This chapter discusses how network management is designed and includes the following sections:
This chapter describes network management design. After introducing the importance of effective network management, we describe the related International Organization for Standardization (ISO) standard and then explore various protocols and tools available. The chapter includes a description of network management strategy and discusses how performance measurements can be made to ensure that requirements are being met. We conclude with a discussion of network management design considerations, including the importance of security.
Note
Appendix B, “Network Fundamentals,” includes material that we assume you understand before reading the rest of the book. Thus, we encourage you to review any of the material in Appendix B that you are not familiar with before reading the rest of this chapter.
As you have seen in previous chapters in this book, many technologies can be involved in today’s networks. After the network has been designed and implemented, all of these technologies must then be managed.
Recall from Chapter 1, “Network Design,” how important it is to clearly define the requirements of the network. When deciding on the network management strategy, protocols, and tools, it is also critical to go back to those requirements; only then can you determine what is valuable to measure and track.
Being proactive, rather than reactive, is crucial to managing your network. This means that you need to understand both the business’s and the end users’ perspectives and priorities, and manage the network so that their expectations are met. To do this, you need to understand the network and have baseline measurements so that you can see that something might be going wrong, before it causes a problem. As networks are being used for more applications (for example, Voice over IP [VoIP], e-commerce, and so forth), they are getting more complicated, which in turn complicates the management of the network.
Effective network management is crucial to ensuring the success of today’s businesses that rely so heavily on their networks. The key to effective network management is to recognize that a network exists to meet the needs of the business—the requirements. Therefore, network management should not be managing the technology for technology’s sake, but as a means to meet these requirements—delivering an appropriate level of service, at an appropriate cost. For example, network management must go beyond traditional measurements (such as effective bandwidth) and instead focus on the availability of critical applications, because those are what the business relies on.
As network management became vital to businesses, ISO developed a standardized framework known as fault, configuration, accounting, performance, and security management (FCAPS). These five functional areas of network management are defined as follows:
Fault management—. Detects, isolates, notifies users about, and corrects faults that occur in the network
Configuration management—. Tracks and maintains network configuration information, including device inventory, configuration files, and software
Accounting management—. Tracks device and network resource usage
Performance management—. Monitors and collects performance measurements from network devices and analyzes the information so that network performance can be proactively managed to meet requirements
Security management—. Controls and logs access to network resources in support of security polices
FCAPS can serve as a reminder of areas of management that need to be included as you design your network. The following sections introduce you to a wide variety of protocols and tools that are available for network management.
In this section, we first introduce some terminology that is related to network management protocols. This is followed by a discussion of the following protocols and tools:
We conclude with a discussion of some other network management tools that are available.
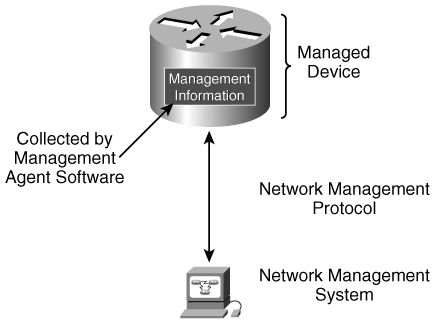
Figure 9-1 illustrates some terms that are related to network management; the terms are described as follows:
Managed device—. A device (for example, a router or a switch) that is to be managed
Management information—. Data used for and collected during the management of a device
Management agent—. Software on a managed device that collects and stores management information
Network management system—. A system that includes the applications that monitor and control managed devices
Network management protocol—. A protocol that exchanges management information between the network management system and managed devices
SNMP is the simplest network management protocol. The management information standard is the MIB, a detailed definition of the information on a managed device. MIB data is accessible through a network management protocol, such as SNMP. The RMON standard is an extension to the MIB; while the MIB only provides static information about a managed device, an RMON agent creates specific groups of statistics that can be collected for long-term trend analysis. These standards are described in the following sections.
Key Point
SNMP is an IP application protocol that runs on top of User Datagram Protocol (UDP) to transport management data. It allows both the configuring and retrieval of management information.
The initial SNMP version 1 (SNMPv1) was extended to SNMP version 2 (SNMPv2) and its variants and then further extended to SNMP version 3 (SNMPv3).
