Chapter 2
Domain 2.0: Vulnerability Management
- During the reconnaissance stage of a penetration test, Cynthia needs to gather information about the target organization's network infrastructure without causing an IPS to alert the target to her information gathering. Which of the following is her best option?
- Perform a DNS brute-force attack.
- Use an Nmap ping sweep.
- Perform a DNS zone transfer.
- Use an Nmap stealth scan.
- A port scan of a remote system shows that port 3306 is open on a remote database server. What database is the server most likely running?
- Oracle
- Postgres
- MySQL
- Microsoft SQL
- During a port scan of her network, Cynthia discovers a workstation that shows the following ports open. What should her next action be?

- Determine the reason for the ports being open.
- Investigate the potentially compromised workstation.
- Run a vulnerability scan to identify vulnerable services.
- Reenable the workstation's local host firewall.
- Which one of the following threats is the most pervasive in modern computing environments?
- Zero-day attacks
- Advanced persistent threats
- Malware
- Insider threats
- Nara is concerned about the risk of attackers conducting a brute-force attack against her organization. Which one of the following factors is Nara most likely to be able to control?
- Attack vector
- Adversary capability
- Likelihood
- Total attack surface
- What is the default Nmap scan type when Nmap is not provided with a scan type flag?
- A TCP FIN scan
- A TCP connect scan
- A TCP SYN scan
- A UDP scan
- Lakshman wants to limit what potential attackers can gather during passive or semipassive reconnaissance activities. Which of the following actions will typically most reduce his organization's footprint?
- Limit information available via the organizational website without authentication.
- Use a secure domain registration.
- Limit technology references in job postings.
- Purge all document metadata before posting.
- Cassandra's Nmap scan of an open wireless network (192.168.10/24) shows the following host at IP address 192.168.1.1. Which of the following is most likely to be the type of system at that IP address based on the scan results shown?

- A virtual machine
- A wireless router
- A broadband router
- A print server
- Several organizations recently experienced security incidents when their AWS secret keys were published in public GitHub repositories. What is the most significant threat that could arise from this improper key management?
- Total loss of confidentiality
- Total loss of integrity
- Total loss of availability
- Total loss of confidentiality, integrity, and availability
- After Kristen received a copy of an Nmap scan run by a penetration tester that her company hired, she knows that the tester used the
-Oflag. What type of information should she expect to see included in the output other than open ports?- OCMP status
- Other ports
- Objective port assessment data in verbose mode
- Operating system and Common Platform Enumeration (CPE) data
- Andrea wants to conduct a passive footprinting exercise against a target company. Which of the following techniques is not suited to a passive footprinting process?
- WHOIS lookups
- Banner grabbing
- BGP looking glass usage
- Registrar checks
- Alex wants to scan a protected network and has gained access to a system that can communicate to both his scanning system and the internal network, as shown in the image here. What type of Nmap scan should Alex conduct to leverage this host if he cannot install Nmap on system A?

- A reflection scan
- A proxy scan
- A randomized host scan
- A ping-through scan
- Maddox is conducting an inventory of access permissions on cloud-based object buckets, such as those provided by the AWS S3 service. What threat is he seeking to mitigate?
- Insecure APIs
- Improper key management
- Unprotected storage
- Insufficient logging and monitoring
- Alex has been asked to assess the likelihood of reconnaissance activities against her organization (a small, regional business). Her first assignment is to determine the likelihood of port scans against systems in her organization's screened subnet (otherwise known as a DMZ). How should she rate the likelihood of this occurring?
- Low.
- Medium.
- High.
- There is not enough information for Alex to provide a rating.
- Lucy recently detected a cross-site scripting (XSS) vulnerability in her organization's web server. The organization operates a support forum where users can enter HTML tags and the resulting code is displayed to other site visitors. What type of cross-site scripting vulnerability did Lucy discover?
- Persistent
- Reflected
- DOM-based
- Blind
- Florian discovered a vulnerability in a proprietary application developed by his organization. The application has a flaw that allows users to log into the system by providing a valid username and leaving the password blank. What term best describes this overflow?
- Directory traversal
- Stack overflow
- Injection flaw
- Broken access control
- The company that Dan works for has recently migrated to an SaaS provider for its enterprise resource planning (ERP) software. In its traditional on-site ERP environment, Dan conducted regular port scans to help with security validation for the systems. What will Dan most likely have to do in this new environment?
- Use a different scanning tool.
- Rely on vendor testing and audits.
- Engage a third-party tester.
- Use a VPN to scan inside the vendor's security perimeter.
- Which one of the following languages is least susceptible to an injection attack?
- HTML
- SQL
- STIX
- XML
- Which one of the following types of malware would be most useful in a privilege escalation attack?
- Rootkit
- Worm
- Virus
- RAT
- Abdul is conducting a security audit of a multicloud computing environment that incorporates resources from AWS and Microsoft Azure. Which one of the following tools will be least useful to him?
- ScoutSuite
- Pacu
- Prowler
- CloudSploit
- Greg is concerned about the use of DDoS attack tools against his organization, so he purchased a mitigation service from his ISP. What portion of the threat model did Greg reduce?
- Likelihood
- Total attack surface
- Impact
- Adversary capability
- Carrie needs to lock down a Windows workstation that has recently been scanned using Nmap with the results shown here. She knows that the workstation needs to access websites and that the system is part of a Windows domain. What ports should she allow through the system's firewall for externally initiated connections?

- 80, 135, 139, and 445.
- 80, 445, and 3389.
- 135, 139, and 445.
- No ports should be open.
- Adam's port scan returns results on six TCP ports: 22, 80, 443, 515, 631, and 9100. If Adam needs to guess what type of device this is based on these ports, what is his best guess?
- A web server
- An FTP server
- A printer
- A proxy server
- In his role as the SOC operator, Manish regularly scans a variety of servers in his organization. After two months of reporting multiple vulnerabilities on a Windows file server, Manish recently escalated the issue to the server administrator's manager.
At the next weekly scan window, Manish noticed that all the vulnerabilities were no longer active; however, ports 137, 139, and 445 were still showing as open. What most likely happened?
- The server administrator blocked the scanner with a firewall.
- The server was patched.
- The vulnerability plug-ins were updated and no longer report false positives.
- The system was offline.
- While conducting reconnaissance, Piper discovers what she believes is an SMTP service running on an alternate port. What technique should she use to manually validate her guess?
- Send an email via the open port.
- Send an SMTP probe.
- Telnet to the port.
- SSH to the port.
Use the following network diagram and scenario to answer questions 26–28.
Marta is a security analyst who has been tasked with performing Nmap scans of her organization's network. She is a new hire and has been given this logical diagram of the organization's network but has not been provided with any additional detail.

- Marta wants to determine what IP addresses to scan from location A. How can she find this information?
- Scan the organization's web server and then scan the other 255 IP addresses in its subnet.
- Query DNS and WHOIS to find her organization's registered hosts.
- Contact ICANN to request the data.
- Use
tracerouteto identify the network that the organization's domain resides in.
- If Marta runs a scan from location B that targets the servers on the datacenter network and then runs a scan from location C, what differences is she most likely to see between the scans?
- The scans will match.
- Scans from location C will show no open ports.
- Scans from location C will show fewer open ports.
- Scans from location C will show more open ports.
- Marta wants to perform regular scans of the entire organizational network but only has a budget that supports buying hardware for a single scanner. Where should she place her scanner to have the most visibility and impact?
- Location A
- Location B
- Location C
- Location D
- Chris wants to gather as much information as he can about an organization using DNS harvesting techniques. Which of the following methods will easily provide the most useful information if they are all possible to conduct on the network he is targeting?
- DNS record enumeration
- Zone transfer
- Reverse lookup
- Domain brute-forcing
- Geoff wants to perform passive reconnaissance as part of an evaluation of his organization's security controls. Which of the following techniques is a valid technique to perform as part of a passive DNS assessment?
- A DNS forward or reverse lookup
- A zone transfer
- A WHOIS query
- Using maltego
- Mike's penetration test requires him to use passive mapping techniques to discover network topology. Which of the following tools is best suited to that task?
- Wireshark
nmapnetcat- Angry IP Scanner
- When Scott performs an
nmapscan with the-Tflag set to 5, what variable is he changing?- How fast the scan runs
- The TCP timeout flag it will set
- How many retries it will perform
- How long the scan will take to start up
- While application vulnerability scanning one of her target organizations web servers, Andrea notices that the server's hostname is resolving to a
cloudflare.comhost. What does Andrea know about her scan?- It is being treated like a DDoS attack.
- It is scanning a CDN-hosted copy of the site.
- It will not return useful information.
- She cannot determine anything about the site based on this information.
- Part of Tracy's penetration testing assignment is to evaluate the WPA3 Enterprise protected wireless networks of her target organization. What major differences exist between reconnaissances of a wired network versus a wireless network?
- Encryption and physical accessibility
- Network access control and encryption
- Port security and physical accessibility
- Authentication and encryption
- Ian's company has an internal policy requiring that they perform regular port scans of all of their servers. Ian has been part of a recent effort to move his organization's servers to an infrastructure as a service (IaaS) provider. What change will Ian most likely need to make to his scanning efforts?
- Change scanning software.
- Follow the service provider's scan policies.
- Sign a security contract with the provider.
- Discontinue port scanning.
- Lauren wants to identify all the printers on the subnets she is scanning with
nmap. Which of the followingnmapcommands will not provide her with a list of likely printers?nmap -sS -p 9100,515,631 10.0.10.15/22 -oX printers.txtnmap -O 10.0.10.15/22 -oG - | grep printer >> printers.txtnmap -sU -p 9100,515,631 10.0.10.15/22 -oX printers.txtnmap -sS -O 10.0.10.15/22 -oG | grep >> printers.txt
- What services will the following
nmapscan test for?nmap -sV -p 22,25,53,389 192.168.2.50/27- Telnet, SMTP, DHCP, MS-SQL
- SSH, SMTP, DNS, LDAP
- Telnet, SNMP, DNS, LDAP
- SSH, SNMP, DNS, RDP
- While conducting a topology scan of a remote web server, Susan notes that the IP addresses returned for the same DNS entry change over time. What has she likely encountered?
- A route change
- Fast-flux DNS
- A load balancer
- An IP mismatch
- Nihar wants to conduct an
nmapscan of a firewalled subnet. Which of the following is not annmapfirewall evasion technique he could use?- Fragmenting packets
- Changing packet header flags
- Spoofing the source IP
- Appending random data
- When Casey scanned a network host, she received the results shown here. What does she know based on the scan results?

- The device is a Cisco device.
- The device is running Red Hat Linux.
- The device was built by IBM.
- None of the above.
- Aidan operates the point-of-sale network for a company that accepts credit cards and is thus required to be compliant with PCI DSS. During his regular assessment of the point-of-sale terminals, he discovers that a recent Windows operating system vulnerability exists on all of them. Since they are all embedded systems that require a manufacturer update, he knows that he cannot install the available patch. What is Aidan's best option to stay compliant with PCI DSS and protect his vulnerable systems?
- Replace the Windows embedded point-of-sale terminals with standard Windows systems.
- Build a custom operating system image that includes the patch.
- Identify, implement, and document compensating controls.
- Remove the POS terminals from the network until the vendor releases a patch.
- What occurs when Mia uses the following command to perform an
nmapscan of a network?nmap -sP 192.168.2.0/24- A secure port scan of all hosts in the 192.168.0.0 to 192.168.2.255 network range
- A scan of all hosts that respond to ping in the 192.168.0.0 to 192.168.255.255 network range
- A scan of all hosts that respond to ping in the 192.168.2.0 to 192.168.2.255 network range
- A SYN-based port scan of all hosts in the 192.168.2.0 to 192.168.2.255 network range
- Amir's remote scans of a target organization's class C network block using the
nmapcommand (nmap -sS 10.0.10.1/24) show only a single web server. If Amir needs to gather additional reconnaissance information about the organization's network, which of the following scanning techniques is most likely to provide additional detail?- Use a UDP scan.
- Perform a scan from on-site.
- Scan using the
-p 1-65535flag. - Use Nmap's IPS evasion techniques.
- Damian wants to limit the ability of attackers to conduct passive fingerprinting exercises on his network. Which of the following practices will help to mitigate this risk?
- Implement an IPS.
- Implement a firewall.
- Disable promiscuous mode for NICs.
- Enable promiscuous mode for NICs.
- As part of his active reconnaissance activities, Frank is provided with a shell account accessible via SSH. If Frank wants to run a default
nmapscan on the network behind the firewall shown here, how can he accomplish this?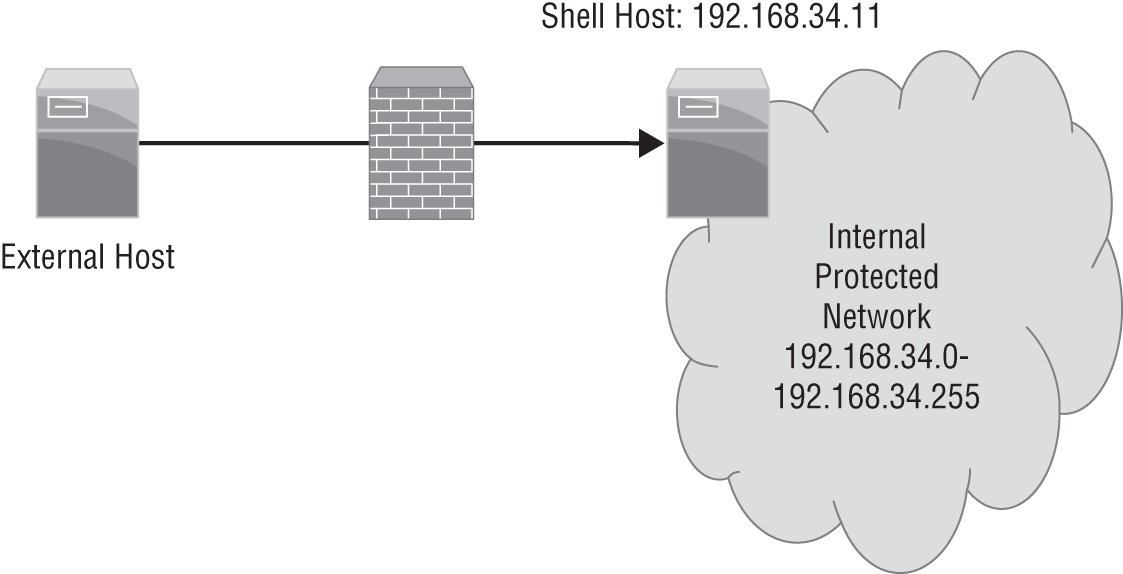
ssh -t 192.168.34.11 nmap 192.168.34.0/24ssh -R 8080:192.168.34.11:8080 [remote account:remote password]ssh -proxy 192.168.11 [remote account:remote password]- Frank cannot scan multiple ports with a single
sshcommand.
- Angela captured the following packets during a reconnaissance effort run by her organization's red team. What type of information are they looking for?

- Vulnerable web applications
- SQL injection
- Directory traversal attacks
- Passwords
- Stacey encountered a system that shows as “filtered” and “firewalled” during an
nmapscan. Which of the following techniques should she not consider as she is planning her next scan?- Packet fragmentation
- Spoofing the source address
- Using decoy scans
- Spoofing the destination address
- Kim is preparing to deploy a new vulnerability scanner and wants to ensure that she can get the most accurate view of configuration issues on laptops belonging to traveling salespeople. Which technology will work best in this situation?
- Agent-based scanning
- Server-based scanning
- Passive network monitoring
- Noncredentialed scanning
- Carla runs a vulnerability scan of a new appliance that engineers are planning to place on her organization's network and finds the results shown here. Of the actions listed, which would correct the highest criticality vulnerability?

