THE OBJECTIVE OF THIS CHAPTER IS TO ACQUAINT THE READER WITH THE FOLLOWING CONCEPTS:
Developing and implementing a risk-based audit strategy
Understanding how to structure an audit
Implementing the principles of quality into audit activities
Planning required for specific audits
Implementing risk management and control practices while maintaining independence
Understanding qualifications and competence requirements
Conducting audits in accordance with standards, guidelines, and best practices
Knowing the types of controls and how they are implemented
Understanding the effect of pervasive controls on audits
Acquiring and using proper audit evidence
Understanding the new challenge of electronic discovery
Dealing with conflict, potential risks, and communicating to stakeholders
Conducting audit documentation and reports

During an audit, it is important to remember that all decisions and opinions will need to be supported by evidence and documentation. It is the auditor's responsibility to ensure consistency in the audit process. An audit quality control plan should be adopted to support these basic objectives.
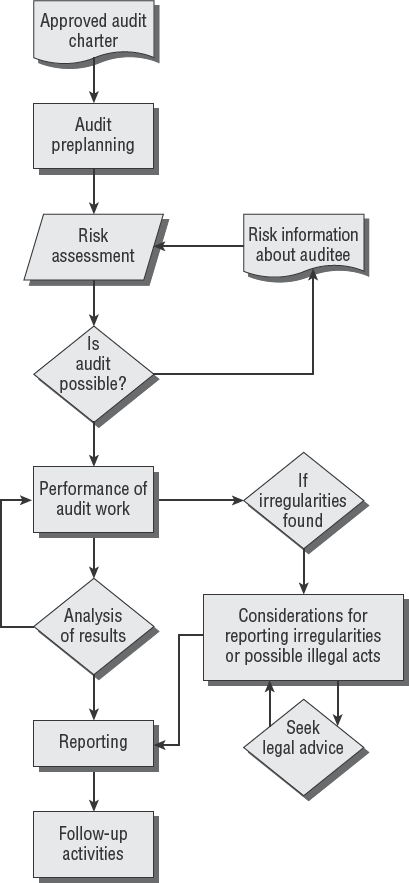
There are 10 audit stages to be aware of when performing an audit. A CISA needs to be aware of their duties in each of these stages:
Approving the audit charter or engagement letter
Preplanning the audit
Performing a risk assessment
Determining whether an audit is possible
Performing the actual audit
Gathering evidence
Performing audit tests
Analyzing the results
Reporting the results
Conducting any follow-up activities
In this chapter, you will look at each of these stages in detail along with various procedures used during the audit. Figure 2.1 illustrates a simple flowchart of the audit process. The actual execution of the audit will be more complex.
We will begin with the process of establishing an audit charter in order to gain the authority to perform an audit.
The first audit objective is to establish an audit charter, which gives you the authority to perform an audit. The audit charter is issued by executive management or the board of directors.
The audit charter should clearly state management's assertion of responsibility, their objectives, and delegation of authority. An audit charter outlines your responsibility, authority, and accountability:
- Responsibility
Provides scope with goals and objectives
- Authority
Grants the right to perform an audit and the right to obtain access relevant to the audit
- Accountability
Defines mutually agreed-upon actions between the audit committee and the auditor, complete with reporting requirements
Each organization should have an audit committee composed of business executives. Each audit committee member is required to be financially literate, with the ability to read and understand financial statements including balance sheets, income statements, and cash flow statements. The audit committee members are expected to have past employment experience in accounting or finance, and hold certification in accounting. A chief executive officer with comparable financial sophistication may be a member of an audit committee.
The purpose of the audit committee is to provide advice to the executive accounting officer concerning internal control strategies, priorities, and assurances. It is unlikely that an executive officer will know every detail about the activities within their organization. In spite of this, executive officers are held accountable for any internal control failures. Audit committees are not a substitute for executives who must govern, control, and manage their organization. The audit committee is delegated the authority to review and challenge the assurances of internal controls made by executive management.
The audit committee is expected to maintain a positive working relationship with management, internal auditors, and independent auditors. The committee manages planned audit activities and the results of both internal and external audits. The committee is authorized to engage outside experts for independent assurance. Both internal auditors and external auditors will have escalation procedures designed to communicate significant weaknesses that have been identified. The auditor will seek to have the weaknesses corrected in order to give a positive assurance that the risk is appropriately controlled and managed. The head of the internal audit and the external audit representative should have free access to the audit committee chairperson. This ensures an opportunity to raise any concerns the auditor may have concerning processes, internal controls, risks, and limitations. This reporting relationship is shown in the following graphic.

The audit committee should meet on a regular basis, at least four times a year, to fulfill this requirement. The Sarbanes-Oxley Act of 2002 (SOX) requires executives to certify that all internal control weaknesses have been discovered, with full disclosure to the audit committee provided every 90 days.
The audit committee is responsible for issuing the audit charter to grant the authority for internal audits. The audit charter should be approved by the highest level of management as well as the audit committee. Authority also needs to be granted for an independent audit. A document called an engagement letter grants authority for an independent external audit.
The audit charter allows the delegation of an audit to an external organization via an engagement letter. The engagement letter helps define the relationship to an independent auditor for individual assignments. The letter records the understanding between the audit committee and the independent auditor.
Note
The primary difference between an engagement letter and an audit charter is that an engagement letter addresses the independence of the auditor.
Engagement letters should include the following:
All points outlined in the audit charter
Independence of the auditor (responsibility)
Evidence of an agreement to the terms and conditions (authority)
Agreed-upon completion dates (accountability)
The second audit objective is to plan the specific audit project necessary to address the audit objectives. Analysis should occur at least annually to incorporate the constant stream of new developments in both the industry and the auditing field.
Your audit objectives will include compliance to professional auditing standards and applicable laws. The IS auditor needs to be prepared to justify any deviation from professional audit standards. Deviation is a rare event.
As an auditor, you will need to consider the impact of the audit on the business operation. You will need to gain an understanding of the business, its purpose, and any potential constraints to the audit. Let's look at the questions an auditor could ask to gain insight of the business operation:
- Knowledge of the business itself
What are their specific industry regulations? For example, are they governed by the U.S. Occupational Safety & Health Administration, any financial securities regulations, or the Health Insurance Portability and Accountability Act because of offering employee medical benefits?
What are the business cycles? The retail industry operates on a schedule that begins Christmas holiday activities in September. Their busy season is at the end of the year, whereas the construction industry is busy from March through August.
What are the reporting cycles? Is their year-end on September 30 or December 31?
What are the critical business processes necessary for survival?
Are reports available from prior audits?
Will the auditors be able to tour the facilities? Which location and when?
Who should be interviewed? Will those people be available?
What are their existing plans? Are any new products, clients, or significant changes planned?
- Strategic objectives
The top executive sets a strategy with supporting definitions for the entire organization. This strategy defines what the business will be doing over the next three to five years. It answers the question of what the business will be engaged in. Is it the same industry or is it branching out into another market?
What is the direction and structure going forward?
What is the organizational plan for integrating IS?
What are the business objectives that IS will be expected to fulfill?
What are the defined IS goals?
What is the strategic plan for the next two to three years?
What are the supporting tactical plan steps during the next one to two years?
What work is occurring from now to the end of the year?
- Financial objectives
Businesses use a portfolio approach to manage their investments, keeping those with the highest return and discarding underperformers. What is the return on investment (ROI) goal for the current capital investment and related expenses?
How are assets managed?
How are costs allocated to departments and projects?
What is the budget and forecasting process?
What are the financial reporting objectives? Will the client need an integrated audit for SOX reporting?
What are the business continuity plans?
- Operational objectives for internal control
Operational activities focus on running the business within a budget period, usually within a 12- to 14-month window. The focus is on what should be done today and this year.
Should any policies or procedures be tested?
Will this be an administrative audit?
How is system administration managed?
How are performance metrics managed?
What is the method used for capacity planning?
What is the strategy and status of business continuity and disaster recovery plans? How many exercise tests have occurred this year?
What controls exist for managing network communications?
What is the nature of the last system audit? Are self-assessments used?
What are the staffing plans?
Figure 2.2 shows four basic areas related to the organization's business requirements.
Every IS auditor will need to provide details when significant restrictions are placed on the scope of an audit. You will need to review your audit objectives and risk strategy to determine whether the audit is still possible and will meet the stated objectives. The audit report should explain specific restrictions and their impact on the audit. If the restrictions preclude the ability to collect sufficient evidence, you should render no opinion or no attestation in the audit.
Examples of restrictions include the following:
Management placing undue restrictions on evidence use or audit procedures that could seriously undermine the audit objective
Inability to obtain sufficient evidence for any reason
Lack of resources or lack of sufficient time
Ineffective audit procedures
Auditors have been known to terminate an engagement if the client places restrictions that are too severe on the audit. It is not unheard of for a client to discharge an auditor after receiving accurate findings that are distasteful to the client. The replacement auditor may need to inquire why a prior auditor is no longer being used by the auditee.
In some instances, the auditee will need to establish a level of communication between the previous auditor and replacement auditor. The purpose of this communication is to ensure that the client is not trying to obstruct truthful findings. Blackouts, or missing audit periods, would be a concern shared by more people than just the auditor. Statement on Auditing Standard 84 (SAS-84) provides additional details if you ever encounter this situation.
Each audit is actually an individual project linked to an ongoing audit program. The IS auditor may be asked to perform a variety of audits, including the following:
- Product or service
Efficiency, effectiveness, controls, and life-cycle costs
- Processes
Methods or results
- System
Design or configuration
- General controls
Preventative, detective, and corrective
- Organizational plans
Present and future objectives
To be successful, the auditor needs to engage in a fact-finding mission. You will need to take into consideration business requirements that are unique to the auditee or common to their industry. Each business has its own opportunities, challenges, and constraints. Remember, the purpose of an audit is to help management verify assertions (claims). Proper planning is necessary to ensure that the audit itself does not disrupt the business, or waste valuable resources, including time and money.
Every audit should have a set of requirements and objectives in support of the ongoing program—for example, the controls and efforts necessary to comply with regulations such as SOX. It is not possible to test all the requirements in one monolithic audit, so we break down (decompile) the larger compliance requirements into a series of smaller audits (modular stages):
- Client duties
Every audit has a client who sets the scope, grants authority, and agrees to pay for the project. The client's duties include the following:
Set the scope
Specify the audit objectives
Grant access to the auditee and resources
Define the reporting structure and confidentiality requirements
- Auditee duties
The auditee is responsible for working with the auditor to do the following:
Confirm purpose and scope
Identify critical success factors (CSFs) and measures of performance
Identify personnel roles and responsibilities
Provide access to information, personnel, locations, and systems relevant to the audit
Cooperate with the gathering of audit evidence
Provide access to prior audit results or to communication with prior auditors if necessary
Specify reporting lines to senior management
Make their assertion of controls and effectiveness independent of the auditor
- Auditor duties
The auditor is responsible for the following:
Plan each audit to accomplish specific objectives necessary for annual compliance.
Identify specific standards used for the audit (such as PCI section 11, NIST 800-53 controls, ISO 27002 management objectives, SOX section 401 or 404, FIPS 142, and so forth).
Use a risk-based audit strategy.
Identify special requirements of confidentiality, security, and safety. The information encountered by the auditor may be sensitive because of competitive value or possible legal repercussions.
Identify specific procedures to be used for the audit. All procedures must be in writing.
Document how the audit procedures are linked with specific audit objectives.
Create a list of the evidence needed to review in order to prepare the audit findings.
Create a written project plan.
Identify resources required, including people, areas for access, hardware, and software.
Develop time and event schedules with estimated start and end times.
Provide audit cost estimates.
Specify a date when the auditee and client can expect to receive a final report.
