Chapter 11
WLAN Deployment and Vertical Markets
In this chapter, you will learn about the following:
 Deployment considerations for commonly supported WLAN applications and devices
Deployment considerations for commonly supported WLAN applications and devices
- Data
- Voice
- Video
- Real-Time Location Services (RTLS)
- Mobile devices (tablets and smartphones)
 Corporate data access and end-user mobility
Corporate data access and end-user mobility
 Network extension to remote areas
Network extension to remote areas
 Bridging—building-to-building connectivity
Bridging—building-to-building connectivity
 Wireless ISP (WISP)—last-mile data delivery
Wireless ISP (WISP)—last-mile data delivery
 Small office/home office (SOHO)
Small office/home office (SOHO)
 Mobile office networking
Mobile office networking
 Branch offices
Branch offices
 Educational/classroom use
Educational/classroom use
 Industrial—warehousing and manufacturing
Industrial—warehousing and manufacturing
 Retail
Retail
 Healthcare—hospitals and offices
Healthcare—hospitals and offices
 Municipal networks
Municipal networks
 Hotspots—public network access
Hotspots—public network access
 Stadium networks
Stadium networks
 Transportation networks
Transportation networks
 Law enforcement networks
Law enforcement networks
 First-responder networks
First-responder networks
 Fixed mobile convergence
Fixed mobile convergence
 WLAN and health
WLAN and health
 WLAN vendors
WLAN vendors
In this chapter, you will learn about environments where wireless networks are commonly deployed. We will consider the pros and cons of wireless in various environments along with areas of concern. Finally, we will discuss the major commercial WLAN vendors and provide links to their websites.
Deployment Considerations for Commonly Supported WLAN Applications and Devices
As wireless networking has expanded, numerous applications and devices have benefited, and along the way these applications and devices have helped to expand the growth of wireless networking. Although applications such as data and video have benefited due to the flexibility and mobility that wireless affords them, they are not wireless-intrinsic applications. Voice, real-time location services (RTLSs), and network access using mobile devices are three uses that are inherently dependent on a WLAN and will continue to expand the use of WLANs. No matter which of these applications or devices you are implementing on your network, you will need to consider certain factors when planning, designing, and supporting your WLAN. The following sections focus on considerations for commonly supported WLAN applications and devices.
Data
When data-oriented applications are discussed, email and web browsing are two of the most common applications that come to mind. When planning for network traffic over any type of network, wireless or wired, you need to first look at the protocols that are being implemented. Protocols are communications methods or techniques used to communicate between devices on a network. Protocols can be well designed, based on documented standards, or they can be proprietary, using unique communications methods. Data-oriented applications are often based on well-known protocols and are therefore usually easy to work with because a great deal of knowledge already exists about how they communicate.
One of the most important aspects of designing a network to handle data-oriented applications is to ensure that the network design is capable of handling the amount of data that will be transferred. Most data applications are forgiving of slight network delays, but problems can arise if there is not enough available data bandwidth. When designing your wireless network, analyze the data requirements of your users and make sure that the data rates at which the users will connect are capable of handling the amount of data that they will be transmitting.
Voice
When designing a WLAN to support voice communications, keep in mind that, unlike data communications, voice communications are not tolerant of network delays, dropped packets, or sporadic connections. Designing a WLAN to support voice communications can also be a challenge because there are so many differences in how vendors implement their voice products. Each vendor has unique guidelines for designing voice applications. This is true not only for vendors of voice handsets or software applications, but also for infrastructure vendors. So, it is important to understand the best practice methods for installing your voice system.
Voice devices are typically handheld devices that do not transmit with as much power as laptops. Since a wireless device requires more battery power to transmit a strong signal, the transmit power of VoWiFi phones is typically less than other devices in order to increase battery longevity. This reduced power level will decrease the distance that a VoWiFi phone can operate from an access point, thus requiring smaller cell sizes, and more APs will be necessary to ensure adequate coverage.
Video
The transmission of video is typically more complex than voice. In addition to multiple streams of data for video and voice, video often includes streams for setting up and tearing down the connection. Unless you are using the WLAN for a real-time videoconference, video can likely take a backseat to audio. In most cases, video has a higher loss tolerance than voice. Choppy audio during a videoconference would likely be highly disruptive, causing participants to ask the speaker to repeat what was said, whereas if the audio is clear and the video choppy, the speaker would likely be understood the first time.
In regard to video transmission, it is important to identify the type of video that is being transmitted and the function or purpose of that transmission. If you ask an average computer user about video transmission, they will likely think of streaming video—a movie, TV show, or funny video clip downloaded by a user, who may be either stationary or mobile. If you were to ask an executive about video transmission, they will likely think of video as part of a videoconference or a webinar, and the user will most likely be stationary. If you were to ask a facilities or security person about video transmission, they will likely think of streaming video generated by a wireless surveillance camera, most likely permanently mounted to the building. Your WLAN might have any or all of these types of video traffic.
Once you have identified the type of video that will be used on your WLAN, you can plan your network. You need to evaluate the system or software that is transmitting the wireless video traffic to determine the type of traffic and protocols along with the network load. As part of the protocol evaluation, you will need to research whether the video transmissions are using multicast transmissions or quality of service (QoS).
Real-Time Location Services
Location-based technology has garnered a lot of attention in WLAN designs. Most manufacturers of enterprise WLAN systems tout some sort of location capability with their products. Some have features that are built in, whereas others offer integration hooks to third-party vendors who specialize in location technology and have sophisticated software applications related to specific industry vertical markets. Figure 11.1 shows an RTLS system, displaying the location of a wireless device.