- Block the use of TLS v1.0.
- Replace the expired SSL certificate.
- Remove the load balancer.
- Correct the information leakage vulnerability.
- Sadiq is responsible for the security of a network used to control systems within his organization's manufacturing plant. The network connects manufacturing equipment, sensors, and controllers. He runs a vulnerability scan on this network and discovers that several of the controllers are running out-of-date firmware that introduces security issues. The manufacturer of the controllers is out of business. What action can Sadiq take to best remediate this vulnerability in an efficient manner?
- Develop a firmware update internally and apply it to the controllers.
- Post on an Internet message board seeking other organizations that have developed a patch.
- Ensure that the ICS is on an isolated network.
- Use an intrusion prevention system on the ICS network.
- Vic scanned a Windows server used in his organization and found the result shown here. The server is on an internal network with access limited to IT staff and is not part of a domain. How urgently should Vic remediate this vulnerability?
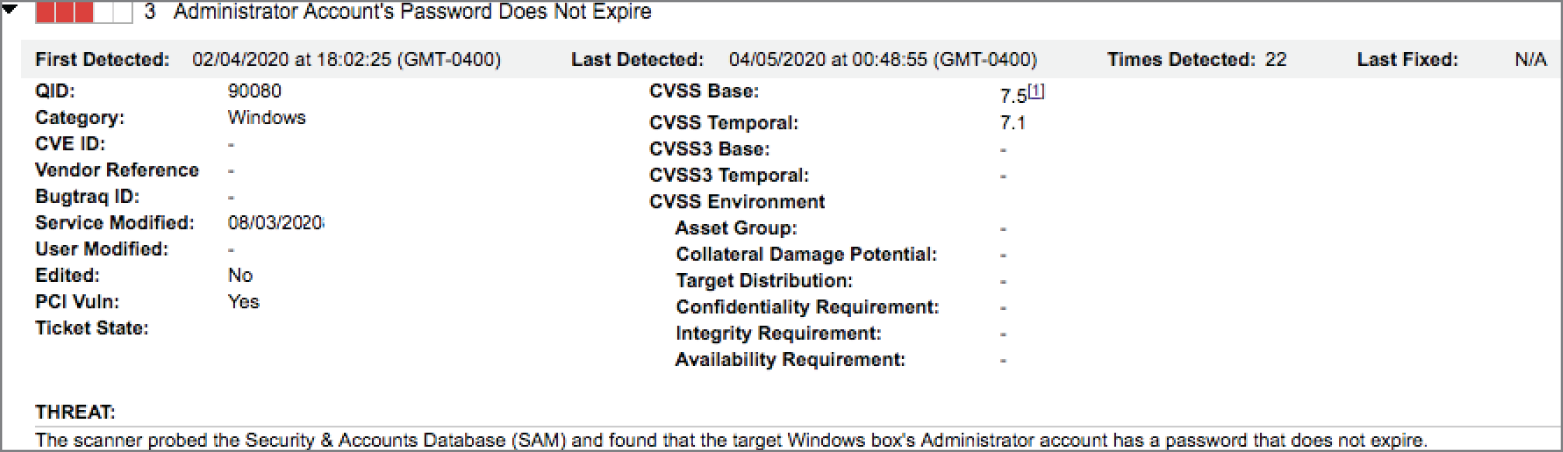
- Vic should drop everything and remediate this vulnerability immediately.
- While Vic does not need to drop everything, this vulnerability requires urgent attention and should be addressed quickly.
- This is a moderate vulnerability that can be scheduled for remediation at a convenient time.
- This vulnerability is informational in nature and may be left in place.
- Rob's manager recently asked him for an overview of any critical security issues that exist on his network. He looks at the reporting console of his vulnerability scanner and sees the options shown here. Which of the following report types would be his best likely starting point?
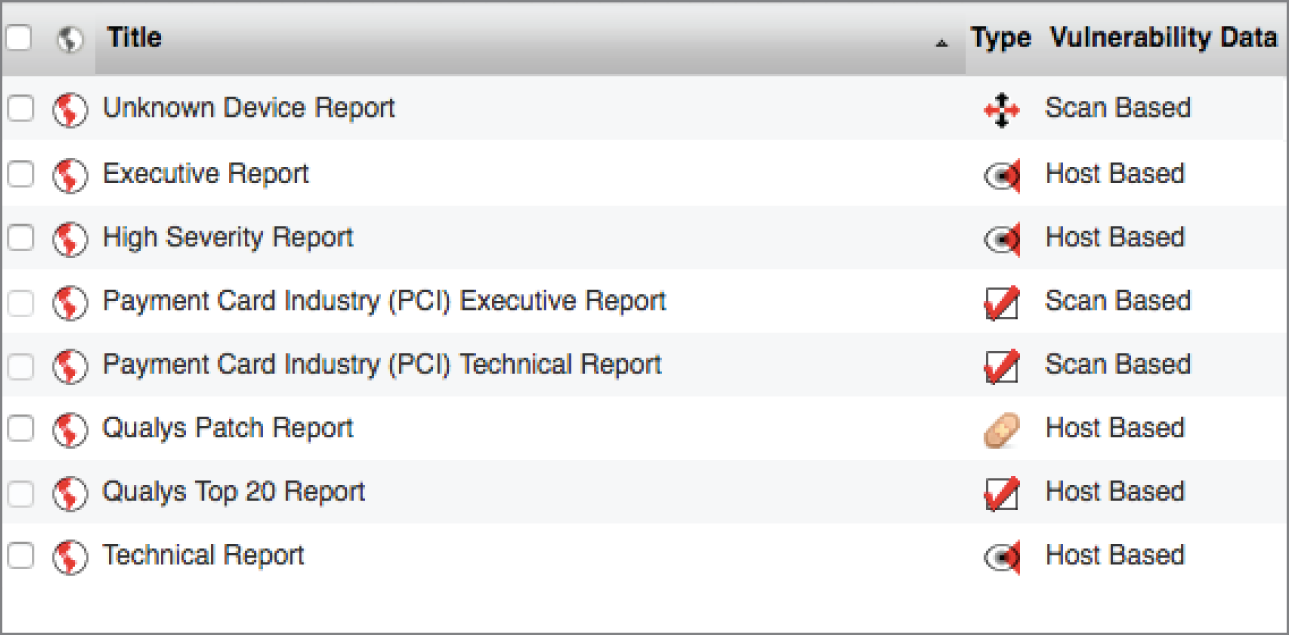
- Technical Report
- High Severity Report
- Qualys Patch Report
- Unknown Device Report
- Wendy is the security administrator for a membership association that is planning to launch an online store. As part of this launch, she will become responsible for ensuring that the website and associated systems are compliant with all relevant standards. What regulatory regime specifically covers credit card information?
- PCI DSS
- FERPA
- HIPAA
- SOX
- During a port scan of a server, Miguel discovered that the following ports are open on the internal network:
- TCP port 25
- TCP port 80
- TCP port 110
- TCP port 443
- TCP port 1433
- TCP port 3389
The scan results provide evidence that a variety of services are running on this server. Which one of the following services is not indicated by the scan results?
- Web
- Database
- SSH
- RDP
- Nina is a software developer, and she receives a report from her company's cybersecurity team that a vulnerability scan detected a SQL injection vulnerability in one of her applications. She examines her code and makes a modification in a test environment that she believes corrects the issue. What should she do next?
- Deploy the code to production immediately to resolve the vulnerability.
- Request a scan of the test environment to confirm that the issue is corrected.
- Mark the vulnerability as resolved and close the ticket.
- Hire a consultant to perform a penetration test to confirm that the vulnerability is resolved.
- George recently ran a port scan on a network device used by his organization. Which one of the following open ports represents the most significant possible security vulnerability?
- 22
- 23
- 161
- 443
Use the following scenario to answer questions 57–59.
Harold runs a vulnerability scan of a server that he is planning to move into production and finds the vulnerability shown here.
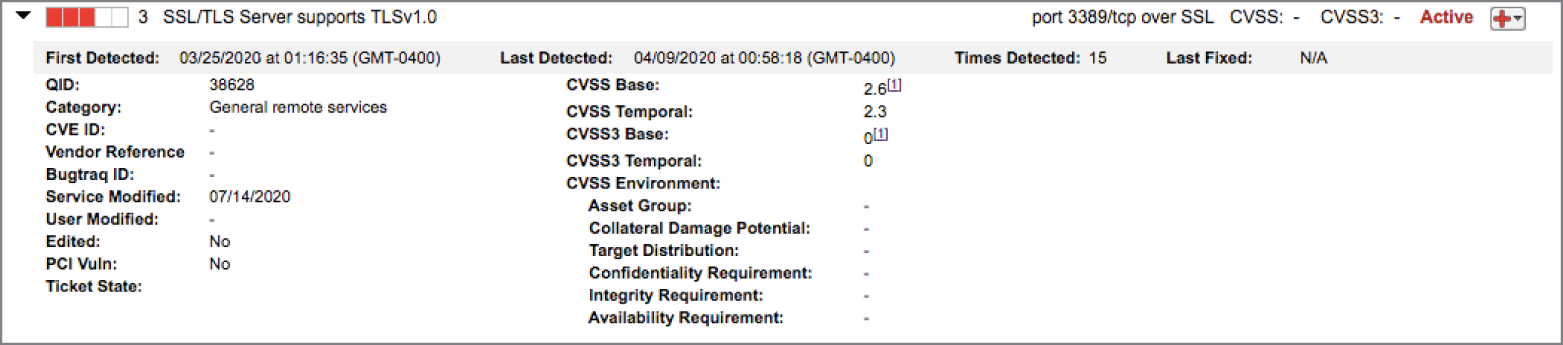
- What operating system is most likely running on the server in this vulnerability scan report?
- macOS
- Windows
- Kali
- RHEL
- Harold is preparing to correct the vulnerability. What service should he inspect to identify the issue?
- SSH
- HTTPS
- RDP
- SFTP
- Harold would like to secure the service affected by this vulnerability. Which one of the following protocols/versions would be an acceptable way to resolve the issue?
- SSL v2.0
- SSL v3.0
- TLS v1.0
- None of the above
- Seth found the vulnerability shown here in one of the systems on his network. What component requires a patch to correct this issue?