Scheduling should be mutually agreed upon so there are no surprises. Surprise requests tend to damage the relationship rather than build confidence. Your auditee will wonder whether you are just an incompetent planner or if you have an ulterior motive. Surprises make the auditee leery, if not downright distrustful, of your intentions.
As an auditor, you need to understand the nature of the systems that your client desires to be audited. It would be nearly impossible to audit systems whose mission you do not understand.
During preplanning, it's important to review the capabilities of each member of the audit team. Is each member of the audit team up to the task? The engagement manager or lead auditor should be made aware if a member of the team is missing a certification or a clearance rating necessary to conduct the audit.
In addition, audit plans can change depending on whether the client is using a centralized or distributed system design. The location of IS facilities and personnel will need to be considered.
The auditor needs to demonstrate due care as a professional in both planning and execution. There are a number of definitions for the word care:
Basic care is defined as the bare minimum necessary to sustain life without negligence.
Ordinary care is better than basic and provides an average level of customary care in the absence of negligence.
Extraordinary care is defined as that which is dramatically above and beyond what a normal person would offer or a situation would entail.
Various degrees of care could fall under the definition of due care. The degrees of care are proportional to the level of risk or loss that could occur. Negligence is the absence of care. A conscientious person will exercise due care in the performance of their job. Failure to exercise due care would be negligence.
Every audit is a systematic approach of testing samples of evidence to measure compliance against a designated standard. Anyone with the correct attitude has the potential to be a good auditor after proper training. Let's start with two foundation-level audit objectives:
To test control implementation to see whether the auditee has implemented adequate safeguards
To comply with legal requirements that specify procedures necessary to remain legal
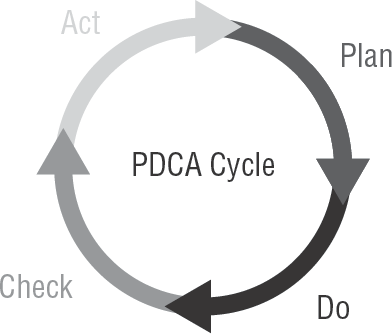
It is not unusual to discover missing controls or the absence of formally documented legal requirements. Auditors may discover that the auditee's understanding of the requirements is quite vague—but no need to fear, because you can be the super auditor with a solution. You can use a special method called the process technique, invented by Walter Shewhart. Shewhart conceived the quality techniques used by Edwards Deming and Philip Crosby.
The purpose of the process technique is to guide a repeating cycle of constant improvement for a process or system. It can be used to identify specific action items necessary to accomplish vague requirements, such as "maintain adequate security." Let's implement the four basic steps used to perform Shewhart's process technique (Plan, Do, Check, Act):
- Plan
Is there a plan or a method?
Did management convey the importance of this objective by sponsoring a policy?
Has the auditee established what needs to be done by identifying specific tasks or procedures?
The auditor may find evidence including outlines, procedures, flowcharts, specifications, or notes.
- Do
Now you look to see whether the plan, procedure, or method is being followed according to their plan. Is the work output matching their plan?
Look for the existence of status reports, meeting records, employee training, or other documentation used in their work area.
- Check
Is anyone monitoring the process? Is there a quality control check or peer review being used? If so, what is the acceptable criterion?
How are problems discovered and reported? Look for compliance testing and evidence of noncompliance, such as rework or discards. What metrics are used? Look for deviation reporting.
- Act
Inevitably, there are differences between what was expected in the plan and the actual outcome. This Act step refers to analyzing the differences, and then taking action to adjust the process so the problem is corrected. Action should always be taken to fix the problems as they are found.
Shewhart's famous graphic is shown next to illustrate the Plan-Do-Check-Act cycle. Using this cycle made Deming famous. It will help you too.
A really smart auditor will focus on situations that are not normal to determine how decisions are made. Auditors should always be curious about how a decision was reached. What evidence is available to justify the decision? Whose approval was required?
A discussion of the audit process would not be complete without mentioning the specific differences between audits and assessments or control self-assessments. The auditee can work to improve their audit score between audits by using assessments and self-assessment techniques.
- Traditional audits
To employ the formal skills of a professional auditor is considered a traditional audit. In a traditional audit, the auditor manages the audit through the entire audit process and renders a final opinion.
Audits are used to specifically measure auditee claims against a reference standard. The audit generates a report viewed to represent a high assurance of truth. Audits are used in attest reporting engagements (when the auditor attests that the auditee claims are true).
The audit results may be used for regulatory licensing and external reporting.
- Assessments
Assessments are less formal and frequently more cooperative processes that scrutinize people and objects. A client may employ a professional auditor to work with the auditee. The goal is usually to "see what is out there." Assessments implement informal activities designed to determine the value of what may already exist. Value is based on relevance and fitness of use. An assessment report is viewed to have a lower value (moderate-to-low value) when compared to an audit. Assessments are excellent vehicles for training and awareness. The goal of an assessment is to help the staff create a sense of ownership while working toward improving their score.
Results of the assessment remain internal to the organization and are not eligible for use in regulatory licensing.
- Control self-assessments (internal)
A control self-assessment (CSA) is executed by the auditee. With a CSA, the auditor becomes a facilitator to help guide the client's effort toward self-improvement. The auditee uses the CSA to benchmark progress with the intention of improving their score. A great deal of pride can be created by the accomplishment of CSA tasks and learning the detail necessary to succeed in a traditional audit. Therefore, the CSA process can generate benefits by empowering the staff to take ownership and accountability.
Control self-assessment will not fulfill the independence requirement, so a traditional audit is still required. CSAs can be used to identify areas that are high risk and may need a more detailed review later.
Tip
Know the difference between audits and assessments. Audits are formal activities that are conducted by a qualified auditor and generate a high assurance of the truth. Audits can be used for licensing and regulatory compliance. Assessments are informal activities designed to determine the value of what may already exist. Value is based on relevance and fitness of use. The assessment is excellent for instilling a sense of ownership in the staff. Assessment results should remain internal to the organization.
As auditors, our goal is to report the truth and to educate our clients. Using traditional audits with a combination of lower-cost assessments will help our client become more successful. Now it's time to move forward into risk management.
After identifying a methodology for risk evaluation and control, the auditor will need to identify potential risks to the organization. The auditee will assist by providing information about their organization.
To properly identify risks, the auditor also needs to identify the following:
Assets that need to be protected
Exposures for those assets
Threats to the assets
Internal and external sources for threats
Security issues that need to be addressed
Part of documenting risk data is for the auditor to identify potential risk response strategies that can be used in the audit with each identified risk. The four risk responses are as follows:
- Accept (de facto)
Take your chances. Ignoring a risk is the same as accepting it. The auditor should be concerned about the acceptance of high-risk situations. By not taking action, the management team has automatically accepted the risk. Not making a decision and taking action means management has already accepted the risk.
- Mitigate (reduce)
Do something to lower the odds of getting hurt. The purpose of mitigation is to reduce the effect of the potential damage. Most internal controls are designed to mitigate risk.
- Transfer
Let someone else take the chance of loss by using a subcontractor or insurance. You can transfer the risk but not the liability for failure. Blind transfer of risk would be a genuine concern. This applies to outsourcing agreements and the reason for a right to audit clause in the contract.
- Avoid
Reject the situation; change the situation to avoid taking the risk.
An assessment of risk will usually include a list of all possible risks that threaten the business and your evaluation of how imminent they are.
Note
Toy manufacturer Mattel experienced the problem of inherited liability for distributing toys manufactured with hazardous lead paint (2007). Mattel was held responsible in the eyes of the public for failing to manage their subcontractor effectively. Unknown to Mattel, their subcontractor chose to ignore specifications in favor of using a lead-based paint. Mattel is under scrutiny for failing to detect the violation prior to shipping their toys. When you transfer risk, you still own the liability. Mattel is only one example of the inherited liability issue.
Note
Other examples of inherited liability include the pet food recall of 2007 caused by tainted flour in the ingredients. The U.S. Food and Drug Administration placed a widespread ban on fish from Chinese suppliers because of questionable practices by the subcontractors using illegal growth hormones. A quick Google search will yield many more examples of liability inherited from subcontractors.
Figure 2.3 shows the basic process of responding to risks. A CISA is expected to understand the different types of responses. Risk management principles will apply to your audit planning. Your client will select from similar choices in their decisions about the risks faced by their organization.
Performing a risk assessment is the next step after the audit objectives have been identified. The purpose of a risk assessment is to ensure that sufficient evidence will be collected during an audit. We will add a new term to your auditor vocabulary: materiality. Materiality refers to evidence that is significant and could change the outcome.
While searching for evidence, it is important to remember that you are not looking for 100 percent of all conceivable evidence. You are interested in material evidence that will be relevant to the outcome of your audit. Please keep in mind that it is easy to be distracted during an audit. You should focus your efforts on material evidence that either proves or disproves your specific audit objective. Your findings and opinion will be based on this material evidence.
An audit risk assessment should take into account the following types of risks:
- Inherent risks
These are natural or built-in risks that always exist. Driving your automobile holds the inherent risk of an automobile accident or a flat tire. Theft is an inherent risk for items of high value.
- Detection risks
These are the risks that an auditor will not be able to detect what they are looking to find. It would be terrible to report no negative results when material conditions (faults) actually exist. Detection risks include sampling and nonsampling risks:
- Sampling risks
These are the risks that an auditor will falsely accept or erroneously reject an audit sample (evidence).
- Nonsampling risks
These are the risks that an auditor will fail to detect a condition because of not applying the appropriate procedure or using procedures inconsistent with the audit objective (detection fault).
- Control risks
These are the risks that an auditor could lose control, errors could be introduced, or errors may not be corrected in a timely manner (if ever).
- Business risks
These are risks that are inherent in the business or industry itself. They may be regulatory, contractual, or financial.
- Technological risks
These are inherent risks of using automated technology. Systems do fail.
- Operational risks
These are the risks that a process or procedure will not perform correctly.
- Residual risks
These are the risks that remain after all mitigation efforts are performed.
- Audit risks
These are the combination of inherent, detection, control, and residual risks.
These are the same risks facing normal business operations. In the planning phase, an IS auditor is primarily concerned with the first three: inherent risk, detection risk, and control risk. All of the risks could place the business or audit in jeopardy and should be considered during some level of advance planning.
An auditor should create plans to allow for alternative audit strategies if an auditee has recently experienced an outage, service interruption, or unscheduled downtime. It would be unwise to pursue an audit before the business has ample time to restabilize normal operations. Plans should include an opportunity to reschedule without violating a legal deadline.
A good auditor remembers that setting priorities is their responsibility. You will need to assess the risk of the audit and ensure that priorities have been fulfilled. If you are unable to perform the necessary audit functions, it is essential that the issues be properly communicated to management and the audit committee. An audit without meaningful evidence would be useless.
The auditor will need to work with the auditee to define specific requirements and identify any third-party providers. You will need to review the auditee's organizational structure and to identify persons in areas of interest that are material to your audit.
Management has the ultimate responsibility for internal controls and holds the authority for delegation. Management may choose to delegate tasks to a third party (outsource). The outsource organization must perform the daily tasks as designated, but unfortunately management will still retain liability that cannot be delegated. Executive management will still be held responsible for any failures that occur with or at the outsource organization. The federal government has gone to great lengths to ensure that the decision maker (management) can be held fully accountable for their actions and liable for any loss or damage.
Organizations with outsourcing contracts and labor unions could be particularly difficult unless you have sufficient cooperation. In the case of labor unions, it is often necessary for the shop steward to be present and involved in all plans and activities. Failure to do so may result in an operational risk of the union workers walking off the job.
Outsourced activities will present their own challenges with potential restrictions on access to personnel and evidence. It would not be uncommon for a service provider to decline your request for an audit. Most outsource providers will attempt to answer such requests by supplying you with a copy of their latest SAS-70 report, which is a standard report format for service providers. Occasionally, when a client requests and receives the SAS-70 report from a service provider, the value of content in the SAS-70 report may be overstated.
