Chapter 9
Mobile Attacks
Information in this chapter:
Mobile devices are any device that is connected to a network that operates from a wireless-type of connection and can be taken with the user for continued use. Mobile devices are often considered handheld devices and have evolved from the older personal digital assistance or PDA. They have many names associated with them, with the most current being “smartphone.” These devices are also often used with a small keypad, a stylus pen or a touch screen for input. These mobile devices have in recent years expanded in use and growth. Aside from smartphones, digital pads are now the successor of the mobile arena. These mobile devices function similarly to a smartphone however generally have a bigger display screen and cross between a smartphone and a laptop.
Today, client-side attacks have grown beyond the enterprise and home user who was tied to their computers at their desk. Now, because of the age of mobility, the network has no boundaries and because of that fact, neither do client-side attacks. The playing field has become more and more difficult to secure because of mobility. Now, just about everyone you know has a mobile device, client side attacks have grown exponentially.
Mobile devices are constructed and sold by many companies to include Research in Motion (RIM), Motorola, Apple, and Samsung. There are many vendors who produce them however these are some of the biggest developers and resellers of mobile devices today. The way these devices connect is generally through an antenna connecting to a cellular or wireless network. They follows specific standards and are not immune to the threats that each medium possesses.
The devices themselves also come with a preloaded (and sometimes replaceable) operations system installed on it. The operating systems then have applications installed on them similar to how a desktop computer works. These applications (most times applets or Web applications) are just as at risk to client-side attacks as they desktop counterparts. The operating systems are also easily attacked as vulnerabilities reside with the code that they are constructed with is not immune to attack. We will cover these specifics in detail with this chapter.
Mobile Devices and Client-Side Attacks
Client-side attacks as we have learned throughout this book are aimed at any device that is deemed an end point where data or services are accessed from. This can be a desktop, laptop, mobile phone, or any other device wired or wireless. There are also many different devices that qualify as “mobile.” For example, undocking a laptop on your desktop and going to a meeting while attached to a wireless network is a mobile device. Attaching your smartphone from a wireless network while also attached to a cellular and Bluetooth network simultaneously is a mobile device. Connecting your Apple iPad to the wireless network qualifies as a mobile device. Worse, every single one of these devices are vulnerable to the same client-side attack that your stationary desktop systems are prone to. They are also moving from place to place, from work to home and back and connected to multiple networks all at the same time. Figure 9.1 shows the attack vector for mobile devices.
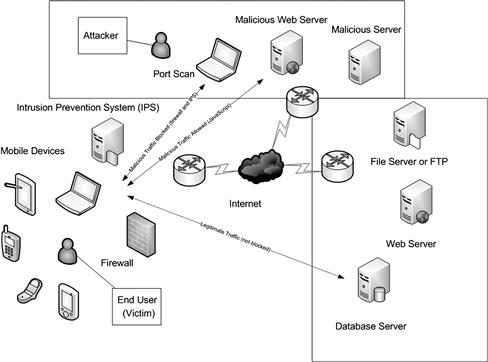
Figure 9.1 Mobile Client-Side Attacks
Did You Know?
The amount of mobile devices in use today are staggering… not only do you have the personal and business use devices we already mentioned such as smartphones, pads and PDA’s, but you have a multitude of other devices that are specific to functions and services—as an example, most companies use their own specific handheld systems for specific functions such as health and hospital systems that use their own mobile phone systems, Radio-frequency identification (RFID) readers, smart card readers, barcode readers and so on, the vectors for attack grow at an alarming rate.
Mobile devices also perform dozens of functions. They are used to play games, send text messages, make phone calls, send and receive emails, do banking, play music, take notes, pictures, video and so much more. In some cases, system administrators use these same devices to manage their networks and use system tools, develop code and plan and manage meetings. There really is no end to what these devices can handle and do. As mentioned earlier, this makes it extremely more difficult to manage them and secure them properly. It’s also a major issue that there are so many different kinds of devices out there with many different operating systems, applications, coded differently and managed differently that it becomes somewhat of an administrative nightmare if you and or your company does not standardize on a manageable platform.
Note
Bring your own device (BYOD) is a new commonly used term and concept in place in most enterprises that is considered a security nightmare. Because so many people bring their own device to work anyway, many companies are expensing them if used for work. Yes, it limits the amount of devices you need to carry and manage, however, it allows anyone to bring a device to work and connect it for use which if exploited, could potentially thwart any security you currently use or have in place to protect your systems and network.
