THE OBJECTIVE OF THIS CHAPTER IS TO ACQUAINT THE READER WITH THE FOLLOWING CONCEPTS:
Understanding the foundation of IS audit standards
Understanding the auditor's professional requirements
Familiarity of auditor skills necessary for a successful audit
Understanding mandatory versus discretionary wording of regulations
Knowing how to communicate with the auditee
Understanding auditor leadership duties, including planning and setting priorities
Understanding the organizational structure of corporations and consulting firms
Understanding the methods of managing projects, including audit projects

Imagine what the world would be like without the Internet. A world without electronic systems would feel prehistoric. The days of manual systems of bookkeeping are gone. All organizations, regardless of size, are being driven toward increasing levels of automation. This increasing dependency on electronic information systems has created the need for a new type of auditor: the information systems auditor.
Just as financial auditors verify monetary balances and bookkeeping practices, the IS auditor verifies the integrity of the electronic system. Information systems are used to maintain customer data, company files, inventory, and records of transactions. IS auditing can provide a fabulous opportunity for people with financial or information technology backgrounds.
You may be asking yourself whether this opportunity would work for you. Becoming an IS auditor will expand your career options.
In this chapter, you will study the foundation of IS audit standards. The Certified Information Systems Auditor (CISA) establishes professional requirements and defines the auditor skills necessary for a successful audit.
The CISA candidate is expected to know the different types of audits. There is an established process for communication with the auditee. Every successful auditor must understand their leadership duties, including planning and setting priorities. Every IS auditor is expected to recognize the difference between mandatory versus discretionary wording in regulations.
We will discuss the organizational structure of corporations and consulting firms. The auditor will need to evaluate the organization's governance structure to determine whether IT objectives are aligned to organizational goals. This chapter reviews methods for managing projects, including audit projects.
Note
This chapter is a foundation for the next chapter, which is about the IS audit process. Each concept we discuss will be in effect from now through to the end of this Study Guide to progressively build your knowledge.
For decades, the dominant control placed upon an organization was the financial audit. Although theft and fraud have always existed, the general expectation was that almost all organizations could be trusted without additional regulations. We expected management to be honest. Well, those naive days are over. Welcome to the new world, which has a growing number of intrusive regulations. Modern business culture is moving rapidly to less trust and more testing.
Let's reflect on a few of the great people who created this wonderful job opportunity for us. Mom always said to give special recognition to those deserving people who help you further your career opportunities:
Italy's Parmalat dairy scandal occurred in 2003, when executives admitted that an account that was supposed to be holding 4 billion Euro dollars of assets in the Cayman Islands did not exist. The 14 billion Euro organization collapsed into bankruptcy. According to industry news, four of the world's leading banks were indicted in June 2007 for their participation.
Adelphia Communications Corporation executives John Rigas and son Timothy Rigas were convicted of securities fraud, bank fraud for misrepresenting the source of $1.6 billion of funds used in company stock, and stealing $51 million in cash advances. Rigas's illegally misrepresented $2.6 billion of off-balance sheet loans, which led to the company's collapse in 2002. In July 2006, Comcast and Time Warner purchased the failed company and relocated it to Colorado.
American International Group (AIG) former CFO Howard Smith overstated income by $3.9 billion (10 percent of income) and loss reserves by $500 million to quiet analyst complaints about AIG's declining financial reserves. Executives at the world's largest insurer are struggling to recover. Securities and Exchange Commission agreed to settle after AIG agreed to pay over 1.6 billon in damages. SEC did not release Mr. Smith from prosecution as the case continues to progress.
Arthur Andersen executive David Duncan violated his independence with his client, CFO Andrew Fastow of Enron. Duncan participated in improper, biased activities for Enron by ordering his staff to shred documents to obstruct the Enron investigation.
Cendant Vice Chairman E. Kirk Shelton was convicted of fraud in an accounting scandal for falsely inflating income to drive up the stock price.
Converse Technology CEO Jacob "Kobi" Alexander was captured by Federal authorities after fleeing the country in an attempt to avoid prosecution for orchestrating a fraudulent scheme of backdating options while running a secret stock options slush fund. This illegal scheme made millions of dollars. CFO David Kreinberg and General Counsel William Sorin voluntarily surrendered to authorities for their participation in the scheme. All three are currently in jail awaiting prosecution.
Enron executives Ken Lay, Jeffrey Skilling, Andrew Fastow, Lea Fastow, Ben Glisan Jr., and Dan Boyle were proven guilty for running the world's largest scam of off-balance sheet (OBS) transactions.
International Product Investment Corp. (IPIC) CEO Gregory Earl Setser was convicted of conspiracy, securities fraud, and money laundering Mr. Setser has been sentenced to 40 years in prison without parole and ordered to pay approximately $62 million in restitution for running an investment pyramid scam.
ImClone Systems CEO Samuel D. Waksal was sentenced to more than 7 years in prison and ordered to pay $4.2 million for insider trading in his attempts to sell off his shares of stock after learning that the Federal Drug Administration was planning to reject ImClone's application for Erbitux, a new cancer drug. In a twist of irony, the FDA granted tentative approval for Erbitux the day after Waksal was sentenced.
Former HealthSouth CFO Weston Smith was sentenced to 27 months in prison for his participation in the $2.7 billion accounting fraud at the company. Smith was one of five ex-CFOs who agreed to plead guilty and testify against former CEO Richard Scrushy. Ultimately Scrushy was acquitted on all counts of the accounting fraud charges.
Tyco ex-CEO Dennis Kozlowski is serving 8–25 years in prison for stealing $134 million from the company. Ex-CFO Mark H. Schwartz was given the same prison sentence. The scheme involved grand larceny, conspiracy of falsifying business records, and inflating statements of operating income by at least $500 million by using improper accounting practices.
Patterson-UTI Energy CFO Jody Nelson was sentenced to 25 years and $77 million restitution for a phony invoice scheme of embezzling $77 million for personal use. (Criminal filing took only two weeks to freeze accounts and assets.)
Lincoln Savings and Loan CEO Charles Keating was found guilty of causing the $2.6 billion collapse of the savings and loan industry in 1988. So far the estimated cost of the bailout is said to be over $110 billion ($10 from every person in America). Mr. Keating accused the auditor of having a vendetta against him for bringing the evidence to the attention of regulators.
WorldCom ex-CEO Bernard Ebbers is serving 25 years for securities fraud and filing false reports concerning an $11 billion accounting fraud. WorldCom triggered the creation of the U.S. Sarbanes-Oxley Act of 2002 (a corporate governance law for internal controls). CFO Scott Sullivan testified against Ebbers to get a reduced sentence. Controller David Myers admitted he told the accounting staff to make billions of dollars in adjustments to financial statements so their stock price would rise. Former accounting director Buford Yates went to prison for following the orders of his superiors to make billions of dollars of unexplained adjustments in financial records.
More than 1,000 successful corporate fraud convictions by the U.S. Securities and Exchange Commission (SEC) from 2002–2005 include the following:
92 corporate presidents
86 chief executive officers (CEOs)
40 chief financial officers (CFOs)
14 chief operating officers (COOs)
98 vice presidents (VPs)
17 attorneys (lawyers serving as corporate council)
Times are rapidly changing worldwide. These global businesses were damaged by bad executive decisions. Even some common business practices that were acceptable five to ten years ago are now illegal. No one in their right mind would want to suffer the fate of those poor souls.
New regulations for more-stringent financial and internal controls are driving business leaders into a controlled frenzy. You may have heard of the following: Sarbanes-Oxley Act (SOX, for corporations), Gramm-Leach-Bliley Act (financial transactions), Federal Information Security Management Act (FISMA, for government), Health Insurance Portability and Accountability Act (HIPAA), Supervisory Control and Data Acquisition (SCADA, for utilities), Fair and Accurate Credit Transactions Act (credit processing), Federal Financial Institutions Examination Council regulations (FFIEC), Payment Card Industry (PCI), and numerous privacy laws worldwide. These are just a sample of the regulations and regulators facing today's businesses.
All of these regulations require businesses to possess two simple components:
An asset is defined as anything of value, including trademarks, patents, secret recipes, durable goods, data files, competent personnel, and clients. Although people are not listed as corporate assets, the loss of key individuals is a genuine business threat. We can define a threat as a negative event that would cause a loss if it occurred. The path that allows a threat to occur is referred to as vulnerability. Your job as an IS auditor is to verify that assets, threats, and vulnerabilities are properly identified and managed to reduce risk.
In the past, businesses were allowed to operate with fewer restrictions. The problem with past regulation (or lack thereof) was that many organizations were taking risks that would have been unacceptable to investors and business partners had they been fully informed of corporate actions. Financial auditors were focused on bank balances and transaction totals proving to be correct. Increasing automation enables little mistakes to cascade into massive catastrophes. Stockholders, customers, and the government are looking for reassurance that management has taken the necessary precautions to prevent loss or corruption.
Our economy is founded on banking and investment. The majority of our global economy invests directly or indirectly in stock and financial markets. You may be an indirect investor through pension funds or bank investment portfolios. Unfortunately, there exists a group of individuals who view stock as their own private monetary system. How wonderful it must be to have our money at their disposal, without any terms of repayment, without interest or consideration, and without the requirement to ever pay the money back. Sounds ridiculous, doesn't it? But frankly, that is exactly how the stock market operates. You invest money with the hope that one day you will see something in return, knowing that you could lose it all.
One of the purposes of a controls audit is to ensure that there is reason to believe investors' money is protected from stupid mistakes. Our free enterprise strives to prevent another market collapse and protect the world banking system from crashing. We expect management to specify policies and to create procedures, processes, and safeguards to prevent loss and corruption. It is the job of management to design a solution that effectively protects corporate assets.
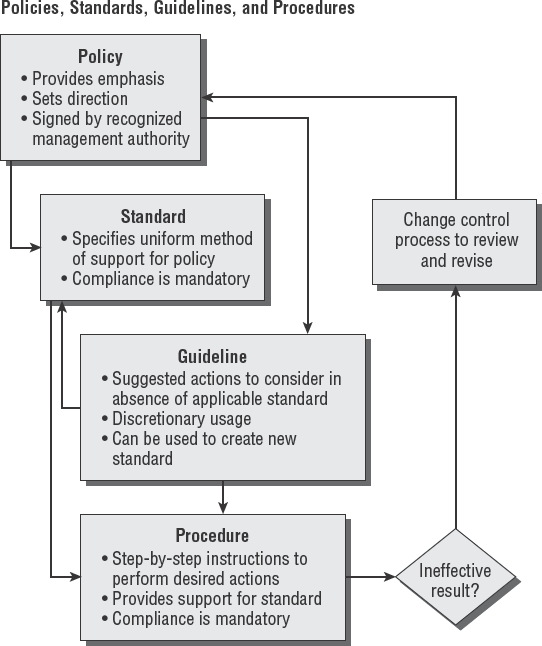
As an IS auditor, you must be familiar with the various policies, standards, and procedures of any organization or company that you are auditing. In addition, you must understand the purpose of your audit. You will look at those topics in this section.
A plethora of documentation exists in the operation of any organization. Management uses this documentation to specify operating and control details. Consistency would be impossible without putting this information into writing.
Organizations typically have four types of documents in place:
- Policies
These are high-level documents signed by a person of significant authority (such as a corporate officer, president, or vice president). The policy is a simple document stating that a particular high-level control objective is important to the organization's success. Policies may be only one page in length. Policies require mandatory compliance.
The highest level of people in charge is the officers of upper management. Chief executives, financial officers, and operating officers are the principal issuers of policies.
- Standards
These are mid-level documents to ensure uniform application of a policy. After a standard is approved by management, compliance is mandatory. All standards are used as reference points to ensure organizational compliance. Testing and audits compare a subject to the standard, with the intention of certifying a minimum level of uniform compliance.
Public standards include the International Organization for Standardization (ISO), Sarbanes-Oxley, and most government laws.
- Guidelines
These are intended to provide advice pertaining to how organizational objectives might be obtained in the absence of a standard. The purpose is to provide information that would aid in making decisions about intended goals (should do), beneficial alternatives (could do), and actions that would not create problems (won't hurt). Guidelines are often discretionary.