SNMPv1 defines five message types between the management application and management agents, as follows:
Get request—. Requests a specific MIB variable from the agent
Get next request—. Retrieves the next object from a table or list after the initial get request
Set request—. Sets a MIB variable on an agent
Get response—. A response to a get request or get next request from a manager
Trap message—. Sends an unsolicited alarm to the manager, for example, when a device detects a failure
SNMPv2 includes the following two new message types:
GetBulk—. Retrieves large amounts of data (for example, tables) in one request so that multiple get next request messages are no longer needed
InformRequest—. Similar to the SNMPv1 trap message
SNMPv3 (implemented on Cisco routers in Internetwork Operating System [IOS] Release 12.0 and later) adds security, including the ability to add authentication and privacy to SNMP communication on a per-user or group-of-users basis. This can be used, for example, to define which objects a user can read or write, and which notifications a user can receive.
A MIB is a standard for collecting management information.
Key Point
A MIB stores the information gathered by a management agent locally on a managed device, for later retrieval by a network management protocol.
Note
The MIB acronym is usually pronounced as a word (that rhymes with bib), not as individual letters.
As shown in Figure 9-2, the MIB structure is logically represented as a tree hierarchy. The root of the tree is not named and splits into three main branches: Consultative Committee for International Telegraph and Telephone (CCITT), ISO, and joint ISO/CCITT.
The branches in the MIB tree are identified by short text strings and integers, which form object identifiers. For example, the Internet standard MIB is represented by the object identifier 1.3.6.1.2.1; this can also be written as iso.org.dod.internet.mgmt.mib. Each object in a MIB has a unique object identifier. Network management applications specify this identifier when they want to set or retrieve a specific object.
Along with the standard MIBs, vendors can reserve their own private branch of the MIB, under which they can create custom objects. For example, Cisco devices have objects in the private section of the MIB tree (1.3.6.1.4.1.9, or iso.org.dod.internet.private.enterprise.cisco) for parameters related to Cisco’s proprietary protocols and other variables. As an example, the Cisco 3800 Series integrated services router’s object identifier is 1.3.6.1.4.1.9.1.544.
Standard MIBs are defined in different Requests For Comments (RFCs). MIB-II, defined by RFC 1213 (“Management Information Base for Network Management of TCP/IP-based Internets: MIB-II”), is an extension of the original MIB (which is now called MIB-I). MIB-II supports some new protocols and provides more detailed and structured information.
RMON is defined as part of the MIB-II collection of objects. RMON not only collects and stores data, but RMON agents within managed objects (or on separate RMON probe devices) also perform some analysis of the data. For example, RMON data can include statistical information for conversations between two hosts, from the perspective of the managed object. The RMON MIB is 1.3.6.1.2.1.16 (iso.ord.dod.internet.mgmt.mib.rmon). Because RMON agents must look at every frame on the network, they can cause performance problems on a managed device. Thus, separate RMON probes can be used to offload the processing to another device.
RMON1 provides statistics at the data link and physical layers of the Open Systems Interconnection (OSI) model, while RMON2 extends RMON1 through to the application layer, as illustrated in Figure 9-3 and described in the following sections.
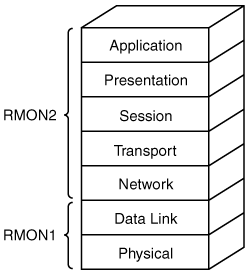
Figure 9-3. RMON1 Provides Visibility at the Lower Two Layers While RMON2 Extends to the Upper Layers
RMON1, defined in RFC 2819, “Remote Network Monitoring Management Information Base,” provides statistics and analysis for remote LAN segments.
Key Point
RMON1 works at the data link layer and physical layer. It therefore provides information relating to Media Access Control (MAC) addresses and LAN traffic.