Personal devices bring a new problem to organizations. As more and more people bring their mobile devices to work, they also potentially bring hazards with them depending on how they are used. For example, computers were generally locked down so that viruses, worms and other malware could not propagate. As an example, securing users from adding external drives such as a USB drive helped alleviate these types of issues. Now, when you connect your mobile device to your PC or MAC (as an example), your mobile device acts like a USB drive loaded with files that could potentially be brought into your network and exposed to your protected systems. Desktop systems are generally locked down, applied policies, monitored and updated with patches, whereas personal systems are generally not. As a security professional, this is something to consider when using mobile devices—they eventually are docked somewhere to get updates, upgrade the operating system or back up the device.
Warning
Desktop system connectivity is a concern. When not mobile, a device can easily be connected to a stationary device such as a PC, where it will be docked. Security concerns such as transferring viruses.
Connectivity to a network or its systems needs to be considered and protected against. A good way around the network connectivity problem is to attempt to separate network connectivity and systems that are accessed from mobile devices from your corporate network. As an example, if your mobile devices are connecting to a wireless access point (as an example), you can separate the traffic to a secure segment with separate connectivity, its own firewall and management software. This offers a layer of protection if needed. Also, new tools and software comes out often to secure mobile devices so try to stay on top of the mobile trend and what is being done to combat client-side attacks as they grow more prevalent on mobile devices. Securing against malware is covered in Chapter 10.
Communication Types
The way mobile devices connect to the network and transfer data, communicate and share resources is similar to commonly used networks today, however they do more than the standard by allowing for multiple types of simultaneous wireless connectivity. This brings challenges to security professionals because as an example, even if you wanted to and were successful at securing a wireless network, segmented it and set up a firewall… what prohibits an end user from using their carriers cellular network to transfer data and expose themselves to risk? In the next sections we will cover the different communication types you will need to be aware of to secure against client-side attacks. Figure 9.2 shows all of the different ways a mobile client could potentially connect to various networks and be exploited.
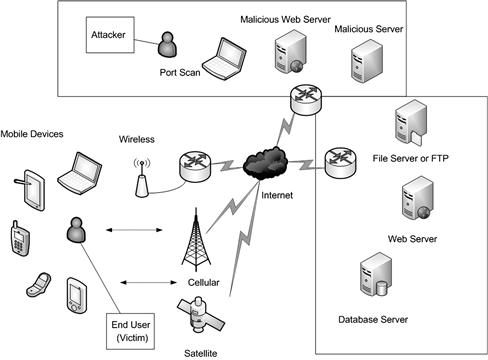
Figure 9.2 Mobile Client-Side Attack Vectors
Cellular Networking
Cellular network is most commonly the native connectivity method deployed with most cell phones, smartphones, and dial-up devices. It’s a mobile-based network used with a radio antenna. These devices are associated with “cell”s and can move from cell to cell in order to communicate and maintain communication. Mobile devices (such as phones) utilize this network to connect to their providers such as AT&T, Sprint and T-Mobile which are some of the most commonly used. Those providers then handoff requests to the internet, or from device to device based on the requests that are sent.
The radio antennas used are commonly set to a specific band/frequency and use specific cellular technology, such as Global System for Mobile Communications (GSM) and Code Division Multiple Access (CDMA), via a tower and or a satellite. Although there are many others, these are the most commonly used today.
Wireless Networking
A mobile device can connect to a network via “wireless networking,” which means that no wired connectivity needed to communicate on a network. This is generally done by using a wireless access network card with a built in antenna that connects to an access point used to aggregate multiple connections to a wired point on the network. It does this similarly to cellular in that is used radio waves/frequencies to connect and transmit signals back and forth between the client and the access point. The data is commonly then placed on a wired network to continue the process of data communication.
Note
The most used wireless standards are IEEE 802.11 which is a set of standards for wireless local area networks (WLAN). This is done via specific frequency bands in the 2.4, 3.6, and 5 GHz ranges. The IEEE is a Standards Committee whom manages all 802 standardization.
Bluetooth
Bluetooth is one of the most commonly used network connectivity methods in use today. Bluetooth is a proprietary networking standard used for short range wireless connectivity and is often used to connect peripherals to base devices. For example, you may have a Microsoft Xbox at home with “wireless” controllers. Your phone may have a “wireless” headset you use for hands-free calling. These devices will most likely be using Bluetooth as the method in which it offers connectivity.
Note
Bluetooth connects devices in the ISM band at 2400–2480 MHz. Devices connected via Bluetooth are considered to be part of a personal area network (PAN).
