Chapter 6. SOHO Networks and Wireless Protocols
2.3 – Given a scenario, install and configure a basic wired/wireless SOHO network
ExamAlert
Objective 2.3 concentrates on the following concepts: router/switch functionality, access point settings, IP addressing, NIC configuration, end-user device configuration, IoT device configuration, cable/DSL modem configuration, firewall settings, QoS, and wireless settings.
To prepare you for this objective we’ll discuss how to set up a SOHO network including a SOHO router, wired connections, and wireless connections. In many cases, SOHO networking is easy, and automated—it was designed that way. However, sometimes you need to manually configure information. That’s what makes a good tech. Let’s go!
Router Setup and Wireless
Okay! Let’s talk about the setup and configuration of our SOHO router. These devices have been called a plethora of different names—router, switch, firewall, access point, or multifunction network device—because they usually incorporate all of those functions into one device. Again, for simplicity, we’ll refer to this as a router.
SOHO Router Setup
First, the router needs to be physically connected, which is very easy. It requires power from an AC outlet and a connection to the Internet, which is done with a twisted-pair patch cable using RJ45 plugs on each end; one end connects to the Internet (or WAN) port of the router, and the other end connects to the cable modem or other network interface device.
Most SOHO routers are set up to be plug-and-play, meaning that computers can be plugged in to the device’s switch ports (often four of them) and they can communicate with each other and access the Internet right out of the box. But a word of caution: Watch out for the default settings that the manufacturer gives you; they might be insecure. So, the first thing we want to do is to log in to the router so that we can make some changes. (We’ll assume that your computers are already cabled to the router.) To do this, open a browser window and type the IP address of the router. For example, different manufacturers use different default IP addresses (such as 192.168.0.1 or 192.168.1.1) or they allow a connection via a URL (such as http://routername). Check your documentation to find out what the address or link is. Sometimes the login information is very basic (for example, “admin” is the username) and there is no password or there is a very basic password (possibly the same as the username). That will depend on the age and manufacturer of the router. Newer routers usually offer more security. Again, the documentation that came with the router will tell you the defaults.
Once you have gained access to the router, the first thing you want to do is change the password to something more complex—in fact, you might be required to do it. Consider changing the username also, if possible. Next, update the firmware so that it gets the latest functionality, options, and security available. Now that the device has some basic security and is updated, it is ready to be configured.
SOHO routers normally obtain an IP address from the Internet service provider (ISP); it is dynamically assigned and is known as the WAN address. It is a public address that is visible on the Internet. The router also has a LAN address, which is a private address visible only to the computers on your network. That is the address you used to log in to the router (192.168.0.1 or 192.168.1.1, and so on) and also acts as the gateway address for the clients on your network. Figure 6.1 shows the LAN and WAN settings on a typical SOHO router.

Figure 6.1 LAN and WAN connections on a typical SOHO router
As you can see from the figure, the router’s LAN address is 192.168.0.1. This device makes use of DHCP, which can be turned on or off. When on, it automatically assigns IP addresses to most of the clients on this network starting with 192.168.0.100 and ascending from there—192.168.0.101, 192.168.0.102, and so on. The router and all of the clients are on the same local area network number (192.168.0.0) using the same subnet mask (255.255.255.0), so they can all communicate with each other. We’ll discuss IP addressing in more depth within Chapter 7, “Networked Hosts and Network Configuration.”
Note
Most people are wireless crazy nowadays, but don’t forget that these SOHO routers have a built-in switch: they normally come with four wired LAN ports typically rated for 1000BASE-T. That means that it can transmit data at 1000 Mbps (1 Gbps). The BASE applies to any speed, and it is short for baseband, meaning every computer on the network shares the same channel or frequency. The T is short for twisted pair. By default, unshielded twisted-pair cables can send data 328 feet (100 meters) before the electronic signal attenuates to such a point where it is useless.
In Figure 6.1, the WAN address is 64.121.138.225. This was obtained automatically from the ISP and allows connectivity to the ISP’s network infrastructure and out to the Internet. The subnet mask (255.255.240.0) is not a default subnet mask, so we know that subnetting (the subdividing of an IP network) has been implemented. The default gateway (64.121.128.1) is the address that our router looks for to get into (and beyond) the ISP network and out to the Internet, just as the LAN clients look for the 192.168.0.1 gateway to go beyond the LAN. Finally, the DNS server addresses (starting with 208) are on a completely different network altogether, as they usually are. These resolve domain names to IP addresses when the router tries to access a server on the Internet.