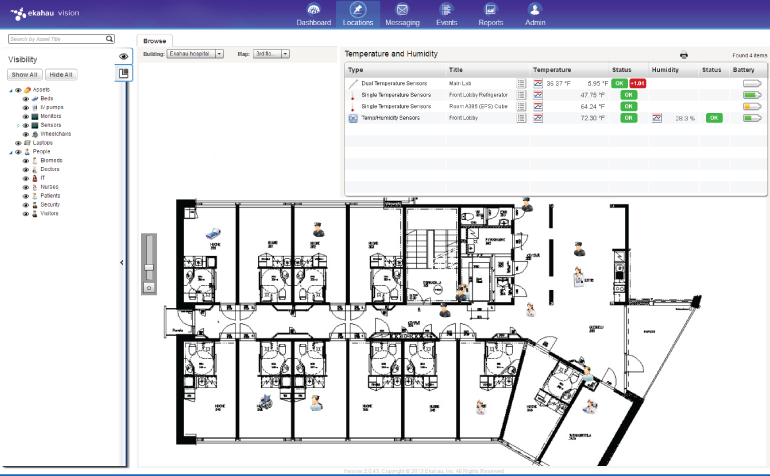
Figure 11.1 Ekahau Vision RTLS software
Location tracking is expanding incredibly quickly as more and more uses are identified. RTLSs can be used to locate or track people or devices on a WLAN. Healthcare is one of the biggest users of location-based technology. Because healthcare providers, such as hospitals, have to run 24/7 shifts, and since many of the assets are shared, RTLSs can be extremely useful for tracking equipment that may be necessary in an emergency or for identifying the closest doctor or specialist.
RTLSs can be used to track any 802.11 radio, or a specialized 802.11 RFID tag can be affixed to a non-802.11 asset so that it can be managed and tracked. Tags can be affixed to any device to provide tracking and help deter theft. Tags can also be worn by employees, children at amusement parks, hospital staff or patients, to name a few. Each RTLS vendor is unique and will be able to provide you with recommendations and best practice documents for deploying your RTLS equipment.
Mobile Devices
We are currently seeing one of the most amazing transitions in networking as employees—from receptionists to CEOs—are bringing their own 802.11-capable devices, such as laptops, tablets, and smartphones, to work and expect—and in many cases demand—that these devices be supported on the corporate network. The primary devices that people are requesting access for are cell phones and tablets that are also capable of communicating using 802.11 radios. Unlike changes in enterprise technology, which is planned and controlled by the IT department, the push for support of mobile devices is being made by the end user. Many organizations see access for these devices as a benefit for employees and are pressuring the IT department to provide access and support.
Multiple concerns arise with integrating these devices into the network:
- Making sure that the devices are capable of connecting to the network using the proper authentication
- Ensuring the use of encryption protocols along with the ability for these devices to be able to smoothly roam throughout the network without losing connectivity
- Providing network access, not only based upon the identity of the user of the device but also based upon the type of device or other device or connection characteristics
Many 802.11 networks that have been in use for a few years were designed to communicate with more powerful devices such as laptop computers. The coverage area of any 802.11 network needs to be designed small enough so that any device can respond back to the access point with a strong enough signal. Handheld devices often transmit at a lower signal level than laptop computers. If a network was designed to communicate with more powerful transmitters, it is possible that a tablet or smartphone may not have sufficient power to transmit back to an access point. If this is the case, these mobile devices are likely to experience RF dead spots throughout the network. Many companies are designing their WLANs to have smaller coverage areas so that these mobile devices do not experience intermittent service.
The introduction of these mobile devices has become a huge trend in the industry, typically known as bring your own device (BYOD), and it has become such a concern that we have dedicated an entire chapter to this topic, Chapter 20, “Bring Your Own Device (BYOD).”
Corporate Data Access and End-User Mobility
With the increased throughput provided by 802.11n and now 802.11ac technology, many organizations have been transitioning to these higher-speed wireless networks while reducing the number of devices connecting to the network via wired connections—in many cases retiring some of the unused or underused wired switches. As mentioned earlier, another major influence pressing organizations to expand their wireless networks is the proliferation of Wi-Fi-enabled personal mobile devices.
The installation of wired network jacks is expensive, often costing as much as—or even more than—$200 (in U.S. dollars) per jack. As companies reorganize workers and departments, network infrastructure typically needs to be changed as well. Other areas, such as warehouses, conference rooms, manufacturing lines, research labs, and cafeterias, are often difficult places to effectively install wired network connections. In these and other environments, the installation of wireless networks can save the company money and provide consistent network access to all users.
Providing continuous access and availability throughout the facility has become paramount in the past few years. With computer access and data becoming critical components of many people's jobs, it is important for networks to be continuously available and to be able to provide the up-to-the-moment information that is being demanded. By installing a wireless network throughout the building or campus, the company makes it easy for employees to meet and discuss or brainstorm while maintaining access to corporate data, email, and the Internet from their laptops and mobile devices, no matter where they are in the building or on the campus.
A big trend in the consumer electronics marketplace has been the addition of wireless radios in devices. Wireless adapters are extremely small and can easily be integrated in these portable devices. Connectivity to the Internet also allows devices to be easily updated, along with providing more capabilities. In addition to the trend of connecting personal electronics, devices keep getting smaller, lighter, and leaner. With this push toward leaner devices, Ethernet adapters have either given way to wireless radios or been bypassed all together in favor of wireless.