- Procedures
These are "cookbook" recipes for accomplishing specific tasks necessary to meet a standard. Details are written in step-by-step format from the very beginning to the end. Good procedures include common troubleshooting steps in case the user encounters a known problem. Compliance with established procedures is mandatory to ensure consistency and accuracy. On occasion a procedure may be deemed ineffective. The correct process is to update the ineffective procedure by using the change control process described later. The purpose of a procedure is to maintain control over the outcome.
Figure 1.1 illustrates the hierarchy of a policy, standard, guideline, and procedure.
The Information Systems Audit and Control Association (ISACA) set forth a code governing the professional conduct and ethics of all certified IS auditors and members of the association. As a CISA, you are bound to uphold this code. The following eight points represent the true spirit and intent of this code:
You agree to support the implementation of appropriate policies, standards, guidelines, and procedures for information systems. You will also encourage compliance with this objective.
You agree to perform your duties with objectivity, professional care, and due diligence in accordance with professional standards. You will support the use of best practices.
You agree to serve the interests of stakeholders in an honest and lawful manner that reflects a credible image upon your profession. The public expects and trusts auditors to conduct their work in an ethical and honest manner.
You promise to maintain privacy and confidentiality of information obtained during your audit except for required disclosure to legal authorities. Information you obtain during the audit will not be used for personal benefit.
You agree to undertake only those activities in which you are professionally competent and will strive to improve your competency. Your effectiveness in auditing depends on how evidence is gathered, analyzed, and reported.
You promise to disclose accurate results of all work and significant facts to the appropriate parties.
You agree to support ongoing professional education to help stakeholders enhance their understanding of information systems security and control.
The failure of a CISA to comply with this code of professional ethics may result in an investigation with possible sanctions or disciplinary measures.
Ethics statements are necessary to demonstrate the level of honesty and professionalism expected of every auditor. Overall, your profession requires you to be honest and fair in all representations you make. The goal is to build trust with clients. Your behavior should reflect a positive image on your profession. All IS auditors are depending on you to help maintain the high quality and integrity that clients expect from a CISA.
Note
Every CISA should have a strong understanding of these objectives and how each would apply to different audit situations.
Auditors are bombarded by certain people attempting to sway us from our straight and narrow course of honesty. Seemingly simple violations can become uncontrollable career killers. Do not allow yourself to participate in any situation that could tarnish your image as an auditor. Just having a false reputation of dishonest activity will quash your career like a black plague. Let's look at a few common examples:
Copyright violations. The possession, purchase, or distribution of bootleg materials will lead to forfeiting your CISA certification along with any other certifications requiring an ethics statement. You don't have to be convicted of a crime to lose your certification. Make sure that you purchase only genuine software and commercially licensed copies of printed material. Don't use anything except your own copies of materials that were rightfully obtained from the license holder. This includes copies of the ISO standards, software tools, special reports, and even this book or CD. Always be prepared to show the receipt and original product to prove you are honest and ethical. Lack of evidence implies guilt. Vendors' shipping records are an excellent source of proof. Trafficking in bootlegs provides an excellent route to living in jail.
Guilty people get amnesty for turning you in. It's unfair, but the guiltiest will typically get amnesty for turning someone else in for participation. So the person who says, "don't worry" is not worried. They secretly know that you will become their scapegoat at the first sign of trouble. Beware of any special deal or exception that can be used against you. The truth never stays secret.
Failing to follow your own rules. Make sure that you uphold the spirit and intent of the audit profession. The worst thing you could do to kill your career is to give the perception that you violate the rules yourself. It's necessary to "walk the talk" by doing everything right, just as you expect from your customer. By doing this religiously, you will become almost bulletproof.
Review the beginning of this chapter again if you need any examples of executives and auditors being "burned at the stake" for violating the public's trust.
Avoid violating the law. Being associated with a suspected scam is nearly as damaging as being convicted in the courtroom. The best way to stay out of trouble is to avoid questionable deals. Never accept a free or loaner copy of software from IT workers. It's a trap that usually involves someone bragging about how they helped you out by violating the law, ethics, or company policy.
Report violations promptly. Remember, the person reporting (in this case, you) will usually get amnesty, unless someone else turns you in first. You need to be prepared to turn over evidence unless you want to join others in their convictions. Honest auditors always report the truth. It's what keeps us in business.
An audit is simply a review of past history. The IS auditor is expected to follow the defined audit process, establish audit criteria, gather meaningful evidence, and render an independent opinion about internal controls. The audit involves applying various techniques for collecting meaningful evidence, and then performing a comparison of the audit evidence against the standard for reference.
If the assertions of management and the auditor's report are in agreement, you can expect the results to be truthful. If management assertions and the auditor's report do not agree, that would signal a concern warranting further attention.
Your key to success in auditing is to accurately report your findings, whether good or bad or indifferent. A good auditor will produce verifiable results. No one should ever come in behind you with a different outcome of findings. Your job is to report what the evidence indicates.
We can classify audits into three basic categories. Each of these represents a slightly different level of trust and unique objectives. The purpose is always to determine the truth.
- Internal audits and assessments
This involves auditing your own organization to discover evidence of what is occurring inside the organization (self-assessment). These have restrictions on their scope, and the findings should not be shared outside the organization. The findings cannot be used for licensing.
- External audits
External audits involve your customer auditing you, or you auditing your supplier. The business audits its customer or supplier, or vice versa. The goal is to ensure the expected level of performance as mutually agreed upon in their contracts.
- Independent audits
Independent audits are outside of the customer-supplier influence. Third-party independent audits are frequently relied on for licensing, certification, or product approval. A simple example is independent consumer reports.
So what will the CISA be asked to look at during an audit? Auditors are called to audit products, processes, and systems. Each of these requires a different approach. Let's review the basic approach required for each of these audits to be successful:
Product audits check the attributes against the design specification (size, color, markings). The 2007 hazardous toy recall of over a million Chinese-manufactured toys for Mattel is an example of using a product audit. The lead-based paint used on the toys was in violation of the design specifications. You can expect that CISAs will audit more software products than toys.
Process audits evaluate the process method to determine whether the activities or sequence of activities meet the published requirements. We want to see how the process is working. This involves checking inputs, actions, and outputs to verify the process performance.
System audits seek to evaluate the management of the system, including its configuration. The auditor is interested in the team members' activities, control environment, event monitoring, how customer needs are determined, who provides authorization, how changes are implemented, preventative maintenance, and so forth, including incident response capability.
Financial audit verifies financial records, transactions, and account balances. This type of audit is used to check the integrity of financial records and accounting practices compared to well-known accounting standards.
Operational audit verifies effectiveness and efficiency of operational practices. Operational audits are used frequently in service and process environments, including IT service providers. An operational audit is detailed in Statement on Auditing Standard 70 (SAS-70).
Integrated audit includes both financial and operational controls audits. An integrated audit is detailed in SAS-94.
Compliance audit verifies implementation of and adherence to a standard or regulation. This could include ISO standards and all government regulations. A compliance audit usually includes tests for the presence of a working control.
Administrative audit verifies that appropriate policies and procedures exist and have been implemented as intended. This type of audit usually tests for the presence of required documentation.
Information systems certification and/or accreditation. Certification usually involves system testing against a reference standard, whereas accreditation represents management's level of acceptance.
Now we need to move on to the different roles people play in the audit.
As an auditor, you are expected to fulfill a fiduciary relationship. A fiduciary relationship is simply one in which you are acting for the benefit of another person and placing the responsibilities to be fair and honest ahead of your own interest. An auditor must never put the auditee interests ahead of the truth. People inside and outside of the auditee organization will depend on your reports to make decisions.
The auditor is depended on to advise about the internal status of an organization. Audits are different from inspections or assessments because the individual performing the audit must be both objective and impartial. This is a tremendous responsibility.
As stated earlier, the audit is a formal process performed by a qualified independent auditor. To clarify, the following provides a comparison of an audit and assessment:
- Audit
An audit generates a report considered to represent a high assurance of truth. Audits are used in asset reporting engagements.
- Assessment
An assessment is less formal and frequently more cooperative with the people/objects under scrutiny. Its purpose is to see what exists and to assess value based on its relevance. The assessment report is viewed to have lower value (moderate-to-low value) when compared to an audit.
The primary goal of an assessment is to help the user/staff work toward improving their score. However, the audit is the score that actually counts for regulatory compliance purposes.
Remember that the basic control requirement is to separate the worker from the person providing authorization (separation of duties). Assessments are considered biased because the separation is not clean as it would be under a formal independent audit.
There are only two titles for persons directly involved in an audit. First is the auditor, the one who investigates. Second is the auditee, the subject of the audit. A third role exists which is normally outside of the audit, known as the client. ISACA refers to these as audit roles versus nonaudit roles.
Let's clarify the titles and basic roles of these people by their relationship to the audit. We can refer to them as members of the following categories:
- Auditor
The auditor is the competent person performing the audit.
- Auditee
The organization and people being audited are collectively called the auditee.
- Client
The client is the person or organization with the authority to request the audit. A client may be the audit committee, external customer, internal audit department, or regulatory group. If the client is internal to the auditee, that client assumes the auditee role.
Everyone else is considered outside of the audit roles. Audit details should be kept confidential from persons not directly involved as auditee or the client.
Your purpose as an auditor is to be an independent set of eyes that can delve into the inside of organizations on behalf of management or can certify compliance on behalf of everyone in the outside world. Independent means that you are not related professionally, personally, or organizationally to the subject of the audit. You cannot be independent if the audit's outcome results in your financial gain or if you are involved in the auditee's decisions or design of the subject being audited.
When determining whether you are able to perform a fair audit, you should conduct an independence test. In addition, you must remain aware of your responsibility as an auditor under the various auditing standards.
Here is a simple self assessment to help you determine your level of independence:
Are you auditing something you helped to develop?
Are you free of any conflicts, circumstances, or attitudes toward the auditee that might affect the audit outcome?
Is your personal life free of any relationships, off-duty behavior, or financial gain that could be perceived as affecting your judgment?
Do you have any organizational relationships with the auditee, including business deals, financial obligations, or pending legal actions?
Do you have a job conflict? Does the organizational structure require your position to work under the executive in charge of the area being audited?
Did you receive any gifts of value or special favors?
If any answer is "yes," you are not independent. Any conflicts will place a shadow of doubt on the objectivity of the audit findings. Only internal auditors (whose aim is to improve internal performance) can answer yes and still possibly continue the audit. External auditors are required to remain independent during an independent audit. Any potential conflicts should be disclosed immediately to the lead auditor. You may be reassigned to eliminate the conflict. The lead auditor may determine that the impact is low enough that you can remain in the role as long as the client sponsor is aware of the situation. Attempting to hide the truth is a bad idea. No conflict means you are cleared to proceed.
What if the client asks you to provide advice to their design staff while you are engaged as their external auditor? The unknowledgeable auditor could create a conflict or lose the client's respect. A good auditor would remind the client of the need for auditor independence. Imagine the power of the following statement that you, as a professional auditor, could make:
Sir/Madam, In my role as external auditor, I must remain independent of design decisions; otherwise, I would not be able to provide you the independence and objectivity required. Providing design advice would be a violation of several standards governing auditor independence, including public corporation audit standard AS-1, GAAP audit practices, ISACA professional standards, and Statement on Auditing Standards 1, 37, and 74 (SAS-1, SAS-37, and SAS-74).
Note
You are encouraged to explain what an auditor looks for during an audit. You must be careful not to participate in design decisions, detailed specification, or remediation during your role as the auditor. You may be hired to help with remediation; however, you will be disqualified from auditing any related work. The same principle applies to design work and system operation.
Auditors have the luxury of being able to rely on well-known accounting standards that have been accepted worldwide. The standards were originally developed for financial audits, but their spirit and intent also apply to IS auditing. Frequently, a minor adaptation will provide the foundation and detail necessary for use in IS audits. These standards allow you to render a fair opinion without fear of retribution or liability.
Understanding the basic types of audits: audits either verify compliance (compliance test) or check the substance and integrity of a claim (substantive test). Just how does an auditor know what to do in these audits? As an IS auditor, you are fortunate to have several credible resources available to assist you and guide your clients.
