THE OBJECTIVE OF THIS CHAPTER IS TO ACQUAINT THE READER WITH THE FOLLOWING CONCEPTS:
Knowledge of service-level management practices including operations workload, scheduling, services management, and preventative maintenance
Knowledge of the Information Technology Infrastructure Library
Knowledge of control functionality in the IT infrastructure
Understanding specific personnel roles and responsibilities
Data administration for integrity and optimization databases
Issues facing the use of mobile code, Java, and ActiveX
IT performance monitoring using analyzers, system utilization, and log management
Understanding of change management, configuration release management, and emergency changes
Knowledge of techniques for problem reporting and incident management
Understanding digital forensic techniques

ISACA expects every IS auditor to understand how to evaluate the techniques and best practices used in IT support.
Every time information technology is mentioned, the conversation turns toward operations. IT suffers from the same perceived fate as facilities management, the plumber, or the electrician. People in each of these fields feel that their contribution is invaluable. Yet the truth is that few possess a mastery of the intricate knowledge of how each business unit operates. This common drawback is the principal reason why IT outsourcing is a popular topic with users. Smart IT executives recognize that a fundamental change is necessary. The key to success is conveying how IT operations is a functional servant to its masters in the business unit.
Everyone in the organization is aware of IT operational problems. They may appear as slow response times, systems being unavailable for any reason, problems with data, and ongoing arguments between people who are trying to accomplish their jobs. So how can we improve operations? Let's start with the two most common statements:
- Buy more
New product advertisements and dropping prices make it appear as though the solution is to continually buy more until you run out of room, people to implement the product, or money.
- Rearrange priorities
Many organizations continuously fight fires and rearrange the priorities rather than fix the root problem. Changing priorities is more of a workaround to circumvent the problem. The result is lots of work without any real progress.
A third choice gets us closer to the real solution. IT leadership will commit the resources necessary to document and measure the current situation. Time and effort will be expended to determine the root of the real problems. Let's investigate what needs to be accomplished to truly fix the problems:
Policies will be added or amended.
Standards will be adopted or modified.
Job descriptions will be updated to reflect the actual jobs performed to ensure genuine assignment of responsibility and accountability.
Better procedures will be created and updated.
Change control will shift from the needs of IT toward the specific business objectives of the users in other departments.
The objective is to change the perception of IT from a bunch of blue-jeans-wearing introverts to organized professionals—sharp-looking individuals able to support the most critical aspects of the business. The vice president of information systems and chief information officer are responsible for creating a corporate culture that recognizes the valuable contributions of a diligent staff.
People strive for recognition. Nobody wants to take a thankless job, especially one that may have long hours. IT governance deals with executives recognizing their responsibility to take control. IT leadership, on the other hand, is focused on only two objectives:
Objective 1: Define IT's mission by using small, simple words, and then set out plans to accomplish it.
Objective 2: Provide the detailed directions and support necessary for your people to succeed.
Without good management, the nifty technical tools are useless. After leadership is in place and operating, the next step is moving to designing the service delivery operation. The majority of this chapter is dedicated to operational measures. Let's begin with a quick reference check of external versus internal measures:
- External measures are the customer viewpoint.
Consider what the customer sees in regard to system availability, perception of the help desk, attitudes of the IT staff, response time, and backlog. All of these factors compose customer satisfaction. The user just wants it to work by calculating something or automating a business task.
- Internal measures are of interest to systems people.
The good people in IT will gauge the impact of availability, disk storage capacity, service requests, and all the little technical details about how it will help or hurt their users get the job done. Some IT staff members may be overly concerned with technology itself. That could be a detrimental situation. Technology is not intended as a safe haven for hiding from the hazards of interacting with other people or becoming involved in the challenges and worries of running a business. Internal measures worthy of IT's interest are the details that help or hurt the user in the performance of business duties.
Tip
Auditors can recognize good IT people by their speech patterns. Questions and statements will start with a specific mention of the user they regard as their customer and friend. This type of IT person is genuinely trying to help. Good people like this can be hard for employers to find. The auditor should take care to be respectful and supportive of this type of individual. Without question, the auditor should never make any sarcastic or diminutive comments because the result may be deemed an unforgivable insult.
IT provides a service to business users. Technology is so pervasive that no organization can exist without computers and telephones. IT service represents a commitment to manage technology as efficiently and effectively as possible within the organization. As business needs change, IT services should adapt accordingly. This constant adaptation can be a significant challenge. There's always the possibility of a gap occurring between the IT services delivered and user expectations.
In previous chapters, we discussed the requirement for IT services to be aligned with business objectives. Many of the topics we discussed are practically transparent to business users. IT service delivery is different. In this chapter, we discuss the daily activities necessary to support information technology.
Let's begin with a basic review of the functions in IT operations:
- Management of the IT department
The Information Technology department contains managers and staff workers focused on system availability, system integrity, and data confidentiality.
- Systems life cycle
All IT systems are to be maintained in a systems life cycle by using the concepts of the System Development Life Cycle (SDLC) and Capability Maturity Model (CMM).
- IT policies
Executive management and IT management are responsible for developing and issuing policies that support agreed-upon information technology objectives. Examples include a corporate acceptable use policy (AUP), antivirus protection policy, and the designation of information technology as the official custodian for corporate data.
- IT standards
Operating standards are developed by managers and approved by executive management. One such standard is the separation of duties. Other examples include the hours of system availability and system certification prior to production use.
- IT procedures
Operating procedures are developed by staff workers with the assistance of their manager. Operating procedures include the handling of software licenses and escalation procedures for user-reported trouble tickets.
- IT job descriptions and responsibilities
To support the operating procedures, the IT department must have job descriptions that reflect the current requirements and responsibilities for each position. Out-of-date or inaccurate job descriptions indicate that nobody is actually responsible for completing the work. It's a control failure because nobody has formal responsibility, formal authorization, or formal authority.
- IT risk management process
Risk management is required in all areas of an organization. The IT department is subject to a high level of inherent risk. Failures that occur in information technology have wide-reaching impact. The IT department is required to exercise risk mitigation on a daily basis. The process of change control is one technique used to help mitigate risk.
- IT asset management
Every Information Technology department maintains control over numerous capital assets, including data, software licenses, computing hardware, networking equipment, and facility space. We view data as a capital asset because of the capital investment necessary to create and maintain current data. Creating a customer list requires substantial investment of capital through marketing campaigns. A list of customers and hot prospects can easily be valued at five to ten times annual gross sales. The organization's total investment in technology, inclusive of all departments, is usually in excess of 4.5 percent of annual gross sales. This makes IT the second-largest custodian of capital assets, following facilities.
- IT service to the user
Information technology exists to support business users. The number one representation of value is IT user satisfaction. Attaining high user satisfaction results from a significant effort in back-office systems coupled with a prompt, helpful, and friendly help desk. The typical business user is interested only in how IT solves their individual problem. Customer satisfaction is earned by individual problem-by-problem solutions.
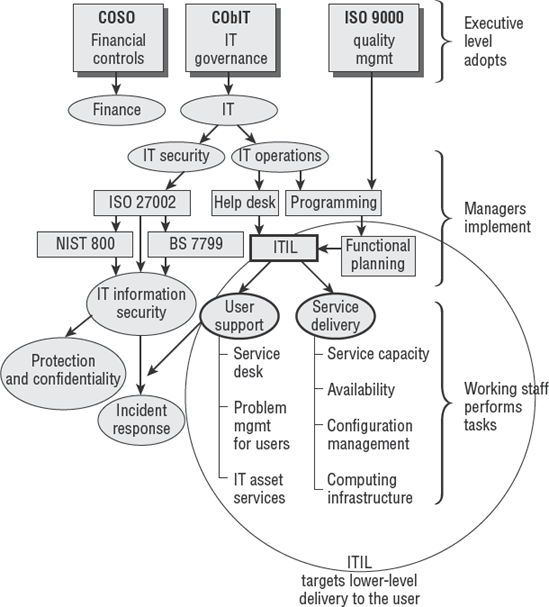
Now let's look at a framework of compliance that is not a regulation but does represent the best practices in the management of IT services.
The number of IT models and frameworks can be confusing. A well-managed organization will implement multiple frameworks including CObIT for governance, CMM for maturity, SDLC for life cycle, ISO standards, and some type of standard for running their help desk. In reality, each framework or standard is designed as a specific tool for different challenges faced in the overall business. Each has its own audience, which must ultimately function as one team.
The Information Technology Infrastructure Library (ITIL) is a collection of management best practices to guide the delivery of information technology services. ITIL provides a comprehensive and integrated set of service management processes targeted at what it takes to run a successful help desk. The goal of ITIL is to control the delivery of services that will be high quality while remaining cost-effective. Each of the service management processes is technology neutral, scalable, and comprehensive.
ITIL's intended audience is as follows:
IT service providers
IT directors
Managers
CIOs
Adopting ITIL's guidance could provide such benefits as reduced costs, improved IT services through the use of published best practices, higher customer satisfaction from a more professional approach to service delivery, less wasted effort by following a standard, and improved management of third-party services. ITIL is designed to complement the other IT frameworks, not to replace them. The help desk is usually the front line for the user to report problems; therefore, ITIL has an interface to ISO 27002:2007 information security services. We can use ITIL as one of the triggers for incident response outside of the help desk.
