2
PLA Views on Informationized Warfare, Information Warfare and Information Operations
Over the course of the past two decades, the Chinese People’s Liberation Army (PLA) has been closely examining the experiences of foreign militaries as it has sought to modernize itself and prepare for warfare under new, more high-technology conditions. Having not fought a war itself since 1979, the PLA nonetheless recognizes that the nature of modern warfare has fundamentally evolved in the intervening 35 years, and that it must adapt if it is to be victorious in future conflicts.
In the view of Chinese analysts, the advances in information technology have fundamentally altered the character of modern warfare. Consequently, an essential part of the PLA’s approach to future wars is the need to secure “information dominance (zhixinxiquan; ![]() )”. This extends beyond the realm of computer network attack and defense, and instead encompasses not only information systems (both hardware and software), but also the cognitive and decision-making aspects of military and political command.
)”. This extends beyond the realm of computer network attack and defense, and instead encompasses not only information systems (both hardware and software), but also the cognitive and decision-making aspects of military and political command.
2.1. The evolution of chinese military thinking
Even before the end of the Cold War, the PLA had already concluded that reliance on massed numbers of ill-trained, poorly equipped troops was no longer appropriate. Chinese assessments of the American war in Vietnam and the “Fourth Middle East War” of 1973 indicate a recognition of the growing importance of technology in warfare. Weapons had greater reach, and significantly improved lethality. Of equal importance, surveillance and reconnaissance systems had improved capabilities, making them more significant in the calculus of effectiveness. The Sino-Vietnam War of 1979 further underscored the growing role of technology in modern warfare.
By the early 1990s, it was clear that high technology was affecting not only weapons, but tactical and even strategic outcomes. Modern weapons, as seen in the first Gulf War (1990-1991), shifted the emphasis from the destruction of opponents to paralyzing them, in the course of defeating them. Moreover, the new technologies also expanded the operating areas, so that land, sea, and air arenas were no longer the complete set of potential battlefields. The same information technologies and improved sensor systems that made modern weapons that much more destructive, effectively made information space and outer space key battlegrounds as well.
Meanwhile, the pace and destructiveness of modern wars was such that even local wars (i.e. those not involving the mass mobilization of the nation and the economy) nonetheless could affect the entire country.1 Warfare was much more non-linear in nature, shifting from primarily ground/sea centered, to an exploitation of all three dimensions. Of particular importance, airpower, including long-range bombers and air-and sea-launched cruise missiles, was now much more destructive and decisive. At the same time, warfare was much more intense, involving round-the-clock operations. This also meant that the sheer material expenditure of warfare was even more substantial, further increasing the importance of logistics and sustainability. All of these elements, marking what the Chinese considered to be a global military transformation, were encompassed in the idea of “Local War Under Modern, High-Tech Conditions”. Preparing for such wars became the basis for PLA operational planning in a Jiang Zemin-issued directive to the Chinese Central Military Commission (CMC) in 1993.
In these directives, Jiang called on the PLA to undertake the “Two Transformations”, in the course of modernizing. The first transformation was in the kind of war that the PLA should be preparing for; a shift from “Local Wars under Modern Conditions”, to “Local Wars Under Modern, High-Tech Conditions”. This, in turn, would require the PLA to transform from focusing on quantity, to emphasizing quality, and especially the incorporation of technology.
In 1999, the PLA issued a new series of thoroughly revised manuals and regulations that constituted the “New Generation Operations Regulations”. These regulations embody and codify the two transformations that Jiang demanded of the PLA. They constituted a wholesale revision of operational doctrine, affecting every aspect of the PLA, from its conception of future wars to training and organization.
Analysis of more recent subsequent conflicts has further complicated PLA planning. NATO operations in the Balkans, the toppling of the Taliban in Afghanistan, and the second Gulf War have led PLA analysts to conclude that “Local Wars under Modern, High Tech Conditions” have now transitioned to “Local Wars under Informationized Conditions”. In these wars, command, control, communications, and intelligence (C3I) assumed ever growing prominence.
The ability to apply airpower effectively required coordinating air forces with land and naval forces. In short, the PLA must be able to conduct joint operations, in order to be able to win future wars. This, in turn, imposed significant demands upon command, control, communications, and intelligence functions. Successful joint operations require, at base, the ability to coordinate forces that operate across the various domains, and the ability to create a shared sense of situational awareness. Consequently, by the 1990s, the PLA recognized that they had to master the ability to bring together, land, sea, and air forces, and be able to operate in the land, sea, air, outer space, and information space domains. Airpower was increasingly seen as an essential tool, enabled through the ability to control the nature and flow of information.