Among these resources are standards and regulations that direct your actions and final opinion. It would be quite rare to depart from these well-known and commonly accepted regulations. In fact, you would be in an awkward situation if you ever departed from the audit standards. By following known audit standards, you are relatively safe from an integrity challenge or individual liability. By adhering to audit standards, a good auditor can operate from a position that is conceptually equal to Teflon nonstick coating. Nothing negative or questionable could stick to the auditor.
You can learn more about auditing standards by reading and then implementing information provided by the following:
American Institute of Certified Public Accountants (AICPA) and International Federation of Accountants (IFAC).
Financial Accounting Standards Board (FASB) with Statement on Auditing Standards (SAS), standards 1 through 114, which are referenced and applied by the AICPA and IFAC.
Committee of Sponsoring Organizations of the Treadway Commission (COSO), providing the COSO internal control framework that is the basis for standards used in global commerce. COSO is the parent for the standards used by governments around the world.
Public Company Accounting Oversight Board (PCAOB) of the Securities and Exchange Commission, issuing audit standards AS-1, AS-2, AS-3, AS-4, and AS-5. PCAOB is the standards body for Sarbanes-Oxley, including the international implementation by the Japanese government and European Union (US-SOX, J-SOX and E-SOX).
Organization for Economic Cooperation and Development (OECD), providing guidelines for participating countries to promote standardization in multinational business for world trade.
International Organization for Standardization (ISO), which represents participation from more than member governments.
U.S. National Institute of Standards and Technology (NIST), providing a foundation of modern IS standards used worldwide. When combined with British Standards/ISO (BS/ISO), you get a wonderful amount of useful guidance.
U.S. Federal Information Security Management Act (FISMA), which specifies minimum security compliance standards for all systems relied on by the government, including the military and those systems operated by government contractors. (The U.S. government is the world's largest customer.)
IS Audit and Control Association (ISACA) and IT Governance Institute (ITGI) issue the Control OBjectives for IT (CObIT) guidelines which are derived from COSO with a more specific emphasis on information systems.
Basel Accord Standard II (Basel II), governing risk reduction in banking.
Although this list may appear daunting, it is important to remember that all these examples are in fundamental agreement with each other. Each standard supports nearly identical terms of reference and supports similar audit objectives. These standards will have slightly different levels of audit or audit scope. ITGA and ISACA have developed a set of IT internal control standards for CISAs to follow. These incorporate several objectives of the COSO internal control standard that have been narrowed to focus on IT functions. Let's look at a brief overview of the ISACA standards.
The members of ISACA are constantly striving to advance the standards of IS auditing. CISAs should check the ISACA website (www.isaca.org) for updates on a quarterly basis. ISACA added five new standards during 2006–2007 to clarify our minimum level of performance. The current body of ISACA Audit Standards is organized using a format numbered from 1 to 16:
- S1 Audit Charter
The audit charter authorizes the scope of the audit and grants you responsibility, authority, and accountability in the audit function.
- S2 Independence
Every auditor is expected to demonstrate professional and organizational independence.
- S3 Professional Ethics and Standards of Conduct
The auditor must act in a manner that denotes professionalism and respect.
- S4 Professional Competence
The auditor must have the necessary skills to perform the audit. Continuing education is required to improve and maintain skills.
- S5 Planning
Successful audits are the result of advance preparation. Proper planning is necessary to ensure that the audit will fulfill the intended objectives.
- S6 Performance of Audit Work
This standard provides guidance to ensure that the auditor has proper supervision, gains the correct evidence to form conclusions, and creates the required documentation of the audit.
- S7 Audit Reporting
The auditor report contains several required statements and legal disclosures. This standard provides guidance concerning the contents of the auditor's report.
- S8 Follow-up Activities
The follow-up activities include determining whether management has taken action on the auditor's recommendations in a timely manner.
- S9 Irregularities and Illegal Acts
This standard outlines how to handle the discovery of irregularities and illegal acts involving the auditee.
- S10 IT Governance
This standard covers the authority, direction, and control of the information technology function. Technology is now pervasive in all areas of business. Is the auditee properly managing IT to meet their needs?
- S11 Use of Risk Analysis in Audit Planning
This standard provides guidance for implementing a risk-based approach in audit planning. Risk planning is used to determine whether an audit is possible. Auditors always weigh our level of competency to conduct the audit. Audit plans should be structured for the maximum return on investment when designing specific audits, aka impact for the dollar spent.
- S12 Audit Materiality
Auditors must use evidence that portrays the most accurate story. The absence of controls or a potential weakness may cumulatively result in unacceptable risk to the organization. Ineffective controls, absence of controls, and control deficiencies should be disclosed in the audit report.
- S13 Using the Work of Other People
It's impossible for the auditor to perform all the work alone. The work of other experts may be included in the audit, provided the auditor is satisfied with their competencies, relevant experience, professional qualifications, independence, and quality control. A scope limitation may be required in the final audit opinion if the other experts do not provide appropriate and sufficient evidence. An expert working in the same area as the one being audited should not be relied on.
- S14 Proper Audit Evidence
Appropriate evidence includes the written procedures performed by the auditor, source documents, corroborating records, samples, and corresponding test results. Reliable evidence is based on its source, natural state, and authenticity. Audit evidence must be specifically identified, cataloged, and cross-referenced in the audit documentation, via auditor notes and working papers.
- S15 Effective IT Controls
Working IT controls represent an integral foundation in the organization's overall internal control environment. IS auditors should monitor and evaluate the effect or absence of IT controls. It's necessary to help management understand the IT controls' design, implementation, and methods of improvement. The level of effective controls provided by outsourcing, or their absence, may help or hurt the organization.
- S16 Electronic Commerce Controls
E-commerce allows the business to conduct electronic transactions with other businesses (business-to-business, or B2B) and directly to consumers (business-to-consumer, or B2C) over the public Internet. E-commerce requires the auditor to implement risk-based audit plans with data-gathering techniques for continuous assurances regarding the security and integrity of the environment. ISACA standard S16 excludes non-Internet-based private networks such as Electronic Data Interchange (EDI) and Society for Worldwide Interbank Financial Telecommunication (SWIFT).
Note
This chapter, as well as Chapter 2, "Audit Process," thoroughly discusses all the objectives contained in ISACA's audit standards.
During the audit process, you will find clients are more receptive when your audit goals are linked to specific citations in the audit standards. You should aim to fill a known and defined point of compliance rather than provide a vague statement relating to something you may have read in a textbook. Don't make the mistake of trusting your job to misinformation, rumors, or free advice on the Internet.
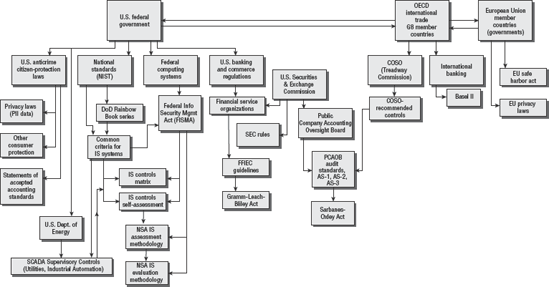
Most of the IT controls originated from demands imposed by a government agency. Security started in the military. Budgets and financial tracking were introduced by the banking industry. In fact, the first internal control in business was the budget. Since 1998, additional internal controls have been added each year. Figure 1.2 demonstrates the relationship of these various sources.
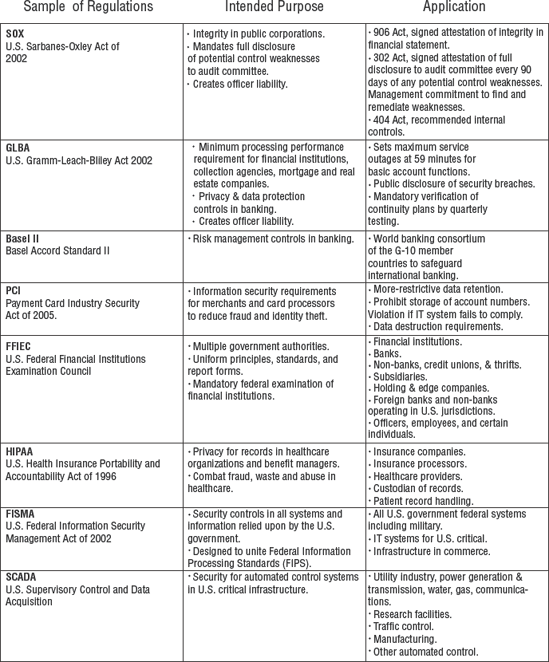
Let's review the basic purpose of several major regulations (see Figure 1.3). These are predominantly U.S. regulations with worldwide compliance implications due to global outsourcing.
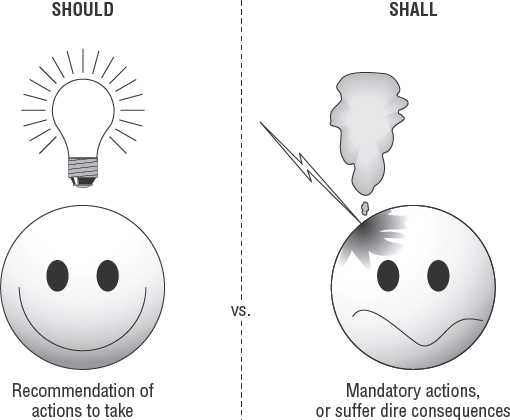
Every regulation is designed to mandate the minimum acceptable requirements when conducting any form of business within that specific industry. The auditor must remain aware of two types of statements contained in all regulations:
- Recommended (discretionary)
These are actions that usually contain statements with the word should—for example, suggested management responsibilities, staffing, control mechanisms, or technical attributes.
- Required (mandatory)
These are actions that contain the word shall. Shall indicates that statement is a commandment of compliance. Shall is not optional. The auditor must remember that failing to meet a required Shall objective is a real concern. The regulations serve to protect the citizens at large.
Incredible justification would usually be required to prove the organization's actions do not fall under the jurisdiction of the regulation. The regulator will accept no excuses without a major battle and on almost every occasion will win any potential disputes. Most juries comprise individuals who will interpret claims by using a basic commonsense approach without detailed knowledge of a particular industry. Almost all excuses for violating the regulatory objective have failed in court battles.
Each organization in that market is required to meet the objective in spite of cost or revenue issues. In other words, the organization must comply even if it means that compliance will cause the organization to lose money. Failure to make a profit is not a valid exception from the law. The organization must strive to obtain compliance or can be forced to exit the industry with fines and sanctions. The auditor may need to consult a lawyer for advice upon discovery of significant violations.
IS auditors may be engaged in a variety of audits. The only fundamental difference between internal and external audits is auditor independence. Although the focus and nature of the audit may vary from time to time, your audit function and responsibilities will remain constant.
Note
Medium-to-large businesses undergo a quarterly audit for their financial statements. IS auditors are called upon to determine whether the systems used for financial reporting are trustworthy. The goal is to ensure that the executives are held accountable for the accuracy of financial reports. A common defense is to claim someone else committed any offenses creating misrepresentation. However, a well-managed IS environment prevents and detects unauthorized modifications. This connects the integrity of the financial statement to the integrity of the IS environment. With this level of combined control, you will have integrity.
Government interpretation of laws and regulations has determined that financial audits and internal controls are interrelated. You could not ensure the integrity of one without verifying the other. As an example, consider the requirements specified under SOX for public corporations. There are two critical reporting functions that management must fulfill under SOX:
SOX Act section 906 statement, in which management attests to the integrity of financials and indicates that no hidden or questionable transactions exist.
SOX Act section 302 statement, in which management attests that full disclosure of the section 401–404 internal controls has been made to the audit committee, and that no deficiencies or weaknesses were withheld.
Management must make their assertions of compliance without reliance on the auditor. The intention of these two statements is to bind management with liability. SOX is essentially a disclosure law. Its purpose is to provide government authorities with a method of ensuring criminal prosecution of corporate officers if management misrepresents the truth.
As an IS auditor, you should remain aware of your leadership responsibilities.
Many people are envious of the CISA's position. They see nice cars, lunches with important people, expensive suits, and comfortable expense accounts. Nobody seems to pay attention to the humorous situation of six auditors sharing one folding table while sitting in a closet, balancing laptop computers with only one network jack and one telephone to share. Frankly, the auditor position grants you the luxury of being well-paid observers with professional benefits. Occasionally, your office and travel accommodations may not be the best. However, the reality is that most people look up to auditors with respect.