Eleven popular processes are associated with ITIL core functions. These functions and associated processes are as follows:
- Service support
Service desk, incident management, problem management
Configuration management, change management, release management
Interface to connect with ISO 27002 Information Security Management System (ISMS)
- Service delivery
Service-level management
Capacity management
IT service continuity management
Availability management
Financial management for IT services
- Functional planning and management
Implementation service management, infrastructure management
Application management, software asset management
Business perspective on delivering better IT services to the business user
Several of these points may appear to be overlapping. However, ITIL is complementary, not competing. IT needs to function as a cohesive team rather than as separate groups of people based on individual function. ITIL's framework helps everyone become involved, whether junior or senior, help desk operator or tenured administrator. Implementing this set of practices helps an organization focus their effort to deliver better customer service to people working in the business unit. Figure 6.1 shows the overview of ITIL.
The goal of operations management is to sustain the business needs of their daily user. Strategy is defined by executive management, technical response is created by middle management, and actual hands-on work is performed by operations managers with their support staff. The work performed should be in direct support of the higher-level business objectives.
As a CISA, you should remain observant of the difference between personnel who are busy and those who are effective. The volume of work performed is not a single measure of success. IT personnel must be focused on specific business objectives and have the necessary skills to be effective.
During any dispute over control, it can be challenging to determine who is actually in charge. The client's organizational chart can render a great deal of valuable information. The chart indicates who is in charge at each level, who each person reports to, and what the basic functions are for each job. It's not uncommon to walk into an organization and find that the organization does not have a current copy of their own organizational chart.
Note
You should recognize that the lack of a current organizational chart is a concern. All positions must have matching job descriptions that are accurate and reflect current responsibilities. Anything more than a small discrepancy in either of these documents indicates a lack of proper internal control. We included a sample organizational chart in Chapter 1, "Secrets of a Successful IS Auditor."
Let's take a quick look at several of the more common IT positions that should be of interest to you. Each of these roles has a unique degree of authority and influence in IT operations:
- IT director
The IT director has the day-to-day responsibility of managing IS/IT managers and executing the executives' plan. He or she is an upper-level manager with the authority to make decisions for their group. IT operations managers receive orders directly from the IT director. The IT director role is similar to the role of a movie director.
- IT operations managers
IT operations managers direct an IT staff working in software development, on the help desk, in server and network administration, and in information security. These managers are the first line of authority for the users. Each manager is responsible for the creation of effective procedures for their work area. IT operations managers are responsible for handling or delegating any issues that arise.
- Systems architect
This individual reviews the data compiled from the systems analyst and determines the preferred design for new systems. A systems architect's role is to create the overall system layout, whereas the systems analyst works with the end user and creates the ideas of what the business users require to fulfill their job or to align IT to their ultimate objectives. The true objective is to create a system that facilitates the generation of revenue for the organization.
- Information security manager (ISM)
The information security manager (ISM) should be an individual with training—such as a Certified Information Systems Security Professional (CISSP) from the International Information Systems Security Certification Consortium, an ISACA Certified Information Security Manager (CISM), or someone with an equivalent credential. The ISM specifies security standards to be implemented for all computer systems. The ISM reviews procedures for compliance to security policies. Security management requires special software and tools to perform effective tests and reviews. The ISM specifies control settings to be implemented by the server and network administrators. An ISM should be a very busy person working on security monitoring, security policy compliance, individual system security certification, and systems accreditation. The information security manager is supported by information system security analysts.
It is important to ensure that the ISM function is fulfilled by using a balanced set of security metrics such as NIST 800-53. The auditor likes to see that the organization is paying full attention to internal security controls (instead of management just saying yes and then turning a blind eye toward the implementation). The ISM function is impossible without full management support.
- Information systems security analyst (ISSA)
The information security manager leads a group of security professionals known as information system security professionals. This group may be large or small, while always in proportion to the size of the organization and its mission requirements. Security analysts work directly with the business users, IT administrators, and the help desk to improve their security posture. This may include investigating security requirements, conducting awareness training, or helping to test security settings. Security analysts work with every department and participate in key positions on the incident response team.
- Change control manager
This position is a quality assurance requirement. In small organizations, an individual may fill this role. Larger organizations may use a committee of managers to fill this function. The change control manager ensures that the staff is following proper procedures, controls, and approved plans.
- Applications programmer
Applications programmers write computer programs to solve problems for users. Their role is to create an automated solution for the business end-user. The applications programmer is supported by the systems analyst.
- Systems programmer
The systems programmer writes programs to change the behavior of the operating system or its design. Do not confuse this position with an enhanced operator. An enhanced operator selects settings, whereas a programmer writes software functions from scratch. The systems programmer role varies depending on the environment.
In a Microsoft Windows environment, the systems programmer is Microsoft Corporation unless the client hired a programmer to rewrite functions in the Microsoft operating system. Does the client have programmers to rewrite the internal functions of the XP or Vista operating systems? If not, the client organization is no more than a user, and their systems administrator is a glorified operator of enhanced authority who simply selects predefined options from menus.
In the Unix and mainframe environments, the systems programmer rewrites or modifies the operating system kernel, support utilities, and Job Control Language (JCL). In a nutshell, the systems programmer focuses on modifying or improving the operating system internal functions.
- Network administrator
This person is the network router technician who handles data communication between devices on the network. The duties include supporting system administrators, managing Internet Protocol (IP) addresses, and monitoring networked devices (usually via Simple Network Management Protocol, or SNMP). The network administrator may be delegated the daily maintenance responsibility of network security devices such as intrusion detection and prevention systems, vulnerability scanners, firewalls, and gateways. A network administrator's primary job is to keep data communications working across the network.
- Server administrator
The server administrator maintains the server hardware and software settings. In a Microsoft environment, the server administrator is an enhanced operator whose role is to select appropriate settings from a GUI interface or predefined menu. The Unix and mainframe administrator counterparts are usually skilled as script programmers or operating system programmers. The Unix or mainframe administrators frequently write their own support utilities or customize the program code of existing utilities to enhance system integration.
- Database administrator
This is the custodian of data, who maintains the database systems. This is usually a role fulfilled by a person with prior experience as senior system administrator or systems programmer.
- Computer operator
This is a junior server technician who assists the system administrator and database administrator. The computer operator functions include starting and stopping software, changing job prioritization, and identifying possible problems during normal processing. A computer operator acts as the eyes, ears, and hands under the direction of the administrator. Computer operators provide clerical assistance on issues of error and log reporting. Operators escalate problems to the attention of more-senior personnel.
- Systems analyst
A systems analyst works with the business end-user to develop requirements. After the requirements are developed, the systems analyst works with the user to define screen layouts and report layouts. The systems analyst then communicates this information to the systems programmer. The systems analyst provides support for business methods to be implemented in technology.
- Data entry staff
Data could be entered by a professional data entry staff for a large volume of data, or it could be entered by the end user. These days, with web forms and the online atmosphere of IT, data entry by the end user is quite common. If that has been the decision, we of course like to see compensating controls to ensure the integrity of that input.
- Media librarian
A media librarian is a critical role even though it's a junior role. We will refer to this IT position by the short name of librarian. The librarian is responsible for keeping track of all media, no matter what type (tape, cartridge, CD, or even a Zip drive or a portable USB memory stick). The librarian is responsible for data storage and its tracking history, including creation date, current storage location, last time accessed, and what data is claimed to be contained on the media. The data may be referred to as a data set.
Backup media is sent to an offsite storage company for safe offsite storage. The librarian is required to track when the media was sent and when it arrived at the destination. Every tape and label must be accounted for at all times. Loss of backup media (tape) may constitute a breach of law or require mandatory public disclosure of loss, depending on contents.
The librarian assists with regular self-audits to verify that the property is still in safe storage with the offsite vendor. Media is recalled from storage by the librarian. Media containing old data is recycled by the librarian in accordance with the organization's reuse policy. The librarian is also responsible for proper disposal and destruction of old media.
- Help desk
Every IS organization will have a help desk of some type to support computer hardware or particular software applications. This is where users initially call for first-level support; the caller is asking for IT assistance. The help desk person handles the most basic needs and then escalates problems to the appropriate personnel. The help desk follows the policies and procedures that are specified by management.
Staff on the help desk usually hold a junior role. This support role provides an interface with IT customers. Each help desk person should be trained to recognize problems that need to be referred to more-senior IT staff. The customer interface serves the business person—the end user. The business end-user's job is to make money, and the help desk is intended to help the business user work more effectively. The help desk must keep performance metrics for all requests, including metrics of escalation and problem delegation.
Each of the roles we discussed has a particular function that is necessary to sustain normal operations. It is important that each transaction is properly authorized before it is executed. A physical or logical separation of duties is necessary to provide proper authorization. With separation of duties, you look at who holds custody of the assets and what compensating controls are present.
Figure 6.2 illustrates separation of duties and authorization in the IT department.
The purpose of separation of duties is to segregate authorization so that no individual can execute an action or have direct access to assets by bypassing control. Authorization is the most important element to separate from each job role. Every position should require authorization from another person before changes are made or before sensitive transactions are executed. The separation of duties is a control mechanism that separates the person doing the job from the person who renders authorization. The goal is to prevent stupid mistakes or possibly fraudulent activity.
The performance of information technology is ultimately interpreted by three fundamental business-performance indicators: IT budget, user satisfaction, and technical indicators. Technical indicators could include a combination of automated and manual metrics. You can gain a reasonable understanding of IT performance by reviewing their chosen indicators and corresponding scores.
Using metrics to measure IT service is required. These service metrics are tools designed to demonstrate the effectiveness of IT operations. Many regulations require the use of IT metrics in general. Each metric should provide a quantifiable measurement corresponding to the organization's internal controls. The IT metrics aid in the evaluation of an organization's performance.