The purpose of the SAS-70 is to eliminate multiple organizations from individually auditing the service provider. You can expect that several points of detailed evidence you requested will have been filtered or masked in the SAS-70 report. Your client's original outsource contract should have included a provision for the right to audit along with the service-level agreement. It must be clearly stated whether the SAS-70 is acceptable or if an individual audit is required. Performing your own audit adds cost but offers high levels of control. Be advised that some outsource providers run on a different business schedule than their clients.
The next objective in the audit is to perform the actual audit. Here you will need to make sure you have the appropriate staff, ensure audit quality control, define auditee communications, perform proper data collection, and review existing controls.
You will need to have personnel for the audit and to define the audit's organizational structure. You also will need to create a personnel resource plan, which identifies specific functions and skill sets necessary to complete your audit objectives. Individual skills and knowledge should be taken into consideration while planning your audit. Remember, it's impossible for the auditor to be an absolute expert in everything.
You will need to rely on the work of others, including your own audit team members, subcontractors, and possibly members of the client's staff. You should create a detailed staff training plan that is reviewed at least semiannually and before each audit. The time to train or retrain personnel is before the audit begins.
The auditor will lead persons with specialized skills, including the use of database scanners and other automated audit tools. A skills matrix should be developed, which indicates areas of knowledge, proficiency, and specialized training required to fulfill the audit. You use the skills matrix to identify members of the audit team according to the specific tasks each will perform. The purpose of the skills matrix is to ensure that the team has the right people with the right qualifications working on the right task. You use the matrix to demonstrate gaps and training needs. This discourages management from assigning you an unskilled "warm body." Table 2.1 shows a sample skills matrix.
Table 2.1. Sample Skills Matrix
Person | Training or Certification | Related Work Experience | Audit Task |
|---|---|---|---|
M. Anderson | IA, CISA | Internal auditor | Audit task 8: Review of existing policies and records for PCI user training, all security, system configuration, and incident response. |
CISA, Network+, CCNA | PCI and PCI section 11 testing | Audit task 9: PCI section 11 network perimeter analysis. | |
R. Martin | CISA | XP admin, BSD Unix admin | Audit task 10: Conduct enumeration scan of network hosts and open ports. Exclude "Zeus" server and customer service computers. |
Audit task 14: Select logs for review. Supervise and assist in review with B. Goldfield performing task. | |||
B. Goldfield | BS Computer Science | Intern, system analyst | Audit task 14: Catalog system log file data for analysis of past events to forensic-test the incident response. |
Occasionally, finding a competent, independent expert in database administration for a particular vendor on your project may prove difficult. However, you might be able to train a member of the client's support staff to provide sufficient assistance to complete the audit.
Auditors frequently use the work of others as long as the following conditions are met:
Assess the independence and objectivity of the provider.
Determine their professional competence, qualifications, and experience.
Agree on the scope of work and approach used.
Determine the level of review and supervision required.
If these conditions are met, the auditor may choose to use the work of others. A CISA should have serious concerns if the work does not meet their audit evidence requirement for any reason. You can use only evidence of sufficient quality, quantity, and relevance. Failure to meet this requirement may require a change in the audit scope or canceling the audit.
Tip
Competence means having the right training, related experience, discipline, and qualifications for the job. Qualifications include recognized certification with the proper clearance for the job. Clearance may include having both permission to work the audit and a valid security clearance, especially in government auditing.
Quality does not happen automatically. It is a methodology that must be designed into your process and not just inspected afterward. Quality control is necessary in every audit.
Let's take a moment to define what quality is and how to recognize quality. We can do this by using three easy-to-remember points:
Quality is defined as conformance to specifications.
Planning and prevention create quality. Quality does not occur by post appraisal.
The standard of performance is zero defects, not by just getting "close enough." Sixth and seventh sigma do not reach zero defects. Quality can be measured by the price of failure (nonconformance).
Audit standards, guidelines, and procedures were developed to promote quality and consistency in a typical audit. The ISACA audit standards were developed to assist CISA auditors in performing audits. Additional guidance can be obtained by reading the ISACA audit guide at www.isaca.org/standards.
Your audit will need a variety of quality performance metrics to ensure success. When designing a quality control process, an auditor should consider doing the following:
Use an audit methodology (documented plan and procedures).
Gain an understanding of the auditee needs and expectations.
Keep a checklist of the tasks to be accomplished.
Respect business cycles and deadlines.
Hold client interviews and workshops.
Use customer satisfaction surveys.
Agree to terms of reference used by client, auditee, and auditor (discussed in Chapter 1, "Secrets of a Successful IS Auditor").
Establish audit performance metrics.
Measure audit plan to actual performance.
Respond to auditee complaints.
Quality can vary according to the requirements set forth by management. The auditor must take all the necessary steps to ensure that audit work is performed with very high standards of quality to generate a high assurance of the truth. Anything less will make you and the images of our profession appear questionable. High standards always bring respect.
The auditor must work with management to define the auditee communication requirements.
As discussed in Chapter 1, the auditee often feels at a disadvantage to the auditor. Without effective communication, the auditee will feel disillusioned, confused, or disconnected from the audit. Each of these conditions would be undesirable; audits without client buy-in would be a major disaster.
Tip
Occasionally, the auditee may request to see information concerning the audit plan. Depending on your assignment, it may be acceptable to allow the auditee to view your blank checklists; however, the auditor's notes should remain confidential during the audit. It is usually not a good idea to give the auditee copies of your blank forms because doing so could provide the foundation for disputes or engineered answers.
It is your job as the auditor to be a "second set of eyes" in reviewing the present condition at the organization. You are responsible for reporting accurate findings to senior management and the audit committee. The audit charter should assist you by defining the required level of auditee communication.
To be effective in your communication, you need to consider several points, including the following:
Describing the audit's purpose, service, and scope
Dealing with problems, constraints, and delays
Responding to client questions and complaints
Dealing with issues outside the scope of this particular audit
Understanding timing and scheduling—knowing when they expect the work to occur
Following the reporting process—knowing when and how the client wants to hear from you
Obtaining an agreement of your findings with your client
Implementing confidentiality, implementing the principle of least privilege (need to know)
Providing special handling for evidence of irregularities or possibly illegal acts
Nothing will replace the simple act of asking the client what level and frequency of communication they expect. The preceding points are simply a starting position. You should synchronize the auditee communication plan with your own internal audit team communication plans.
During the planning process, the auditor will need to gain approval from management for access to the appropriate staff personnel. A member of the audit team may be assigned to coordinate everyone's schedule.
Now is a good time to introduce some of the data collection techniques that auditors use in audits.
As part of the planning process, the auditor needs to determine how data will be gathered for evidence to support the audit report. To collect useful data, the savvy auditor will use a combination of techniques, including the following:
- Staff observation
You can observe staff in the performance of their duties. Auditor observation is a powerful form of evidence.
- Document review
Remember, the evidence rule will apply as you review existing documentation. Presence of a document does not mean it is actually in use. You should review the auditee documentation and any related legal documentation. Legal documentation may be either contracts or regulatory laws.
- Interviews
You can interview selected personnel appropriate to the audit. Be sure to structure the timing and questions for the interview. You need to ensure that the questions are consistent and to allow extra time to discuss any interesting points raised.
- Workshops
Workshops can generate awareness and understanding. The audit committee may be a good audience for a workshop. Well-executed workshops can save time compared to individual interviews.
- Computer assisted audit tools (CAAT)
Newer auditing software does a fabulous job of checking configuration settings, user account parameters, system logs, and other time-consuming details.
- Surveys
Conducting surveys is a tried-and-true method of obtaining cheap and easy answers. Unfortunately, the truthfulness of individual responses raises questions about the survey's consistency and resulting trustworthiness. People may answer the question using a skewed perspective, or just respond with answers they believe you want to hear, regardless of the truth. Overall reliability of the survey remains an ongoing concern.
Each technique has its advantages and disadvantages. For example, surveys offer an advantage of time but have the disadvantages of inconsistency and limited response. A survey cannot detect a personal mannerism such as hesitancy, surprise, or restlessness.
An auditor can observe an auditee during an interview and ask additional probing questions based on the auditee response. The auditor weighs each response in an attempt to create consistent scoring of answers by multiple interview subjects. Interviews consume more time but can gather additional information.
Surveys may execute quickly but carry extra administrative support burdens. It will take time and resources to create the survey, distribute the survey, track responses, provide answer assistance, ensure quality control, and tally the results. Because of human nature, people will seldom answer a survey in a manner that reduces their agenda and perceived value to an organization.
Tip
Most clients will be impressed if you demonstrate genuine interest and take good notes. It will help you obtain auditee buy-in and make them feel the audit report will contain statements of value. Just be sure to avoid the perception of an interrogation.
Every auditor should consider two fundamental issues concerning internal control:
- Issue 1: Management is often exempt from controls. "Ye who make the rules might try to avoid those rules."
Management has the responsibility of installing controls for the organization, yet some of the executives themselves are exempt from their own control. An excellent set of examples is noted at the beginning of Chapter 1, where multiple executives fraudulently altered records. One of the fundamental purposes of an audit is to determine whether executives are providing an honest and truthful representation based in fact.
- Issue 2: How controls are implemented determines the level of assurance.
Implementing strong controls contributes to the level of assurance, which may be confirmed by the auditor. Strong assurance means it represents a 95 percent or greater degree of truth. Unsatisfactory implementation of controls compromises the overall objectives. No auditor can provide a satisfactory report if the controls are improperly implemented or insufficient for their objective.
Let's review the basic framework of controls according to the ISACA standards. ISACA based their standards on the common auditing guidelines for financial audits as well as the government guidelines for auditing and for the computer environment. Information systems controls are composed of four high level controls: general controls, pervasive IS controls, detailed IS controls, and application controls. This clarification is required because portions of the financial audit techniques may not be appropriate for some IS audits. Computer environments can be rather complex and abstract.
- General controls (Overall)
This is the parent class of controls governing all areas of the business. Examples of general controls include separating duties to prevent employees from writing their own paychecks and creating accurate job descriptions. We expect management to implement administrative controls to govern the behavior of their entire enterprise. General controls also include defining an organizational structure, establishing HR policies, monitoring workers and the work environment, as well as budgeting, auditing, and reporting.
- Pervasive IS controls (Technology)
A pervasive order or pervasive control defines the direction and behavior required for technology to function properly. The concept of pervasive control is to permeate the area by using a greater depth of control integration over a wide area of influence. Internal controls are used to regulate how the business operates in every area of every department.
The IS function uses pervasive controls in the same manner as a manufacturing operation, bank, or government office. Pervasive controls are a subset of general controls with extra definition focused on managing and monitoring a specific technology. For example, pervasive IS controls govern the operation of the information systems duties.
Pervasive IS controls are used across all internal departments and external contractors. Proper implementation of pervasive IS controls improve the reliability of the following:
Overall service delivery
Software development
System implementation
Security administration
Disaster recovery and business continuity planning
The lack of pervasive IS controls, or weak controls, indicates the possibility of a high-risk situation that should draw the auditor's attention. Lower-level detailed controls will be compromised if the pervasive controls are ineffective.
At the pervasive control level, the auditor needs to consider the experience level, knowledge, and integrity of IS management. Look for changes in the environment or pressure that may lead to concealing or misstating information. This problem is prevalent when users manage their own departmental systems separate from the IT department. External influences include outsourcing, joint ventures, and direct relationships. Internal influences include flaws in the organizational structure or reporting relationship where a built-in conflict may exist.
- Detailed IS controls (Tasks)
Specific tasks require additional detailed controls to ensure that workers perform the job correctly. Detailed controls refer to specific steps or tasks to be performed. In the finance department, a specific set of controls is practiced when creating a trial balance report. Detailed IS controls work in the same manner to specify how system security parameters are set, how input data is verified before being accepted into an application, or how to lock a user account after unsuccessful logon attempts. Detailed IS controls specify how the department will handle acquisitions, security, implementation, delivery, and support of IS services.