Your clients expect you to be authoritative and professional regardless of the circumstances. Your office is mobile, so you are depended on to handle decisions in the field. Your clients include the highest levels of management within an organization. Those clients expect you to assist them with your observations and occasional advice. You will deal with the challenges of providing advice in a manner that does not interfere with the independent audit. Remember the independence question raised earlier in this chapter?
Personnel at every level of your client's organization have an expectation of your appearance. You are going to be judged by your speech, mannerisms, clothing, and grooming. You should always wear professional attire to a level more formal than the attire of your client. Your neat and pressed appearance instills respect and confidence. Your courtesy of manner and speech dictates that you should use reassuring words. Any humor by the auditor should always be restrained and professional.
The client entrusts the auditor with sensitive information. A good auditor would never betray that confidence nor allow sensitive information to be revealed at any time. Any breach of confidentiality would be unforgivable. It is conceivable that during your audit, you may discover information that could cause some level of damage to the client if disclosed. You should prepare for the possibility of detecting irregular or even illegal acts that have occurred.
To protect yourself, you must exercise caution and least privilege in all activities. The concept of least privilege refers to providing only the minimum information necessary to complete a required task. It is the auditor's responsibility to implement security controls to maintain confidentiality. An auditor's working papers contain details and secrets that need to be protected. The information you're privy to may be alarming to some, damaging to others, or trigger additional actions by a perpetrator.
To ensure confidentiality, the auditor should adopt the following operating principles:
Sensitive information is the property of the owner and should not be removed from their office by the auditor.
The auditor should contact legal counsel for advice concerning confidentiality and laws that would dictate disclosure to authorities. You should follow basic principles of confidentiality at all times.
Many auditors use automated working papers (WPs) during an audit. Spreadsheets and report-writing templates are common tools to increase efficiency. We refer to audit checklists, procedures, computer-generated output, templates, and databases as working papers. The next level of automation is entering our workplace to aid even the smallest auditor. This includes more-advanced database automation, evidence tracking, and report-generation tools. The data must be protected with access control and regular data backup. Make sure to back up your work. It would be unforgivable to lose your audit work and client data by failing to implement your own controls.
Every auditor should seriously consider using locking security cables and privacy viewing screens for laptops. You will gain respect by demonstrating your concern for maintaining confidentiality while protecting assets. The laptop could still be stolen with broken parts lying on the floor, but at least you would have some evidence that the theft was not completely your fault. At prior audit firms where I worked, these controls were mandatory for continued employment.
A document file archive is created during each audit. The archive is subject to laws governing records retention. Every auditor is advised to leave all records in the custody of the client unless criminal activity is suspected. The client shall maintain sole responsibility for the safe retention of the archive.
There is much discussion concerning who should hire the auditor. Is it the client or is it their lawyer? At stake is the legal argument of confidentiality under attorney-client privilege. Most communication between lawyers and the client may be exempt from legal discovery (disclosure).
We suggest that you ask the client. If necessary, the lawyer could issue a letter authorizing the auditor's work on their behalf. As an auditor, you have to be able to do your job without intimidation in order for it to be fair and honest work. This should be spelled out in the audit charter or your engagement letter. A good auditor will leave the legal issues to the lawyers and focus on their job of performing a good audit. Truth often serves as an excellent defense.
In most cases, the archive of the integrated audit may need to be kept for seven years. Each type of audit may have a longer or shorter retention period, depending on the regulations identified during audit planning. If the client loses the files, that would be their problem and not yours.
Note
When I hear that a client does not have a complete archive, the first sound in my head is chi-ching! I get to charge them extra money for re-creating the missing documentation.
During an audit, you will be preparing reports and documentation on laptops belonging to members of your audit staff. All members of the audit team should practice good physical security, including using physical cable locks on the laptops and locking up sensitive files each evening or when not in use. You must be wary of prying eyes and big ears. It is advisable for the audit team to implement a designated "war room" as a secure work location. Meetings and interviews with all other persons should occur in a different location that is also safe from prying eyes and ears.
Have you ever felt nervous, threatened, or intimidated? What are your own feelings when you're told an auditor is coming to visit? Nothing launches a person's defensive attitude faster than the threat of an audit. A good auditor understands client expectations and realizes it is necessary to take time to speak with customers who may be curious or nervous.
It is a good idea to alleviate fear and anxiety by implementing the following objectives with your client:
The auditor's job is to be a second set of eyes and ask the right questions.
Establish mutual respect. To be successful, mutual respect must exist between the auditees and auditor. When you find a problem, do not place blame on a specific individual, because the very person you are speaking with could be the one who made the poor decision. Do not insult your client; just stick to the facts. You could say the following: "Based on the information available at the time, it may have looked like an acceptable idea; however, it is time for you to consider. . ." A good auditor is always respectful of other people and their feelings.
Note
As a former auditee, I always appreciated an auditor who took the time to explain to me what the audit would entail. Please keep in mind that the auditee feels at a disadvantage. It will be helpful to simplify your explanations. You can measure your own performance by the general attitude toward you at the auditee site. You are doing a good job if the client shows interest and is forthcoming with truthful answers.
A good auditor spends time planning and setting priorities before commencing an audit. You will need to make plans on how you will be working with your own team. Develop the leadership style you want to implement. The days of Captain Bligh shouting orders "lest ye be flogged" are gone.
Let's look at the characteristics of good leadership:
Your leadership style needs to clearly identify when your directions are mandatory and when they are open to feedback and comments. Team members should feel comfortable making comments and asking questions.
A good leader will develop specific requirements for success and then share those plans. A good leader will strive for the buy-in and cooperation of the staff. You cannot lead those who do not want to be led or those who do not understand the objectives.
An old and still valuable leadership lesson states that the staff holds the fate of their manager in their hands. The manager will be promoted or disgraced by the performance of their staff. If your people believe the work is good, you will usually get good results. If they do not believe in what you're doing, it will become a failure. Your personal opinion of good or bad is not the pinnacle factor. What matters is what the staff believes. True believers can generate exceptional results. Making time to educate your staff and demonstrating a willingness to take criticism are traits of a good leader.
The audit manager is responsible for creating clearly defined responsibilities and authority. There can be only one boss in order to prevent confusion. It is the responsibility of this one boss to make the hard decisions and answer for the choices made.
A regular schedule of briefings for both the auditee and the audit team are required. All client communication should be vetted before it is shared. Vetting is the process of evaluating and editing words to obtain the desired outcome.
Good auditing is the result of proper planning, not magic or luck. Every audit starts with an audit charter or engagement letter. The customer will define the focus and scope of the audit. It is the auditor's responsibility to gather pre-audit information and develop a schedule integrating the audit team functions with the customer's schedule. To be successful, a project management methodology should be used.
Let's look at a few of the auditor's responsibilities during the planning phase:
Gaining an understanding of the customer's business
Respecting business cycles (monthly, quarterly, seasonal, and annual)
Establishing priorities
Selecting an audit strategy based on risk and information known or observed
Finding the people for your audit team
Coordinating the logistics prior to the audit for resources, work space, and facilities
Requesting documents (discovery requests)
Scheduling people's time and availability
Arranging travel and accommodations
Planning for delays or nonperformance
Considering rescheduling if recent downtime or risks warrant it
Developing alternative strategies
Developing a briefing schedule
Note
We will be spending a significant amount of time on the subject of audit planning in the next chapter.
A professional auditor provides the auditee with a list of basic requirements and necessary resources well in advance of the audit team arrival.
A good auditor gives plenty of notice as to what they need to perform their job. This includes documentation requests for manuals, policies, and procedures that will be included in the subject of the audit.
Note
We are astounded by how many times auditors fail to request sufficient desk space and access to IT resources prior to an audit team's arrival.
The auditor needs to remain fair and objective when executing an audit. As an auditor, you should be consistent and courteous to your clients. Standard terms of reference can be developed to promote respectful and honest interpretation. As an auditor, you should try using the following terms, or something similar:
A good auditor recognizes that some degree of conflict is inevitable and failures are always possible. IS auditors face the challenges of time, money, resources, and attitudes.
These challenges may be with the client or with the auditor. The auditor must always demonstrate professionalism. An exceptional auditor will exercise common sense with a quick response. An exceptional auditor uses past experiences and makes the job look effortless, especially when dealing with change or conflict.
In this Study Guide, we as authors are often implying an external auditor position. This is intentional in order to emphasize auditor independence. However, substantial opportunities exist for both internal and external auditors.
External auditors are paid to be independent reviewers for an organization. Internal auditors can add enormous value to an organization by providing ongoing efforts that help prepare the organization for an external audit. The internal auditor could approach the situation with an attitude of independence even though they will be unable to certify or attest final results. Their expert audit skills could help guide design and remediation efforts at a substantially lower cost than that of their external counterparts.
Note
In the internal auditor position, I would focus my efforts on reducing a four-week external audit to only ten days. Depending on the organization, it may take a few years to reach this noble objective. In the meantime, my auditing services will definitely be adding value to the organization through emphasis and cost reduction. Internal auditors can aid every organization by improving evidence collection.
The audit world revolves around the collection and review of reliable evidence. Without evidence, a claim or assertion is unverifiable and an auditor cannot separate fact from fiction. Good evidence is intended to substantiate a claim or prove the existence of something you have interest in knowing.
A good auditor will use sufficient evidence to formulate their auditor's opinion. No opinion can be formed when you lack evidence of acceptable quantity, relevance, and reliability. Your job is to be a professional skeptic and demand proof in the form of evidence you can verify. The best evidence will need little explanation to interpret. When more judgment is required to understand the evidence, that evidence has decreased value. Your job is to render a score based on the evidence captured during the audit. Having no evidence would warrant a zero score.
Let's suppose you are looking for evidence concerning an existing corporate policy. First, you would look for the policy itself. Is it a paper or electronic document? Documents that cannot be located within a couple of hours could be assumed not to exist. Inability to find the policy would indicate it is not actively used. Now assume the client has found a copy of the policy. Was it easily accessible or covered with dust?
The next step is to verify that you have the current edition. Your audit charter may or may not ask you to review (test) the contents of the policy. Either way, you will need to verify that the policy is actually in use by the client's organization. You might conduct a random survey of workers, asking whether they can show you a current copy of the policy.
Next, you would ask questions to see whether the workers had actually read the document.
Note
It is not uncommon for an auditee to respond that the policy is on their website. You should ask the person to show you the link and open the page. You want to know if the client can successfully demonstrate an ability to find the document.
However, existence of the policy alone does not meet the evidence rule. The auditee's score would improve as more persons demonstrate that they read the document.
Another method would be to look for notes containing the minutes of meetings where the policy was discussed. It is rare for a policy to exist without some form of questions being raised or argued. Challenges to the policy may exist in emails. You may also ask for a person to perform the tasks related to the policy and observe their actions. Direct observation is powerful evidence. Simply ask the client to reperform a task whenever you want to cut to the heart of a claim. The words show me can invoke either fear or pride depending on the truth of the situation. Once again, no evidence equals no score.
Note
We will discuss evidence again in Chapter 2.
As an IS auditor, it is important for you to be cognizant of whom you should be interviewing, and how long those interviews should take. Every auditor will frequently face a time crunch due to the customer's schedule or other issues. You will need to pay particular attention to the value of the others' time. Consider the work outage created when you take someone out of their job role to spend time with you. Will it be necessary to backfill their position by providing a substitute during this time away?
Think for a moment of what it would cost the organization for a key executive to spend 15 minutes with you. This executive's time may be measured in personal compensation or by the revenue they generate for the organization. Top executives, such as the CEO, will have compensation packages that include both money and substantial shares of stock. Based on total compensation, the CEO may be receiving several thousand dollars per hour or more.
Note
Former Walt Disney CEO Michael Eisner received compensation equal to $27,000 per hour, which was equivalent to approximately .01 percent of the revenue generated under his leadership during the same time period.
The moral is that to justify 15 minutes of somebody's time, you better have something to discuss that is of greater value than his prorated value to the organization (greater than prorated revenue + compensation). Consider the cost for a meeting of high-level executives. You need to ensure that the time spent is relevant and remains focused on the audit objectives. The savvy auditor respects the value of a person's time.