Metrics must be developed for each organization. Each metric should be developed by using the following four principles:
Data for calculating metrics must be readily obtainable.
Each process under consideration needs to be repeating and measurable. It must represent a value to the business.
Each metric must demonstrate a level of performance by using quantifiable information in the form of a numeric total, average, or percentage.
A metric can be derived by automated or manual means.
The success of IT metrics depends on finding useful measurements that are of value to the organization's stakeholders. Data can be obtained from automated system reports. Data can also be collected manually through self-assessment tools, questionnaires, and user surveys. The metrics may change as new processes and projects are developed in the organization. It is important that each metric selected is realistic and can be used for measuring performance improvement.
The goal of every metric is to establish a performance target. Performance targets are combined to establish a baseline. Four basic types of metrics can be used to measure IT performance:
- Implementation metric
An implementation metric provides a percentage or comparative count for the quantity of conforming installations—for example, the number of systems with antivirus software installed, or the number of users who have attended IT security orientation training.
- Efficiency metric
The efficiency metric measures the timeliness of service delivery. Examples include resolution time from the help desk or elapsed time for response to an incident.
- Effectiveness metric
This metric evaluates the quantifiable effectiveness of IT service activities. An example is the number of user-reported trouble tickets opened and closed by the help desk with a resolution that was satisfactory to the user. Another example is the number of systems currently maintained in a life cycle program by IT staff.
- Impact metric
The impact metric provides a quantitative measure of incidents by their type—for example, the number of help desk tickets opened and closed for the month. Another example is the number of systems compromised by a virus attack. This metric can be presented as a numeric value, a percentage of the total population, or a dollar value.
Figure 6.3 illustrates the nature of the four basic types of measurement metrics.
The IT department and each major stakeholder need to agree on which metrics to use. It is important to limit the number of metrics to a sustainable quantity. It is recommended that no more than five to ten metrics be collected for each major stakeholder. The metrics are not free; an organization must allocate resources to gather and create meaningful metrics. The data collection and subsequent reporting process must be standardized.
Every metric developed will contain nine elements of information. ISACA does not expect you to recite each of these points in detail. The objective is to understand how a valid metric is created and managed. Let's look at the nine elements:
- Purpose
Describe the overall functional value of this metric. Is this metric for customer measurement, compliance with a regulatory requirement, or internal performance?
- Performance goal
State the desired results of implementation, or the question to be answered by this metric. For example, the goal may be orientation training for new hires or separation of duties on IT servers.
- Performance objective
State the actions that are required to obtain the performance goal. This may be posed as one or multiple questions. For example, are participant-training materials in place for the orientation of new hires? What is the training schedule?
- Type of measurement
Define the quantitative measurement to be used. The measurement is expressed as a percentage, average, number, or frequency—for example, the numeric count and percentage based on attendance.
- Data source
Indicate where the data was captured from. List the specific tools, databases, and personnel that provided the data used in this metric—for example, a Human Resources (HR) employee count, and class attendance records signed upon entry and exit from training.
- Available evidence
List the sources of proof that can document the success or failure represented by this particular metric—for example, an HR roster, invitation list, attendance sheet, or attendee exit examination.
- Frequency
State the time period used for data collection. Is this information based on hours, days, weeks, months, or years? For example, data collection may be reported monthly.
- Formula used
State the formula used in the calculation. One example is the number of incidents divided by the total number of systems. Another example is the formula (ratio) = (attendees ÷ total number of employees).
- Indicators
Explain the goal of this metric and how it should be interpreted by the reader. For example, if the target for a metric on system certification is 100 percent, a low percentage would indicate a high risk exposure. A higher percentage would indicate a risk reduction by educating users about basic IS security safeguards and high-level notification procedures.
The purpose of a help desk is to provide ad hoc assistance to business users. The help desk is the point of origination for new support requests. A help desk may support specific applications or general computer needs. In service delivery, the objective is to provide high-quality and prompt service to the user during the appropriate work hours.
People may call in for help with a variety of computing problems. It is the help desk's responsibility to escalate trouble tickets in a timely manner. Some trouble tickets might be escalated to the system administrator or application support programmer. Other trouble tickets might be escalated to a third party. The help desk provides a single point of contact for the user. Each trouble ticket should be tracked by the help desk until closed or resolved to the user's satisfaction.
The help desk tracks call metrics so that trends can be analyzed. As an IS auditor, you should understand the help desk function. It would be beneficial to conduct a review of the staff on the help desk to determine their level of competency. An audit trail should exist, documenting the process for logging and tracking service requests. You should evaluate the level of documentation for help desk activities and troubleshooting procedures.
A service-level agreement (SLA) represents an understanding between users and the service provider. The purpose of this agreement is to define performance criteria by specifying the quantity and quality of service desired by the customer.
Let's look at some of the components of the service-level agreement:
- System availability
What are the scheduled hours of system uptime and system downtime for maintenance? How is the processing workload scheduled to prevent conflict? What is the nature and extent of continuity plans?
- Service definition
What are the specific services expected by the user?
- Personnel qualifications
What are the qualifications of the IT support personnel? Will these same personnel be supporting business users? Will the support personnel be trained in the unique requirements of the business?
- Security requirements
What access controls will be implemented? How will physical and logical access controls be implemented? How will the program libraries be protected? How will the data be protected? Will separation of duties be fully implemented?
- Data integrity
What are the data storage and retention requirements? What is the method and frequency of data backup? How will data be protected during transportation?
- SLA performance reporting
Are all metrics reported against a quantifiable service level? What metrics will be reported? How will the content and format of the metrics be reported? Do the report metrics fulfill actual business objectives? What is the frequency of reporting?
- Right to audit
What level of cooperation and access will a customer have to audit the service provider? Define any schedule or access restrictions in regard to auditing. This was discussed in Chapter 3, "IT Governance."
- SLA change procedures
What is the process for making changes to the service? What is the cancellation process, and how much would it cost?
- Cost of service
What is the cost of the service offered? How are the charges calculated? How will the service be billed? Are the charges realistic for the level of service provided?
This list is provided as an overview of the components in a service-level agreement. Every service-level agreement should be a formal contract between the vendor and customer. This contract should include the effective period of coverage and renewal options. It is understood that internal service-level agreements will take the form of an agreement of mutual understanding. Either type of agreement must be formally approved by appropriate management, representing both the provider's interests and the user's interests.
The subject of outsourcing can spark an emotional response. Selecting whether to outsource functions or keep them in-house is a decision that should be based on the facts in evidence. It is a common practice for individuals to outsource automobile repair, housecleaning, and lawn maintenance chores. A person purchasing a new home may choose to outsource interior decorating to a professional decorator. Take a look at the reasons why outsourcing may be considered:
The scope of needs is unknown. Therefore, we need the help of someone more experienced who should know what to do.
The current staff is not generating the expected results.
Management decided it would be better to let someone else do it.
The scope and requirements are extremely well defined—for example, CMM level 5. Now the objective is to reduce operating costs while delivering this well-defined level of service.
The auditor may want to investigate the maturity of the outsourced process, metrics, and user expectations. It is interesting how many times the decision to outsource is later reversed after the true scope is known, the actual requirements are identified, and the shock of the outsourcer's total invoice price is realized. Some processes may be outsourced with the long-term intention of remaining external.
At CertTest, we write two editions of our books, a special expanded edition for our class students plus a general version for Sybex. Both are commercially printed, professionally bound, and shipped by an outsource vendor. Writing the books is a core process we want to do. Printing and binding books internally would cost more money and therefore is not something to undertake. Executives will typically choose to outsource low-profit tasks in order to dedicate all available resources to processes with a high rate of return.
Blindly outsourcing is fraught with hazards. Every outsource agreement requires a contract as evidence of the details agreed upon by both parties. Let's take a moment to look at the minimum contents of a business contract according to ISACA:
- Prior to negotiations
Identification of the parties to the contract, usually by company name and address
Legal name of entity providing service, and legal name of recipient entity (DBA, Inc., LLP, LLC)
Continuity of service assurances, or lack thereof
Delivery location and legal jurisdiction
- Specific details
General description of services provided
Duration of the contract with applicable dates
Description of specific deliverables
Cost of service changes (fixed price, cost plus, or time and materials)
- Performance during execution
Criteria of acceptance or rejection of deliverables
Anticipated service-level agreement with both qualitative and quantitative measurement
Security and confidentiality requirements (access levels, nondisclosure, and so forth)
Frequency of invoicing and payment for service
Roles of both parties during the contract, with specific points of contact
Reporting process, report content, distribution, and frequency
Right to audit
Dissolution process
Penalties for nonperformance
- Changes and resolution of issues
Cost of changes in service (fixed price, cost plus, or time and materials)
Modification process to change terms, service, or price
Problem resolution process
Recourse
All contracts evidence a formal commitment to purchase and to pay for services or goods. The courts usually regard a contract as the sum total of the agreement between the parties. As a layperson, this means to me that services not specified in the contract should not be expected to occur. If the vendor made a special offer or promise, it should be prominently mentioned in the contract. IT contracts should always be negotiated with the assistance of a professional purchasing manager and legal counsel. A smart auditor allows the legal work to be performed by qualified lawyers. As a rule of thumb, the best lawyer keeps you out of court by preventing the disputes that lead to a lawsuit.
Your job as a CISA is to evaluate an organization's internal controls. Internal controls are required during the normal processing at every computer terminal or computer workstation. Without proper controls, a minor error could become a major outage.