RMON1 defines nine groups of statistics (ten, including Token Ring extensions, defined in RFC 1513, “Token Ring Extensions to the Remote Network Monitoring MIB”) that can be implemented by RMON1 agents and that can then be requested by the network management system. The RMON1 groups are as follows:
Statistics—. Contains real-time statistics for each monitored interface on the device, including, for example, the number of packets and bytes sent, the number of broadcast and multicast packets, and so forth
History—. Stores periodic statistical samples
Alarm—. Contains specific thresholds for managed objects that, when reached, trigger an event, as specified in an events group
Host—. Contains statistics associated with each host that is discovered on the network
HostTopN—. Contains statistics for the top N hosts on a list ordered by one of their observed variables
Matrix—. Contains statistics for conversations between sets of two hosts
Filters—. Contains definitions of packet filters that generate events or define what should be stored locally in a packet capture group
Packet capture—. Contains data packets that matched filters
Events—. Controls the generation and notification of alarms or filters on the device
TokenRing—. Contains Token Ring interface statistics
RMON2 is defined in RFC 2021, “Remote Network Monitoring Management Information Base Version 2 using SMIv2.”
Key Point
RMON2 is not a replacement for RMON1, but an extension to it. RMON2 adds nine more groups that provide the visibility into the upper layers.
With RMON2, conversations can be viewed at the network and application layers. For example, statistics can be gathered for traffic generated by a specific application on a specific host, such as a file-transfer program.
The RMON2 groups added are as follows:
Protocol directory—. Holds a list of the protocols supported by the device
Protocol distribution—. Contains traffic statistics for each of the supported protocols
Address mapping—. Provides a mapping of network layer addresses to MAC addresses
Network layer host—. Contains statistics for the network layer traffic to or from each host
Network layer matrix—. Contains network layer traffic statistics for conversations between sets of two hosts
Application layer host—. Contains statistics for the application layer traffic to or from each host
Application layer matrix—. Contains application layer traffic statistics for conversations between sets of two hosts
User history collection—. Contains periodic samples of user-specified variables
Probe configuration—. Provides a standard way to remotely configure probe parameters
RFC 3577, “Introduction to the Remote Monitoring (RMON) Family of MIB Modules,” describes RMON1 and RMON2; it also has references to various RMON extensions needed to support today’s networks, including the following:
RFC 2613, “Remote Network Monitoring MIB Extensions for Switched Networks Version 1.0,” defines objects for managing remote network-monitoring devices in switched network environments.
RFC 3144, “Remote Monitoring MIB Extensions for Interface Parameters Monitoring,” defines a method of sorting the interfaces of a monitored device according to values of parameters specific to the interfaces.
RFC 3273, “Remote Network Monitoring Management Information Base for High Capacity Networks,” defines objects for managing remote network-monitoring devices for use on high-speed networks.
RFC 3287, “Remote Monitoring MIB Extensions for Differentiated Services,” describes managed objects used to monitor Differentiated Services Code Point (DSCP) usage in packets that contain a DSCP field. Recall that DSCP values indicate or mark the type of traffic; this marking can then be used by other tools to provide the appropriate quality of service (QoS) for that traffic.
Cisco NetFlow technology allows the measurement of flows that pass through devices.
Key Point
A network flow is a unidirectional stream of packets between a given source and destination. A flow is very granular—it can be defined by the source and destination IP addresses, source and destination port numbers, protocol type, type of service (ToS), and input interface.
NetFlow has two key components:[2] the NetFlow cache, which stores the flow information, and the NetFlow export mechanism, which sends the flow data to a network management collector for data reporting.
NetFlow can benefit the network in the following ways:
NetFlow can be used to monitor network data, application use, and users. Billing or other accounting can be done based on network flows, allowing intercompany or customer charges to be based on actual usage. Aggregated usage data can also be helpful for other uses, such as marketing efforts (for example, for keeping track of who is using which data) and when planning an upgrade to the network.
The NetFlow cache switches packets that belong to a flow, resulting in faster processing of those packets.
How does NetFlow compare with RMON? NetFlow provides more detailed information and more types of data on a per-interface basis, and can scale to include more interfaces. NetFlow has less of a performance impact than RMON and does not require external probes.
Cisco network devices, such as routers and switches, produce messages with the following format:
The portions of this code are described as follows:
mm/dd/yy:hh/mm/ss—. The timestamp, if enabled.
FACILITY—. The hardware device, protocol, or module of the system software to which the message pertains. Some examples of the facility are IP, IF (for interface), and LINK (for data link).
SEVERITY—. A number from 0 to 7 that indicates the severity of the condition, as follows:
Emergency (level 0, which is the highest level)
Alert (level 1)
Critical (level 2)
Error (level 3)
Warning (level 4)
Notice (level 5)
Informational (level 6)
Debugging (level 7)
MNEMONIC—. Uniquely identifies the error message.