- Operating system
- VPN concentrator
- Network router or switch
- Hypervisor
- Quentin ran a vulnerability scan of a server in his organization and discovered the results shown here. Which one of the following actions is not required to resolve one of the vulnerabilities on this server?
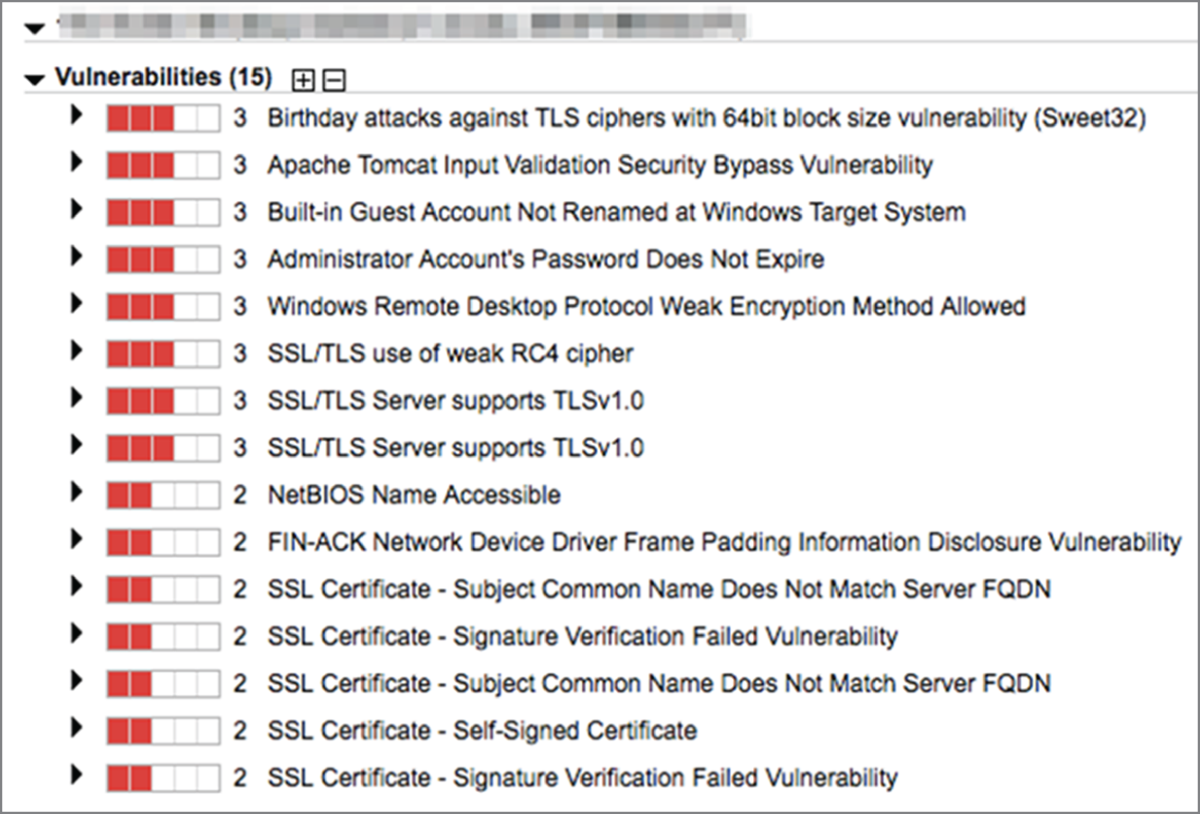
- Reconfigure cipher support.
- Apply Window security patches.
- Obtain a new SSL certificate.
- Enhance account security policies.
- The presence of ____________ triggers specific vulnerability scanning requirements based on law or regulation.
- Credit card information
- Protected health information
- Personally identifiable information
- Trade secret information
Use the scenario to answer questions 63–65.
Stella is analyzing the results of a vulnerability scan and comes across the vulnerability shown here on a server in her organization. The SharePoint service in question processes all of the organization's work orders and is a critical part of the routine business workflow.
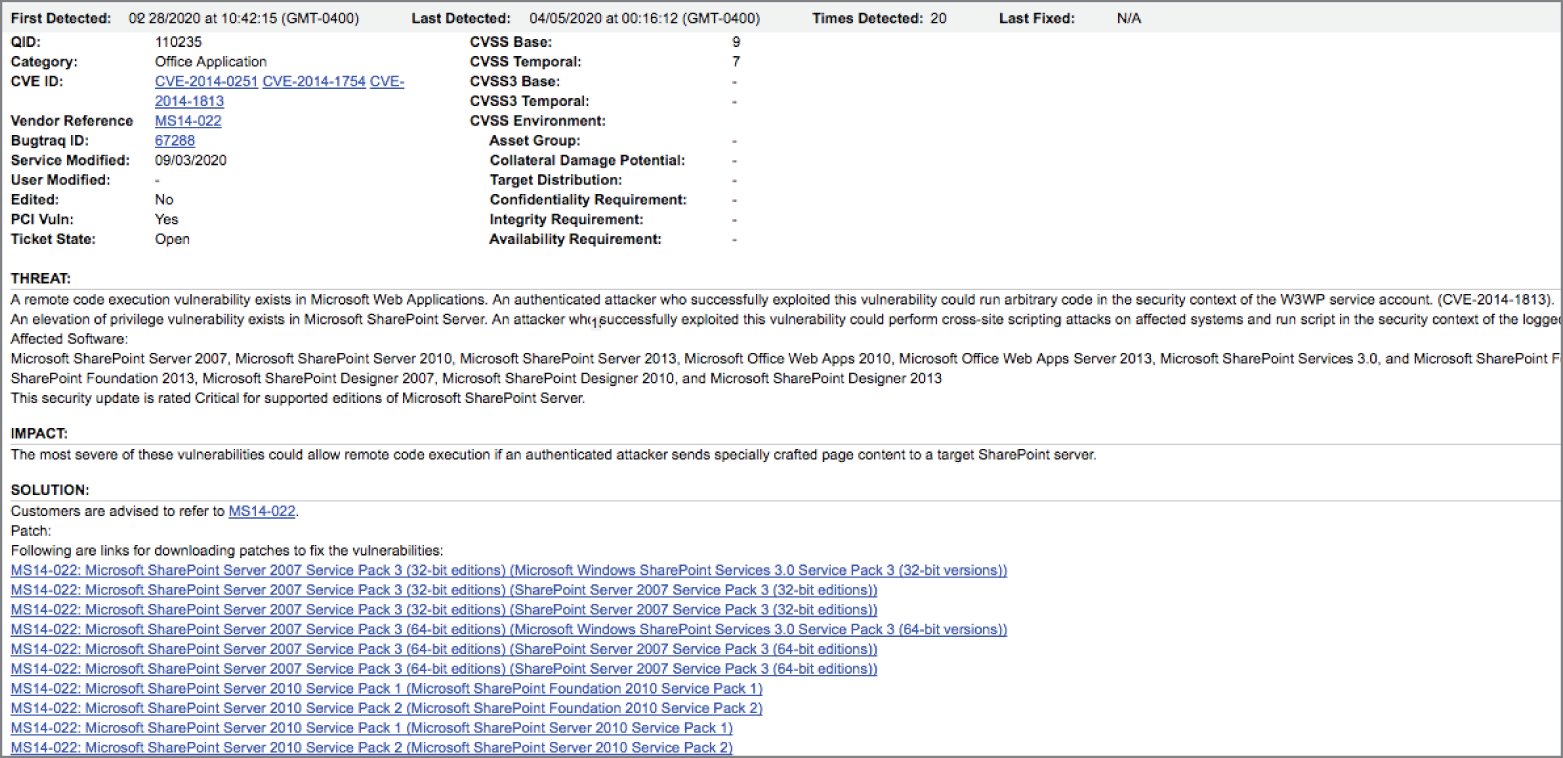
- What priority should Stella place on remediating this vulnerability?
- Stella should make this vulnerability one of her highest priorities.
- Stella should remediate this vulnerability within the next several weeks.
- Stella should remediate this vulnerability within the next several months.
- Stella does not need to assign any priority to remediating this vulnerability.
- What operating system is most likely running on the server in this vulnerability scan report?
- macOS
- Windows
- Kali
- RHEL
- What is the best way that Stella can correct this vulnerability?
- Deploy an intrusion prevention system.
- Apply one or more application patches.
- Apply one or more operating system patches.
- Disable the service.
- Harry is developing a vulnerability scanning program for a large network of sensors used by his organization to monitor a transcontinental gas pipeline. What term is commonly used to describe this type of sensor network?
- WLAN
- VPN
- P2P
- SCADA
- This morning, Eric ran a vulnerability scan in an attempt to detect a vulnerability that was announced by a software manufacturer yesterday afternoon. The scanner did not detect the vulnerability although Eric knows that at least two of his servers should have the issue. Eric contacted the vulnerability scanning vendor, who assured him that they released a signature for the vulnerability overnight. What should Eric do as a next step?
- Check the affected servers to verify a false positive.
- Check the affected servers to verify a false negative.
- Report a bug to the vendor.
- Update the vulnerability signatures.
- Natalie ran a vulnerability scan of a web application recently deployed by her organization, and the scan result reported a blind SQL injection. She reported the vulnerability to the developers, who scoured the application and made a few modifications but did not see any evidence that this attack was possible. Natalie reran the scan and received the same result. The developers are now insisting that their code is secure. What is the most likely scenario?
- The result is a false positive.
- The code is deficient and requires correction.
- The vulnerability is in a different web application running on the same server.
- Natalie is misreading the scan report.
- Kasun discovers a missing Windows security patch during a vulnerability scan of a server in his organization's datacenter. Upon further investigation, he discovers that the system is virtualized. Where should he apply the patch?
- To the virtualized system
- The patch is not necessary
- To the domain controller
- To the virtualization platform
- Joaquin is frustrated at the high level of false positive reports produced by his vulnerability scans and is contemplating a series of actions designed to reduce the false positive rate. Which one of the following actions is least likely to have the desired effect?
- Moving to credentialed scanning
- Moving to agent-based scanning
- Integrating asset information into the scan
- Increasing the sensitivity of scans
- Joe is conducting a network vulnerability scan against his datacenter and receives reports from system administrators that the scans are slowing down their systems. There are no network connectivity issues, only performance problems on individual hosts. He looks at the scan settings shown here. Which setting would be most likely to correct the problem?
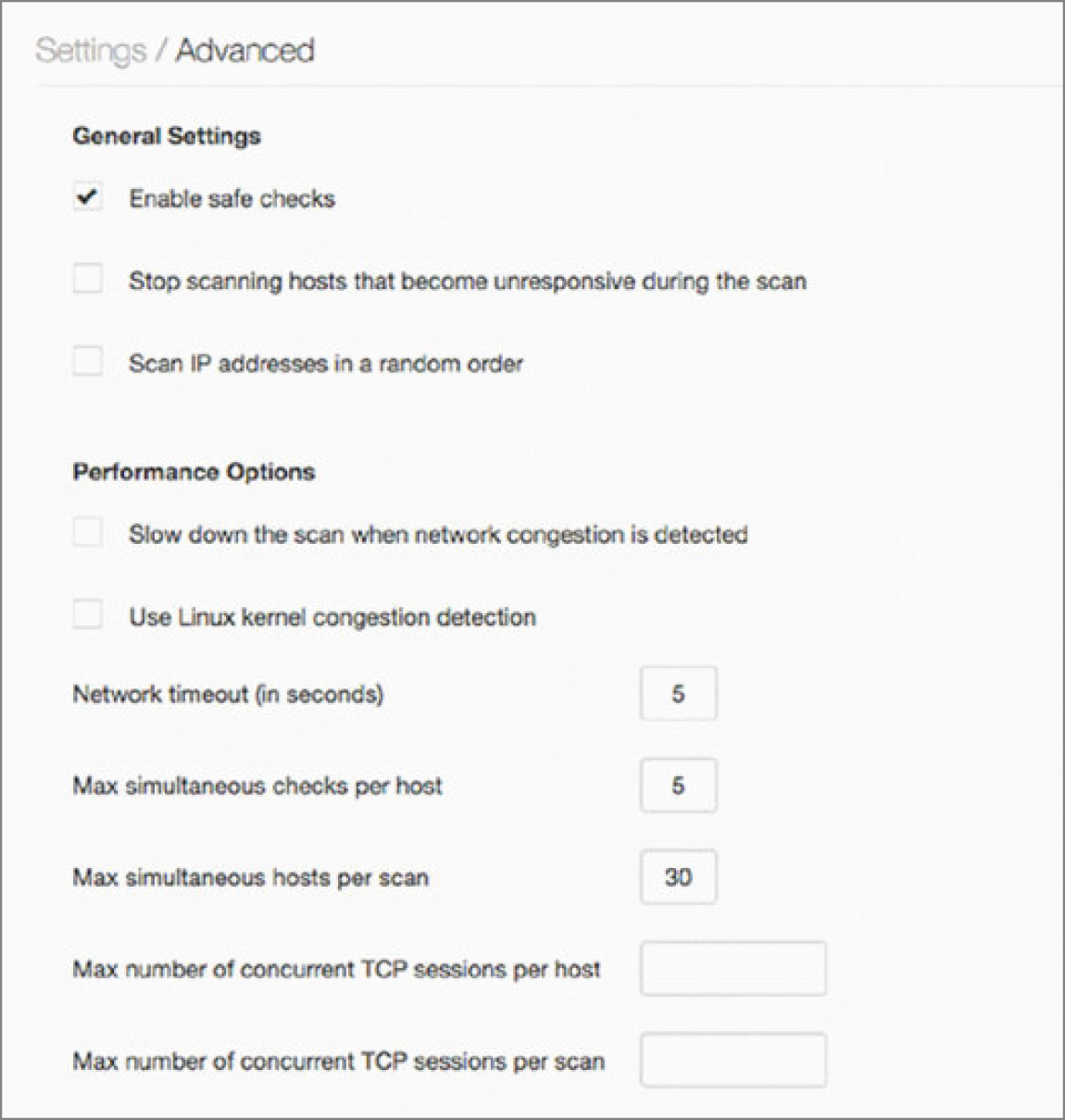
- Scan IP addresses in a random order
- Network timeout (in seconds)
- Max simultaneous checks per host
- Max simultaneous hosts per scan
- Isidora runs a vulnerability scan of the management interface for her organization's DNS service. She receives the vulnerability report shown here. What should be Isidora's next action?

- Disable the use of cookies on this service.
- Request that the vendor rewrite the interface to avoid this vulnerability.
- Investigate the contents of the cookie.
- Shut down the DNS service.
- Zara is prioritizing vulnerability scans and would like to base the frequency of scanning on the information asset value. Which of the following criteria would be most appropriate for her to use in this analysis?
- Cost of hardware acquisition
- Cost of hardware replacement
- Types of information processed
- Depreciated hardware cost
- Laura is working to upgrade her organization's vulnerability management program. She would like to add technology that is capable of retrieving the configurations of systems, even when they are highly secured. Many systems use local authentication, and she wants to avoid the burden of maintaining accounts on all of those systems. What technology should Laura consider to meet her requirement?
- Credentialed scanning
- Uncredentialed scanning
- Server-based scanning
- Agent-based scanning
- Javier discovered the vulnerability shown here in a system on his network. He is unsure what system component is affected. What type of service is causing this vulnerability?

- Backup service
- Database service
- File sharing
- Web service
- Alicia runs a vulnerability scan of a server being prepared for production and finds the vulnerability shown here. Which one of the following actions is least likely to reduce this risk?
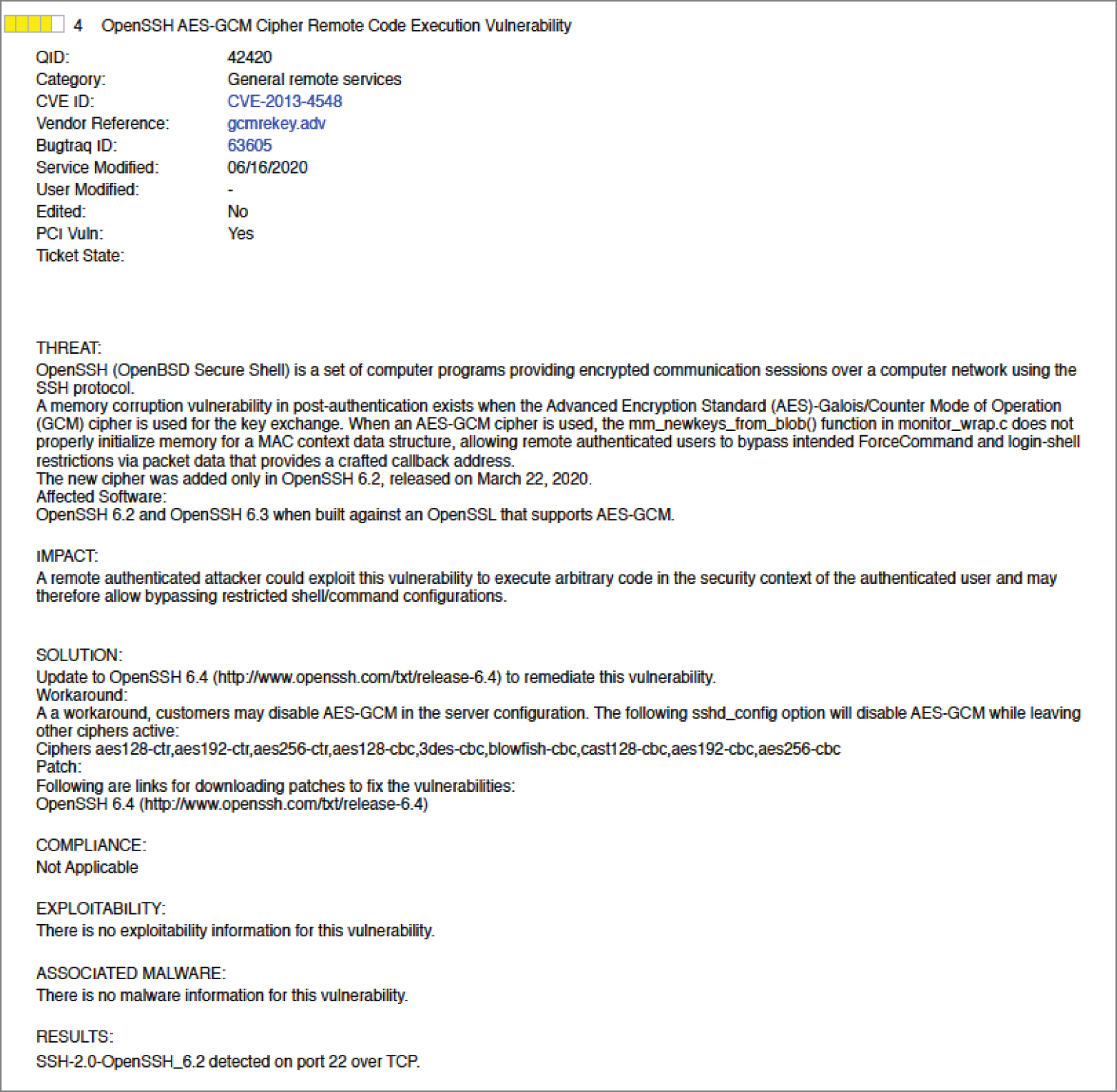
- Block all connections on port 22.
- Upgrade OpenSSH.
- Disable AES-GCM in the server configuration.
- Install a network IPS in front of the server.
- After scanning his organization's email server, Singh discovered the vulnerability shown here. What is the most effective response that Singh can take in this situation?

- Upgrade to the most recent version of Microsoft Exchange.
- Upgrade to the most recent version of Microsoft Windows.
- Implement the use of strong encryption.
- No action is required.
- A SQL injection exploit typically gains access to a database by exploiting a vulnerability in a(n)__________.
- Operating system
- Web application
- Database server
- Firewall
Use the following scenario to answer questions 79–81.
Ryan ran a vulnerability scan of one of his organization's production systems and received the report shown here. He would like to understand this vulnerability better and then remediate the issue.

- Ryan will not be able to correct the vulnerability for several days. In the meantime, he would like to configure his intrusion prevention system to watch for issues related to this vulnerability. Which one of the following protocols would an attacker use to exploit this vulnerability?
- SSH
- HTTPS
- FTP
- RDP
- Which one of the following actions could Ryan take to remediate the underlying issue without disrupting business activity?
- Disable the IIS service.
- Apply a security patch.
- Modify the web application.
- Apply IPS rules.
- If an attacker is able to exploit this vulnerability, what is the probable result that will have the highest impact on the organization?
- Administrative control of the server
- Complete control of the domain
- Access to configuration information
- Access to web application logs
- Ted is configuring vulnerability scanning for a file server on his company's internal network. The server is positioned on the network as shown here. What types of vulnerability scans should Ted perform to balance the efficiency of scanning effort with expected results?

- Ted should not perform scans of servers on the internal network.
- Ted should perform only internal vulnerability scans.
- Ted should perform only external vulnerability scans.
- Ted should perform both internal and external vulnerability scans.
- Zahra is attempting to determine the next task that she should take on from a list of security priorities. Her boss told her that she should focus on activities that have the most “bang for the buck.” Of the tasks shown here, which should she tackle first?

- Task 1
- Task 2
- Task 3
- Task 4
- Morgan is interpreting the vulnerability scan from her organization's network, shown here. She would like to determine which vulnerability to remediate first. Morgan would like to focus on vulnerabilities that are most easily exploitable by someone outside her organization. Assuming the firewall is properly configured, which one of the following vulnerabilities should Morgan give the highest priority?

- Severity 5 vulnerability in the workstation
- Severity 1 vulnerability in the file server
- Severity 5 vulnerability in the web server
- Severity 1 vulnerability in the mail server
- Mike runs a vulnerability scan against his company's virtualization environment and finds the vulnerability shown here in several of the virtual hosts. What action should Mike take?

- No action is necessary because this is an informational report.
- Mike should disable HTTPS on the affected devices.
- Mike should upgrade the version of OpenSSL on the affected devices.
- Mike should immediately upgrade the hypervisor.
- Juan recently scanned a system and found that it was running services on ports 139 and 445. What operating system is this system most likely running?
- Ubuntu
- macOS
- Kali
- Windows
- Gene is concerned about the theft of sensitive information stored in a database. Which one of the following vulnerabilities would pose the most direct threat to this information?
- SQL injection
- Cross-site scripting
- Buffer overflow
- Denial of service
- Which one of the following protocols is not likely to trigger a vulnerability scan alert when used to support a virtual private network (VPN)?
- IPsec
- SSL v2
- PPTP
- SSL v3
- Rahul ran a vulnerability scan of a server that will be used for credit card processing in his environment and received a report containing the vulnerability shown here. What action must Rahul take?