We have discussed a series of controls in this Study Guide. In Chapter 7, "Information Asset Protection," we discuss specific security controls for protecting information assets. Let's recap the controls that apply to IT service delivery:
Technology systems require continuous monitoring to uncover operational inconsistencies, errors, and processing failures. Managing a system would be impossible if you did not know its present condition.
Let's discuss a few types of monitoring that should be implemented by IT:
- Hardware
Electronic hardware should be monitored for workload utilization, errors, and availability. Utilization and errors could indicate an upcoming condition that will affect system availability. The goal is for every system to be usable. The system administrator should always be aware of hardware conditions observed, problems reported, and alerts recorded in system logs.
- Software
Most computer software provides event logging. Event logs and audit logs should be enabled and configured to capture information of interest—for example, error conditions, successful logins, unsuccessful login attempts, and configuration changes.
- Centralized system logging (Syslog)
It is a recommended practice for centralized system logging to be installed. This process forwards a copy of each system log to a centralized console for review. The configuration process is relatively simple. A log-reading tool is necessary to convert raw data into meaningful information. System logs contain a lot of duplicate entries. Without a log-reading tool, understanding the priorities would be difficult because of the volume of log entries.
- Network device monitoring
Servers and routers on the network can be managed by using the SNMP discussed in Chapter 4, "Networking Technology." One of the most common SNMP platforms is HP OpenView, although less-expensive management platforms such as OpenNMS are also available. Network-management software provides insight into the overall condition of the networked environment. System alarms are generated before a user calls in to complain. The network-management system is useful only if someone is available to view the alert.
- Uptime-downtime reporting
SNMP provides an excellent method of tracking uptime and downtime. Some people get very defensive about how this subject is reported. Let's clarify the point for everyone's benefit. There are only two categories, although additional descriptions may exist:
- Uptime
The system is available for the user to process whatever they desire or need.
- Downtime
The system is unavailable for any reason. This may be due to failure or a scheduled outage for service. The word outage indicates that the system is effectively down. Down means down. No matter what the user does, the system will not be available. If this is distasteful, the downtime statistics can be used to justify additional resources. Management may choose to accept the downtime in spite of IT's desire to have 99.999 percent uptime. IT is a humble servant to the business, not the other way around.
Tip
Downtime means the system is unavailable for any reason—including failure, maintenance, or while running the backup/restore operations. IT management may refer to downtime as planned maintenance or unplanned outage. Just consider this from the user's perspective. It's counted as downtime if the user is unable to use the system for any reason.
Computer logs are an excellent source of information. The only drawback is that without the right tools, computer log files are difficult to read. Assuming you have the right tools, the next question is whether anyone is actually reading the logs. Software logs offer valuable insight into events occurring within systems and throughout the network. The syslog feature we discussed in Chapter 4 is one of the most powerful tools an organization could use.
Effective log management is based on six easy requirements:
Enable logging for security-related events.
Enable logging in application software.
Configure syslog to export logs from the device to be watched.
Configure a syslog server to receive the log files; this does not require any server license.
Read the log files. A simple log-reading utility is used to glean duplicate data.
The devices on the network continually generate log entries on an ongoing basis. Log files present valuable information for telling a story of what is actually occurring across the network. The benefit is obtained by reading the files as part of a regular monitoring procedure. Log files need to be continuously backed up and archived. The information discovered in the log file may be the best trigger for incident response.
Access to computing resources needs to be controlled. It is imperative that the concept of least privilege be implemented with regard to user access of IT computing resources. No individual should be able to log in to the system by using a level of authority higher than their job requires. There are three types of login accounts you need to consider: user login, privileged administrator login, and maintenance login.
New user login IDs are created after Human Resources notifies the IT department of an employee being hired. A similar process should exist when a contractor begins work. Some type of authorization mechanism must exist to control the creation of new accounts.
Each system user is required to have a unique login ID and password. The user login accounts should be given the minimum access rights necessary to perform their job (least privilege). Biometrics or electronic tokens may be implemented on systems with higher levels of security. Every user login should contain the following control attributes:
A warning banner is displayed prior to login to inform the user that inappropriate access may result in prosecution.
A minimum password length of six to eight characters is required. The password should be a mix of numbers and letters. The password should not be a printed word found in any dictionary, regardless of language. Automated password-cracking tools start the attack by trying common words and names obtained from dictionaries. (We discuss the details of this in Chapter 7.)
Unique passwords are forced. The computer system will not allow a password to be reused.
Passwords are required to be changed at a frequency of 30 to 60 days, depending on the organization's policy.
A user login ID is suspended after three to five unsuccessful login attempts.
Unauthorized attempts to access the system are recorded in audit logs.
The date and time of the last successful login will be displayed to the user upon login. This is to inform the user of when their login ID was last used.
A user login account is suspended or disabled when a notice is received from HR that a particular user is no longer employed by the organization. The disabled account needs to undergo administrative review prior to deletion of the user ID. This review seeks to discover whether the user engaged in any attempts of unauthorized access. If not, the user's data files are archived and forwarded to the appropriate department manager.
Tip
Just setting account lockout at three to five failed attempts is not good enough to thwart an attacker. Most hackers will try only one or two login attempts and then wait until later. This type of under-the-radar attack is common. I bet it's already occurring somewhere on your systems. Nobody would be wise to the attack unless they are monitoring every failed login attempt. This type of attack may occur for months, until the hacker gets a successful login.
Logical access to system administration functions needs to be protected by a separation of duties. Privileged login accounts should not be used for any function other than administration and maintenance. System administrators should possess two separate login accounts. The first login account should be used exclusively for system administration duties. The second login account should have no privileges other than the basic rights of the common user.
The system administrator should perform office administration functions while logged in as a regular user. This reduces the potential impact of errors. In addition, it improves security by reducing the time duration of privileged access. If the administrator walks down the hall to the restroom, the risk of another individual gaining physical access to the computer has been reduced. The logical separation of duties can be verified by reading system logs.
All privileged login accounts contain control attributes of a normal user plus the following additional controls:
Passwords must be changed every 30 days.
Retired passwords must be written down and stored with backup tapes. Those passwords may be necessary again when older files are restored. Both the tapes and the password lists shall be stored in a fireproof-rated media safe, and also in a secure controlled environment designed for offsite media storage.
The current passwords should be written down and stored in a safe in case something unforeseen happens to the system administrator. Current passwords will be required for disaster recovery. A second copy of the passwords should be kept in a safe offsite location separate from the data files.
Tip
You may use CertTest's free password generator to help create unique passwords. We grant you limited permission, for nonhostile purposes, to link to our web page. Auditors should encourage the use of stronger passwords. Just visit http://www.certtest.com/passgen.
All computer systems have default user accounts for system setup and maintenance. The login IDs of these maintenance accounts are often well known and commercially published. Hackers love to use maintenance accounts that have been left open by careless administrators. Default login accounts should be disabled in a production system. Any valid maintenance accounts should utilize nontypical login names with strong passwords or station restrictions. A station restriction allows login to occur only from a particular system, based on the machine's serial number or address.
Access to data files should be controlled to ensure that unauthorized access is effectively impossible. Data access can occur through a perimeter control, direct file access, and middleware. Middleware is software that handles data traveling from the user interface to its destination in the database. Each of these types of access requires special controls. It is naive to think that a perimeter control will be completely effective.
Four basic types of data protection controls are required:
- Standing data controls
Standing data refers to information contained in a file or database table. The information should possess controls commensurate with the data value or regulatory requirement. Standing data can be found in file cabinets, on disk drives, and on tape backups. Standing data may require additional controls such as storage in encrypted format within the database.
Note
A significant portion of credit-card-number theft on the Internet is due to unauthorized copying of standing data in shopping cart databases. The U.S. Fair and Accurate Credit Transactions Act of 2003 mandates increased security with truncation of account numbers on receipts and destruction of account numbers after the transaction is processed. The Payment Card Industry (PCI) has its own rules governing credit card data regardless of whether it's printed or electronic.
- System control parameters
Data files should be protected from system control parameters that would change the way the files are processed. System control parameters are used to customize the configuration settings and software applications. These settings can alter performance, logging, or file security. Improper implementation can lead to the loss of data, unauthorized access, or undetected errors.
- Logical access controls
All access to data files should be forced through authentication in a user rights management program (access control program). Direct access to data files through Open Database Connectivity (ODBC) should be prohibited unless controlled by a rights management program with user authentication. It is common for a user to request direct access to the database for the purpose of reading data from another program. This type of uncontrolled direct access should be discouraged.
- Transaction processing controls
All transactions involving data files should be controlled with authentication and validation checks. The data transformation procedure must be officially approved and managed as part of the system application life cycle. Transaction processing monitors (TP monitors) are frequently used to ensure that database activity does not overload the processing capacity of the available hardware.
System security and integrity is assured through the use of application processing controls. Logical access controls require the user to log in with a unique ID and password. The user can begin processing after a successful login. Each application should provide at least three internal processing controls: input, authorization, and output.
An input control ensures that only valid and authorized information is entered into a transaction. Input controls operate by using a combination of user authorization rights, edit checking, and data entry validation. Sequence checks are used to ensure that each transaction is processed only once. For an excellent analogy, consider how checks and ATM transactions are authorized at a bank.
Input authorization controls include the following:
Unique login and password
Signatures on source documents
Identification of client workstation or terminal
The purpose of processing controls is to ensure that the data and transactions are valid. Production software programs reside in the production program library. Access to the production program library should be restricted to read-only. There is no reason for the computer programmer or the user to have write access into a production program library.
