General Conclusion
The scenario of a Chinese cyber-threat feeds into the discourse held in the circles of security and defense in many countries. It intersects with the scenario of the threat against critical infrastructures. For example, Congressman Mike Rogers, Chairman of the House Permanent Select Committee on Intelligence and a former FBI agent, is the proponent of a law bill entitled “The Cyber Intelligence Sharing and Protection Act”1, the aim of which is to “facilitate information sharing, interaction, and collaboration among and between federal, state, local, tribal, and territorial governments, cybersecurity providers, and self-protected entities.”2 He supports this project because of the need to protect America from the threat of cyber-attacks from China, Russia and Iran against the country’s infrastructures. Others maintain that China is conducting massive-scale cyber-espionage operations. According to the US Office of the National Counter Intelligence Executive (ONCIX): “America’s annual costs due to cyber espionage could be as high as $400 billion a year [...] Chinese actors are the world’s most active and persistent perpetrators of economic espionage.”3
The topics and arguments interweave with one another to form the scenario presented in the graph below.
Figure C.1. The scenarios (and their components) of the Chinese cyber-threat

Yet to what extent are the argument of the “Chinese cyber-threat”, or even simply China’s cyberspace policy and strategy, taken into account in the definition of the cybersecurity and cyberdefense strategies for other nations, be they large or small, near to or far from China?
An initial indication can be found in the formulations of the national cyber strategies published in recent years.
Table C.1. National strategies for cybersecurity
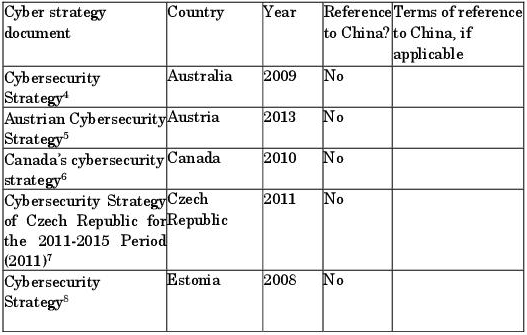
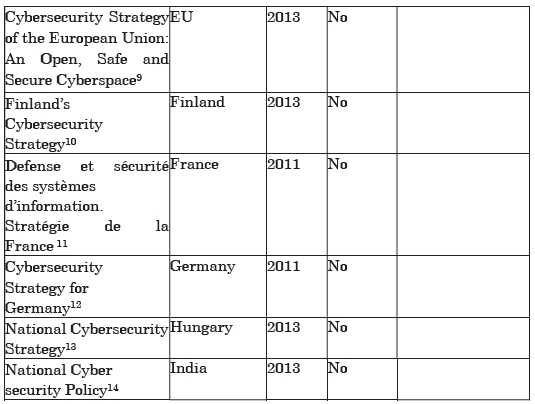






Only 3 documents in this corpus actually make reference to China: one to point out the IPv6 is being adopted by China; the second to mention the establishment of, or willingness for, dialog with China over cybersecurity issues; and the third to speak of China’s increasingly close military ties with third parties, although the cyber issue is not mentioned. Perhaps the writers of the various national strategies are conscious of the threats posed by China, but these national strategies are primarily formulated with the aim of overall protection, against all types of attacks. The “problem” of China, which is so apparent in the discourse in the media, from political and industrial actors, is not mentioned in the official documents. Other variables have recently come into play to constrain these strategic stances. The crisis of trust which has taken hold in the international community, in the wake of Edward Snowden’s revelations about American cyber-espionage practices (America’s allies were not at all appreciative of being targeted by such measures), is liable to impact numerous political and strategic choices for cyberspace – at least as much as considerations about China’s policies and practices.
1 H.R.624 – Cyber Intelligence Sharing and Protection Act, [http://beta.congress.gov/bill/113th-congress/house-bill/624].
2 Summary: H.R.624 – 113th Congress (2013-2014), [http://beta.congress.gov/bill/113th-congress/house-bill/624].
3 Cited in: Lu Jinghua, China’s Cyber Threat: Real or Imaginary?, June 7, 2013, [http://www.chinausfocus.com/peace-security/chinas-cyber-threat-real-or-imaginary/].
4 Cybersecurity Strategy, Australian Government, 2009, 38 pages, [http://www.ag.gov.au/RightsAndProtections/CyberSecurity/Documents/AG%20Cyber%20Security%20Strategy%20-%20for%20website.pdf].
5 Austrian Cybersecurity Strategy, Federal Chancellery of the Republic of Austria, 2013, 25 pages, [https://www.bka.gv.at/DocView.axd?CobId=50999].