- Remediate the vulnerability when possible.
- Remediate the vulnerability prior to moving the system into production and rerun the scan to obtain a clean result.
- Remediate the vulnerability within 90 days of moving the system to production.
- No action is required.
Use the following scenario to answer questions 90–91.
Aaron is scanning a server in his organization's datacenter and receives the vulnerability report shown here. The service is exposed only to internal hosts.
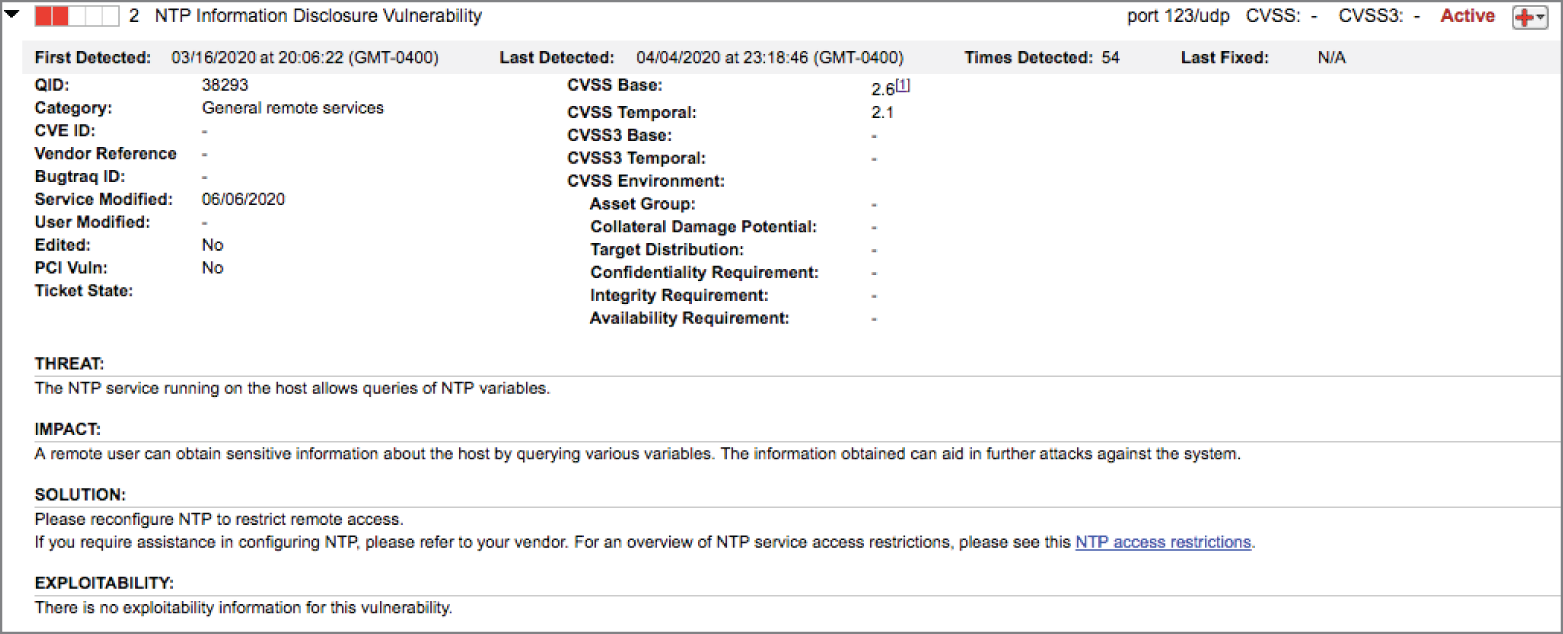
- What is the normal function of the service with this vulnerability?
- File transfer
- Web hosting
- Time synchronization
- Network addressing
- What priority should Aaron place on remediating this vulnerability?
- Aaron should make this vulnerability his highest priority.
- Aaron should remediate this vulnerability urgently but does not need to drop everything.
- Aaron should remediate this vulnerability within the next month.
- Aaron does not need to assign any priority to remediating this vulnerability.
- Without access to any additional information, which one of the following vulnerabilities would you consider the most severe if discovered on a production web server?
- CGI generic SQL injection
- Web application information disclosure
- Web server uses basic authentication without HTTPS
- Web server directory enumeration
- Gina ran a vulnerability scan on three systems that her organization is planning to move to production and received the results shown here. How many of these issues should Gina require be resolved before moving to production?

- 0.
- 1.
- 3.
- All of these issues should be resolved.
- Ji-won recently restarted an old vulnerability scanner that had not been used in more than a year. She booted the scanner, logged in, and configured a scan to run. After reading the scan results, she found that the scanner was not detecting known vulnerabilities that were detected by other scanners. What is the most likely cause of this issue?
- The scanner is running on an outdated operating system.
- The scanner's maintenance subscription is expired.
- Ji-won has invalid credentials on the scanner.
- The scanner does not have a current, valid IP address.
- Isabella runs both internal and external vulnerability scans of a web server and detects a possible SQL injection vulnerability. The vulnerability appears only in the internal scan and does not appear in the external scan. When Isabella checks the server logs, she sees the requests coming from the internal scan and sees some requests from the external scanner but no evidence that a SQL injection exploit was attempted by the external scanner. What is the most likely explanation for these results?
- A host firewall is blocking external network connections to the web server.
- A network firewall is blocking external network connections to the web server.
- A host IPS is blocking some requests to the web server.
- A network IPS is blocking some requests to the web server.
- Rick discovers the vulnerability shown here in a server running in his datacenter. What characteristic of this vulnerability should concern him the most?
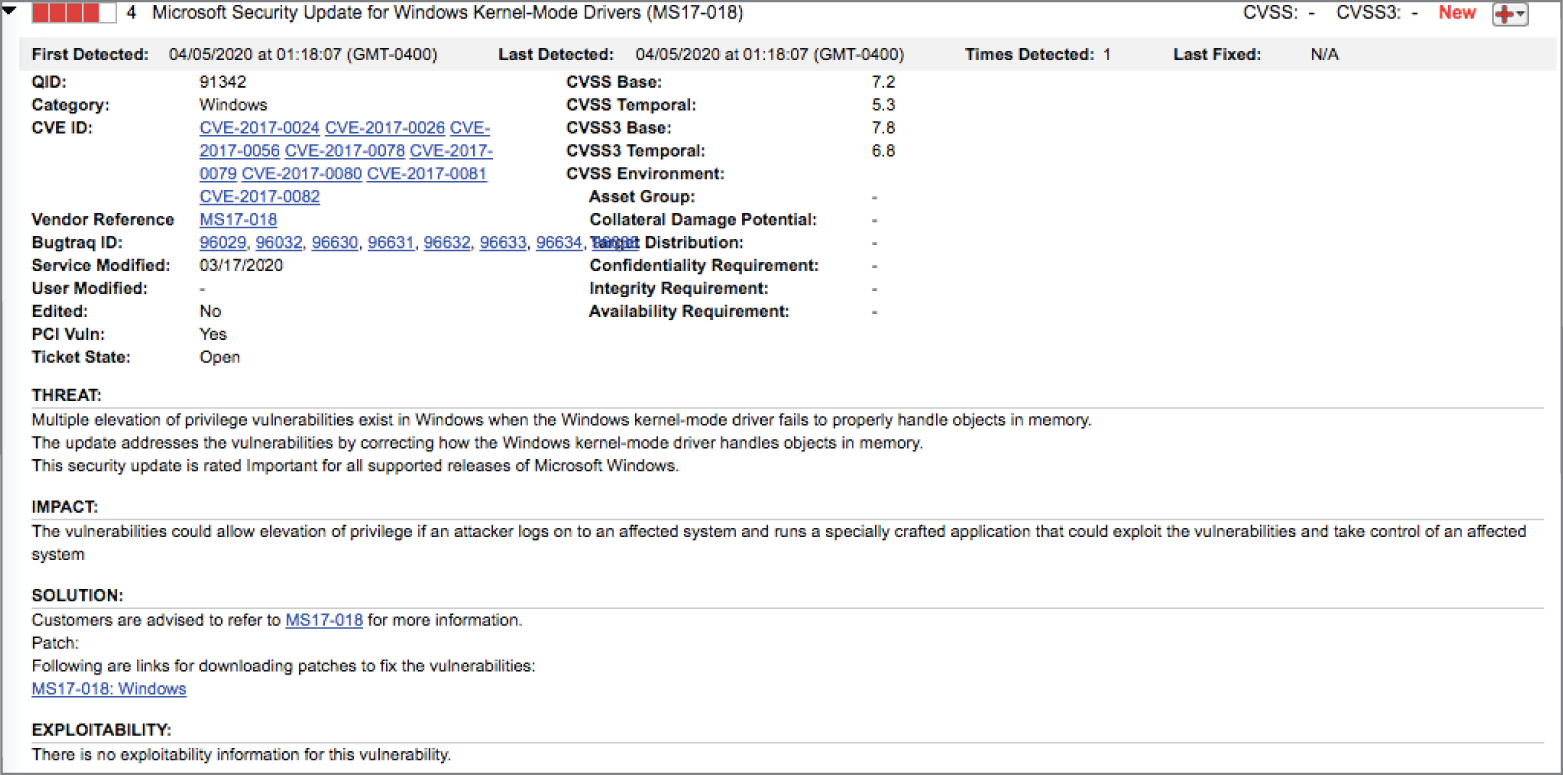
- It is the subject of a recent security bulletin.
- It has a CVSS score of 7.8.
- There are multiple Bugtraq and CVE IDs.
- It affects kernel-mode drivers.
- Carl runs a vulnerability scan of a mail server used by his organization and receives the vulnerability report shown here. What action should Carl take to correct this issue?

- Carl does not need to take any action because this is an informational report.
- Carl should replace SSL with TLS on this server.
- Carl should disable weak ciphers.
- Carl should upgrade OpenSSL.
- Renee is configuring a vulnerability scanner that will run scans of her network. Corporate policy requires the use of daily vulnerability scans. What would be the best time to configure the scans?
- During the day when operations reach their peak to stress test systems
- During the evening when operations are minimal to reduce the impact on systems
- During lunch hour when people have stepped away from their systems but there is still considerable load
- On the weekends when the scans may run unimpeded
- Ahmed is reviewing the vulnerability scan report from his organization's central storage service and finds the results shown here. Which action can Ahmed take that will be effective in remediating the highest-severity issue possible?

- Upgrade to SNMP v3.
- Disable the use of RC4.
- Replace the use of SSL with TLS.
- Disable remote share enumeration.
Use the following scenario to answer questions 100–101.
Glenda ran a vulnerability scan of workstations in her organization. She noticed that many of the workstations reported the vulnerability shown here. She would like to not only correct this issue but also prevent the likelihood of similar issues occurring in the future.
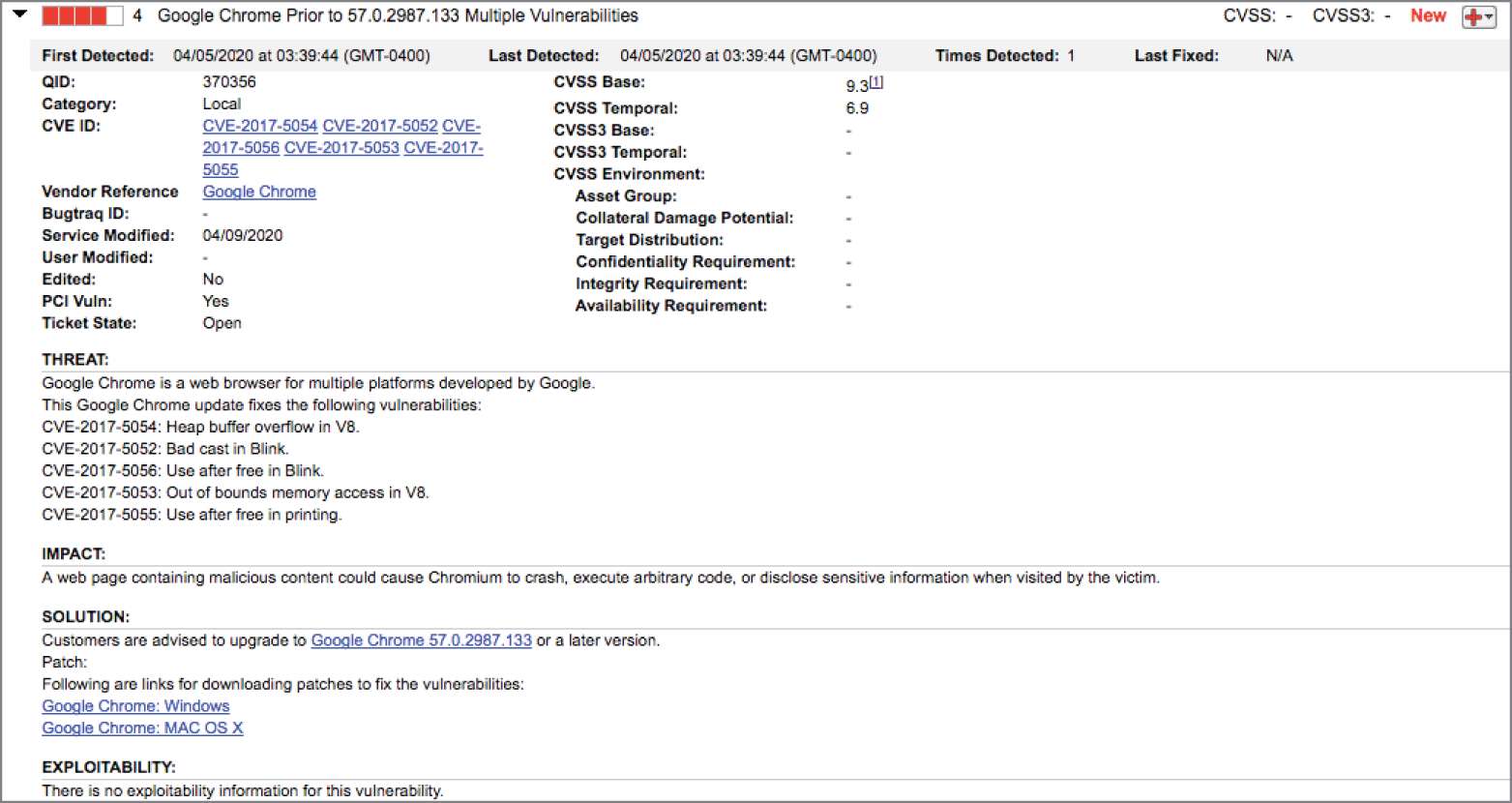
- What action should Glenda take to achieve her goals?
- Glenda should uninstall Chrome from all workstations and replace it with Internet Explorer.
- Glenda should manually upgrade Chrome on all workstations.
- Glenda should configure all workstations to automatically upgrade Chrome.
- Glenda does not need to take any action.
- What priority should Glenda place on remediating this vulnerability?
- Glenda should make this vulnerability her highest priority.
- Glenda should remediate this vulnerability urgently but does not need to drop everything.
- Glenda should remediate this vulnerability within the next several months.
- Glenda does not need to assign any priority to remediating this vulnerability.
- After reviewing the results of a vulnerability scan, Gabriella discovered a flaw in her Oracle database server that may allow an attacker to attempt a direct connection to the server. She would like to review NetFlow logs to determine what systems have connected to the server recently. What TCP port should Gabriella expect to find used for this communication?
- 443
- 1433
- 1521
- 8080
- Terry recently ran a vulnerability scan against his organization's credit card processing environment that found a number of vulnerabilities. Which vulnerabilities must he remediate to have a “clean” scan under PCI DSS standards?
- Critical vulnerabilities
- Critical and high vulnerabilities
- Critical, high, and medium vulnerabilities
- Critical, high, medium, and low vulnerabilities
- Himari discovers the vulnerability shown here on several Windows systems in her organization. There is a patch available, but it requires compatibility testing that will take several days to complete. What type of file should Himari be watchful for because it may directly exploit this vulnerability?

