8
Discourse Regarding China: Cyberspace and Cybersecurity
The significant position acquired, in recent years, by discourse analysis in studies conducted in international relations is, to a large extent, attributable to the success of the constructivist paradigm (Nicolas G. Onuf1, Alexander Wendt2, Thomas Lindemann3), and notably to the techniques of the Copenhagen School (security theories).4
Discourse is not a way of learning something about a reality, but rather a way of producing reality, rendering something a reality.5 The basic premise of discourse theory runs that the way in which we think and say things reflects the way in which we act in relation to the object of that discourse.6 Thus, according to this view, there exists no real world untouched by our thoughts, our ideas, and it would be useless to try to distinguish fixed political and social structures, a static reality, independently of our own interpretation of it.7
This theory also postulates that language is a form of social power. The social implications of discourse lie in its power to influence, its persuasive nature, its capacity to alter ideas, beliefs and behaviors.8 Discourse is a social practice which produces the effects of power, i.e. which is aimed at dominating other people.9
Discourse analysis, which is a relatively recent method in the field of international relations10, is commonly used to reveal the established relations between discourse and political practice11, in order to understand the way in which the textual and social processes are connected, and what the implications of those connections are12: how and why the political conditions behind the discourse arise13; to reveal the intentions inherent in the discourse14; to identify the discursive strategies employed to legitimize15 political actions (consensus- or consent-seeking; discourse in the service of a particular ideology; etc.).16
In this chapter, we examine the changes in the way in which China is viewed (representations, perceptions), by way of analysis of the discourse on the subject of China and its relation with the issues of cyberspace, Cybersecurity and cyberdefense strategies.
The corpora upon which this analysis is founded are as follows:
– for our first section, aimed at identifying the main themes in discourse and research about China (cyberspace, Cybersecurity), we use a very large corpus comprising essentially academic work and resources available on the Internet. We have limited the scope of our observation to resources in English and French;
– for the second section, where the goal is to study the arguments of discourse circulating within the American institutions of power, we draw upon three sources: the annual reports submitted by the Department of Defense to the United States Congress; the projections published by the National Intelligence Council; and the discourse of the successive US Secretaries of Defense. These sources enable us to cover a sufficiently long period of time (DoD annual reports are available for 2002 onwards; the NIC reports for 1997 onwards; and the speeches made by the Secretaries of Defense, online archives begin in 1995), offer the advantage of being available online in their entirety, and reflect the viewpoints of the people in power: the political and military decision-makers, and influential personalities.
To illustrate this discourse, we give many long verbatim quotes, but also show summaries in table form so as to clearly reveal the evolution in terms of themes. The aim is to demonstrate the variables of the available discourses, the relationships between them, and the evolution of those discourses, over the past two decades. This initial analysis could, undoubtedly, later be supplemented by work on the evolution of the discourse conveyed through the media, but also in industrial environments. Finally, an additional project could address the more complex task of reconstructing the path of various ideas (where they first surface; what paths they follow as they are diffused; who has the power to influence). In this chapter, we limit this study of the evolution of ideas to identifying the scenarios which have emerged over the past 20 years.
8.1. Identification of prevailing themes
By way of a state of the art on the work conducted on the subject of China – particularly its relationship to cyberspace – we can see that the discourse on China is organized around relatively few themes, types of discourse, arguments, viewpoints.
8.1.1. Depictions of the Internet in China
Many research projects have been conducted on the topic of China’s Internet from a historical point of view (when it came about, how its industries have developed, who the designers of the Chinese Net are), from a statistical standpoint (number of users, evolution of uses), but also from a cartographic perspective (how the networks are organized, how the users and data flows are distributed geographically, etc.).17
The sources which can be consulted are many and diverse. Since the late 1990s, such reports have been being published by the Chinese government (White Paper on the Internet in China)18, the CNNIC (Statistical Report in the Internet Development in China)19, with regular statistical reports20 on the evolution of the Internet in the country being published.21 Many international websites give statistical data on the Chinese Internet.22 Studies are also regularly being produced by researchers, describing China’s Internet both from a technical and a general point of view (Liu Dong, 200523; Jane Lael, 200524; Z. Shi, Z. Guo, 200725; Burson-Marsteller, 201126); examining the roles of the actors involved in the Internet (Qiheng Hu, 200727; Zhang Guanqun, Wang Hui, Yang Jiahai, 200928), and the distribution of users (L. He, L. Gui, Q. Le, 200429; Guo Liang, 200530; Guo Liang, 200731).
These studies are joined by analyses which focus more specifically on the development of technologies in China:
– the history and evolution of the ICT industry in China (Zhu Gaofeng 200532; Nir Kshetri, 200933; Jiang Zemin, 201034; Xiangning Wu, 201035; George I. Askew, 201036; Guobin Yang, 201237; Michael Pecht, Weifeng Liu38; EU Report, 201339)
– the impact of China’s industrial development on the level of competitiveness of other states, both on a regional level (Zhu W. 200140; Ted Tschang, 200341; Xiangning Wu, 201042) and worldwide, notably analyzing the role of companies such as Huawei, ZTE, Lenovo (Report of the US Congress, 201243; Lucas Solorio, 201444);
– market access conditions applicable to the Chinese Internet (Peter K. Yu, 200145; WilmerHale report, 200646; etc.);
– regulation of industry (Lijun Cao, 200747). transform China, on the international stage48, but also internally (Z. Jonathan; W. Enhai, 200549)? What are the instruments (political, legal, etc.) and who are the actors involved in the regulation of the Chinese Internet (Mayer Brown, 201250)? Does the Internet have a levelling role in Chinese society (Scott J. Shackelford, 201451)?
8.1.2. Impact of cyberspace on Chinese society
Beyond descriptive, cartographic or statistical (etc.) approaches, the analyses in the existing body of literature focus, in particular, on the social, political, economic and legal transformations caused by the introduction of networking in China: for instance, civilian capability of expression, State surveillance and control of the populace, use of social networks, etc.; to what extent can cyberspace
The political nature of the Internet is noteworthy. Thus, a very great many publications examine the question of the democratization of societies thanks to the new powers granted to individuals by cyberspace (a space for expression, for circumventing censorship, for challenging), and the tension between (cyber) surveillance and sousveillance.
Thus, many works look at the question of democratization, organization of dissidence, the strategies of the Internet users to circumvent the State’s surveillance52, and those of the governments to control the Internet (Philip Sohmen, 200153; Jason P. Abbott, 200154; Michael S. Chase, James Mulvenon, 200255; Christopher R. Hughes, 200256; Chin-fu Hung, 200357, 200558, 201059; OpenNet Initiative reports, 200460; Wei Qi, 200561; Gary D. Rawnsley, 200662; Chunzhi Wang, Benjamin Bates, 200863; Xiaoru Wang, 200964; Ashley Esarey, Xiao Qiang, 201165; Séverine Arsène, 201266; Yiyi Lu, 201367; Jiao Bei, 201368; Loubna Skalli-Hanna, 201369]. The question of censorship and cyber surveillance, which is directly linked to the questions about the democratization of societies, is a crucial one (Jonathan Zittrain, Benjamin Edelman, 200370; James A. Lewis, 200671; Rebecca Mackinnon, 200872; Xiaoru Wang, 200973; Shishir Nagaraja, 200974; RSF report75; Xueyang Xu, Z. Morley Mao and J. Alex Halderman, 201176; Emilie Frenkiel, 201377). Researchers are also posing questions about the reconfiguration of national identities in the Network Age, and the manifestations of nationalism (S. Zhao, 199878; Christopher R. Hughes, 200079; Yu Huang, 200280; Françoise Mengin, 200481; Z. Wang, 200882; etc.), which is a potential source of insecurity for other states.83
The role of the social media is also essential in these analyses (Louis Yu, 201184; US Congress report, 201185; Edward Tse, Adam Xu, Andrew Cainey, 201286; KPMG report, 2013).87 The hypothesis usually formulated is that of the empowerment of the citizens, for whom the networks represent a forum to express themselves, where there is a relatively reduced degree of control by the authorities over free expression, the capacity to impose a political agenda (Haiqing Yu, 200488; Rebecca Mackinnon, 201089; Qin Guo, 201190; Gary King, Jennifer Pan, Margaret E. Roberts, 201391). The evolution of the Internet in China, its uses, its construction, reflect a “dynamic, changing Chinese society”.92 This upheaval is desired and supported by the State, which has invested heavily in the development of infrastructures, and encourages the development of the information society. In China, like everywhere else, the Web benefits everybody, although it does also expose everybody to new risks: greater openness, fuller communication, more abundant exchanges, freer expression, and greater capacity to watch and control. The revolution in ICTs does not directly lead to democracy. However, it does have political consequences. It impacts on societies’ development: the rise in power of the middle classes (who account for the majority of the population of Internet users), the desire for modernization, patriotism, social mobilization, disputes, etc.
It should be pointed out that a number of Chinese authors, or of Chinese descent, have discussed this socio-political aspect of the Internet (Tai Zixue 200693; Zhou Yongming, 200694; Xu Wu 200795; Yongnian Zheng 200796; Rebecca Fannin 200897; Sherman So and J. Christopher Westland 200998; Tiebing Xu, 200999; Hong Xue, 2010100; Yun Zhao2011101; Wang Jun 2011102; Guobin Yang 2011103; Rodney Wai-chi Chu, Leopoldina Fortunati, Pui-Lam Law, Shanhua Yang, 2012104; Guosong Shao, 2012105). cyberdefense are even often defined as being indicative of China’s true ambitions on the international stage.
8.1.3. The Chinese cyber threat
The “Chinese cyber threat” plays an important part in the considerations about China’s evolution and the relations it can have with the rest of the world.106 China’s practices in cyberspace, its policies and strategies for Cybersecurity and
Also, many observers view the cyber threat as being only one facet of the threat constituted by China, which is engaged in a processof growth, but whose unpredictable evolution presents cause for concern.
These issues (cyber threat, Cybersecurity, cyberdefense, cyber-policy and strategies) thus fit into the more global discourse about the Chinese threat. They are the topic of specific publications, which emerged in the United States in the 1990sand have since been widely disseminated the world over.
The topic of cyber threat is jointed around a number of variables:
The discourse about international insecurity, rooted in the worrying evolution of Chinese State- and non-State capacities and practices in cyberspace, dates from the end of the 1990s and the start of the 2000s (T. Yoshihara, 2001115; Peter Hays Gries116, whose study relates to the expression of Chinese nationalism following the bombing of the Chinese Embassy in Belgrade in 1999). Since then, a copious body of literature has been produced on this subject, and the overview given here is not, by any stretch of the imagination, intended to be exhaustive. Let us simply cite the works of John Tkacik, 2008117; Jayadeva Ranade, 2010118; Derek Scissors, Steven Bucci, 2012.119
In the discourse in the media worldwide about Cybersecurity, the Chinese hacker has become an imposing and unavoidable figure. However, s/he is absent from the academic reference works on the sociology of hackers from the late 1990s120, or even more recent works121, on the psychology of hackers.122 China is believed to be targeting cyber-attacks in all directions, without imposing any limitations at all on that activity (testing what it is possible to do, and attacking anything and everything that is exposed).123 Chinese hacking could have a significant impact on trade law and human rights.124 The phenomenon is so widespread that 2008 could, in fact, be dubbed the “Year of the Chinese hacker”.125
The literature about Chinese hackers mentions:
– non-State-sanctioned cyber-espionage126;
– the significance of cybercrime (Michael Yip127; Zhuge Jianwei, Gu Liang, and DuanHaixin128; Aidong Xu, Yan Gong, Yongquan Wang, Nayan Ai129), as a phenomenon in juvenile crimes130; in international relations (Lennon Yao-Chung Chang writes about the prevention of cybercrime, specifically in the context of the relations between continental China and Taiwan131), or indeed the threat to the West (David Hanel, 2013132); certain authors attribute the dynamism of this threat to the permissive attitude of the Chinese State;
– military-based operations (intelligence units133 stealing intellectual property on a worldwide scale134);
– the intervention of patriotic/nationalistic hackers, hacktivists (hackers whose motives are political), who have been besieging the networks for nearly 20 years, and whose practices are specifically examined in works such as those of Michael Yip and Craig Webber, who call them “cyber-warriors” 135; Alexandra Samuel136, who compares them to cyber activists, one of whose main objectives is to circumvent the State’s cyber control mechanisms; and Sheo Nandan Pandey137, who seeks to identify the Chinese characteristics of this hacktivism.
Figure 8.1. Hacktivism: defacement of a Website, signed by the group Honker Union of China. The content of the slogan displays the desire to defend the interests of the Chinese nation138

Figure 8.2. Screenshot of the Webiste http://www.ssol.com/ defaced by China Honkers139
8.1.4. The Chinese army: its practices, capabilities and strategies
The Chinese army, its strategies, its developments in terms of capacity, its manifest interest in information warfare, mastery of information space (and cyberspace), and the increasing use of computerization in the forces (or more specifically the notion of informationization, which covers the computerization of weapons systems but also the integration of operations in cyberspace), modernization of the forces as part of the revolution in military affairs140, are the focus of a not-insignificant portion of literary production, mainly in the form of official reports produced by or for the American administration.
These works may relate to the impact of China’s cyber-policies on international relations.
Amongst the numerous English-language publications on these subjects, we can cite the most significant as being: the work of James Mulvenon (1999)141, Toshi Yoshihara (2001)142, Nina Hachigan (2001)143, Timothy L. Thomas (2001144, 2004145, 2006146, 2007147, 2009148), Ken Dunham and Jim Melnick (2006)149, Brian Mazanec (2008)150, Kevin Coleman (2008)151, Ron Deibert and Rafal Rohozinski (2009)152, Bryan Krekel and George Bakos153, Jeffrey Carr (2009)154, Gurmeet Kanwal (2009)155, R. A. Clarke and R. Knake (2010)156, Elisabette M. Marvel (2010)157, Martin Libicki (2011)158, Dmitri Alperovitch (2011)159, Venusto Abellera (2011)160, C. Paschal Eze (2011)161, Mark A. Stokes, Jenny Lin and L.C. Russell Hsiao (2011)162, Li Yan (2012)163, William T. Hagestad (2012)164, Dennis F. Poindexter (2013), Larry M. Wortzel (2014).165
It would be remiss to neglect to mention the official reports painting China as a potential threat because of the development of its military capabilities. In seeking to uncover the view of the Americans, we can exploit the following resources:
– a report from the Committee on Homeland Security, House of Representatives177, including China in a specific group of actors posing a cyber threat (China, Russia and Iran).
Reports from Cybersecurity companies contribute to this discourse about the actions of the Chinese army in cyberspace. The report most recently released in the media was produced by the American company Mandiant, in 2013.
8.1.5. Espionage
The question of cyber-espionage, which is an issue of strategic importance178, is cross-cutting, and therefore is included in works on cybercrime, cyber-attacks and State practices.
Whilst it clearly offers an advantage to infiltrate the computer systems of major enterprises, State services, armed forces, etc., the same actions directed at more modest actors raise questions: “Google Inc. (GOOG) and Intel Corp. (INTC) were logical targets for China-based hackers, given the solid-gold intellectual property data stored in their computers. An attack by cyber spies on iBahn, a provider of Internet services to hotels, takes some explaining […] The hackers’ interest in companies as small as Salt Lake City-based iBahn illustrates the breadth of China’s spying against firms in the U.S. and elsewhere. […] “They are stealing everything that isn’t bolted down, and it’s getting exponentially worse,” said Representative Mike Rogers, a Michigan Republican who is chairman of the Permanent Select Committee on Intelligence”.179 This “no-holds-barred” strike is perhaps attributable to the voracious appetite of China, which is determined to make up lost ground (in terms of knowledge, technologies, all kinds of expertise) and, as quickly as possible, turn itself into a competitor or a credible alternative to American power. Scott Borg, Director of the US Cyber Consequences Unit, denounced what he believes “…may be the biggest transfer of wealth in a short period of time that the world has ever seen.”180
According to the US authorities, it is in this respect that Chinese espionage is radically different from that of the United States: the American cyber spies target the secrets of foreign governments, military secrets, and fight against terrorism. American cyber-espionage, it seems, is acceptable because it fits into the context of an acceptable norm – that of the power game on the international scene – and is only for defensive purposes (to protect the country against future threats). Chinese espionage goes beyond the bounds of the norm, attacking illegitimate targets, and having offensive objectives. With this discourse, the United States refuses to assume the role of the villain, which they place on the shoulders of China, Russia and Iran.
The threat constituted by Chinese cyber-espionage is apparently different from the cybercrime which takes place in the rest of the world. It is held to be a major threat, as “China’s economic espionage activities against the United States are greater than the economic espionage activities are of all other countries combined.”181 Many official reports are devoted to defining that threat.182
However, the author of that assessment, who feels the need to avoid any exaggerated statements (“Many discussions of Cybersecurity invariably involve exaggeration. The source of this exaggeration is often a lack of specificity in precisely assessing intent, capabilities, and effect”), tempers his judgment: “The effect, however, is not one of clear-cut benefit to China. The strategic implications of this theft are difficult to assess. Some call it the greatest transfer of wealth in history; others call it a rounding error for an economy as big as that of the U.S. Neither characterization is correct”. However, China’s espionage activities are singled out: “What is unacceptable is espionage for purely commercial purposes […] Where China’s espionage efforts differ significantly from international practice is in the rampant economic espionage carried out by Chinese government entities, including the PLA”.
Hence, returning to the example of the attack on Google a few years ago (2009-2010), James Lewis defines the acceptable limit: provided China’s intelligence services are attacking systems for subjects in the areas of security and national defense, it is acceptable; when those same espionage operations are used to steal industrial secrets, it becomes scandalous. The disagreement between China and the rest of the world appears to lie in this difference of opinion, the lack of sharing of international norms that are tacitly accepted by the actors within this international community.