Note
Allowing a programmer to have write access to a production program library would be a violation of change control. The computer operator will move authorized software from the development library to the production library when instructed and authorized by the change control manager.
Most data processing occurs by using a batch processing mode. The data batch may be small or large. The frequency of processing may be seconds or hours. Regardless of the method, it is necessary to ensure data integrity by using data validation and edit procedures. Without operational processing controls, the database would be no more effective than a garbage can.
Processing controls include the following:
- Batch totals
To compare input against actual processing.
- Total number of items
To verify that each item was processed.
- Transaction logs
- Run-to-run totals
To provide verification of the data values during the different stages of processing. This helps ensure the completeness of all transactions.
- Limit checks
To prevent processing of any amount in excess of the expected average. Overly large transactions will not be processed. For example, no employee should receive a paycheck for $50,000. That amount would obviously be excessive.
- Exception reporting
To identify errors. The exception may hold the batch and suspension until the errors are corrected, or reject individual transactions containing errors, or reject the entire batch of transactions.
- Job cost accounting
The operating cost of computer processing may be billed to a particular department, project, or application. It is important to observe the effectiveness of job cost accounting when it is used.
Data generated by the system should be protected to ensure confidentiality until it is delivered to the designated user. Output controls are just as important for paychecks as confidentiality is for business plans or HR records.
Let's review a few basic output controls:
- Report generation and distribution
Confidential reports should be output on a printer with restricted access. The report title should indicate that the report is confidential. Exception reports should always generate a page to indicate the exceptions that occurred, or a page to indicate that no exceptions occurred.
- Negotiable instruments
Checks, bonds, and stock certificates are frequently printed on computers. These items should be protected by a combination of logical and physical controls.
- Report retention
Certain types of reports may be required to be controlled under a document retention policy. This applies to records used for regulatory or legal compliance.
- Event logs
Processing logs and audit trails should be protected for integrity and confidentiality at all times. These logs need to be placed under record retention controls.
Computers are constantly attacked by malicious software. The attack may be in an email or file attachment. Viruses work by attaching themselves to the end of a file. Antivirus (AV) software will search for the signature (attributes) of known viruses. Without the latest AV updates, the system will be susceptible to attack by new viruses. It's not uncommon for AV updates to cause a conflict with other software on the user's computer. The IT help desk may direct users to download updates from the vendor's website or instruct the users to download updates only from an internal IT server.
Auditors should inquire how the user is to acquire AV updates. Is it directly from the vendor or from IT? The auditor would be interested to see whether the IT staff is actually testing updates on a computer similar to the user. If so, what is the delay interval between a vendor releasing AV updates and the time to install this update on all the user computers?
Every IS auditor needs to understand the concept of active code and how it affects system security. Active content is software that is readily available for download from the Internet. Downloading special drivers, templates, updates, and utilities is a useful function for many people. Anyone who has used FedEx Kinko's online print service would agree that their software utility makes it easy to get your print job formatted, printed, bound, and delivered without ever leaving your desk. The FedEx programmers did an excellent job of developing downloadable software that helps the user.
Web pages have evolved into multimedia portals capable of delivering live weather maps, streaming news reports, business intelligence, and online education for those without the resources to attend class. Active content provides a useful capability that cannot be ignored. Attackers can abuse the vulnerabilities of active content unless preventative, detective, and corrective controls are implemented:
IT executives should develop a policy regarding the use of active content (preventative).
Additional procedures need to be developed to help reduce the associated risk. These include making configuration settings, enabling virus detection, enabling intrusion detection on each system, and linking violations to an incident response mechanism (detective and corrective controls).
When surfing the Internet, the web pages we see are composed of special formatting codes along with embedded function tags. Hypertext Markup Language (HTML) handles the screen formatting. Special function tags perform other actions such as retrieving images, playing a multimedia video, playing music, or linking into another program. Programs such as Java and ActiveX extend the browser functionality.
MIME was originally designed to be used for electronic mail, although it has evolved for use by all types of multimedia. These extensions include content for the following:
Audio transmission.
Video images.
Embedding text, images, and other data into a file. This is how Portable Document Format (PDF) and email works.
Support for plug-in applications.
The magic of the Internet is powered by MIME. Benefits of using the Internet are so great that IT has to deal with the situation and be prepared to clean up any mess that occurs. The alternative is to disable Internet access. This strategy of no access may work if the mission data is beyond valuation. Otherwise, the replacement IT staff will be called upon to provide a more palatable solution.
It's easy to download new programs from the internet. Sometimes a web page will automatically download a program for the user to increase the functionality of the web page. This is referred to as Mobile software. It's also known as mobile code or applets. The two dominate leaders are Java and ActiveX. Let's explore the basic characteristics of each.
- Java
Java is one of those wonderful programs that runs inside the browser with special security to protect the user's computer. Java uses the Java Virtual Machine (JVM) program inside your browser to provide an elaborate level of security. This helps prevent Java programs from damaging your computer. Java permissions can be set to allow digitally signed applications to be run from websites you trust. Unsigned applications can be rejected for security. Three of the most common implementations of Java include:
Java is object oriented, which provides the delegation capability for applets and servlets to off-load work to another applet or servlet. Untrusted servlets can be executed in a secure JVM environment to protect users from undesirable behavior by the program. Java's security manager feature mediates all access to system resources. Java still poses a minor security issue because it does not prevent a program from creating a denial-of-service condition nor does it prevent the exportation of a user's identity.
- Active Server Pages (ASP)
Microsoft's operating system is written using Beginners All-purpose Symbolic Instruction Code (BASIC) with C++ and C# (C Sharp). This software language for beginners has evolved to include additional functions. The latest version is called Visual Basic and Visual Basic Scripting Edition (VBScript). Windows XP and Vista share the same programming language used in ASP. This programming commonality with the operating system is the root issue of security problems. Let's look at the security problems created when using Active server pages.
Visual Basic and VBScript create interactive web pages under the nickname ActiveX.
In theory, Microsoft's programming language was supposed to provide isolation boundaries to create a relatively secure environment. Implementation flaws and increased integration of the browser to the operating system have violated the barrier concept.
Well-written ASP programs of a malicious nature can subvert Microsoft security by executing commands throughout the entire Microsoft operating system.
ActiveX places no restrictions on what the programmer can do. ActiveX software is digitally signed by the author via a technology scheme called authenticode. The publisher certificate for authenticode requires the publisher to pledge that they will not knowingly distribute harmful code; it does not ensure that the program is well behaved. Poorly designed programs can still do damage. ActiveX and authenticode place responsibility for security upon the user. We can see a comparison of risks in Table 6.1.
The mobile code security risk can be managed by using one of four basic concepts. Each of these will be determined by the organization's mission, capability, and value of data. The business unit and IT need to agree on which of these basic choices will be used:
Disallow functionality (no benefit, no risk)
Allow functionality only from internal servers (lower risk)
Allow functionality from trusted external servers (moderate risk)
Let the user do whatever they want from any server (high risk)
Choices made can be supported by the addition of technical controls using automated filters, application settings, digital signatures, isolation tools, and software behavior controls. Administrative controls are required to provide security audit, version control, user awareness training, and incident handling.
Tip
As an IS auditor, you will be interested in how the decision was reached regarding the use of mobile code. Particular areas of interest include available evidence supporting or challenging the decision, how problems are detected, and the implementation of corrective controls.
Maintenance controls exist to ensure that hardware and software changes will have a minimum impact on processing schedules and system availability. All maintenance should be approved by the change control process before it occurs. It is not uncommon for an organization to issue blanket approval for small changes with low risk. Let's look at some of the issues that should be addressed prior to performing maintenance.
System programs and data should be backed up before maintenance occurs. The backup tapes (or media) should be read/write verified. Verifying a backup ensures that the data copy matches the original. The backup provides a second copy of current data if something goes horribly wrong.
Project management with a risk analysis should be performed prior to starting maintenance. Most maintenance is a mini project. As the scope of the maintenance increases, so should the project planning. Each project plan should include a provision for workarounds and fallback procedures. A fallback procedure will be executed if the change fails to deliver the desired result.
We discussed change management in Chapter 3 and Chapter 5, "Life Cycle Management." In terms of IT service delivery, change management concerns relate to hardware and software maintenance. The introduction of any change constitutes a risk to system integrity and availability. However, change is inevitable.
A flowchart of the change management process appears in Figure 6.4.
Note
ISACA wants every CISA to be aware of four concepts that apply to change management in IT service delivery.
The configuration of production systems must be controlled. The method of configuration control is similar to the one we discussed in Chapter 5 concerning software development. Changes should not be made to a production system unless the change has undergone formal testing under the control of the change management process.
No change should occur without management authorization, and any changes must remain within the authorized scope. It is unfortunate that some technicians will attempt to implement additional changes at the first opportunity. These changes have consistently proven to be the source of a related failure. The objective of change authorization is to ensure that nobody bypasses the life cycle management process.
At times, emergency changes are necessary to minimize system interruption. A senior individual should be consulted for review and approval prior to implementing an emergency change. If the emergency change works, it may remain in production. If it fails, the change should be withdrawn (backed out) immediately. After an emergency change is implemented, the standard change control process will be invoked after the fact. The change should undergo formal testing and analysis to determine whether it may have created additional problems.
The best way to prevent outages is through diligent testing. A separate test environment will save money by preventing outages that would otherwise occur. The price of nonconformance (failure) provides an excellent financial justification. Use the price of downtime to demonstrate the need (price of nonconformance). It will be more difficult if the auditee has misrepresented their actual downtime metrics. Remember system time is either counted as "up" for the user to operate at will, or it's counted as "down."