If you have one, take a look at your SOHO router and identify the LAN and WAN addresses. The numbers will often be different, but the concepts remain the same. If you don’t have a SOHO router, you can easily find an emulator of a router online—many manufacturers offer them.
ExamAlert
Understand the concept of the LAN and WAN addresses of a SOHO router. It is the basis for all routing!
In some cases, you need to use a static IP address for your WAN connection, or perhaps you need to configure a secure connection to the Internet with Point-to-Point Tunneling Protocol (PPTP) or Layer 2 Tunneling Protocol (L2TP). If that is the case, you would have to input the correct information, including IP address, subnet mask, gateway, and DNS servers (and possibly a username). This information should be provided to you by the ISP you connect to.
Access Point Settings
Let’s take a look at the actual wireless settings of a typical router. Examine Figure 6.2.
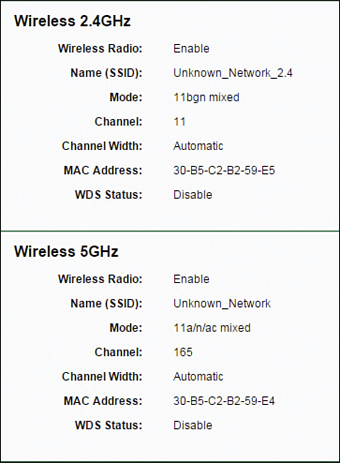
Figure 6.2 Wireless configuration on a typical SOHO router
We can see that this device is running two wireless networks: one on the 2.4-GHz frequency and one on 5 GHz. Each has its own network name, also known as a Service Set Identifier (SSID). For example, the 5-GHz network’s SSID is “Unknown_Network”. (A bit of a quirky name, but you’ll find that peculiar names are somewhat common when it comes to SSIDs.) That’s the name that users would need to know in order to make a wireless connection to the LAN. It’s currently running on channel 165. If using the 5-GHz frequency range in the United States, a wireless access point can be set up on several channels between 48 and 165. Other countries may have slightly different ranges. The wireless network shown in Figure 6.2 is currently configured to run in mixed mode, meaning that it can accept connections from wireless clients running the 802.11a, 802.11n, or 802.11ac protocols. This allows for greater compatibility. However, some organizations will require only a single type of connection for all clients (for example, 802.11ac). This can result in greater WAP efficiency and, of course, greater speed for all clients involved—but at greater expense.
The other wireless network on the 2.4-GHz frequency is set to channel 11. In the United States, the 2.4-GHz frequency range consists of channels 1 through 11. (Again, other countries may differ slightly.) For noninterference with other wireless networks, space your frequency selection apart wisely (more on that later in the “802.11 Wireless” section). This network is also running in mixed mode; it allows connections from 802.11b, 802.11g, and 802.11n (2.4 GHz) wireless clients.
ExamAlert
Know the difference between the wireless frequencies 5 GHz and 2.4 GHz and the channel ranges for each.
It’s important to encrypt the wireless connection. The accepted standard for SOHO networks (as of the writing of this book) is to use the protocols Wi-Fi Protected Access Version 2 (WPA2) and Advanced Encryption Standard (AES). We’ll discuss these protocols more as we progress through the book.
NIC and End-user Device Configuration
When configuring and analyzing the NIC, we can use several status indicators; some are hardware-based and some are software-oriented.
Note
Technicians use several terms when referring to a network card: network adapter, network interface controller (NIC), network interface card, Ethernet card, and so on. Be ready for different terminology on the exam and in the field. For this chapter, I usually refer to it as network adapter because it won’t always be in “card” format.
The first types of indicators are physical; they show up as LED lights on the network adapter itself. Different network adapters have different LED lights, but typically you have a connectivity LED and an activity LED. The connectivity LED tells you if you have a good connection to a router or switch by displaying a solid color (for example, solid green), which would mean connectivity at 1000 Mbps. However, if the connectivity LED is blinking, then you know there is an intermittent connection that should be troubleshot. The activity LED blinks when data is passing through the network adapter. The functionality of both might be combined into one LED on some network adapters.
The second group of indicators is logical and shows up in the operating system. In Windows, these indicators normally manifest themselves in the Notification Area and can be put there by Windows or by the manufacturer of the network adapter, depending on whether you let Windows install the card or you used the additional software that came with the network adapter. However, you can add a shortcut to network adapters and place them on the desktop or on the taskbar.