Other stances seem to demonstrate China’s incompatibility with the “norms” of the international community: at the ITU conference, China proposed rules which were different to those accepted by the West. It marginalizes itself by way of its practices, its choices, its way of acting and thinking. Yet the problem of the background discord does not only involve China, because from the Western point of view, there are many states which do not conform to the norm, and the motives are numerous, especially in terms of respecting the fundamental values defined by the West as universal standards.
The West’s position, or at least that of the United States, seems firmly rooted. The solution proposed by James Lewis in his discussion of how to deal with the issue of Chinese cyber-espionage is essentially to attempt to change China’s behavior. In Lewis’ eyes, China’s “economic espionage provides a technology boost, but puts bilateral relations with the U.S. at risk and hampers China’s ability to create indigenous innovation”.183 There are significant limitations on the pressure which the USA can exert on China: “This is not a new Cold War. We cannot have a Cold War with one of our largest trade partners”.184
Published in February 2013, the report APT1: Exposing One of China’s Cyber-espionage Units185 claims to provide proof of the existence of Chinese military groups specializing in cyber-espionage operations, specifically targeting the United States. The survey, which examines 150 incidents observed over a period of 7 years, was able to reconstruct the profile of Unit 61398, attached to the 2nd bureau of the PLA, 3rd Department, located near to Shanghai. Besides this group, the authors of the report also claim to be observing dozens of others distributed throughout the world – around twenty of them in China.
All of the literature produced about Chinese cyberwarfare and information warfare capabilities has, since the 1990s, been painting the picture of an aggressive, fearsome nation, possessed of inexhaustible capacities (because when it is not a question of the threats represented by State actors themselves, it is a question of cybercriminals or indeed millions of citizens turned nationalistic hackers, constituting as many threats for the rest of the planet, in view of their skills and their motives); a nation whose defense strategies are unclear186, whose current approach of attacks carried out in information space is rooted in secular warrior practice (Sun Tzu’s The Art of War, Chairman Mao’s irregular warfare). This portrait is based on the existence of forces of techno-warriors set up during the Cold War187, and expresses China’s determination to establish itself as an alternative to America’s hegemonic power, thus upsetting the international order established at the end of the Cold War. Faced with this situation, America and the whole of the industrialized world is in a vulnerable and inferior position (R. Clarke188; Joel Brenner189) because of their dependency on cyberspace, the number of potential enemies and the motives held by those foes, and seems to have no option but to prepare for confrontation by trying to make up their lost ground in terms of capabilities, both defensive and offensive.190 An alarmist discourse, rooted in the predictions made during the 1990s of a Cyber Pearl Harbor and other forms of cybernetic chaos, has taken hold amongst the political classes (for example, the Republican US Senator Mike Rogers declares that the United States is losing the cyberwar against China).191
It should also be noted that the subject of the Chinese cyber threat is often discussed by military or ex-military personnel: Timothy L. Thomas192, Scott J. Henderson193, Rich Barger194, Mark. A. Stokes195 and William T. Hagestad196 are among these commentators.197 Because of the profile of a portion of its directors, we can also consider that the publications emanating from Mandiant also fit into this category. Indeed, before he set up the company in 2004, Kevin Mandia worked as part of the 7th Communications Group (Pentagon), as a Special Agent for AFOSI (U.S. Air Force Office of Special Investigations). Travis Reese and Dave Merkel, both members of the company’s board of directors, are also former members of AFOSI. Richard Bejtlich, another member of Mandiant’s board of directors, and founder of the Website Tao Security198, was an intelligence officer in the U.S. Air Force CERT, as well as the Air Force Information Warfare Center (AFIWC) and the Air Intelligence Agency (AIA).
The publication of the report comes as the American authorities are engaged in a policy of toughening their positions in relation to cyberdefense: the announcement of the enhanced powers granted to Cyber Command199, a speech from the US Secretary of Defense about the need to protect the nation from cyber-attacks200, President Obama’s Executive Order on Cybersecurity201, dialog at the highest level between the United States and China over the question of Cybersecurity202, and toughening of the legal framework relating to cyber-warfare.203
Finally, the report has a place in an unusual economic context, which is extremely favorable for the Cybersecurity market (Mandiant’s turnover for 2012, which is over 100 million USD, is up by 76% in comparison to the previous year).204 The initiative does little to hide the commercial strategy of the enterprise: “Meet the Company That’s Profiting from Chinese Hacking.”205 The conclusions advanced by the report therefore may not be as objective as may otherwise be thought, and may not reflect reality, but only one aspect of that reality, with the perspective having been chosen with commercial or political aims in mind. These remarks lead us to consider all of the criticisms which have been leveled at the report, and the lessons that can be drawn from those criticisms.
The criticisms have come from China, based on clearly-defined arguments. The spokesman for the Foreign Ministry points the finger at the way in which the United States constantly levels accusations at China, saying that this type of approach is not helpful in solving the problem of cybercrime; that only international cooperation in the fight against cybercrime should be envisaged; that China too is one of the most prevalent victims of cyber-attacks; that the United States is the no. 1 source of those attacks, according to IP analysis; that China’s legislation, which has been toughened in recent years, and Chinese policy, take a dim view of such practices; that on the international scene, China, along with Russia and a few other countries, has proposed a code of good conduct which has thus far been snubbed by the United States; and finally, the spokesman expresses surprise that it is technically possible to so precisely locate and attribute blame to the aggressors, as it is well known that they tend to carefully anonymize their operations.206
Other criticisms, however, have come from the United States207 – particularly from the expert, Jeffrey Carr, first picking up on the numerous errors with which the dossier is fraught, and then the unsatisfactory methodology used. Thus, he points out:
These criticisms cast doubt on the very quality of the document itself, the validity of its conclusions, and the impartiality of its authors.
Another criticism relates to the taking of undue risks. Revealing information about the investigative capacities used in the gathering of the data will inevitably lead the aggressors to alter their behavior, thereby (temporarily, at least) weakening the united states’ security.208 However, the company gives a certain amount of self-criticism in this regard, explaining the choice within the report itself: it was felt that the publication of the truth merited this risk.
Whilst it does not truly provide any new information209, and fails to prove the identity of the aggressors, the report does, in its own way, contribute to the alarmist discourse, conforms to the train of thought developed over more than 15 years: it stresses how dangerous the operations carried out by the Chinese intelligence unit are, confirms the existence of units of techno-warriors (high-tech spies much like those employed by America), and emphasizes the vulnerability of the American actors (by highlighting the number of recorded incidents and the relative ease with which the aggressors carry out their espionage operations). The “experts” belonging to the company channel the same fear mongering discourse, backed up by evidence. Of course (as is their trade), they propose solutions to defend against these threats.
The process of securitization210 involves first identifying the threat (China, and its actions in cyberspace); naming the referential objects (critical infrastructures, companies, stability of the nation-State, western civilization, democracy, liberalism, cyberspace); next comes securitization proper, which entails the finding of solutions (cyberdefense policies, increasing of defensive and offensive resources, tightening of surveillance and control regulations, and commercial solutions).
In this process, the Cybersecurity firm is one of the key actors, on the side of the State, capable not only of offering solutions to the problems identified (protecting against the threat) but also of identifying and describing the threat. Thus, it has a significant degree of responsibility in the process of threat definition. The report and the criticisms of it demonstrate, once again, that, in spite of the effects of declarations, it is always possible to call the results into question, and put forward other, equally-credible hypotheses. The problem of attribution remains to be solved. However, though it may use uncertain results and debatable conclusions as a starting point, the technique still has an important part to play in the definition of a threat and (re)construction of a reality, which may have an impact not only from a commercial point of view (opening up new markets for (in)security) but also from a political standpoint (influencing the world view of the political decision-makers).
In the United States, a few rare critical voices are beginning to be heard – some of them calling for greater objectivity and discernment in the analysis of the threats (J. Carr and the various commentators on his blog about the Mandiant report; Eric C. Anderson in his Sino phobic discourse analysis211); others for greater restraint in the expression of the stakes in Cybersecurity policies (Martin Libicki, decrying America’s warlike rhetoric, which runs the risk of triggering an uncontrollable escalation in international violence212). Yet we may also ask about how much counterweight can actually be carried by critical views and calls for caution, in the face of an alarmist discourse which is anchored in nearly two decades of propaganda painting the image of a major adversary.
8.1.6. China, cyberspace and international relations
China’s might and its management of cyberspace are invariably of great importance in its international relations.213 The emphasis in debates and analyses is placed on a few central topics.
China’s use of cyberspace as a tool of power (John Oakley, 2011214; Sérgio Tenreiro de Magalhães, 2009215): interpretation error, an improperly-controlled action with unforeseen consequences, could put the spark to the powder keg. The risk is of the escalation of force, and of violence.228
These debates focusing on cyber-issues fit in with the broader question of the conditions of the ratio of strength between the two powers (David C. Gompert, 2011229), of which cyber is, ultimately, only one aspect, but one which causes numerous genuine tensions between the two states. Besides, adding cyberwarfare to the list of points of discord between China and the United States is, undoubtedly, not the best way to achieve better entente between the two states.230
In this context, it is rare to hear voices which attempt to relativize the significance of this specific threat: “Despite the PLA’s interest in and preparations for cyber operations, and the importance of networks to military operations, open source evidence does not justify the conclusion that the PRC is a threat per se. Much of what has been classified as a cyberattack is not hostile at all and is actually clandestine spying and a form of intelligence gathering inside computer networks. Hackers, China’s internal security threat, are likely their first and foremost priority.”231
8.1.7. Particular points from the Western perspective
Westerners are not capable of understanding Chinese society.232 This idea is formulated not by the Chinese, but by Westerners themselves.
Westerners have difficulty in comprehending the complex nature of modern China, because it does not fit into any of the typical categories. Tzvetan Todorov233 summarizes this complexity in the following terms: “China no longer corresponds to the “ideal model” of a totalitarian regime. Rather, to outside observers, China appears to be a baroque hybrid of communist rhetoric, represessive centralized administration and a market economy which allows, or even favors (something which would have been inconceivable in the time of Soviet and Maoist communism) openness to the outside world and enrichment of individuals.” The published analyses often dwell on the differences.234
Without appropriate referential frameworks to aid comprehension, for example, Westerners cannot understand why a society which frequently rises up against injustices does not rise up against the governing regime at the same time; why that society speaks out against corruption and embezzlement, but continues to have faith in its leaders.
Indeed, if we Westerners do not understand, affirms Jean-Louis Rocca, it is because our analytical filter yields nothing but contradictions. We would first be convinced that a democratic market is the only envisage able prospect; yet the culturalist paradigm speaks of the existence of a “Chinese model”, a specific approach, a particular channel, which is entirely defined. From this point of view, there would only seem to be solutions “à la chinoise”, different from our own. Interpretations of China thus hesitate between these two paradigms: thus, in order to discuss China’s political evolution, we say that it does not conform to the single model which is becoming widely adopted on the international scene (democracy), but we also accept that the switch to democracy in China may first require a political modernity “à la chinoise”, a transition to democracy or another form of democracy.235 Hence, analyses of China are constrained by the two paradigms (conformity to the Western democratic model; and the culturalist model).
These two paradigms are also found in the discourse produced about Chinese cyber strategy:
– China is far removed from the democratic model (there is control and censorship of the Internet in China), but also more generally from usages in accordance with the rules set by the international community. By placing emphasis on the lack of respect for these international rules with regard to espionage, the United States paint a picture of China which is outside of the “norms” which are becoming those of the modern international scene. The Chinese themselves appear to place themselves outside of this system, beyond the governance of these rules: after all, they published “Unrestricted Warfare”, meaning the usage of all kinds of technological tools in all directions, in contravention of the norms of international deontological laws or rules? By the principle of this contrast between an innocent (Western) democracy and authoritarianism236, measures taken by China would be condemnable (censorship, cyber surveillance), whereas those taken by democracies would be legitimate (cyber surveillance is a necessity for the maintaining of peace in a democracy). Could it be that the arguments are exaggerated when it comes to China? Do we lose some of the necessary objectivity? If this is so, however, is the problem limited to discourse about China or is it more general in discourse about Cybersecurity? Does the discourse about the cyber threat represented by the Chinese hacker accurately reflect the reality, or is it exaggerated?
– in addition, analysts also emphasize the development of a specifically Chinese channel, and have no hesitation in drawing the connection between ancient Chinese philosophy and modern thought (e.g. viewing China’s cyberdefense strategies and doctrines as deriving directly from Sun Tzu’s strategy). Western authors even affirm that China, because of its culture, its way of thinking, its philosophy, and its tradition, might be better prepared for cyberconflict than other nations in the world. Culturalism appears to be a practical way of explaining the Chinese exceptionality, as that country’s culture has always been deemed different, “separate”.237 Yet that uniqueness is not only to be understood in a negative light. We can hold up the difference as a model from which it would be wise to draw inspiration (e.g. by first understanding and then transposing the seminal principles laid down by Sun Tzu to our own culture, our own strategy).
Thus, our referential framework oscillates between two limits whereby China is an outsider, a “different” actor. This fundamental postulate greatly constrains any analysis, and is visible in the discourse published about China; “cyber” issues, security and defense are no exception to this phenomenon.
8.2. The evolution of American discourse about China, Cybersecurity and cyberdefense
We can gain an insight into American discourse and its evolution by analyzing three corpora: the Defense Department’s annual reports, relating to the evolution of China’s defense; the speeches given by the US Secretaries of Defense; and the prospective exercises carried out by the National Intelligence Council and published every four years. This corpus is not a reflection of the whole of American thinking, which would of course also be reflected through other political discourse (White House communiqués, Congress, GAO reports, etc.), the media, research publications, or websites, blogs, social media in the broadest sense. However, we have chosen to limit our corpus to these three sources, because we believe they give a fairly accurate illustration of the discourse of the dominant actors, which are capable of influencing political decision-making. Finally, these corpora have been chosen because they are easy to access (available on the Internet in their entirety), and for the period which they cover (the past two decades), which serve our objective here, i.e. to demonstrate the main arguments in the discourse and the evolution of those arguments over time.
8.2.1. The annual reports of the US Defense Department
As stipulated by the National Defense Authorization Act for Fiscal Year 2000, Section 1202, Public Law 106-65, amended by Section 1246, “Annual Report on Military and Security Developments Involving the People’s Republic of China”, of the National Defense Authorization Act for Fiscal Year 2010, Public Law 111-84, the Defense Department annually delivers a report to Congress on the progression of Chinese military power. Two versions of this annual report are produced: one which is not classified, which is available online on the Defense Department’s Website; the other which is classified. The report must focus on four aspects of the development of Chinese defense: its technological, strategic, organizational and conceptual dimensions. Finally, the report must not merely give overviews and observations, but rather must convey a prospective vision, all from the viewpoint of US/China relations, and of cooperation on issues of security.
The first report published in 2002238 spoke of information operations and information warfare, and highlighted the strategic nature of those two concepts in Chinese defense policy: “China views information operations/information warfare (IO/IW) as a strategic weapon foruse outside of traditional operational boundaries”. Information space, which would later be called “cyberspace”, had a leveling effect: “China is particularly sensitive to the potential asymmetric applications IO/IW can have in any future conflict with a technologically superior adversary”. China was paying particular attention to IO and IW: “Both the Academy of Military Science and the National Defense University have published several books devoted, in part or completely, to this subject. These writings indicate a growing sophistication in the PLA’s understanding of all aspects of IO”. It was evident even at that point that China, like the United States, was integrating the use of ICT into military affairs: “China is pursuing IO/IW development as part of its overall military modernization. Combining information warfare--such as computer hacking--with irregular special and guerilla operations, would allow China to mount destructive attacks within the enemy’s own operations systems, while avoiding a major head-on confrontation”, with both an offensive and defensive objective: “Efforts have focused on increasing the PLA’s proficiency in defensive measures, most notably against the threat of computer viruses […] Increases in network defense likely will enhance China's understanding of virus propagation and behavior, creating a solid knowledge base not only for computer network defense (CND), but potentially also for computer network attack(CNA) through malicious software development”.
The report also highlighted China’s initiatives in terms of R&D in the domain, and the method of taskforce construction (in terms of human resources), based on using reserves of specialists – a method which would later be used by other countries: “In an effort to improve its skill base in the IT field, the PLA has been recruiting specialists via its reserve officer selection program”.
In spite of these efforts, the US felt that China did not yet have the means to penetrate the most heavily protected networks: “China has the capability to penetrate poorly protected U.S. computer systems”, but that did not take away from the potential danger it posed: China “potentially could use CNA to attack specific US civilian and military infrastructures”.
The development of nationalistic hacking added to the concerns created by the rise in power of China’s military capabilities, especially as the government could be supporting this kind of action: “In the near term, nationalistic hacking is likely to occur during periods of tension or crises. Chinese hacking activities likely would involve extensive web page defacements with themes sympathetic to China. Although the extent of Chinese government involvement would be difficult to ascertain, official statements concerning the leveraging of China’s growing presence on the Internet, and the application of the principles of “People’s War” in “net warfare”, suggest the government will have a stronger role in future nationalistic hacking”.
The 2003 report239 again deals with the same topics, but goes into greater depth. It again mentions the role of IO and IW in Chinese strategy, with these concepts notably encompassing “computer warfare, network warfare, temporal-spatial analysis, knowledge warfare, information protection, and electronic security”. The concept of IO is therefore a complex construct: it includes “elements such as combat secrecy, military deception, psychological warfare, electronic warfare, physical destruction of C2 infrastructure, and computer network warfare”. Above all, though, according to the United States, these IOs are, for China, a pre-emptive weapon, a non-conventional weapon, for asymmetrical conflicts.