Whatever the reason for installing wireless networking, companies must remember its benefits and its flaws. Wireless provides mobility, accessibility, and convenience, but if not designed and implemented properly, it can lack in performance, availability, and throughput. Wireless is an access technology, providing connectivity to end-user stations. Wireless should rarely be considered for distribution or core roles, except for building-to-building bridging or mesh backhaul. Even in these scenarios, make sure that the wireless bridge will be capable of handling the traffic load and throughput needs.
Network Extension to Remote Areas
If you think about it carefully, network extension to remote areas was one of the driving forces of home wireless networking, which also helped drive the demand for wireless in the corporate environment. As households connected to the Internet and as more households purchased additional computers, there was a need to connect all the computers in the house to the Internet. Although many people installed Ethernet cabling to connect their computers, this was typically too costly, impractical because of accessibility, or beyond the technical capabilities of the average homeowner.
At the same time, 802.11 wireless devices were becoming more affordable. The same reasons for installing wireless networking in a home are also valid for installing wireless in offices, warehouses, and just about any other environment. The cost of installing network cabling for each computer is expensive, and in many environments, running cable or fiber is difficult because of building design or aesthetic restrictions. When wireless networking equipment is installed, far fewer cables are required, and equipment placement can often be performed without affecting the aesthetics of a building.
Bridging: Building-to-Building Connectivity
To provide network connectivity between two buildings, you can install an underground cable or fiber between the two buildings, you can pay for a high-speed leased data circuit, or you can use a building-to-building wireless bridge. All three are viable solutions, each with its benefits and disadvantages.
Although a copper or fiber connection between two buildings will potentially provide you with the highest throughput, installing copper or fiber between two buildings can be expensive. If the buildings are separated by a long distance or by someone else's property, this may not even be an option. After the cable is installed, there are no monthly service fees since you own the cable.
Leasing a high-speed data circuit can provide flexibility and convenience, but because you do not own the connection, you will pay monthly service fees. Depending on the type of service that you are paying for, you may or may not be able to easily increase the speed of the link.
A wireless building-to-building bridge requires that the two buildings have a clear RF line of sight between them. After this has been determined, or created, a point-to-point (PTP) or point-to-multipoint (PTMP) transceiver and antenna can be installed. The installation is typically easy for trained professionals to perform, and there are no monthly service fees after installation, because you own the equipment.
In addition to connecting two buildings via a PTP bridge, three or more buildings can be networked together by using a PTMP solution. In a PTMP installation, the building that is most centrally located will be the central communication point, with the other devices communicating directly to the central building. This is known as a hub and spoke or star configuration.
Wireless ISP: Last-Mile Data Delivery
The term last mile is often used by phone and cable companies to refer to the last segment of their service that connects a home subscriber to their network. The last mile of service can often be the most difficult and costly to run because at this point a cable must be run individually to every subscriber. This is particularly true in rural areas where there are very few subscribers and they are separated by large distances. In many instances, even if a subscriber is connected, the subscriber may not be able to receive some services such as high-speed Internet because services such as xDSL have a maximum distance limitation of 18,000 feet (5.7 km) from the central office.
Wireless Internet service providers (WISPs) deliver Internet services via wireless networking. Instead of directly cabling each subscriber, a WISP can provide services via RF communications from central transmitters. WISPs often use wireless technology other than 802.11, enabling them to provide wireless coverage to much greater areas. Some small towns have had success using 802.11 mesh networks as the infrastructure for a WISP. However, 802.11 technology generally is not intended to scale to the size needed for citywide WISP deployments.
Service from WISPs is not without its own problems. As with any RF technology, the signal can be degraded or corrupted by obstacles such as roofs, mountains, trees, and other buildings. Proper designs and professional installations can ensure a properly working system.
Small Office/Home Office
One common theme of a small office/home office (SOHO) is that your job description spans janitor to IT staff and includes everything in between. Small-business owners and home-office employees are typically required to be self-sufficient because there are usually few, if any, other people around to help them. Wireless networking has helped to make it easy for a SOHO employee to connect the office computers and peripheral devices together, as well as to the Internet. The main purpose of a SOHO 802.11 network is typically to provide wireless access to an Internet gateway. As depicted in Figure 11.2, many wireless SOHO devices also have multiple Ethernet ports, providing both wireless and wired access to the Internet.

Figure 11.2 D-Link wireless SOHO router
Most SOHO wireless routers provide fairly easy-to-follow installation instructions and offer reasonable performance and security, though less than what their corporate counterparts provide. They are generally not as flexible or feature rich as comparable corporate products, but most SOHO environments do not need all the additional capabilities. What the SOHO person gets is a capable device at a quarter of the price paid by their corporate counterparts. Dozens of devices are available to provide the SOHO worker with the ability to install and configure their own secure Internet-connected network without spending a fortune. Many SOHO wireless routers even have the ability to provide guest access, allowing visitors Internet access while preventing them from accessing the local network.
Mobile Office Networking
Mobile homes or trailer offices are used for many purposes: as temporary offices during construction or after a disaster or as temporary classrooms to accommodate unplanned changes in student population, for example. Mobile offices are simply an extension of the office environment. These structures are usually buildings on wheels that can be easily deployed for short- or long-term use on an as-needed basis. Since these structures are not permanent, it is usually easy to extend the corporate or school network to these offices by using wireless networking.