- Private key files
- Word documents
- Image files
- Encrypted files
- Aaron is configuring a vulnerability scan for a Class C network and is trying to choose a port setting from the list shown here. He would like to choose a scan option that will efficiently scan his network but also complete in a reasonable period of time. Which setting would be most appropriate?

- None
- Full
- Standard Scan
- Light Scan
- Haruto is reviewing the results of a vulnerability scan, shown here, from a web server in his organization. Access to this server is restricted at the firewall so that it may not be accessed on port 80 or 443. Which of the following vulnerabilities should Haruto still address?

- OpenSSL version.
- Cookie information disclosure.
- TRACK/TRACE methods.
- Haruto does not need to address any of these vulnerabilities because they are not exposed to the outside world.
- Brian is considering the use of several different categories of vulnerability plug-ins. Of the types listed here, which is the most likely to result in false positive reports?
- Registry inspection
- Banner grabbing
- Service interrogation
- Fuzzing
- Binh conducts a vulnerability scan and finds three different vulnerabilities, with the CVSS scores shown here. Which vulnerability should be his highest priority to fix, assuming all three fixes are of equal difficulty?

- Vulnerability 1.
- Vulnerability 2.
- Vulnerability 3.
- Vulnerabilities 1 and 3 are equal in priority.
- Which one of the following is not an appropriate criterion to use when prioritizing the remediation of vulnerabilities?
- Network exposure of the affected system.
- Difficulty of remediation.
- Severity of the vulnerability.
- All of these are appropriate.
- Landon is preparing to run a vulnerability scan of a dedicated Apache server that his organization is planning to move into a screened subnet (DMZ). Which one of the following vulnerability scans is least likely to provide informative results?
- Web application vulnerability scan
- Database vulnerability scan
- Port scan
- Network vulnerability scan
- Ken recently received the vulnerability report shown here that affects a file server used by his organization. What is the primary nature of the risk introduced by this vulnerability?
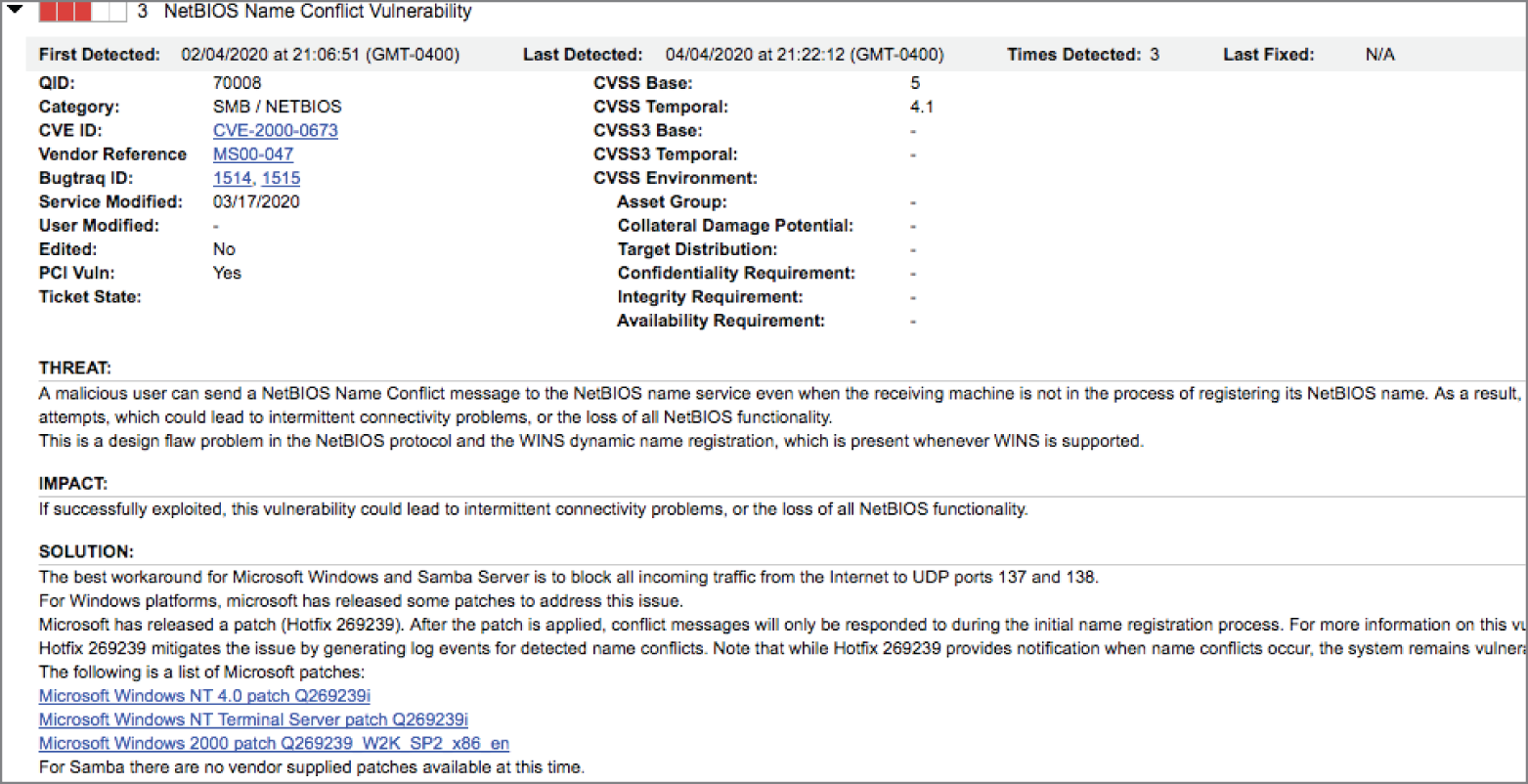
- Confidentiality
- Integrity
- Availability
- Nonrepudiation
- Aadesh is creating a vulnerability management program for his company. He has limited scanning resources and would like to apply them to different systems based on the sensitivity and criticality of the information that they handle. What criteria should Aadesh use to determine the vulnerability scanning frequency?
- Data remanence
- Data privacy
- Data classification
- Data sovereignty
- Tom recently read a media report about a ransomware outbreak that was spreading rapidly across the Internet by exploiting a zero-day vulnerability in Microsoft Windows. As part of a comprehensive response, he would like to include a control that would allow his organization to effectively recover from a ransomware infection. Which one of the following controls would best achieve Tom's objective?
- Security patching
- Host firewalls
- Backups
- Intrusion prevention systems
- Kaitlyn discovered the vulnerability shown here on a workstation in her organization. Which one of the following is not an acceptable method for remediating this vulnerability?
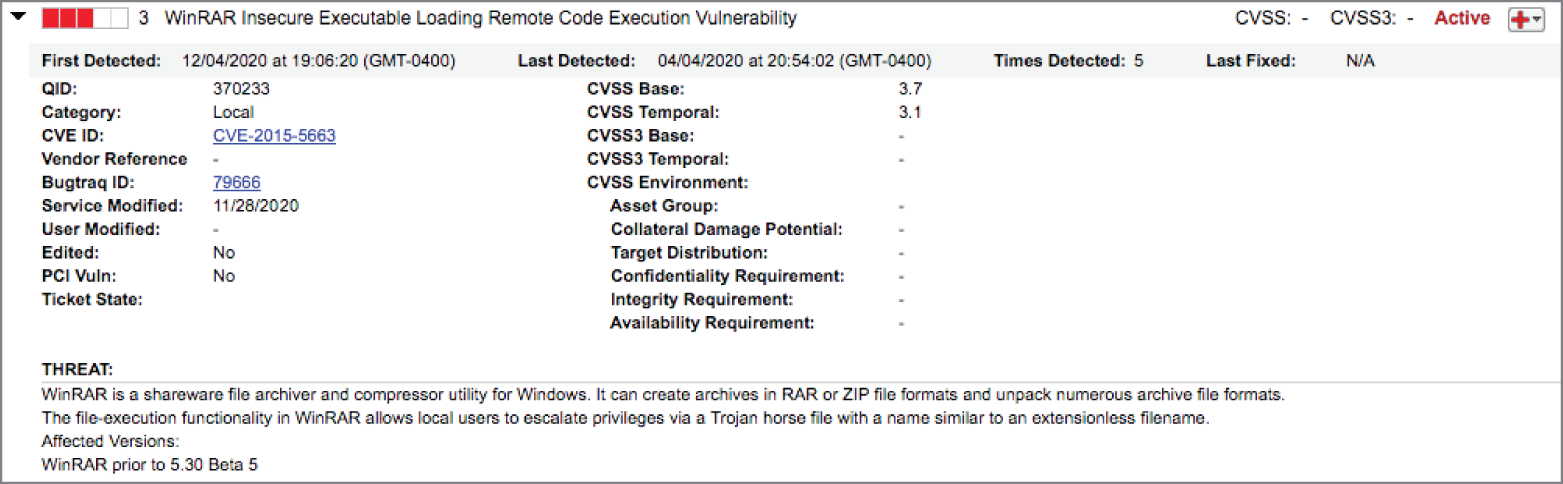
- Upgrade WinRAR.
- Upgrade Windows.
- Remove WinRAR.
- Replace WinRAR with an alternate compression utility.
- Brent ran a vulnerability scan of several network infrastructure devices on his network and obtained the result shown here. What is the extent of the impact that an attacker could have by exploiting this vulnerability directly?

- Denial of service
- Theft of sensitive information
- Network eavesdropping
- Reconnaissance
- Yashvir runs the cybersecurity vulnerability management program for his organization. He sends a database administrator a report of a missing database patch that corrects a high severity security issue. The DBA writes back to Yashvir that he has applied the patch. Yashvir reruns the scan, and it still reports the same vulnerability. What should he do next?
- Mark the vulnerability as a false positive.
- Ask the DBA to recheck the database server.
- Mark the vulnerability as an exception.
- Escalate the issue to the DBA's manager.
- Manya is reviewing the results of a vulnerability scan and identifies the issue shown here in one of her systems. She consults with developers who check the code and assure her that it is not vulnerable to SQL injection attacks. An independent auditor confirms this for Manya. What is the most likely scenario?
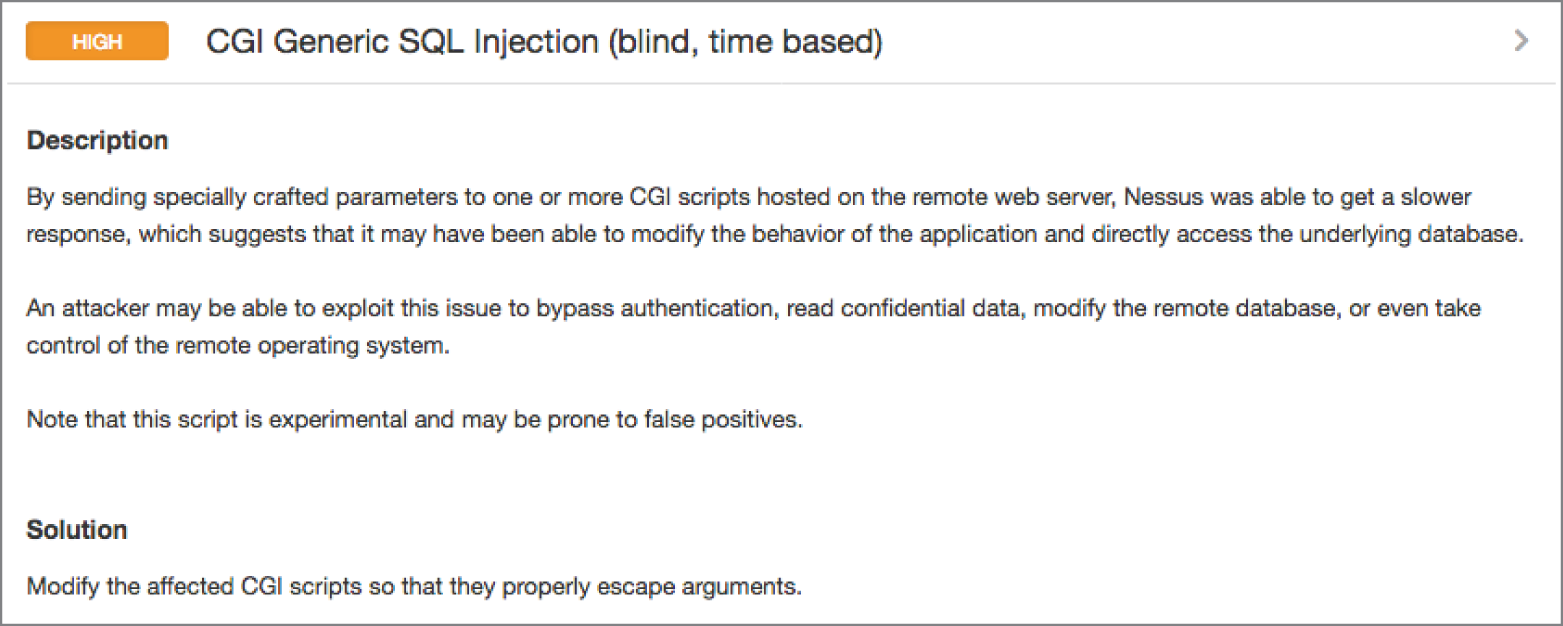
- This is a false positive report.
- The developers are wrong, and the vulnerability exists.
- The scanner is malfunctioning.
- The database server is misconfigured.
- Erik is reviewing the results of a vulnerability scan and comes across the vulnerability report shown here. Which one of the following services is least likely to be affected by this vulnerability?