Message-text—. A text string that further describes the event, including, for example, addresses, port numbers, and so forth.
These messages are sent to console sessions by default, but devices can be configured to send the messages to a syslog server. A syslog server is a server that runs a syslog application, a standard for logging system messages. The messages can then be retrieved and analyzed by the network manager.
Note
Syslog output generated by network devices is clear text, so for security purposes, it could be sent to the syslog server using an encrypted communication channel, such as a virtual private network (VPN) tunnel. This is most important when the syslog data is traversing a publicly accessible network, such as a demilitarized zone.
Cisco has a variety of network management products; the full portfolio is listed on the Network Management Products and Services page on the Cisco website (http://www.cisco.com/en/US/products/sw/netmgtsw/index.html).
CiscoWorks is the Cisco network management application. CiscoWorks is available either as stand-alone applications or as bundles of tools for specific uses. For example, the CiscoWorks LAN Management Solution (LMS) version 2.5 bundles the following components to allow the configuration, administration, monitoring, and troubleshooting of networks:[3]
CiscoWorks Device Fault Manager (DFM)—. Provides real-time, detailed detection, analysis, and reporting of faults that can occur on Cisco devices
CiscoWorks Campus Manager (CM)—. Includes tools for configuring, managing, visualizing, and identifying discrepancies in OSI Layer 2 infrastructures
CiscoWorks Resource Manager Essentials (RME)—. Provides tools for managing network inventory, device configurations and changes, and software updates
CiscoWorks Internetwork Performance Monitor (IPM)—. Performs proactive measurement of network response time and availability, providing both real-time and historical analysis of congestion and latency problems
CiscoWorks CiscoView (CV)—. Provides graphical displays of Cisco devices so that users can easily interact with device components to change configuration parameters and monitor statistics
CiscoWorks Common Services (CS)—. Is an application infrastructure for all CiscoWorks applications, providing common data storage, login, user role definitions, access privileges, and security protocols
In a recent Networkers presentation, Cisco included a simplified network management framework and some of the suggested tools that would help to manage each aspect within the framework, as illustrated in Figure 9-4.
This framework includes the five elements of the FCAPS model, as described in the “ISO Network Management Standard” section, earlier in this chapter. In addition, the following four new elements are introduced:
Inventory management—. Procedures and processes for maintaining an up-to-date inventory of all assets
Change management—. Procedures, documentation, systems, and metrics for successfully managing change within an organization
Event management—. Procedures and processes for managing significant events within the network, including faults, security breaches, and so forth
Problem management—. Systems, procedures, and organizational structure for documenting, tracking, reporting, resolving, and analyzing problems
The tools mentioned in Figure 9-4 that we have not already introduced include the following:
CiscoWorks VPN/Security Management Solution (VMS)—. Includes Web-based tools for configuring, monitoring, and troubleshooting VPNs, firewalls, network intrusion detection systems (IDSs), and host intrusion prevention systems (IPSs). CiscoWorks VMS also includes network device inventory, change audit, and software distribution features.
MicroMuse Netcool—. Tools for collecting and consolidating real-time data from the network, and then analyzing and acting upon the results (http://www.micromuse.com).
Remedy’s Action Request System (ARS)—. Platform and development environment for automating service management business processes (http://www.remedy.com).
Concord eHealth—. For performance management, including measuring and monitoring application performance management (http://www.concord.com).
HP OpenView (OV) Network Node Manager (NNM)—. For network discovery, identifying network problems, monitoring, and alarm management (http://www.openview.hp.com/products/nnm/index.html).
A variety of other network management tools are available, many of which are also discussed in this same Networkers presentation (see http://www.cisco.com/warp/public/732/Tech/grip/docs/deploymanage.pdf).
One network analysis tool available for 802.11a/b/g wireless LANs (WLANs) is Fluke’s OptiView Series II Integrated Network Analyzer (http://www.flukenetworks.com/) equipped with the wireless option.
Note
The tools mentioned in this chapter are examples of available tools and are provided for your information only; their inclusion here does not represent an endorsement or recommendation by the authors.
