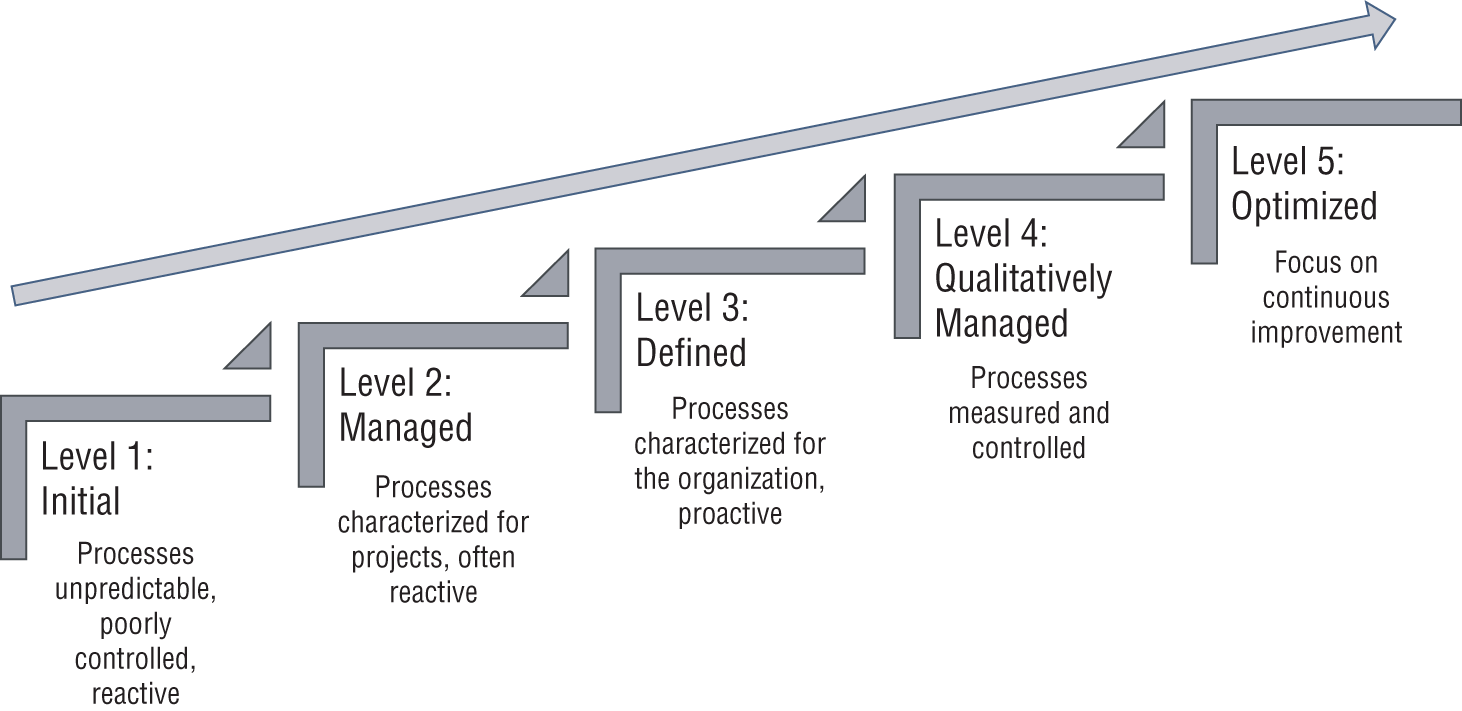
FIGURE 5.4 CMMI levels
NIST
The National Institute for Standards and Technology (NIST) is responsible for developing cybersecurity standards across the U.S. federal government. The guidance and standard documents it produces often have wide applicability across the private sector and are commonly referred to by nongovernmental security analysts because they are available in the public domain.