A wireless bridge can be used to distribute wireless networking to the mobile office. If needed, an AP can then be used to provide wireless network access to multiple occupants of the office. By providing networking via wireless communications, you can alleviate the cost of running wired cables and installing jacks. Additional users can connect and disconnect from the network without the need for any changes to the networking infrastructure. When the mobile office is no longer needed, the wireless equipment can simply be unplugged and removed.
Moveable wireless networks are used in many environments, including military maneuvers, disaster relief, concerts, flea markets, and construction sites. Because of the ease of installation and removal, mobile wireless networking can be an ideal networking solution.
Branch Offices
In addition to the main corporate office, companies often have branch offices in remote locations. A company might have branch offices across a region, an entire country, or even around the world. The challenge for IT personnel is how to provide a seamless enterprise wired and wireless solution across all locations. A distributed solution using enterprise-grade WLAN routers at each branch office is a common choice. Branch routers have the ability to connect back to corporate headquarters with VPN tunnels. Employees at the branch offices can access corporate resources across the WAN through the VPN tunnel. Even more important is the fact that the corporate VLANs, SSIDs, and WLAN security can all be extended to the remote branch offices. An employee at a branch office connects to the same SSID that they would connect to at corporate headquarters. The wired and wireless network access policies are therefore seamless across the entire organization. These seamless policies can be extended to WLAN routers, access points, and switches at each branch location.
Most companies do not have the luxury or need to have an IT employee at each branch office. Therefore, a network management server (NMS) at a central location is used to manage and monitor the entire enterprise network.
Educational/Classroom Use
Wireless networking can be used to provide a safe and easy way of connecting students to a school network. Because the layout of most classrooms is flexible (with no permanently installed furniture), installing a wired network jack for each student is not possible. Because students would be constantly connecting to and disconnecting from the network at the beginning and end of class, the jacks would not last long even if they were installed. Prior to wireless networking, in classrooms that were wired with Ethernet, usually all the computers were placed on tables along the classroom walls, with the students typically facing away from the instructor. Wireless networking enables any classroom seating arrangement to be used, without the safety risk of networking cables being strung across the floor.
A wireless network also enables students to connect to the network and work on schoolwork anywhere in the building without having to worry about whether a wired network jack is nearby or whether someone else is already using it. In addition to the flexibility the wireless network is able to provide in a classroom environment, in many schools wireless networking has become a necessity: Computer tablets are quickly becoming commonplace devices in all levels of education. These tablets rely solely on wireless networking to provide Internet and local area networking access.
Schools typically require more access points for coverage because of the wall materials between classrooms. Most classroom walls are made of cinderblock to attenuate noise between classrooms. The cinderblock also attenuates the 2.4 and 5 GHz RF signals dramatically. In order to provide –70 dBm or greater coverage, an access point is often needed in at least every other classroom.
The use of wireless bridging is also prevalent in campus environments. Many universities and colleges use many types of wireless bridge links, including 802.11, to connect buildings campuswide.
Network access control (NAC) has become an integral part of many school networks. NAC can be used to “fingerprint,” or identify authentication and authorization information about devices connecting to the network. This information is then used to regulate or control the access that the user has on the network. Access can be regulated or restricted based upon many different criteria, such as time, location, access method, device type, and user identity along with many other properties. NAC is discussed in more detail in Chapter 20.
Industrial: Warehousing and Manufacturing
Warehouses and manufacturing facilities are two environments in which wireless networking has been used for years, even before the 802.11 standard was created. Because of the vast space and the mobile nature of the employees in these environments, companies saw the need to provide mobile network access to their employees so they could more effectively perform their jobs. Warehouse and manufacturing environments often deploy wireless handheld devices, such as bar code scanners, which are used for inventory control.
Most 802.11 networks deployed in either a warehouse or manufacturing environment are designed for coverage rather than capacity. Handheld devices typically do not require much bandwidth, but large coverage areas are needed to provide true mobility. Most early deployments of 802.11 frequency hopping technology were in manufacturing and warehouse environments. Wireless networks are able to provide the coverage and mobility required in a warehouse environment—and provide it cost-effectively.
Retail
There are four key uses of wireless in retail locations. The first is the wireless network that provides support relating to the operations of the store and the retail transactions. The second is a newer and growing use, which is tracking analytics of the retail customer. The third is location-based mapping and tracking services. The fourth is supplemental Internet access, often necessitated by poor cellular coverage inside the retail establishment.
The retail environment is similar to many other business environments. Cash registers, time clocks, inventory control scanners, and just about every electronic device used to run a retail location is becoming networked with a WLAN radio. Connectivity of these devices provides faster and more accurate information and enhances the retail environment for the customer.
To further support and understand customers and their behaviors, retail analytic products are being installed to monitor customer movement and behavior. Strategically placed access points or sensor devices listen for probe frames from Wi-Fi-enabled smart phones. MAC addresses are used to identify each unique device, and signal strength is used to monitor and track the location of the shopper. Figure 11.3 shows a retail analytics dashboard. Analytics can identify the path the shopper took while walking through the store as well as the time spent in different areas of the store. This information can be used to identify shopping patterns along with analysis of the effectiveness of in-store displays and advertisements. One such company that is partnering with multiple WLAN vendors is Euclid Analytics.