An auditor investigating the IS controls should consider findings from previous audits in the subject area. Give consideration to the amount of manual intervention required, the activities outside the daily routine, and the susceptibility of bypassing the IS controls. A smart auditor will always consider the experience, skills, and integrity of the staff involved in applying the controls.
- Application controls (Embedded in programs)
This is the lowest subset in the control family. All activity should have filtered through the general controls, then the pervasive controls and detailed controls, before it reaches the application controls level. The higher-level controls help protect the integrity of the application and its data. Leaving an application exposed without the higher-level controls makes as much sense as leaving a child naked in the woods to fend for itself. Just like children, the application needs to be sheltered and protected from harm.
Management is responsible for having applications tested prior to production through a recognized test method. The goal is to provide a technical certification that each system meets the requirements. Management has to sign a formal accreditation statement granting their approval for the system to enter production based on fitness of use and accepting all responsibilities of ownership. Accreditation makes management accountable for system performance and liability of failure (who to blame or who to reward).
The next step in the planning process is to review the existing internal controls that are intended to prevent, detect, or correct problems. Management is responsible for designating and implementing internal controls to protect their assets. You can obtain initial information about existing controls by reviewing current policies and procedures, and later by interviewing managers and key personnel. The purpose of internal controls can be classified into one of three categories:
- Preventative
Controls that seek to stop (prevent) the problem from occurring. A simple example is prescreening job applicants for employment eligibility. Synonyms for preventive controls include words such as proactive or deterrent activities designed to discourage or stop a problem.
- Detective
Controls that are intended to find a problem and bring it to your attention. Auditing is a detective control for discovering information.
- Corrective
Controls that seek to repair the problem after detection. Restoring data from a backup tape after a disk drive failure is a corrective control. Reactive control is a synonym of corrective control.
Controls from the three mid-level categories are implemented by using one of the following three methods:
- Administrative
Using written policies and procedures (people based)
- Technical
Involving a software or hardware process to calculate a result (special technology)
- Physical
Implementing physical barriers or visual deterrents (building design)
The auditor should be concerned with the attitude and understanding demonstrated by the auditee. An excellent exercise is to ask the auditee to which category their control would best apply. You may hear some unique and often incorrect responses. The process of reviewing the controls to prevent, detect, or correct is an excellent awareness generator with your auditee.
Table 2.2 lists some examples of these control types.
Table 2.2. Controls and Methods of Implementation
Control Type | Implementation Method | Some Examples |
|---|---|---|
Preventative "stops" | Administrative | Hiring procedures, background checks, segregation of duties, training, change control process, acceptable use policy (AUP), organizational charts, job descriptions, written procedures, business contracts, laws and regulations, risk management, project management, service-level agreements (SLAs), system documentation |
Technical | Data backups, virus scanners, designated redundant high-availability system ready for failover (HA standby), encryption, access control lists (ACLs), system certification process | |
Physical | Access control, locked doors, fences, property tags, security guards, live monitoring of CCTV, human-readable labels, warning signs | |
Detective "finds" | Administrative | Auditing, system logs, mandatory vacation periods, exception reporting, run-to-run totals, check numbers, control self-assessment (CSA), risk assessment, oral testimony |
Technical | Intrusion detection system (IDS), high-availability systems detecting or signaling system failover condition (HA failure detection), automated log readers (CAAT), checksum, verification of digital signatures, biometrics for identification (many search), CCTV used for logging, network scanners, computer forensics, diagnostic utilities | |
Physical | Broken glass, physical inventory count, alarm system (burglar, smoke, water, temperature, fire), tamper seals, fingerprints, receipts and invoices | |
Corrective "fixes" | Administrative | Termination procedures (friendly/unfriendly), business continuity and disaster recovery plans, outsourcing, in sourcing, implementing recommendations of prior audit, lessons learned, property and casualty insurance |
Technical | Data restoration from backup, high-availability system failover to redundant system (HA failover occurs), redundant network routing, file repair utilities | |
Physical | Hot-warm-cold sites for disaster recovery, fire-control sprinklers, heating and AC, humidity control |
When you exercise this awareness game of preventative, detective, and corrective controls, it is interesting to notice how technology-oriented people will provide an overt emphasis on technology, while nontechnology-oriented people will focus on administrative and physical controls. If your background is technology, you will need to consider administrative or physical solutions to approach a reasonable balance of controls. Nontechnology-oriented people will need to force their emphasis to include technical controls and achieve a similar level of balance.
The secret to achieving strong controls is to implement layers. The minimum for an effective control is to have at least one point in each of the three areas: preventative, detective, and corrective. For example, a policy without a detective mechanism or a corrective mechanism is not enforceable. The strongest controls implement all nine layers (Preventative, Detective, Corrective implemented using administrative methods, physical methods and technical methods).
The preventative control, for example, would include an administrative policy with technical protection and physical signs or barriers. A corresponding detective control would be implemented with authorization to audit proper job descriptions and procedures. The detective control would include technical methods, such as intrusion, and detection and physical indicators, such as a video recording of people's activity in secure areas. The control would be coupled with corrective actions—such as manual procedures for isolation, and technical recovery using data restored from backup tapes or physical replacement. This is referred to as depth of controls.
Strong control = multiple preventive controls + multiple detective controls + multiple corrective controls
Weak control = shallow bare minimum control + implementation or no implementation
Now that we have covered the basic preventative, detective, and corrective controls, it is time to move on to the impact of pervasive controls.
Every good auditor understands the necessity of collecting tangible and reliable evidence. You read an introduction to the evidence rule in Chapter 1. Although you may really like or admire the people who are the subject of the audit, your final auditor's report must be based on credible factual evidence that will support your statements.
Consider for a moment something not related to IS auditing: police investigations or famous television courtroom dramas. Every good detective story is based on careful observation and common sense. A successful detective searches for clues in multiple places. Witnesses are interviewed to collect their versions of the story. Homes and offices are tirelessly searched for the minutest shred of relevant evidence. Detectives constantly ask whether the suspected individual had the motive, opportunity, and means to carry out the crime. The trail of clues is sorted in an attempt to determine which clues represent the greatest value and best tell the story. Material clues are the most sought after. From time to time, the clues are reviewed, and the witnesses reinterviewed. The detective orders a stakeout to monitor suspects. Ultimately, the suspects and clues of evidence are brought together in one place for the purpose of a reenactment. Under a watchful eye, the materially relevant portions of the crime are re-created in an attempt to unmask the perpetrator. In the movies, the detective is fabulously successful, and the criminal is brought to justice.
Unfortunately, IS auditing is not so dramatic or thrilling to watch. A CISA candidate needs to possess a thorough understanding of evidence, because IS auditing is centered on properly collecting and reviewing evidence. Let's start with a short discussion on the characteristics of good evidence.
Evidence will either prove or disprove a point. The absence of evidence is the absence of proof. In spite of your best efforts, if you're unable to prove those points, you would receive zero credit for your efforts. An auditor should not give any credit to claims or positive assertions that cannot be documented by evidence. No evidence, no proof equals no credit.
Tip
All auditees start the audit with zero points and have to build up to their final score.
There are two primary types of evidence, according to legal definition:
- Direct evidence
This proves existence of a fact without inference or presumption. Inference is when you draw a logical and reasonable proposition from another that is supposed to be true. Direct evidence includes the unaltered testimony of an eyewitness and written documents.
- Indirect evidence
Indirect evidence uses a hypothesis without direct evidence to make a claim that consists of both inference and presumption. Indirect evidence is based on a chain of circumstances leading to a claim, with the intent to prove the existence or nonexistence of certain facts. Indirect evidence is also known as circumstantial evidence.
An auditor should always strive to obtain the best possible evidence during an audit. Using direct evidence is preferable whenever it can be obtained. Indirect evidence represents a much lower value because of its subjective nature. An auditor may find it difficult to justify using indirect evidence unless the audit objective is to gather data after detecting an illegal activity. An audit without direct evidence is typically unacceptable.
You will attempt to gather audit evidence by using similar techniques as a detective. Some of the data you gather will be of high value, and other data may be of low value. You will need to continually assess the quality and quantity of evidence. You may discover evidence through your own observations, by reviewing internal documentation, by using computer assisted audit tools (CAAT), or by reviewing correspondence and minutes of meetings.
Examples of the various types of audit evidence include the following:
Documentary evidence, which can include a business record of transactions, receipts, invoices, and logs
Data extraction, which mines details from data files using automated tools
Auditee claims, which are representations made in oral or written statements
Analysis of plans, policies, procedures, and flowcharts
Results of compliance and substantive audit tests
Auditor's observations of auditee work or reperformance of the selected process
All evidence should be reviewed to determine its reliability and relevance. The best evidence will be objective and independent of the provider. The quality of evidence you collect will have a direct effect on the points you wish to prove.
Computer assisted audit tools (CAAT) are invaluable for compiling evidence during IS audits. The auditor will find several advantages of using CAAT in the analytical audit procedure. These tools are capable of executing a variety of automated compliance tests and substantive tests that would be nearly impossible to perform manually.
These specialized tools may include multifunction audit utilities, which can analyze logs, perform vulnerability tests, or verify specific implementation of compliance in a system configuration compared to intended controls.
CAAT includes the following types of software tools and techniques:
Host evaluation tools to read the system configuration settings and evaluate the host for known vulnerabilities
Network traffic and protocol analysis using a sniffer
Mapping and tracing tools that use a tracer-bullet approach to follow processes through a software application using test data
Testing the configuration of specific application software such as a SQL database
Software license counting across the network
Testing for password compliance on user login accounts
Many CAATs have a built-in report writer that can generate more than one type of predefined report of findings on your behalf.
Numerous advantages may exist, but they come at a cost. These expert systems may be expensive to acquire. Specialized training is often required to obtain the skills to operate these tools effectively. A significant amount of time may be required to become a competent CAAT operator.
Some of the concerns for or against using CAAT include the following:
Auditor's level of computer knowledge and experience
Level of risk and complexity of the audit environment
Cost and time constraints
Specialized training requirements
Speed, efficiency, and accuracy over manual operations
Need for continuous online auditing
Security of the data extracted by CAAT
Warning
A CISA may encounter individuals who are self-proclaimed auditors based solely on their ability to use CAAT software. You should consider this when using the work of others. The ability to use CAAT alone does not represent the discipline and detailed audit training of a professional auditor.
The new audit tools offer the advantage of providing continuous online auditing. You should be aware of the six types of continuous online auditing techniques:
- Online event monitors
Online event monitors include automated tools designed to read and correlate system logs or transaction logs on behalf of the auditor. This type of event monitoring tool will usually generate automated reports with alarms for particular events. A few examples include software that reads event logs, intrusion detection systems, virus scanners, and software that detects configuration changes, such as the commercial product Tripwire. (Low complexity.)
- Embedded program audit hooks
A software developer can write embedded application hooks into their program to generate red-flag alerts to an auditor, hopefully before the problem gets out of hand. This method will flag selected transactions to be examined. (Low complexity.)
- Continuous and intermittent simulation (CIS) audit
In continuous and intermittent simulation, the application software always tests for transactions that meet a certain criteria. When the criteria is met, the software runs an audit of the transaction (intermittent test). Then the computer waits until the next transaction meeting the criteria occurs. This provides for a continuous audit as selected transactions occur. (Medium complexity.)
- Snapshot audit
This technique uses a series of sequential data captures that are referred to as snapshots. The snapshots are taken in a logical sequence that a transaction will follow. The snapshots produce an audit trail, which is reviewed by the auditor. (Medium complexity.)