In 2018, NIST released version 1.1 of a Cybersecurity Framework (CSF) (www.nist.gov/cyberframework), which provides a common language and systematic methodology for managing risk. The following are the five functions acting as the backbone in the core framework:
- Identify: Helps in developing an understanding of cybersecurity risks to people, systems, data, and assets
- Protect: Outlines the proper safeguards to make sure critical infrastructure is secure
- Detect: Defines how to identify a cybersecurity event
- Respond: Defines what action to take if a cybersecurity event occurs
- Recover: Identifies the plans necessary for resilience and restoration of services impaired due to a cybersecurity event
NIST also releases special publications for cybersecurity guidance such as the 800-100, which is the Information Security Handbook: A Guide for Managers, and 800-53, which is the Security and Privacy Controls for Information Systems and Organizations. NIST works closely with the Information Technology Laboratory (ITL) to promote the U.S. economy and public welfare by providing technical leadership for the nation's measurement and standards infrastructure. ITL develops tests, test methods, reference data, proof-of-concept implementations, and technical analyses to advance the development and productive use of information technology. ITL's responsibilities include the development of management, administrative, technical, and physical standards and guidelines for the cost-effective security and privacy of non-national, security-related information in federal information systems. This Special Publication 800 series reports on ITL's research, guidelines, and outreach efforts in information system security and its collaborative activities with industry, government, and academic organizations.
COPPA
Children today spend more time online than ever before. From virtual school to online games, children spend hours on the Internet and deserve protection so that they may learn and play safely. The Children's Online Privacy Protection Rule (COPPA) was passed in the Congress of the United States in 1998. The rule summary from the Federal Trade Commission, which can be found at ftc.gov, states that COPPA imposes certain requirements on operators of websites or online services directed to children under 13 years of age, and on operators of other websites or online services that have actual knowledge that they are collecting personal information online from a child under 13 years of age.
Operators governed by COPPA must do the following:
- Post a clear and comprehensive online privacy policy describing their information practices for personal information collected online from children.
- Provide direct notice to parents and obtain verifiable parental consent, with limited exceptions, before collecting personal information online from children.
- Give parents the choice of consenting to the operator's collection and internal use of a child's information but prohibiting the operator from disclosing that information to third parties (unless disclosure is integral to the site or service, in which case, this must be made clear to parents).
- Provide parents access to their child's personal information to review and/or have the information deleted.
- Give parents the opportunity to prevent further use or online collection of a child's personal information.
- Maintain the confidentiality, security, and integrity of information they collect from children, including by taking reasonable steps to release such information only to parties capable of maintaining its confidentiality and security.
- Retain personal information collected online from a child for only as long as is necessary to fulfill the purpose for which it was collected and delete the information using reasonable measures to protect against its unauthorized access.
- Not condition a child's participation in an online activity on the child providing more information than is reasonably necessary to participate in that activity.
COPPA was implemented to protect children online, and fines for failing to comply with the law were recently increased to up to $43,280 per privacy violation per child. The FTC announced in September 2019 that Google and its subsidiary YouTube would pay a $170 million fine to settle the FTC's allegations that YouTube collected children's personal information without parental consent. YouTube collected information from children on pages specifically directed toward children, such as videos about children's toys and nursery rhymes.
CSA-STAR
The cybersecurity community offers many reference documents to help organizations come to a common understanding of the cloud and cloud security issues. The Cloud Security Alliance (CSA) is an industry organization focused on developing and promoting best practices in cloud security. It developed the Cloud Controls Matrix (CCM) as a reference document designed to help organizations understand the appropriate use of cloud security controls and map those controls to various regulatory standards. The CCM is a lengthy Excel spreadsheet, available for download from cloudsecurityalliance.org.
The Security, Trust, Assurance, and Risk (STAR) incorporates the fundamental principles of transparency, auditing, and coordination of standards outlined in the Cloud Controls Matrix (CCM). Publishing to the registry allows organizations to show customers their security and compliance posture, including the regulations, standards, and frameworks they follow. In Figure 5.5, you see the STAR levels outlined in the CCM.