- HTTPS
- HTTP
- SSH
- VPN
Use the following scenario to answer questions 119–120.
Larry recently discovered a critical vulnerability in one of his organization's database servers during a routine vulnerability scan. When he showed the report to a database administrator, the administrator responded that they had corrected the vulnerability by using a vendor-supplied workaround because upgrading the database would disrupt an important process. Larry verified that the workaround is in place and corrects the vulnerability.
- How should Larry respond to this situation?
- Mark the report as a false positive.
- Insist that the administrator apply the vendor patch.
- Mark the report as an exception.
- Require that the administrator submit a report describing the workaround after each vulnerability scan.
- What is the most likely cause of this report?
- The vulnerability scanner requires an update.
- The vulnerability scanner depends on version detection.
- The database administrator incorrectly applied the workaround.
- Larry misconfigured the scan.
- Mila ran a vulnerability scan of a server in her organization and found the vulnerability shown here. What is the use of the service affected by this vulnerability?
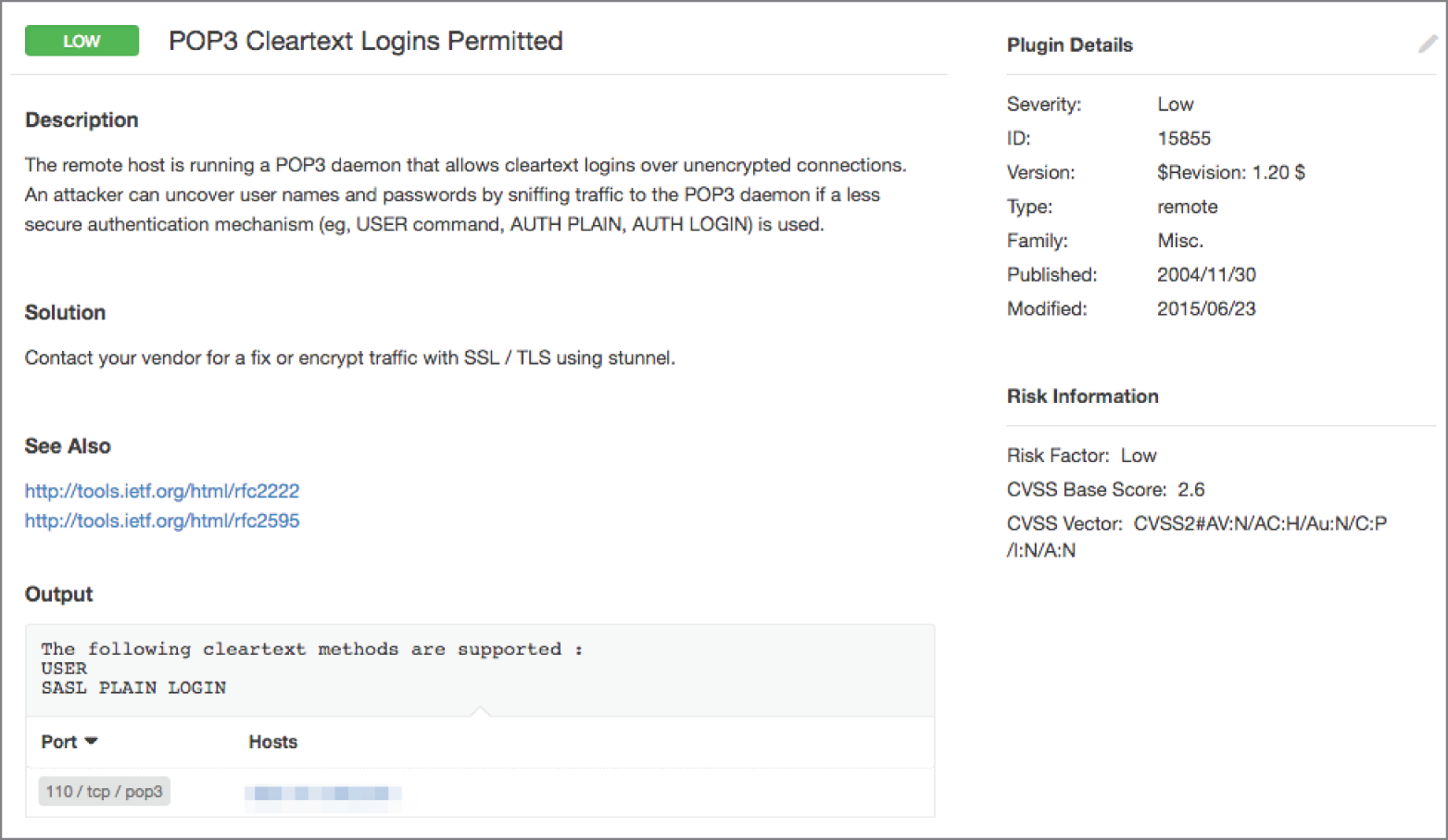
- Web server
- Database server
- Email server
- Directory server
- Margot discovered that a server in her organization has a SQL injection vulnerability. She would like to investigate whether attackers have attempted to exploit this vulnerability. Which one of the following data sources is least likely to provide helpful information?
- NetFlow logs
- Web server logs
- Database logs
- IDS logs
- Krista is reviewing a vulnerability scan report and comes across the vulnerability shown here. She comes from a Linux background and is not as familiar with Windows administration. She is not familiar with the
runascommand mentioned in this vulnerability. What is the closest Linux equivalent command?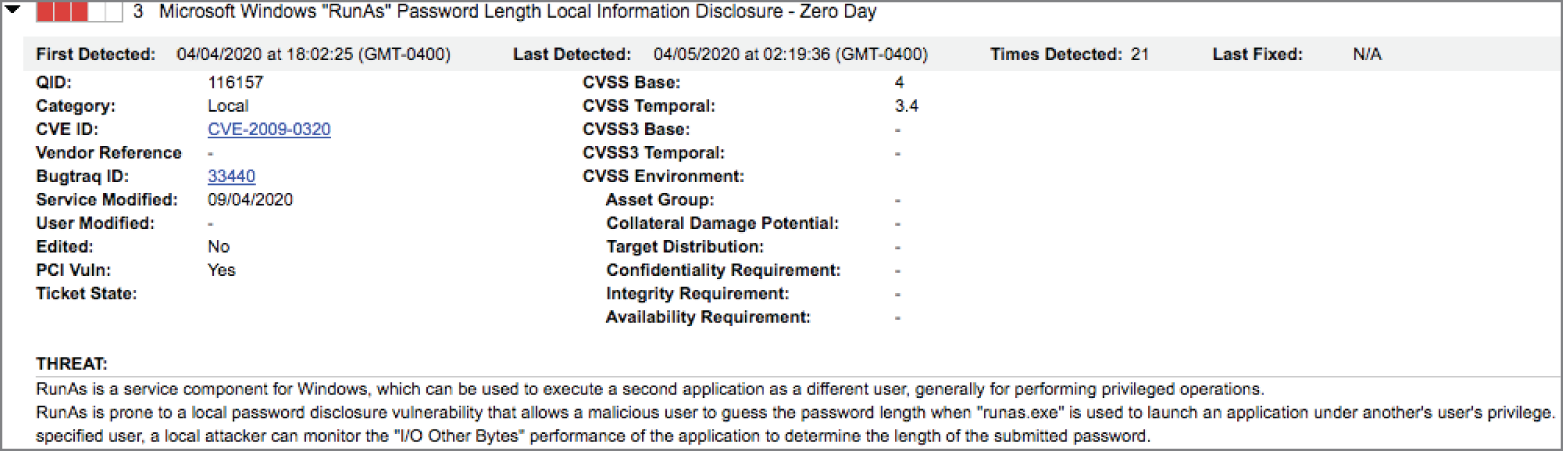
sudogrepsups
- After scanning a web application for possible vulnerabilities, Barry received the result shown here. Which one of the following best describes the threat posed by this vulnerability?
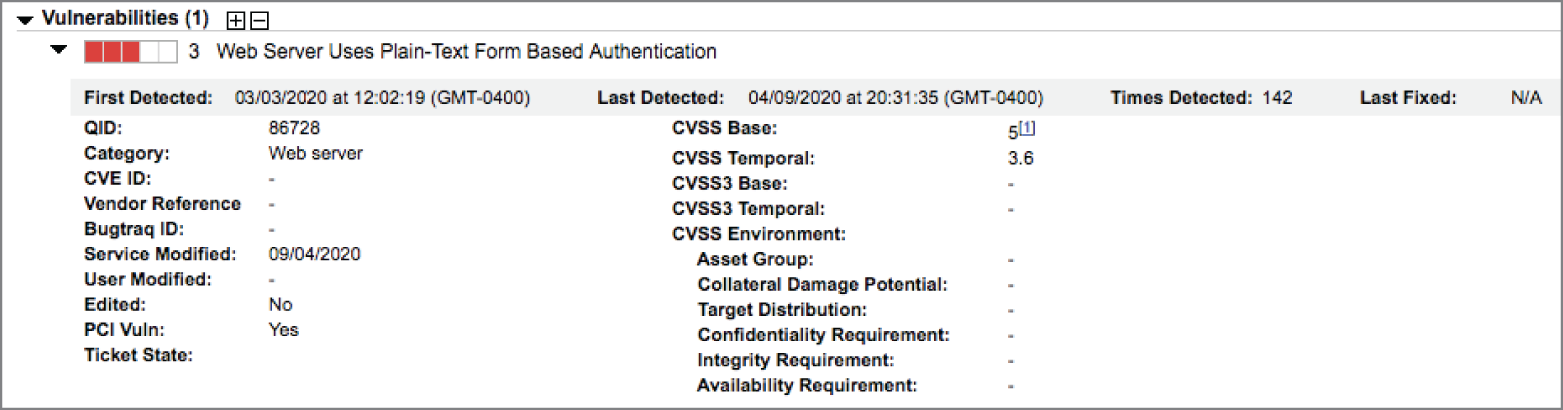
- An attacker can eavesdrop on authentication exchanges.
- An attacker can cause a denial-of-service attack on the web application.
- An attacker can disrupt the encryption mechanism used by this server.
- An attacker can edit the application code running on this server.
- Javier ran a vulnerability scan of a network device used by his organization and discovered the vulnerability shown here. What type of attack would this vulnerability enable?
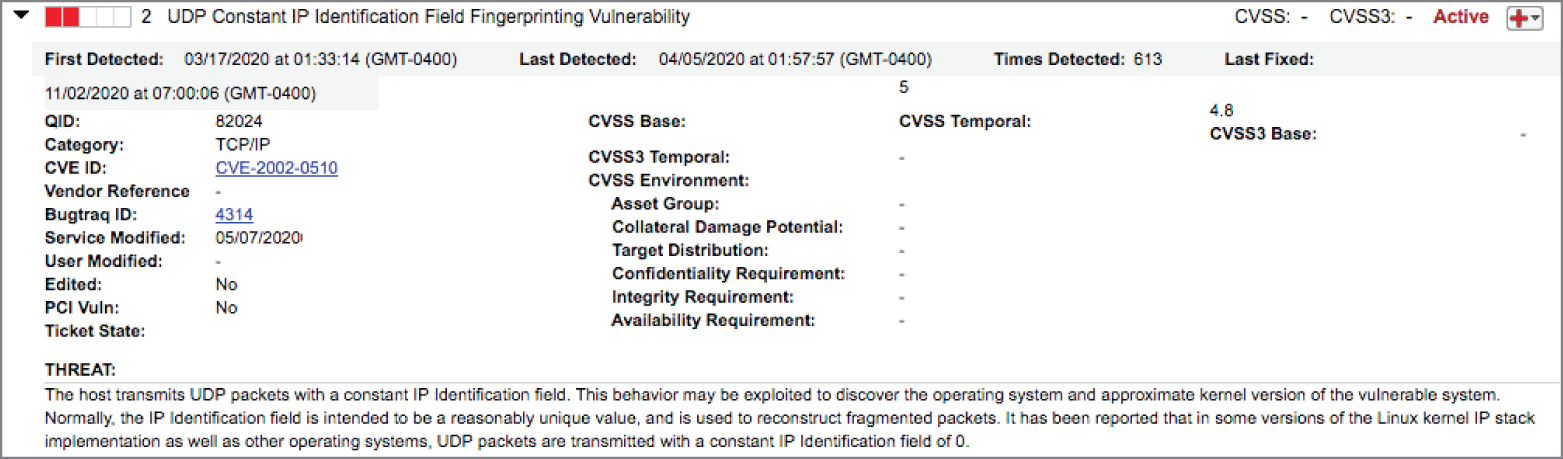
- Denial of service
- Information theft
- Information alteration
- Reconnaissance
- Akari scans a Windows server in her organization and finds that it has multiple critical vulnerabilities, detailed in the report shown here. What action can Akari take that will have the most significant impact on these issues without creating a long-term outage?

- Configure the host firewall to block inbound connections.
- Apply security patches.
- Disable the guest account on the server.
- Configure the server to only use secure ciphers.
- During a recent vulnerability scan of workstations on her network, Andrea discovered the vulnerability shown here. Which one of the following actions is least likely to remediate this vulnerability?

- Remove JRE from workstations.
- Upgrade JRE to the most recent version.
- Block inbound connections on port 80 using the host firewall.
- Use a web content filtering system to scan for malicious traffic.
- Doug is preparing an RFP for a vulnerability scanner for his organization. He needs to know the number of systems on his network to help determine the scanner requirements. Which one of the following would not be an easy way to obtain this information?
- ARP tables
- Asset management tool
- Discovery scan
- Results of scans recently run by a consultant
- Mary runs a vulnerability scan of her entire organization and shares the report with another analyst on her team. An excerpt from that report appears here. Her colleague points out that the report contains only vulnerabilities with severities of 3, 4, or 5. What is the most likely cause of this result?

- The scan sensitivity is set to exclude low-importance vulnerabilities.
- Mary did not configure the scan properly.
- Systems in the datacenter do not contain any level 1 or 2 vulnerabilities.
- The scan sensitivity is set to exclude high-impact vulnerabilities.
- Mikhail is reviewing the vulnerability shown here, which was detected on several servers in his environment. What action should Mikhail take?
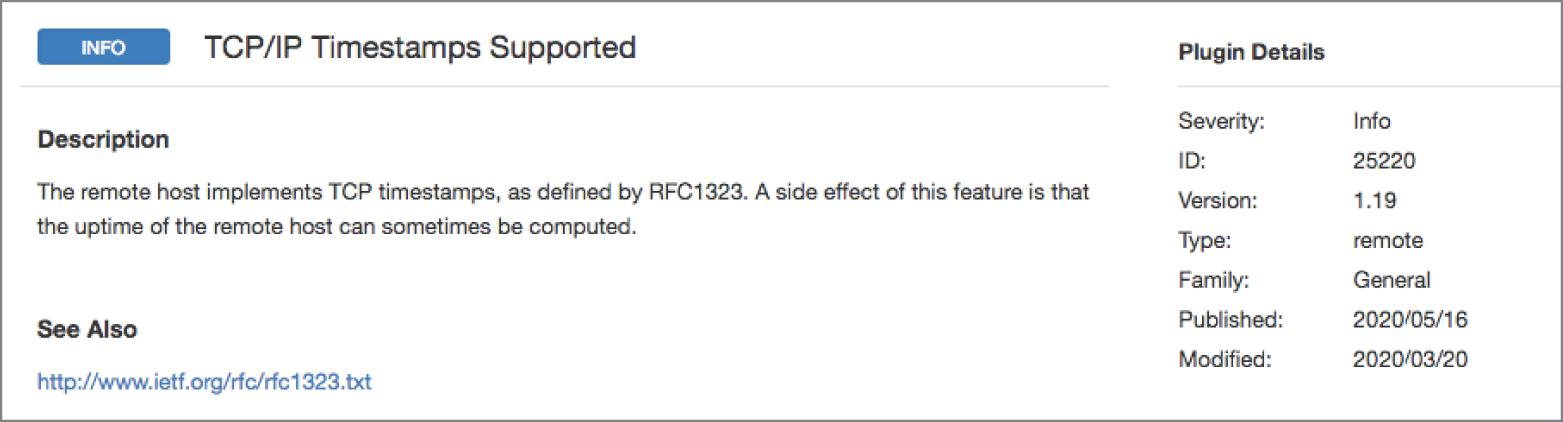
- Block TCP/IP access to these servers from external sources.
- Upgrade the operating system on these servers.
- Encrypt all access to these servers.
- No action is necessary.
- Which one of the following approaches provides the most current and accurate information about vulnerabilities present on a system because of the misconfiguration of operating system settings?
- On-demand vulnerability scanning
- Continuous vulnerability scanning
- Scheduled vulnerability scanning
- Agent-based monitoring
Use the following scenario to answer questions 132–134.
Pete recently conducted a broad vulnerability scan of all the servers and workstations in his environment. He scanned the following three networks:
- Screened subnet (DMZ) network that contains servers with public exposure
- Workstation network that contains workstations that are allowed outbound access only
- Internal server network that contains servers exposed only to internal systems
He detected the following vulnerabilities:
- Vulnerability 1: A SQL injection vulnerability on a screened subnet (DMZ) server that would grant access to a database server on the internal network (severity 5/5)
- Vulnerability 2: A buffer overflow vulnerability on a domain controller on the internal server network (severity 3/5)
- Vulnerability 3: A missing security patch on several hundred Windows workstations on the workstation network (severity 2/5)
- Vulnerability 4: A denial-of-service vulnerability on a screened subnet (DMZ) server that would allow an attacker to disrupt a public-facing website (severity 2/5)
- Vulnerability 5: A denial-of-service vulnerability on an internal server that would allow an attacker to disrupt an internal website (severity 4/5)
Note that the severity ratings assigned to these vulnerabilities are directly from the vulnerability scanner and were not assigned by Pete.
- Absent any other information, which one of the vulnerabilities in the report should Pete remediate first?
- Vulnerability 1
- Vulnerability 2
- Vulnerability 3
- Vulnerability 4
- Pete is working with the desktop support manager to remediate vulnerability 3. What would be the most efficient way to correct this issue?
- Personally visit each workstation to remediate the vulnerability.
- Remotely connect to each workstation to remediate the vulnerability.
- Perform registry updates using a remote configuration tool.
- Apply the patch using a GPO.
- Pete recently conferred with the organization's CISO, and the team is launching an initiative designed to combat the insider threat. They are particularly concerned about the theft of information by employees seeking to exceed their authorized access. Which one of the vulnerabilities in this report is of greatest concern given this priority?
- Vulnerability 2
- Vulnerability 3
- Vulnerability 4
- Vulnerability 5
- Wanda recently discovered the vulnerability shown here on a Windows server in her organization. She is unable to apply the patch to the server for six weeks because of operational issues. What workaround would be most effective in limiting the likelihood that this vulnerability would be exploited?