- Embedded audit module (EAM)
This integrated audit testing module allows the auditor to create a set of dummy transactions that will be processed along with live, genuine transactions. The auditor then compares the output data against their own calculations. This allows substantive integrity testing without disrupting the normal processing schedule. EAM is also known as integrated test facility. (High complexity.)
- System control audit review file with embedded audit modules (SCARF/EAM)
The theory is straightforward. A system-level audit program is installed on the system to selectively monitor the embedded audit modules inside the application software. Few systems of this nature are in use. The idea is popular with auditors; however, a programmer must write the modules. (High complexity.)
Table 2.3 summarizes the differences between these CAAT methods.
Table 2.3. Summary of CAAT Methods
CAAT Method | Characteristics | Complexity |
|---|---|---|
Online event monitors | Reads logs and alarms. | Low |
Flags selected transactions to be examined. | Low | |
Continuous and intermittent simulation (CIS) | Audits any transaction that meets preselected criteria, waits for the next transaction meeting audit criteria. | Medium |
Snapshot | Assembles a sequence of data captures into an audit trail. | Medium |
Embedded audit module (EAM) | Processes dummy transactions along with genuine, live transactions. | High |
System control audit review file with embedded audit modules (SCARF/EAM) | System-level audit program used to monitor multiple EAMs inside the application software. This is a mainframe class of control. | High |
CAAT simplifies the life of an auditor by automatically performing the more menial, repetitive, detail tasks. The auditor needs to consider the CAAT reports while tempering them with some basic commonsense observations.
New developments are occurring in legal procedures for courts. The increased use of computers has led to widespread reliance on electronic data records. In the old days, evidence could be discovered by rummaging through printed mail, business records, file cabinets, and the dusty storage warehouse. Electronic record keeping is a wonderful tool for automation, yet it can also perpetuate fraud, intentional omissions, or misrepresentation. Electronic discovery is the investigation of electronic records for evidence to be used in the courtroom.
The new legal standard for electronic discovery is referred to as e-discovery. These rules were created to aid auditors and investigators by requiring owners of electronic records to disclose their existence and to provide the data in a simple easy-to-read format (unencoded). Under e-discovery rules, the party who owns or possesses the data is required to perform the conversion and to certify that the contents are truthful and complete in their representation of the content. Put simply, the data owner is no longer permitted to use unintelligible or secret codes to keep database contents a secret from investigators.
State and federal courts are still debating the final rules for e-discovery. The law recognizes two parties: the producing party, which provides the evidence, and the receiving party, which receives the evidence. Here's what the auditor can expect until a final ruling is ratified:
Discovery starts with a conference between the parties to plan the discovery process. Any issues related to disclosure of electronically stored information should be identified.
The conference sets the scope to identify possible sources of information. The judge may be asked to include the decisions of the meeting in a court order.
Limitations on scope may be identified based on undue cost or undue burden of production. Limitations will be determined by the judge after considering assertions of both parties and the nature of the case. Discovery may be ordered if the requesting party shows good cause in support of a claim or defense.
The scope may include data available online on any system.
The scope may include recovering deleted data.
The scope may include searching standing data from backup media and other offline sources.
The scope may include discovery of email and email records.
A search protocol will be agreed upon by the parties or ordered by the judge.
Unless the parties agree otherwise, the format shall be PDF or TIFF images without alteration of format or removal of revision history.
The judge may order the costs to be allocated equally, or unequally if good cause is shown why the other party should bear the cost.
Sometimes portions of data, such as formulas and lawful business secrets, are protected by a claim of privilege. If privileged information is produced in discovery, it may be recalled for return, sequester, or destruction after notification is given to the receiving party with an explanation of the basis for privilege. The information may not be disclosed after notice is given, and the producing party must preserve the information until the claim is resolved.
Under rule 37, the court may not impose sanctions on a party for failure to provide electronically stored information that was lost as a result of routine good-faith operations, if the records preservation was not mandated by regulation or exceptional circumstances.
E-discovery applies to criminal cases and civil lawsuits. The courts have determined that using encryption to hide or to cover illegal activities will result in multiple criminal penalties. Failure to cooperate with e-discovery requests can result in fines or prosecution. E-discovery requests include access to audit company records, HR files, database files, financial systems, and email correspondence.
Note
The management of every organization, as well as auditors, need to learn more about the impact of e-discovery on their business activities. Awareness can prevent future legal headaches.
All evidence is graded according to four criteria. This grading aids the auditor in assessing the evidence value. It is important to obtain the best possible evidence. The four characteristics are as follows:
- Material relevance
Evidence with material relevance influences the decision because of a logical relationship with the issues. Materially relevant evidence indicates a fact that will help determine that a particular action was more or less probable. The purpose of material evidence is to ascertain whether the same conclusion would have been reached without considering that item of evidence. Evidence is irrelevant if it is not related to the issue and has no logical tendency to prove the issue under investigation.
- Evidence objectivity
Evidence objectivity refers to its ability to be accepted and understood with very little judgment required. The more judgment required, the less objective the evidence. As you increase the amount of judgment necessary to support your claims, the evidence quickly becomes subjective or circumstantial, which is the opposite of objective. Objective evidence is in a state of unbiased reality during examination, without influence by another source. Objective evidence can be obtained through qualitative/quantitative measurement, and from records or statements of fact pertaining to the subject of the investigation. Objective evidence can be verified by observation, measurement, or testing.
- Competency of the evidence provider
Evidence supplied by a person with direct involvement is preferred. The source of their knowledge will affect the evidence value and accuracy. A secondhand story still holds value by providing information that may lead to the evidence the auditor is seeking.
An expert is legally defined as a person who possesses special skill or knowledge in a science or profession because of special study or experience with the subject. An expert possesses a particular skill in forming accurate opinions about a subject; in contrast, a common person would be incapable of deducing an accurate conclusion about the same subject.
- Evidence independence
Evidence independence is similar to auditor independence, meaning the provider should not have any gain or loss by providing the evidence. Evidence supplied by a person with a bias is often questionable. The auditor should ask whether the evidence provider is part of the auditee's organization. Qualifications of the evidence provider should always be considered. A person with a high degree of detailed understanding is vastly more qualified than an individual of limited knowledge. Evidence and data gathered from a novice may have a low value when compared to data gathered by an expert. A person who is knowledgeable and independent of the audit subject would be considered the best source of evidence.
Table 2.4 lists examples of evidence grading. An IS auditor should always strive to obtain the best evidence, which is shown in the far right column.
Table 2.4. Example of Evidence Grading
Poor Evidence | Good Evidence | Best Evidence | |
|---|---|---|---|
Material Relevance | Unrelated | Indirect (low relation) | Direct (high relation) |
Objectivity | Subjective (low) | Requires few supporting facts to explain the meaning | Needs no explanation |
Unrelated third party with no involvement | Indirect involvement by second party | Direct involvement by first party | |
Competency of Provider | Biased | Nonbiased | Nonbiased and independent |
Evidence Analysis Method | Novice | Experienced | Expert |
Resulting Trustworthiness | Low | Medium | High |
Evidence is analyzed by using a structured test method to further determine the value it represents. The audit process itself represents a major portion of preparation work to support the analysis of actual evidence.
Note
Every test procedure must be documented in writing to ensure that a duplicate test for verification will yield the same result. Tests may need to be repeated quarterly or annually to measure the auditee's level of improvement. Each test execution should be well documented with a record of time, date, method of sample selection, sample size, procedure used, person performing the analysis, and results.
It is often a good practice to use video recording to document the test process when the execution of the test method may be challenged—for example, to videotape a forensic computer audit if the results may be subject to dispute by individuals who are unfamiliar with the process.
The evidence grading effort aims to improve the resulting trustworthiness of the evidence. A competent IS auditor who can gather evidence and provide expert analysis with a high evidence trustworthiness rating is quite valuable indeed.
An additional factor to consider in regards to evidence is timing. Evidence timing indicates whether evidence is received when it is requested, or several hours or days later. In electronic systems, the timing has a secondary meaning: Electronic evidence may be available only during a limited window of time before it is overwritten or the software changes to a new version.
We have discussed the character of evidence, evidence grading, and timing. The next section explains the evidence life cycle relating to the legal chain of custody.
The evidence will pass through seven life-cycle phases that are necessary in every audit. Every IS auditor must remain aware of the legal demands that are always present with regard to evidence handling. Failure to maintain a proper chain of custody may disqualify the evidence. Evidence handling is just as important for SOX compliance is it would be for suspected criminal activity. Evidence handling is crucial for compliance to most industry regulations.
Warning
Mishandling of evidence can result in the auditor becoming the target of legal action by the owner. Mishandling evidence in criminal investigations could result in the bumbling auditor becoming the target of both the owner and the alleged perpetrator of a criminal activity.
The seven phases of the evidence life cycle are identification, collection, initial preservation storage, analysis, post analysis preservation storage, presentation, and return of the evidence to the owner. The entire set of seven phases is referred to as the chain of custody. Let's go down the list one by one:
- Identification
The auditor needs to identify items that may be objective evidence lending support to the purpose of the audit. The characteristics of the evidence location or surroundings should be thoroughly documented before proceeding to the collection stage. All evidence shall be labeled, dated, and notated with a short description about its purpose or discovery. From this point forward, the evidence movements must be logged into a tracking record. Your client will not be happy if evidence is misplaced.
Note
It may be important to demonstrate how the evidence looked when it was discovered. Identification includes labeling and can include photographing physical evidence in an undisturbed state at the time of discovery.
- Collection
The collection process involves taking possession of the evidence to place it under the control of a custodian. Special consideration should be given to items of a sensitive nature or high value. The IS auditor needs to exercise common sense during the collection process. Client records need to be kept in a secure location.
Tip
For most audits except criminal investigations, the IS auditor should be cognizant of the liability created by taking the client's confidential records out of the client's office. We strongly advise that all records remain within the client's facility to relieve the auditor of potential liability. The best way to prevent accusations is to ensure that you never place yourself in a compromising position. Allow the client to remain responsible for evidence security. Just be sure to lock up each evening before you leave.
Evidence of compliance is required for regulations such as SOX. A smart auditor recognizes that storage of any evidence in their own office is not acceptable. Records should be placed in a bonded record storage facility with the cost paid by your client. Consider the liability created by exposing records in your office to theft, destruction, or disclosure by a search order from an unrelated court subpoena.
Tip
Criminal evidence should not be disturbed until after proper identification and labeling. It may be beneficial to have a nonbiased observer present as a witness to attest to the investigator's actions as observed during the collection activity.
- Initial preservation storage
A major problem with evidence is the challenge of preserving it in its original state. The preservation and storage process is a vital component in the chain of custody. The custodian of the evidence must be able to prove that the evidence has been protected and no alteration has occurred. The slightest change will transform the evidence without changing its identity. Electronic evidence requires special handling procedures to overcome future claims that the evidence has been altered (evidence tampering).
Warning
The chain of custody must remain unbroken to prevent evidence from being disqualified. In legal proceedings, a common method of disqualifying evidence is to argue that the custodian has failed the chain of evidence requirements. A related accusation is that evidence has been tampered with, which is often a plausible argument unless it can be proven that mishandling never occurred.
- Analysis
In this phase, the evidence samples are examined by observation, scientific test, and qualitative and quantitative measurement. The entire process and results should be well documented. Individual tests may need to be rerun if errors are discovered with the test procedure, sample, or personnel executing the test.
In some instances, the test results may need to be duplicated by a second independent tester to validate the initial finding.
As you may recall, regulatory compliance is an ongoing requirement. The same internal controls will need to be tested at least once each year. The auditor should ensure that the testing process produces a reasonable degree of consistency in each subsequent audit.
- Post analysis preservation storage
After testing, the evidence and samples must be returned to preservation and secure storage. The evidence will continue to stay in storage except during presentation or retesting.