Administrative management controls are used to provide written policy and procedure guidance for people. These management controls help overcome shortfalls from the limited implementation of technical controls. You need to be aware of the common administrative controls used in IT service delivery. We will begin with software licensing.
Software licenses are an asset of the corporation and need to be controlled and managed. All computer systems are required to have a valid, lawfully obtained software license for the operating system along with a license for each application and each utility installed. A violation of software copyright laws carries substantial penalties and the possibility of public embarrassment. You should observe the client's attitude toward software licenses. Most organizations purchase licenses by a per user count. There should be evidence to indicate that the licenses are managed for copyright compliance.
Technology assets should be inventoried and tracked. Proper ownership labels or property tags should be in use. Tagging and labeling are preventative controls. The audit of inventory tags is a detective control. Media containing software and data should be managed under a physical asset program. This is required under several regulations, including Sarbanes-Oxley, Gramm-Leach-Bliley, HIPAA, Basel I & II, and the EU data protection act.
All media should be properly labeled. The media librarian is responsible for tracking the location of media. Evidence should exist to indicate that assets and media are properly controlled.
Note
Canadian-based Absolute Software sells a special tracking service designed to recover stolen laptops. Their special utility installs on the laptop as a hidden software program. The laptop can be located by its unique beacon while on the Internet. Absolute's recovery desk notifies law enforcement and automatically provides all the paperwork necessary for search warrants. Absolute can remotely wipe the hard disk clean if necessary to prevent disclosure of the laptop data files. The company is run by former law enforcement officers and advertises a successful history of recovering three out of four laptops (75 percent).
A proper asset-disposal process contains procedures to ensure that data is purged (erased) from all equipment prior to disposal so that the data can never be recovered. Physical assets should be formally discharged from inventory. These assets can be destroyed, sold, or donated depending on the organization's desire. This is the seventh phase of the SDLC life cycle, as covered in Chapter 5.
All devices leaving the controlled environment must be purged of data by using disk-wiping utilities or degaussing methods. Disk reformatting is not an effective method because it will not destroy raw data that is accessible via special utilities that bypass the operating system. As an IS auditor, you need to determine whether the organization is following an acceptable asset-disposal process.
Proper training of system users can reduce the occurrence of problems. User training may include new hire orientation, security awareness training, software application training, and refresher programs for existing users. Well-educated users can provide valuable assistance to IT objectives. The educated user will understand when to bring potential concerns to the attention of IT management.
The procedures used in the operation of information technology systems should reflect the actual work performed. The purpose of a procedure is to ensure consistency with the desired result. Actual work that does not match the procedure would indicate a management control failure.
Compensating controls are used to reduce the impact of an error or omission. As you will recall from Chapter 2, "Audit Process," controls may be implemented by using a physical method (barrier), technical method (logical), or administrative method (policy and procedure). Compensating controls are used whenever there is a lack of segregation of duties. Examples of compensating controls include the following:
- Job rotation
Rotating individuals between job functions reduces the potential of questionable activities. A person may be asked to take vacation in one- or two-week intervals. During that time, another person performs the job while looking to discover whether anything is out of the ordinary. This is a type of detective control. A collateral benefit is having more than one trained person capable of performing the function.
- Audit
Auditing is an essential component of internal control. It is imperative that audit logs are functional and well preserved. The audits may be internal self-assessments or formal independent audits.
- Reconciliation
Reconciliation is a type of audit in which records are compared to ensure that a balance exists. Reconciliation is used in financial reporting, project management, scope verification, computer processing batch verification, and other instances where an answer should be verified. Proper reconciliation increases the level of confidence.
- Exception report
On occasion, an error or exception will exist in computer processing and audit logs. All jobs processed should print an automatic exception report to identify the jobs not processed correctly or print a report indicating that no exceptions existed. Exception reporting should be forwarded to the supervisor, escalating up each level until the problem is handled. The supervisor reviews evidence of the event and determines the action required. The goal is to ensure that exceptions are handled properly in accordance with the organizational goals, policies, and standards for internal control.
- Transaction logs
Transaction logs provide audit trails that are designed to alert the user about a particular condition. The IS auditor needs to understand how the client reviews transaction logs, along with what action is taken. The absence of a transaction log would represent a major concern. A similar concern would exist if the transaction logs are not reviewed on a regular basis.
- Supervisor review
The supervisor should review each of the compensating controls through observation and inquiry. Failure to do so may constitute negligence. The supervisory review is the last level of compensating control.
Capacity management focuses on the monitoring of computing resources and planning for future availability. By using system-monitoring tools, the IT administrator should be able to reasonably estimate the system capacity needed. System utilization reports provide insight into the current processing workload. This workload can be prorated against the operating schedule to forecast future shortfalls.
External changes in the service-level agreements or number of users will have a direct impact on available capacity. During capacity management planning, it is important to assess single points of failure. There will always be a few single points of failure in a system because of the technology selected or the cost of redundancy.
The IT operations staff should have a problem management process in place. Effective problem management provides a timely response by using predefined procedures that include a method for problem escalation.
Situations requiring problem management include the following:
- Acceptable use policy (AUP) violation
Violation of the acceptable use policy could include the misuse of corporate resources or the presence of nonbusiness materials. The discovery of an AUP violation should trigger the incident-handling process and notification to Human Resources.
- Job accounting
Computer processing is always subject to problems. Conditions of concern include abnormal job terminations and exception handling. Other problems can include jobs that run too fast or excessively slow for the volume of work. Jobs that end too fast may indicate that a portion of the processing was skipped. Consider, for example, a tape backup that appears to complete in record time. An investigation may find that the data written to tape is incomplete or nonexistent. Either condition would indicate a substantial problem.
- Training
The training of users and staff is a good response to prevent the recurrence of a problem. Training plans should exist for new-hire orientation, basic user training, and additional awareness training. Test exercises for business continuity also serve to train individuals about their job role during a crisis.
All incidents, problems, and errors are to be recorded. Incidents reported to IT may be either accidental or malicious. An established procedure is required to ensure a thorough investigation.
Certain events will need to be analyzed by a competent individual with the proper training. Every organization needs an incident response team (IRT) readily available. Whenever someone discovers or suspects that an incident has occurred, this team is quietly notified and called into action. One or more team members begin the investigation by analyzing available data to determine the possible impact. The objective is to limit the damage. A problem should be referred to the appropriate management to ensure that it receives the proper attention. All instances of problems are expected to be resolved in a timely manner. For example, computer security problems should be dealt with immediately. Network printer problems may be a lower priority.
Incident response teams are structured into one of three categories:
Centralized team
Distributed team reporting to a central authority
Coordination team providing guidance and advice to individual responders
Members of the IRT should be formally designated via a written charter. This will help eliminate disputes over responding versus continuing to work on the tasks of their normal job. The staff of the IRT could be employees, outsourced, or a hybrid model. Team members may be needed 24/7, which creates a need for schedule planning. Each response will follow four phases of the incident response life cycle:
- Phase 1: Preparation
The basic tasks include appointing team members, getting the team trained, and providing the necessary procedures with appropriate tools to perform the job. Preventative controls can save money by reducing the occurrence of problems. For example, properly maintained antivirus software eliminates many of the virus attacks. Dividing the network with predetermined disconnect points allows undamaged portions of the business to continue near-normal operation after infected areas have been isolated.
- Phase 2: Detection and Analysis
System log reports and telephone calls to the help desk are excellent sources of detection. IT's constant monitoring should become the number one source of detection. The team is quietly activated after a problem is detected. In some instances, the incident may be a malicious attack. It is important not to signal the attacker that activity has been discovered. Certain events may require the assistance of outside experts, as in the case of forensic analysis. Test procedures and samples need to be documented. It is possible that the incident is a cyber crime scene containing evidence that must be protected.
- Phase 3: Containment, Eradication, and Recovery
Incidents need to be contained as quickly as possible to prevent spreading more damage. Early containment helps keep the situation small enough to manage. Swift decisions are necessary to contain the problem. Acting too late will result in the situation overwhelming the available resources. This means that tough decisions should be preapproved with agreed-upon activation criteria. When the criteria are met, the predetermined action proceeds without any delay. Separate containment strategies should be developed for each major type of incident (fraud, theft, virus attack, server failure, and so forth).
- Phase 4: Postincident Activity
After all the documentation is completed, the next step is to report the incident according to the requirements for your industry. Disclosure is becoming more common for legal compliance. One of the most valuable benefits from incident response is conducting a lessons learned meeting. The purpose is to analyze expected results and unexpected consequences in order to improve. Data and records collected from the event may need to be placed in longer-term evidence storage. (See the evidence life cycle in Chapter 2).
Now we need to finish the incident response section with a quick discussion about forensic computer investigations to dispel any misunderstanding.
Digital forensic investigations target computer data for laboratory analysis. This tiny section on the subject should not be construed as legal advice, because the scope of performing a digital forensic investigation exceeds the capability of this book. Our goal is to provide an introduction to the steps involved in conducting digital investigations related to criminal activity. New electronic discovery laws (e-discovery) are changing the rules and responsibilities in civil and criminal court cases. Auditors and investigators should require a clear, written mandate from the appropriate authority to indicate that they have received lawful authorization before starting a forensic investigation.
There are four basic phases in the forensic life cycle—acquisition, examination, utilization, and review.
