INTRODUCTION
The dizzying pace of information systems innovation has made vast expanses of information available to organizations and the public. Often, design flaws and technical vulnerabilities bring unintended consequences, often in the form of information theft and disclosure. The result: a patchwork of laws, regulations, and standards such as Sarbanes-Oxley, GLBA, HIPAA, PCI-DSS, NYDFS, PIPEDA, GDPR, CCPA, and scores of U.S. state laws requiring public disclosure of security breaches involving private information. Through these, organizations are either required or incentivized to perform their own internal audits or undergo external audits that measure compliance in order to avoid penalties, sanctions, and embarrassing news headlines.
These developments continue to drive demand for IT security professionals and IS auditors. These highly sought professionals play a crucial role in the development of better compliance programs and reduced risk.
The Certified Information Systems Auditor (CISA) certification, established in 1978, is indisputably the leading certification for IS auditing. Demand for the CISA certification has grown so much that the once-per-year certification exam was changed to twice per year in 2005, then three times each year, and is now offered on a continuous basis. In 2005, the CISA certification was awarded accreditation by the American National Standards Institute (ANSI) under international standard ISO/IEC 17024. CISA is also one of the few certifications formally approved by the U.S. Department of Defense in its Information Assurance Technical category (DoD 8570.01-M). In 2009 and 2017, SC Magazine named CISA the best professional certification program. In 2016, there were more than 129,000 professionals holding the certification.
IS auditing is not a “bubble” or a flash in the pan. Instead, IS auditing is a permanent fixture in organizations that have to contend with new technologies; new systems; new threats; and new data security and privacy laws, regulations, and standards. The CISA certification is the gold standard certification for professionals who work in this domain.
Purpose of This Book
Let’s get the obvious out of the way: This is a comprehensive study guide for the security or audit professional who needs a serious reference for individual or group-led study for the Certified Information Systems Auditor (CISA) certification. The majority of the content in this book contains the technical information that CISA candidates are required to know.
This book is also a reference for aspiring and practicing IS auditors. The content that is required to pass the CISA exam is the same content that practicing auditors need to be familiar with in their day-to-day work. This book is an ideal CISA exam study guide as well as a desk reference for those who have already earned their CISA certification.
This book is also invaluable for security and business professionals who are required to undergo external audits from audit firms and examinations from regulators. Readers will gain considerable insight into the practices and methods used by auditors; this helps not only in internal audit operations but also in understanding external auditors and how they work. This knowledge and insight will lead to better audit outcomes.
This book is an excellent guide for someone exploring the IS audit profession. The study chapters explain all the relevant technologies and audit procedures, and the appendices explain process frameworks and the practical side of professional audits. The glossary contains a rich collection of terms used by IT security and IS auditors. These are useful for those readers who may wonder what the IS audit profession is all about.
How This Book Is Organized
This book is logically divided into four major sections:
• Introduction This Introduction to the book plus Chapter 1 provide an overview of the CISA certification and the IS audit profession.
• CISA study material Chapters 2 through 6 contain everything an aspiring CISA candidate is required to know for the CISA exam. This same material is a handy desk reference for aspiring and practicing IS auditors.
• IS auditor reference Appendix A walks the reader through the entire process of a professional IS audit, from audit planning to delivery of the final report. Appendix B discusses control frameworks; this will help an IS auditor who needs to understand how control frameworks function, or who is providing guidance to an organization that needs to implement a control framework.
• Practice exams Appendix C explains the CISA practice exams and TotalTester Online test engine that accompany this book.
Notes on the Fourth Edition
ISACA has historically recalibrated the contents of its certifications every five years. In late 2018, ISACA announced that it would update the CISA job practice (the basis for the exam and the requirements to earn the certification), effective in the June 2019 examination. In order to keep this book up to date, I contacted Wendy Rinaldi at McGraw-Hill so that we might develop a plan for the fourth edition of this book as quickly as possible. This book is the result of that effort.
The new CISA job practice information was made available in late December 2018. We began work at that time to update the third edition manuscript. The result is this book, which has been updated to reflect all of the changes in the CISA job practice, as well as changes in audit practices, information security, and information technology since the second edition was published.
Changes to the CISA Job Practice
Table 1 illustrates the previous and current CISA job practices and their relation to chapters in this book.