Again, the senior leadership codified this shift by giving new guidance to the PLA. Hu Jintao, in his role as Chairman of the Central Military Commission, issued “new historic missions” to the PLA. According to Hu, the PLA would be responsible for:
2.2. The growing importance of information
As PLA authors note, wars reflect the broader state of societal and industrial development. Thus, as society has evolved from the Industrial Age to the Information Age, its wars have shifted from mechanized warfare to informationized warfare (xinxihuazhanzheng; ![]() ). In such wars, information and knowledge are core resources, and the resulting broad use of information technology allows the creation of a single, integrated information-space within which participating forces operate.
). In such wars, information and knowledge are core resources, and the resulting broad use of information technology allows the creation of a single, integrated information-space within which participating forces operate.
Informationized wars, not surprisingly, require informationized militaries, forces where information is integrated into each and every function – not just the weapons and their employment, but also logistics, personnel management, command and control. Only in this manner can there be real-time sharing and exploitation of information, to maximize its effect on operations. Only informationized forces can have fully developed integrated strength, drawing upon the capabilities of all the participating services and exploiting their respective strengths, while shielding each of their weaknesses.3
Informationized warfare, then, is in many ways a conflict between rival systems-of-systems. Each side seeks to create an integrated situational picture, and best exploit their respective capabilities. At the same time, since a system requires the smooth interoperation of all of its subordinate systems and sub-systems, an essential part of informationized warfare is striving to prevent that smooth interoperation. Thus, informationized warfare will involve attacking the key nodes and links within the other side’s system-of-systems, to precipitate cascading failures.
While informationized warfare is the application of information technology across the full range of military activities, information war (xinxizhan; ![]() ) involves making information itself the focus of warfare. Within this concept, information collection, management and analysis, transmission and exploitation are some of the main operational techniques. The focus is on disrupting the enemy’s information, information systems, and information users, while defending one’s own. The side that is best able to do this is able to secure the “information advantage (xinxiyoushi;
) involves making information itself the focus of warfare. Within this concept, information collection, management and analysis, transmission and exploitation are some of the main operational techniques. The focus is on disrupting the enemy’s information, information systems, and information users, while defending one’s own. The side that is best able to do this is able to secure the “information advantage (xinxiyoushi; ![]() )”.
)”.
In the Chinese view, information war (sometimes also translated as “information warfare”) has both a broad and a narrow meaning. The broad meaning of information war can also be termed “strategic information war”, which refers to the two sides’ use of information and information technology in the political, economic, S&T, diplomatic, cultural, and military arenas in order to secure information advantage. In this broad sense, information war spans military and civilian spheres, peacetime and wartime, and has a global nature. Strategic information war is an ongoing process.
The Chinese interest in “political warfare”, including public opinion warfare, psychological warfare, and legal warfare, is an example of “strategic information war”. It targets not just information per se, to fundamentally influence the context and framework of information. Strategic information war is aimed at influencing how information is perceived and interpreted, by not just military audiences, but the opponent’s civilian population, top leadership (military and civilian), and also third-party governments, militaries, and civilian populace.
The narrow meaning of information war involves the two sides in wartime driving to secure the information advantage, and undertaking information conflict, primarily in the military arena. As the Chinese note, this is what the US terms “battlefield information warfare”. The narrow form of information war targets the C4ISR systems, degrading the enemy’s and protecting and preserving one’s own. It builds upon the use of electronic technology as a support for electronic warfare (i.e. electronic warfare is the foundation), and its core remains electronic warfare.4
The main goal in information war, especially in the narrow sense, is securing “information dominance (zhixinxiquan; ![]() ”. This is consistent with other PLA writings, which emphasize the importance of establishing “space dominance”, “air dominance”, and “maritime dominance”.
”. This is consistent with other PLA writings, which emphasize the importance of establishing “space dominance”, “air dominance”, and “maritime dominance”.
Information dominance refers to the ability to establish control at a given time and space over battlefield information, while denying an opponent the same. In this context, battlefield information refers to information relating to the activities and changes in friendly and enemy forces, as well as the physical conditions of the battlefield (e.g., weather).5 Information dominance is generally seen as a temporary condition; it is difficult, if not impossible, to create a permanent condition of information dominance, unless one side enjoys an overwhelming advantage.