Another tool that can be useful for network management is the Cisco Network-Based Application Recognition (NBAR) classification software feature, running within the IOS on Cisco routers. As mentioned in Chapter 6, “Quality of Service Design,” NBAR allows classification (and marking) of a wide variety of applications, including web-based and other difficult-to-classify protocols that use dynamic Transmission Control Protocol (TCP)/UDP port assignments.
One more tool, specifically for managing networks of small to medium businesses (SMBs)—which Cisco defines as having 250 employees or less—is the Cisco Network Assistant Windows-based management application.[5] Network Assistant can be used to manage Cisco switches, routers, access points, and IP phones, and includes configuration management, inventory reporting, password synchronization, and IOS upgrade capability. This tool also includes the Smartports Advisor, which automatically detects the type of device connected to a switch port (for example, an IP phone, a wireless access point, or a PC) and then applies Cisco’s recommended best-practice configuration to the port appropriate for that device.
Now that we have explored some of the various network management tools and protocols available, we next look at how these can be incorporated into a strategy for successfully managing a network, including service-level contracts (SLCs) and service-level agreements (SLAs).
It is important to develop a network management strategy that details what information is to be collected from each device and how that information is to be analyzed. The appropriate protocols and tools, as described in the previous section, can then be selected.
Thresholds should be set so that alerts or alarms can be raised if parameters start to go out of range. To determine what these threshold levels should be, baseline measurements can be taken to create a snapshot of the “working” network. Instead of waiting for a failure and reacting to it, alerts and alarms relative to baseline measurements help the network manager to be proactive and solve problems before the network is adversely affected.
Cisco recommends the following network management best practices:[6]
Keep an archived copy of the software images (for example, Cisco IOS) and configurations of all devices.
Keep an up-to-date inventory and log any configuration and software changes.
Monitor critical parameters, including any syslog-reported errors, SNMP traps, and RMON statistics that are important for your network.
Use tools to identify any configuration discrepancies (for example, CiscoWorks Campus Manager can detect inconsistent trunking configurations on switch ports).
SLCs and SLAs can also be a part of a network management strategy.
Key Point
An SLC specifies connectivity and performance levels for the service’s end user, to be met by the service provider.
SLAs define specific service performance measurements between pairs of devices, for example, between a router and a server.
An SLC typically includes multiple SLAs, so a violation of any particular SLA could result in a violation of the overall SLC.
The service provider could be either within the organization—for example, an IT department providing services to internal users—or an external company, such as an ISP providing hosted application services.
Traditional SLCs and SLAs concentrated on measurements over a specific network; for example, Frame Relay committed information rates. However, today’s complex applications, including VoIP, for example, require end-to-end guarantees of service levels. For this type of environment, a new way of measuring and ensuring network performance is required. The Cisco IP SLAs technology, described in the next section, provides this functionality.
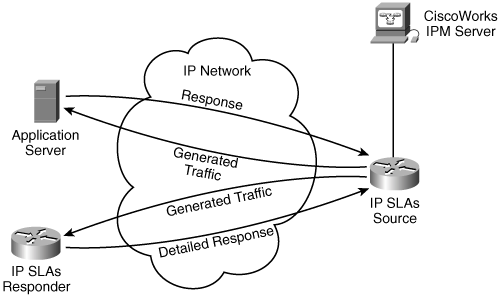
Cisco IOS IP SLAs[7] technology is embedded in most IOS devices to allow users to analyze service levels being experienced by IP applications. IP SLAs allows test traffic to be generated and then measures the performance of that traffic through the network, either between Cisco IOS devices or from a Cisco IOS device to a remote device such as a server. Figure 9-5 illustrates IP SLAs operation.
In Figure 9-5, the IP SLAs source generates some traffic destined for the application server, similar to an extended ping. The server’s response includes a timestamp, which can then be used by the source to determine the network delay. The IP SLAs source also generates traffic destined for the IP SLAs responder device, which has IP SLAs software enabled. In this case, the response is more detailed, including, for example, the processing delays within the device.
Note
The Cisco IOS IP SLAs monitoring and management feature set replaced the Cisco IOS Service Assurance Agent (SAA) feature in Cisco IOS Release 12.3(14)T. [8] This feature set incorporates most of the features available in SAA, and SAA commands have been replaced by the IP SLAs monitor’s command set and configuration structure.