- Restrict interactive logins to the system.
- Remove Microsoft Office from the server.
- Remove Internet Explorer from the server.
- Apply the security patch.
- Garrett is configuring vulnerability scanning for a new web server that his organization is deploying on its screened subnet (DMZ) network. The server hosts the company's public website. What type of scanning should Garrett configure for best results?
- Garrett should not perform scanning of screened subnet (DMZ) systems.
- Garrett should perform external scanning only.
- Garrett should perform internal scanning only.
- Garrett should perform both internal and external scanning.
- Frank recently ran a vulnerability scan and identified a POS terminal that contains an unpatchable vulnerability because of running an unsupported operating system. Frank consults with his manager and is told that the POS is being used with full knowledge of management and, as a compensating control, it has been placed on an isolated network with no access to other systems. Frank's manager tells him that the merchant bank is aware of the issue. How should Frank handle this situation?
- Document the vulnerability as an approved exception.
- Explain to his manager that PCI DSS does not permit the use of unsupported operating systems.
- Decommission the POS system immediately to avoid personal liability.
- Upgrade the operating system immediately.
- James is configuring vulnerability scans of a dedicated network that his organization uses for processing credit card transactions. What types of scans are least important for James to include in his scanning program?
- Scans from a dedicated scanner on the card processing network.
- Scans from an external scanner on his organization's network.
- Scans from an external scanner operated by an approved scanning vendor.
- All three types of scans are equally important.
- Helen performs a vulnerability scan of one of the internal LANs within her organization and finds a report of a web application vulnerability on a device. Upon investigation, she discovers that the device in question is a printer. What is the most likely scenario in this case?
- The printer is running an embedded web server.
- The report is a false positive result.
- The printer recently changed IP addresses.
- Helen inadvertently scanned the wrong network.
- Julian recently detected the vulnerability shown here on several servers in his environment. Because of the critical nature of the vulnerability, he would like to block all access to the affected service until it is resolved using a firewall rule. He verifies that the following TCP ports are open on the host firewall. Which one of the following does Julian not need to block to restrict access to this service?

- 137
- 139
- 389
- 445
- Ted recently ran a vulnerability scan of his network and was overwhelmed with results. He would like to focus on the most important vulnerabilities. How should Ted reconfigure his vulnerability scanner?
- Increase the scan sensitivity.
- Decrease the scan sensitivity.
- Increase the scan frequency.
- Decrease the scan frequency.
- Sunitha discovered the vulnerability shown here in an application developed by her organization. What application security technique is most likely to resolve this issue?

- Input validation
- Network segmentation
- Parameter handling
- Tag removal
- Sherry runs a vulnerability scan and receives the high-level results shown here. Her priority is to remediate the most important vulnerabilities first. Which system should be her highest priority?
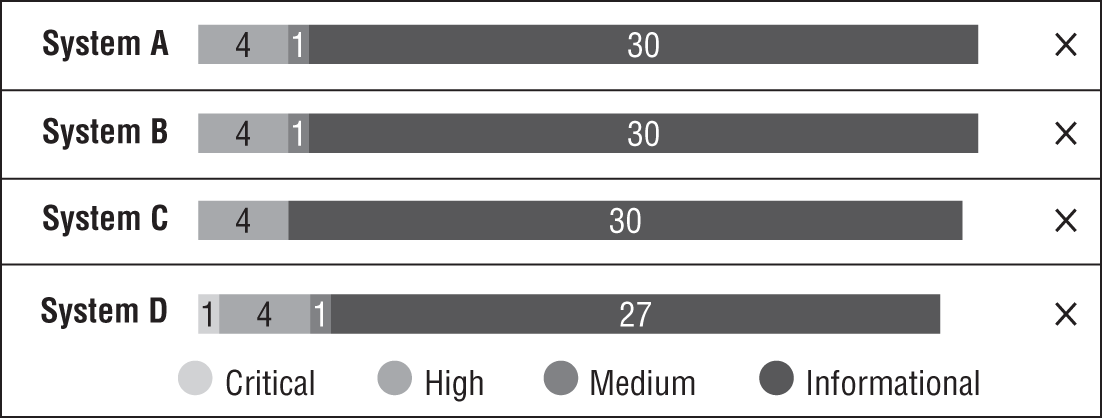
- A
- B
- C
- D
- Victor is configuring a new vulnerability scanner. He set the scanner to run scans of his entire datacenter each evening. When he went to check the scan reports at the end of the week, he found that they were all incomplete. The scan reports noted the error “Scan terminated due to start of preempting job.” Victor has no funds remaining to invest in the vulnerability scanning system. He does want to cover the entire datacenter. What should he do to ensure that scans complete?
- Reduce the number of systems scanned.
- Increase the number of scanners.
- Upgrade the scanner hardware.
- Reduce the scanning frequency.
- Vanessa ran a vulnerability scan of a server and received the results shown here. Her boss instructed her to prioritize remediation based on criticality. Which issue should she address first?

- Remove the POP server.
- Remove the FTP server.
- Upgrade the web server.
- Remove insecure cryptographic protocols.
- Terry is reviewing a vulnerability scan of a Windows server and came across the vulnerability shown here. What is the risk presented by this vulnerability?

- An attacker may be able to execute a buffer overflow and execute arbitrary code on the server.
- An attacker may be able to conduct a denial-of-service attack against this server.
- An attacker may be able to determine the operating system version on this server.
- There is no direct vulnerability, but this information points to other possible vulnerabilities on the server.
- Andrea recently discovered the vulnerability shown here on the workstation belonging to a system administrator in her organization. What is the major likely threat that should concern Andrea?
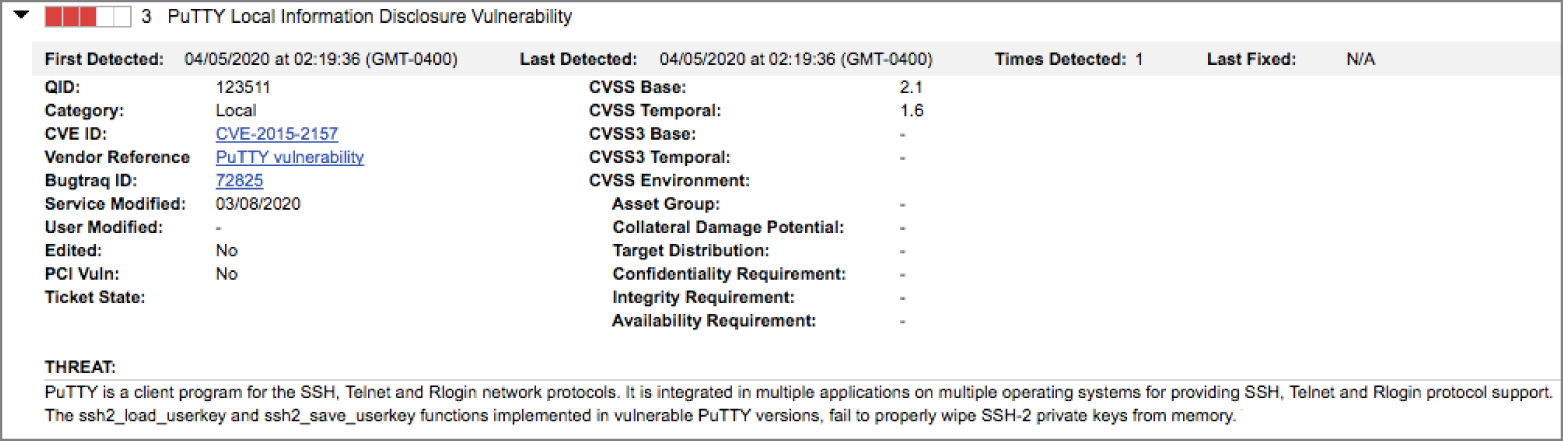
- An attacker could exploit this vulnerability to take control of the administrator's workstation.
- An attacker could exploit this vulnerability to gain access to servers managed by the administrator.
- An attacker could exploit this vulnerability to prevent the administrator from using the workstation.
- An attacker could exploit this vulnerability to decrypt sensitive information stored on the administrator's workstation.
- Avik recently conducted a PCI DSS vulnerability scan of a web server and noted a critical PHP vulnerability that required an upgrade to correct. She applied the update. How soon must Avik repeat the scan?
- Within 30 days
- At the next scheduled quarterly scan
- At the next scheduled annual scan
- Immediately
- Chandra's organization recently upgraded the firewall protecting the network where they process credit card information. This network is subject to the provisions of PCI DSS. When is Chandra required to schedule the next vulnerability scan of this network?
- Immediately
- Within one month
- Before the start of next month
- Before the end of the quarter following the upgrade
- Fahad is concerned about the security of an industrial control system (ICS) that his organization uses to monitor and manage systems in their factories. He would like to reduce the risk of an attacker penetrating this system. Which one of the following security controls would best mitigate the vulnerabilities in this type of system?
- Network segmentation
- Input validation
- Memory protection
- Redundancy
- Raphael discovered during a vulnerability scan that an administrative interface to one of his storage systems was inadvertently exposed to the Internet. He is reviewing firewall logs and would like to determine whether any access attempts came from external sources. Which one of the following IP addresses reflects an external source?
- 10.15.1.100
- 12.8.1.100
- 172.16.1.100
- 192.168.1.100
- Nick is configuring vulnerability scans for his network using a third-party vulnerability scanning service. He is attempting to scan a web server that he knows exposes a CIFS file share and contains several significant vulnerabilities. However, the scan results only show ports 80 and 443 as open. What is the most likely cause of these scan results?
- The CIFS file share is running on port 443.
- A firewall configuration is preventing the scan from succeeding.
- The scanner configuration is preventing the scan from succeeding.
- The CIFS file share is running on port 80.
- Thomas learned this morning of a critical security flaw that affects a major service used by his organization and requires immediate patching. This flaw was the subject of news reports and is being actively exploited. Thomas has a patch and informed stakeholders of the issue and received permission to apply the patch during business hours. How should he handle the change management process?
- Thomas should apply the patch and then follow up with an emergency change request after work is complete.
- Thomas should initiate a standard change request but apply the patch before waiting for approval.
- Thomas should work through the standard change approval process and wait until it is complete to apply the patch.
- Thomas should file an emergency change request and wait until it is approved to apply the patch.
- After running a vulnerability scan of systems in his organization's development shop, Mike discovers the issue shown here on several systems. What is the best solution to this vulnerability?
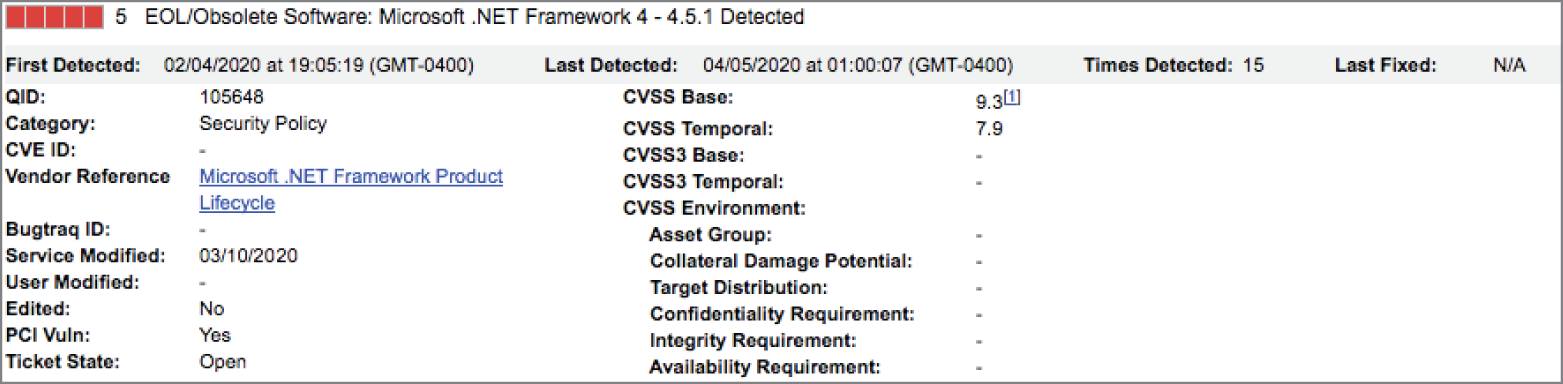
- Apply the required security patches to this framework.
- Remove this framework from the affected systems.
- Upgrade the operating system of the affected systems.
- No action is necessary.
- Tran is preparing to conduct vulnerability scans against a set of workstations in his organization. He is particularly concerned about system configuration settings. Which one of the following scan types will give him the best results?
- Unauthenticated scan
- Credentialed scan
- External scan
- Internal scan
- Brian is configuring a vulnerability scan of all servers in his organization's datacenter. He is configuring the scan to detect only the highest-severity vulnerabilities. He would like to empower system administrators to correct issues on their servers but also have some insight into the status of those remediations. Which approach would best serve Brian's interests?
- Give the administrators access to view the scans in the vulnerability scanning system.
- Send email alerts to administrators when the scans detect a new vulnerability on their servers.
- Configure the vulnerability scanner to open a trouble ticket when they detect a new vulnerability on a server.
- Configure the scanner to send reports to Brian who can notify administrators and track them in a spreadsheet.
- Xiu Ying is configuring a new vulnerability scanner for use in her organization's datacenter. Which one of the following values is considered a best practice for the scanner's update frequency?
- Daily
- Weekly
- Monthly
- Quarterly
- Ben’s manager recently assigned him to begin the remediation work on the most vulnerable server in his organization. A portion of the scan report appears here. What remediation action should Ben take first?
- Install patches for Adobe Flash.
- Install patches for Firefox.
- Run Windows Update.
- Remove obsolete software.