6 Canada’s Cybersecurity Strategy, Government of Canada, 17 pages, 2010, [http://www.publicsafety.gc.ca/cnt/rsrcs/pblctns/cbr-scrt-strtgy/cbr-scrt-strtgy-eng.pdf].
7 Cybersecurity Strategy of Czech Republic for the 2011-2015 Period, 2011, 10 pages, [http://www.enisa.europa.eu/media/news-items/CZ_Cyber_Security_Strategy_20112015.PDF].
8 Cybersecurity Strategy, Ministry of Defence, Tallinn, 2008, 36 pages, [http://www.eata.ee/wp-content/uploads/2009/11/Estonian_Cyber_Security_Strategy.pdf].
9 Cybersecurity Strategy of the European Union: An Open, Safe and Secure Cyberspace, European Commission, 7 February 2013, 20 pages, [http://ec.europa.eu/information_society/newsroom/cf/dae/document.cfm?doc_id=1667].
10 Finland’s Cybersecurity Strategy, Government Resolution 24.1.2013, 2013, 44 pages, [http://www.defmin.fi/files/2378/Finland_s_Cyber_Security_Strategy.pdf].
11 ANSSI, Défense et sécurité des systèmes d’information. Stratégie de la France, February 2011, 24 pages, [http://www.ssi.gouv.fr/IMG/pdf/2011-02-5_Defense_et_securite_des_systemes_d_information_strategie_de_la_France.pdf].
12 Strategy for Germany, Federal Ministry of the Interior, February 2011, 20 pages, [http://www.cio.bund.de/SharedDocs/Publikationen/DE/Strategische-hemen/css_engl_download.pdf?__blob=publicationFile].
13 National Cybersecurity Strategy, Hungary, 7 pages, March 2013, [http://www.nbf.hu/anyagok/Government%20Decision%20No%201139_2013%20on%20the%20National%20Cyber%20Security%20Strategy%20of%20Hungary.docx].
14 National Cybersecurity Policy, India, July 2013, 10 pages, [http://deity.gov.in/sites/upload_files/dit/files/National%20Cyber%20Security%20Policy%20(1).pdf].
15 National Strategic Framework for Cyberspace Security, Presidency of the Council of Ministers, Italy, December 2013, 48 pages, [http://www.sicurezzanazionale.gov.it/sisr.nsf/wp-content/uploads/2014/02/italian-national-strategic-framework-for-cyberspace-security.pdf].
16 International Strategy on Cybersecurity - j-Initiative for Cybersecurity, Information Security Policy Council, 2 October 2013, 17 pages, [http://www.nisc.go.jp/active/kihon/pdf/InternationalStrategyonCybersecurityCooperation_e.pdf].
17 Cybersecurity Strategy, Information Security Policy Council, 10 June 2013, 55 pages, [http://www.nisc.go.jp/active/kihon/pdf/cybersecuritystrategy-en.pdf].
18 Information Security Strategy for protecting the nation, Information Security Policy Council, Japan, May 2010, 20 pages, [http://www.nisc.go.jp/eng/pdf/New_Strategy_English.pdf].
19 National Cybersecurity Strategy and Master Plan, Ministry of Information and Communication, February 2013, [http://www.information.go.ke/Downloads/ICT_MASTER_PLAN_2017.pdf].
20 Programme for the development of electronic information security (cybersecurity) for 2011-2019, Government of the Republic of Lithuania, June 2011, 17 pages, [http://www.ird.lt/doc/teises_aktai_en/EIS(KS)PP_796_2011-06-29_EN_PATAIS.pdf].
21 Stratégie nationale en matière de cyber sécurité, Ministère d’Etat, Le Gouvernement du Grand-Duché de Luxembourg, 10 pages, 2011, [http://www.mediacom.public.lu/cybersecurity/Strat__gieCybersecurity_122011.pdf].
22 The NATO Policy on Cyberdefence, Brussels, 2011, 2 pages, [http://www.nato.int/nato_static/assets/pdf/pdf_2011_09/20111004_110914-policy-cyberdefence-fr.pdf].
23 The National Cybersecurity Strategy 2, National Coordinator for Security and Counterterrorism, 36 pages, 2013, [http://english.nctv.nl/images/national-cyber-security-strategy-2_tcm92-520278.pdf].