Establishing information dominance requires targeting and protecting information collection, management, and allocation assets; the communications and data links involved in getting information from sensors to users; the users themselves, including the decision-makers, commanders, weapons systems, and their controllers); and the information itself. One of the key targets is the decision-maker. Isolating them, destroying them, influencing and undermining them, are all elements of establishing information dominance.
In this regard, the Chinese are engaging in the obverse of what the NATO forces sought to do in the 1980s. For NATO, the purpose was to get inside the OODA loop of the Soviet adversary, to be able to engage in the OODA chain faster than their Soviet counterparts. At this point in time, the Chinese do not seem to think that they can be faster, so securing information dominance involves slowing down the opponent’s OODA loop.
Because of the importance of information in informationized war and information war, information dominance is seen as the prerequisite for establishing dominance in other domains, including sea, air, and outer space. As important, establishing information dominance includes operations in these other domains, because it entails not only things like cyberwarfare, but also the physical destruction and degradation of enemy information systems, such as command posts and communications systems. It therefore includes firepower strikes, special operations forces activities, as well as electronic and computer network warfare operations.6 Conversely, establishing air or space dominance facilitates establishing information dominance. In particular, space capabilities are seen as intimately linked with informationized war and information war – space will be a key battleground in the struggle for information dominance.
Information dominance is rarely absolute. Instead, the initial focus should be on establishing it at key times and places, or denying it to an enemy at those essential periods. The expectation is that the struggle for information dominance will be constant, lasting throughout the course of a conflict. This, in turn, means that there are different means that might gain or lose importance over that period. Thus, at one point, it might mean affecting decision-makers; at another, it might involve computer network attack.
2.3. Information operations
Information war (xinxizhan; ![]() ) involves campaigns and battles in pursuit of information dominance. Information operations (xinxizuozhan;
) involves campaigns and battles in pursuit of information dominance. Information operations (xinxizuozhan; ![]() are focused on specific activities and operations aimed at securing and maintaining information dominance, in terms of friendly and adversary attempts to be able to freely collect battlefield information.7 Information operations refers to those activities that seek to disrupt the enemy’s information and information systems, influence their ability to exploit information, while preserving one’s own abilities in this regard.
are focused on specific activities and operations aimed at securing and maintaining information dominance, in terms of friendly and adversary attempts to be able to freely collect battlefield information.7 Information operations refers to those activities that seek to disrupt the enemy’s information and information systems, influence their ability to exploit information, while preserving one’s own abilities in this regard.
Information operations are guided by the concept: “information as the main guide, offense and defense both prepared, network and electronic [warfare] unified, systems mutually accommodating [or linked] (xinxizhudao, gongfangjianbei, wangdianyiti, xitongjianrong; ![]() )”.8 PLA writings suggest that all forms of information operations are likely to include aspects of electronic warfare (dianzizhan;
)”.8 PLA writings suggest that all forms of information operations are likely to include aspects of electronic warfare (dianzizhan; ![]() ), computer network warfare (wangluozhan;
), computer network warfare (wangluozhan; ![]() ), and psychological warfare (xinlizhan;
), and psychological warfare (xinlizhan; ![]() ). Computer network warfare, or cyberwarfare, then, is not the only type of information operations, nor even the most important; rather, it is integrated into this broader conception of seeking to secure information dominance, and works in conjunction with electronic warfare (sometimes described as integrated network and electronic warfare) and psychological warfare.
). Computer network warfare, or cyberwarfare, then, is not the only type of information operations, nor even the most important; rather, it is integrated into this broader conception of seeking to secure information dominance, and works in conjunction with electronic warfare (sometimes described as integrated network and electronic warfare) and psychological warfare.
The concept of information operations covers four broad mission areas in Chinese analyses; as presented in the following sections.
2.3.1. Command and control missions
First and foremost is the ability to exercise command and control over one’s own forces. This entails the ability to collect, transmit, and exploit information. It requires commanders and staffs who can operate consistent with the operational plan, and whose decisions are not adversely affected by enemy propaganda, enemy influence, or enemy perception management. The struggle to be able to implement effective command and control in the face of electronic warfare, computer network warfare, and psychological warfare has given rise to what some Chinese analysts term “command and control warfare”.
Effective exercise of command and control, in light of advances in information technology, should allow for a flatter command and control structure, as well as a greater reliance on “mission oriented orders”. Commanders are expected to think one level higher, when setting objectives, consistent with their understanding of the overall objectives of campaigns.