As you can see, there are many risks associated with mobile devices because not only are they in great numbers, but they are also hard to monitor and control and have many avenues in which they can connect to different networks. To secure against client-side attack, make sure that you consider the use of mobile devices in your organization and protect with end-user education, security policy, and/or enforcement. Enforcement can be policy based, where you eliminate all personal device usage and do not allow for it to be a part of your company network, connect to PCs, or used freely on the network. For example, if you wanted to secure Apple iPhones from connecting to your corporate desktops, you can enforce a policy that disallows for it, barring iTunes (which is needed when connecting an iPhone to your desktop) from loading or being installed. This is but one example of how to enforce not using a mobile device on your corporate network.
Types of Mobile Devices
There are literally hundreds of devices to choose from. With nearly every major vendor creating a form of mobile device for end users and businesses, it’s difficult to account for them all. Vendors such as Samsung, Nokia, Cisco, Microsoft, RIM, Apple, Google, and Toshiba (to name a few) are all creating handhelds, tablets, smartphones, and other mobile devices for personal and enterprise use. In this section we will cover some of the more commonly used mobile devices and explain their functionality and use. By understanding the feature sets, functionality and how they are used, it will help you understand their weaknesses and how to secure them from attack.
Apple
Apple has released some of the most well-known, functional and widely used devices of all time to include the iPod, iPhone, and iPad. All of which are considered mobile devices. Like most other Apple devices (computers, mobile devices, etc.), Apple functions off of a proprietary model that limits the functionality of the user to customize their systems. For example, with Google Android which we will cover in the next section of this chapter, you can “root” the device and alter the operating system on the device. With Apple, the security concerns are the same as what we covered earlier in the book. The Safari Web browser is used on the phone. You are susceptible to the same issues with it, as well as email, texting, and transmitting viruses via USB connectivity.
When you are unsure of the mobile device and want to start fresh, it’s recommended that you wipe the system clean. A full data wipe of the system can be conducted quickly to restore your device to factory defaults. However, ensure you have a complete backup of all of your settings and data before proceeding. An example of a data wipe is seen in Figure 9.3. On your Apple device, go to settings and you can perform a restore.
Figure 9.3 Performing a Restoration on your Apple iPhone
You can conduct a security assessment of the device. With Safari, make sure you switch private browsing on, and control your cookies. You can clear your history, cookies, and other data. You can also apply other security features such as fraud warning, and control your JavaScript and Block Pop-up settings. Figures 9.4 and 9.5 show an example of configuring security settings on your Apple device.
Figure 9.4 Configuring Security Settings on your Apple iPhone
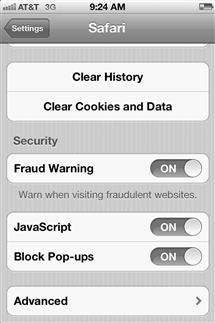
Figure 9.5 Advanced Security Configuration on your Apple iPhone
Similar to how your desktop computer is exploited by client-side attacks, you can mitigate threats by simply tightening up the security of your mobile device through the base operating system. If you do not want your Web browser hijacked (as an example), its recommended that you harden your mobile device as much as possible.
In the general settings applet, you can disable Location Services. If you do not want your location being tracked, you can turn off this feature globally, or on a per application basis. For example, if you wanted to turn off location tracking for your photo’s. Figure 9.6 shows you how to turn off this feature. Although this may not seem directly related to client-side attacks, it is a way that you can be profiled, and then attacked in a different way based on how you are profiled. It’s recommended for added security that you turn off this feature.
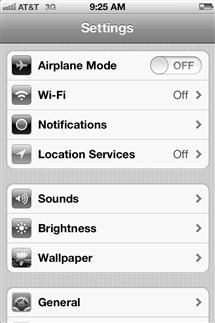
Figure 9.6 Disabling Location Services on the iPhone
Did You Know?
Your phone can become a card reader with a swipe pad and that is yet another reason why you should pay close attention to hardening your mobile device. If your device is processing credit card information, it’s imperative that you keep it clean from client-side attack.
Android from Google is one of the most popular mobile systems used today aside from Apple’s iPhone and its biggest competitor. Although it’s common to get an iPhone from Apple with the same look and feel as the versions before it, Android it a little different. iPhone is closed-source, meaning the operating system and hardware it is installed on is kept on a guarded leash so to speak, whereas when you purchase Android, you not only have an open-source based operating system with many different versions, you have a wide array of hardware to install it on such as Google’s Nexus line, Motorola’s Droid line, Samsung Epic, HTC’s Legend, EVO 4G, and Wildfire. That being said, not only do you have to worry about security across many platforms, you also have to worry that it’s an open-source solution. The Linux-based Android operating system is completely customizable, a far different experience than that of the Apple iPhone. The Android operating system can be seen in Figure 9.7.