Let’s check out the status of a wired network connection and a wireless network connection. On a Windows system, right-click the Network icon in the Notification Area and select Open Network and Sharing Center. If wireless is your primary method of connecting to the network, you will see a wireless icon; if your primary connection is wired, you will see a little icon displaying a monitor and network cable.
In the Network and Sharing Center window, click the Change adapter settings link. This opens the Network Connections window. Double-click the desired connection to bring up its status window. This is named “Wi-Fi” for the wireless adapter or “Ethernet” (“Local Area Connection” in Windows 7) for the wired adapter. Figure 6.3 shows both types of connections.

Figure 6.3 Wireless and wired network adapter status
Note
You can change the name of the network connection. Know the different names and the default settings.
From here, we can see what our “speed” is, how long we have been connected, and how many bytes have been sent and received. For example, the Wi-Fi connection is connected at 87 Mbps, even though it is a strong signal on an 802.11ac network (you can imagine the data that flies through my airwaves). On less frequently used wireless networks—or scenarios where the computer is in close proximity to the WAP—you might see connections of up to 300 Mbps, 600 Mbps, or even 1 Gbps. As you can see, the speed indicator can be very telling about a wireless connection. If you suspect a slow wireless speed, make sure that the latest driver is installed, verify placement of the wireless antennas, check for interference, and even check for unauthorized usage of the wireless network. Consider using a Wi-Fi analyzer to investigate your wireless network and the wireless networks around you. You might find that there is some frequency and channel overlap.
In the second window in Figure 6.3, we see that the Ethernet connection has a 1-Gbps connection. Remember that these connection speeds are the maximum at which the network adapter will transfer data. In addition, to get this speed, every link in the networking chain must operate at 1 Gbps (1000 Mbps), including the network adapter, patch cables, and the SOHO router itself. If any one of those links runs at less than 1000 Mbps, the entire connection would be brought down to that lesser number.
Data Networking Terms
In the computer networking world, “speed” is also referred to as “bandwidth,” though both terms might not be quite accurate technically. If you purchase a gigabit network adapter for your computer, its maximum data transfer rate will be 1 Gbps. However, the actual data transferred is known as data throughput, which will usually be less than 1 Gbps.
Going further, most network adapters can send and receive data simultaneously, which is called full-duplex. This means that they can actually send 1 Gbps and receive 1 Gbps at the same time. Conversely, half-duplex means that the network adapter can send and receive data, but only one at a time.
IoT Device Configuration
We’ve mentioned the Internet of Things in this book already and said that just about anything that can be connected to the Internet could be considered part of the Internet of Things. More strictly speaking, technicians (and many consumers) look at the Internet of Things as a group of technology goodies found in home automation, within appliances, and as voice-activated digital assistants—devices that go beyond desktops, laptops, smartphones, and tablets. The key is that they connect to the SOHO network and ultimately to the Internet to receive updates and so that they can be controlled from a mobile device or other computing system.
IoT devices include thermostats, light switches, security cameras, door locks, refrigerators (and other appliances), and smart speakers. They connect to the Internet, and collect and exchange data. Configuration of these is usually intuitive. The important part is how they are connected to the SOHO network and how they are secured. That’s because they all connect out to the Internet, and the apps that control them may or may not have the most brilliant programming, and then—security vulnerabilities abound!
A great method for configuring and securing these devices is to do the following:
Update the firmware on the SOHO router.
Create a separate network.
One good method is to use the guest network. Place the IoT devices on that network. Configure strong encryption; for example, WPA2 and AES, with a separate passcode from the main wireless networks.
Disable UPnP.
Universal Plug and Play can make a user’s life easier as far as discovery, but can create security vulnerabilities if it is running.
Update the firmware on the IoT devices.
Use strong passwords.
Different passwords should be used for the main login to the SOHO router, the guest wireless network, and the IoT devices themselves. If the IoT device only has the option for a PIN, use it. While there are only 10,000 possible combinations in a four-digit PIN, it’s still better than nothing.
Update the operating system.
Update the OS on the mobile device or other computer that will be used to configure and control the IoT devices.
Update the app used to control the IoT devices.
Use only what you need.
Use only the devices that are absolutely necessary and disconnect or turn them off when not needed.
Carefully select and monitor cloud-based connections.
If your device relies on the cloud for control, then be very careful with the manufacturer you select, and the information that you give, as well as the actual connectivity made to the device. Every connection into your network increases the attack surface and creates new vulnerabilities.