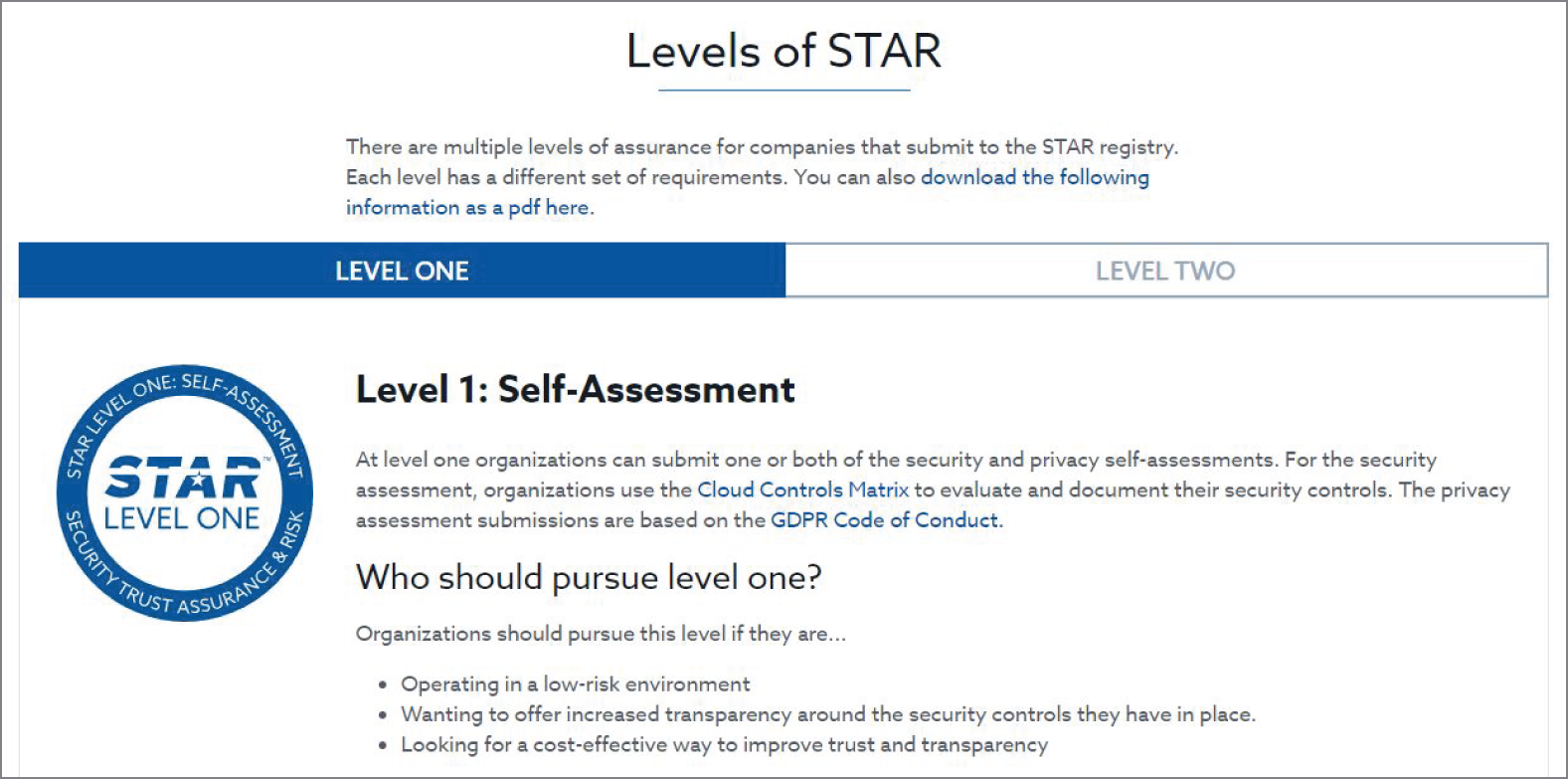
FIGURE 5.5 CSA STAR levels
HIPAA, SOX, and GLBA
You should also be familiar with several other compliance, regulatory frameworks, or standards that relate to privacy and the security of health, financial, PII, and other data, including HIPAA, SOX, and GLBA.
The Health Insurance Portability and Accountability Act (HIPAA) includes security and privacy rules that affect healthcare providers, health insurers, and health information clearinghouses in the United States. HIPAA was signed into law in 1996. It has two parts: Title I of the HIPAA protects health insurance coverage for workers and their families when they change or lose their jobs. Title II requires the U.S. Department of Health and Human Services (DHHS) to establish national standards for electronic healthcare transactions and national identifiers for providers, health plans, and employers.
Under HIPAA, the United States was required to publish a set of rules regarding privacy. The Privacy Rule dictates controls that organizations must put in place to protect personal information. The privacy rule defines three major purposes:
- “To protect and enhance the rights of consumers by providing them access to their health information and controlling the inappropriate use of that information.”
- “To improve the quality of health care in the United States by restoring trust in the health care system among consumers, health care professionals, and the multitude of organizations and individuals committed to the delivery of care.”