The 2003 report also reiterates the importance of reserve units in the organization of IOs and IW, and states that China is setting up specialized units, in various cities throughout the country, thus forming a corps of cyberwarriors: “Specialized IO/IW reserve units are active in several cities developing “pockets of excellence” that could gradually develop the expertise and expand to form a corps of “network warriors” able to defend China’s telecommunications, command, and information networks, while uncovering vulnerabilities in foreign networks”.
According to the same report, the Chinese army possessed the means to carry out attacks on networks in armed conflicts: “Special information warfare units could attack and disrupt enemy C4I, while vigorously defending PRC systems”.
The 2004 report240 estimates that China’s IO capabilities are expanding and improving, although its “equipment is dated and does not appear to be readily available to most units”. However, the report predicts that: “domestic production, along with foreign technology transfers, probably will give the PLA access to a wider range of modern equipment in the future”. It also states that: “China is experiencing a rapid buildup of its information technology capabilities”. The rapidity of Chinese technological progress is founded largely on the acquisition of foreign technologies, technology transfers, knowledge-sharing, the installation in China of R&D centers for foreign companies, and the creation of joint ventures. Economic, industrial and research partnerships are thus helping speed up the process of modernization of the Chinese army.
One of the central subjects around which the American analysis pivots is the relationship between China and Taiwan, and the potential for that situation to evolve into an armed conflict. The scenario of this conflict thus serves as the background for the argument about Chinese development of IW capabilities, and is used to demonstrate the pertinence of the concerns formulated by the American observers: “During a cross-Strait conflict, China most likely would initiate an intensive perception management campaign, with both global and regional audiences, to reduce the desire of Taiwan to resist, justify China’s military campaign, and deter U.S. intervention”. Indeed, by controlling that information space, China would have the possibility to act quickly, to win a victory by playing with public perceptions (which are gold dust in psychological operations), and attacking the critical infrastructures and command systems of the enemy country. China could use information space to its advantage at every stage of the offensive operation: “China anticipates that this strategy will succeed because of the fragility of the Taiwan population’s psychology. The Chinese perception management campaign most likely would use Chinese, Hong Kong, Taiwan, and other regional media to deliver messages to the Taiwan people and leaders. Unclassified Chinese writings reveal that attacking C4I systems, civilian information technology, and communication infrastructure are critical for gaining information superiority. Prior to an attack, Chinese information operations personnel and special forces or espionage agents most likely would gain and maintain access to such communication nodes for intelligence exploitation and disrupt critical infrastructure, such as the power grid and vulnerable collocated military and civilian telecommunications. Exploiting other portions of the information operations spectrum (through electronic warfare and denial and deception) also could disrupt Taiwan’s defenses, and attacks against unclassified DoD computer networks related to logistics could delay U.S. efforts to intervene”.
China’s capabilities are deemed entirely sufficient to be able to carry out operations against Taiwan. The report notes that Taiwanese experts have suggested their armed forces begin to prepare for this new kind of attack. Taiwan has high-level technologies and high-level engineers at its disposal, and can use them for its cyberdefense.
The 2005 report241 speaks not of “cyber”, but rather of “information technologies” and “Computer network operations”. The report highlights the emergence of a new expression in China’s vocabulary surrounding defense: "China’s latest Defense White Paper deployed authoritatively a new doctrinal term to describe future wars the PLA must be prepared to fight: “local wars under conditions of informationalization”. This term acknowledges the PLA’s emphasis on information technology as a force multiplier and reflects the PLA’s understanding of the implications of the revolution in military affairs on the modern battlefield”. This formulation defines the extent of the Chinese use of IW capabilities, whose development is continuing apace: “The PLA continues to improve its potential for joint operations by developing a modern, integrated command, control, communications, computers, intelligence, surveillance, and reconnaissance (C4ISR) network and institutional changes”.
The report describes the components of information operations using a referential framework which is very similar to that employed by the US Department of Defense, notably distinguishing between CNO242, CNA243, CNE244 and CND245: “China’s computer network operations (CNO) include computer network attack, computer network defense, and computer network exploitation. The PLA sees CNO as critical to seize the initiative and “electromagnetic dominance” early in a conflict, and as a force multiplier”.
Specialists in Chinese affairs speak of the Chinese technique of Integrated Network Electronic Warfare. The report also stresses the lack of a formal Chinese doctrine concerning operations in cyberspace. This lack of official references, of a publically-available doctrine, destabilizes the United States, who must continue to pressure China to communicate about its projects, developments, capabilities, doctrines, etc., as the US does.
The 2006246, 2007247, 2008248, 2009249 and 2010 reports250 reiterate the observations on the same points:
In 2008258, the report alludes to the cyber-attacks originating in China, affecting networks all over the world:
– “In the past year, numerous computer networks around the world, including those owned by the U.S. Government, were subject to intrusions that appear to have originated within the PRC.”259 Although the attacks require particular capabilities and skills, there is, as yet, nothing to unequivocally indicate that they were the work of the Chinese army. Yet the very mention of the possibility of the Chinese army’s involvement is, in itself, a thinly-veiled accusation: “Although it is unclear if these intrusions were conducted by, or with the endorsement of, the PLA or other elements of the PRC government, developing capabilities for cyberwarfare is consistent with authoritative PLA writings on this subject”.260 The report also mentions other actors on the international scene who have openly laid blame at China’s door: “Hans Elmar Remberg, Vice President of the German Office for the Protection of the Constitution (Germany’s domestic intelligence agency), publicly accused China of sponsoring computer network intrusions “almost daily”261.
The 2009 report262 introduces the notion of cyber-warfare. The chapter entitled “Cyber-warfare” discusses the cyberattacks suffered by the US government, which are suspected (though cannot be proven) to have been carried out by the Chinese authorities. The report cites a number of cases of cyber-attacks recorded the world over (India, Belgium, the US), indicating the extent of the phenomenon: this is not merely a question of conflict between China and the United States.
The 2010263 and 2011264 reports take the same approach, citing a number of cyber-attacks recorded all over the world. These operations are classified as espionage activities, because the factor they have in common is the exfiltration of (often sensitive) data – e.g. strategic or military data. Although the 2010 report speaks of “cyber-warfare”, it often comes back to the notion of “IW”, and its psychological dimension, encompassed within the concept of the “Three Warfares” – a concept developed specifically by the Chinese army: “In 2003, the CCP Central Committee and the CMC approved the concept of “Three Warfares” (san zhong zhanfa), a PLA information warfare concept aimed at influencing the psychological dimensions of military activity”. These “three warfares” include Psychological Warfare, Media Warfare, and Legal Warfare. “The concept of the “Three Warfares” is being developed for use in conjunction with other military and non-military operations.”
The 2011 report265 defines what the United States views are the potential uses of the Chinese cyber capabilities: “Cyberwarfare capabilities could serve PRC military operations in three key areas. First and foremost, they allow data collection through exfiltration. Second, they can be employed to constrain an adversary’s actions employed to constrain an adversary’s actions based logistics, communications, and commercial activities. Third, they can serve as a force multiplier when coupled with kinetic attacks during times of crisis or conflict”. It also identifies sources of the Chinese doctrine – specifically two publications which have caught the attention of the American analysts: Science of Strategy and Science of Campaigns.
The question of cyberdefense cannot be reduced to the development of cyber capabilities and computer network operations. China is making an effort in the area of diplomacy by participating in multilateral and international fora, where it is often aligned with Russia – particularly in terms of promoting a vision of Internet governance. The United States is unhappy that China has not yet come around to its (the US) point of view, and accepted the application of international humanitarian law and the laws of war in cyberspace. Although it deals with cyber capabilities, the 2011 report preserves the notion of “IW”, highlighting the continuity of the Chinese policy of developing its capabilities in this domain for more than 10 years previously: “China is pursuing a variety of air, sea, undersea, space, counter space, information warfare systems, and operational concepts to achieve this capability, moving toward an array of overlapping, multilayered offensive capabilities extending from China’s coast into the western Pacific. [...] China is improving information and operational security to protect its own information structures, and is also developing electronic and information warfare capabilities, including denial and deception, to defeat those of its adversaries”. Later on in the same chapter, we find the same elements which have consistently been appearing since 2002, i.e., those relating to capability development, human resources, reservists, and strategic elements (CNO, CAN, CND and CNE).
In the 2012 report266, the notions of Information Warfare and Information Operations are absent this time.
The emphasis is again placed on the development of China’s capabilities: “In addition to the direct-ascent antisatellite weapon tested in 2007, these counter space capabilities also include jamming, laser, microwave, and cyber weapons”. At the heart of the concerns is the issue of cyber-espionage, in a section entitled “Cyber-espionage and Cyberwarfare Capabilities”, which begins by recapping the cyber-attacks carried out in 2011, stressing the nature of the targets affected. Up until then, the government’s and the army’s systems had been targeted. The report eagerly points out that private businesses have now fallen prey to the same operations. These allusions are reminiscent of the accusations of economic espionage carried out by the Chinese army for the benefit of the nation’s companies. These practices, which the US condemns, compound the differences of opinion regarding the means of governance of cyberspace. A section is given over to the economic espionage carried out by China, recalling that, of course, at least a dozen different nations conduct similar operations against the United States. China, however, appears to be the most active and the most persistent offender: “Chinese actors are the world’s most active and persistent perpetrators of economic espionage”.
The 2013 report267 touches on at least four aspects of cyberdefense: the developing Chinese power; the notions of pre-emptive weapons, informational superiority and asymmetry; economic cyber-espionage; and the code of conduct in the area of security.
China is firstly depicted as a power which has been in the process of development for over 10 years, but is now operational, according to the 2013 report: “The PLA has made huge progress in developing information technology and realizing information integration in recent years.”268 China is investing in the development of technological and cyber capabilities: “Beijing is investing in military programs and weapons designed to improve extended-range power projection and operations in emerging domains such as cyber, space, and electronic warfare.”
The PLA’s operations are considered as pre-emptive action weapons, with the aim of achieving informational superiority; this would enable China to combat superior adversaries (asymmetrical conflict, the equalizing nature of cyberspace). This informational superiority also contributes to its so-called Anti-Access/Area Denial (A2/AD) capabilities.
The report points out that in 2010, in China’s 2010 Defense White Paper, the PCR itself expressed concern over the cyberwarfare programs run by foreign nations. Each party (the US, China and other nations) thus believes itself to be in the right in its cyberdefense projects and measures, because the strategy is shared by all the major actors on the international stage.
According to the US Department of Defense, the development of cyber capabilities for warfare is consistent with Chinese military doctrine. The report, once again, draws on two reference documents from the Chinese body of strategic literature: Science of Strategy and Science of Campaigns. These two texts refer to information warfare, rather than cyber-operation directly.
The finger is also pointed at China for its practices of economic cyber-espionage, aimed at obtaining advanced foreign technologies: “Numerous computer networks, including those owned by the US government, were targeted for intrusion, some of which were attributable to the Chinese government and military.”269 The accusation is direct: “China is using its computer network exploitation (CNE) capability to support intelligence collection against the U.S. diplomatic, economic, and defense industrial base sectors that support U.S. national defense programs.”
China, along with Russia, is also internationally promoting its proposed Information Security Code of Conduct, which is intended to affirm the principle of exercising of the right of sovereignty over content and information flow.
All of this makes China a threat. Firstly, its technological capabilities in cyberspace (which give China the means to carry out offensive operations); and secondly the anti-access strategy is a threat to the freedom of projection of the American forces in the Pacific region. These observations have been being formulated since the beginning of the 2000s by the United States. China’s practices (economic cyber-espionage) and its objectives (the Code of Conduct) are contrary not only to the United States’ interests (of course), but also its values. There is a significant difference of opinion on these points.
8.2.2. Speeches of the Secretaries of Defense
China has essentially been part of the discourse of the US Secretaries of Defense from the start of the 2000s. Chronologically, this corresponds to the date of establishment of the annual reports on Chinese military development produced by the Department of Defense, in accordance with the National Defense Authorization Act for Fiscal Year 2000, Section 1202, Public Law 106-65.
Whilst, in general terms, the speeches of the successive Secretaries of Defense between 1995 and 2014 increasingly discuss the issue of “cyber”, when we analyze the whole of the available corpus, we can see that China is not remotely associated with that issue until 2008, but that from that point on, the China issue becomes more apparent. Thus, between 2000 and 2007, the Chinese are mentioned essentially because of the concerns that they raise:
– because of the increasingly important role China is assuming on the international stage, and the uncertain prospects for its evolution: “…I don’t think it’s written exactly how they’re going to enter the world, goodness knows all the countries in the region and in the world are working to try to see that they enter the global community in a peaceful, rational way, without any grinding of gears”;270
– there are many unknowns in the equation – particularly in relation to the true efforts made by China in terms of military development, and in relation to China’s intentions (is this development of capability for peaceful or aggressive ends?): “Among other things, the report concludes that China’s defense expenditures are much higher than Chinese officials have published. It is estimated that China’s is the third largest military budget in the world, and clearly the largest in Asia. China appears to be expanding its missile forces, allowing them to reach targets in many areas of the world, not just the Pacific region, while also expanding its missile capabilities within this region. China also is improving its ability to project power, and developing advanced systems of military technology. Since no nation threatens China, we must wonder: Why this growing investment? Why these continuing large and expanding arms purchases? Why these continuing robust deployments? Though China’s economic growth has kept pace with its military spending, it is to be noted that a growth in political freedom has not yet followed suit. With a system that encouraged enterprise and free expression, China would appear more a welcome partner and provide even greater economic opportunities for the Chinese people”;271
– the nature of the diplomatic relations, when an incident occurs between the two countries: “A few months ago, as we all know, an unarmed EP-3 reconnaissance aircraft flying in the airspace over the China Sea was struck by a Chinese fighter and, of course, for a while we had 24 of our great personnel detained. Some ask why are we conducting surveillance against another nation? My answer to that is, “That’s what we do.” We are vigilant, we are watchful because we know that our interests and those of our allies in the region may be challenged and we must be ready”;272
– generally speaking, the United States criticize the Chinese approach for its opacity, the lack of transparency regarding China’s intentions and methods, and wonders about the effect such a stance might have on international relations: “China has a strong economic growth rate today and an industrious workforce. But there are aspects of China's actions that can complicate their relationships with other nations. As we discussed last year, a lack of transparency with respect to their military investments understandably causes concerns for some of their neighbors.”273
Regardless of the concerns, and of the developments of capabilities, the Secretary of Defense points out that the Sino-American relation cannot be envisaged as a hostile one: “I disagree with those who portray China as an inevitable strategic adversary of the United States.”274
Although this statement was made in 2011, from 2008 onwards the discourse has evolved. China has become a more openly apparent threat by virtue of the level of its defense capabilities: “In the case of China, investments in cyber-and anti-satellite warfare, anti-air and anti-ship weaponry, submarines, and ballistic missiles could threaten America’s primary means to project power and help allies in the Pacific: our bases, air and sea assets, and the networks that support them.”275 Now, therefore, the question of Chinese cyberwarfare capabilities arises.
The remarks were repeated in very similar terms the following year: “As we know, China is modernizing across the whole of its armed forces. The areas of greatest concern are Chinese investments and growing capabilities in cyber-and anti-satellite warfare, anti-air and anti-ship weaponry, submarines, and ballistic missiles.”276 Rather than the capabilities for symmetrical conflict, cyberdefense contributes to the Chinese anti-access strategy, thus endangering America’s abilities to project power and intervene in the Pacific region: “In fact, when considering the military-modernization programs of countries like China, we should be concerned less with their potential ability to challenge the U.S. symmetrically – fighter to fighter or ship to ship – and more with their ability to disrupt our freedom of movement and narrow our strategic options. Their investments in cyber and anti-satellite warfare, anti-air and anti-ship weaponry, and ballistic missiles could threaten America’s primary way to project power and help allies in the Pacific – in particular our forward air bases and carrier strike groups. This would degrade the effectiveness of short-range fighters and put more of a premium on being able to strike from over the horizon – whatever form that capability might take.”277
This concern did not disappear, because in 2011 the Secretary of Defense put forward the same arguments: “As I alluded to earlier, advances by the Chinese military in cyber and anti-satellite warfare pose a potential challenge to the ability of our forces to operate and communicate in this part of the Pacific. Cyber-attacks can also come from any direction and from a variety of sources – state, non-state, or a combination thereof – in ways that could inflict enormous damage to advanced, networked militaries and societies. Fortunately, the U.S. and Japan maintain a qualitative edge in satellite and computer technology – an advantage we are putting to good use in developing ways to counter threats to the cyber and space domains.”278 The concern expressed here is barely tempered by the certainty of a technological advantage on the part of the United States and Japan.
In view of the number of speeches given by the Secretaries of Defense, those which speak about the issue of Chinese cyberwarfare are, in the final analysis, relatively few.