Cable/DSL Modem Configuration
When it comes to cable and DSL modems, configuration is usually performed by the ISP. They can remotely connect to your modem and reconfigure and/or reset it. However, as a consumer there are a couple of things you should know. The first is how to connect the devices physically.
Cable modems have two important ports: a coaxial port and a twisted-pair port. The coaxial port is the same that is used for CATV—it accepts an RG-6 coaxial cable with a screw-on F-connector on the end. The other end of that coaxial patch cable connects to the wall jack (or similar device) and ultimately goes to your ISP. The twisted-pair port accepts an Ethernet patch cable with an RJ45 plug on the end. The other end of that connects to your router. There are also all-in-one devices that act as a cable modem and a router and have a four-port switch incorporated into the device. For configuration of those included router options, see the earlier sections of this chapter.
A DSL modem has the same twisted-pair port for connectivity to a router, but some also have an RJ11 port for use with a land-based phone line.
Firewall Settings and Additional Configurations
Most SOHO routers have a built-in firewall with some basic security functionality. Let’s discuss a few of the common features you might find.
▸ NAT: Network address translation is the process of modifying IP addresses as information crosses a router. It hides an entire IP address space on the LAN (for example, 192.168.0.1 through 192.168.0.255). Whenever an IP address on the LAN wants to communicate with the Internet, the IP is converted to the public IP of the router (for example, 68.54.127.95) but it will be whatever IP address was assigned to the router by the ISP. This way, it looks like the router is the only device making the connection to remote computers on the Internet, providing a modicum of safety for the computers on the LAN. NAT also allows a single IP to do the work for many IP addresses in the LAN.
▸ Port forwarding: This forwards an external network port to an internal IP address and port. This enables you to have a web server, FTP server, and other servers, but you need to have only one port for each open on the WAN side of the router. It can be any port you like; of course, you would need to tell people which port they need to connect to if it is not a standard one. Some devices use what are called virtual servers, making the process a lot more user-friendly. So, for example, you might have an FTP server running internally on your LAN; its IP address and port might be 192.168.0.100:21 (notice how the colon separates the IP address from the port), but you would have users on the Internet connect to your router’s WAN address (for example, 65.43.18.1) and any port you want. The router takes care of the rest, and the forwarding won’t be noticed by the typical user. Port forwarding is also referred to as destination NAT (DNAT).
▸ DMZ: A demilitarized zone is an area that is not quite on the Internet and not quite part of your LAN. It’s a sort of middle ground that is for the most part protected by a firewall, but particular traffic will be let through. It’s a good place for web servers, e-mail servers, and FTP servers because these are services required by users on the Internet. The beauty of this is that the users will not have access to your LAN—if it is configured correctly, of course. Quite often, the DMZ is set up as the third leg of a firewall. The first leg connects to the LAN, the second leg connects to the Internet, and the third connects to the DMZ. You need to know the ports that your servers will use and create rules within the firewall (or an all-in-one device, such as a SOHO router) to allow only the required traffic into the DMZ.
▸ UPnP: Universal Plug and Play is a group of networking protocols that allows computers, printers, and other Internet-ready devices to discover each other on the network. It is a consumer-level technology designed to make networking easier for the user. For example, if you wanted easier accessibility and connectivity of a PC, a smartphone, and a printer that were all connected to the SOHO router, UPnP can provide that. However, it is often recommended to disable this function if you are concerned about security.
▸ MAC filtering: MAC filtering is the screening of computers that are allowed access to a device or network. Every computer, wired or wireless, gets a unique MAC address. It is difficult to change or mask, so it makes for a good address to screen out unwanted connections. And because the switch portion of a SOHO router sees the MAC addresses of the computers connected to it, it’s the perfect place to incorporate filtering. Generally, MAC filtering—which might also be referred to as Access Control or something similar—is disabled by default, but if you were to enable it, you would have two options. First, you could specify a list of computers with allowed MAC addresses, also known as a whitelist. Second, you could specify the computers that are denied access, also known as a blacklist. Whatever you choose, it’s the MAC address that is used to determine connectivity and access control. For ease of use, SOHO routers will often display the computers that are currently connected, including information such as the device name, connection type (wired or wireless), IP address, and of course, the MAC address.
Note
To find out the MAC address of a system, go to the command line and run the appropriate command, which, for example, is ipconfig /all in Windows.
ExamAlert
Understand that MAC filtering is also known as Access Control on some SOHO routers, and that filtering is broken down into accepted MAC addresses (whitelisting) and denied MAC addresses (blacklisting).