2.3.2. Offensive information missions
Offensive information operations (xinxijingongzuozhan;![]() ) are essential for obtaining information advantage and establishing information dominance, since we cannot achieve information dominance solely through defensive measures. The PLA envisions several different means of implementing offensive information missions, including information coercion, information blockade, creating an information advantage, information contamination, and information paralysis, in each case combining various techniques including electronic warfare, computer network warfare, psychological warfare, and physical attacks.9
) are essential for obtaining information advantage and establishing information dominance, since we cannot achieve information dominance solely through defensive measures. The PLA envisions several different means of implementing offensive information missions, including information coercion, information blockade, creating an information advantage, information contamination, and information paralysis, in each case combining various techniques including electronic warfare, computer network warfare, psychological warfare, and physical attacks.9
2.3.2.1. Information coercion/information deterrence
The Chinese term for “deterrence”, weishe ( ![]() ), can also be translated into “coercion”. In the case of information operations, PLA writings suggest that we may be able to coerce an opponent through displays of information attack capabilities, including electronic interference and computer network attacks. PLA writings suggest that information coercion should be implemented in coordination with conventional and even nuclear measures. Thus, electronic interference should be undertaken at times that might mask other conventional force deployments, to induce confusion in the opponent’s camp.
), can also be translated into “coercion”. In the case of information operations, PLA writings suggest that we may be able to coerce an opponent through displays of information attack capabilities, including electronic interference and computer network attacks. PLA writings suggest that information coercion should be implemented in coordination with conventional and even nuclear measures. Thus, electronic interference should be undertaken at times that might mask other conventional force deployments, to induce confusion in the opponent’s camp.
Similarly, information coercion methods should be coordinated with public opinion warfare techniques, so that the threat is publicized to senior political leaders and the broader populace. Ideally, an information coercion effort would lead to degraded adversary information systems, confusion about overall Chinese capabilities, and a general lowering of adversary morale as a consequence.
In the Chinese view, information coercion methods have the advantage that they are more credible than conventional military or nuclear deterrent/coercive methods. The various methods involved in such an effort need not be formally acknowledged, and may not directly damage an opponent’s physical or data infrastructure, while nonetheless applying psychological pressure against their key military and civilian decision makers.
2.3.2.2. Information blockade
An information blockade involves large-scale suppression and interference with an adversary’s electronic and information systems. It includes not only electronic interference measures such as jamming, but also electronic deception and computer network penetration, to effectively cut an opponent’s ability to communicate with the outside world. It also involves efforts to prevent an opponent from obtaining information about the outside world; so, information blockades may also incorporate such steps as radar jamming, blinding or dazzling of reconnaissance satellites, and even physical destruction of reconnaissance aircraft and other information gathering systems.
According to PLA analysts, information blockades can be difficult to impose, because of the myriad ways that we can obtain information. Consequently, sequencing one’s information blockade efforts, such as by attacking terrestrial communications systems and then jamming radios, is essential. For the same reason, any information blockade will likely require the application of many different methods, and cannot rely on just computer network attack or jamming.
2.3.2.3. Information misdirection.
Information misdirection (xinxizaoshi; ![]() ) involves employing various means, including electronic and computer network deception, decoys, false information, etc., to manipulate an opponent’s perceptions, thereby misleading them regarding one’s own capabilities, intentions, and actions, and creating the opportunity for surprise. With the PLA’s longstanding interest in the application of deception and stratagem, information misdirection is the merging of such techniques with modern information technology.
) involves employing various means, including electronic and computer network deception, decoys, false information, etc., to manipulate an opponent’s perceptions, thereby misleading them regarding one’s own capabilities, intentions, and actions, and creating the opportunity for surprise. With the PLA’s longstanding interest in the application of deception and stratagem, information misdirection is the merging of such techniques with modern information technology.
As with any misdirection effort, information misdirection must be integrated into the overall strategic and operational plan. Troop movements, air and missile strikes, other communications should all be consistent with the misdirection effort. At the same time, information misdirection efforts should be consistent with realistic military goals. The Chinese assessment resembles the Allied effort to conceal the invasion at Normandy by emphasizing Calais, which played to the Germans’ firmly held belief that any invasion would have to seize a port.
To this end, information misdirection efforts must be comprehensive, and cannot rely on a single source or method. As PLA analysts note, the misleading information must be capable of fooling the enemy’s battlefield reconnaissance systems, their intelligence agencies and departments, and the other side’s commanders. This can only occur if the false information is independently corroborated, which in turn requires many different strands of mutually supporting false information. They must also incorporate defensive measures, to ensure that one’s misdirection plans are not leaked or otherwise discovered by an adversary.