The acquisition phase deals with acquiring data from the best possible sources. Data may be recovered from deleted files, which are not actually erased by the operating system. The computer simply marks the file as being eligible for overwriting at any time. The actual data is still present.
Computer backups are referred to as logical backups. The logical backup copies the directories and files of the volume but ignores deleted files and residual data in slack space. The slack is the difference between space actually used by the file and the space allocated. Slack space refers to remnant areas on the hard disk. Physical disk imaging, known as bitstream imaging, creates a bit-for-bit copy of the original media, including the deleted files and residual data in slack space. A special write blocker is used to prevent the analyzed computer from writing to its storage media.
Note
Without a write blocker, the evidence becomes altered (tainted), which destroys the chain of custody.
Data may be permanently destroyed on a hard disk by a wiping utility, which uses random values to overwrite portions of the media. Security professionals use wiping utilities to clear hard disks for redeployment. Hackers use wiping utilities to destroy the evidence, thereby covering their tracks.
Four important points to remember in the acquisition phase are volatile data, nonvolatile data, avoiding use of the keyboard, and creating multiple images of the files.
Volatile data refers to information in memory that will be lost when the power is shut off. Prematurely shutting off power erases the evidence of an attack, which is stored in computer chip RAM. (We covered this in the hardware section of Chapter 4).
Nonvolatile data is the information contained on the hard disk and flash memory devices. A graceful shutdown causes the operating system to clean up temporary files and clear the swap file before shutting down. A hacker may attach a utility in the shutdown process to erase the trail of their malicious attack. Abruptly removing power from the system can preserve swap files, temporary data, and other information that may have been deleted during a graceful shutdown. Some systems will create an automatic dump of all their contents into a special file, known as a crash dump. Unfortunately a sudden loss of power could also corrupt the data.
Tip
Preplan response procedures by conducting a review by a forensics expert before getting attacked. The best response will be different on different operating systems.
Keyboard remapping allows for individual keys or a combination of keystrokes to perform a very different function than their standard purpose. Hackers frequently remap their keyboard so a simple keystroke such as Ctrl+Alt or F2 will start an automatic wiping of the hard disk to destroy evidence. The best way for the forensic analyst to acquire data is without using the keyboard. Special disk-imaging hardware has been designed specifically for this purpose.
Multiple copies of the files should be created to avoid working with the originals. Integrity of the files is important. Logical backup is acceptable for informal collection from a live system. Physical bitstream imaging is required if preserving the file times is important.
Forensic analysts must work with read-only copies of the files, not the originals. Many files contain a header, which can identify the type of data it contains. File extensions are not trustworthy, because the user can assign any extension to a file. Examination should use a toolkit that is well recognized by law enforcement agencies. The de facto standard for prosecution is EnCase Forensic software. Examination includes at least the following files:
Live data files and deleted files that can be recovered
Contents of memory, network connections, network shares, strings, and directories
Configuration files for OS, users, passwords, processes run, and jobs
Log files of system events, audit records, command history, and previously accessed files
Application files
System swap files, dump files, temporary files, and hibernation files
Files may be examined from the computer system and the network traffic. Security event management (SEM) software is capable of importing log history from various devices and creating a correlation of events. This allows the reconstruction of events by replaying log and traffic data. Examination of forensic information has been helpful to prosecute espionage, theft of intellectual property, fraud, blackmail, hacking, spamming, murder, and child pornography. Policies and procedures are also needed in case the investigation creates an inadvertent disclosure of sensitive information.
Note
Forensics experts with prior law enforcement experience are preferred as investigators. The special training and experience as a police officer or special agent are well respected by the judge.
Analysts should review the results of data from individual applications to determine how events will fit together during reconstruction. Correlating events is the most effective way to handle the situation. A detailed, methodical approach is required.
Constant review of the processes can help identify procedural errors, skill gaps, and shortcomings in the plans. Changes and updates in the legal process must be incorporated into the process. Failure to prove the case with a successful conviction may backfire with a countersuit for damages.
Now we have covered the most important objectives for this chapter. We are ready to begin the chapter review.
The performance of information technology is ultimately interpreted by three fundamental business performance indicators: the IT budget, user satisfaction, and technical indicators. Technical indicators could include a combination of automated and manual metrics. You can gain a reasonable understanding of IT performance by reviewing these indicators.
IT management should conduct regular performance reviews of all the items discussed in this chapter. Management and staff should make provisions for an independent audit to review their work. The auditor's focus in IT service delivery will be to determine the effectiveness and efficiency of IT.
When reviewing IT service delivery, the paramount concern is that action items are identified, properly tracked, assigned to a competent individual, and resolved in a timely manner. IT's performance can be measured by a combination of metrics, budget performance, and user satisfaction.
The IT auditor evaluates the client's performance and effectiveness of their management techniques.
- Know how to evaluate service-level management practices from internal and external providers.
Service-level management is based on an understanding between the provider and the user as to system availability, service definition, personnel qualifications, security requirements, and data integrity requirements. Service-level agreements (SLAs) need to include performance reporting, right to audit, SLA change procedures, and the cost of service.
- Understand the principles of IT operations management to ensure that the service meets the business requirements.
IT operations management can be aligned to business requirements by using the traditional processes of mission, strategy, and metrics supported by policies, standards, and procedures. The alignment can occur by using the balanced scorecard methodology we discussed in Chapter 3.
- Understand how the IT organization implements functional controls for service delivery.
Controls are established for system access, data files, input, application processing, output, maintenance, change management, asset control, capacity management, and problem management.
- Understand the issues surrounding software licensing.
Software licenses are assets that need to be controlled, inventoried, tracked, and managed. Unauthorized installation of computer software is a violation of copyright law, which carries stiff penalties.
- Understand production change control, release management, and configuration control.
Changes need to be carefully managed in a production environment to prevent an interruption or outage. Software may be released as a major release, an update, or an emergency fix. Emergency changes should undergo the standard change management process after implementation.
- Understand the demands of ensuring processing integrity.
Data files must be protected from unauthorized access. Standing data is vulnerable to unauthorized copying. Application processing uses input controls, processing controls to ensure the completeness of processing, and output controls to ensure the confidentiality of the output.
- Understand the purpose of valid backups and project management in maintenance controls.
Data backups are used to ensure that two copies of the data exist in case a failure occurs during maintenance. Project management is used with risk analysis to manage maintenance changes. The goal is to ensure that the maintenance occurs with the least possible impact to the system's availability and integrity.
- Know the issues in problem and incident management.
Problem and incident management requires a timely response via predefined procedures and a method for escalating problems. The purpose of problem response is to correct a condition. Incident response determines the impact and the steps necessary for resolution. A concern is that the location of an incident may be a potential technology crime scene.
- Understand the issues of maintaining evidence integrity during forensic investigations.
Forensics requires special handling procedures during the four phases of acquisition, examination, utilization, and review. Useful data may be scavenged from volatile RAM and nonvolatile temporary files on the hard disk in slack space or swap files. Data files should be obtained by using a write blocker to prevent the source media from being accidentally altered, which would taint the evidence.
Performance of a third party should be compared to the agreed-upon service-level metrics and must be
Supplied by an independent employee of the service provider.
Accepted at face value by the customer.
Reviewed by management.
Review is not necessary because it is a third party and outside the customer's control.
What is the most important responsibility of the IT security person?
Controlling and monitoring compliance to data security policies
Promoting security awareness within the organization
Establishing procedures for IT and reviewing for legal accuracy
Assisting in system administration of the servers and database
Segregation of duties may not be practical in a small environment. A single employee may be performing the combined functions of server operator and application programmer, for example. The IS auditor should recommend controls for which of the following?
Automated logging of changes made to development libraries
The hiring of additional technical staff to force segregation of duties
Preventing the operator login ID from making program modifications
Procedures verifying that only approved program changes are implemented
What are the four basic types of metrics that can be used to measure IT performance?
Efficiency, implementation, impact, effectiveness
Cost, quantifiable, qualitative, historical
Process control, compliance, efficiency, cost
Service definition, performance goal, cost, effectiveness
What type of control is representative of exception reporting?
Processing
Output
Database integrity
Service level
How should management act to best deal with emergency changes?
Emergency changes cannot be made without advance testing.
All changes should still undergo review.
The change control process does not apply to emergency conditions.
Emergency changes are not allowed under any condition.
What is one of the bigger concerns regarding asset disposal?
Residual asset value
Employees taking disposed property home
Standing data
Environmental regulations
Why is ongoing system monitoring important?
For preventative control
For historical logging and trend analysis
To collect metrics for SLA reports
To find inconsistencies and errors
What is the primary objective in problem escalation?
Improve customer satisfaction
Optimize the number of skilled personnel
Ensure the correct response
Prove that the IT staff is competent
Which of the following is a major issue facing incident response?
The location may be a technology crime scene.
Scheduling of personnel.
Developing appropriate procedures.
Compliance with IT policies.
Which of the following functions should be separated from the others if segregation of duties cannot be achieved in an automated system?
Origination
Authorization
Correction
Reprocessing
What is the primary concern regarding maintenance login accounts?
Computer systems have default user accounts for system setup.
Access to maintenance accounts must be restricted to a particular station address.
Maintenance accounts must be configured to use the hardware that was selected by the organization.
The default login ID used by maintenance accounts is often well known.
An IS auditor is auditing controls related to an employee termination. Which of the following is the most important aspect to be reviewed?
Company staff are notified about the termination.
All login accounts of the employee are terminated.
The details of the employee have been removed from active payroll files.
Company property provided to the employee has been returned.