▸ QoS: Quality of service is a feature that attempts to prioritize data for specific computers or for specific programs. It could be that you want to prioritize certain types of data, such as Remote Desktop Protocol (RDP) traffic, streaming media, Voice over IP (VoIP) phone calls, gaming, or audio or video playback. Or, perhaps a user wants a gaming PC or a smartphone to have a higher priority in general. QoS allows a user to do both of these things. Figure 6.4 shows an example of QoS configured on a basic SOHO router. One computer has been given high-priority access to the router. Also, an application (FTP) has been given low priority for all systems connected. Most SOHO routers have a QoS database that can be updated to include newer types of applications. However, if the application is not listed, then there is usually an option to add a custom application by using its port number.
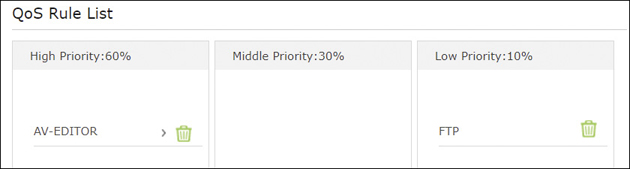
Figure 6.4 Example QoS configuration
Configuring Wireless Encryption
SOHO routers (as well as most operating systems) support wireless networking protocols such as WPA2 and encryption methods such as AES to provide data confidentiality. Figure 6.5 displays a common secure wireless encryption technique on a typical router. Table 6.1 shows the characteristics of the various wireless protocols and encryption methods.

Figure 6.5 Wireless network settings on a common router
Table 6.1 Wireless Encryption Methods
Wireless Protocol |
Description |
Encryption Level |
|---|---|---|
WEP |
Wired Equivalent Privacy Deprecated and vulnerable to attacks |
64-bit |
WPA |
Wi-Fi Protected Access |
128-bit |
WPA2 |
Wi-Fi Protected Access Version 2 |
256-bit |
TKIP |
Temporal Key Integrity Protocol Deprecated encryption protocol used with WEP or WPA |
128-bit |
AES |
Advanced Encryption Standard Encryption protocol used with WPA/WPA2 Strongest encryption method in this table |
128-, 192-, and 256-bit |
Figure 6.5 shows a router that is using WPA2 only and AES as the encryption protocol. It also has a 16-character key for accessing the wireless network. Aside from using external servers for authentication, this is the best method on this router (and similar routers as well). This is the best line of defense against war drivers—attackers who attempt to gain access to unprotected wireless networks from their vehicles.
ExamAlert
As of the writing of this book, the best SOHO wireless encryption is WPA2 and AES. But be on the lookout for new and better versions and protocols!
WEP is the weakest type of encryption; WPA is stronger, and WPA2 is the strongest of the three. However, it is better to have WEP as opposed to nothing. If this is the case, use encryption keys that are difficult to guess and consider changing those keys often. Some devices can be updated to support WPA, whether it is through a firmware upgrade or through the use of a software add-on.
Final Word
When all configuration is complete, we need to place our SOHO router. It is important to keep the device away from any electrical sources (such as outlets, uninterruptible power supplies, or microwaves) and any large amounts of metal to avoid electromagnetic interference (EMI). The basement is probably not the best place for a router due to the thick walls, copper pipes, and electrical panels causing wireless interference. The device should be placed in the physical center of the office or the home for best reception. The more centralized the router is, the better the wireless access your computers will get. The antennas should be either at a 90-degree angle from each other or pointing toward where the computers are. And that pretty much wraps up the basic configuration of a SOHO router.
Cram Quiz
Answer these questions. The answers follow the last question. If you cannot answer these questions correctly, consider reading this section again until you can.
1. Which of the following allows for network throttling of individual computers or applications?
![]() A. QoS
A. QoS
![]() B. Port forwarding
B. Port forwarding
![]() C. DMZ
C. DMZ
![]() D. DHCP
D. DHCP
2. Which of the following forwards an external network port to an internal IP address/port on a computer on the LAN?
![]() A. NAT
A. NAT
![]() B. Port forwarding
B. Port forwarding
![]() C. DMZ
C. DMZ
![]() D. DHCP
D. DHCP
3. Which of the following is described as the simultaneous sending and receiving of network data?
![]() A. Half-duplex
A. Half-duplex
![]() B. Latency
B. Latency
![]() C. PoE
C. PoE
![]() D. Full-duplex
D. Full-duplex
Cram Quiz Answers
1. A. Quality of service (QoS) is a technology used in SOHO routers that can throttle bandwidth and give higher priority to individual computers or applications. Port forwarding is used to forward outside network ports to internal IP addresses. A demilitarized zone (DMZ) is a protected area between the LAN and the Internet—often inhabited by company servers. The Dynamic Host Configuration Protocol (DHCP) is the protocol in charge of automatically handing out IP address information to clients.