- “To improve the efficiency and effectiveness of health care delivery by creating a national framework for health privacy protection that builds on efforts by states, health systems, and individual organizations and individuals.”
The Sarbanes-Oxley (SOX) Act applies to the financial records of U.S. publicly traded companies and requires that those companies have a strong degree of assurance around the IT systems that store and process those records. The SOX Act was signed into law in 2002. This act mandated a number of reforms to enhance corporate responsibility and financial disclosures and combat corporate and accounting fraud.
Sections 302 and 404 are the two sections that address IT infrastructures and information security.
- Section 302 requires the CEO and CFO to certify personally that the organization has the proper internal controls. It also mandates that the CEO and CFO report on the effectiveness of internal controls around financial reporting.
- Section 404 sets requirements on areas of the management's structure, control objectives, and control procedures. Staying compliant with Section 404 requires companies to establish an infrastructure that is designed to archive records and data and protect it from destruction, loss, unauthorized alteration, or other misuse. It requires that a set of comprehensive controls be put in place and holds CEOs and CFOs accountable.
Gramm-Leach-Bliley Act (GLBA) covers U.S. financial institutions, broadly defined. It requires that those institutions have a formal security program and designate an individual as having overall responsibility for that program. GLBA was signed into law in 1999 and resulted in the most sweeping overhaul of financial services regulation in the United States.
GLBA Title V addresses financial institution privacy with two subtitles. Subtitle A requires financial institutions to make certain disclosures about their privacy policies and to give individuals an opt-out capability. Subtitle B criminalizes pretexting, which can be described as the practice of obtaining personal information under false pretenses. In these situations, people misrepresent themselves to collect personal information.
Under GLBA, financial institutions are required to protect the confidentiality of individual privacy information. As specified in GLBA, financial institutions are required to develop, implement, and maintain a comprehensive information security program with appropriate administrative, technical, and physical safeguards. The controls specified in the information security program must include the following items:
- The assignment of a designated program manager for the organization's information security program
- A periodic risk and vulnerability assessment and audit
- A program of regular testing and monitoring
- The development of policies and procedures for control of sensitive information and PII
Remember that this is only a brief listing of security regulations. There are many other laws and obligations that apply to specific industries and data types. You should always consult your organization's legal counsel and subject matter experts when designing a compliance strategy for your organization. You'll need to understand the various national, territorial, and state laws that apply to your operations, and the advice of a well-versed attorney is crucial when interpreting and applying cybersecurity regulations to your specific business and technical environment.
Contract and Agreement Types
Organizations may deploy some standard agreements and practices to manage security risks. Commonly used agreements include the following:
- Master service agreements (MSAs) provide a top-level contract for the work that a vendor does with an organization over an extended period of time, setting the boundaries of the relationship to keep the workflow moving and resolve any disputes. It generally specifies payment terms, warranties, geographic location, and intellectual property ownership. The MSA typically includes detailed security and privacy constraints. Each time the organization enters into a new project with the vendor, they may then create a statement of work (SOW) that contains project-specific details and references the MSA.
- Service level agreements (SLAs) are critical contracts that specify the conditions of service that will be provided by the supplier and the remedies available to the customer if the vendor fails to abide by the SLA. SLAs commonly cover issues such as system availability, data durability, and response time. SLAs are usually written between a customer and external suppliers and should be reviewed by legal counsel. For critical security systems, customers should have a way to measure SLA performance data.
The SLA should specify the uptime, response time, and maximum outage time to which they are agreeing. An SLA can also be used as a type of contract with a hardware vendor that provides a certain level of protection. For a fee, the vendor agrees to repair or replace the equipment within the contracted time.
- A memorandum of understanding (MOU) documents aspects of the starting point relationship that define the purpose of the association. MOUs are an informal method that allows the parties to document their relationship to avoid future misunderstandings. MOUs are frequently used in cases where an internal service provider is offering a service to a client that is in a different business unit of the same company. Sometimes, an MOU may be used as a temporary device prior to an overall blanket contract or agreement. An MOU is different from an NDA. Whereas NDAs are used to maintain secrecy or confidentiality of information, the MOU goes much further: it outlines what each party is responsible for and what each party is to provide or perform.