Every system will have an inherent need for controls. The auditor needs to ensure that discussions occur with the correct individuals concerning appropriate controls. Three basic IT-related roles exist for every system: owner, user, and custodian. Table 1.1 shows examples of individuals with their associated roles and responsibilities.
Table 1.1. Responsibilities of Data Owner, User, and Custodian
Example | Basic Responsibilities | |
|---|---|---|
Data owner | Vice president | Determine classification Specify controls Appoint custodian |
Data user | Internal business user Business partner Business client (web) | Follow acceptable usage requirements Maintain security Report violations |
Data custodian |
Database administrator Production programmer System administrator | Protect information Ensure availability Implement and maintain controls Provide provisions for independent audit Support data users |
These individuals don't have to work in the IT department. On the contrary, these roles exist regardless of the individual department boundaries. If someone performs the function, the responsibility of the role applies to that person. No exceptions. If a person performs two roles, two sets of responsibilities apply. If someone performs all three roles, either it's a one-person operation or you need to have a talk about separation of duties and the value of their data.
It is always helpful for the auditor to clearly understand the relationships and responsibilities at different levels of an organization. The auditor needs to understand who holds the authority. Let's focus on some basics that will be pervasive throughout this book.
Businesses are focused on generating money for investors. There will always be some type of management hierarchy in order to maintain control. Government and nonprofit organizations will use a similar control hierarchy; however, the titles will be different. For government and nonprofit organizations, the term mission objectives would be substituted for the term revenue.
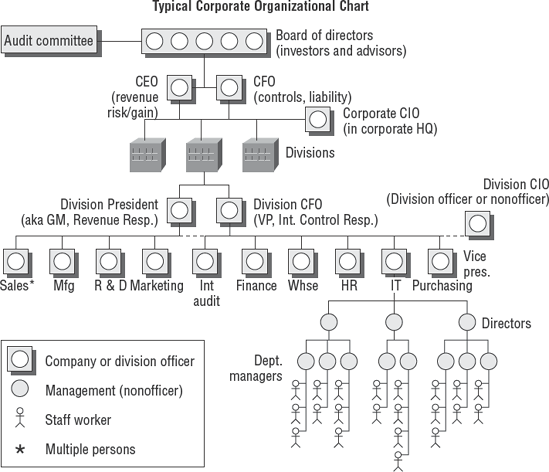
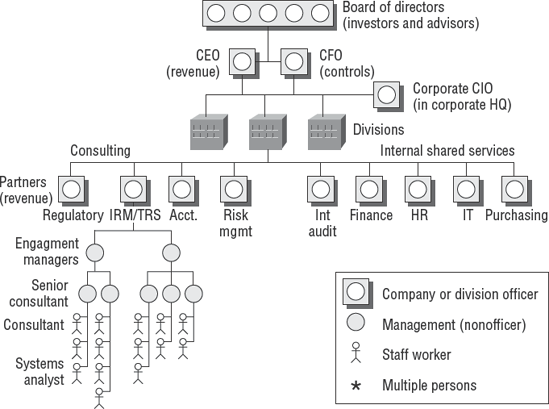
Figure 1.4 illustrates a typical business corporation. Let's start at the top of the diagram and work our way down:
- Board of directors
The board of directors usually comprises key investors and appointed advisers. These individuals have placed their own money at stake in the hopes of generating a better return than the bank would pay on deposits. Board members are rarely—usually never—involved in day-to-day operations. Some members may be retired executives or run their own successful businesses. Their job is to advise the CEO and the CFO. Most organizations indemnify board members from liability; however, government prosecutors will pursue board members if needed.
- Audit and oversight committee
The members of the board will have a committee comprising directors outside of the normal business operations. Executives from inside the organization can come to the committee for guidance and assistance in solving problems. This committee has full authority over all the officers and executives. They can hire or fire any executive. Each audit committee has full authority with a charter to hire both internal and external auditors. Auditors are expected to discuss their work with the audit committee. An auditor has the right to meet in private to discuss issues with the audit committee once a year without the business executives present. If auditors discover certain matters that stockholders should be informed about, the auditor shall first bring it to the attention of the audit committee. Regulations such as SOX require that all significant weaknesses be disclosed to the audit committee every 90 days.
- Chief executive officer (CEO)
The CEO is primarily focused on generating revenue for the organization. The CEO's role is to set the direction and strategy for the organization to follow. The CEO's job is to find out how to attract buyers while increasing the company's profits. As a company officer, the CEO is liable to government prosecutors. Corporate officers have signing authority to bind the organization.
- Chief operating officer (COO)
The COO is dedicated to increasing the revenue generated by the business. This is a delegate in charge of making decisions on behalf of the CEO with assistance from the CFO. COOs are often found in larger organizations. As a company officer, the COO is liable to government prosecutors.
- Chief financial officer (CFO)
The CFO is in charge of controls over capital and other areas, including financial accounting, human resources, and IS. Subordinates such as the CIO usually report to the CFO. As a company officer, the CFO is liable to government prosecutors.
- Chief information officer (CIO)
The CIO is subordinate to the CFO. The CFO is still considered the primary person responsible for internal control. A CIO might not be a true company officer, and this title may bear more honor than actual authority, depending on the organization. An exception may be the CIO in the corporate headquarters. The CIO has mixed liability, depending on the issue and their actual position in the organization.
- President/general manager
The president, sometimes referred to as the general manager, is the head of a business unit or division. As a company officer, the president/general manager is usually liable to government prosecutors. Regulations such as SOX encourage management to require all divisional presidents and controllers to sign the integrity statements in an effort to increase divisional officer liability.
- Vice president (VP)
The vice president is the second level of officer in a business unit or division. As a company officer, the vice president is usually liable to government prosecutors.
- Department directors (line management position)
Typically directors are upper-level managers supervising department managers and do not have company officer authority. In large organizations, you may encounter a major-level director and minor-level director.
- Managers and staff workers
Managers are responsible for providing daily supervision and guidance to staff members. Staff members may be employees or contractors working in the staff role. Managers and staff members are seldom held responsible for the actions of a company unless they knowingly participate in criminal activity.
Now we will look at the structure of a typical consulting firm. A consulting firm is a hybrid organization. Internal clerical and support functions are similar to those in a typical business. The consulting side of the firm uses functional management positions. The staff is allocated according to temporary project assignments. At the end of each engagement, the staff will be reallocated by either returning to the available resource pool or by becoming unemployed until the next engagement.
Figure 1.5 illustrates the organizational structure of a typical audit firm. We'll review the structure here:
- Managing partner
A managing partner refers to a C-level executive in the consulting practice. This could be a position equal to a corporate president. Managing partners have the responsibility and authority to oversee the business divisions. Various partners in the firm will report to the managing partner.
- Partner
A partner is equivalent to a divisional president or vice president and is responsible for generating revenue. Their role is to represent the organization and provide leadership to maximize income in their market segment. Partners are required to maintain leadership roles in professional organizations and to network for executive clients. Most partners have made financial commitments to produce at least $15 million in annual revenue along with supporting other business management functions. The partner and all lower managers are responsible for professional development of the staff.
- Engagement manager
This is a director-equivalent position with the responsibility of managing the client relationship. The engagement manager is in charge of the audit's overall execution and the audit staff. The engagement manager is responsible for facilitating the generation of new income opportunities from the client.
- Senior consultant
This is a field manager whose responsibilities include leading the daily on-site audit activities, interacting with the client staff, making expert observations, and managing staff assigned to the audit.
- Consultant
This is a lead position carrying the responsibility of interacting with the client and fulfilling the audit objectives without requiring constant supervision. A consultant is often promoted by demonstrating an ability to fulfill the job of senior consultant or supporting manager.
- Systems analyst
This is usually an entry-level position. Often the individual is selected for their ambition and educational background and may be fresh out of college. Systems analysts perform some lower-level administrative tasks as they build experience.
A typical IS audit has many elements in common with projects and project management. We believe that the two disciplines go hand in hand. To excel in auditing, you must excel at project management. Through project management, you define what you strive to accomplish and the actions that will be taken as part of the project.
Note
During our careers, we have worked with organizations using each of the different models for managing projects and quality. The project models are used for unique events or to refresh quality-control programs. The quality-control programs require every person in the organization to be trained and participate in support of every quality effort. Projects are typically run with less overhead, using smaller groups of people focused on a particular goal.
Table 1.2 shows the most common models for either managing projects or ensuring quality.
Table 1.2. Project Management and Quality-Control Models
Source | Focus | Structure |
|---|---|---|
Projects (international) Unique or repeating for everyone | 44 process areas Well defined, especially initiating solid projects | |
Prince2 | Projects (UK) Unique or repeating for the British government | 9 process areas Less defined than PMI |
Quality control Repeating process control | Zero defects program Statistical process control Invented by William Shewhart (1930) and better known from works by Phillip Crosby and Edwards Deming | |
Quality control Repeating process control | Reduce defects from 16,000 to 3.4 per million Motorola derivative of TQM for widget-type mass production. | |
Quality control Repeating process control | Revision of ISO 9000 quality standards International derivative of TQM |
The Project Management Institute (PMI) is one organization that stands above all others for defining project management and commercial project management processes.
PMI has created a definitive standard for managing projects. This standard is called A Guide to the Project Management Body of Knowledge (PMBOK), detailing a complete process framework and recipe for successfully managing a project. The first version was published in 1987. This guide is now updated every four years. The third edition was released in 2004, with a revised fourth edition expected in 2008. The PMBOK provides project managers a framework of processes to professionally manage both large and small projects.
In this section, you will learn some basic information about using the PMBOK standard to help you manage your audit. It would be a very good idea to acquire additional knowledge about project management and how to manage specialized projects. We suggest two sources for additional information:
CertTest Training Center (
www.certtest.com)—the company we work for—for training courses in project management. CertTest is a PMI global Registered Education Provider (REP). In addition to CISA training, we teach people how to become exceptional project managers.PMI (
www.pmi.org) for additional information about the project management standard, ordering copies of the PMBOK, or information about becoming a certified Project Management Professional (PMP).
The purpose of a project is to create a better result than would naturally occur. If you have so much money that you can just write a check for whatever you want, that would not be a project, only an expense. The purpose of a project is to help overcome the limitations of time, resources, and quality. All projects have three characteristics that define it as a project rather than a perpetual ongoing program.
- A project is temporary.
The project has a defined start (beginning) and a definite end (stop). The project is not an ongoing operation of the company. It lasts for only a specific time period.
- A project is unique.
All projects are run for a unique purpose. The project will create a product or service with unique characteristics. It may be used to fix something broken or to add new features.
- A project is progressively elaborated.
The project starts out with simple high-level ideas that are polished and becomes defined into more and more detail during planning. Each successive version of the plan adds details about the definition of work and the purpose. Interrelated processes are used to further define and control the project.
Let's discuss each of these project characteristics as they relate to auditing:
- What defines a project as temporary?
Your project must have a start date and an end date. For example, SOX requires the organization to report their status of internal controls on an annual basis with their annual financial filings. The SOX regulation also requires weaknesses to be assessed and disclosed to the organization's audit committee every 90 days (quarterly). Performing multiple internal security control audits in multiple departments over the calendar year is an ongoing business operation, yet each individual audit is a separate entity with separate definitions (scope) and goals. The individual audits with specific scope are projects.
Tip
Each little audit project adds up to create the overall compliance program.
- What defines your project as unique?
You are probably using the same processes and similar procedures for each audit. Auditing a new functional area that has never been audited before will have unique goals or outcomes. This is certainly a project. Performing the audit again next year will have to include changes to match the differences in the environment since last year. Its evolutionary successor audit is a unique project as well. Each audit uses similar processes and has similar goals, but the data, new tests, samples, and outcome will be unique. It never fails that the software version or the people involved have changed since the last time. You will be revising your plans before each audit.
Tip
Projects are always unique events of limited duration. Programs are simply a series of smaller projects tied together to keep things running.
- How do we define progressively elaborated?
The PMBOK defines 5 major process groups and 44 specialized processes for managing a project. These processes take a project from a high-level vision down into more and more detail to create your final product. The processes flow from one process to the next and act as a framework to guide proper definition with built-in control.