2.3.2.4. Information contamination
Information contamination efforts involve the deliberate introduction of false, useless or infected information into the enemy’s information systems. The goal is to degrade an opponent’s ability to transmit information, disrupt their ability to use information, and infect their information systems, so that their information processing and exploitation capacities are crippled.
Information contamination efforts include denial of service attacks and introduction of computer viruses and logic bombs into opposing computer networks, but extend further, to include attacks on the enemy’s entire communications network, including both land-lines (e.g. fiber optic cables) and wireless systems, and information misdirection methods, to overwhelm an opponent with a flood of false information. They also include physical measures to obstruct or confuse enemy reconnaissance systems, so that the intelligence collected is incomplete or misleading.
2.3.2.5. Information paralysis
The PLA also discusses the need to paralyze an opponent’s information collection, transmission and management systems, through electronic, physical and other attacks. This goes beyond denying an opponent information (as in an information blockade), to actively destroying and disrupting their information systems. As one PLA analysis notes,
This means concentrating information attack troops and weapons, and undertaking electronic interference, [computer] virus attacks, and firepower strikes against enemy information systems, especially specific key elements (such as nodes). This will reduce and disrupt the integrated operational effectiveness of enemy information systems.10
Information paralysis efforts will entail both hard kill and soft kill methods, and employ electronic means, firepower strikes from land, sea, and aerial platforms, and also employ special operations forces. They will focus on command centers and command posts, as well as key sub-systems, including battlefield early warning command and control structures, main routers and switching centers of the telecommunications system, and radar networks and associated communications links. In the Chinese conception, once such systems are successfully attacks, an opponent’s command and control system will be unable to function normally, and will become paralyzed.
2.3.3. Defensive information missions
Defensive information operations (xinxifangyuzuozhan; ![]() ) complement offensive information operations. They are aimed at maintaining information resources, shielding them from enemy interference and restoring them, should they nonetheless be disrupted. This includes concealment, camouflage and deception, deterrence, early warning, and crisis response.11
) complement offensive information operations. They are aimed at maintaining information resources, shielding them from enemy interference and restoring them, should they nonetheless be disrupted. This includes concealment, camouflage and deception, deterrence, early warning, and crisis response.11
– Information concealment includes both physical concealment, camouflage, and deception (CCD), but also electronic concealment measures. Part of this is aimed at preserving the physical infrastructures and facilities, but also preventing information leaks. The goal is to prevent an adversary from obtaining information about one’s own information networks and systems.
– Information deterrence refers to the use of international law, diplomatic conflict, and potential retaliation techniques to make the enemy reduce or entirely lose their interest or capacity to undertake information attacks. This would apply to legal warfare and public opinion warfare techniques, aspects of “political warfare”.
– Early warning provides the opportunity for Chinese forces to detect signs of an impending attack, and allow for the activation of back-up information system, creation of pristine copies, etc. The goal is to minimize the impact of enemy information offensive operations, and might also contribute to information deterrence. In the Chinese view, if they can make clear that an opponent’s information offensive has already been detected, the adversary may choose not to proceed. Similarly, if previously existing vulnerabilities in Chinese electronic systems are suddenly neutralized, an adversary may decide that it should delay action, and perhaps even avoid conflict altogether.
– Early warning works intimately with information crisis response preparations. This includes physical dispersal and redundancy. Chinese analysts emphasize that information systems need to be networked, so that attacks on any given node or element will not necessarily collapse the system. In the event of a crisis, additional information resources may be activated, while civilian and commercial assets may be mobilized.
2.3.4. Information support and safeguarding missions
Mechanized warfare mainly involves the expenditure of steel, explosives, material instruments, and manpower. Informationized warfare, aside from these expenditures, also emphasizes the large demands for information and the large-scale consumption of information-related systems. In informationized operations, the two sides will not only be engaged in a contest between information offense and defense capability, but will also compete in logistical support capacity for those information operations. In the complex electromagnetic environment, it is necessary to ensure the smooth operation, and replacement when necessary, of electronic warfare equipment, information networks (including their physical facilities), and command networks. The battlefield commander needs geographic survey information, meteorological and hydrographic information, as well as civilian information resources, etc., which is also part of the responsibility of information safeguarding work.
2.4. Key types of information operations
In order to fulfill these broad mission areas, PLA analysts believe that future military forces must be able to engage in specific types of information operations. The most important are electronic combat, computer network combat, psychological warfare (including deception), but also include intelligence combat, command and control strength, and physical destruction.