The traffic generated by IP SLAs simulates real data by allowing many options to be configured, including source and destination IP addresses, UDP/TCP port numbers, ToS (either DSCP or IP precedence bits), VPN routing/forwarding instance (VRF), and Uniform Resource Locator (URL) web address. IP SLAs can be configured end to end over an entire network to best represent the metrics that an end user is likely to experience.
Measurements taken can include response time, latency, jitter, packet loss, voice quality scoring, network resource availability, application performance, and server response time.
IP SLAs is accessible using the command-line interface or SNMP. Performance-monitoring applications such as CiscoWorks IPM and other third-party Cisco partner performance management products can also use SNMP to configure and retrieve information from IP SLAs.
Recall from Chapter 1 that the Enterprise Composite Network Model Enterprise Campus functional area includes a Management module that encompasses the network management functions. The Management module provides monitoring, logging, security, and other management features to the campus. The Cisco SAFE blueprint (available at http://www.cisco.com/go/safe) provides recommendations for what should be included in this module and how it should be secured. The devices and services provided within this module are illustrated in Figure 9-6.
The Management module contains one or more of the following:
Authentication server—. Provides strong authentication services for remote and local users on the network. An example is a two-factor, one-time password (OTP) system based on token cards (as described in Chapter 4, “Network Security Design”).
Access control server—. Provides centralized command and control for all user authentication, authorization, and accounting (AAA).
Network-monitoring server—. Is responsible for monitoring the devices in the network.
Host intrusion prevention system (HIPS)/network intrusion detection system (NIDS) management server—. Provides configuration and viewing of alarms on IDS and IPS sensors deployed throughout the campus network.
Syslog server—. Collects network events and traps.
System administration server—. Configures network management and other network devices.
Because the management network provides administrative access to the rest of the network it must be secure. The previously mentioned servers, and the routers that act as terminal servers (to provide a reverse Telnet to the console port of devices throughout the rest of the network), are on the inside segment of a firewall router. An outside segment connects to all the devices that require management, on a separate network, for SNMP and other management traffic. These two segments provide out-of-band (OOB) management—the management data is separate from other traffic, providing a first level of security for this critical data. A third interface connects to the production network for in-band management where it is required; this segment should be encrypted with IPsec so that management traffic cannot be compromised.
Other security features implemented in the management module can include the following:[10]
Use of secure shell (SSH), a protocol similar to Telnet, but with encryption, for configuration.
SNMP read-only access, so that SNMP’s clear-text password cannot be used to make configuration changes.
Possible use of SNMPv3 with encryption, on either the in-band or out-of-band management network.
Private virtual LANs (VLANs) on the management module switches so that traffic cannot travel from one device to another over the management network; it instead goes to the firewall to ensure only authorized access.
Other design considerations for the network management module include the following:
The number of network management systems required, depending on the number of end-user and other devices, the amount of data to be collected, and the capacity of the systems.
The effect of Network Address Translation (NAT) (described in Chapter 3, “IPv4 Routing Design”) and firewalls on management protocols. For example, SNMP is not compatible with NAT because addresses are embedded within the SNMP data.
The bandwidth required for management data. For example, if a lot of syslog messages are sent across a WAN, the bandwidth can become a bottleneck.
In this chapter, you learned about network management design, including the following topics:
Why effective and secure network management is critical
The various protocols and tools available, including SNMP, MIB, RMON, NetFlow, syslog, and CiscoWorks
SLCs and SLAs, and the IP SLAs technology embedded in Cisco IOS that allows users to analyze service levels being experienced by IP applications
Network management design considerations, including security of this critical traffic

![Internet MIB Hierarchy[1]](http://imgdetail.ebookreading.net/design/12/1587052229/1587052229__campus-network-design__1587052229__graphics__09fig02.gif)
![Cisco Network Management Framework[4]](http://imgdetail.ebookreading.net/design/12/1587052229/1587052229__campus-network-design__1587052229__graphics__09fig04.gif)
![Management Module Provides Monitoring, Logging, and Security Functions [9]](http://imgdetail.ebookreading.net/design/12/1587052229/1587052229__campus-network-design__1587052229__graphics__09fig06.gif)