Figure 9.7 Example of the Android OS
Just like any other mobile device, it’s imperative to tighten security in order to prevent client-side attack. Android has its own share of security issues. In the past few years, it has been noted not only is the system vulnerable, but also the Apps installed on it increase the possibility for attack exponentially. These “Apps” are downloaded online over the internet from the Google Play (Android Market) online store and other third-party Web sites. Figure 9.8 shows the security Apps available to install on your mobile device.
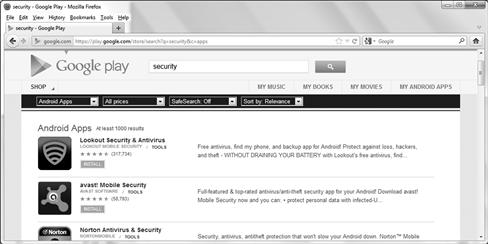
Figure 9.8 The Google Play Store
The software you download and install on your mobile device always has the potential to cause issues with keeping tighter security on your system. Android follows the same sandboxing model used with many other operating systems currently available. This means that when you install something, it is supposed to limit the impact on the core operating system if exploited. For example, Android uses a permissions model in which an App is installed with only the permissions needed to work with the system. When an App is untrusted or written by a third-party vendor, you may be inviting danger. Although Google Play is made to be safe, its Apps are not closely vetted like Apple’s iTunes store. With a maliciously written App, your phone could be made susceptible to a wide range of attacks such as an attacker listening in on and recording your conversations.
Warning
Android can be “rooted.” A non-rooted device is one that remains locked down whereas if it is rooted, it is opened up to the user and able to be further customized. This provides full permissions to the user who can then alter the operating system in any way they desire. It is ill advised to those who know little about their mobile device because the wrong change can render it useless. A “bricked” phone is one that is made useless, although it can be restored if you have a backup and know how to restore it.
RIM
Research in Motion (RIM)’s Blackberry was at one time the de facto mobile device to have and many corporate businesses deployed them in large numbers. With the movement towards BYOD, as well as the plethora of problems RIM has seemed to have over the years keeping their network, devices and business stable, it has slipped behind many of the other mobile offerings available today. Although RIM is trying to build itself back up by offering security software for mobile devices in general, it does not have the footprint it once did. Mobile Fusion, a device management—security software for the iPhone and Android is being developed to manage and protect mobile devices in general. It is however worth mentioning because it is still widely used and susceptible to client-side attack none-the-less. As with Apple and Google’s offerings, you should pay close attention to the same problematic scenarios that plague any mobile device, such as malware, unsecured Web applications, browser-based attacks, and so on.
Did You Know?
There are many other phones. Windows Phone is another commonly sold mobile device that although not as widely used as the others, has a large install base. Obviously we cannot cover every single mobile device and operating system in use, nor the countless applications that can be used on and with them. No matter what mobile device you use, whether it be a pad, a smartphone, PDA or other, you should always pay close attention to the basics. When considering client-side attacks always pay strict attention to the device’s software and treat it like any other operating system you would secure. Consider permissions… consider patches, bugs, how your applications are downloaded and installed and keep an eye on how the device is used. Also, make sure you do not physically lose the phone. Make sure you consider all aspects of client-side security when you enter the mobile-market.
Mobile Devices Attacks
Now that we have covered the different offerings and their basic functionality, common security issues and their inherent differences, let’s take a look at the types of attacks most commonly seen on a mobile device:
These although not all, are the most commonly seen attacks on mobile devices today. You can protect yourself by following solutions we have provided, however being conscious to the problems and exploitable factors and hardening your system the best you can is the best advice you can follow when securing your mobile devices from client-side attacks.
Snooping and Tracking
When using mobile devices, you have a lot of functionality you rely on, for example you can rely on the fact that if you want to connect and have a video conversation with someone, you can and you can rely on that if your device is stolen or law enforcement wants to track you, it can be done but in the same token, so could an attacker. You can in fact be snooped on if your device is exploited.
An exploited device can transmit what it see’s back to an attacker which is an invasion of privacy. Law enforcement can track you, online management software can track you and if exploited, a hacker can track you.