Defense relations with China need to take place in a climate of cooperation, and encourage exchanges: “We also need you to strengthen defense ties with China. China’s military is growing and modernizing. We must be vigilant. We must be strong. We must be prepared to confront any challenge. But the key to peace in that region is to develop a new era of defense cooperation between our countries – one in which our militaries share security burdens to advance peace in the Asia-Pacific and around the world.”279
During his visit to Beijing in September 2012, Leon Panetta mentioned the cyberspace issue: “We’ve made it very clear that our engagement will continue to be guided by our adherence to a set of basic principles, including the following: one, free and open commerce; two, a just international order that emphasizes the rights and responsibilities of nations and the fidelity to the rule of law; three, open access by all to the shared domains of sea and air and space and cyberspace; and, lastly, resolving disputes peacefully, without coercion or the use of force.”280
In a speech delivered in New York in 2012, Leon Panetta pointed to the United States’ direct competitors in cyberspace, whose strategies lend legitimacy to the process of reinforcing America’s cyberdefense resources: “Our most important investment is in skilled cyber-warriors needed to conduct operations in cyberspace. Just as DoD developed the world’s finest counterterrorism force over the past decade, we need to build and maintain the finest cyber force and operations. We’re recruiting, we’re training, we’re retaining the best and the brightest in order to stay ahead of other nations. It’s no secret that Russia and China have advanced cyber capabilities. Iran has also undertaken a concerted effort to use cyberspace to its advantage.”281 In the same section, two types of threats are mentioned: terrorism, and the rise in power of the states of China, Russia and Iran. Leon Panetta identifies two major risks: that of the rise in capability, and that of the opacity, which could give rise to possible misunderstandings, incomprehension, doubts, and interpretation errors: “I recently met with our Chinese military counterparts just a few weeks ago. As I mentioned earlier, China is rapidly growing its cyber capabilities. In my visit to Beijing, I underscored the need to increase communication and transparency with each other so that we could avoid a misunderstanding or a miscalculation in cyberspace. This is in the interest of the United States, but it’s also in the interest of China.”282
China and cyberwarfare constitute a threat to the collective security of Europe and the United States, said Chuck Hagel in 2013, because they contribute to the global threat: “The foundation of our collective security relationship with Europe has always been cooperation against common threats. Throughout most of the 20thcentury, these common threats were concentrated in and around Europe. But today, the most persistent and pressing security challenges to Europe and the United States are global. They emanate from political instability and violent extremism in the Middle East and North Africa, dangerous non-state actors, rogue nations, such as North Korea, cyber-warfare, demographic changes, economic disparity, poverty and hunger. And as we confront these threats, nations such as China and Russia are rapidly modernizing their militaries and global defense industries, challenging our technological edge in defense partnerships around the world.”283 On the other hand, China has to play an active role in security – particularly in Asia: “No security architecture in Southeast Asia can succeed without the active involvement and participation of the two large emerging powers that border this region, China and India.”284
Cooperation with China has now been engaged in matters of Cybersecurity: “As part of our rebalance, the United States is committed to pursuing a positive and constructive relationship with China. We have very open discussions with China, including a productive visit last week by my counterpart, Defense Minister General Chang, whom I hosted at the Pentagon. He and I agreed that we must increase our cooperation and our mutual understanding, including through more defense exercises and the recently established U.S.-China Cyber Working Group. And we continue to encourage China to work toward greater transparency.”285
The DoD accuses China of cyber-attacks, whilst calling for greater cooperation and dialog on the issue: “We are also clear-eyed about the challenges in cyber. The United States has expressed our concerns about the growing threat of cyber intrusions, some of which appear to be tied to the Chinese government and military. As the world’s two largest economies, the U.S. and China have many areas of common interest and concern, and the establishment of a cyber working group is a positive step in fostering U.S.-China dialogue on cyber. We are determined to work more vigorously with China and other partners to establish international norms of responsible behavior in cyberspace.”286
In June 2014, Chuck Hagel delivered a speech at the National Defense University in Beijing. In it, he made mention of cyberspace several times:
– The economies of the great nations are mutually interdependent, but in order to prosper they require stability – particularly at a regional level. However, the threats arising in cyberspace are among the destabilizing factors liable to hamper economic expansion. In this respect, China and the United States have a shared interest (peace for/because of the economy): “As our economic interdependence grows, we have an opportunity to expand the prosperity this region has enjoyed for decades. To preserve the stable regional security environment that has enabled this historic economic expansion, the United States and China have a very big responsibility to address new, enduring regional security challenges alongside all the partners of the Asia-Pacific. We face North Korea’s continued dangerous provocations, its nuclear program, and its missile tests; ongoing land and maritime disputes; threats arising from climate change, natural disasters, and pandemic disease; the proliferation of dangerous weapons; and the growing threat of disruption in space and cyberspace.”287
– The United States wishes to decry Chinese practices (cyber-espionage) and also to find a solution; the Americans want greater communication and less opacity, and call on China to communicate about its cyber strategies, as the US does: “Openness and two-way communication is especially important in the area of strategic and emerging capabilities, and in managing regional security challenges. It is why we seek to resume a U.S.-China nuclear policy and strategy dialogue. It is also why, through our Cyber Working Group, the United States has been forthright in our concerns about Chinese use of networks to perpetrate commercial espionage and intellectual property theft. We’ve also made efforts to be more open about our cyber capabilities, including our approach of restraint. Those efforts recently took a major step forward when the Department of Defense, for the first time ever, provided to representatives of the Chinese government a briefing on DoD’s doctrine governing the use of its cyber capabilities. We’ve urged China to do the same.”288
– The United States will defend the principle of freedom of access to cyberspace: “Here in the Asia-Pacific and around the world, the United States believes in maintaining a stable, rules-based order built on free and open access to sea lanes and air space, and now, cyberspace”. The “freedom”, of course, relates to economic and security interests, but also to conflicting values (America’s desire to impose liberal democratic values on the whole of the world).
8.2.3. Prospective analyses conducted by the National Intelligence Council
The “Global Trends 2010” report289, published in November 1997, predicts that powerful states will lose some of their prerogatives because of the expansion of information technologies throughout the world: “governments whose states are relatively immune from poverty and political instability will still find that they are losing control of significant parts of their national agendas due to the globalization and expansion of the economy, and the continuing revolution in information technology”. The report also holds that “information technologies will continue to be the hallmarks of the revolution in military affairs”. These considerations about ICTs do not include the prefix particle “cyber”. Nor do they associate China with ICT issues. The authors of the report do not envisage China, in the short or medium term, becoming a genuine military power, as they imagine this process would be disrupted by the country’s internal problems (managing growth, urbanization, energy and food requirements, etc.).
“Global Trends 2015”290, published in December 2000, introduces the issue of the cyber threat – one of a variety of transnational problems which the United States is likely to have to face by 2015. The cyber threat is all the greater because American society is so heavily dependent on computer networks. Thus, this theme – a cyber threat posed to the critical infrastructures, and therefore to the whole of society – was already on the radar nearly 15 years ago: “Increasing reliance on computer networks is making critical US infrastructures more attractive as targets. Computer network operations today offer new options for attacking the United States within its traditional continental sanctuary—potentially anonymously and with selective effects. Nevertheless, we do not know how quickly or effectively such adversaries as terrorists or disaffected states will develop the tradecraft to use cyberwarfare tools and technology, or, in fact, whether cyberwarfare will ever evolve into a decisive combat arm”. China is not associated with the issue of a cyber threat. It is, however, associated with the threat of Weapons of Mass Destruction: “Short- and medium-range ballistic missiles, particularly if armed with WMD, already pose a significant threat overseas to US interests, military forces, and allies. By 2015, the United States, barring major political changes in these countries, will face ICBM threats from North Korea, probably from Iran, and possibly from Iraq, in addition to long-standing threats from Russia and China.”
The report “Global Trends 2020, Mapping the Global Future”291, published in 2004, tackles the question of cyber-warfare, which is the title of one of its chapters.292 Major cyber-attacks are likely to be attributable to terrorism. (“Bioterrorism appears particularly suited to the smaller, better-in found groups. We also expect that terrorists will attempt cyber-attacks to disrupt critical information networks and, even more likely, to cause physical damage to information systems”) rather than to a State such as China. When the report speaks of China, it is not to describe it as presenting a cyber threat, but rather to highlight its vulnerability to economic instability and its progress in terms of knowledge production (China produces more graduates than any other major power – a process which will undoubtedly help it to eventually overcome its technological out datedness), and its capacity to create a regional security order in case the Americans withdraw.
In the view of the authors of the “Global Trends 2025” report293, published in 2008, America is likely to lose some of its advantage in terms of power, although its power will remain quite considerable. Cyberspace is one of the factors in the closing of the gap, which will have consequences for the exercising of American power: “growing use of cyberwarfare attacks increasingly will constrict US freedom of action”. The report defines “cyber” both as one of the non-military aspects of confrontation between states (“Non-military means of warfare, such as cyber, economic, resource, psychological, and information-based forms of conflict will become more prevalent in conflicts over the next two decades”) and as a tool to help circumvent American strength (“Cyber and sabotage attacks on critical US economic, energy, and transportation infrastructures might be viewed by some adversaries as a way to circumvent US strengths on the battlefield and attack directly US interests at home”). The mention of cyberspace (only 4 times) is not associated with the mention of China (154 references in the text). In this document, the Chinese cyber threat is not amongst the scenarios for the evolution of the international scene.
“Global Trends 2030”294, published in 2012, makes more mention of the “cyber” notion (36 references). In relation to cyber, the report evokes:
– the new capabilities provided to individuals and nonstate actors (“individuals and small groups will have greater access to lethal and disruptive technologies (particularly precision-strike capabilities, cyber instruments, and bioterror weaponry), enabling them to perpetrate large-scale violence— a capability formerly the monopoly of states”) which will benefit from facilitated access to a whole new range of weapons. Terrorists could profitably exploit these new technologies and those who have mastery of them: “With more widespread access to lethal and disruptive technologies, individuals who are experts in such niche areas as cyber systems might sell their services to the highest bidder, including terrorists who would focus less on causing mass casualties and more on creating widespread economic and financial disruptions;”
– “cyber” technologies are amongst the four forms of technology which will shape the world’s economic, social and military future. In particular, the report identifies data managing as a source of power (as the world moves into the Age of Big Data). However, the fear of an Orwellian order could drive societies to rein their governments in, with relation to their exploitation of big data;
– the risks of cyber-attacks by non-state actors rank among the major destabilizing factors;
– the report introduces notions which are absent from the previous reports: cyber weapons, cyber-attacks and cybercrime.295
In the various scenarios proposed, the cyber object is not directly correlated with the variable “China”. China is presented as one of the potential major factors in destabilizing the international scene: “China is slated to pass the threshold of US$15,000 per capita purchasing power parity (PPP) in the next five years or so—a level that is often a trigger for democratization. Chinese “soft” power could be dramatically boosted, setting off a wave of democratic movements. Alternatively, many experts believe a democratic China could also become more nationalistic. An economically collapsed China would trigger political unrest and shock the global economy”. This scenario does not associate China with a cyberthreat.
8.3. Conclusion
Table 8.1. The topics discussed in the Global Trends reports (regarding Chinaand cyberspace)
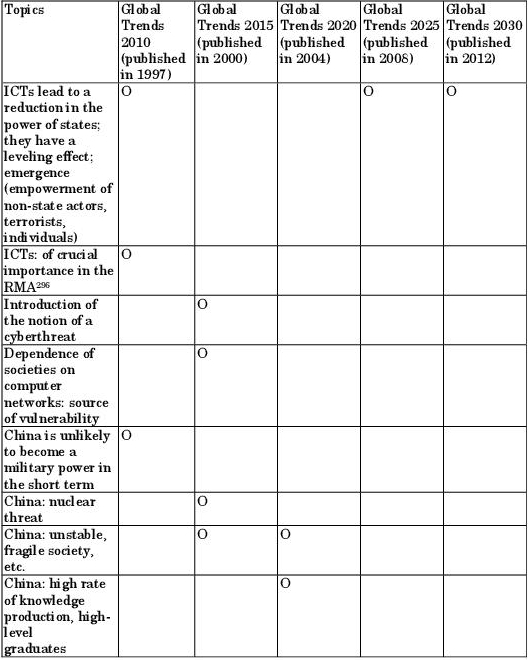
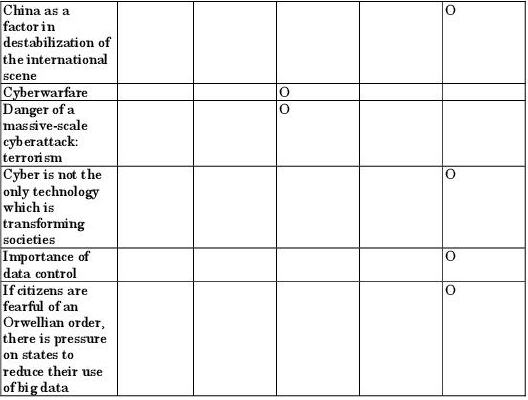
The reports of the National Intelligence Council therefore do not always associate China with “cyber”. China is not depicted as being a cyber threat. The authors of the reports prefer to emphasize the uncertainties engendered by the situation in China (what form of growth is taking place, how is the society evolving? etc.), which cause destabilization both within China and on the international scene. Whilst ICTs are at the heart of the issues of reconfiguration of the power balances (empowerment of individuals, non-state actors, terrorism, etc.), and whilst social pressure (because of the fear of an Orwellian world order) could cast doubt on the policies of countries in terms of data control and exploitation, it is also worthy of note that ICTs are not the only factors in the evolution of modern societies. This approach enables us to situate cyber issues within a broader field of problems, and to view China in the international space as something other than an agent upsetting order and security strategy because of its ambitions in cyberspace.
Table 8.2. Chinese Cybersecurity, cyberdefense and cyberspace, according to the DoD’s annual report to Congress
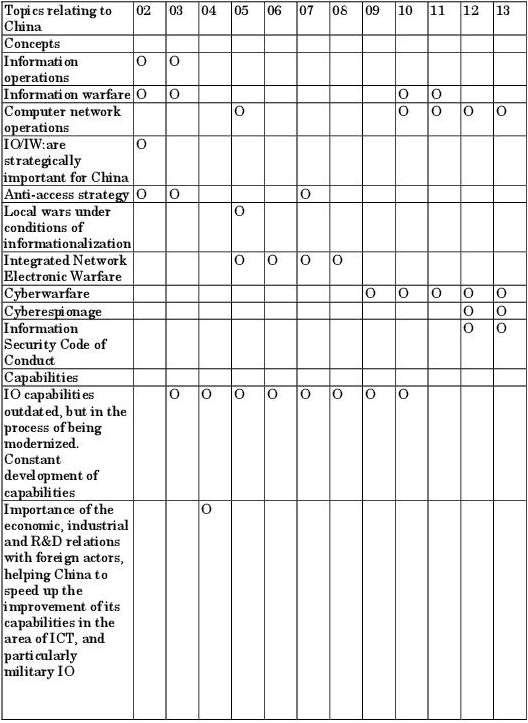

The DoD reports seem to focus on three main areas: the concepts which feed into China’s policies and defense strategies; the development of capabilities; and the strategy itself, the role attributed to ICTs and cyberspace.
In terms of concepts, although the notions of IW and IO have remained throughout the period 2002-2013, we can see that a transition takes place around 2005 (when the discussion is of the notion of Integrated Network Electronic Warfare), and then around 2008 there is a change of vocabulary to “cyber”, with discussions about cyberdefense (cyber-warfare, cyber-espionage, etc.). In terms of capabilities, whilst the reports highlighted how outdated the Chinese army was in 2002, all the later reports speak of the constancy of its efforts to develop, which are based on industry, and policies of acquisition of resources from outside the army (reserves and militias). Finally, in 2013, the report states that China’s cyberdefense is operational. Whilst the threat lay in the volatile relations between China and Taiwan at the start of the 2000s, from 2008 onwards the United States’ main concern demonstrably changes to the cyber-attacks to which it is being subjected. Thus, in the space of 12 years, according to these reports, China seems to have gone from having an armed force “under construction” to having an operational, active and offensive cyberdefense protocol. In this process, 2007-2008 seems to have been a hinge point. However, is this impression actually a reflection of the reality in China, or is it one that has been strategically projected by the Americans?
From the speeches given by the US Secretaries of Defense, we can also see that a transition took place in 2005-2006. From then on, China began making appearances in their speeches. There are two competing themes: one which condemns the opacity of the Chinese discourse, the lack of perspectives and clearly-declared intentions in terms of defense, which gives rise to doubts and concerns, instability which is damaging for the world economy; in parallel to this we see the call for greater exchanges and dialog, because the two nations are not enemies, but in fact have shared responsibilities when it comes to ensuring world stability. The table below clearly demonstrates the emergence of debate about China from the mid-2000s – particularly around 2007-2008, i.e. the period when the DoD reports began to openly condemn the cyber-attacks directed at America. Thus, just as we speak of “post-9/11” in reference to the turning point in the area of terrorism, in the debates about China and cyberspace in general, we can speak of the “post-2007” period.
Table 8.3. Themes in discourse on China in the DoD Annual Reports
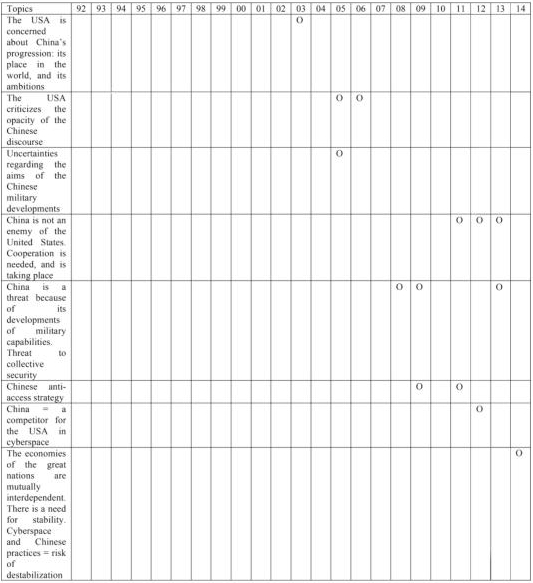
1 Nicholas Greenwood Onuf, World of Our Making. Rules and Rule in Social Theory and International Relations, Columbia (SC), University of South Carolina Press, 1989, 341 pages.
2 Alexander Wendt, Anarchy is what States make of it: The Social Construction of Power Politics, International Organization, 1992, vol. XLVI, no. 2, pp. 391–425.
3 Thomas Lindemann, Penser la guerre, l’apport constructiviste, Paris, L’Harmattan, 2009, 230 pages, p. 31.
4 Thierry Balzacq, Constructivism and Securitization Studies, in Myriam Dunn Cavelty, Victor Mauer (eds.), Handbook of Security Studies, London, Routledge, 504 pages. [http://graduateinstitute.ch/webdav/site/developpement/shared/developpement/cours/E777/Securitization_Balzacq.pdf].