2. B. Port forwarding is used to forward external network ports to an internal IP and port. This is done so a person can host services such as FTP internally. Network address translation (NAT) is used by most routers to convert the internal network of IP addresses to the single public IP address used by the router. The demilitarized zone (DMZ) is an area that is protected by the firewall but separate from the LAN. Servers are often placed here. DHCP is the protocol that governs the automatic assignment of IP addresses to clients by a server.
3. D. Full-duplex is when a network adapter (or other device) can send and receive information at the same time. Half-duplex is when only sending or receiving can be done at one time. Latency is the delay it takes for data to reach a computer from a remote location. PoE is Power over Ethernet, a technology that allows devices to receive data and power over an Ethernet network cable.
2.4 – Compare and contrast wireless networking protocols
ExamAlert
Objective 2.4 focuses on the following concepts: 802.11 protocols (a, b, g, n, and ac), frequencies, channels, Bluetooth, NFC, RFID, Zigbee, Z-Wave, 3G, 4G, 5G, and LTE.
In this section we’ll discuss the IEEE 802.11 wireless protocols, and some other wireless standards available for cellular connections and for home automation. Bluetooth, NFC, and cellular protocols are also listed in the CompTIA objective, but we covered them previously in Chapters 3 and 4—make sure you know them. Let’s go!
802.11 Wireless
To standardize wireless LAN (WLAN) communications—also known as Wi-Fi—the Institute of Electrical and Electronics Engineers (IEEE) developed the 802.11 series of protocols. These define the various speeds, frequencies, and protocols used to transmit data over radio waves in small geographic areas using unlicensed spectrums.
There are several different 802.11 derivatives you need to know for the exam: 802.11a, 802.11b, 802.11g, 802.11n, and 802.11ac. Table 6.2 shows these technologies and the characteristics that differentiate them.
Table 6.2 802.11 Standards
802.11 Version |
Maximum Data Rate |
Frequency |
|---|---|---|
802.11a |
54 Mbps |
5 GHz |
802.11b |
11 Mbps |
2.4 GHz |
802.11g |
54 Mbps |
2.4 GHz |
802.11n |
300/600 Mbps |
5 and/or 2.4 GHz |
802.11ac |
1.7 Gbps |
5 GHz |
ExamAlert
Know the data rates, and frequencies used, for each of the 802.11 versions!
One thing I left out of the table is coverage or distance. It is difficult to put an exact number on the maximum wireless transmission distances for each standard because it depends on the signal strength of the WAP’s antenna, the use of additional features, and environmental factors such as obstructions and interference. But generally, the wireless range from WAP to client increases with each standard listed in the table, with 802.11n and 802.11ac providing similar ranges.
Note
New technologies are being developed as of the writing of this book that use higher frequency ranges and can transmit much more data per second. For example, 802.11ad runs at 60 GHz and can transfer multiple gigabits of data per second. Always be on the alert for emerging networking technologies!
The data transfer rates of newer wireless network technologies are increased using a concept known as multipath propagation. This is when an antenna (or antennas) receives radio signals on two or more paths. A common example of this is multiple-input and multiple-output (MIMO) technology, which is incorporated into 802.11n and 802.11ac wireless networks (as well as 4G LTE). As of the writing of this book, typical 802.11ac wireless devices use three or four antennas; the 802.11ac standard complies with multiuser MIMO (or MU-MIMO), which can have four simultaneous downlinks.
Depending on the frequency used, there are different channels that can be utilized by the average home or company. We touched on these previously, but let’s summarize them in Table 6.3, and then expand on the concept.