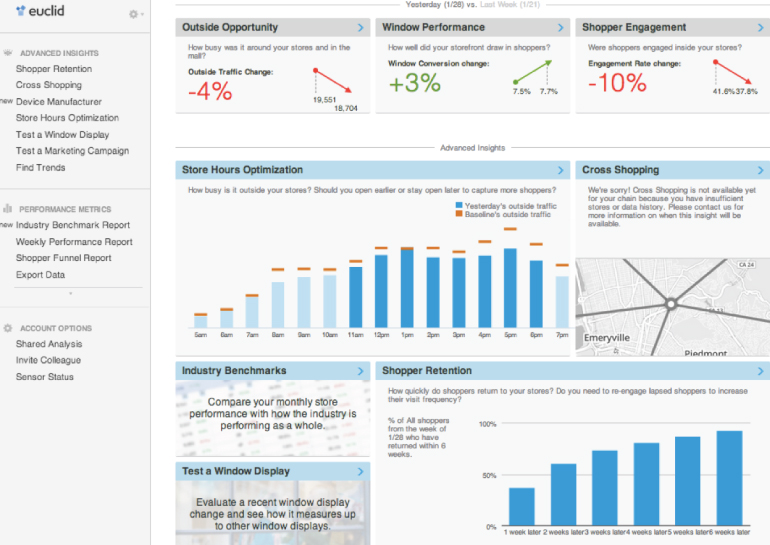
Figure 11.3 Retail analytics
In addition to retail location and trend analysis, indoor location and mapping applications are beginning to provide new services to shoppers and visitors. Retail centers, hospitals, hotels, subways, and museums (and many other types of organizations) can provide turn-by-turn directions to visitors, along with promotions, and other location-based services. As an example, navigating through a large hospital can be confusing. A mobile app can provide turn-by-turn directions for family and friends to locate a patient's room. Conference centers and hotels can use this technology to direct visitors to meeting and event rooms. Special events, advertisements, or services can be offered as the visitor is navigating through the building.
Another key reason to implement wireless in a retail location is to provide supplemental connectivity in lieu of cellular coverage. Retail locations cannot depend upon customers having Internet access through their cellular phone network. Due to the scale and often product density, cellular phone access may not exist or be dependable. Providing wireless access for shoppers may make for a more pleasant and satisfied shopping experience and will likely result in more sales.
Healthcare: Hospitals and Offices
Although healthcare facilities such as hospitals, clinics, and doctors' offices may seem very different from other businesses, they have many of the same networking needs as other companies: data access and end-user mobility. Healthcare providers need quick, secure, and accurate access to patient and hospital or clinic data, so they can react and make decisions. Wireless networks can provide mobility, giving healthcare providers faster access to important data by delivering the data directly to a handheld device that the doctor or nurse carries with them. Medical carts used to enter and monitor patient information often have wireless connections back to the nursing station. Some companies have even integrated 802.11 wireless adapters directly into the equipment that is used to monitor and track the patient's vital signs, such as the monitoring system shown in Figure 11.4, which uses Wi-Fi to transmit patient EKG and vital signs to the nursing station.

Figure 11.4 Welch Allyn Propaq
VoWiFi is another common use of 802.11 technology in a medical environment, providing immediate access to personnel no matter where they are in the hospital. RTLS solutions using 802.11 Wi-Fi tags for inventory control are also commonplace.
Hospitals rely on many forms of proprietary and industry-standard wireless communications that may have the potential of causing RF interference with 802.11 wireless networks. Many hospitals have designated a person or department to help avoid RF conflicts by keeping track of the frequencies and biomedical equipment used within the hospital.
Distributed healthcare is also an emerging trend. Hospitals often have many remote locations. Urgent care facilities are widespread and very often a WLAN branch office solution is required.
Municipal Networks
Over the past few years, municipal networks have received much attention. Cities and towns announced their intentions of providing wireless networking access to their citizens throughout the area. Many municipalities viewed this as a way of providing service to some of their residents who could not necessarily afford Internet access. Although this is a well-intentioned idea, communities often underestimated the scale and cost of these projects, and many taxpayers did not want their taxes spent on what they considered to be an unnecessary service. Although most of these earlier plans for citywide municipal 802.11 networks have been scrapped, there has been an increased interest and success in deploying 802.11 in many downtown and high-density areas. Some of these are provided by the municipality, and others are provided by individuals or business groups.
Hotspots: Public Network Access
The term hotspot typically refers to a free or pay-for-use wireless network that is provided as a service by a business. When people think of hotspots, they typically associate them with cafes, bookstores, or a hospitality-type businesses, such as a hotel or convention center. Hotspots can be used effectively by businesses to attract customers or as an extension of a business's services, in the case of Internet service providers offering these services in heavily travelled areas. Business travelers and students often frequent restaurants or cafes that are known to provide free Internet access. Many of these establishments benefit from the increased business generated by offering a hotspot. Free hotspots have drawn much attention to the 802.11 wireless industry, helping to make more people aware of the benefits of the technology.
Other hotspot providers have had difficulty convincing people to pay upward of $40 per month for a subscription. Many airports and hotel chains have installed pay-for-use hotspots; however, there are many providers, each one offering a separate subscription, which is often not practical for the consumer.
Most hotspot providers perform network authentication by using a special type of web page known as a captive portal. When a user connects to the hotspot, the user must open up a web browser. No matter what web page the user attempts to go to, a logon web page will be displayed instead, as shown in Figure 11.5. This is the captive portal page. If the hotspot provider is a paid service, the user must enter either their subscription information if they are a subscriber to the service or their credit card information if they are paying for hourly or daily usage. Many free hotspots also use captive portals as a method for requiring users to agree to a usage policy before they are allowed access to the Internet. If the user agrees to the terms of the policy, they are required to either enter some basic information or click a button, validating their agreement with the usage policy. Many corporations also use captive portals to authenticate guest users onto their corporate networks.