5 Bradley Klein, Strategic Discourse and its alternatives, Center on Violence and Human Survival Occasional Paper, New York, January 1987, 24 pages.
6 – Michel Foucault, Power/Knowledge, Brighton, UK, Harvester, 1980, 288 pages.
– Michel Foucault, The Archeology of Knowledge and the Discourse on Language, London, Tavistock, 1972, 245 pages.
– Stuart Hall (ed.), Representation: Cultural Representations and Signifying Practices, London, Sage Publications, 1997, 408 pages.
– Nelson Phillips, Cynthia Hardy, Discourse Analysis: Investigating Processes of Social Construction, London, Sage, 2002, 104 pages.
7 Jeremy Moses, Discourse Analysis and International Politics: Rethinking Relations between the United States and China, Wuhan, China, International Conference on Political Communication, October 2007 [http://ir.canterbury.ac.nz/bitstream/10092/4989/1/12610075_Wuhan%20Paper.pdf].
8 – Liu Yongtao, Discourse, Meanings and IR Studies: Taking the Rhetoric of “Axis of Evil” As a Case, CON fines de relaciones internacionales y ciencia política, January–May 2010, no. 11, pp. 85–107, [http://web2.mty.itesm.mx/temporal/confines/articulos11/YongtaoL.pdf].
– John Langshaw Austin, Quand dire c'est faire, Paris, Éditions du Seuil, 1970, 202 pages.
– Pierre Bourdieu, Ce que parler veut dire : l'économie des échanges linguistiques, Paris, Fayard, 1982, 239 pages.
9 John Langshaw Austin, How to Do Things with Words, Oxford, Clarendon Press, 1962, 174 pages.
10 Jennifer Milliken, The Study of Discourse in International Relations: ACritique of Research and Methods, European Journal of International Relations, 1999, vol. 5, no. 2, ppp. 225–254.
11 Daniel Sabbagh, De la rhétorique à la pratique : les tribulations de la politique des États-Unis à l'égard de la Corée du Nord (1994-2002), Les Études du CERI, no. 89, September 2002 [http://www.sciencespo.fr/ceri/sites/sciencespo.fr.ceri/files/etude89.pdf].
12 Jim George, Discourses of Global Politics: ACritical (re) Introduction to International Relations, Boulder, Lynne Rienner, 1994, 266 pages.
13 Jeremy Moses, Discourse Analysis and International Politics: Rethinking Relations between the United States and China, Wuhan, China, International Conference on Political Communication, October 2007 [http://ir.canterbury.ac.nz/bitstream/10092/4989/1/12610075_Wuhan%20Paper.pdf].
14 [http://cadaad.net/files/journal/CADAAD2-2-Reyes-Rodriguez-2008-Hot&Cold_War.pdf].
15 Le pouvoir est un phénomène social qui a constamment besoin d'être légitimé : le langage est le vecteur, le médium de légitimation. Martin Wight, Power Politics, Hedley Bull, Carsten Holbraad (eds.), Leicester, Leicester University Press, 1978, 317 pages.
16 Ioana Laura Raicu, Critical Discourse Analysis of the War on Terror – Blairian Discourse and Philosophical Framework, Recent Advances in Computers, Communications, Applied social science and Mathematics, 2011, pp. 178–182.
17 Gilles Puel, “Géographie des lieux d'accès à Internet. Les conditions de l'accès public et les modèles d'usages dans les grandes villes de Chine”, L’Espace géographique, 2009, Vol. 38, no. 1, pp. 17–29, [www.cairn.info/revue-espace-geographique-2009-1-page-17.htm].
18 White Paper on the Internet in China, 15 June 2010, [http://china.org.cn/government/whitepaper/node_7093508.htm].
19 – CNNIC. Statistical Report on Internet Development in China, January 2013, 89 pages, [http://www1.cnnic.cn/IDR/ReportDownloads/201302/P020130221391269963814.pdf].
– CNNIC. Statistical Report on Internet Development in China, July 2013, 57 pages, [http://www1.cnnic.cn/IDR/ReportDownloads/201310/P020131029430558704972.pdf].
– China Internet Network Information Center (CNNIC), Statistical Report on the Internet Development in China, January 2012, [http://www.cnnic.cn/dtygg/dtgg/201201/t20120116_23667.html].
– Statistical report on Internet Development in China, 2011, CNNIC, 99 pages, [http://www1.cnnic.cn/uploadfiles/pdf/2011/2/28/153752.pdf].
- Statistical report on Internet Development in China, July 2010, CNNIC, 67 pages, [http://www.cnnic.cn/uploadfiles/pdf/2010/8/24/93145.pdf].
– The 23rd Statistical Survey Report on the Internet Development in China,[http://www.cnnic.net.cn/uploadfiles/pdf/2009/3/23/153540.pdf].
– Statistical Survey Report on the internet development in China, January 2008, CNNIC, 87 pages, [http://www.cnnic.cn/uploadfiles/pdf/2008/2/29/104126.pdf].
– CNNIC, The First Statistical Survey Reports on the Internet Development in China, 1997, 3 pages, [http://www.cnnic.net.cn/download/manual/en-reports/1.pdf].
20 2008 China Statistical Yearbook, [http://www.stats.gov.cn/tjsj/ndsj/2008/indexeh.htm].
21 China Websites Ranking, [http://main.chinarank.org.cn/statistics/hot_vid.html].
22 Sogou User Query Logs, [http://www.sogou.com/labs/dl/q.html].
23 Liu Dong, China Internet Overview, 2005, 13 pages, [http://www.meti.go.jp/report/downloadfiles/gokin11j.pdf].
24 Jane Lael, Internet in China, US-China Review, summer 2006, 5 pages, [http://www.uscpfa.org/document/Internet%20in%20China.pdf].
25 Z. Shi, Z. Guo, Chinese Internet AS-level Topology, IET Communications. Vol. 1, no.° 2, ppp. 209–214, 2007 .
26 Burson-Marsteller, State of the Chinese Internet, March 2011, 57 pages, [http://www.bmchina.com.cn/EN/Documents/Burson-Marsteller_State_of_the_Chinese_Internet_March_2011.pdf].
27 Qiheng Hu, Internet development in China, Internet society of China and CNNIC, September 2007, Potsdam, Germany, 30 pages, [http://www.hpi.uni-potsdam.de/fileadmin/hpi/veranstaltungen/china/slides/070919_S1_2_HU_Internet_in_China.pdf].
28 Zhang Guanqun, Wang Hui, Yang Jiahai, Understanding Web Hosting Utility of Chinese ISPs, The Network Research Center, Tsinghua University, Tsinghua National Laboratory for Information Science and Technology (TNList), Beijing, China, Lecture Notes in Computer Science Volume 5787, 2009, pp. 11–20, [http://nmgroupp.tsinghua.edu.cn/yang/paper/(54540)Understanding%20Web%20Hosting%20Utility%20of%20Chinese%20ISPs.pdf].
29 He L., Gui L., Le Q., Spatial-Temporal Analysis of Regional Disparities of Internet in China. Chinese Geographical Science.14(4), 314-319 (2004).
30 Guo Liang, Surveying Internet usage and impact in five Chinese cities, CASS Internet survey report, Washington, United States, 2005, 144 pages, [http://www.policyarchive.org/handle/10207/bitstreams/15538.pdf].
31 Guo Liang, Surveying Internet usage and impact in seven Chinese cities, CASS Internet survey report, Washington, United States, November 2007, 126 pages, [http://www.policyarchive.org/handle/10207/bitstreams/16013.pdf].
32 Zhu Gaofeng, ICT initiatives in China, China Communications, April 2005, pp. 4–12, [http://www.china-cic.org.cn/english/digital%20library/200504/1.pdf].
33 Nir Kshetri, The Evolution of the Chinese Online Gaming Industry, Journal of Technology Management in China, vol.4, no. 2, pp. 158–197, 2009.
34 Jiang Zemin, On the Development of China's Information Technology Industry, 2010, Academic Press, 336 pages.
35 Xiangning Wu, China’s ICT Industry and East Asian Regional Production Networks, PhD Thesis, University of Birmingham, 2010, 371 pages, [http://etheses.bham.ac.uk/1150/1/Wu10PhD.pdf].
36 George I. Askew, Steve Rubis, China Internet Industry – Vast, Unique and Dynamic, Stifel Nicolaus, November 16, 2010, 48 pages, [http://www.arbaholdings.com/insights/doc/China_Internet_Industry.pdf].
37 Guobin Yang, A Chinese Internet? History, Practice, and Globalization, Chinese Journal of Communication, Vol. 5, No. 1, March 2012, 49–54, [http://www.asc.upenn.edu/gyang/CJC_Chinese_Internet.pdf].
38 Michael Pecht, Weifeng Liu, Computers in China, Chapter 3, pp. 47–60, [http://itri2.org/ttec/aemu/report/c3.pdf].
39 The ICT Market in China, EU SME Centre, 2013, 18 pages, [http://www.ccilc.pt/sites/default/files/eu_sme_centre_report_the_ict_market_in_china_en.pdf].
40 Zhu W., China Factor in International Division in East Asia of 1990s, China Opening Herald, 06/01/01, p. 15.
41 Ted Tschang, China’s Software Industry and its implications for India, OECD Report, February 2003, 37 pages, [http://www.oecd.org/dev/2497604.pdf].
42 Xiangning Wu, China’s ICT Industry and East Asian Regional Production Networks, PhD Thesis, University of Birmingham, 2010, 371 pages, [http://etheses.bham.ac.uk/1150/1/Wu10PhD.pdf].
43 Investigative Report on the U.S. National Security Issues Posed by Chinese Telecommunications Companies Huawei and ZTE, House Permanent Select Committee on Intelligence, October 8, 2012, 60 pages.
44 Lucas Solorio, China's Evolving IT Capabilities: Cloud Computing, Network Operations and Cyber Espionage, Nova Science Publishers Inc, 193 pages, March 2014.
45 Peter K. Yu, Barriers to foreign investment in the Chinese internet industry, 2001, 5 pages, [http://www.peteryu.com/gigalaw0301.pdf].
46 A Crackdown on Foreign Involvement in China’s Internet Industry?, September 2006, Wilmer Hale, Briefing series, 4 pages, [http://www.wilmerhale.com/uploadedFiles/WilmerHale_Shared_Content/Files/Editorial/Publication/06_449_China.pdf].
47 Lijun Cao, A Study on Self-regulatory Initiatives in China’s Internet Industry, 2007, 59 pages, [http://www.lse.ac.uk/media@lse/research/mediaWorkingPapers/MScDissertationSeries/Past/Cao_final.pdf].
48 Séverine Arsène, “Chine : Internet, levier de puissance nationale”, Politique étrangère, 2/ 2012 (Eté), pp. 291–303, [www.cairn.info/revue-politique-etrangere-2012-2-page-291.htm].
49 Jonathan Z., Enhai W., Diffusion, Use, and Effect of the Internet in China, Communications of the ACM, Vol. 48, no.°4, pp. 49–53, 2005.
50 Mayer Brown, New Internet rules in China, 3 pages, 15 February 2012, [http://www.mayerbrown.com/public_docs/120215_PRC_IPP.pdf].
51 Scott J. Shackelford, “Beyond the new digital divide: analyzing the evolving role of national governments in internet governance and enhancing cybersecurity”, Stanford Journal of International Law, Vol.5, no. °1, pp. 119–184, 2014.
52 Calum MacLeod, “Chinese create online jokes to vent political frustration”, 29 December 2012, USA Today, [http://usatoday30.usatoday.com/money/world/2010-12-29-chinainternet29_CV_N.htm].
53 Philip Sohmen, 2001, “Taming the Dragon: China’s Efforts to Regulate the Internet”, Stanford Journal of East Asian Affairs, Spring 2001, Vol.1, pp. 17-26, [http://www.stanford.edu/group/sjeaa/journal1/china1.pdf].
54 Jason PP. Abbott, “[email protected]? The challenges of the emancipatory potential of the net: lessons from China and Malaysia”, Third World Quarterly, vol. 22, n°, pp. 99–114, 2001, [http://courses.essex.ac.uk/gv/gv905/W20%20Readings/internet_china_malaysia.pdf].
55 Michael S. Chase, James Mulvenon, Political use of the internet in China, Chapter 1, 43 pages, dans Michael Case, James Mulvenon, You've got dissent, Chinese dissident use of the internet and Beijing's counter-strategies, RAND Corporation, United States, 2002, 132 pages, [http://www.rand.org/pubs/monograph_reports/MR1543.html].
56 Christopher R. Hughes, “Pourquoi Internet ne démocratisera pas la Chine”, Critique internationale 2/2002 (no. 15), pp. 85–104, [http://www.cairn.info.gate3.inist.fr/revue-critique-internationale-2002-2-page-85.htm#citation].
57 Chin-fu Hung, “Public Discourse and ‘Virtual’ Political Participation in the PRC: The Impact of the Internet”, Issues & Studies, Vol. 39, No. 4, December 2003, ppp. 1–38.
58 Chin-fu Hung, The Political Impact of the Internet in the People’s Republic of China: A Critical Perspective, Paper presented to the 2005 Annual Meeting of the Taiwan Information Society Association at the Shih Hsin University, Taipei, on 5 June 2005, 38 pages, [http://www.tais.org.tw/doc/2005/2005-8.pdf].
59 Chin-Fu Hung, “The Politics of China’s Wei-Quan Movement in the Internet Age”, International Journal of China Studies, Vol. 1, No. 2, October 2010, pp. 331–349, [http://ics.um.edu.my/images/ics/IJCSV1N2/hung.pdf].
60 – The OpenNet Initiative: Probing Chinese search engine filtering. Bulletin 005, August 2004, [http://www.opennetinitiative.net/bulletins/005/].
– The OpenNet Initiative: Internet Filtering in China in 2004{2005: A Country Study, June 2004, [http://www.opennetinitiative.net/studies/china/ONIChinaCountryStudy.pdf].
61 Wei Qi, Cyberspace and Political Participation in Contemporary China, Lund University, 2005, 52 pages, [http://lupp.lub.lu.se/luur/download?func=downloadFile&recordOId=1326373&fileOId=1326374].
62 Gary D. Rawnsley, The media, Internet and governance in China, China Policy Institute, The University of Nottingham, Discussion paper 12, September 2006, 18 pages, [http://www.nottingham.ac.uk/cpi/documents/discussion–papers/discussion-paper-12-china-media-internet-governance.pdf].
63 Chunzhi Wang, Benjamin Bates, Online Public Sphere and Democracy in China, Paper presented at IAMCR, Stockholm, July 2008, 19 pages, [http://web.cci.utk.edu/~bates/papers/iamcr08-wang-bates-publics.pdf].
64 Xiaoru Wang, Behind the great firewall: the internet and democratization in China, University of Michigan, United States, 261 pages, 2009, [http://deepblue.lib.umich.edu/bitstream/2027.42/64681/1/wangx_1.pdf].
65 Ashley Esarey, Xiao Qiang, Digital Communication and Political Change in China, International Journal of Communication 5 (2011), 298– 319, [http://ijoc.org/index.php/ijoc/article/viewFile/688/525].
66 Séverine Arsène, Protester sur le Web chinois (1994-2011), Le Temps des médias, 1/ 2012 (no.° 18), pp. 99–110, [www.cairn.info/revue-le-temps-des-medias-2012-1-page-99.htm].
67 Yiyi Lu, The Extreme Tilt of Chinese Internet Politics, November 4, 2013, blog The Wall Street Journal, [http://blogs.wsj.com/chinarealtime/2013/11/04/the-extreme-tilt-of-chinese-internet-politics/].
68 Jiao Bei, How Chinese journalists use microblogging for investigative reporting, University of Oxford, 2013, 39 pages, [https://reutersinstitute.politics.ox.ac.uk/fileadmin/documents/Publications/fellows__papers/2012-2013/How_Chinese_journalists_use_Weibo_microblogging_for_investigative_reporting.pdf].
69 Loubna Skalli-Hanna, Cyber Dissidents: The Potentials and Limitations of Using Social Media for Political Activism, Washington, American University, Spring 2013, 31 pages, [http://aladinrc.wrlc.org/bitstream/handle/1961/14956/Baumgartner,%20Jackie%20-%20Spring%202013.pdf?sequence=1].
70 Jonathan Zittrain, Benjamin Edelman, Internet filtering in China, Harvard Law School Public Law, Research Paper No. 62, Social Science Research Network Electronic Paper Collection, IEEE Internet Computing, March/April 2003, 9 pages, [http://unpan1.un.org/intradoc/groups/public/documents/apcity/unpan011043.pdf, [http://ssrn.com/abstract_id=399920].
71 James A. Lewis, The Architecture of Control: Internet Surveillance in China, Center for Strategic and International Studies, Washington, United States, July 2006, 8 pages, [http://csis.org/files/media/csis/pubs/0706_cn_surveillance_and_information_technology.pdf].
72 Rebecca Mackinnon, Cyber Zone, China’s online pioneers are pushing the boundaries of free speech, July 2008, pp. 82–89, [http://www.indexoncensorshipp.org/wp-content/uploads/2008/07/mackinnon_a_308337.pdf].
73 Xiaoru Wang, Behind the great firewall: the internet and democratization in China, 2009, PhD Thesis, University of Michigan, 261 pages, [http://deepblue.lib.umich.edu/bitstream/handle/2027.42/64681/wangx_1.pdf?sequence=1].
74 Shishir Nagaraja, Ross Anderson, The snooping dragon: social-malware surveillance of the Tibetan movement, March 2009, technical report n°746, University of Cambridge, United Kingdom, 12 pages, [http://www.cl.cam.ac.uk/techreports/UCAM-CL-TR-746.pdf].
75 China, journey to the heart of internet censorship, RSF, October 2007, 17 pages, [http://www.rsf.org/IMG/pdf/Voyage_au_coeur_de_la_censure_GB.pdf].