All of the processes interrelate to manage your efforts and to generate the final outcome. PMI set forth standards of planning that will help you convert a good idea into a deliverable product. It is not a magic spell that converts a bad idea or poor decisions into a good product.
Let's apply this to an example for auditing. The first step of a project is to get a signed project charter. The project charter is signed by the client sponsor to give the project manager responsibility, authority, and accountability for the project (exactly the same as an audit charter). This charter authorizes the project and provides the money necessary to begin.
Next you use the project charter as input for developing your preliminary scope statement. Your preliminary scope statement adds more details to describe the high-level project activities. You will use this as input (along with the project charter) to create a scope plan. In scope planning, you further define how the scope will be controlled—with a scope management plan.
You continue to use the information in the previous documents as more input for the Scope Definition process. The objective is to elaborate and document the total scope of the project in the final scope statement. After the scope is complete, you can move down into more and more detailed planning. It may seem like a lot of work, but this is the best way to cut through politics. Besides, good planning with clear definition is the way you avoid stupid mistakes. It's impossible to delegate work when people don't agree on what the work entails. The better your planning definition, the more likely you will get to actually enjoy a peaceful vacation or day off.
We can relate this portion of the process to a security audit: getting authorization to audit (project charter), defining a high-level need (preliminary project scope), planning how to handle change to the audit scope (scope planning), and then setting the goals and objectives as well as documenting all items to be audited (scope definition).
This describes just the first four processes and their relationship. There are 40 more processes available to help us make every project a success.
Project management is defined in the PMBOK as the application of knowledge, skills, tools, and techniques to perform the activities needed by your project requirements. A good project manager will use their knowledge of the subject, their knowledge of project management, and all available processes to fulfill the goals of their project.
A simple definition of project management is to balance competing demands. These demands are referred to as the triple constraint. We can define them as competing values of
Scope
Resources (cost, time)
Quality
Think about it: Could you ever satisfy all the items on your to-do list within the budget and available time? Maybe if the scope is small or you win the lottery. Could you finish the project in the time allotted and not fulfill all the to-dos? What effect will time or scope have on your project's objective? Managing competing demands determines whether a security audit is complete when it is due or when all necessary items have been properly audited. The project scope document will help you defend your decision. Project managers and audit managers will have to work with multiple stakeholders while managing the project and the competing demands. Stakeholders are defined as anyone with viable interest in the project. Stakeholders can be above the project manager in the organization, below the project manager, or peers. Stakeholders can also be outside the organization.
It is stressed that the project manager should concentrate on the defined scope of the project. Our motto is that "all the scope and only the scope" should be done. Sometimes the project manager will be required to make difficult decisions to balance the competing demands of scope, time, and cost. This will require negotiation skills or leadership skills to "sell" an unpopular decision.
Note
The CISA exam will expect you to understand project management. You need to be prepared to explain project management terminology and objectives. As practitioners, we have found that the PMI reference information provides an excellent fit in the audit world.
A project manager must have several levels of knowledge and skills to be successful:
Project management knowledge and skills. (Know how to lead and control projects.)
General management knowledge and skills. (Understand the business details.)
Interpersonal skills. (Be nice yet convince people to agree.)
Application area knowledge and skills. (Know how this darn thing actually works.)
Without all of these elements, the project manager has problems leading to an unsuccessful end. Many times we need some form of "expert judgment" to define our needs. The problem is compounded by a misunderstanding of who is qualified to be an expert.
Tip
Real experts will have more experience than anyone else, or special training with direct experience. A real expert will form the correct conclusion when others will not. For example, Burt Rutan could be considered an expert on building low-cost spacecraft because of his direct experience in successfully developing the SpaceShipOne reusable fiberglass spacecraft. He is the winner of the scientific industry Ansari X Prize, as the first commercial venture to successfully launch a privately owned, manned spacecraft into orbit and return safely back to earth.
Without specialized application knowledge and skills, the project manager would not know what specific requirements were needed or specific tasks must be accomplished to fulfill the project goals.
To translate this into controls auditing, the auditor must have the following:
Project managers are not created equal. Their level of authority and influence is dictated by the organizational structure and culture. The same issues exist in managing the audit as would exist when clients are managing their own projects.
Table 1.3 demonstrates the basic differences among management structures and cultures. Every auditor needs to understand the advantages and disadvantages of each.
Table 1.3. Differences in Project Manager Authority and Organizational Structure
Organization Type | Advantages | Disadvantages |
|---|---|---|
Functional (Weak matrix) | Functional manager remains in charge. Project manager has no real authority. Good for recurring operations-oriented projects in which change is very small. | Project manager has no formal authority. Project manager is a low-level staff function that needs to beg for resources or rely on personal influence. Common titles are project leader, coordinator, or expediter. |
Balanced matrix | Project manager shares authority with functional managers. Staff members are dedicated to the project manager. Functional department manager provides HR support and paychecks. Allows for efficiency in resource use. | Project manager and functional manager usually wind up arguing over resources. Without clear direction, team members may feel torn between two bosses. |
Projectized (Strong matrix) | Project manager holds formal authority and has the ability to decide project direction with little second guessing or interference. Authority level improves team dynamic and communications. | Project manager's success or failure is based on project results. This encourages hoarding of resources with competition toward other groups. Jobs in the project will end upon project completion. Expect a lack of focus toward the end as people search for employment. |
The PMI standard for project management as defined in the PMBOK is intended to be applied to all sorts of projects in all sorts of environments. The project manager may use all or some of the processes along with their inputs, tools, and techniques, and outputs for the project they are managing. The use of these processes is need based. The PMI processes provide an excellent checklist to prevent errors and omissions in the project management of any specific project.
As previously stated, we look upon the PMI standard as a framework for project management. You and your company define specific specialized processes and procedures to be used for project management within your enterprise. PMI provides this standard for you to measure your internal processes against.
The PMBOK provides a reference for defining the project life cycle. Your organization may decide to modify this life cycle to meet the unique challenges facing your needs. There is also specific definition of a project phase. Consider that each phase:
Is defined by the organization
Is part of the life cycle
Is a subset of the overall project
Has a measurable deliverable
Ends with a review
PMI places the project management framework as defined in the PMBOK into the specialized life cycle and phases that are defined by the organization. The PMBOK focuses on process groups, processes, inputs to processes, tools and techniques used in processes, and outputs from processes.
A simple outline of this framework would look something like this:
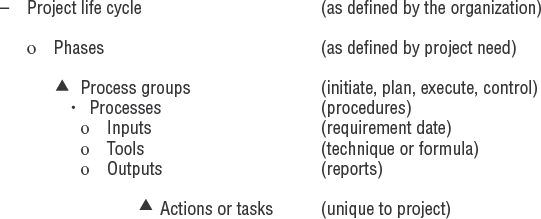
The five process groups as defined by PMI are as follows:
Initiating
Planning
Executing
Monitoring and Controlling
Closing
Each process group has a general function and contains processes that have specific functions to be accomplished. The process groups are interdependent; changes made in one process group can generate cascading change into another group. Each process group performs the functions indicated by its name:
- Initiating
This process group begins the project or a phase of the project. This group contains two processes. One component sets the scope; the second component authorizes the project to begin.
- Planning
This process group contains almost half of the 44 processes. Planning is where the project scope, goals, and objectives are detailed.
- Executing
The largest portion of resources is used during executing activities. The processes within this group are used to create the project deliverables.
- Monitoring and Controlling
This is where you control the project. These 12 processes are used to measure performance and control changes. Examples include review meetings, dealing with substitutions, and schedule changes. You might fire a vendor and hire a replacement.
- Closing
When a phase or the project is completed, this process group will pay vendors and put the files in an archive to close out the project.
PMI defines 44 processes that fit into these 5 process groups. As the project runs, changes will be discovered that create a revision in the planning and execution phases. Figure 1.6 illustrates the relationship of each process group.
Changes in scope or poor results will force the project manager to loop backward to the sponsor from the initiation phase. Sometimes a project exceeds the scope or needs revision before it can continue. Your sponsor may help or decide to cancel it.
The following information is a quick reference describing the knowledge areas and associated processes. You'll learn where each process fits in to a process group, the actions taken in the process, and the main output or result from the process.
Note
For further reference, refer to A Guide to the Project Management Body of Knowledge (current edition).
Project Integration Management is the knowledge area containing processes that tie all of the other processes together. Each process can feed iterative changes into the next process. This is why project management is referred to as an iterative management process. A change in scope or deadlines, for example, will trigger changes throughout the entire plan. As a result, each process would need to be updated to remain synchronized. Therefore, another iteration of the plan is created.
Table 1.4 shows the various processes of the Project Integration Management knowledge area.
Table 1.4. The Project Integration Management Processes
Process | Process Group | Action Taken | Main Output |
|---|---|---|---|
Develop Project Charter | Initiating | Documenting intent of project and obtaining approval | Project charter |
Develop Preliminary Scope Statement | Initiating | Elaborating project definition | Scope statement |
Develop Project Management Plan | Planning | Combining all of the other project outputs into one collection of documents that defines the project | Project management plan |
Direct and Manage Project Execution | Executing | Obtaining work results and identifying changes | Deliverables |
Monitor and Control Project Work | Monitoring and Controlling | Identifying actions required to create work results | Recommended corrective actions, change requests |
Integrated Change Control | Monitoring and Controlling | Updating project definition | Approved change requests |
Close Project | Closing | Obtain final approvals | Project archives |
Project Scope Management contains processes that define the product created by the project and the work to be performed on the project. During this process, a structure is created that breaks each task into itemized details of work to be performed. This is an excellent method for defining your audit plans to get better funding with higher sponsor satisfaction.
Table 1.5 shows the various processes of the Project Scope Management knowledge area.
Table 1.5. The Project Scope Management Processes
Process | Process Group | Action Taken | Main Output |
|---|---|---|---|
Scope Planning | Planning | Documenting intent of project to define the scope | Scope management plan |
Scope Definition | Planning | Elaborating preliminary project scope statement | Scope statement |
Create Work Breakdown Structure (WBS) | Planning | Decomposing the scope statement into a work breakdown structure | Work breakdown structure and dictionary |
Scope Verification | Monitoring and Controlling | Obtaining work results and acceptance of work | Accepted deliverables |
Scope Control | Monitoring and Controlling | Identifying changes to project scope | Project scope updates |
Project Time Management contains processes that define and control the activities required to complete the project as well as resources for the project. In this knowledge area, the project manager defines the baseline schedule for the project. You can use this to organize your audit activities into a high-impact plan.
Table 1.6 shows the various processes of the Project Time Management knowledge area.
Table 1.6. Project Time Management Processes
Process | Process Group | Action Taken | Main Output |
|---|---|---|---|
Activity Definition | Planning | Decomposing WBS to create an activity list | Activity list |
Activity Sequencing | Planning | Identifying interactivity in logical relationships | Network diagrams (PERT or Gantt chart) |
Activity Resource Estimating | Planning | Determining resource requirements for activities | Resource requirements |
Planning | Estimating a time duration for each task | Activity duration estimates | |
Schedule Development | Planning | Calendaring activity durations and sequences | Project schedule |
Schedule Control | Monitoring and Controlling | Identifying schedule changes and variances | Schedule updates |
Project Cost Management comprises three processes that define, specify, and control costs for the project. This knowledge area uses earned value technique to measure cost performance for the project. Earned value (EV) is the current value of work that has been performed in the project.
Table 1.7 shows the various processes of the Project Cost Management knowledge area.
Table 1.7. Project Cost Management Processes
Process | Process Group | Action Taken | Main Output |
|---|---|---|---|
Cost Estimating | Planning | Using task estimates and resource estimates to create a cost estimate | Cost estimate |
Cost Budgeting | Planning | Assigning cost estimates to work packages (from WBS) | Cost baseline |
Cost Control | Monitoring and Controlling | Identifying changes and variances to baseline | Budget updates |
Quality is just as relevant in audit planning as it is in manufacturing. The Project Quality Management knowledge area comprises three processes that define the level of quality applied to the project's product and performance. Project team members audit the performance of their project. Next, the product created by the project is inspected for conformance to the design objectives. Inspection tests determine whether the product created will live up to its intended fitness for use. Any necessary changes are cycled into plan revisions. The entire process repeats until the product is acceptable or the project ends.