The auditor should be aware that proper handling is paramount for success in legal proceedings. Evidence used in legal trials may be retrieved and returned multiple times for use in court presentations prior to final release for return to the owner. The U.S. legal process allows for trials in at least three separate courts as the case progresses through to final appeal.
Note
A bonded evidence storage facility might be used for storage when the evidence is used in legal cases lasting several years. An example would be a case of corporate fraud or theft.
Management may decide that the evidence used in routine compliance audits should be copied and bound into storage binders. Selected copies of those documents would be sent to storage with the client's financial records. This ensures the ability to demonstrate the evidence in a near original state for any future investigation by industry regulators. Initial evidence collection is a time-consuming process that might be difficult to duplicate in the future.
- Presentation
The evidence and findings are to be presented in support of the auditor's report. A variety of details may be included or omitted depending on the nature of the report. Reports of system performance offer little detail when compared to reports of criminal activity.
- Return to owner
The evidence is returned to the owner after the audit test results are successfully evaluated, or after legal proceedings are officially concluded by order of the final court. It is important to notice the distinction. In noncriminal activity, the evidence is promptly returned when the audit is concluded. Evidence may be held in preservation storage for several years if situations of suspected criminal activity exist.
Figure 2.4 demonstrates the logical flow through the entire chain of custody. A CISA is required to be competent in this evidence life cycle.
Now we will discuss examples of evidence that an IS auditor will typically use during an audit.
All auditors are required to prepare a thorough set of audit documentation at the start of each audit. This includes copies of the charter and scope, audit plans, policies, and specific procedures used during the audit. You should record both handling and test procedures. Audit reports are frequently used as evidence in lawsuits and criminal cases of embezzlement or fraud. As you recall, in Chapter 1 we mentioned several cases involving corruption perpetuated by dishonest executives. Professional auditors will need to demonstrate the extent to which they have complied with IS auditing standards.
Your job as an auditor is to provide consistency. All your findings should be repeatable by another auditor. Documentation should include auditor's working notes and evidence necessary to reperform the audit. The key to building a successful practice is to map each of your planned tasks and corresponding findings to a specific point of compliance in the standard or regulation. This mapping may require you to identify the page, paragraph, and line number in the regulation and for each item you will show as compliant or noncompliant. During the audit, you should be preparing records to answer the following questions:
Who was involved?
What was audited, how was the evidence obtained, and what specific test procedure was used?
When did it occur?
Where did it occur?
Why (the purpose of the audit)?
How were the audit plan and procedures executed?
Later, the auditor's final working papers should be placed into an audit documentation archive, including copies of any reports that were issued.
The auditor should always remember that records of each audit may be needed again in the future. Integrated audits such as SAS-94 will have documentation retention requirements equal to the financial statement, typically at least seven years. Financial and internal control records for an integrated audit serve as a matched pair that should not be separated. Records for certain systems or processes may have a retention requirement specified in their service-level agreement or contract. Very specialized systems used in aerospace, life safety, hazardous materials, or the military may be retained for decades.
Let's look at the selection method for your audit samples and begin the move toward actual testing.
Audit samples are selected for the purpose of collecting representative evidence to be subjected to either compliance testing or substantive testing (which is defined later in this chapter). The auditor should consider a selection technique that will provide the most relevant evidence supported by appropriate analytical procedures.
Two basic types of audit samples can be designed by the auditor to fulfill their requirements: statistical and nonstatistical. Figure 2.5 shows the various audit samples, as well as their testing methods. Care is given to the selection process in order to avoid drawing the wrong conclusion from the wrong sample. This is referred to as a sampling risk. Let's look at each of these samples more closely.
Statistical sampling uses mathematical techniques that result in an outcome that is mathematically quantifiable. Statistical samples are usually presented as a percentage. The purpose of statistical sampling is to gain an objective representation. Samples are selected by an objective mathematical process. The auditor should be aware that if the client has strong internal controls, the sample sizes may be smaller because the odds of fraud or failure will be lower.
Examples of statistical sampling include the following:
- Random sampling
Samples are selected at random.
- Cell sampling
Random selection is performed at predefined intervals.
- Fixed interval sampling
The sample existing at every n + interval increment is selected for testing.
Nonstatistical sampling is based on the auditor's judgment (also referred to as judgmental sampling). The auditor determines the sample size, the method of generating the sample, and the number of items to be analyzed. The results of judgmental sampling are unlikely to represent the actual population. This is a subjective process usually based on elements of risk or materiality. An example of nonstatistical sampling includes haphazard sampling, in which the samples are randomly drawn for testing.
After the samples are selected, the next step is to perform compliance tests or substantive testing.
As stated earlier, the basic test methods used will be either compliance testing or substantive testing. Appropriate audit samples will have to be generated for the test.
Compliance testing tests for the presence or absence of something. Compliance testing includes verifying that policies and procedures have been put in place, and checking that user access rights, program change control procedures, and system audit logs have been activated. An example of a compliance test is comparing the list of persons with physical access to the data center against the HR list of current employees.
Compliance testing is based on one of the following types of audit samples:
- Attribute sampling
Generally popular in compliance testing. The objective is to determine whether an attribute is present or absent in the subject sample. The result is specified by the rate of occurrence—for example, the presence of 1 in 100 units would be 1 percent.
- Stop-and-go sampling
Used when few errors are expected. Stop-and-go allows the test to occur without excessive effort in sampling and provides the opportunity to stop testing at the earliest possible opportunity. It is a simple form of testing to reinforce any claim that errors are unlikely in the sample population.
- Discovery sampling
A 100 percent sampling used to detect fraud or when the likelihood of evidence existing is low. Forensics is an excellent example of discovery sampling. This is an attempt to discover evidence.
- Precision, or expected error rate
The precision rate indicates the acceptable margin of error between audit samples and the total quantity of the subject population. This is usually expressed as a percentage, such as 5 percent. To obtain a very low error rate, it is necessary to use a very large sample in testing. Auditors are justified in using a smaller sample size when the total population is expected to be error-free. A larger sample is required when errors are expected to be present in the population. The larger sample can yield a higher average. When errors are expected, the auditor must examine more data to determine whether the actual errors are within a tolerable error rate (maximum errors you would accept).
Error levels may be determined by reviewing the findings of a prior audit and by considering changes in the organization's procedures. Use the risk-based audit strategy to determine whether your samples and tests are telling the truth about the auditee.
Substantive testing seeks to verify the content and integrity of evidence. Substantive tests may include complex calculations to verify account balances, perform physical inventory counts, or execute sample transactions to verify the accuracy of supporting documentation. Substantive tests use audit samples selected by dollar value or to project (forecast or estimate) a total for groups with related characteristics.
Substantive testing is based on one of the following types of audit samples:
- Variable sampling
Used to designate dollar values or weights (effectiveness) of an entire subject population by prorating from a smaller sample. Consider the challenge of counting large volumes of currency by its weight. Variable sampling could be used to count currency by multiplying the physical weight of one unit by the total weight of the combined sample, and then multiplying by the face value printed on the bill or coin. A demonstration is a single $50 bill weighing 1.0 gram, with the entire sample of $50 bills weighing 61 grams altogether. The combined sample weight would indicate a total quantity of 61 bills for an estimated dollar value of $3,050. This is a common technique for forecasting quantity and value of inventory based on particular characteristics.
- Unstratified mean estimation
Used in an attempt to project an estimated total for the whole subject population.
- Stratified mean estimation
Used to calculate an average by group, similar to demographics, whereby the entire population is divided (stratified) into smaller groups based on similar characteristics. Examples are teenagers from the ages of 13 to 19, people from the ages of 20 to 29, people from the ages of 30 to 39, and those who are male or female, smokers or nonsmokers, and so on.
- Difference estimation
Used to determine the difference between audited and unaudited claims of value.
Used to indicate the maximum number of errors that can exist without declaring a material misstatement.
For compliance tests, a tolerable error rate is the maximum deviation from a procedure that the auditor is willing to accept. Hint: If you want to remain an auditor, it had better be a very small deviation.
In substantive testing, the auditor uses their judgment concerning material relevance and concludes whether the audit objective has been achieved. The test procedure and results should indicate a truthful pass or fail. A smart auditor will always lean toward the conservative side for safety in their measurement.
Regardless of the audit sample and test method used, the auditor is presumed to have a high degree of confidence when the audit coefficient is 95 percent or higher. The audit coefficient represents your level of confidence about the audit results. It is also referred to as a reliability factor.
Just like Leonardo DaVinci and Louis Pasteur, every auditor needs to keep logs documenting their tests, samples, results and observations. The auditor must trace all findings of conformity and nonconformity in their documentation of test results. Always remember your audit test results must be repeatable by another auditor.
Each finding of evidence can be classified into one of these common reporting statements, presented in order of most desirable to least desirable.
- Noteworthy achievement
Auditee has demonstrated some aspect in the process or system is being done very well. Auditee's efforts are very effective and the auditor wants to bring recognition where credit is due. Auditee has exceeded the requirements.
- Conformity
The testing of evidence proves the auditee is accomplishing their stated objectives. Minimum requirements have been met.
- Opportunity for improvement
A specific item found is not in violation, but should be targeted as an opportunity for improvement. For example the level of work integration is low, therefore fixing this issue could reduce waste or the amount of manual effort required.
- Concern
The evidence and auditor's observations indicate the possibility for future problems that need to be understood by management. Examples include over reliance, inefficiency, cascading problems and the likelihood of failure.
- Nonconformity
Testing indicates a violation exists which needs to be corrected. The violation found may be minor or major significance. Nonconformities include system defects or missing control capabilities.
Using your audit plan as a roadmap, it's time to analyze the evidence samples. The goal is to determine if the samples tested by the auditor indicate conformity (meets requirement) or nonconformity (fails requirement).
We have two concerns as auditors related to testing: sufficiency of evidence and contradictory evidence. Let's look into this further.
- Sufficiency of evidence
Is there enough evidence of sufficient quantity and quality to fulfill the intended purpose and scope of the audit? If not, the auditor will not be able to prove conformity. The auditor should continue working the audit and report the limitations. Unless enough evidence can be found the auditee will fail to meet compliance or substantive goals.
- Contradictory evidence
Let the evidence tell the story. Contradictory evidence suggests either the auditor is doing something wrong or you have discovered evidence proving a problem actually exists (nonconformity). The auditor needs to perform additional quality assurance checks and recheck the test results to determine the reason why this nonconformity has been detected.
It is management's responsibility to implement the controls and supervision necessary to detect irregularities and potentially illegal acts in their environment. Management is responsible for making written assertions as to their representation of internal controls. Audit plans should include provisions and procedures in the event an auditor encounters irregularities or possibly illegal acts.
Examples of illegal activities include the following:
- Fraud
Any act of deception used to gain an advantage. Misrepresentation is a type of fraud. Examples include posting transaction records that are intentionally false and without genuine merit.
- Theft
Taking or acquiring resources that are not rightfully yours. The legal term conversion is another name for theft. Embezzlement is a form of theft.
- Suppression
Suppressing data or records and their effects in business transactions. This is related to obstruction and willful omission.
- Racketeering
The process of repeated (pervasive) fraud or other crimes. Racketeering is governed by the Racketeer Influenced and Corrupt Organizations (RICO) Act, which carries dire consequences to those parties alleged to have participated.
- Regulatory violations
Intentionally or unintentionally violating the law.
The IS auditor should understand that an organization's internal controls will not eliminate the possibility of irregular or illegal activity. Although it is not the auditor's job to detect these conditions, it is important to be alert to potential indicators. The auditor should be on the lookout for the following symptoms:
- Questionable payments
Examples include fees that appear to be excessively high or low, failed account reconciliation, payments to government officials, and payments for unspecified services.
- Unsatisfactory record control
Examples include poor record keeping in general, proper controls not in use, evidence of falsified documents, missing documentation, and the untimely shredding of documents in advance of corporate retention guidelines.