Choosing the right partner is extremely important and should be done with the utmost care. To be binding, the MOU must be signed by a representative from each organization who has the legal authority to sign. This is typically a member of senior management, someone from the legal department, or a board member. Such documents are typically secured since they are considered confidential. Confidentiality is required because the agreement may describe processes, activities, or even services provided that the signing parties would not want others to know about.
- Privacy-level agreements (PLAs) address privacy, which is one of the top concerns for cloud customers and regulators. Both cloud service providers (CSPs) and potential users struggle with the range of data protection legislation around the world. Inconsistencies between countries’ legislations represent a significant hurdle in the broad adoption of cloud computing. Privacy compliance is a fundamental evaluation criterion when choosing a cloud service provider.
- Business partnership agreements (BPAs) exist when two companies agree to trade with each other in a collaborative partnership. For example, if two companies jointly develop and market manufactured goods, the BPA might identify each partner's obligations and the distribution of revenues. The BPA is a written agreement created by lawyers along with input from the partners and contains standard clauses related to security and cooperation.
- A nondisclosure agreement (NDA) is designed to protect confidential information. For example, before taking the CASP+ exam, you will be asked to sign an NDA stating that you will not reveal the test questions to others. Many companies require employees and contractors to sign NDAs at the time of employment or before gaining access to specific information.
In Exercise 5.3, you will review your company's NDA for areas and items it should contain.
Organizations need to select the agreement type(s) most appropriate for their specific circumstances. A CASP+ should also understand the following documents used to support security:
- Business Impact Analysis The business impact analysis (BIA) is a central part of the disaster recovery business continuity process. The BIA has three components: criticality prioritization, downtime estimates, and resource requirements. The BIA is used to identify costs linked to failures, such as loss of cash or replacement of equipment, cash flows, salaries, or other losses. The BIA can be quantitative or qualitative in design. Business impact analysis is explored further in Chapter 1, “Risk Management.”
- Interoperability Agreement An interoperability agreement (IA) is a document that establishes and maintains requirements for organizations to be able to exchange data. As an example, United Airlines may share flight codes with Lufthansa Airlines, and as such both need access to a common dataset. These common datasets are typically specified through the use of protocols such as TCP/IP or standards such as XML or SQL.
- Continuity of Operations Just consider the natural and human-caused disasters that many of us have witnessed over the past several decades, coupled with increasingly stringent regulatory requirements. These events have led to a much greater need for business continuity. Continuity of operations (COOP) comprises all of the processes and procedures that organizations must put in place to ensure that businesses can continue to operate. The COOP document is needed because companies must have plans and procedures to continue operations in the event of a failure or catastrophe.
- Interconnection Security Agreement An interconnection security agreement (ISA) is a security document that details the requirements for establishing, maintaining, and operating an interconnection between systems or networks. The document specifies the requirements for connecting the systems and networks and details what security controls are to be used to protect the systems and sensitive data. An ISA typically details how specific systems and networks are connected and contains a drawing of the network topology.
- Operating Level Agreement An operating level agreement (OLA) works in conjunction with and supports the SLA process. The OLA defines the responsibilities of each partner's internal support group. So, whereas the SLA may promise no more than five minutes of downtime, the OLA defines what group and resources are used to meet the specified goal.
- Uptime Agreement An uptime agreement (UA) is one of the best-known types of SLA; it details the agreed amount of uptime. For example, UAs can be used for network services, such as a WAN link, or equipment, like servers. Common ratings for uptime include 99.999 percent (described in industry jargon as “five nines”), which is equal to about five minutes of downtime per year. If the UA was to specify 99.9999 percent (“six nines”), the downtime would drop to a maximum of around 30 seconds per year.
Third-Party Attestation of Compliance
It is critical to manage potential risk to your company and have the right safeguards in place. It is important to know that your vendors are managing and processing data according to your compliance needs. Many companies rely on third-party service providers to host or manage information, and these relationships challenge the regulatory, compliance, and data security requirements of the industry.
Outsourced providers must prove the proper and effective internal controls when accessing and processing data. Ensuring transparency in the compliance and control capabilities of third-party organizations demands the trust of your management team, board, and shareholders.
Third-party attestation services can help an organization deliver comfort and assurance to customers, shareholders, suppliers, regulators, and other stakeholders by creating reporting that delivers an objective opinion about your control environment and identifying weaknesses, issues, and risks to minimize disruptions to the business.