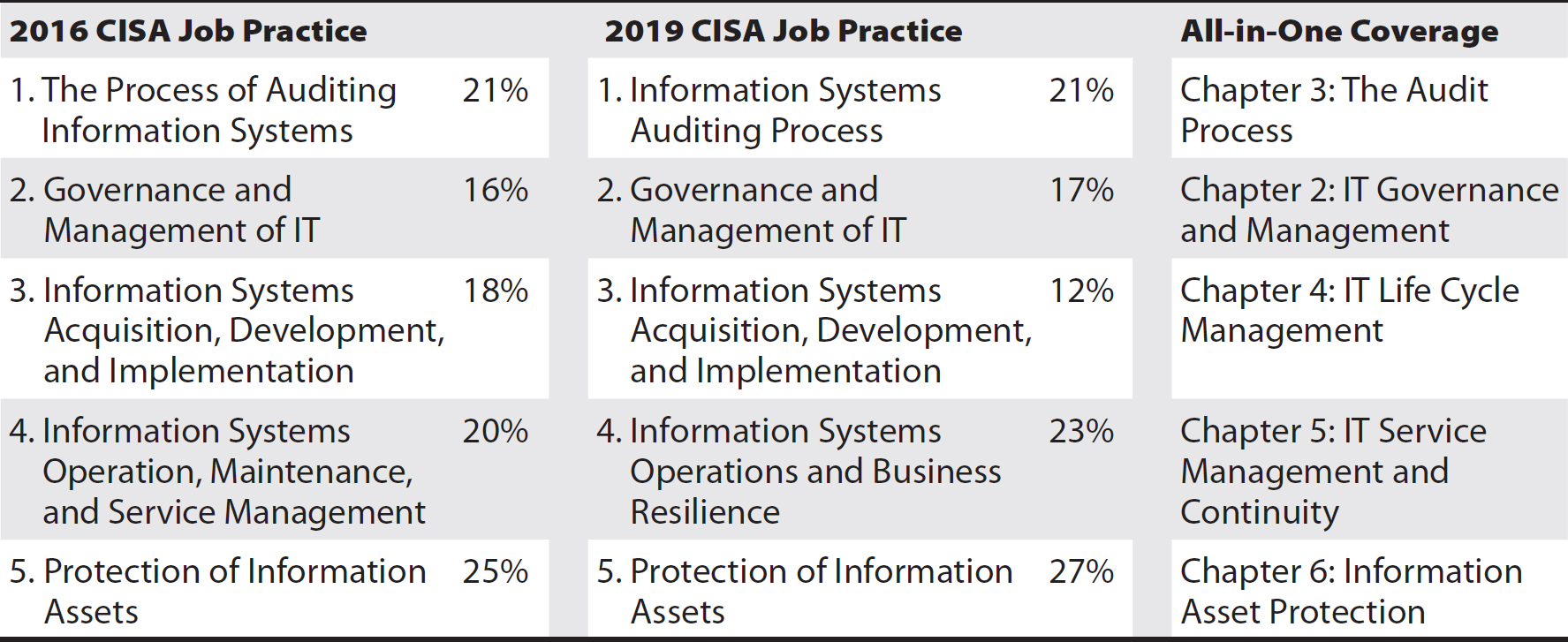
Table 1 Previous and Current CISA Job Practices
For the 2019 CISA job practice, ISACA reformatted the way that the practice areas are described. Previously, each job practice had a set of Knowledge Statements and Task Statements. In the 2019 edition, each job practice consists of two major categories, and each category has four to eleven subtopic areas. This is followed by 39 Supporting Tasks for CISA overall that are not specifically associated with the five domains.
As is typical for each new job practice and revision of this CISA All-In-One Exam Guide, I perform a gap analysis to understand what subject matter has been added to the new job practice and what has been eliminated. While the change in structure made this a bit more tedious, in general here are the noteworthy changes in content:
• Audit Project Management is a new topic.
• Audit Data Analytics is a new topic.
• Privacy Principles is a new topic.
• Business continuity planning and disaster recovery planning moved from domain 2 (Governance and Management of IT) to domain 4 (Information Systems Operations and Business Resilience) but are otherwise unchanged.
• Enterprise Architecture moved from domain 3 to domain 2.
• IoT is a new topic.
In addition to the changes to the CISA practice, there are several topics that are altogether new or expanded from the third edition. These changes include
• Segmentation and microsegmentation
• Virtualization, containerization, and virtual keyboards
• 5G
• A greater emphasis on systems acquisition with the systems development life cycle, which reflects the migration away from custom software development toward the acquisition of shrink-wrap software and Software-as-a-Service for core business applications
• The impact of digital transformation
• Zero Trust principles of enterprise architecture
• The NIST Cybersecurity Framework (CSF)
• New laws and regulations such as GDPR and CCPA
• Agile methodology for managing changes to infrastructure and business processes
• Several new development methodologies
• Cloud responsibility models
• Passwords, and whether they should periodically expire
• The threat of ransomware and destructware
• Changes in the meaning of remote access and VPNs
• Addition of numerous new technologies such as BLE and WPA3
• Removal of long-deprecated technology such as X.25
• Addition of 64 new items and cross-references to the glossary (and a few deprecated items removed)
By the time we completed this book, there were even more new developments, technologies, techniques, and breaches that provided additional insight and the promise of still more improvements. Like the surface of Saturn’s moon, Io, our profession is ever changing. The technology boneyard is filled with vendors, products, protocols, techniques, and methodologies that once held great promise, later replaced with better things. This underscores the need for IS auditors (and IT, security, and risk professionals) to stay current by reading up on current events, new technologies, and techniques.