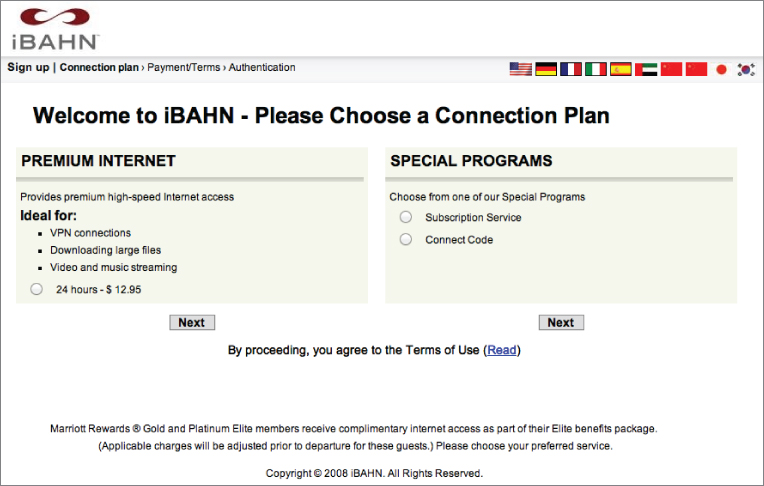
Figure 11.5 Example of a captive portal
Stadium Networks
Technology-savvy fans are driving sport, concert, and event stadiums and arenas to expand the services that they are providing. Fans expect and demand a complete multimedia experience when attending events, including access to replays and real-time statistics. Through apps or websites, in-seat food and beverage ordering and delivery enhances the experience by allowing the fan to enjoy the action instead of standing in line for refreshments. Through texting and social media, fans expect to be able to share their sporting or concert experience with friends or interact with other attendees.
A well-designed stadium network can allow the venue to target sections or groups of people with directed advertisements, special offers, or customized services. Offers or services for fans in the bleacher seats would likely be different than those targeting the fans in the skyboxes. In addition to providing wireless services to the fans, it is important to remember that the stadium is a business and needs to support its own infrastructure and services at an event. A wireless network is needed to provide event operations with services such as reliable high-speed Internet access in the press box, ticketing and point-of-sale transaction processing, and video surveillance.
Transportation Networks
In discussing Wi-Fi transportation networks, the three main modes of transportation—trains, planes, and automobiles—are typically mentioned. In addition to these three primary methods of transportation, two others need to be mentioned. The first is boats, both cruise ships and commuter ferries, and the second is buses, similar to but different from automobiles.
Providing Wi-Fi service to any of the transportation methods is easy. Simply install one or more access points in the vehicle. Except for the cruise ship and large ferries, most of these methods of transportation would require only a few access points to provide Wi-Fi coverage. The primary use of these networks is to provide hotspot services for end users so that they can gain access to the Internet. The difference between a transportation network and a typical hotspot is that the network is continually moving, making it necessary for the transportation network to use some type of mobile uplink services.
To provide an uplink for a train, which is bound to the same path of travel for every trip, a metropolitan wireless networking technology such as WiMAX could be used along the path of the tracks. With the other transportation networks, for which the path of travel is less bounded, the more likely uplink method would be via some type of cellular or satellite network connection. However, if WiMAX begins to be deployed in larger areas, either could be an acceptable uplink method for trains, buses, or automobiles.
Commuter ferries are likely to provide uplink services via cellular or WiMAX, because they are likely within range of these services. For ferries that travel farther distances away from shore and cruise ships, a satellite link is typically used.
Many airlines either have installed or are in the process of installing Wi-Fi on their planes. The Wi-Fi service in the plane consists of one or more access points connected either to a cellular router that communicates with a skyward facing network of cellular towers on the ground or to a satellite router that uplinks that data to a satellite and then to a terrestrial station. The cellular-based system requires a network of terrestrial-based cellular receivers; therefore, it is not used for transoceanic flights. This in-flight service is typically offered for a nominal fee and is available only while the airplane is flying and when the airplane is at cruising altitude. Bandwidth metering is used to prevent any one user from monopolizing the connection.
Law Enforcement Networks
Although Wi-Fi networks cannot provide the wide area coverage necessary to provide continuous wireless communications needed by law enforcement personnel, they can still play a major role in fighting crime. Many law enforcement agencies are using Wi-Fi as a supplement to their public safety wireless networks.
In addition to the obvious mobility benefits of using Wi-Fi inside police stations, many municipalities have installed Wi-Fi in the parking lots outside the police station and other municipal buildings as a supplement to their wireless metropolitan networks. These outdoor networks are sometimes viewed as secured hotspots. Unlike public hotspots, these networks provide both authentication and high levels of encryption. In addition to municipalities incorporating wireless technology into law enforcement, many are adding non-Wi-Fi-based automation to utilities through the use of supervisory control and data acquisition (SCADA) equipment. Because of this growth in the use of different wireless technologies, we are starting to see municipalities designate a person or department to keep track of the frequencies and technologies that are being used.
Municipal Wi-Fi hotspots typically provide high-speed communications between networking equipment in the police cars and the police department's internal network. An interesting example of a good use of this network is the uploading of vehicle video files. With many police cars being equipped with video surveillance, and with these surveillance videos often being used as evidence, it is important to not only transfer these video files to a central server for cataloging and storage, but to also do it with the least amount of interaction by the police officer to preserve the chain of evidence.
When a police car arrives at one of these municipal Wi-Fi hotspots, the computer in the car automatically uploads the video files from the data storage in the car to the central video library. Automating this process minimizes the risk of data corruption and frees up the officer to do other, more important tasks.