Table 1.8 shows the various processes of the Project Quality Management knowledge area.
Table 1.8. Project Quality Management Processes
Process | Process Group | Action Taken | Main Output |
|---|---|---|---|
Quality Planning (plan, design) | Planning | Documenting intent of project and product quality | Quality management plan |
Perform Quality Assurance (do, monitor) | Executing | Performing project audits to determine project quality | Quality improvement |
Perform Quality Control (check, act) | Monitoring and Controlling | Inspecting outputs to ascertain quality | Acceptance or rejection of work results |
We will cover the complete quality model of Plan, Do, Check, Act (PDCA) in Chapter 2, "Audit Process"
Project Human Resource Management facilitates planning the organizational structure, job roles, specific responsibilities, and acquisition of staff for the project. This is the best technique to get the skilled people needed for your project. Use the work breakdown structure (WBS) from scope management planning to build a skills matrix. The skills matrix documents special skills needed to perform each task. This technique can eliminate problems of being assigned an unskilled person who is simply a "warm body" on your team. Unskilled team members create an undesirable drain of valuable project money.
Tip
A comprehensive staff management plan is a key tool for managing resources and controlling project costs and schedules. A skills matrix is required for audit projects.
Table 1.9 shows the various processes of the Project Human Resource Management knowledge area.
Table 1.9. Project Human Resource Management Processes
Project Communications Management defines the communications needs of the project stakeholders, and then facilitates and controls communications distribution during the life of the project. Audit projects need this level of planning to clarify what is discussed or reported to our stakeholders. Consider the different conversational needs to communicate with our auditees, clients, and our own audit team members. A calculation of EV is used to show stakeholders the value of work performed in the project. EV provides a financial measurement of the value created to date.
Table 1.10 shows the various processes of the Project Communications Management knowledge area.
Table 1.10. Project Communications Management Processes
Process | Process Group | Action Taken | Main Output |
|---|---|---|---|
Communications Planning | Planning | Documenting communications needs of project stakeholders | Communications management plan |
Information Distribution | Executing | Sending out info as per plan | Project records |
Performance Reporting | Monitoring and Controlling | Measuring performance using EV | Performance reports |
Manage Stakeholders | Monitoring and Controlling | Resolved issues |
Project Risk Management comprises six processes that define the risk methods to be used, define the risks of the project, analyze the risks, and document responses to identified risks. Through these processes, managing the risk becomes a high priority for the project and remains in the forefront of project activities.
Table 1.11 shows the various processes of the Project Risk Management knowledge area.
Table 1.11. Project Risk Management Processes
Process | Process Groups | Action Taken | Main Output |
|---|---|---|---|
Risk Management Planning | Planning | Documenting intent of project regarding risk management | Risk management plan |
Risk Identification | Planning | Reviewing project to identify risks | Risk register |
Qualitative Risk Analysis | Planning | Analyzing risk impacts and probabilities | Risk register updates |
Quantitative Risk Analysis | Planning | Analyzing risks numerically to predict outcomes | Risk register updates |
Risk Response Planning | Planning | Identifying actions to respond to prioritized risks | Risk register updates |
Risk Monitoring and Control | Monitoring and Controlling | Monitoring for identified risks and symptoms, looking for new risks | Risk register updates |
Risk management is an area of major focus during the audit planning process described in Chapter 2.
Project Procurement Management defines the processes that are required to purchase resources. All projects need to procure people, equipment, and materials from outside the organization. Advance planning in procurement creates an orderly, documented method for contracting with vendors. Special handling procedures need to be honored in the bid process as well as in government-awarded projects. Mishandling will create legal problems.
Table 1.12 shows the various processes of the Project Procurement Management knowledge area.
Table 1.12. Project Procurement Management Processes
Process Groups | Action Taken | Main Output | |
|---|---|---|---|
Plan Purchases and Acquisitions | Planning | Deciding whether to make or purchase. | Procurement management plan |
Plan Contracting | Planning | Determining type of procurement document. Decision 1: Offer fixed price, cost reimbursable, or time and material. Decision 2: Use request for proposal (RFP), request for information (RFI), or invitation to tender (ITT). Controlling communications and visitation with bidders to prevent accusation of bias. | Procurement documents |
Request Seller Responses | Executing | Sending out procurement documents, holding bidders conferences. | Procurement packages |
Select Sellers | Executing | Negotiating a contract. | Signed contract |
Contract Administration | Monitoring and Controlling | Managing sellers work. | Contract documentation |
Contract Closure | Closing | Giving seller formal acceptance. | Closed contract |
Effective project management requires a significant level of communication and integration. Two of the more common diagramming techniques include Gantt charts and PERT network diagrams. All projects have a critical path of tasks. This critical path represents the minimum steps necessary to complete a successful project. This path is the longest route in the diagram and the shortest time estimate for project completion
Gantt charts (see Figure 1.7) are used to schedule and sequence activities in a waterfall-type representation. Planned activities are shown flowing downward to completion. The figure shows both sequential and concurrent activities in a linear bar-chart-style presentation. Milestones will be identified and progress reported against planned activities. Gantt charts are more simplistic than PERT diagrams. In a typical Gantt chart, the bars show tasks, and diamond symbols indicate milestones. The long, dark overhead bars depict a phase or a section of the schedule. Unfortunately, Gantt charts fail to illustrate the relationships between activities and the most important activities (critical path). Only an idiot would try to manage projects by using a Gantt chart without the critical path clearly identified. To be successful, every Gantt chart should have a matching PERT chart in use.
Tip
The better projects are run by a PERT chart. Gantt charting makes it look like all the tasks are going to be accomplished, usually in a serial sequence. In reality, the tasks outside of the PERT's critical path may be eliminated from the project.
Program Evaluation Review Technique (PERT) is used to illustrate the relationship between planned activities (see Figure 1.8). PERT diagramming shows multiple routes through the project activities, as necessary for accomplishing the goal. PERT has two major advantages. First is the ability to demonstrate a critical path. The second advantage is that PERT provides a quantitative measurement tool for risk analysis. It can help measure the risk of delays, failure, and likely completion. The most successful project managers use both Gantt and PERT—Gantt to display resource detail, and PERT to show the current and most up-to-date critical path.
You can use the critical path method for planning your audit. This is an excellent technique to show your sponsor the effects of any changes or delays in your project activities:
Make a list of all your planned activities.
Group the related activities into boxes.
Calculate the duration of each activity by using three estimates (optimistic, most likely, pessimistic).
Pick the most important activity boxes, and then use arrows to construct a sequence diagram.
Adjust your plans to fit the available time. If your plans don't fit, request a change in scope.
Beginners in project management will often use Microsoft Project to build project plans with primitive Gantt charts. Unfortunately, it is almost impossible to persuade sponsors by using Gantt reports because of the report's serial nature and lack of dependency analysis. PERT analysis is the best method to show the effect of dependencies with quantitative measurement. Advanced project managers use software such as that from Primavera Systems, which provides fabulous reporting features not found in MS Project. If you are an MS Project user, your best chance of survival is to use a PERT reporting add-in such as PERT chart Expert from Critical Tools. This nifty tool will automatically create several of the basic PERT reports using your MS Project activity list.
In this chapter, we covered the pervasive foundation of knowledge necessary for you to be a successful IS auditor. Our goal is to provide basic auditor knowledge to help guide your decisions. The secret of a successful auditor is to understand who to believe and their motivation. A successful IS auditor will follow industry-accepted practices while dealing with conflict and change in a manner that generates admiration from their clients. It is your responsibility as an IS auditor to demonstrate effective leadership skills in the pursuit of your work. A good leader will take control of the situation to direct all effort toward fulfilling the desired objective.
In the next chapter, we will discuss the audit process in detail.
- Know the purpose of policies, standards, guidelines, and procedures.
Policies are high-level objectives designated by a person of authority, and compliance to policies is mandatory. Standards ensure a minimum level of uniform compliance to a policy, and compliance to standards is mandatory. Guidelines advise with preferred objectives and useful information in the absence of a standard. Guidelines are often discretionary. Procedures are a cookbook recipe of specific tasks necessary to implement a standard. Compliance to procedures is mandatory.
- Know the ISACA standards governing professional conduct and ethics.
The auditor is expected to perform with the highest level of concern and diligence. Each audit should be conducted in accordance with professional standards and objectivity, and should implement best practices.
- Understand the general purpose of the audit and the role of the IS auditor.
The purpose of auditing is to challenge the assertions of management and to determine whether evidence will support management's claims.
- Understand an audit role versus a nonaudit role.
There are only two roles in an audit. The first role is that of the auditor who performs an objective review, and the second is the role of everyone else. A person cannot be an auditor and also involved in the design or operation of the audit subject.
- Understand the importance of IS auditor independence.
It is unlikely that an auditor could be truly independent if the auditor were involved with the subject of the audit. Auditor independence is an additional assurance of truth.
- Know the difference between discretionary and mandatory language.
In regulatory language, the word shall designates a mandatory requirement. The word shall indicates that there is no excuse for failing to meet the stated objective, even if compliance would cause a financial loss. The word should indicates a recommendation that could be optional, depending on the circumstance.
- Know the different types of audits.
The types of audit are financial, operational (SAS-70), integrated (SAS-94), compliance, administrative, and information systems.
- Understand the importance of IS auditor confidentiality.
The IS auditor shall maintain confidentiality at all times to protect the client. Sensitive information should not be revealed at any time. Your client expects you to protect their secrets whenever legally possible.
- Understand the need to protect audit documentation.
The data must be protected with access controls and regular backup. Sensitive information is the property of the owner, and its confidentiality shall be protected by the auditor. A document archive is created during the audit and is subject to laws governing record retention.
- Know how to use standard terms of reference.
The auditor should communicate by using standardized terms of reference to avoid misunderstanding or confusion. The standard terminology should be defined through a mutual agreement at the beginning of the audit.
- Understand application of the evidence rule.
Audit evidence needs to be confirmed or verified to ensure that it is actually used in the production process.
- Identify who the auditor may need to interview.
The IS auditor needs to consider the roles of data owner, data user, and data custodian when selecting persons to interview. Data owners specify controls, data users are to follow acceptable usage requirements, and custodians protect the information while supporting data users.
- Understand the organizational structure.
Officers of an organization are usually persons with the title of vice president or higher, up to the board of directors. Department directors, managers, and staff workers are seldom liable for the organization, unless criminal activity is involved.
- Understand how to manage projects, including the audit project.
The IS auditor is expected to manage audit projects and be cognizant of project management techniques. The auditor is expected to be competent in evaluating the client's management of projects. Every project contains the three competing values of scope, cost, and time. A project manager in the projectized, or strong matrix, organization has more authority than a project manager in a weak matrix, or functional, organization.
What is the difference between a policy and a procedure?
Compliance to a policy is discretionary, and compliance to a procedure is mandatory.
A procedure provides discretionary advice to aid in decision making. The policy defines specific requirements to ensure compliance.
A policy is a high-level document signed by a person of authority, and compliance is mandatory. A procedure defines the mandatory steps to attain compliance.
A policy is a mid-level document issued to advise the reader of desired actions in the absence of a standard. The procedure describes suggested steps to use.
Which of the following in a business organization will be held liable by the government for failures of internal controls?
President, vice presidents, and other true corporate officers
Board of directors, president, vice presidents, department directors, and managers
All members of management
Board of directors, CEO, CFO, CIO, and department directors
What does fiduciary responsibility mean?
To use information gained for personal interests without breaching confidentiality of the client.
To act for the benefit of another person and place the responsibilities to be fair and honest ahead of your own interest.
To follow the desires of the client and maintain total confidentiality even if illegal acts are discovered. The auditor shall never disclose information from an audit in order to protect the client.
None of the above.
What are the different types of audits?
Forensic, accounting, verification, regulatory
Integrated, operational, compliance, administrative
Financial, SAS-74, compliance, administrative
Information systems, SAS-70, regulatory, procedural
What is the difference between the word should and shall when used in regulations?
Shall represents discretionary requirements, and should provides advice to the reader.