76 Xueyang Xu, Z. Morley Mao, and J. Alex Halderman, Internet Censorship in China: Where Does the Filtering Occur?, N. Spring and G. Riley (eds.): PAM 2011, LNCS 6579, ppp. 133–142, 2011., Springer-Verlag Berlin Heidelberg, 10 pages, [http://web.eecs.umich.edu/~zmao/Papers/china-censorship-pam11.pdf].
77 Emilie Frenkiel, Entre les mailles. L’internet chinois, pp. 81–94 in Emilie Frenkiel, Jean-Louis Rocca (eds.), La Chine en mouvements, Presses Universitaires de France, 2013, 100 pages.
78 S. Zhao, A State-led Nationalism: The Patriotic Education Campaign in Post-Tiananmen China, Communist and Post-Communist Studies, 31(3), pp. 287–302, 1998.
79 Christopher R. Hughes, Nationalism in Chinese Cyberspace, Cambridge Review of International Affairs, 13(2), pp. 195–209, 2000, [http://www.informaworld.com/10.1080/09557570008400309].
80 Yu Huang, Approaching “Pareto Optimality”? --- A Critical Analysis of Media-Orchestrated Chinese Nationalism, Intercultural Communication Studies XI, 2, 2002, pp. 69–82, [http://www.uri.edu/iaics/content/2002v11n2/05%20Yu%20Huang.pdf].
81 Françoise Mengin (ed.), Cyber China: Reshaping National Identities in the Age of Information, CERI Series in International Relations and Political Economy, Palgrave Macmillan, November 2004, 288 pages.
82 Z. Wang, National Humiliation, History Education, and the Politics of Historical Memory: Patriotic Education Campaign in China, International Studies Quarterly, 52, pp. 783–806, 2008.
83 W.A. Callahan, National Insecurities: Humiliation, Salvation, and Chinese Nationalism, Alternatives, 29, pp. 199–218, 2004.
84 Louis Yu, Sitaram Asur, Bernardo A. Huberman, What Trends in Chinese Social Media, The 5th SNA-KDD Workshop’11 (SNA-KDD’11), August 21, 2011, San Diego CA USA, 10 pages, [http://www.hpl.hpp.com/research/scl/papers/chinatrends/china_trends.pdf].
85 China's censorship of the internet and social media: the human toll and trade impact, Hearing before the Congressional-executive Commission on China, 17 November 2011, 77 pages, [http://www.cecc.gov/sites/chinacommission.house.gov/files/documents/hearings/2011/CECC%20Hearing%20-%20China's%20Censorship%20of%20the%20Internet%20and%20Social%20Media%20-%2011.17.11.pdf].
86 Edward Tse, Adam Xu, Andrew Cainey, Impact of social media in China, Booz&co, 2012, 12 pages, [http://www.strategyand.pwc.com/media/file/Strategyand_Impact-of-Social-Media-in-China_EN.pdf].
87 Social media in China: Local innovation connecting the country, KPMG, China 360, April 2013, 5 pages, [https://www.kpmg.com/CN/en/IssuesAndInsights/ArticlesPublications/Newsletters/China-360/Documents/China-360-Issue8-201304-Social-media-in-China-v1.pdf]
88 Haiqing Yu, The power of thumbs: the politics of SMS in urban China, Graduate Journal of Asia-Pacific Studies, 2:2 (2004), 30-43, [http://www.crr.unsw.edu.au/media/File/The_Power_of_Thumbs.pdf].
89 Rebecca Mackinnon, Networked Authoritarianism in China and Beyond: Implications for global Internet freedom, Stanford University, paper presented at Liberation Technology in Authoritarian Regimes, 11-12 October 2010, 31 pages, [http://iis-db.stanford.edu/evnts/6349/MacKinnon_Libtech.pdf].
90 Qin Guo, Internet and political participation in China, Masaryk University Journal of Law and Technology, vol.5, no. 1, 2011, pp. 83–103, [http://mujlt.law.muni.cz/storage/1327951326_sb_08-guo.pdf].
91 Gary King, Jennifer Pan, Margaret E. Roberts, How Censorship in China Allows Government Criticism but Silences Collective Expression, American Political Science Review, May 2013, 18 pages, [http://gking.harvard.edu/files/gking/files/censored.pdf].
92 Emilie Frenkiel, Entre les mailles. L’internet chinois, in Emilie Frenkiel, Jean-Louis Rocca (eds.), La Chine en mouvements, Presses Universitaires de France, 2013, p. 81.
93 Tai Zixue, The Internet in China: Cyberspace And Civil Society, 2006.
94 Zhou Yongming, Historicizing Online Politics: Telegraphy, the Internet, and Political Participation in China, 2006, 304 pages, Stanford University Press.
95 Xu Wu, Chinese Cyber Nationalism: Evolution, Characteristics, and Implications, Lexington Books, United States, 2007, 280 pages.
96 Yongnian Zheng, Technological Empowerment: The Internet, State, and Society in China, Stanford University Press, United States, November 2007, 272 pages.
97 Rebecca Fannin, Silicon Dragon: How China Is Winning the Tech Race, McGraw-Hill, January 2008, 300 pages.
98 Sherman So, J. Christopher Westland, Red Wired: China’s Internet Revolution, Marshall Cavendish Limited, November 2009, 256 pages.
99 Tiebing Xu, L'émergence des opinions parallèles, Hermès, La Revue 3/ 2009 (no. 55), pp. 80–82, [www.cairn.info/revue-hermes-la-revue-2009-3-page-80.htm].
100 Hong Xue, Cyber Law in China, 2010.
101 Yun Zhao, Cyber Law in Hong Kong, 2011.
102 Wang Jun, Cyber Nationalism and China's Foreign Affairs, China Social Sciences Press, January 2011, 299 pages.
103 Guobin Yang, The Power of the Internet in China: Citizen Activism Online, Columbia University Press, 320 pages, 2011.
104 Rodney Wai-chi Chu, Leopoldina Fortunati, Pui-Lam Law, Shanhua Yang, Mobile Communication and Greater China, Routledge Research on Social Work, Social Policy and Social Development in Greater China, 2012.
105 Guosong Shao, Internet law in China, Chandos Asian Studies, 2012.
106 David Hanel, Chinese Cybercrime - A Threat to the Occident? The Impact of Chinese Cybercrime on EU –China Relations, University of Twente, Netherlands, June 2013, 45 pages, [http://essay.utwente.nl/63300/1/Bachelor_Paper_Final_Version_d.hanel_s1062336.pdf].
107 Tobias Feakin, Enter the Cyber Dragon, Understanding Chinese intelligence agencies cyber capabilities, Special Report, ASPI, Australia, June 2013, 12 pages, [https://www.aspi.org.au/publications/special-report-enter-the-cyber-dragon-understanding-chinese-intelligence-agencies-cyber-capabilities/10_42_31_AM_SR50_chinese_cyber.pdf].
108 – Victor Benjamin, Hsinchun Chen, Securing cyberspace: identifying key actors in hacker communities, 2013, 6 pages, [http://web.elastic.org/~fche/mirrors/www.jya.com/2013/03/key-hackers.pdf].
– Jack Linchuan Qiu, Chinese Hackerism in Retrospect: The Legend of a New Revolutionary Army, 14 pages, [http://ncsi-net.ncsi.iisc.ernet.in/cyberspace/societal-issues/Qiu1.pdf].
109 – Risk Briefing Paper: China & Cyber Crime, KCS Country Risk & Threat Advisory, 20 December 2011, 9 pages, [http://www.kcsgroupp.com/wp-content/uploads/2012/01/KCS_China.pdf].
– Council of Europe, China, Cybercrime Legislation, Country Profile, 28 March 2008, 39 pages, [http://www.cyberlawdb.com/gcld/wp-content/uploads/2010/04/china.pdf].
– Man Qi, Yongquan Wang, Rongsheng Xu, Fighting cybercrime: legislation in China, Int. J. Electronic Security and Digital Forensics, Vol. 2, No. 2, 2009, pp. 219–227, [http://inderscience.metapress.com/content/a67161603x6x8011/].
110 Flora Yufen Wang, Riding the Tiger, Chinese Cyber Nationalism and the Sino-Japanese Relationship, Stanford University, Thesis, 31 May 2013, 146 pages, [http://iis-db.stanford.edu/docs/785/Wang_Flora_Thesis_Final.pdf]
111 – Michael Riley, John Walcott, China-Based Hacking of 760 Companies Shows Cyber Cold War, Bloomberg, Dec 14, 2011, [http://www.bloomberg.com/news/2011-12-13/china-based-hacking-of-760-companies-reflects-undeclared-global-cyber-war.html].
– Robert Lai, Syed (Shawon) Rahman, Analytic of China Cyber-Attack, The International Journal of Multimedia & Its Applications (IJMA), Vol.4, No.3, June 2012, pp. 37-56, [http://airccse.org/journal/jma/4312ijma04.pdf].
112 – Zhuge Jianwei, Gu Liang, Duan Haixin, Investigating China’s Online Underground Economy, IGCC, University of California, July 2012, 54 pages, [http://igcc.ucsd.edu/assets/001/503677.pdf].
– Lion Gu, The Mobile Cybercriminal Underground Market in China, Cyber Criminal Underground economy Serie S, A Trend Micro Research Paper, 2014, 17 pages, [http://www.trendmicro.com/cloud-content/us/pdfs/security-intelligence/white-papers/wp-the-mobile-cybercriminal-underground-market-in-china.pdf].
113 James A. Lewis, Computer Espionage, Titan Rain and China, Center for Strategic and International Studies – Technology and Public Policy Program, December 2005, 2 pages, [http://csis.org/files/media/csis/pubs/051214_china_titan_rain.pdf].
114 Mike Rogers, Investigative Report on the U.S. National Security Issues Posed by Chinese Telecommunications Companies Huawei and ZTE, U.S. House of Representatives, 112th Congress, October 8, 2012, 52 pages, [https://intelligence.house.gov/sites/intelligence.house.gov/files/documents/Huawei-ZTE%20Investigative%20Report%20(FINAL).pdf].
115 T. Yoshihara, Chinese Information Warfare a Phantom Menace or Emerging Threat? Carlisle, Strategic Studies Institute, U.S. Army War College, 2001.
116 Peter Hays Gries, Tears of rage: Chinese nationalist reactions to the Belgrade Embassy bombing, The China Journal, n°46, July 2001, pp. 25-43, [http://www.ou.edu/uschina/gries/articles/texts/TearsofRage.pdf].
117 John Tkacik, Trojan Dragon: China’s Cyber Threat, 8 February 2008. [http://www.heritage.org/research/reports/2008/02/trojan-dragon-chinas-cyber-threat].
118 Jayadeva Ranade, China and the latent cyber threat, Centre for Air Power Studies, New Delhi, 1 March 2010, 5 pages, [http://capsindia.org/files/documents/ISSUE-BRIEF_22_CHINA-AND-THE–LATENT-CYBER-THREAT_01-March-2010.pdf].
119 Derek Scissors, Steven Bucci, China Cyber Threat: Huawei and American Policy Toward Chinese Companies, The Heritage Foundation, Issue Brief, Washington, October 23, 2012, n°3761, 3 pages, [http://thf_media.s3.amazonaws.com/2012/pdf/ib3761.pdf].
120 Tim Jordan, Paul Taylor, A sociology of hackers, Blackwell Publishers, pp. 757–780, 1998, [http://cj-resources.com/CJ_Crim_Theory_pdfs/A%20sociology%20of%20hackers%20-%20Jordan%20et%20al%201998.pdf].
121 Thomas J. Holt, Deborah Strumsky, Olga Smirnova, Max Kilger, Examining the Social Networks of Malware Writers and Hackers, International Journal of Cyber Criminology, Vol 6 Issue 1 January – June 2012, pp. 891–903, [http://www.cybercrimejournal.com/holtetal2012janijcc.pdf].
122 Christian S. Fötinger, Wolfgang Ziegler, Understanding a hacker’s mind – A psychological insight into the hijacking of identities, Danube-University Krems, Austria, 48 pages, [http://www.donau-uni.ac.at/de/department/gpa/informatik/DanubeUniversityHackersStudy.pdf].
123 Josh Rogin, Cyber Officials: Chinese Hackers Attack ‘Anything and Everything’, FCW.com, February 13, 2007, [https://www.grc.com/sn/files/fcw_on_%20cyber_warefare.pdf].
124 Chinese Hacking: impact on human rights and commercial rule of law, Hearing before the Congressional-executive Commission on China, 113th Congress, 1st Session, USA, June 25, 2013, 58 pages, [http://www.gpo.gov/fdsys/pkg/CHRG-113hhrg81855/pdf/CHRG-113hhrg81855.pdf].
125 Formule qui aurait été utilisée par des experts en sécurité de la société Arbor Networks. Cited in: Scott Henderson, Beijing’s Rising Hacker Stars… How Does Mother China React?, IO Sphere, Fall 2008, pp. 25-30.
126 – Scott Henderson, Beijing’s Rising Hacker Stars… How Does Mother China React?, IO Sphere, Fall 2008, pp. 25–30, [http://fmso.leavenworth.army.mil/documents/Beijings-rising-hackers.pdf]. – Zhang Jianwen, The current situation of cybercrimes in China, International Centre for Criminal Law Reform and Criminal Justice Policy, Vancouver, Canada, November 2006, [http://www.icclr.law.ubc.ca/china_ccprcp/files/Presentations%20and%20Publications/47%20The%20Current%20Situation%20of%20Cybercrime%20in%20China_English.pdf]
127 Michael Yip, An investigation into Chinese cybercrime and the underground economy in comparison with the West, 2011, [http://journal.webscience.org/411/1/yipp.pdf].
128 Zhuge Jianwei, Gu Liang, DuanHaixin, Investigating China’s Online Underground Economy, University of California, IGCC, July 2012, 54 pages, [http://www-igcc.ucsd.edu/assets/001/503677.pdf].
129 Aidong Xu, Yan Gong, Yongquan Wang, Nayan Ai, On Different Categories of Cybercrime in China, Forensics in Telecommunications, Information, and Multimedia, Lecture Notes of the Institute for Computer Sciences, Social Informatics and Telecommunications Engineering Volume 56, 2011, pp. 277-281.
130 Yao Chung Lennon Chang, Sing Wing Dennis Wong, Cyber-crime and cyber-deviance among adolescents in Hong-Kong, City University of Hong Kong, HKFYG Youth Crime Prevention Centre, July 2013, 91 pages, [http://ycpc.hkfyg.org.hk/files/youthlaw/download/201307-web-cyber-crime_and_cyber-deviance_among_adolescents_in_hong_kong.pdf].
131 Lennon Yao-Chung Chang, Cybercrime in the Greater China Region: Regulatory Responses and Crime Prevention Across the Taiwan Strait, Edward Elgar, January 2013, 272 pages.
132 David Hanel, Chinese Cybercrime – A Threat to the Occident? The Impact of Chinese Cybercrime on EU – China Relations, University of Twente, Netherlands, June 2013, 45 pages, [http://essay.utwente.nl/63300/1/Bachelor_Paper_Final_Version_d.hanel_s1062336.pdf].
133 Mandiant, APT1: Exposing One of China’s Cyber Espionage Units, 76 pages, February 2013, [http://intelreport.mandiant.com/Mandiant_APT1_Report.pdf].
134 James Lewis, Cyber Espionage and the Theft of U.S. Intellectual Property and Technology, Testimony, Committee on Energy and Commerce, U.S. House of Representatives, July 9, 2013, 10 pages, [http://csis.org/files/attachments/ts130709_lewis.pdf].
135 Michael Yip, Craig Webber, Hacktivism: a Theoretical and Empirical Exploration of China’s Cyber Warriors, 2011, WebSci ’11, June 14-17, 2011, Koblenz, Germany, 8 pages, [http://www.websci11.org/fileadmin/websci/Papers/59_paper.pdf].
136 Alexandra Samuel, Hacktivism and the Future of Political Participation, Chapter I, 35 pages, 2006, [http://www.alexandrasamuel.com/dissertation/pdfs/Samuel-Hacktivism-chapter1.pdf].
137 Sheo Nandan Pandey, Hacktivism of Chinese Characteristics and the Google Inc. Cyber-Attack Episode, ISPSW Institute for Strategic, Political, Security and Economic Consultancy, 2010, 8 pages, [http://mercury.ethz.ch/serviceengine/Files/ISN/113440/ipublicationdocument_singledocument/2533e975-eb94-4b60-97c3-8ac96ee73ddd/en/Hacktivism_Pandey_Mar10.pdf].
138 Image source: [http://www.wyxuan.coni/pic/liacker/22.jpg]. Placed online in 2011. Downloaded on 20 March 2014.
139 Other Screenshots from websites defaced by Chinese hacktivists are available at: [http://cache.baiducontent.com/c?m=9d78d513d9d706ef06e2ce384b54c0676a499d33628a85027fa3d31fcf240cld506694ea7a7d0d4589963c301caa4b5ceaf7367235083db69bce8d4ddabf972e2d&p=8b2a975490934ead0cflc52a4d&newp=8b2a970786cc43fe02b3dd3clb53d8304a02c70e3f95&user=baidu].
140 Arthur S. Ding, China’s Revolution in Military Affairs: An Uphill Endeavour, Security Challenges, vol. 4, no. 4 (Summer 2008), pp. 81–99, [http://securitychallenges.org.au/ArticlePDFs/vol4no4Ding.pdf].
141 James Mulvenon, The PLA and Information Warfare, in James Mulvenon, Richard H. Yang (eds.), The People’s Liberation Army in the Information Age, 297 pages, 1999, RAND Corporation, Washington, United States, pp. 175-186, Actes de la conférence tenue à San Diego, Californie, 9-12 July 1998, [http://www.rand.org/content/dam/rand/pubs/conf_proceedings/CF145/CF145.chap9.pdf; [http://www.rand.org/pubs/conf_proceedings/CF145.html].