- Unsatisfactory explanations
Examples include large or unusual transactions, and especially transactions with related companies at the end of the financial reporting period such as month-end or quarter-end. Other examples include overbooked or under booked sales, unexplained or unusual items, or unexplained funds held in suspense accounts.
- Other questionable circumstances
These might relate to the lifestyles of the organization's executives and employees.
If you discover any potentially irregular or illegal activity, the next step is to attempt to determine whether management is aware of the situation or has participated in the suspected activities. The auditor should document all information, evidence, findings, and conclusions that led to the discovery of the suspected activities:
The auditor should consider any unusual or unexpected relationships that could lead to material misstatements or misrepresentations.
The auditor should maintain a position of professional skepticism.
Upon learning of material irregularities or illegal acts, the auditor should promptly notify one level of management higher than where the suspected activities may have taken place.
If the activities involve a person charged with internal controls or governance, reporting should take place at the highest level possible.
The auditor should not contact law enforcement or regulators until advised to do so by the auditor's legal counsel. Special handling procedures are usually required to protect the auditor.
The auditor should never become a party to the suspected activity. The auditor should seek competent legal advice if unsure about what actions to take. You may be advised to prepare for termination of the audit.
Don't be surprised to discover something outside the scope of your audit; it happens all the time. Smart auditors recognize their obligation to stay within the mutually agreed-upon scope of their client. No respectable auditor would ignore problems found outside the original scope. The first objective is to determine whether the problem is major or just a minor nuisance. Here's what to do:
- Minor problem
Report the discovery to the auditee and continue the audit within the original scope.
- Major problem
Report the finding to your lead auditor or engagement manager. The audit team leader is responsible for reporting the discovery to the auditee's management. In addition, a decision needs to be made regarding whether this situation warrants additional investigation, and whether the audit should stop or continue within the original scope. Major problems outside of scope should be listed in your audit report. Be sure to ask your lead auditor whether the problem warrants reporting as a nonconformity within this particular audit or just mentioning it without marking as a nonconformity. The most successful auditors understand that the highest level of professionalism is necessary to handle this type of situation. Well-mannered professionals may gain additional audit work if the situation is handled correctly.
After performing your audit, the next step is to prepare a presentation to report your findings. Reporting is the process by which the auditor conveys to management their findings, including the following:
Audit scope
Audit objectives
Methods and criteria used
Nature of findings
Extent of work performed
Applicable dates of coverage
In addition, the final report should state any restrictions, reservations, or qualifications (concerns) that the auditor holds in relation to the audit. The auditor may provide a final opinion or no opinion based on these potential limitations. Auditors may issue qualified or unqualified opinions:
A qualified opinion means there are restrictions on the nature or the content of the findings.
An unqualified opinion has no restrictions on its use because the findings have no reservations.
Statement on Auditing Standards (SAS), the COSO internal controls framework, and the IT Governance Institute (ISACA-ITGI) publish several points of information that should be included in the final report. You should consult their publications for specific details. In summary, the recommendations include the following:
A title that includes the word independent (for an external audit)
The applicable date of the report
Identification of the parties and subject matter
An executive summary
Any visual representations, charts, graphs, or diagrams
A statement of the standards followed during the audit
A statement of the procedures performed, and whether they were agreed to by the specified parties
Any necessary disclaimers
A statement of additional procedures, if performed
A statement of restrictions on the use of the report
A statement of any auditor concerns, reservations, or qualifications to the audit
Detailed findings and the auditor's opinion
Auditor signature and contact information
The IS auditor's signature attests that the audit report and stated findings are true and correct. Attestation is the act of providing your assurance via a signature that the contents of a document are authentic and genuine.
Tip
You should keep your report easy to read. Simple graphics, tables, and color coding will be appreciated by your client.
After producing the final report, you will need to meet with the auditee and management to review the findings. The primary purpose of this meeting is not to change your findings, but to obtain acceptance and agreement by the auditee. This is the final quality-control check before issuing your final report. You want to ensure that the facts are correctly presented in your report. A final copy of this report and of your working notes will need to be placed into the audit archive for document retention.
On the rare occasion that an auditor determines after issuing a final report that one or more auditing procedures have been omitted, it may be necessary to review some of the audit alternatives to compensate for the omission. If the omitted procedures present material bearing on the outcome, and the audit alternatives cannot compensate for the deficiency, canceling the report and reissuing a new report (if appropriate) may be necessary. If the omitted procedures have tangible bearing on the outcome, the auditor should consult with their lawyer for advice concerning any possible avenues or potential legal actions.
After issuing a report, the auditor is required to conduct an exit interview with management to obtain a commitment for the recommendations made in the audit. Management is responsible for acknowledging the recommendations and designating whatever corrective action will be taken, including the estimated dates for the action.
In subsequent audits, you will check whether management honored their commitments to fix or remediate deficiencies found in a prior audit. Occasionally, the deficiencies are left uncorrected because changes in the organizational design or practice have eliminated the conditions of the prior control's weakness. Particular findings may apply to events that are no longer relevant. Otherwise, you expect management to act in a timely manner to correct the deficiency as originally reported.
Warning
The auditor should never take ownership of any problems found. This would violate your independence. All issues raised in your findings should be regarded as owned by the auditee. It's the job of their management to fix it.
Sometimes events of concern are discovered, or occur, after an audit has been completed. You would be concerned about the discovery of subsequent events that pose a material challenge to your final report. Accounting standards recognize these events and classify them as follows:
Depending on the type of audit, you may have additional reporting requirements or activities. These may require additional disclosures or adjustments to your report based on the nature of the event that was recently discovered or occurred.
Tip
It is not the auditor's responsibility to detect subsequent events.
This concludes our review of the IS audit process. A CISA is expected to have a thorough understanding of the entire audit process. You will be expected to understand the issues and motivation behind each step.
A violation of the audit process would be a concern and would likely indicate that the outcome is meaningless. As an IS auditor, you should always strive to honor the spirit and intent of the audit process. Conduct audits in accordance with recognized audit standards, guidelines, and best practices. It is your job to plan the audit around the business requirements by using a risk-based approach and to collect meaningful evidence. You are expected to produce an objective report based on the evidence you obtained during the audit. The final report will be communicated to management with the goal of gaining their commitment to resolve any weaknesses found. Your actions should be well documented and reproducible by another auditor.
Chapter 1 covered how the auditor should look, act, and think. This chapter discussed how the auditor should carry out the audit. The next chapter presents the techniques used for IT governance.
- Know how to develop and implement a risk-based audit strategy.
The auditor should focus on areas of high value. The risk assessment will help to determine whether the audit will yield meaningful information. Certain types of conditions may be difficult to audit. It is important that the audit is based on meaningful evidence that is materially relevant.
- Understand how to conduct IS audits in accordance with published standards, guidelines, and best practices.
The auditor is expected to follow published audit standards to ensure thoroughness and consistency. Deviations from standards and guidelines is rare. Any deviation must be well documented, but results may not be accepted by the audit community. The purpose of best practices is to aid the auditor by identifying useful procedures and techniques. Every audit should be designed to adhere to standards.
- Be familiar with how to plan for specific audits.
The CISA needs to understand the constraints and requirements of individual audits. It is the auditor's job to identify the resource requirements, sampling requirements, test methods, and procedures to be used. The auditor will identify appropriate personnel to be interviewed. The interview process must be scheduled and must implement predefined questions for the purpose of gathering data. An audit involving third-party personnel will present its own unique challenges.
- Know the auditing practices and techniques.
Well-established IS auditing procedures ensure thoroughness and consistency necessary for a successful audit. Good audits will implement a well-thought-out sequence of procedures to evaluate materially relevant samples. ISACA provides the auditor with foundation knowledge that should be implemented during your audit. Effective sample selection of meaningful tests should yield materially relevant results.
- Be familiar with IS control objectives and performing control assessment.
High-level controls are categorized as general controls, pervasive controls, detailed controls and application controls. Internal controls are intended to be preventative, detective, and corrective. Each control may be implemented using administrative methods, physical methods, and technical methods. The purpose of the controls is to prevent harm and protect an asset. The IS auditor is responsible for evaluating the effectiveness of controls.
- Know some of the various types of computer assisted audit tools (CAAT).
Computer assisted audit tools are software tools that can provide detailed analysis of computer systems configuration, vulnerability, logs, and other information. The CAAT output should be kept confidential because of the potentially sensitive nature of its contents.
- Understand the continuous auditing methods.
Continuous audit methods such as audit hooks or SCARF with embedded audit modules (SCARF/EAM) are used in environments where it is not possible to interrupt production.
- Know the techniques to gather information and manage the evidence life cycle.
The auditor can collect information through traditional sources of business records, computer data files, and CAAT. Meaningful information can be obtained through personal interviews, workshops, and surveys. All information and evidence should be recorded and tracked. The evidence life cycle comprises identification, collection, preservation, analysis, safe storage, and finally its return to the owner. Evidence used for criminal prosecution must be handled with the highest degree of care. Evidence that is mishandled will void legal claims and may result in punitive legal action.
- Know the types of evidence and evidence grading.
The best evidence will tell its own story. The best evidence will prove or disprove a point. The best evidence is both objective and independent. The timing of evidence must be considered when calculating its useful value. Evidence that is late and subjective will be of low value. Material evidence will have a bearing on the final outcome. Irrelevant evidence will not affect the final decision.
- Familiarize yourself with the types of audit tests and sample selection.
Audit tests can be substantive or compliance based. It is important to select an appropriate sample in order to generate data to reflect the actual situation. Audit test procedures and sample selection methods must be well documented to ensure verifiable and reproducible tests. The sample may be selected based on physical characteristics, value, or size of population.
- Understand how evidence is analyzed for reporting conformity or nonconformity.
The auditor must have sufficient evidence of quality and quantity in order to report a conformity. Test results are usually reported as noteworthy for special achievement, conforming to minimum requirements, opportunity for improvement, concern that's not a violation yet, and nonconformity.
- Know how to deal with irregular and illegal acts.
It is possible that you could encounter evidence of irregular or illegal acts. The discoveries should be communicated to the next level of management higher than where the act occurred. Such a discovery involving persons responsible for internal controls must be reported to the absolute highest level of management. The auditor should consult their attorney for legal advice.
- Know how to advise clients on implementing risk management and control practices while maintaining independence.
The auditor is encouraged to educate their client and help increase awareness of control issues. It is important that the auditor does not participate in specific discussions of design or architecture. The auditor must not work on fixing problems if the auditor is expected to be independent. A client may hire an auditor for remediation and use a separate, unrelated auditor for the audit. The auditor cannot be independent if they participated in the audit subject.
- Be able to communicate issues, potential risks, and audit results.
The auditor is expected to communicate materially relevant issues to management through the audit reporting process. Issues of high significance should be communicated directly to the audit committee. The final results of each audit should be verifiable and reproducible. All communication must convey the facts without placing blame on individuals.
- Understand the role of traditional audits compared to control self-assessment (CSA).
Control self-assessments are designed to empower the customer's staff. The intention is to generate awareness and ownership of problems. A control self-assessment is an excellent way to improve the performance of an organization between traditional audits. The traditional audit is still necessary to the independence requirement.
Failing to prevent or detect a material error would represent which type of risk?
Overall audit risk
Detection risk
Inherent risk
Control risk
Which term best describes the difference between the audit sample and the total population?
Precision
Tolerable error rate
Level of risk
Analytic delta
Which is not a purpose of risk analysis?
Support risk-based audit decisions
Assist the auditor in determining audit objectives
Assist the auditor in identifying risks and threats
Ensure absolute safety during the audit
Which of the following is not a type of quantitative sampling model?
Difference estimation
Stratified mean per unit
Unstratified mean per unit
Qualitative estimation per unit
Which of the following is false concerning a control self-assessment?
Empowers the user to take ownership and accountability
Eliminates the need for a traditional audit
May be used to identify high-risk areas for later review
Will not have the level of independence provided by an external auditor
Which control classification attempts to repair the impact of a threat?