Should indicates mandatory actions, whereas shall provides advisory information recommending actions when appropriate
Should and shall are comparable in meaning. The difference is based on the individual circumstances faced by the audit.
Should indicates actions that are discretionary according to need, whereas shall means the action is mandatory regardless of financial impact.
Highest authority for a project manager is in the ________ organizational structure.
Projectized
Functional
Cross-functional matrix
Business corporation
Which of the following is not defined as a nonaudit role?
System designer
Operational staff member
Auditor
Organizational manager
Why is it necessary to protect audit documentation and work papers?
The evidence gathered in an audit must be disclosed for regulatory compliance.
A paper trail is necessary to prove the auditor is right and the auditee is wrong.
The auditor will have to prove illegal activity in a court of law.
Audit documentation work papers may reveal confidential information that should not be lost or disclosed.
Which of the following is a network diagram that shows the critical path for a project?
Program Evaluation Review Technique
Gantt chart with activity sequencing
Shortest Path Diagramming Technique
Milestone reporting
What is the purpose of standard terms of reference?
To meet the legal requirement of regulatory compliance
To prove who is responsible
To ensure honest and unbiased communication
To ensure that requirements are clearly identified in a regulation
What does the term auditor independence relate to?
It is not an issue for auditors working for a consulting company.
It is required for an external audit.
An internal auditor must undergo certification training to be independent.
The audit committee bestows independence upon the auditor.
Which of the following is true concerning the roles of data owner, data user, and data custodian?
The data user implements controls as necessary.
The data custodian is responsible for specifying acceptable usage.
The data owner specifies controls.
The data custodian specifies security classification.
What is the definition of a work breakdown structure?
A detailed staffing plan
Sequence of steps with milestones in support of the project scope
The levels of authority delegated by the project manager
Decomposition of tasks
What is the definition of a standard as compared to a guideline?
Standards are discretionary controls used with guidelines to aid the reader's decision process.
Standards are mandatory controls designed to support a policy. Following guidelines is discretionary.
Guidelines are recommended controls necessary to support standards, which are discretionary.
Guidelines are intended to designate a policy, whereas standards are used in the absence of a policy.
Who should issue the organizational policies?
Policies should originate from the bottom and move up to the department manager for approval.
The auditor should issue the policies in accordance with standards and authorized by the highest level of management to ensure compliance.
Any level of management.
The policy should be signed and enforced by the highest level of management.
The auditor's final opinion is to be based on:
The objectives and verbal statements made by management
An understanding of management's desired audit results
The audit committee's specifications
The results of evidence and testing
What is the purpose of ISACA's professional ethics statement?
To clearly specify acceptable and unacceptable behavior
To provide procedural advisement to the new IS auditor
To provide instructions on how to deal with irregularities and illegal acts by the client
To provide advice on when it is acceptable for the auditor to deviate from audit standards
How does the auditor derive a final opinion?
From evidence gathered and the auditor's observations
By representations and assurances of management
By testing the compliance of language used in organizational policies
Under advice of the audit committee
What are the three competing demands to be addressed by project management?
Scope, authority, and money
Time, cost, and scope
Requirements, authority, and responsibility
Authority, organizational structure, and scope
What is the difference between a threat and a vulnerability?
Threats are the path that can be exploited by a vulnerability.
Threats are risks and become a vulnerability if they occur.
Vulnerabilities are a path that can be taken by a threat, resulting in a loss.
Vulnerability is a negative event that will cause a loss if it occurs.
Which of the following statements is not true regarding the audit committee?
Executives inside the organization oversee the audit committee and are responsible for keeping the committee busy working on compliance programs.
Executives can be hired and fired by the audit committee because this committee is responsible for management oversight.
The audit committee is composed of members from the board of directors. This committee has the authority to hire external auditors, and external auditors may meet with the committee on a quarterly basis without other executives present.
The audit committee provides senior executives a method of bringing problems into a confidential discussion for the purpose of exploring a resolution.
What is the functional difference between managing a project by using Gantt charts as compared to PERT diagrams?
Gantt charts show the sequence of project activities, and PERT diagrams display a more detailed work breakdown structure. The PERT diagrams provide valuable details necessary to create a skills matrix.
PERT charts put work packages from the work breakdown structure in sequence to show multiple routes through the project, using time estimates of most likely, least likely, and optimistic for quantitative measurement.
PERT diagrams follow a waterfall-type sequence to provide a bar graph diagram of details, milestones, and activities. PERT provides qualitative measurement of the work breakdown structure.
Projects of any size can be effectively managed by using Gantt chart diagrams. PERT diagrams are optional reports.
How should the auditor assist in the remediation of problems found during the audit?
Take ownership of the issue and participate in designing the plan for fixing the problem.
The auditor should decide whether the problem is major or minor, and then advise the auditee with a specific solution after considering the impact to the business.
The auditor should help the auditees. The auditor can add value by defining the specific steps necessary for remediation of the problem.
The auditor should never take ownership of problems found. Auditors are encouraged to provide general advice to the auditee, including an explanation of what to look for during the audit.
The __________ type of audit checks attributes against the design specifications.
Process
System
Compliance
Product
Assessments and audits have several points in common. Which of the following statements provides the best description of an assessment compared to an audit?
Audits are more formal than assessments.
They are similar in nature; the difference is in wording.
Both provide reports that can be used for licensing purposes.
Assessment reports provide a high assurance of the situation.
The audit may uncover irregularities and illegal acts that require disclosure. The auditor is obligated to promptly disclose this information to the authorities.
True
False
Corporations can avoid compliance under the Sarbanes-Oxley Act by using which of the following strategies?
Relocating the corporate headquarters offshore to a country such as Japan.
Remediating their internal controls to fulfill the requirements of SOX section 404.
Auditing their internal controls and reporting the findings to the audit committee at least once every 90 days.
Applicable corporations in the United States and Japan are not able to avoid compliance.
Which of the following statements is true?
The auditee is the person running the audit, and the client is the subject of the audit.
The auditor is the person running the audit, and the client is the subject of the audit.
The client is the person setting the scope for the audit, and the auditor performs the work.
The client pays for the audit, and the auditor sets the scope of the audit that will follow.
What is the purpose of the skills matrix?
Identify which person to interview during the audit
Describe the person needed during the performance phase of the audit
Identify the skills required by the auditee in order to complete the audit within scope
Show the client how to save money during the audit engagement
Which of the following is the best description of an ongoing audit program for regulatory compliance?
An audit is performed once for the entire year, and then repeated by using the same information for each successive year.
An audit may be automated by using audit program software.
An audit is a series of unique projects of short duration that add up to cover all the steps necessary for annual compliance.
An audit is a set of assessments performed by the auditee for the purpose of licensing and regulatory compliance.
C. A policy is signed by the person of highest authority to ensure compliance by the members of the organization. Compliance to policies, standards, and procedures is mandatory.
A. Officers of the organization will typically hold the title of vice president or higher. A CIO might not be a corporate officer, unless the position is located in the parent organization. A division-level CIO may or may not be a true corporate officer. Those holding the position of department director and below are seldom held liable by the government for internal control failure. A department director is a supporting manager to the vice president.
B. Accountants, auditors, and lawyers act on behalf of their client's best interests unless doing so places them in violation of the law. It is the highest standard of duty implied by law for a trustee and guardian.
B. All of the audit types are valid except procedural, SAS-74, verification, and regulatory. The valid audit types are financial, operational (SAS-70), integrated (SAS-94), compliance, administrative, forensic, and information systems. A forensic audit is used to discover information about a possible crime.
D. Should represents discretionary information in a regulation. Shall indicates that compliance is mandatory regardless of profit or loss.
A. The highest level of authority is in the projectized organization, followed in decreasing authority by the balanced matrix, and weak matrix (functional). In functional organization the project manager has almost no authority and relies on begging and personal influence.
C. Every role except an auditor is a nonaudit role. Anyone in a nonaudit role is disqualified from being an independent auditor.
D. The auditor may discover information that could cause some level of damage to the client if disclosed. The information could trigger additional actions by a perpetrator. In addition, the auditor shall implement controls to ensure security and data backup of their work.
A. A Program Evaluation Review Technique (PERT) diagram is designed to show the critical path of a project. A Gantt chart shows activity sequences and milestones without identifying the critical path. Answers C and D are distracters.
C. Standard terms of reference are used between the auditor and everyone else to ensure honest and unbiased communication. Without standard terminology, it would be difficult to know whether we were discussing the same issue or agreed on the same outcome.
B. The auditor must be independent. Having a personal relationship with the organization being audited could result in a biased opinion. The business relationship is also an issue if the organization has influence over the auditor. The goal is to be fair, objective, and unrelated to the subject of the audit.
C. The data owner specifies controls, is responsible for acceptable use, and appoints the data custodian. The data users will comply with acceptable use and report violations. The data custodian will protect information and ensure its availability. The custodian will also provide support to the users.
D. A work breakdown structure is the decomposition of tasks necessary to perform the required work for the project.
B. A standard is implemented to ensure a minimum level of uniform compliance. Guidelines are advisory information used in the absence of a standard. Compliance to standards is mandatory; compliance to guidelines is discretionary.
D. Policies should be signed, issued, and enforced by the highest level of management to ensure compliance by the organization. It is the responsibility of management (not the auditor) to implement internal controls.
D. The auditor is to be a professional skeptic who tests assertions of management and renders an opinion based on the evidence discovered during the audit.
A. This statement specifies that IS auditors are expected to fulfill their duties with the highest standards of honest and truthful representation. It is unacceptable to violate the fiduciary relationship with your client.
A. A final opinion is based on evidence gathered and testing. The purpose of an audit is to challenge the assertions of management. Evidence is gathered that will support or disprove claims.
B. Scope, cost, and time are the three constraints in every project. Scope includes authority, while cost includes resources and personnel. Time affects both cost and scope of the project to be completed as planned.
C. Assets are anything of value. Threats are negative events that cause a loss if they occur. Vulnerabilities are paths that allow a threat to occur.
A. All of the answers except A are true. The audit committee is responsible for management oversight of the executives. The audit committee is usually composed of board members who provide executives a forum to discuss problems in order to rectify the situation. The audit committee can hire or fire anyone in the organization, usually focusing their attention on external auditors and senior executives.
B. A Program Evaluation Review Technique diagram provides a visual representation of the critical path. The critical path is the shortest route through the tasks necessary to accomplish the delivery of the highest-priority objectives in each project. Smart project managers will use Gantt chart data to build a PERT diagram for management of the project.
D. The auditor must never take ownership of the problems found. The auditor may provide general advice to the auditee and demonstrate what we are looking for during the audit. The auditee needs to design their own remediation plan. Auditors who participate in detailed remediation planning are no longer objective nor independent.
D. Product audits compare design specifications (feature, size, color, markings, and so forth) against the attributes of the finished product. The CISA may use this type of audit during certification of custom-built software programs or prior to software release from a development company.
A. An assessment is less formal than an audit. The purpose of an assessment is to determine value based on relevance. Assessments have a lower value because they are not independent or a regimented independent audit.
B. False. The auditor should contact one level of management above where the suspected activity took place. If the problem involved managers responsible for internal controls, the auditor should report it to the highest level of management available, which is usually the audit committee. Auditors should never contact the authorities directly unless advised to do so by their own attorney.
Answer: D. Corporations that fall under the Sarbanes-Oxley Act (SOX) are not able to avoid compliance if they are located in the United States or Japan. SOX is forcing the use of internal controls and now expanding into other countries, including the European Union. Foreign countries are implementing laws such as SOX to deter corporate corruption by holding the executives liable.
C. The client sets the scope of the audit. The auditee is the target (subject) of the audit. The auditor designs the audit plan according to the client's scope and then performs the audit in accordance with published audit standards and procedures.
B. A skills matrix is created during preplanning to identify the skills necessary to perform a competent audit. The purpose of the skills matrix is to justify the training of personnel or to describe the skills needed by members of the audit team. A skills matrix prevents the auditor from being stuck with an unskilled "warm body."
Answer: C. Projects are unique and usually of limited duration, for a fixed period of time with a definite start and stop date. The projects may be coupled together into a series of projects in order to fulfill an ongoing operational need, such as an annual audit program or perpetual quality program.