Table 6.3 2.4 GHz and 5 GHz Channels
Frequency |
Typical Channels |
Example |
|---|---|---|
2.4 GHz |
1 through 11 |
802.11g |
5 GHz |
36, 40, 44, 48, 149, 153, 157, 161, 165 |
802.11ac |
Let’s take it to the next level. More accurately, 2.4 GHz and 5 GHz are frequency ranges. The exact range for these will vary from one country to the next. For example, the range for 2.4-GHz Wi-Fi in the United States is between 2.412 GHz and 2.462 GHz, broken up as channels 1 through 11—each is spaced 5 MHz apart from the next. When you set up a 2.4-GHz Wi-Fi network, it will have a channel width associated with it. By default, this is often 20 MHz—an amount that spans multiple channels. That’s why I usually recommend placing wireless networks (and access points) on separate channels that are distant from each other. In the United States, the 2.4-GHz non-overlapping channels are 1, 6, and 11. For example, one Wi-Fi network could be on Channel 1 (2.412 GHz) and the next could be on Channel 6 (2.437 GHz), which allows for 25 MHz of space—more than enough in most cases to avoid interference.
However, to increase data rates, you can increase the channel width on many routers to 40 MHz for 2.4-GHz networks, and up to 80 MHz for 5-GHz networks. This is known as channel bonding. As you can guess, the chance for interference increases as well, so this notion can be risky. If we used 40-MHz channel bonding with our previous example, we would have interference from one Wi-Fi network to the next. Channel 6 is too close to channel 1 in this case. We would need to go to at least channel 9 (2.452 GHz) to avoid overlapping of the two Wi-Fi networks. The same goes for 5-GHz Wi-Fi networks. For example, channel 36’s center frequency is actually 5.180 GHz. Channel 40 is 5.200 GHz. That is 20 MHz of channel width. If we wanted a separate Wi-Fi network on each of those channels, it would work fine by default, but if we wanted to perform channel bonding, then we would have to select another channel, such as channel 149 (5.755 GHz), which would allow for 40- or 80-MHz channel bonding, and possibly, higher data rates.
But air is free, right? So, we should perform a wireless site survey, and identify other companies’ and homes’ Wi-Fi networks that are nearby. They could be using channels that are too close, and cause interference. A Wi-Fi analyzer program is the best way to go when it comes to seeing who is using which frequencies, and then selecting frequencies that we can use (even with channel bonding) without causing overlap and interference. There are vendors that develop these programs for Windows, Android, and iOS. A Wi-Fi analyzer makes it easier for a person to discern where Wi-Fi networks exist in a given frequency range by showing the information in a graphical format, a chart, or something similar. It will also show the strength of the signal of each network. All of this can help you to decide on the right channel to use when you are performing your wireless site survey.
ExamAlert
Don’t stand so close to me! Seriously, make sure your selected Wi-Fi channel is in its own “space” by investigating the airwaves with a Wi-Fi analyzer.
RFID
Radio-frequency identification (RFID) is a wireless technology used to read information that is stored on “tags.” These tags can be attached to, or embedded in, just about anything. They are used in many industries and have many uses such as access control, commerce, advertising, manufacturing, agriculture, and so on.
For example, RFID tags can be used in a retail store. They can help with the tracking of inventory, and protection from theft. Tags are attached to clothing or other items, and are read by an RFID reader as part of the checkout process. After a customer pays for the item, the RFID reader deactivates that tag. In the case that a customer fails to pay for the item, an RFID detector can be placed at the entrance/exit. This will read the tag and send an alert. These readers and detectors must be nearby, but not necessarily within line-of-sight, which improves upon a basic barcode system. Plus, the RFID tag can hold a lot more information and can be programmed if necessary. For readers that can track items over larger distances, beyond close proximity, an active RFID system would be necessary, where the reader is AC powered.
When it comes to computers, networks, and authentication, RFID plays a vital role. For instance, as part of an access control solution, RFID tags are used as ID badges—proximity cards, dongles, and so forth—which can take the place of older and less secure magnetic stripe cards. Entrances to the building, specific offices, server rooms, data centers, and so on, can be equipped with an RFID reader. Simply placing the RFID badge on or near the reader will activate the reader and verify the ID of the employee. Of course, badges can be stolen; that’s why a second factor of authentication is common, such as a passcode, which we will discuss in the security chapters. RFID is also present in smartphones and some other computing devices. Many smartphones are furnished with NFC, which is actually a subset of RFID. These readers are often locked down so that they can only read tags from a certain manufacturer, or for a specific purpose. Refer to Chapter 3, “Smartphones, Tablets, and Other Mobile Devices, Part 1,” if you need a refresher on NFC.
Zigbee and Z-Wave
Zigbee and Z-Wave are two wireless protocols used primarily with home automation products, appliances, and voice-activated assistants. They each allow for communication between hundreds of different devices from different manufacturers. Generally, the two are incompatible, but there are hubs that can be used that will support both protocols. Smartphone apps are available to control the various Zigbee and Z-Wave devices and hubs that connect them together.