2.4.1. Electronic combat (dianzizhan; 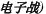
Electronic combat is a subset of the larger array of information operations. It refers to the capacity to attrit and disrupt the enemy’s electronic equipment, while defending one’s own electronic facilities and systems, and their normal operational capacity. Electronic combat is linked to computer network combat, but is more focused on electronic systems, and not solely those relating to information collection and transmission, or computer systems. In the PLA’s view, it is the foundation for broader information operations.12
Electronic combat includes electronic reconnaissance, measurement and signature intelligence, computer network reconnaissance, and electronic information management and security. It includes electronic offensive and defensive measures, and can incorporate physical as well as electronic measures.
2.4.2. Network combat (wangluozhan; 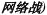
Network combat, or computer network combat, refers to those operational activities that employ computer network facilities, and the undertaking of computer network reconnaissance, offensive, and defensive missions. The goal of network combat is to establish network dominance (zhiwangluoquan; ![]() ) by attacking enemy computer networks and the information that passes over them.
) by attacking enemy computer networks and the information that passes over them.
It includes, on the one hand, any effort aimed at disrupting information networks, whether by nations, sub-national groups, the broad population (e.g. “patriotic hackers”), or terrorists. More narrowly, it refers to the range of information operations involving computer networks that are aimed at securing network dominance by attriting or disrupting the enemy’s computer networks systems’ information and ability to operate, while ensuring that one’s own computer network systems’ information and security.13 Network combat can therefore entail operations against computer hardware, computer software, as well as data passing over the computer network itself.
Network combat can be divided into strategic network combat and battlefield network combat.
Strategic network combat refers to the use of the Internet to attack the enemy’s national political, economic, military, cultural, diplomatic, and other information basic facilities, attriting the enemy’s strategic information resources and ability to employ information. We seeks, through network conflict activities to attrit the enemy’s comprehensive national power, while at the same time protecting one’s own strategic information facilities, information resources, and information capability.
Battlefield network combat is the narrow meaning of network combat. It involves network attack, network defense, and network support operations and missions, as conducted by information operations units (xinxizuozhanbudui; ![]() ).
).
2.4.3. Psychological combat (xinlizhan;
From the Chinese perspective, the human element is as much part of information warfare as the digital or physical elements. Consequently, information operations include a large component of psychological warfare.
The goal of psychological combat, in the context of information operations, is to influence the perceptions and thought processes of the two sides’ decision-makers and information users. It involves the employment of various types of information, delivered through such means as news media, social media, public opinion, to influence an adversary’s emotions, perspectives, concepts, attitudes, so as to reduce their spirit and will, and disrupt their psychological balance, shaking their willingness to fight.14 There is also an element of disrupting their cognitive functions, whether through information overload or the imposition of psychological pressures, so as to lead to poor judgments and reduced combat effectiveness.
Psychological combat can occur at the strategic, operational, and tactical levels of war. Such efforts include emotional appeals, intimidation (such as warnings sent to the private accounts of senior officers and political figures), deception, and the spreading of defeatist attitudes. These efforts can be implemented through such means as social media and Internet memes, as well as more traditional broadcasts, leaflets, etc.15
Psychological defensive measures not only seek to neutralize enemy information attacks, including psychological attacks, but also to break any enemy attempts at imposing an information blockade, which creates a sense of isolation and helplessness. This is one lesson the Chinese seem to have derived from the two Gulf Wars, that the imposition of an “information blockade” can have devastating psychological consequences.
2.4.4. Intelligence combat (qingbaozhan; .
.
Intelligence combat (qingbaozhan; ![]() ) is an essential element of information warfare and information operations. It involves efforts to collect intelligence information, control its flow, and apply it more effectively than an opponent, while at the same time defeating their efforts to obtain and exploit intelligence. Intelligence combat is ultimately focused on the collection of information.16
) is an essential element of information warfare and information operations. It involves efforts to collect intelligence information, control its flow, and apply it more effectively than an opponent, while at the same time defeating their efforts to obtain and exploit intelligence. Intelligence combat is ultimately focused on the collection of information.16
Intelligence combat has a broad and a narrow meaning. The broad meaning refers to the effort by the antagonists to collect information pertaining to politics, economics, science and technology, as well as military, cultural, and diplomatic aspects. The narrow meaning of intelligence combat refers to the efforts to secure or counter the securing of military intelligence. In each case, there are strategic, operational, and tactical dimensions.