Using an information security framework like HITRUST CSF provides a way for organizations to comply with ISO and HIPAA. This framework is a set of 135 controls that meet the requirements and standards of several different compliance regulators and can complete a self-assessment internally or hire an assessor for an external engagement. These controls include third-party assurance, data classification, data retention, and rules for data removal, destruction, and sanitization.
In the HITRUST 9.5.0 Shared Responsibility Matrix, there are 13 control categories. In Control Reference 13.1, there are control specifications, regulatory factor types, and implementation instructions for data retention and sanitization.
Organizations will limit the retention of PII to only that which is deemed necessary and for as long as necessary to fulfill the organization's specific and legitimate purpose and/or required by law. Unless certain exceptions apply, PII must be deleted thereafter. Organizations will ensure that retention periods are appropriately followed and PII is disposed of in accordance with the defined retention periods.
Regardless of the method of storage, organizations will destroy, erase, dispose, sanitize, and/or anonymize the PII in a manner which prevents PII from being lost, stolen, misused, or accessed without authorization once the PII is no longer needed for the stated purpose for which it was collected and/or at the end of the applicable legally required retention period.
HIPAA is a federal act that regulates companies in healthcare and their affiliates by ensuring that they safeguard individuals’ sensitive data and personal health information. HITRUST is a private organization that creates a framework to help companies achieve compliance standards created and enforced by HIPAA. An increasing number of health systems and hospitals are requiring their business associates to become HITRUST certified because the certification demonstrates that the organization has made a dedicated commitment to maintain the greatest level of protection for their customers' healthcare data.
Legal Considerations
When companies implement minimum levels of security for a legal defense, they may need to show that they have done what any reasonable and prudent organization would do in similar circumstances. This minimum level of security is known as a standard of due care. If this minimum level is not maintained, a company might be exposed to legal liability.
Such standards are increasingly important in the IT security field, because so much company data is kept in electronic databases. There are also large amounts of personally identifiable information (PII) kept electronically. This makes it imperative for companies to practice due care and due diligence.
Implementing best practices is not easy—different industries must provide different levels of compliance. One of the most important parts of an acquisition of a vendor or merger with a new company when it comes to security of integrating organizations is due care and due diligence. Due care in cybersecurity means taking acceptable and practical steps to defend your organization's reputational, financial, and legal best interests. Due diligence is the measure or exercise of care enacted by a prudent, rational individual or entity under certain circumstances. The act of performing due diligence results in legally defensible due care.
Due diligence tasks are time-consuming and complex. Incomplete investigation is one of the major causes of integration failure. Security concerns involve examining all of the elements of a company's operations with the objective of evaluating the condition of technology and assets to find any hidden risk or liability.
Some companies choose to implement more than the minimum level of required security. These efforts can be seen as best practices. Best practices seek to provide as much security as possible for information and information systems while balancing the issue of security versus usability. Any implemented control must not cost more than the asset it is protecting. Fiscal responsibility must be maintained.
The U.S. government maintains a complicated set of regulations that provide export controls to govern the export of goods—including technology, software, and technical data—to foreign countries and specified foreign entities and individuals. Cybersecurity products and services present a challenge because the exports may contain a mixture of different software, encryption functions, and controlled technical information.
As the importance of cybersecurity has grown from a national defense perspective, the U.S. government's interest in regulating the export of sensitive technology has grown. A growing number of enforcement actions involve selling software, encryption products, and other cybersecurity-related information abroad, such as an eight-year prison sentence for a resident who tries to obtain sensitive encryption, communications, and global positioning system equipment without a license.
The United States Commerce Department's Bureau of Industry and Security (BIS) released an interim final rule on October 20, 2021, establishing controls on the export, reexport, or transfer (in-country) of certain items that can be used for malicious cyber activities. This rule also created a new License Exception Authorized Cybersecurity Exports (ACE) and requested public comments on the projected impact of the proposed controls on U.S. industry and the cybersecurity community.
License Exception ACE would allow the export, reexport, and transfer (in-country) of “cybersecurity items” to most destinations, while maintaining a license requirement for exports to countries of national security or weapons of mass destruction concern. In addition, countries subject to a U.S. arms embargo involve a license.