Zigbee is standardized as IEEE 802.15-4. It is a low-power wireless technology that is similar to Bluetooth as far as frequency, transmission power, and distance. For example, it runs on 2.4 GHz as well as 915 MHz for Zigbee Pro and typically has a communications distance of 10 to 20 meters maximum. However, it is designed and manufactured in such a way that Zigbee products can be cheaper than Bluetooth and Wi-Fi equivalents. Also, it has a unified data communications methodology that BT and Wi-Fi do not, allowing for more configurability, greater control, and better communications between devices. Zigbee-based devices have low power consumption, which increases their battery life tremendously compared to Wi-Fi and BT devices. You might find Zigbee modules in sensors that can control lighting, temperature, window blinds, and much more, including home entertainment control, industrial control, medical data collection, smoke and fire alarms, and safety and security in general.
Z-Wave is a protocol that is standardized by the Z-Wave Alliance and works within the 800- and 900-MHz frequencies. As with Zigbee, you might find Z-Wave modules in security systems, lighting control devices, thermostats, and so on. As of the writing of this book, Z-Wave has a longer transmission distance than Zigbee and is very common in the realm of home automation. However, protocol choice also depends on the manufacturer of the device, the exact purpose for the device, and cost. Some homes and offices use both Zigbee and Z-Wave because many devices only use one or the other. To control either Z-Wave or Zigbee devices, a smart hub is required that has support for one or both of the protocols. As with any wireless devices, security is a concern. Devices that use Zigbee or Z-Wave utilize 128-bit encrypting technologies— check and make sure that this is enabled. Also, make use of any PINs or passcodes available on devices.
ExamAlert
Remember that Zigbee and Z-Wave technologies transmit data on different frequencies.
Note
Chapter 4 discusses cellular (or WWAN) connections such as 3G, 4G, LTE, and 5G.
And that closes out this section on the electromagnetic spectrum. Transmission of data over radio waves can be done in so many ways. Be sure to know the basics of each technology we discussed in this chapter.
Cram Quiz
Answer these questions. The answers follow the last question. If you cannot answer these questions correctly, consider reading this section again until you can.
1. Which of the following would a company most likely use for authentication to a server room?
![]() A. 802.11ac
A. 802.11ac
![]() B. 802.15-4
B. 802.15-4
![]() C. RFID
C. RFID
![]() D. Z-Wave
D. Z-Wave
![]() E. MIMO
E. MIMO
2. Which standard can attain a data transfer rate of 1 Gbps over a wireless connection?
![]() A. 802.11a
A. 802.11a
![]() B. 802.11b
B. 802.11b
![]() C. 802.11g
C. 802.11g
![]() D. 802.11ac
D. 802.11ac
![]() E. 802.3ab
E. 802.3ab
3. Which of the following is often broken down into groups of channels including 1-5, 6–10, and 11?
![]() A. 802.11ac
A. 802.11ac
![]() B. 2.4 GHz
B. 2.4 GHz
![]() C. 5 GHz
C. 5 GHz
![]() D. 802.11a
D. 802.11a
Cram Quiz Answers
1. C. RFID (radio-frequency identification) is commonly used for access to areas of a building such as a server room. It is often implemented as a proximity-based ID card or badge. The other options are not usually associated with authentication. 802.11ac is a WLAN (Wi-Fi) standard that runs on 5 GHz and can provide 1 Gbps of data transfer. 802.15-4 is the IEEE standard for Zigbee. Z-Wave, like Zigbee, is a home automation and wireless sensor control technology. MIMO (multiple-input and multiple-output) is a multiple propagation technology used to increase data transfer in 802.11n and 802.11ac wireless networks.
2. D. 802.11ac can attain speeds in excess of 1 Gbps over wireless. 802.11a and g have a typical maximum of 54 Mbps. 802.11b (rarely used today) has a maximum of 11 Mbps. 802.3ab is the IEEE specification for 1-Gbps transfer over twisted-pair cables—it is wired, not wireless. By the way, this is also known as 1000BASE-T.
3. B. In the United States, the 2.4-GHz frequency range is broken down into three categories: Channel 1–5, 6–10, and 11. By placing separate wireless networks on separate distant channels (such as 1 and 11), you can avoid overlapping and interference. 802.11ac and 802.11a are standards, not frequencies. 5 GHz uses channels such as 36, 40, 149, 153, and so on.
You are doing fantastic! Great job with the chapter. Keep going, there’s lots more!