What are the three layers for scoring IT performance according to ISACA?
Policy, standards, established procedures
Budget, service-level agreement, problem management
Mission, strategy, metrics
Definition of service, internal controls, change management
What is one of the first concerns that the IS auditor should have when reviewing service-level agreements?
The vendor can provide evidence that security controls are present.
The services in the agreement are aligned to actual business needs.
The client received the absolute best price for services offered.
The contract guaranteed the right to audit the outsource vendor
Which of the following statements is not true concerning SLA performance reporting?
Metrics are reported against qualitative measurement.
Both parties need to agree on the content of metrics.
Metrics are reported against quantitative measurement.
Metrics must be developed to fill actual business objectives.
Which of the following statements about standing data is true?
Standing data improves database performance. The data is standing ready for processing.
Standing data is an operational requirement.
Standing data is a security concern.
Standing data is a normal occurrence in the database.
Which of the following is not an input authorization control?
Signatures on source documents
Sequence numbers
Management review
Separation of duties
What are three of the four key perspectives used to create the IT balanced scorecard for service delivery?
Cost reduction, business process, growth
Business justification, service-level agreements, budget
Organizational staffing, cost reduction, employee training
Service level, critical success factors, vendor selection
What is biggest advantage of using a lights-out operation?
Reduced operating expense.
The ability to run systems by remote control.
Removing personnel from the data center reduces risk.
Service personnel will occupy the room only during times of maintenance.
What is likely to be the biggest issue regarding log management?
Systems need to be configured, and then someone needs to read the logs and respond to the findings.
Log management is not required. It's considered a waste of time.
Log files need to be configured, captured, read, and backed up.
System log files consume valuable disk space and are used only by the auditor.
What is an applet compared to a servlet?
An applet is mobile program running on the workstation, and a servlet is a server-side include (SSI).
There is no difference, because both can run on the same computer.
An applet is safer than a servlet.
A servlet uses a Java Virtual Machine or ActiveX control to prevent crashing.
When separation of duties is not possible, what would be the terminology for forcing employees to take vacation, job rotation, reconciliation, and supervisor review?
Preventative control
Corrective control
Compensating control
Transaction control
Which qualification would be preferred in forensic investigations?
Advanced Microsoft training and MCSE certification
College degree in criminal science
Masters degree in computer science
Prior experience as a police officer or special agent
What is the purpose of a transaction processing monitor?
Notify the operator or user of processing exceptions
Verify the account totals for each job processed
Provide limit checks so overly large transactions will not be processed
Keep database activity from overloading the hardware
Which of the following statements is true regarding the programmer?
Is responsible for maintaining the production software currently in use by the user
Should never have access to the production software library
Makes changes to the production version of software under the supervision of a computer operator
Is responsible for reviewing user change requests and implementing approved changes to the production library
Which of the following refers to providing verification of data values during different stages of processing for the purpose of completeness of the transaction?
Run-to-run totals
Job cost accounting
Limit checks
Validation checker
Which of the following is the best definition of slack space on a hard disk?
Unused space leftover after disk formatting
Disk tracks and sectors marked as unusable
Difference between space allocated and space actually used
Uncompressed space remaining on the disk partition
Which of the following methods is used to make a backup copy of all the data files for a forensic investigation?
Bitstream image backup
Logical image backup
Full disk backup
Nonvolatile backup
Which of the following methods is designed to permanently destroy data on a hard disk?
Reformatting the disk
Deleting files
Read blocker
Disk wiping
Which of the following is the best description for a computer-generated report being printed during each processing run to indicate that no problems occurred during processing?
Exception report
Job audit log
Run totals report
Problem log
Which of the following is the best description of nonvolatile data?
Contents of random access memory
Data on the hard disk
Data acquired by forensic recovery
Data from logical disk backups
Which of the following is the most important component of customer satisfaction according to ISACA?
External measurement
System performance metrics
Customer surveys
Internal measurement
Who is responsible for the daily handling and tracking of physical media containing data files?
System administrator
IT manager
Media librarian
Business user
Why is a write blocker needed during the acquisition phase of digital forensics?
To keep the hacker from changing or destroying evidence remaining on the hard disk, in order to preserve the chain of custody
To prevent evidence from being altered, which destroys the chain of custody
To disable the hacker's self-destruct utility from wiping the disk and destroying the chain of evidence
To prevent activating a hidden keyboard remapping utility that the hacker installed to destroy evidence and cover their tracks
C. All performance by a third party under the service-level agreement should be compared to the service levels that the provider and the user of the service agreed on.
A. The primary responsibility of the IT information security person is to ensure the proper implementation of data security policies and to monitor the level of compliance.
D. Compensating controls may be used when segregation of duties is not practical for a small staff. Procedures must exist to verify that only approved program changes are implemented.
A. The four basic types of metrics are efficiency (which indicates timeliness), implementation (which demonstrates a comparative count or percentage attained), impact (shown as a qualitative measure of incidents sorted by type or represented as a dollar figure), and effectiveness (measured as a quantifiable number demonstrating satisfactory resolution).
A. Exception reporting is a processing control used to capture input errors before processing occurs. The exception may be held in suspension until the errors are corrected or rejected.
B. All emergency changes should still undergo the formal change management process after the fact.
C. Any standing data should be purged from the equipment prior to disposal.
D. Proper IT management focuses on proactive discovery of inconsistencies, errors, and processing failures. The results can be used for secondary value in trend analysis and SLA reporting.
C. Problem escalation is used to ensure that the problem is analyzed by a competent individual with the proper training.
A. The incident location may be a technical crime scene. The response should be preplanned and structured to ensure that the value of evidence is not diminished and confidentiality is maintained. The other points may be contributing circumstances but are not major issues.
B. Authorization for changes should be separated from other work if separation of duties cannot be achieved. Additional compensating controls would be required.
D. The default login ID used for maintenance accounts is frequently well known and commercially published. Login may be restricted to a particular station address. However, that is not the primary concern.
B. Employee access to information systems should be promptly terminated. The accounts for contractors no longer employed by the organization should be suspended. All accounts should be reviewed before the account is deleted.
C. ISACA defines the three layers for IT scoring as mission, strategy, and meaningful metrics for performance measurement.
B. The services provided should fulfill the organization's business objectives. The second concern would be the presence of security controls, followed by the right to audit. The last concern should be the absolute best price. Price would not matter if the services provided did not fulfill an actual business requirement.
A. Service-level performance metrics should be quantitative measurements rather than qualitative. Qualitative measurements are too subjective. All other statements are true.
C. Standing data is a security concern that requires additional controls such as storage in an encrypted format.
D. Separation of duties does not grant input authorization. The other three answers represent valid input authorization.
A. The four perspectives on the IT balanced scorecard are the customer perspective, business process perspective, financial perspective, and growth perspective. Each of these seek to define the highest return by IT. The scorecard concept was introduced in Chapter 3. It's used to define the user's view for specifications of IT operations mentioned in this chapter.
C. Removing personnel from the data center reduces the risk to systems by reducing the risk of error, malicious attacks, and environmental contaminants.
C. Log files must be backed up. The best practice is to export log files to a Syslog. This helps protect the files from damage by moving them to another computer. Logs need to be configured to include the best possible data. Log files are used by IT operations staff for incident response. Auditors use log file data for audit evidence.
A. Applets are small programs that download to the user's computer. Applets are considered mobile code. The equivalent program running on the server is called a server-side include (SSI), named after the programmer's terminology.
C. Compensating controls are administrative controls used to detect problems that may be hidden by the person performing the work. Examples include audits, supervisor review, forced vacations, transaction logging, and account reconciliation.
D. Prior experience as a police officer or special agent is preferred because of their special training in crime scene management. Law enforcement officers are usually well respected by the court judge.
D. TP monitors are used to keep the database activity from overloading the available hardware.
B. Software developers (programmers) should not have privileged access to production libraries. A programmer may have the same limited access as the user, but should never be allowed to move programs into production. Doing so would violate change control and separation of duties. The system operator is responsible for moving approved programs into the production library.
A. Run-to-run totals are used to ensure the completeness of transaction during various stages of processing.
C. Slack space refers to the remnant areas of the hard disk. The slack is the difference between space actually used by the file and the space allocated. Remnants of data files often remain in slack space until overwritten or until the drive is defragmented.
A. Physical disk imaging (also known as bitstream backup) copies the entire disk by using every data bit, including deleted files and residual data in slack space. A standard computer backup would copy only.
D. A disk-wiping utility is designed to prevent data from being recovered from a hard disk. Disk formatting simply maps available storage locations. Reformatting the disk is equivalent to tearing the index section out of a book and leaving all the other original pages intact. Disk wiping writes random characters across every data bit location on the disk by using multiple passes to ensure that no data is leftover that may be readable.
A. Exception reports should be automatically created during all job processing. The report identifies any exceptions that occurred or indicates that no exceptions occurred. Exception reporting is a type of detective control.
B. Volatile data still remains on the hard disk, including temporary files and the contents of the system swap file.
A. External measurement represents the customer's perspective. Their interest is system availability, perception of the service received from the help desk, IT worker's attitude, and response time to get their problem fixed.
C. The media librarian is responsible for tracking all the media containing data. Proper tracking includes signing in and signing out physical backup media as it's transferred to and from offsite storage or elsewhere in the organization. The media librarian is usually a dedicated person in larger organizations or at least someone formally assigned in smaller organizations.
B. Write blockers are used during forensic bit-imaging backups to prevent evidence from being altered, which destroys the chain of custody.