Preventative
Detective
Corrective
Deterrent
The two types of tests are referred to as _________ and _________ using _________ sampling methods.
Substantive tests, compliance tests, variable and attribute
Compliance tests, substantive tests, variable and discovery sampling
Predictive tests, compliance tests, stop-and-go and difference estimation
Integrity tests, compliance tests, stratified mean and unstratified mean
What is the purpose of the audit charter?
To engage external auditors
To grant responsibility, authority, and accountability
To authorize the creation of the audit committee
To provide detailed planning of the audit
Which of the following would be a concern of the auditor that should be explained in the audit report along with their findings?
Detailed list of audit objectives
The need by the current auditor to communicate with the prior auditor
Communicating results directly to the chairperson of the audit committee
Undue restrictions placed by management on evidence use or audit procedures
The concept of due care is best defined as which of the following?
Proportional to the level of risk or loss that could occur
Basic care providing a minimal level
Ordinary care providing an average level
Extraordinary care above and beyond average
What is the purpose of the audit committee?
To assist managers with training in auditing skills
To govern, control, and manage the organization
To challenge and review assurances
To provide daily coordination of all audit activities
What is the best data collection technique the auditor can use if the resources are available?
Surveys that create a broad sample
Review of existing documentation
Auditor observation
Interviews
Which of the following types of risk are of the most interest to an IS auditor?
Control, detection, noncompliance, risk of strike
Inherent, noninherent, control, lack of control
Sampling, control, detection, inherent
Unknown, quantifiable, cumulative
Which of the following best describes the early stages of an IS audit?
Documenting the IS environment
Testing for compliance to applicable regulations as agreed to
Reviewing prior IS audit reports
Commencing the planning process
Which of the following describes the relationship between compliance testing and substantive testing?
Compliance testing checks for the presence of controls; substantive testing checks the integrity of internal contents.
Substantive testing tests for presence; compliance testing tests actual contents.
The tests are identical in nature; the difference is whether the audit subject is under the Sarbanes-Oxley Act.
Compliance testing tests individual account balances; substantive testing checks for written corporate policies.
What is the principal issue surrounding the use of CAAT?
The capability of the software vendor.
Possible cost, complexity, and the security of output.
Inability of automated tools to consider the human characteristics of the environment.
Documentary evidence is more effective.
An IS auditor is performing a review of an application and finds something that might be illegal. The IS auditor should
Disregard or ignore because this is beyond the scope of this review
Conduct a detailed investigation to aid the authorities in catching the culprit
Immediately notify the auditee of the finding
Seek legal advice before finishing the audit
The auditor is permitted to deviate from professional audit standards when they feel it is necessary because of which of the following?
Standards are designed for discretionary use.
Deviation is almost unheard of and would require significant justification.
Deviation depends on the authority granted in the audit charter.
The unique characteristics of the client will require auditor flexibility.
What are the proper names of the four methods of risk response?
Avoid, accept, transfer, and mitigate
Mitigate, accept, transfer, and reduce
Ignore, accept, assign, and mitigate
Analyze, mitigate, reduce, and assign
Audits are intended to be conducted in accordance with which of the following ideals?
Specific directives from management concerning evidence and procedure
Reporting and communication
Assessment of the organizational controls
Adherence to standards, guidelines, and best practices
Which is the best document to help define the relationship of the independent auditor and provide evidence of the agreed-upon terms and conditions?
Audit charter
Annual audit plan
Engagement letter
Auditor's report
Who has the responsibility of setting the scope of the audit?
Auditor
Client
Audit manager
Auditee
What technique could the auditor use for planning an audit when the requirements and process to audit are vague?
Monte Carlo
Process technique
Delphi technique
Inverted straw-dog estimation
Which type of audit may be used for regulatory licensing or external reporting?
Qualified audit
Independent assessment
Control self-assessment
Traditional audit
What is the biggest issue with the decision to transfer risk to an outsourced contractor?
There is potential for uncontrollable increase in operating cost over time.
Outsourcing shifts the entire risk to the contractor.
The company still retains liability for whatever happens.
Outsourcing shields the company from intrinsic risks.
Why is the best practice in contracting to have a provision for the right to audit along with service performance metrics?
SAS-70 reports may be used to reduce the number of audits requested by clients.
SAS-70 reports contain all the important details of interest for the client.
SAS-70 reports may be used if agreed to by the client; however, the auditor producing the report is more important than the content.
Performing your own audit bears a higher cost than accepting the SAS-70 report.
During audit planning, several documents are produced in support of the project. Which of these is used to identify the person responsible for specific tasks in order to gain funding and ensure quality?
Skills matrix
Procurement matrix
Task matrix
Activities matrix
Which of the following conditions is false in regard to using the work of other people during your audit?
Ensure independence of the provider.
Accept the work based on job position.
Use agreed-upon scope and approach.
Provide supervision and review.
What is the best reason why quality control planning techniques are important in auditing?
To ensure that better products are manufactured.
Quality inspection will improve the audit.
Quality appraisal is the best metric for measuring success.
Quality is measured by the price of nonconformance.
ISACA refers to testing for strong controls. What is the best description of a strong control?
Effective implementation of multiple controls targeting the same objective
Preventative controls that stop the problem from ever occurring
Using at least one control in each of the three categories of preventative, detective, corrective
Implementing comprehensive pervasive controls inside of an ERP application
Which of the following choices gives the best definition of controls focused on managing and monitoring inside a specific department?
General controls
Pervasive controls
Technical controls
Application controls
Which of these statements is true regarding electronic discovery?
It provides access to data and systems, and may include recovering deleted data from any storage medium.
If privileged information is unintentionally disclosed during discovery, there is no way to retrieve it.
The data owner is liable if the stored information was lost during normal operations, even if the loss was not the result of negligence.
Encryption can be used to prevent disclosing confidential information requested in the discovery process.
Auditors base their report on findings, evidence, and the results of testing. It's more of a score than an opinion. Which of the following types of evidence sampling refer to a 100 percent sample?
Attribute
Stop-and-go
Cell
Discovery
Which of these types of computer assisted audit tools (CAAT) is designed to process dummy transactions during the processing of genuine transactions?
Continuous and intermittent simulation
Embedded program audit hooks
Embedded audit module
Online event monitor
What does the term unqualified opinion refer to?
There are no restrictions on use.
The auditor is not properly qualified to give an opinion.
Evidence testing methods did not produce a conclusive answer.
There are restrictions on use.
B. A detection risk is that you would fail to detect that a material error has occurred.
A. The compliance testing uses precision to describe the expected error rate of the sample compared to total population. Precision is usually expressed as a percentage. Depending on the consequence of error, higher rates above 5% may indicate the auditor needs to increase sampling and test more evidence.
D. Risk analysis does not ensure absolute safety. The purpose of using a risk-based audit strategy is to ensure that the audit adds value with meaningful information
D. Difference estimation, stratified mean, and unstratified mean are valid sample types for substantive testing. Qualitative estimation is just a distracter.
B. All of the statements are true except B. A CSA is not a substitute for a traditional audit.
C. Corrective controls are designed to fix the damage caused by the threat's impact.
A. Answer B is incorrect because compliance testing uses discovery sampling to detect fraud. C and D are distracters.
B. The audit charter's purpose is to grant the right to audit and delegate responsibility, authority, and accountability.
D. Undue restrictions on scope would be a major concern as would the lack of time or the inability to obtain sufficient reliable evidence.
A. Due care is proportional to the level of risk or loss that could occur. Greater care is required for items of high value or greater impact due to loss.
C. The audit committee's purpose is to review and challenge assurances made, and to maintain a positive working relationship with management and the auditors.
D. Interviewing selected personnel is the best technique. Surveys, document review, and observations generate a lower yield.
C. The answers including risk of strike, lack of control, and unknown are distracters.
D. You start the planning process to identify objectives, resources, and the risk-based audit approach.
A. Substantive testing checks the substance or integrity of a transaction. Compliance testing looks for presence.
B. CAATs are able to perform faster than humans and produce more-accurate data in functions such as system scanning. Cost, training, and security of output are major considerations.
D. Seek competent legal advice. It is not the auditor's job to detect potentially illegal acts; however, the auditor should seek the aid of a lawyer concerning liability and reporting requirements.
B. Standards are mandatory, and any deviation would require justification.
A. The proper answer is avoid, accept, transfer to another party, and mitigate to reduce exposure. The other answers contain distracters.
D. Audits should adhere to standards, guidelines, and best practices. Answer A represents a restriction on scope. B and C are components of answer D.
C. The engagement letter is used with independent auditors to define the relationship. This letter serves as a record to document the understanding and agreement between the audit committee and the independent auditor. It provides the independent auditor the responsibility, accountability, and authority to conduct the audit.
B. Every audit is paid for and requested by a client, who is responsible for setting the scope, granting authority, and providing access to the auditee.
B. Shewhart's process technique of Plan-Do-Check-Act can be used to gather the requirements and refine the definition of any process. Repeat the cycle until you have enough information to conduct an audit. Findings can be used on the next cycle to improve the results.
D. Traditional independent audits are conducted with formality and adherence to standards necessary for regulatory licensing and external reporting. It's true that there is always a small shady accounting firm ready to lie for a client. The world expects an independent audit to be conducted by a qualified auditor representing a high degree of truth. Assessments are too informal and therefore can be used only internally in the organization.
C. The work can be outsourced; however, the liability for failure remains with the company. One example is the Firestone tire failure affecting Ford Motor Company. Another is the lead paint used by subcontractors forcing the giant toy recall of 2007. Liability cannot be outsourced.
C. Not all SAS-70 reports are created equal. The subcontractor will use the SAS-70 to reduce or eliminate audits by their customer. A poorly run SAS-70 audit is not worth the paper it's written on. In addition, the client may know details omitted or ignored by the SAS-70. Every contract must contain a clause granting right to audit at any time, and must specify who pays the expense.
A. A skills matrix is used to identify the skills of each person and to ensure that the right person is performing the task. Using a skills matrix in planning is an excellent method to justify proper funding for training or additional personnel.
Answer: B. The auditor should never base the decision on the job position of the other person. All of the other choices are vague but truthful. Always assess the independence of the provider, check their qualifications, agree on scope and procedures used, and supervise and review their work. Don't use it if the results are questionable or fail to follow very high adherence to audit standards.
D. Quality is measured by the added costs for failure (nonconformance). Planning, prevention, and conformance to specifications will create quality. This means that your audit needs to have a clear definition of requirements to be successful. The standard of performance is zero defects.
A. Strong controls will implement multiple types of preventative, detective, and corrective controls using a combined approach of administrative methods, physical methods, and technical methods. This is referred to as depth of control, hopefully using all nine layers. Using the bare minimum would be a weak control.
B. Pervasive controls define the direction and behavior of a department. The IS department uses pervasive controls that permeate their activities to create a cooperative environment of help desk, software support, security, and administration. General controls govern all the departments. Detailed controls focus on specific steps and procedures.
B. All the other options are false and contradict the laws of electronic discovery. You can't block disclosure of evidence during discovery unless the information is protected by the legal definition of privilege. Accidental disclosure may occur; therefore, the disclosing party can notify the other party to sequester, destroy, or return the information. The receiving party is prohibited from disclosing the information after notice of privilege is given.
D. Discovery sampling is used to find 100 percent of everything possible when fraud is suspected or the likelihood of finding evidence is low. All the other possible choices are valid sampling methods used in compliance testing.
C. Embedded audit module (EAM) processes dummy transactions during the processing of genuine transactions. The intention is to determine whether the system is functioning correctly.
A. A qualified opinion means the auditor had reservations about the results and the report is valid for only certain conditions. An unqualified opinion has no restrictions on use. The auditor is happy with the findings and how the audit was conducted.