Often lawyers battle over the discovery of electronic data and how to get more data from adversaries in court. To accomplish this, a lawyer can issue a legal hold on electronic data. A legal hold could require that certain email messages be retained and intact until they are no longer required for e-discovery or litigation. Legal hold requirements apply both to the content of messages and to the metadata, which can offer evidence of transport and other important nonrepudiation evidence. A legal hold (also known as a litigation hold) is a notification sent from an organization's legal team to employees telling them not to delete electronically stored information (ESI) or discard paper documents that may be pertinent to a recent or pending legal case.
Having a legal hold process in place and using legal hold–specific tools is vital to show defensible and good faith efforts to preserve evidence. If documents are disposed of or emails are deleted after a litigation hold letter is issued, even without ill intent, a court can deem certain facts as established, prohibit the business from relying upon other documents to support a defense, or instruct a jury that an inference should be made that the missing documents would be harmful to the business. Considering these risks, a business should have a strategy in the event it receives a litigation hold letter.
Summary
This chapter focused on two broad areas:
- Managing and mitigating vendor risk
- Compliance frameworks and legal considerations and their organizational impact
The second part of this chapter focused on integrating diverse industries, many different data considerations, and geographic and legal considerations. It also covered the different regulations, accreditations, and standards that affect cybersecurity as well as covering what contract and agreement types protect your organization.
Exam Essentials
Be able to describe the process of performing ongoing research. Performing ongoing research means that the CASP+ must analyze industry trends and outline potential impact on an enterprise. This requires knowing best practices, understanding new technologies, knowing how to evaluate new security systems and services, and understanding documentation.
Be able to describe the correct regulation, accreditation, and standard for different organizations and controls. Many organizations have controls that make them unique, but they also have controls that unite them. A CASP+ must be able to identify an organization's vertical market and know which compliance and control would be used for that organization. HIPAA is for healthcare, and PCI DSS is for payment cards. ISO and NIST are for everyone.
Be able to analyze security contracts to ensure that they meet business needs. Although it may sometimes appear that there are many solutions to a problem, as a CASP+ you must ensure that proposed contracts meet the specific needs of your organization. This means that the agreement meets the required security, privacy, inner connectivity, and operational needs of the company.
Know the importance of managing and mitigating vendor risk. The shared responsibility model, including roles and responsibilities, is very important to cloud customers and providers. Understanding vendor agreements and the CIA triad implementation in storage, networking, and infrastructure becomes integral to vendor viability.
Know compliance frameworks and legal considerations and their organizational impact. Data consideration, third-party attestation, regulations, and standards are all very important to compliance and vendor risk. Legal and contractual agreement types, including privacy agreements, service level agreements, memorandums of understanding, and operational level agreements, are all fundamental for managing the needs of the organization.
Review Questions
You can find the answers in Appendix.
- An external audit is a formal process involving an accredited third party. It can be expensive and time intensive. What is a key to a component having an external audit?
- An internal agent and a security framework
- An independent authority against a recognized standard
- A global internal assessment with gap analysis
- A validated outcome and scheduled future audits
- Your organization decided to outsource systems that are not mission critical. You have been tasked to calculate the risk of outsourcing these systems because a recent key risk indicator review shows that core business functions are dependent on these outsourced systems. What is the best tool to use?
- Gap analysis
- Annual loss expectancy
- Total cost of ownership
- Business impact analysis
- You need an agreement that lets your business implement a comprehensive risk allocation strategy and provides indemnification, the method that holds one party harmless against existing or future losses. What contract should you negotiate?
- Master service agreement
- Business impact agreement
- Interconnection security agreement
- Memorandum of understanding
- You are a financial provider accessing a cloud-based server where your collaboration tool resides. What is the most important question you need to ask the vendor/host of this cloud-based server?
- Is this server PCI-DSS compliant?
- Is this server SCADA compliant?
- What is your SLA if the server goes down?
- What is the TCO of this software?
- A data user reached out to the data steward to request permission to give access to sensitive information to a third-party marketing agency. The third-party vendor has been vetted by security to make sure they are trusted and viable. Who should be contacted next before access is granted?
- Data owner
- CEO
- Board of directors
- Marketing VP
- Your organization's security policy specifies a length of time to keep data, after which the data must be destroyed to help mitigate the risk of that data being compromised. This type of policy helps reduce legal liability if the data becomes unrecoverable. What type of policy is this?