It should be noted that even under the narrow meaning, intelligence warfare includes broad aspects of information collection, such as of meteorological and hydrologic information and space situational awareness so as to better understand likely battlefield conditions. Similarly, it involves the creation of electronic and physical orders of battle, accumulating libraries of electronic and acoustic signatures and characteristics.17 Because such information can only be acquired over an extended period of time, intelligence combat is a constant effort that overlaps the boundaries between peace and war.
2.4.5. Command and control combat (zhihuikongzhizhan;
Command and control combat (zhihuikongzhizhan; ![]() is the struggle by the two sides in a conflict to secure an advantage in the exercising of command and control over one’s forces. It involves preserving one’s own command and control networks, while disrupting and destroying the enemy’s. Command and control warfare involves the comprehensive coordination of operational security, military deception, as well as electronic, network, and psychological warfare.18
is the struggle by the two sides in a conflict to secure an advantage in the exercising of command and control over one’s forces. It involves preserving one’s own command and control networks, while disrupting and destroying the enemy’s. Command and control warfare involves the comprehensive coordination of operational security, military deception, as well as electronic, network, and psychological warfare.18
In the Chinese conception, command and control combat is distinct from computer network combat, highlighting a fundamental difference between PLA and western military thinking.19 Computer network combat is mainly undertaken by breaking into networks, engaging in electronic recon, breaking into (storage) media, in order to gain network information, and obtain local network superiority (jubuzhiwangluoquan; ![]() . Command and control warfare mainly focuses on disrupting command and control network operations, affecting and attriting enemy command and control system effectiveness, so that the enemy’s command and control systems are paralyzed or suffer temporary breaks. Chinese writings imply that this focus is on military C2 systems, which would suggest that SCADA-type attacks would be part of computer network, rather than command and control, combat.
. Command and control warfare mainly focuses on disrupting command and control network operations, affecting and attriting enemy command and control system effectiveness, so that the enemy’s command and control systems are paralyzed or suffer temporary breaks. Chinese writings imply that this focus is on military C2 systems, which would suggest that SCADA-type attacks would be part of computer network, rather than command and control, combat.
To a particular degree, it may be said that command and control combat is a special type of computer network combat. Command and control strength refers to the command and control information systems at command centers (zhihuizhongxin; ![]() ), and the associated command posts (zhihuisuo;
), and the associated command posts (zhihuisuo; ![]() ), as well as the facility systems and workers at command terminals (zhihuizhongduan;
), as well as the facility systems and workers at command terminals (zhihuizhongduan; ![]() ), who employ command and control information systems, in the process of exercising operational command, in future information operations or joint campaign operational activities (weilaixinxizuozhanhuolianhezhanyizuozhanxing dong;
), who employ command and control information systems, in the process of exercising operational command, in future information operations or joint campaign operational activities (weilaixinxizuozhanhuolianhezhanyizuozhanxing dong; ![]() ). Command and control combat, then, will incorporate computer network attack aimed at those command centers and command posts, and efforts to defend one’s own facilities. However, it will also encompass physical attacks aimed at those facilities as well.
). Command and control combat, then, will incorporate computer network attack aimed at those command centers and command posts, and efforts to defend one’s own facilities. However, it will also encompass physical attacks aimed at those facilities as well.
2.4.6. Physical combat
Just as information operations include psychological efforts aimed at the human factor, it also includes physical attacks against the various components of the opponent’s command, control, and information networks. Consequently, PLA writings note that physical attacks, by the range of military systems, from ballistic missiles to aircraft to special operations forces, are also an essential part of information operations.
PLA analyses note that physical attacks can often have synergistic effects, complementing other forms of information operations. In the 1979 Sino-Vietnamese War, for example, it is noted that Chinese forces targeted Vietnamese artillery communications land-lines, compelling artillery forces to rely on radios to communicate with spotters and observation posts. The Chinese then employed jammers and other methods to disrupt the radio-links, neutralizing coordination efforts.20 We can posit similar effects through, for example, the destruction of enemy reconnaissance aircraft which may compel reliance on predictable satellites. Conversely, destroying satellites may eliminate wide-coverage surveillance capabilities which can only be partially compensated through aircraft.
Physical attacks can also provide windows of opportunity. We need not destroy an entire constellation of observation satellites, it may be sufficient to simply create periods of blindness. Similarly, because information dominance is difficult to maintain over the entire course of a conflict, physical attacks may create conditions of local superiority, or cause the enemy to withdraw or limit their information collection efforts (in order to preserve their own resources).21
2.5. Computer network warfare and information operations
All of this suggests that, for the Chinese People’s Liberation Army, computer network reconnaissance, computer network attack, computer network defense, and computer network exploitation are not necessarily seen as stand-alone operations, but are integral to the broader tasks of information operations. Thus, computer network operations are part of command and control combat, psychological combat, and intelligence combat, as well as network combat.