142 Toshi Yoshihara, Chinese Information Warfare: a phantom menace or emerging threat? Strategic Studies Institute, November 2001, 41 pages, [http://www.au.af.mil/au/awc/awcgate/ssi/chininfo.pdf].
143 Nina Hachigan, China’s Cyber-Strategy, Foreign Affairs 80, no. 2, 2001, pp. 118–133.
144 Timothy L. Thomas, The Internet in China: Civilian and Military Uses, Information & Security, An International Journal, Volume 7, 2001, pp. 159–173, [http://library.uoregon.edu/ec/e-asia/read/netuse.pdf].
145 Timothy L. Thomas, Dragon Bytes: Chinese information war theory and practice, Foreign Military Studies Office, 2004, 168 pages, United States; [http://www.ists.dartmouth.edu/events/abstract-TimThomas.html].
146 Timothy L. Thomas, Cyber Silhouettes: Shadows Over Information Operations, Foreign Military Studies Office, 334 pages, United States.
147 Timothy L. Thomas, Decoding The Virtual Dragon – Critical Evolutions In The Science And Philosophy Of China's Information Operations And Military Strategy – The Art Of War And IW, Foreign Military Studies Office (FMSO), United States, 2007.
148 Timothy L. Thomas, Cyber Silhouettes: Shadows Over Information Operations, Foreign Military Studies Office (FMSO), Fort Leavenworth, KS, United States, 2009, 298 pages.
149 Ken Dunham, Jim Melnick, ‘Wicked Rose’ and the NCPH Hacking Group, VeriSign iDefense, 2006.
150 Brian Mazanec, Cyberwarfare as an Element of PRC National Power and its Implications for U.S. National Security, Brian Mazanec Pub., Amazon Digital Services, 113 pages, December 2008.
151 K. Coleman, Defense Tech: China’s Cyber Forces, 8 May 2008, Defensetech.org, [http://defensetech.org/2008/05/08/chinas-cyber-forces/].
152 Ron Deibert, Rafal Rohozinski, Tracking GhostNet: Investigating a Cyber Espionage Network, Sec Dev Group & University of Toronto, Munk Centre for International Studies, 29 March 2009, Canada, 53 pages, [http://www.nartv.org/mirror/ghostnet.pdf].
153 – Bryan Krekel, George Bakos, Capability of the People’s Republic of China to Conduct Cyber Warfare and Computer Network Exploitation, Northrop Grumman Corp, prepared for the US-China Economic and Security Review Commission, 9 October 2009, 61 pages, United States, [http://www.uscc.gov/researchpapers/2009/NorthropGrumman_PRC_Cyber_Paper_FINAL_Approved%20Report_16Oct2009.pdf].
– Bryan Krekel, Patton Adams, George Bakos, Occupying the information high-ground; Chinese capabilities for computer network operations and cyber-espionage, Prepared for the U.S.-China Economic and Security Review Commission by Northrop Grumman Corp, 7 March 2012, 136 pages, United States, [http://origin.www.uscc.gov/sites/default/files/Research/USCC_Report_Chinese_Capabilities_for_Computer_Network_Operations_and_Cyber_%20Espionage.pdf].
154 Jeffrey Carr, Inside Cyber Warfare: mapping the cyber underworld, O'Reilly Media, United States, December 2009, 240 pages.
155 Gurmeet Kanwal, China’s emerging cyberwar doctrine, Journal of Defense Studies, pp. 14–22, vol.3, no. °3, July 2009, [http://www.idsa.in/system/files/jds_3_3_gkanwal_0.pdf].
156 R. A. Clarke, R. Knake, Cyber War: The Next Threat to National Security and What to Do About It, Ecco Publisher, United States, April 2010, 320 pages.
157 Elisabette M. Marvel, China’s Cyberwarfare Capability, 105 pages, Nova Science Pub Inc, 31 October 2010.
158 Martin Libicki, Chinese use if cyberwar as an anti-access strategy, Testimony presented to the U.S. China Economic and Security Review Commission, 27 January 2011, Publication Rand Corporation, 6 pages, [http://www.rand.org/content/dam/rand/pubs/testimonies/2011/RAND_CT355.pdf].
159 Dmitri Alperovitch, Revealed: Operation Shady RAT, McAfee, 2011, [http://www.mcafee.com/us/resources/white-papers/wp-operation-shady-rat.pdf].
160 Venusto Abellera, Exploring China's Use of Known Cyber Capabilities in the Intrusions of United States Public Sector Networks, ProQuest, UMI Dissertation Publishing, 124 pages, September 2011.
161 C. Paschal Eze, Cyber Coexistence Code: Whither U.S.-China Cyber Cold War?, Global Mark Makers, 29 pages, October 2011.
162 Mark A. Stokes, Jenny Lin and L.C. Russell Hsiao, The Chinese People’s Liberation Army Signals Intelligence and Cyber Reconnaissance Infrastructure, Project 2049, 11 November 2011, 32 pages, [http://project2049.net/documents/pla_third_department_sigint_cyber_stokes_lin_hsiao.pdf].
163 Li Yan, The Global Commons and the Reconstruction of Sino–U.S. Military Relations, Asia paper, March 2012, 35 pages, [http://www.isdpp.eu/images/stories/isdp-main-pdf/2012_li-yan_the-global-commons.pdf].
164 William T. Hagestad, 21st Century Chinese Cyber Warfare, IT Governance Publishing, Cambridge, United Kingdom, 314 pages, 1° March 2012.
165 Larry M. Wortzel, China’s Military Modernization and Cyber Activities, Strategic Studies Quarterly, Pennyhill Press, March 2014, 22 pages, [http://www.au.af.mil/au/ssq/digital/pdf/spring_2014/wortzel.pdf].
166 Department of Defense, United States, Annual Report to Congress. Military Power of the People’s Republic of China, 2000 and subsequent.
167 Law from 2000.Last report dates from November 2012.
168 [https://www.cia.gov/news-information/speeches-testimony/1995/index.html].
169 [http://www.nsa.gov/public_info/speeches_testimonies/].
170 [http://www.dhs.gov/news-releases/speeches].
171 Frank Wolf, Change needed in addressing cyber threat, Congressman, 10th District of Virginia, October 22, 2013, [http://wolf.house.gov/media-center/press-releases/wolf-change-needed-in-addressing-cyber-threat#.U234Ovl_vX4].
172 USCC Research Staff, The National Security Implications of Investments and Products from the People's Republic of China in the Telecommunications Sector, 104 pages, January 2011, Create Space Independent Publishing Platform.
173 [http://search.house.gov/htbin/search].
174 United States House of Representatives, Communist Chinese Cyber-Attacks, Cyber-Espionage and Theft of American Technology, United States, 30 June 2011, 91 pages, Kindle Edition available at: [http://www.amazon.com/Communist-Cyber-Attacks-Cyber-Espionage-Technology-ebook/dp/B005966LG2/ref=sr_1_7?s=books&ie=UTF8&qid=1364229259&sr=1-7&keywords=cyber+china].
175 Office of the National Counterintelligence Executive, Foreign Spies Stealing US Economic Secrets in Cyberspace, October 2011, 31 pages, United States, [http://www.ncix.gov/publications/reports/fecie_all/Foreign_Economic_Collection_2011.pdf].
176 The report is believed to confirm that China is the main cyber threat facing America. The existence of the document is mentioned in various press articles – e.g. Stacy Curtin, China is America’s #1 Cyber Threat: U.S. Govt. Report, 11 February 2013, [http://finance.yahoo.com/blogs/daily-ticker/china-america-1-cyber-threat-u-govt-report-150621517.html].
177 Committee on Homeland Security House of Representatives, Cyber Threats from China, Russia, and Iran: Protecting American Critical Infrastructure, 50 pages, January 2014.
178 Magnus Hjortdal, China's Use of Cyber Warfare: Espionage Meets Strategic Deterrence, Journal of Strategic Security, Volume IV Issue 2 2011, pp. 1–24, [http://cryptocomb.org/Espionage%20Meets%20Strategic%20Deterrence.pdf].
179 Michael Riley, John Walcott, China-Based Hacking of 760 Companies Shows Cyber Cold War, Bloomberg, Dec. 14, 2011, [http://www.bloomberg.com/news/2011-12-13/china-based-hacking-of-760-companies-reflects-undeclared-global-cyber-war.html].
180 Cited in Michael Riley, John Walcott, China-Based Hacking of 760 Companies Shows Cyber Cold War, Bloomberg, Dec. 14, 2011, [http://www.bloomberg.com/news/2011-12-13/china-based-hacking-of-760-companies-reflects-undeclared-global-cyber-war.html].
181 James Lewis, Cyber Espionage and the Theft of U.S. Intellectual Property and Technology, Testimony, Committee on Energy and Commerce, U.S. House of Representatives, July 9, 2013, page 4.
182 Occupying the information High Ground: Chinese capabilities for Computer Network Operations and Cyber Espionage, Report prepared for the U.S.- China Economic and Security Review Commission by Northrop Grumman Corp. , March 7, 2012, 136 pages.
183 James Lewis, Cyber Espionage and the Theft of U.S. Intellectual Property and Technology, Testimony, Committee on Energy and Commerce, U.S. House of Representatives, July 9, 2013, page 7.
184 James Lewis, Cyber Espionage and the Theft of U.S. Intellectual Property and Technology, Testimony, Committee on Energy and Commerce, U.S. House of Representatives, July 9, 2013, page 7.
185 Mandiant, APT1: Exposing One of China’s Cyber Espionage Units, 76 pages, February 2013, [http://intelreport.mandiant.com/Mandiant_APT1_Report.pdf].
186 – Richard Halloran, The Opacity of China's Military, The Washington Times (Washington, DC), 10 March 2009.
– Kristopher Harrison, Why China’s economic opacity is a serious problem, Foreign Policy, 10 July 2012, [http://shadow.foreignpolicy.com/posts/2012/07/10/why_chinas_economic_opacity_is_a_serious_problem].
– Kerry B. Collison, Opacity the heart of China’s PLA strategy, 10 June 2010, [http://kerrycollison.blogspot.fr/2010/06/opacity-heart-of-chinas-pla-strategy.html].
– Office of the Secretary of Defense, Annual Report to Congress, Military Power of the People's Republic of China, 2008, United States, 66 pages, p. I, [http://www.defense.gov/pubs/pdfs/China_Military_Report_08.pdf].
187 Evan Feigenbaum, China's Techno-Warriors: National Security and Strategic Competition from the Nuclear to the Information Age, Stanford University Press, Stanford, United States, April 2003, 360 pages.
188 R. A. Clarke, R. Knake, Cyber War: The Next Threat to National Security and What to Do About It, Ecco Publisher, United States, April 2010, 320 pages.
189 Joel Brenner, America the Vulnerable: Inside the New Threat Matrix of Digital Espionage, Crime, and Warfare, The Penguin Press HC, United States, September 2011, 320 pages, J. Brenner was a legal counsellor on cybersecurity for the NSA (United States).
190 Defense Science Board, Resilient Military Systems and the advanced cyber threat, Department of Defense, Office of the Under Secretary of Defense for Acquisition, Technology and Logistics, Washington DC, 20301-3140, United States, January 2013, 146 pages, [http://www.acq.osd.mil/dsb/reports/ResilientMilitarySystems.CyberThreat.pdf].
191 Mike Rogers, America is losing the cyber war vs. China, 8 February 2013, [http://www.detroitnews.com/article/20130208/OPINION01/302080328/1007/OPINION/Rogers-America-losing-cyber-war-vs-China].
192 Lieutenant Colonel Timothy L. Thomas was an an analyst in the FMSO (Foreign Military Studies Office), at Fort Leavenworth (Kansas, United States), Director of USARI, Soviet Studies – United States Army Russian Institute, at Garmischin Germany.
193 Scott J. Henderson, a former officer (analyst) for the US Army, wrote the book The Dark Visitor and maintains the well-known Website of the same name, focusing on the activities of Chinese hackers.
194 Rich Barger, who is in charge of intelligence issues at Cyber Squared, served in the US Army (1st Information Operations Command). On the Cyber Squared Website, mention is made of the existence of many APT groups who are being analyzed by the company. [http://www.cybersquared.com/just-the-tip-of-the-iceberg/].
195 A member of Project 2049, and co-author of the report The Chinese People’s Liberation Army Signals Intelligence and Cyber Reconnaissance Infrastructure, M. A. Stokes served for 20 years in the US Air Force.
196 US Marine Lieutenant Colonel.
197 In China, the military is also the source of the majority of publications, which have profoundly marked western perceptions of China’s ambitions and intentions over the course of the 2000s: the infamous Unrestricted Warfare preached by Colonels Liang Qiao and Wang Xiangsui. This publication has probably had more of an impact on western thinking than the equally important works relating to information warfare produced by other Chinese military figures (e.g. Wang Baocun, Dai Qingmin or Wang Pufeng) since the 1990s, but which have proved more confidential because of their more conceptual/theoretical nature and the language barrier. Liang Qiao, Wang Xiangsui, Unrestricted Warfare, Beijing: PLA Literature and Arts Publishing House, February 1999, 228 pages, [http://www.cryptome.org/cuw.htm].
198 [http://taosecurity.blogspot.fr/].
199 Elisabeth Bumiller, Pentagon Expanding Cybersecurity Force to Protect Networks Against Attacks, The New York Times, 27 January 2013, [http://www.nytimes.com/2013/01/28/us/pentagon-to-beef-up-cybersecurity-force-to-counter-attacks.html?_r=0].
200 Leon A. Panetta, Defending the Nation from Cyber-Attack, Speech by the Secretary of Defense, New York, United States, 12 October 2012, [http://www.defense.gov/speeches/speech.aspx?speechid=1728].
201 White House, Executive order on cybersecurity, United States, 12 February 2013, [http://www.whitehouse.gov/the-press-office/2013/02/12/executive-order-improving-critical-infrastructure-cybersecurity].
202 Steve Holland, Obama, China's Xi discuss cybersecurity dispute in phone call, 14 March 2013, Reuters, [http://www.reuters.com/article/2013/03/14/us-usa-china-obama-call-idUSBRE92D11G20130314].
203 Michael N. Schmitt (US Naval War College), Tallinn Manual on the International Law Applicable to Cyber Warfare, Cambridge University Press, April 2013, 300 pages.
204 Brad Stone, Michael Riley, Mandiant, the Go-To Security Firm for Cyber-Espionage Attack, Bloomberg Business Week, 7 February 2013, [http://www.businessweek.com/articles/2013-02-07/mandiant-the-go-to-security-firm-for-cyber-espionage-attacks#p2].
205 Matthew Yglesias, Meet the Company That’s Profiting From Chinese Hacking, 19 February 2013, Slate.com, [http://www.slate.com/blogs/moneybox/2013/02/19/mandiant_is_the_big_winner_from_increased_anxiety_about_chinese_hacking.html].
206 China opposes hacking allegations: FM spokesman, XinhuaNet, 19 February 2013, [http://news.xinhuanet.com/english/china/2013-02/19/c_132178666.htm].
207 – Jeffrey Carr, Mandiant APT1 Report Has Critical Analytic Flaws, 19 February 2013, [http://jeffreycarr.blogspot.fr/2013/02/mandiant-apt1-report-has-critical.html#!/2013/02/mandiant-apt1-report-has-critical.html].
– Jeffrey Carr, More on Mandiant's APT1 Report: Guilt by Proximity and Wright Patterson AFB,http://jeffreycarr.blogspot.fr/2013/02/mandiant-apt1-report-has-critical.html#!/2013/02/more-on-mandiants-apt1-report-guilt-by.html].
208 Ellyne Phneah, Embarassing China with reports won’t aid security, ZDnet, 27 February 2013, [http://www.zdnet.com/cn/embarrassing-china-with-reports-wont-aid-security-7000011886/?s_cid=e305].
209 The existence of Unit 61398 is not revealed by the Mandiant report. An article in the Chinese press (China Digital Times) made open reference to its existence in May 2004. The China Digital Times on 13 May 2004 stated that Unit 31398 of the Chinese army, located in the Pudong District in Shanghai, was recruiting computer specialists, and offering university study grants. Laura Saporito and James A. Lewis, Cyber Incidents attributed to China, CSIS, Washington, United States, 14 pages, 5 March 2013, [http://csis.org/files/publication/130311_Chinese_hacking.pdf]. The Project2049 Institute also published specific information about that unit in its November 2011 report. Mark A. Stokes, Jenny Lin and L.C. Russell Hsiao, The Chinese People’s Liberation Army Signals Intelligence and Cyber Reconnaissance Infrastructure, 11 November 2011, 32 pages, [http://project2049.net/documents/pla_third_department_sigint_cyber_stokes_lin_hsiao.pdf].
210 Theories of the Copenhagen School, security studies.
211 Eric C. Anderson, Sino phobia: the Huawei Story, January 2013, Create Space Independent Publishing Platform, 400 pages, January 2013.
212 Kim Zetter, Tone Down the Cyberwarfare Rhetoric, Expert Urges Congress, Wired, 20 March 2013, [http://www.wired.com/threatlevel/2013/03/tone-down-cyberwar-rhetoric/?utm_source=dlvr.it&utm_medium=twitter].
213 – Michael D. Swaine, Chinese Views on Cybersecurity in Foreign Relations, China Leadership Monitor, no. 42, 27 pages, June 23 2013, [http://media.hoover.org/sites/default/files/documents/CLM42MS.pdf].
– David Hanel, Chinese Cybercrime – A Threat to the Occident? The Impact of Chinese Cybercrime on EU-China Relations, University of Twente, 23th June 2013, 45 pages, [http://essay.utwente.nl/63300/1/Bachelor_Paper_Final_Version_d.hanel_s1062336.pdf].