24 The National Cybersecurity Strategy, Ministry of Security and Justice, Netherlands, 16 pages, June 2011.
25 Ministry of Defence, The Defence Cyber Strategy, Netherlands, September 2012, 20 pages, [http://www.ccdcoe.org/strategies/Defence_Cyber_Strategy_NDL.pdf]
26 New Zealand’s Cybersecurity Strategy, New Zealand Government, 2011, 16 pages, [http://www.dpmc.govt.nz/sites/all/files/publications/nz-cybersecurity-strategy-june-2011_0.pdf].
27 Cybersecurity Strategy for Norway, Norwegian Ministries, 32 pages, April 2013, [http://www.regjeringen.no/upload/FAD/Vedlegg/IKT-politikk/Cyber_Security_Strategy_Norway.pdf].
28 Cybersecurity Strategy and the National Action Plan on implementation of the national cybersecurity, 2013, 17 pages, [http://www.certro.eu/files/doc/StrategiaDeSecuritateCiberneticaARomaniei.pdf].
29 The Information Security Doctrine of the Russian Federation, September 2000, [http://www.mid.ru/bdomp/ns-osndoc.nsf/1e5f0de28fe77fdcc32575d900298676/2deaa9ee15ddd24bc32575d9002c442b!OpenDocument].
30 National Strategy for Information security in the Slovak Republic, 2008, 20 pages, [http://www.enisa.europa.eu/activities/Resilience-and-CIIP/national-cyber-security-strategies-ncsss/Slovakia_National_Strategy_for_ISEC.pdf].
31 Cybersecurity policy of South Africa, May 2011, 33 pages, [http://www.cyanre.co.za/national-cybersecurity-policy.pdf].
32 Defense White Paper, Ministry of National Defense, South Korea, 2010, 440 pages, [http://www.nti.org/media/pdfs/2010WhitePaperAll_eng.pdf?_=1340662780].
33 Estrategia de Ciberseguridad Nacional, Presidencia del Gobierno, Departamento de Seguridad Nacional, 55 pages, 2013, [https://www.enisa.europa.eu/activities/Resilience-and-CIIP/national-cyber-security-strategies-ncsss/ES_NCSS.pdf enisa.europa.eu/activities/Resilience-and-CIIP/national-cyber-security-strategies-ncsss/ES_NCSS.pdf].
34 National strategy for Switzerland’s protection against cyber risks, Federal Department of Defence, Civil Protection and Sport DDPS, 27 June 2012, 42 pages, [http://www.isb.admin.ch/themen/01709/01710/index.html?lang=en&download=NHzLpZeg7t,lnp6I0NTU042l2Z6ln1ad1IZn4Z2qZpnO2Yuq2Z6gpJCEeX9,fGym162epYbg2c_JjKbNoKSn6A--&t=.pdf].
35 National Cybersecurity Strategy, Government of the Republic of Trinidad & Tobago, December 2012, 29 pages, [http://www.nationalsecurity.gov.tt/Portals/0/Pdf%20Files/National_Cyber_Security%20Strategy_Final.pdf]
36 National Cybersecurity Strategy and 2013-2014 Action Plan, Republic of Turkey, Ministry of Transport, Maritime Affairs and Communications, 47 pages, 2013, [https://www.enisa.europa.eu/activities/Resilience-and-CIIP/national-cyber-security-strategies-ncsss/TUR_NCSS.pdf].
37 National Information Security Strategy, Republic of Uganda, Ministry of Information and Communications Technology, March 2011, 55 pages, [http://www.nita.go.ug/uploads/NISS.pdf].
38 Cabinet Office, The UK Cybersecurity Strategy, November 2011, 43 pages, [https://www.gov.uk/government/uploads/system/uploads/attachment_data/file/60961/uk-cyber-security-strategy-final.pdf].
39 Cybersecurity Strategy of the United Kingdom, Cabinet Office, June 2009, 32 pages, [http://www.official-documents.gov.uk/document/cm76/7642/7642.pdf].
40 The National Cybersecurity Strategy, The Cabinet Office, December 2013, 15 pages, [https://www.gov.uk/government/uploads/system/uploads/attachment_data/file/265386/The_National_Cyber_Security_Strategy_Our_Forward_Plans_December_2013.pdf].
41 International Strategy for Cyberspace, The White House, Washington, May 2011, 30 pages, [http://www.whitehouse.gov/sites/default/files/rss_viewer/international_strategy_for_cyberspace.pdf].
42 White House, The National Strategy to Secure Cyberspace, United States, February 2003, 76 pages [https://www.us-cert.gov/sites/default/files/publications/cyberspace_strategy.pdf]
43 Department of Defense, Department of Defense Strategy for Operating in Cyberspace, United States, July 2011, 19 pages, [http://www.defense.gov/news/d20110714cyber.pdf].