Malware
Malware can traverse and infect any device, regardless of make, model and version. Whether it be a network switch, email server, client desktop, or mobile phone, any device that uses software can be susceptible to malware. In Chapter 10 we will cover in depth coverage of malware and ways to protect against it, however the best way to protect yourself from malware attacks on mobile devices is to treat those devices identically to their desktop counterparts. You need to harden your operating system settings, keep the system patched and up to date and beware what you do on it, download and install on it and what networks you connect to.
Unsafe Web Applications
When you get a mobile device, generally, to use it you must add applications to it in order to be more productive. Accessing and downloading protected content from trusted providers is the best way to go, such as Google Play or the iTunes store, however, that does not mean their vetting process is always 100% accurate. Be wary of all third-party vendors and always consider that anything installed on your system could potentially be malicious. Figure 9.9 shows where safer applications can be downloaded and installed on your mobile device.
Figure 9.9 The iTunes Store
You should also consider that your privacy can be a concern when installing applications because sometimes it will activate additional services on your device in order for them to function. For example, you may install an application that requires or is dependent on Apple’s location service functionality which allows your online movements to be traceable.
Web Browser Exploits
Most if not all operating systems today come with a Web browser or allows for one to be freely downloaded and installed. As we have covered thoroughly throughout this book we have explained the many ways a Web browser can be exploited in a client-side attack and this is no different for a mobile device. Web browsers need to be patched, updated, and hardened so that they are less exploitable. You should also follow the same precautions you would with a desktop system or any other browser in that you should try to only visit reputable sites.
Another phenomenon is being sent links to problem sites from your text messenger. Although the attack comes from a phone number, it sends a link that will open your browser and set you up for attack. Figure 9.10 shows the attack pattern of this type of threat.
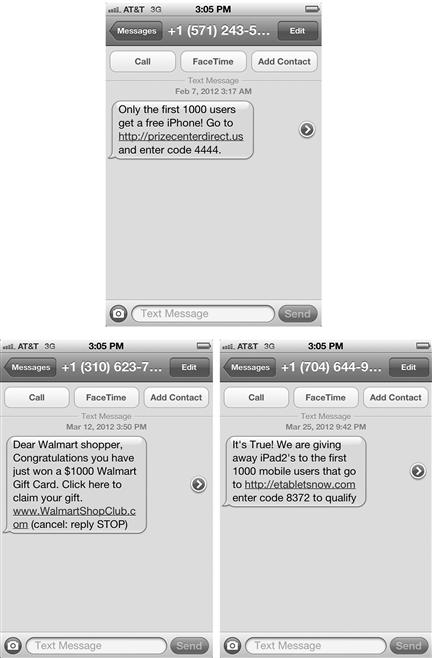
Figure 9.10 Example of a Texting Hoax
To avoid being exploited, simply ignore these requests from numbers you do not know and never click on a link in which you are unsure of.
Device Theft
Nothing is worse than relying on your mobile device for all you do and have it stolen or losing it. Not only is it extremely inconvenient, it’s incredibly dangerous. There are many things that can happen from losing your device. When a device is lost and found by someone or stolen from your care, you can suffer from not only losing data that may or may not be backed up, but that data can be exploited. You can protect against this with a password or other security mechanism on your device, but it can easily be thwarted.
In cases, where your mobile device is open and exploitable, a potential attacker can access all of the data on your phone. This includes any data currently on it to include (but not limited to) your address book, media, texts, and other sensitive data. For example, what if you kept a list of your passwords on a notepad saved within your device and now that device has been compromised. Not only is that device the source of all other areas in which you store data, but also the vehicle in which it can be accessed. Sometimes users will cache passwords such as the one to their voicemails directly on their mobile device so an attacker can learn more about you through your voicemails, text, email, and other communication methods.
Your device can store a lot of personal data and if you lose it you stand to not only lose it but have it used against you. Luckily, devices such as the Apple iPhone have the ability to be tracked online through applications such as MobileMe. This application will allow you to track your phone if lost or stolen and backup and restore the data you may have kept on it. This does not stop it from being compromised in the first place and much like losing your wallet or pocket book and your credit cards, much like you have to take extra steps to cancel and put freezes on these accounts, similarly you will need to follow the same procedures if your device turns up missing.
Man in the Middle (MITM) Attacks
Man in the Middle (MITM) attacks are those where an attacker inserts themselves in between a legitimate conversation and can either listen to the conversation and or pose as one of the recipients of communication. Mobile devices are commonly attacked this way when trying to set up a secure connection with a Web site or other connection point, an attacker can insert bogus information such as certificates, and because of this potential issue, could redirect you to an unsecured site, submit a fake key in a key exchange or other potential hacking scenario.