First-Responder Networks
When medical and fire rescue personnel arrive at the scene of an emergency, it is important for them to have fast and easy access to the necessary resources to handle the emergency at hand. Many rescue vehicles are being equipped with either permanently mounted Wi-Fi access points or easily deployed, self-contained portable access points that can quickly and easily blanket a rescue scene with a Wi-Fi bridge to the emergency personnel's data network. In a disaster, when public service communications systems such as cellular phone networks may not be working because of system overload or outages, a Wi-Fi first-responder network may be able to provide communications between local personnel and possibly shared access to central resources.
During a disaster, assessing the scene and triaging the victims (grouping victims based on the severity of their injuries) is one of the first tasks. Historically, the task of triage included paper tags that listed the medical information and status of the victim. Some companies have created electronic triage tags that can hold patient information electronically and transmit it via Wi-Fi communications.
Fixed Mobile Convergence
One of the hot topics relating to Wi-Fi is known as fixed mobile convergence (FMC). The goal of FMC systems is to provide a single device, with a single phone number that is capable of switching between networks and always using the lowest-cost network. Figure 11.6 illustrates an FMC phone network.
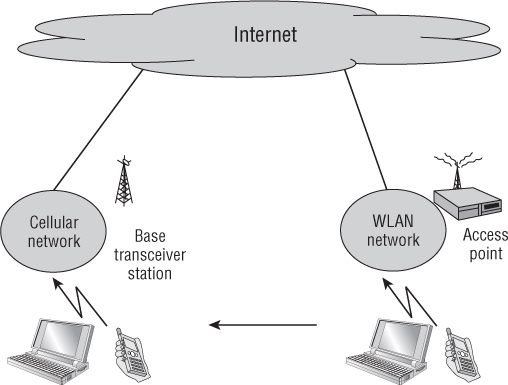
Figure 11.6 FMC network design
With the flexibility and mobility of cellular phones, it is common for people to use them even in environments (home or work) where they are stationary and have access to other phone systems that are frequently less costly. FMC devices typically are capable of communicating via either a cellular phone network or a VoWiFi network. If you had an FMC phone and were at your office or home, where a Wi-Fi network is available, the phone would use the Wi-Fi network for any incoming or outgoing phone calls. If you were outside either of these locations and did not have access to a Wi-Fi network, the phone would use the cellular network for any incoming or outgoing phone calls.
FMC devices also allow you to roam across networks, so you could initiate a phone call from within your company by using the Wi-Fi network. As you walk outside, the FMC phone would roam from the Wi-Fi network to the cellular network and seamlessly transition between the two networks. With fixed mobile convergence, you would be able to have one device and one phone number that would work wherever you were, using the least costly network that was available at the time.
WLAN and Health
Over the years, there has been a concern about adverse health effects from the exposure of humans and animals to radio waves. The World Health Organization and government agencies set standards that establish exposure limits to radio waves, to which RF products must comply. Tests performed on WLANs have shown that they operate substantially below the required safety limits set by these organizations. Also, Wi-Fi signals, as compared to other RF signals, are much lower in power. The World Health Organization has also concluded that there is no convincing scientific evidence that weak radio-frequency signals, such as those found in 802.11 communications, cause adverse health effects.
You can read more about some of these findings at the following websites:
- U.S. Federal Communications Commission:
transition.fcc.gov/oet/rfsafety/rf-faqs.html - World Health Organization:
www.who.int/peh-emf - Wi-Fi Alliance:
www.wi-fi.org
WLAN Vendors
There are many vendors in the 802.11 WLAN marketplace. The following is a list of some of the major WLAN vendors. Please note that each vendor is listed in only one category, even if they offer products and services that cover multiple categories. This is most notable with the infrastructure vendors, who often offer additional capabilities as features of their products, such as security and troubleshooting.