214 John Oakley, Cyber Warfare: China's strategy to dominate in cyber space, University of Minnesota, 2011, 99 pages, [http://www.dtic.mil/dtic/tr/fulltext/u2/a547718.pdf].
215 Sérgio Tenreiro de Magalhães, Maria J. Rios,Leonel Santos, Hamid Jahankhani, The People’s Republic of China – The Emerging Cyberpower, Communications in Computer and Information Science,Volume 45, 2009, ppp. 138–144.
216 Ronald Deibert, China’s Cyberspace Control Strategy: an overview and consideration of issues for Canadian policy, Canadian International Council, February 2010, 18 pages, [http://cic.verto.ca/wp-content/uploads/2011/05/Chinas-Cyberspace-Control-Strategy-Ronald-Deibert.pdf].
217 Jayson M. Spade, China’s cyber power and America’s National Security, US Army War College, 81 pages, 2012, [http://www2.gwu.edu/~nsarchiv/NSAEBB/NSAEBB424/docs/Cyber-072.pdf].
218 Yao-chung Chang, Cyber Conflict Between Taiwan and China, Strategic Insights, Spring 2011, pp. 26–35, [http://edocs.nps.edu/npspubs/institutional/newsletters/strategic%20insight/2011/SI-v10-I1_Chang.pdf].
219 Deepak Sharma, China’s Cyber Warfare Capability and India’s Concerns, Journal of Defence Studies, Vol. 5, No 2. April 2011, pp. 62–76, [http://www.idsa.in/system/files/jds_5_2_dsharma.pdf].
220 Randolph Kluver, US and Chinese expectations of the Internet, China Information, XIX; 2, pp. 299-324, 2005, [http://www.asc.upenn.edu/usr/ogandy/c734%20resources/kluver-uschinapolicyexpectationsinternet.pdf].
221 Ronald Deibert, China’s Cyberspace control strategy: an overview and consideration of issues for Canadian policy, Canadian International Council, China Papers n°7, 18 pages, February 2010, [http://cic.verto.ca/wp-content/uploads/2011/05/Chinas-Cyberspace-Control-Strategy-Ronald-Deibert.pdf].
222 Milton L. Mueller, China and Global Internet Governance, A Tiger by the Tail, Chapter 9, pp. 177–194, in R. Deibert, J. Palfrey, R. Rohozinski & J. Zittrain (eds.) Access Contested: Security, Identity and Resistance in Asian Cyberspace. Cambridge, MA: MIT Press, 2011, [http://access.opennet.net/wp-content/uploads/2011/12/accesscontested-chapter-09.pdf].
223 Jayson M. Spade, China’s cyber power and America’s national security, US Army War College, 2011, 81 pages, [http://www.carlisle.army.mil/dime/documents/China's%20Cyber%20Power%20and%20America's%20National%20Security%20Web%20Version.pdf].
224 Viktor Nagy, The geostrategic struggle in cyberspace between the United States, China, and Russia, AARMS, Vol. 11, No. 1 (2012) 13–26, [http://www.konyvtar.zmne.hu/docs/Volume11/Issue1/pdf/02.pdf].
225 Alistair D. B. Cook, The cybersecurity challenge and China-US relations, EAI Background Brief, No. 828, 20 June 2013, 3 pages, [http://www.eai.nus.edu.sg/BB828.pdf].
226 Wilson Vorn Dick, The Real U.S.-Chinese Cyber Problem, The National Interest, July 30, 2013, [http://nationalinterest.org/commentary/the-real-us-chinese-cyber-problem-8796].
227 – Bilateral Discussions on Cooperation in Cybersecurity China, Institute of Contemporary International Relations (CICIR) – Center for Strategic and International Studies (CSIS), June 2012, 4 pages, [http://csis.org/files/attachments/120615_JointStatement_CICIR.pdf].
– C. Raja Mohan, US-China Cyber Talks: Internet Security in the Global Economy, RSIS, Singapore, RSIS Commentaries, n°046/2013, 18 March 2013, 2 pages, [http://www.rsis.edu.sg/publications/Perspective/RSIS0462 013.pdf].
228 The author refers to the American official document: Army’s Escalation of Force Handbook.
229 David C. Gompert, Phillip C. Saunders, The Paradox of Power: Sino--American Strategic Restraint in an Age of Vulnerability, Center for Study of Chinese Military Affairs, and National Defense University Press; Washington, 2011, 236 pages, [http://ndupress.ndu.edu/Portals/68/Documents/Books/paradox-of-power.pdf].
230 Ting Xu, China and the United States: hacking away at cyber warfare, East-West Center, Asia Pacific Bulletin, n°135, November 1, 2011, 2 pages, [https://www.eastwestcenter.org/sites/default/files/private/apb135_1.pdf].
231 Ammilee A. Oliva, China: Paper Tiger in Cyberspace, 17 May 2012, 46 pages, [http://www.stormingmedia.us/54/5456/A545665.html].
232 Jean-Louis Rocca, Pourquoi nous ne comprenons pas la société chinoise, p. 5, in Emilie Frenkiel, Jean-Louis Rocca (eds.), La Chine en mouvements, Presses Universitaires de France, 2013, 100 pages.
233 Tzvetan Todorov, Les ennemis intimes de la démocratie, Le Livre de Poche, Robert Laffont, Paris, 2012, 284 pages.
234 “Russia and China have different conceptual models for cyber agreements”. Christopher Ford, The Trouble with Cyber Arms Control, Hudson Institute, September 2011, [http://www.hudson.org/files/publications/20110301_TNA29Ford.pdf].
235 Jean-Louis Rocca, Pourquoi nous ne comprenons pas la société chinoise, p. 5, in Emilie Frenkiel, Jean-Louis Rocca (eds.), La Chine en mouvements, Presses Universitaires de France, 2013, pp. 5–6.
236 Jean-Louis Rocca, Pourquoi nous ne comprenons pas la société chinoise, p. 5, in Emilie Frenkiel, Jean-Louis Rocca (eds.), La Chine en mouvements, Presses Universitaires de France, 2013, 100 pages.
237 Jean-Louis Rocca, Pourquoi nous ne comprenons pas la société chinoise, p. 5, in Emilie Frenkiel, Jean-Louis Rocca (eds.), La Chine en mouvements, Presses Universitaires de France, 2013, pp. 14–15.
238 Department of Defense, Annual Report on the Military Power of the People’s Republic of China, Washington, 56 pages, 2002, [http://www.defense.gov/news/jul2002/d20020712china.pdf].
239 Department of Defense, Annual Report on the Military Power of the People’s Republic of China, Washington, 28 July 2003, 52 pages, [http://www.defense.gov/pubs/2003chinaex.pdf].
240 Department of Defense, Annual Report on the Military Power of the People’s Republic of China, Washington, 2004, 54 pages, [http://www.defense.gov/pubs/d20040528prc.pdf].
241 Department of Defense, The Military Power of the People’s Republic of China 2005, Washington, 2005, 52 pages, [http://www.defense.gov/news/jul2005/d20050719china.pdf].
242 Computer network operations.
243 Computer network attacks.
244 Computer network exploitation.
245 Computer network defense.
246 Department of Defense, Military and Security Developments Involving the People’s Republic of China 2006, Washington, 58 pages, [http://www.dod.mil/pubs/pdfs/China%20Report%202006.pdf].
247 Department of Defense, Military and Security Developments Involving the People’s Republic of China 2007, Washington, 50 pages, [http://www.defense.gov/pubs/pdfs/070523-China-Military-Power-final.pdf]
248 Department of Defense, Military and Security Developments Involving the People’s Republic of China 2008, Washington, 66 pages, [http://www.defense.gov/pubs/pdfs/China_Military_Report_08.pdf].
249 Department of Defense, Military and Security Developments Involving the People’s Republic of China 2009, Washington, 78 pages, [http://www.defense.gov/pubs/pdfs/China_Military_Power_Report_2009.pdf]
250 Department of Defense, Military and Security Developments Involving the People’s Republic of China 2010, Washington, 83 pages, [http://www.defense.gov/pubs/pdfs/2010_CMPR_Final.pdf].
251 Department of Defense, Military and Security Developments Involving the People’s Republic of China 2006, Washington, 58 pages, [http://www.dod.mil/pubs/pdfs/China%20Report%202006.pdf].
252 Department of Defense, Military and Security Developments Involving the People’s Republic of China 2007, Washington, 50 pages, [http://www.defense.gov/pubs/pdfs/070523-China-Military-Power-final.pdf]
253 Department of Defense, Military and Security Developments Involving the People’s Republic of China 2006, Washington, 58 pages, [http://www.dod.mil/pubs/pdfs/China%20Report%202006.pdf].
254 Department of Defense, Military and Security Developments Involving the People’s Republic of China 2006, Washington, 58 pages, [http://www.dod.mil/pubs/pdfs/China%20Report%202006.pdf].
255 Department of Defense, Military and Security Developments Involving the People’s Republic of China 2007, Washington, 50 pages, [http://www.defense.gov/pubs/pdfs/070523-China-Military-Power-final.pdf].
256 Department of Defense, Military and Security Developments Involving the People’s Republic of China 2007, Washington, 50 pages, [http://www.defense.gov/pubs/pdfs/070523-China-Military-Power-final.pdf].
257 Department of Defense, Military and Security Developments Involving the People’s Republic of China 2007, Washington, 50 pages, [http://www.defense.gov/pubs/pdfs/070523-China-Military-Power-final.pdf].
258 Department of Defense, Military and Security Developments Involving the People’s Republic of China 2008, Washington, 66 pages, [http://www.defense.gov/pubs/pdfs/China_Military_Report_08.pdf].
259 Department of Defense, Military and Security Developments Involving the People’s Republic of China 2008, Washington, 66 pages, [http://www.defense.gov/pubs/pdfs/China_Military_Report_08.pdf].
260 Department of Defense, Military and Security Developments Involving the People’s Republic of China 2008, Washington, 66 pages, [http://www.defense.gov/pubs/pdfs/China_Military_Report_08.pdf].
261 Department of Defense, Military and Security Developments Involving the People’s Republic of China 2008, Washington, 66 pages, [http://www.defense.gov/pubs/pdfs/China_Military_Report_08.pdf].
262 Department of Defense, Military and Security Developments Involving the People’s Republic of China 2009, Washington, 78 pages, [http://www.defense.gov/pubs/pdfs/China_Military_Power_Report_2009.pdf].
263 Department of Defense, Military and Security Developments Involving the People’s Republic of China 2010, Washington, 83 pages, [http://www.defense.gov/pubs/pdfs/2010_CMPR_Final.pdf].
264 Department of Defense, Military and Security Developments Involving the People’s Republic of China 2011, Washington, 94 pages, [http://www.defense.gov/pubs/pdfs/2011_cmpr_final.pdf].
265 Department of Defense, Military and Security Developments Involving the People’s Republic of China 2011, Washington, 94 pages, [http://www.defense.gov/pubs/pdfs/2011_cmpr_final.pdf].
266 Department of Defense, Annual Report to Congress. Military and Security Developments Involving the People’s Republic of China 2012, Washington, 52 pages, [http://www.defense.gov/pubs/pdfs/2012_CMPR_Final.pdf].
267 Annual Report to Congress, Military and Security Developments Involving the People’s Republic of China 2013, Office of the Secretary of Defense, Washington, 92 pages, 2013, [http://www.defense.gov/pubs/2013_China_Report_FINAL.pdf].
268 Annual Report to Congress, Military and Security Developments Involving the People’s Republic of China 2013, Office of the Secretary of Defense, Washington, 92 pages, 2013, [http://www.defense.gov/pubs/2013_China_Report_FINAL.pdf].
269 Annual Report to Congress, Military and Security Developments Involving the People’s Republic of China 2013, Office of the Secretary of Defense, Washington, 92 pages, 2013, [http://www.defense.gov/pubs/2013_China_Report_FINAL.pdf].
270 AUSA Air, Space, and Missile Defense Symposium, Remarks as Delivered by Secretary of Defense Donald H. Rumsfeld, via video teleconference, Wednesday, December 10, 2003, [http://www.defense.gov/Speeches/Speech.aspx?SpeechID=595].
271 International Institute for Strategic Studies, Remarks as Delivered by Secretary of Defense Donald H. Rumsfeld, Shangri-La Hotel, Singapore, Saturday, June 04, 2005, [http://www.defense.gov/Speeches/Speech.aspx? SpeechID=77].
272 Testimony before the House Appropriations Committee: Fiscal Year 2002 Defense Budget Request, As Delivered by Secretary of Defense Donald H. Rumsfeld, Chairman of the Joint Chiefs of Staff General Hugh Shelton, Rayburn House Office Building, Washington, DC, Monday, July 16, 2001, [http://www.defense.gov/Speeches/Speech.aspx?SpeechID=408].
273 International Institute for Strategic Studies Conference, As Delivered by Secretary of Defense Donald H. Rumsfeld, Shangri-La Hotel, Singapore, Saturday June 3 2006, Saturday June 03 2006, [http://www.defense.gov/Speeches/Speech.aspx?SpeechID=11].
274 Keio University, As Delivered by Secretary of Defense Robert M. Gates, Keio University, Tokyo, Japan, Friday, January 14, 2011, [http://www.defense.gov/Speeches/Speech.aspx?SpeechID=1529].
275 National Defense University (Washington, D.C.), As Delivered by Secretary of Defense Robert M. Gates, Washington, D.C., Monday, September 29, 2008, [http://www.defense.gov/Speeches/Speech.aspx?SpeechID=1279].
276 Submitted Statement on DoD Challenges to the Senate Armed Services Committee,As Submitted by Secretary of Defense Robert M. Gates, Room SD-106, Dirksen Senate Office Building, Washington, D.C., Tuesday, January 27, 2009, [http://www.defense.gov/Speeches/Speech.aspx?SpeechID=1337].
277 Air Force Association Convention, As Delivered by Secretary of Defense Robert M. Gates, National Harbor, MD, Wednesday, September 16, 2009, [http://www.defense.gov/Speeches/Speech.aspx?SpeechID=1379].
278 Keio University, As Delivered by Secretary of Defense Robert M. Gates, Keio University, Tokyo, Japan, Friday, January 14, 2011, [http://www.defense.gov/Speeches/Speech.aspx?SpeechID=1529].
279 U.S. Naval Academy Commencement, As Delivered by Secretary of Defense Leon E. Panetta, Annapolis, MD, Tuesday May 29, 2012, [http://www.defense.gov/Speeches/Speech.aspx?SpeechID=1679].
280 PLA Engineering Academy of Armored Forces, As Delivered by Secretary of Defense Leon E. Panetta, Beijing, China, Wednesday, September 19, 2012, [http://www.defense.gov/Speeches/Speech.aspx?SpeechID=1723].
281 “Defending the Nation from Cyber-Attack” (Business Executives for National Security), As Delivered by Secretary of Defense Leon E. Panetta, New York, New York, Thursday, October 11, 2012, [http://www.defense.gov/Speeches/Speech.aspx?SpeechID=1728].
282 “Defending the Nation from Cyber-Attack” (Business Executives for National Security), As Delivered by Secretary of Defense Leon E. Panetta, New York, New York, Thursday, October 11, 2012, [http://www.defense.gov/Speeches/Speech.aspx?SpeechID=1728].
283 Munich Security Conference, As Delivered by Secretary of Defense Chuck Hagel, Munich, Germany, Saturday, February 01, 2014, [http://www.defense.gov/Speeches/Speech.aspx?SpeechID=1828].
284 Malaysian Institute of Defense and Security, As Delivered by Secretary of Defense Chuck Hagel, Malaysian Ministry of Defense, Kuala Lumpur, Malaysia, Sunday August 25 2013, [http://www.defense.gov/Speeches/Speech.aspx?SpeechID=1799].
285 Malaysian Institute of Defense and Security, As Delivered by Secretary of Defense Chuck Hagel, Malaysian Ministry of Defense, Kuala Lumpur, Malaysia, Sunday August 25 2013, [http://www.defense.gov/Speeches/Speech.aspx?SpeechID=1799].
286 International Institute for Strategic Studies (Shangri-La Dialogue), As Delivered by Secretary of Defense Chuck Hagel, Singapore, Saturday June 01 2013, [http://www.defense.gov/Speeches/Speech.aspx?SpeechID=1785].
287 PLA National Defense University,As Delivered by Secretary of Defense Chuck Hagel, Beijing, China, Tuesday April 08 2014, [http://www.defense.gov/Speeches/Speech.aspx?SpeechID=1838].
288 PLA National Defense University, As Delivered by Secretary of Defense Chuck Hagel, Beijing, China, Tuesday April 08 2014, [http://www.defense.gov/Speeches/Speech.aspx?SpeechID=1838].
289 National Intelligence Council, Global Trends 2010, Washington, November 1997, [http://www.dni.gov/index.php/about/organization/national-intelligence-council-global-trends/global-trends-2010].
290 National Intelligence Council, Global Trends 2015, A Dialogue about the Future with nongovernment experts, Washington, December 2000, 98 pages, [http://www.dni.gov/files/documents/Global%20Trends_2015%20Report.pdf].
291 National Intelligence Council, Global Trends 2020, Mapping the Global Future, December 2004, Washington, 123 pages, [http://www.dni.gov/files/documents/Global%20Trends_Mapping%20the%20Global%20Future%202020%20Project.pdf].
292 See page 97 of the report.
293 National Intelligence Council, Global Trends 2025, A transformed world, November 2008, Washington, 120 pages, [http://www.aicpa.org/research/cpahorizons2025/globalforces/downloadabledocuments/globaltrends.pdf].
294 National Intelligence Council, Global Trends 2030, Alternative Worlds, 166 pages, 2012, Washington, [http://globaltrends2030.files.wordpress.com/2012/11/global-trends-2030-november2012.pdf].
295 See page 67 of the report.
296 RMA: Revolution in Military Affairs.