Denial of Service (DoS) Attacks
Any device that connects to a network can be subject to being overwhelmed by a malicious exchange of traffic to disrupt services, for example, overwhelmed buffers on IP networks, flooding inboxes with trash and other similar attacks. These are also prevalent on mobile devices, even more so now that most people work and live off their mobile devices instead of stagnant desktop PCs.
Social Engineering
There are many non-technical attacks leveraged against mobile devices. A common one is shoulder surfing. This can be used to collect a password. Social engineering is employed in order to garnish information from the mobile device without touching it or technically trying to hack into it. Someone could leave their mobile device out and someone could come by and alter it without the owner knowing. Or, you could be tricked into doing something by an attacker helping you do something on your phone but misleading you to do something they intend so that they can maliciously.
For example, asking someone to borrow their phone to make a quick phone call and gleaning information from the device as appropriate to enact an attack later, or by installing something on the phone that the owner did not know or realize was being installed. For example, tracking software that does not show up as an icon on the mobile device screen but installed and running being used to track your location and activity like a keylogger for PC’s.
Mobile Device Weaknesses
Mobile devices have many weaknesses. For one, they are newer and less mature than their desktop counterparts. Even laptops have decades of use in the field to expose the many points of attack that are available. Mobile devices such as pads, smartphone, and so on, have similar weakness as desktop system mostly because they are comprised of the things such as a hardware platform that an operating system installs on which then allows for applications/software to be further installed on the operating system. Mobile devices are the same in that they too are hardware platforms built for the use an operating system and application in which can be installed on it. Because of this, you will have the same weaknesses on both platforms—drivers for hardware, operating systems and applications can all be exploited.
Web Browsers
As with computer desktops, mobile devices also rely heavily on the use of Web browsers. Somewhere in between the operating system and the applications installed on it lies the Web browser. Although a core OS tool, the Web browser is nothing more than an application tightly integrated to provide the core level security functionality of the OS itself.
Apps/Web Applications
Web applications can cause serious issues if not reputable and/or come from a non-proven source. Code within the application can cause you great harm, both technically and socially. For example, there are many applications that can be installed on your mobile device that can track your behaviors. There are some that can spy on you directly and visually. Web applications need to be written securely and those that are, installed and tested. Those that are not, should be avoided at all costs. In Chapter 10 we cover how to develop secure code and develop applications responsibly for any platform.
Physical Security
The physical security of the mobile device should be of upmost concern. This is because if your device is lost or stolen, it can be used against you by the wrong party. Just recently a person in the news lost their phone and it was recovered at the hospital that they had visited. The person who found the device submitted it to their internal security department. In hopes of returning the phone the security officer decided to see if they could find the identity of the person so that they could contact them and return the phone. The device was not secured so as the security officer looked through the phone, they found a large amount of child pornography stored on the device. The mobile device was then turned over to Police. The Police in turn waited for the person who lost the device to come claim it and when they did, arrested and charged the person with a crime.
Now this is a case of someone getting what they deserved, however what if someone found your mobile device and had malicious intentions? What if it was stolen from you? Much worse could be done because in this instance, someone is intentionally trying to harm you, steal something from you, or worse. What if all of your banking information was stored on your phone including passwords to access it? What if they stole your identity?
Make sure that you keep your device secure on your person and secure the mobile device so that if it is stolen or lost, it cannot easily be broken into. Also, attempt to limit the amount of personal information you keep on it, simply be memorizing specific pieces of information such as pins and passwords.
Summary
In this chapter we covered the use of, the attacks against and the weaknesses of mobile devices. We also looked at how to secure yourself against mobile device client-side attacks. Mobile devices are any device that is connected to a network that operates from a wireless-type of connection and can be taken with the user for continued use. Today, client-side attacks have grown beyond the enterprise and home user who was tied to their computers at their desk. Now, because of the age of mobility, the network has no boundaries and because of that fact, neither do client-side attacks. The playing field has become more and more difficult to secure because of mobility. Now, just about everyone you know has a mobile device, client side attacks have grown exponentially. To secure from client-side attack, make sure understand the exploits available for your device, harden as necessary and apply the same concepts of security to a mobile device that you would to any other device, even more so since this device can more easily be lost or stolen.
In the next chapter we will look at how to develop secure code, apply advanced security to applications so that they are harder to exploit and mitigate the threat of malware such as viruses and worms.