- WLAN Infrastructure These 802.11 enterprise equipment vendors manufacture and sell controllers and access points:
- Aerohive Networks:
www.aerohive.com - AirTight Networks:
www.airtightnetworks.com - Aruba Networks:
www.arubanetworks.com - Cisco Systems:
www.cisco.com - Extreme Networks:
www.extremenetworks.com - Extricom:
www.extricom.com - Hewlett-Packard:
www.hp.com - Juniper Networks:
www.juniper.net - Meru Networks:
www.merunetworks.com - Motorola:
www.motorolasolutions.com - Proxim Wireless Corporation:
www.proxim.com - Ruckus Wireless:
www.ruckuswireless.com - Ubiquiti Networks:
www.ubnt.com - Xirrus:
www.xirrus.com
- Aerohive Networks:
- WLAN Mesh Infrastructure These WLAN vendors specialize in 802.11 mesh networking:
- Ericsson:
www.ericsson.com - Firetide:
www.firetide.com - General Dynamics C4 Systems:
www.gdc4s.com/wireless - MeshDynamics:
www.meshdynamics.com - Strix Systems:
www.strixsystems.com - Tropos Networks:
www.tropos.com
- Ericsson:
- WLAN Troubleshooting and Design Solutions These are some companies that make and/or sell 802.11 protocol analyzers, spectrum analyzers, site survey software, RTLS software, and other WLAN analysis solutions:
- AeroScout:
www.aeroscout.com - Berkeley Varitronics Systems:
www.bvsystems.com - Ekahau:
www.ekahau.com - Euclid Analytics:
www.euclidanalytics.com - Fluke Networks:
www.flukenetworks.com - MetaGeek:
www.metageek.net - Riverbed Technology:
www.riverbed.com - TamoSoft:
www.tamos.com - WildPackets:
www.wildpackets.com - Wireshark:
www.wireshark.org - 7signal:
www.7signal.com
- AeroScout:
- WLAN Security Solutions These WLAN companies offer client onboarding solutions or 802.1X/EAP supplicant/server solutions:
- Cloudessa:
cloudessa.com - Cloudpath Networks:
www.cloudpath.net
- Cloudessa:
- VoWiFi Solutions Manufacturers of 802.11 VoWiFi phones and VoIP gateway solutions include the following:
- Ascom:
www.ascom.com - ShoreTel Networks:
www.shoretel.com - Spectralink:
www.spectralink.com - Vocera:
www.vocera.com
- Ascom:
- Mobile Device Management Vendors These are some of the WLAN vendors selling mobile device management (MDM) solutions:
- Airwatch:
www.air-watch.com - JAMF Software:
www.jamfsoftware.com - Mobile Iron:
www.mobileiron.com
- Airwatch:
- WLAN SOHO Vendors These are some of the many WLAN vendors selling SOHO solutions that can provide Wi-Fi for the average home user:
- Apple:
www.apple.com - Belkin International:
www.belkin.com - Buffalo Technology:
www.buffalotech.com - D-Link:
www.dlink.com - Hawking Technology:
www.hawkingtech.com - Netgear:
www.netgear.com - SMC Networks:
www.smc.com
- Apple:
Summary
This chapter covered some of the design, implementation, and management environments in which wireless networking is used. Although many of these environments are similar, each has unique characteristics. It is important to understand these similarities and differences and how wireless networking is commonly deployed.
Exam Essentials
- Know the different WLAN vertical markets. Wireless networking can be used in many environments, with each vertical market having a different primary reason or focus for installing the wireless network. Know these environments and their main reasons for deploying 802.11 wireless networking.
- Know fixed mobile convergence. With cellular networking and Wi-Fi networking so common, phone vendors are beginning to provide phones that are capable of communicating over both networks and provide roaming between them. Know what FMC is and the reasons and benefits of deploying it.
Review Questions
- Which of the following are objectives of fixed mobile convergence? (Choose all that apply.)
- Have a single phone number.
- Have a single device.
- Always use the best-performing network.
- Use the lowest-cost network.
- Which of the following is another form of a public hotspot network? (Choose all that apply.)
- Law enforcement network
- First-responder network
- Transportation network
- Municipal network
- Which type of organization often has a person responsible for keeping track of frequency usage inside the organization?
- Law enforcement
- Hotspot
- Hospital
- Cruise ship
- On which of these transportation networks is satellite a functional solution for providing uplink to the Internet?
- Bus
- Automobile
- Train
- Cruise ship
- Fixed mobile convergence provides roaming across which of the following wireless technologies? (Choose all that apply.)
- Bluetooth
- Wi-Fi
- WiMAX
- Cellular phone
- Which of the following is typically the most important design goal when designing a warehouse WLAN?
- Capacity
- Throughput
- RF interference
- Coverage
- Corporations often install wireless networks to provide which of the following capabilities? (Choose all that apply.)
- Easy mobility for the wireless user within the corporate building or campus environment
- Highest-speed network access when compared with wired networking
- Internet access for visitors and guests
- The ability to easily add network access in areas where installation of wired connections is difficult or expensive
- Last-mile Internet service is provided by which of the following? (Choose all that apply.)
- Telephone company
- Long-distance carrier
- Cable provider
- WISPs
- Which of the following is the main purpose of a SOHO 802.11 network?
- Shared networking
- Internet gateway
- Network security
- Print sharing
- Which of the following are examples of mobile office networking? (Choose all that apply.)
- Construction-site offices
- Temporary disaster-assistance office
- Remote sales office
- Temporary classrooms
- Warehousing and manufacturing environments typically have which of the following requirements? (Choose all that apply.)
- Mobility
- High-speed access
- High capacity
- High coverage
- Which of the following is least likely to be offered by a hotspot provider?
- Free access
- Paid access
- Network authentication
- Data encryption
- Which of the following are good uses for portable networks? (Choose all that apply.)
- Military maneuvers
- Disaster relief
- Construction sites
- Manufacturing plants
- Which of the following terms refer to a PTMP network design? (Choose all that apply.)
- PTP
- Mesh
- Hub and spoke
- Star
- Most early deployments of 802.11 FHSS were used in which type of environment?
- Mobile office networking
- Educational/classroom use
- Industrial (warehousing and manufacturing)
- Healthcare (hospitals and offices)
- When using a hotspot, you should do which of the following to ensure security back to your corporate network?
- Enable WEP.
- Enable 802.1X/EAP.
- Use an IPsec VPN.
- Security cannot be provided because you do not control the access point.
- What are some popular 802.11 applications used in the healthcare industry? (Choose all that apply.)
- VoWiFi
- Bridging
- RTLS
- Patient monitoring
- Multiple point-to-point bridges between the same locations are often installed for which of the following reasons? (Choose all that apply.)
- To provide higher throughput
- To prevent channel overlap
- To prevent single point of failure
- To enable support for VLANs
- What are some of the key concerns of healthcare providers when installing a wireless network? (Choose all that apply.)
- RF interference
- Faster access to patient data
- Secure and accurate access
- Faster speed
- Public hotspots typically provide clients with which of the following security features?
- Server authentication.
- Encryption.
- TKIP.
- No client security is available.