This suggests that Chinese computer network operations need to be analyzed in the context of larger military operations. Given the Chinese emphasis on coordination, it is likely that their computer network operations will be coordinated with planned physical attacks in the land, sea, air, and outer space domains. Peacetime operations are likely intended to benefit wartime operations, whether by reconnoitering command and control structures, identifying key command and communications nodes, or influencing military and political decision-makers.
Conversely, it should be expected that Chinese efforts at computer network security are likely coordinated with other aspects of information security, including the civilian sector. Indeed, one Chinese analysis observes that computer “networks have become the front line and main staging ground for military information security efforts”.22 Chinese efforts in this regard likely benefit from both the outsize role of the government in Chinese cybersecurity (the so-called “Great Firewall of China”), and the extensive integration between military and civilian information networks.
1 Gao Yubiao, Chief Editor, Joint Campaign Course Materials (Beijing: AMS Publishing House, August 2001), p. 45.
2 Chinese Military Encyclopedia Committee, Chinese Military Encyclopedia, Vol. II, (Beijing, PRC: Academy of Military Science Publishing House, July 1997), pp. 126–127.
3 AMS Operations Theory and Regulations Research Department and Informationized Operations Theory Research Office, Information Operations Theory Study Guide (Beijing, PRC: AMS Publishing House, 2005), pp. 42–43.
4 AMS Operations Theory and Regulations Research Department and Informationized Operations Theory Research Office,Information Operations Theory Study Guide (Beijing, PRC: AMS Publishing House, 2005), pp. 67–69.
5 AMS Operations Theory and Regulations Research Department and Informationized Operations Theory Research Office, Information Operations Theory Study Guide (Beijing, PRC: AMS Publishing House, 2005), pp. 13–14.
6 Yuan Wenxian, Joint Campaign Information Operations Teaching Materials (Beijing, PRC: NDU Publishing House, 2009), pp. 179–185.
7 Tan Rukun, Teaching Materials on Operational Strength Construction (Beijing, PRC: AMS Publishing, 2011), pp. 196–197, and Yuan Wenxian, Joint Campaign Information Operations Teaching Materials (Beijing, PRC: NDU Publishing House, 2009), p. 2.
8 Tan Rukun, Teaching Materials on Operational Strength Construction (Beijing, PRC: AMS Publishing, 2011), p. 202.
9 Drawn from Yuan Wenxian, Joint Campaign Information Operations Teaching Materials (Beijing, PRC: NDU Publishing House, 2009), pp. 109–114.
10 Yuan Wenxian, Joint Campaign Information Operations Teaching Materials (Beijing, PRC: NDU Publishing House, 2009), p. 114.
11 Tan Rukun, Teaching Materials on Operational Strength Construction (Beijing, PRC: AMS Publishing, 2011), p. 202.
12 AMS Operations Theory and Regulations Research Department and Informationized Operations Theory Research Office,Information Operations Theory Study Guide (Beijing, PRC: AMS Publishing House, 2005), p. 94.
13 Tan Rukun, Teaching Materials on Operational Strength Construction (Beijing, PRC: AMS Publishing, 2011), p. 204.
14 Yuan Wenxian, Joint Campaign Information Operations Teaching Materials (Beijing, PRC: NDU Publishing House, 2009), pp. 14–15.
15 Xie Zheng, Science of Information Operations Teaching Materials (Beijing, PRC: AMS Publishing House, 2013), pp. 179–180.
16 Li Naiguo, New Concepts of Information Warfare (Beijing, PRC: AMS Publishing House, 2004), p. 35.
17 Sung Yuejin, Command and Control Warfare (Beijing, PRC: National Defense Industry Press, 2012), pp. 29–30.
18 Sung Yuejin, Command and Control Warfare (Beijing, PRC: National Defense Industry Press, 2012), p. 29.
19 Tan Rukun, Teaching Materials on Operational Strength Construction (Beijing, PRC: AMS Publishing, 2011), pp. 205–206.
20 Yuan Wenxian, Joint Campaign Information Operations Teaching Materials (Beijing, PRC: NDU Publishing House, 2009), p. 111.
21 Xie Zheng, Science of Information Operations Teaching Materials (Beijing, PRC: AMS Publishing House, 2013), p. 189.
22 Guo Ruobing, Discussions of Military Information Security (Beijing, PRC: NDU Publishing House, 2013), p. 66.