- Data protection
- Data remanence
- Data retention
- Data destruction
- You are a service provider responsible for ensuring that an audit for PCI DSS occurs and that the correct documentation is completed by the relevant parties. This is part of the assessment you provide. What is this process called?
- Service provider request
- Attestation of compliance
- Payment request
- Security standards council
- Your global software organization is required to conduct a BIA for any new company acquisition. Your organization has acquired a new software startup. Your organization and the startup outsource the LMS and CMS for education to noncompatible third parties. What are you most concerned about?
- Data sovereignty
- Encryption
- Data migration
- Disaster recovery
- You must identify a person who will have the administrative control of and be accountable for a specific set of information and dataset. It could be the most senior person in a department. What is their role?
- Cloud engineer
- Data user
- Data owner
- Chief financial officer
- You researched and conferred with your legal department as to what your data retention policy should be. Which of the following compliances places restrictions on data retention?
- GLBA
- HIPAA
- SOX
- All of the above
- Your company holds large amounts of company data in electronic databases as well as personally identifiable information (PII) of customers and employees. What do you do to ensure that implemented controls provide the right amount of protection?
- Best practices
- Forensics
- Due diligence
- Auditing
- Your HR recruiter, Jane, is having problems finding skilled applicants for a role that you have open for an IT security manager. Your division has discussed moving operation solutions to a third party that will manage and sustain processes. Which of the following deployment solutions is this most likely to be?
- Cloud
- Hosted
- On-premises
- Automated
- Your financial company hires a third party to provide cloud-based processing that will have several different types of virtual hosts configured for different purposes, like multiple Linux Apache web server farms for different divisions. Which of the following best describes this service?
- SaaS
- PaaS
- IaaS
- AaaS
- Alonzo is a security architect, and he has decided to build multiple virtual hosts with different security requirements. Numerous virtual hosts will be used for storage, while others will be used as databases. What should he do with these hosts?
- Encrypt all hosts with AES
- Store each host on a separate physical asset
- Move these virtual hosts to the cloud for elasticity
- Verify that each server has a valid certificate
- Craig is a project manager with a software company. His organization needs to be able to use a third party's development tools to deploy specific cloud-based applications. Platform as a service (PaaS) is the choice that has been approved to launch these cloud services. Which of the following is not a true statement?
- PaaS can use API to develop and deploy specific cloud-based services.
- Cloud storage is a term used to describe the use of a third-party vendor's virtual file system as a document or repository.
- You can purchase the resources you need from a cloud service provider on a pay-as-you-go basis.
- With PaaS, you must buy and manage software licenses.
- Asher has a newly formed IT team that is investigating cloud computing models. He would like to use a cloud computing model that is subscription based for general services, and the vendor oversees developing and managing as well as maintaining the pool of computer assets shared between various tenants across the network. The best choice for this situation would be which of the following?
- Public
- Private
- Agnostic
- Hybrid
- Shanyn works for a governmental agency. Her organization has opted into a public cloud solution for all of the business customers' testing environments. Which one of these is not a disadvantage?
- TCO can rise exponentially for large-scale use.
- Not the best solution for security and availability for mission-critical data.
- Low visibility and control of the environment and infrastructure, which might lead to compliance issues.
- Reduced complexity and requirement of IT experts as the vendor manages the environment.
- The objectives and key results (OKR) being measured by management for this quarter are to realize benefits of multitenancy cloud architecture. Which one of these results would not be applicable to a multitenancy cloud service?
- Financial
- Usage
- Vulnerabilities
- Onboarding
- Yaniv is a cloud security consultant working with a large supply chain management firm that is advocating applying the highest level of protection across all cloud assets. His manager has suggested this is not what the priority should be. What would be a more strategic priority?
- Determine what to protect through data discovery and classification.
- Run an anti-malware software on all cloud instances daily.
- Use vulnerability scanning software only on mission-critical servers.
- Implement threat mitigation strategies on IoT devices.
- While running IaaS environments, you retain the responsibility for the security of all operating systems, applications, and network traffic. Which of these would not be advantageous to deploy to protect this cloud environment?
- Anti-malware should be installed.
- Application whitelisting should be used.
- Memory exploit prevention for single-purpose workloads.
- Negotiate an SLA that spells out the details of the data the provider will share in case of an incident.