- Zhang Wei completed a vulnerability scan of his organization's virtualization platform from an external host and discovered the vulnerability shown here. How should he react?
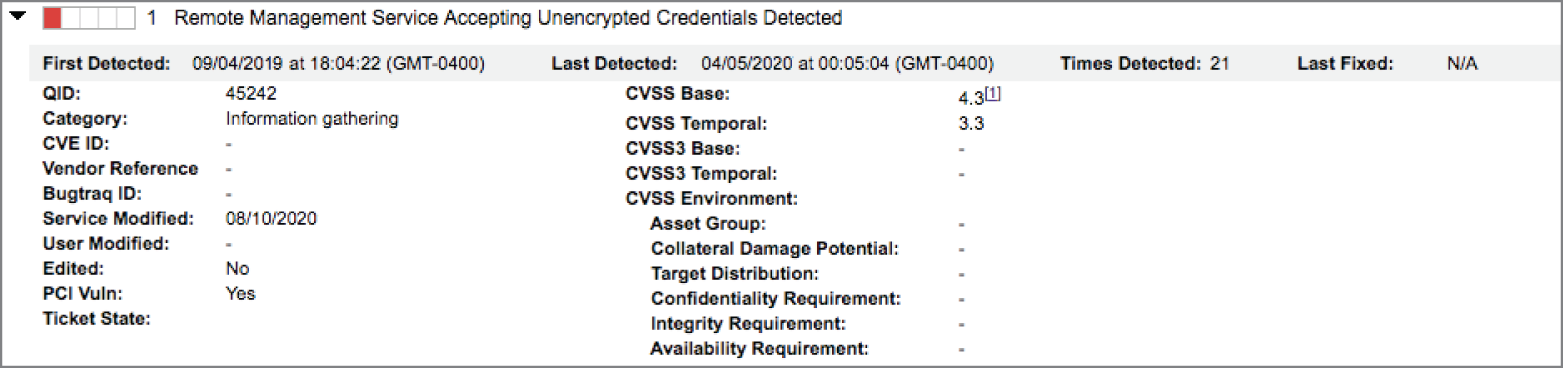
- This is a critical issue that requires immediate adjustment of firewall rules.
- This issue has a very low severity and does not require remediation.
- This issue should be corrected as time permits.
- This is a critical issue, and Zhang Wei should shut down the platform until it is corrected.
- Elliott runs a vulnerability scan of one of the servers belonging to his organization and finds the results shown here. Which one of these statements is not correct?
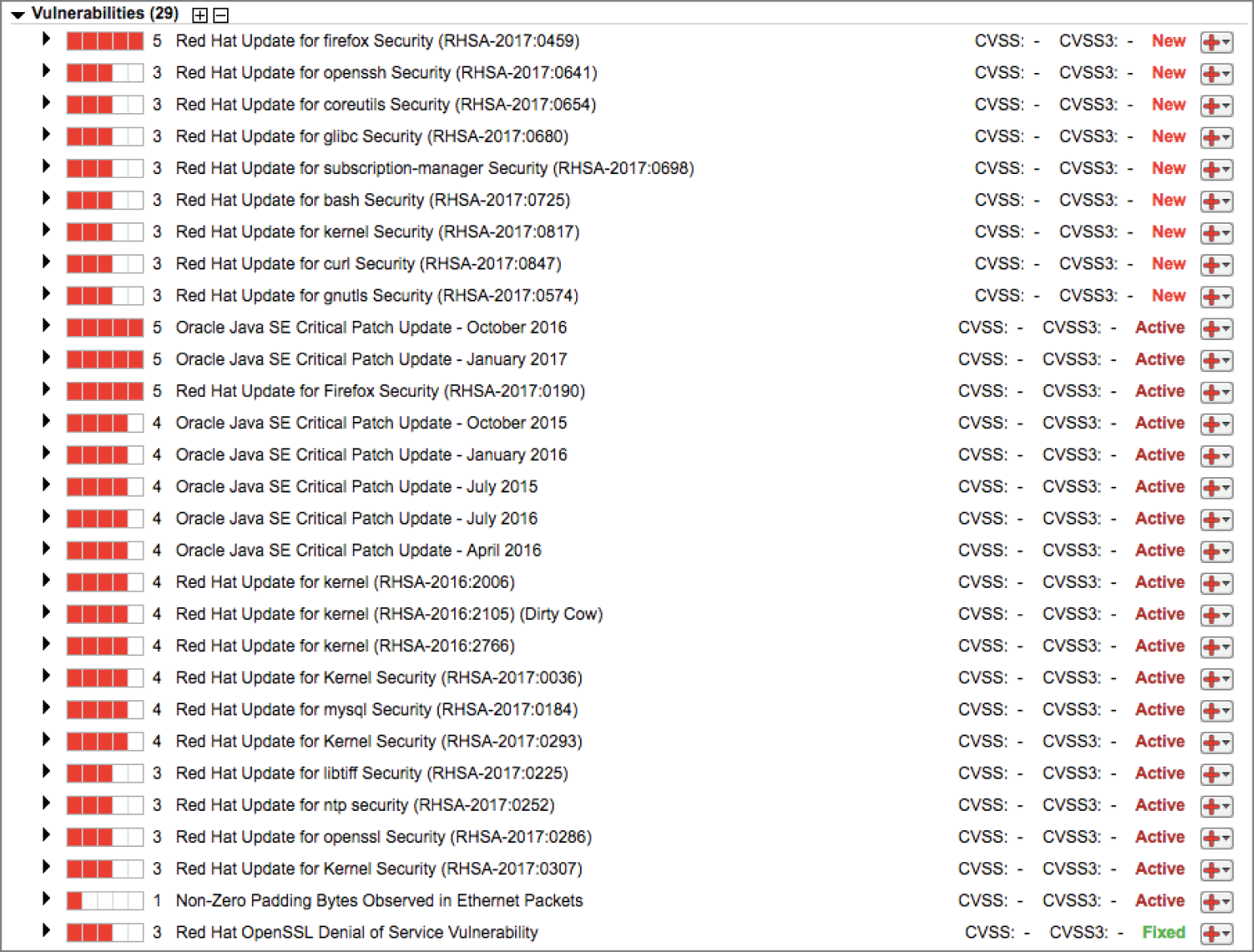
- This server requires one or more Linux patches.
- This server requires one or more Oracle database patches.
- This server requires one or more Firefox patches.
- This server requires one or more MySQL patches.
- Tom runs a vulnerability scan of the file server shown here.

He receives the vulnerability report shown next. Assuming that the firewall is configured properly, what action should Tom take immediately?
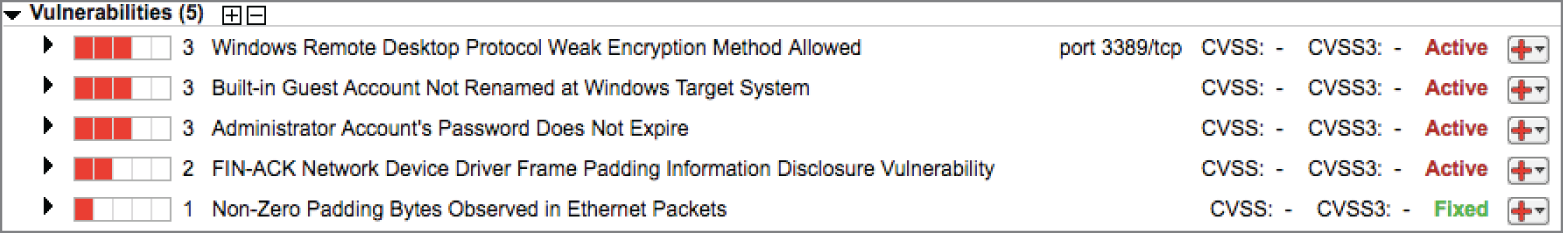
- Block RDP access to this server from all hosts.
- Review and secure server accounts.
- Upgrade encryption on the server.
- No action is required.
- Dave is running a vulnerability scan of a client's network for the first time. The client has never run such a scan and expects to find many results. What security control is likely to remediate the largest portion of the vulnerabilities discovered in Dave's scan?
- Input validation
- Patching
- Intrusion prevention systems
- Encryption
- Kai is planning to patch a production system to correct a vulnerability detected during a scan. What process should she follow to correct the vulnerability but minimize the risk of a system failure?
- Kai should deploy the patch immediately on the production system.
- Kai should wait 60 days to deploy the patch to determine whether bugs are reported.
- Kai should deploy the patch in a sandbox environment to test it prior to applying it in production.
- Kai should contact the vendor to determine a safe timeframe for deploying the patch in production.
- Given no other information, which one of the following vulnerabilities would you consider the greatest threat to information confidentiality?
- HTTP TRACE/TRACK methods enabled
- SSL Server with SSL v3 enabled vulnerability
- phpinfo information disclosure vulnerability
- Web application SQL injection vulnerability
- Ling recently completed the security analysis of a web browser deployed on systems in her organization and discovered that it is susceptible to a zero-day integer overflow attack. Who is in the best position to remediate this vulnerability in a manner that allows continued use of the browser?
- Ling
- The browser developer
- The network administrator
- The domain administrator
- Jeff's team is preparing to deploy a new database service, and he runs a vulnerability scan of the test environment. This scan results in the four vulnerability reports shown here. Jeff is primarily concerned with correcting issues that may lead to a confidentiality breach. Which vulnerability should Jeff remediate first?
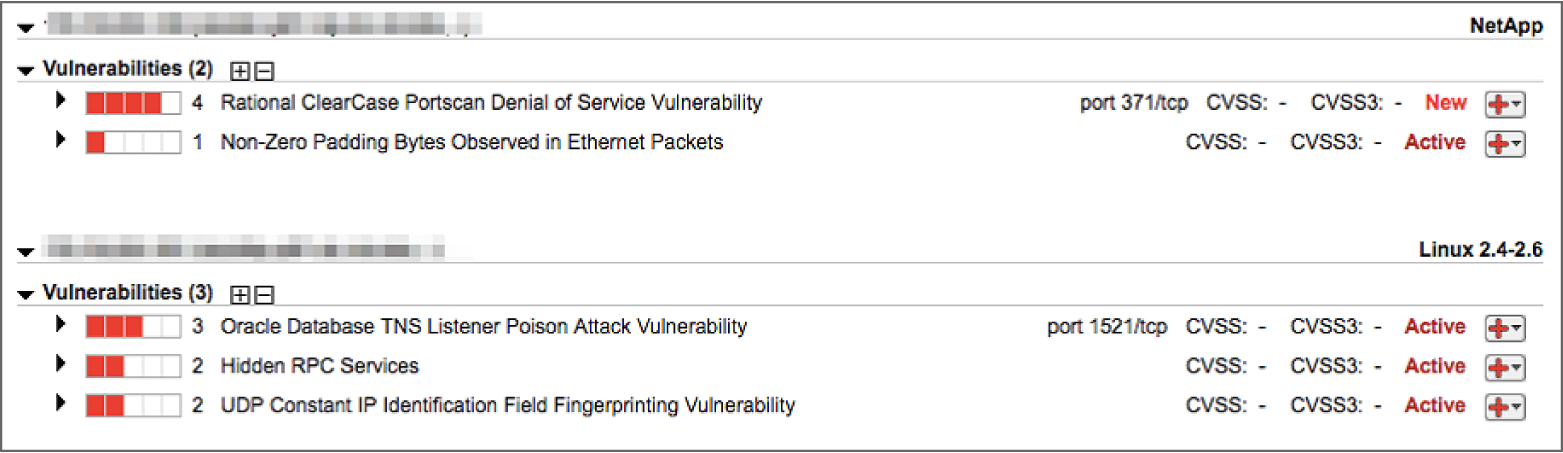
- Rational ClearCase Portscan Denial of Service vulnerability
- Non-Zero Padding Bytes Observed in Ethernet Packets
- Oracle Database TNS Listener Poison Attack vulnerability
- Hidden RPC Services
- Eric is a security consultant and is trying to sell his services to a new client. He would like to run a vulnerability scan of their network prior to their initial meeting to show the client the need for added security. What is the most significant problem with this approach?
- Eric does not know the client's infrastructure design.
- Eric does not have permission to perform the scan.
- Eric does not know what operating systems and applications are in use.
- Eric does not know the IP range of the client's systems.
- Renee is assessing the exposure of her organization to the denial-of-service vulnerability in the scan report shown here. She is specifically interested in determining whether an external attacker would be able to exploit the denial-of-service vulnerability. Which one of the following sources of information would provide her with the best information to complete this assessment?

- Server logs
- Firewall rules
- IDS configuration
- DLP configuration
- Mary is trying to determine what systems in her organization should be subject to vulnerability scanning. She would like to base this decision on the criticality of the system to business operations. Where should Mary turn to best find this information?
- The CEO
- System names
- IP addresses
- Asset inventory
- Paul ran a vulnerability scan of his vulnerability scanner and received the result shown here. What is the simplest fix to this issue?
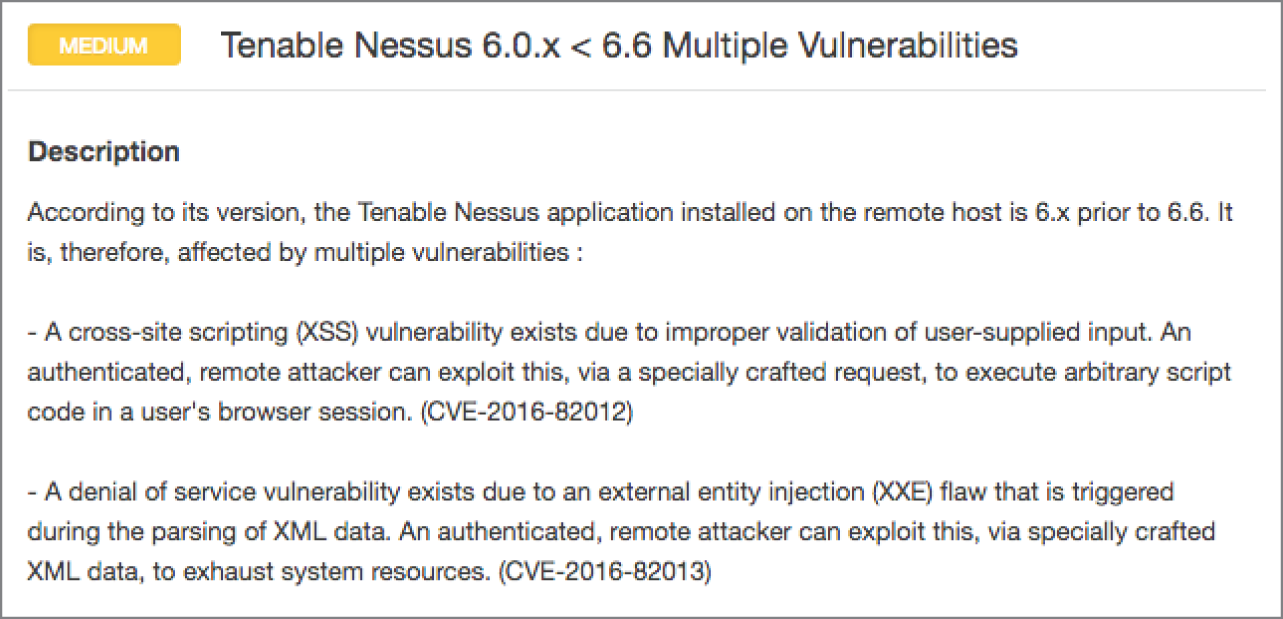
- Upgrade Nessus.
- Remove guest accounts.
- Implement TLS encryption.
- Renew the server certificate.
- Kamea is designing a vulnerability management system for her organization. Her highest priority is conserving network bandwidth. She does not have the ability to alter the configuration or applications installed on target systems. What solution would work best in Kamea's environment to provide vulnerability reports?
- Agent-based scanning
- Server-based scanning
- Passive network monitoring
- Port scanning
- Aki is conducting a vulnerability scan when he receives a report that the scan is slowing down the network for other users. He looks at the performance configuration settings shown here. Which setting would be most likely to correct the issue?

- Enable safe checks.
- Stop scanning hosts that become unresponsive during the scan.
- Scan IP addresses in random order.
- Max simultaneous hosts per scan.
- Laura received a vendor security bulletin that describes a zero-day vulnerability in her organization's main database server. This server is on a private network but is used by publicly accessible web applications. The vulnerability allows the decryption of administrative connections to the server. What reasonable action can Laura take to address this issue as quickly as possible?
- Apply a vendor patch that resolves the issue.
- Disable all administrative access to the database server.
- Require VPN access for remote connections to the database server.
- Verify that the web applications use strong encryption.
- Emily discovered the vulnerability shown here on a server running in her organization. What is the most likely underlying cause for this vulnerability?
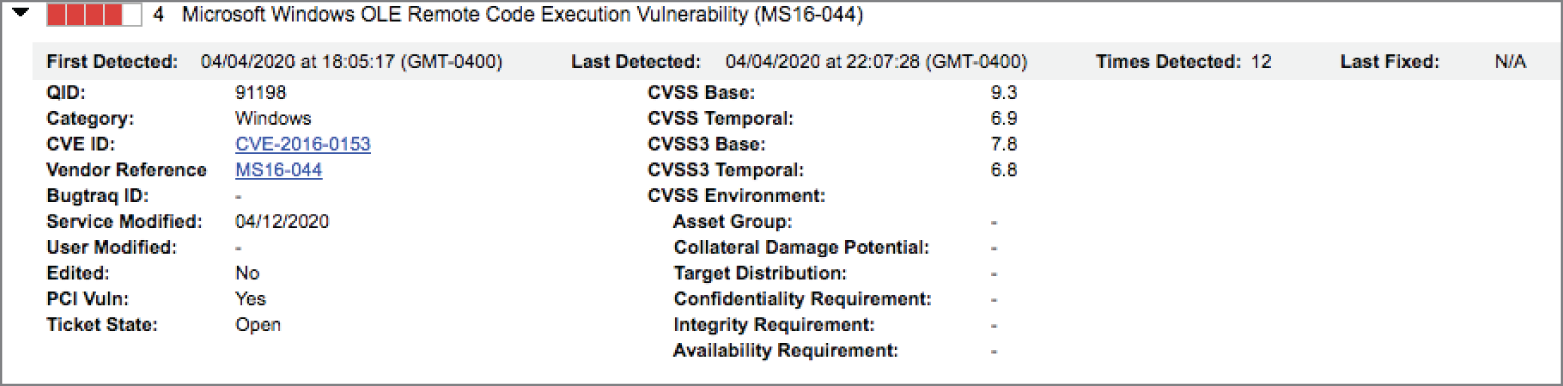
- Failure to perform input validation
- Failure to use strong passwords
- Failure to encrypt communications
- Failure to install antimalware software
- Rex recently ran a vulnerability scan of his organization's network and received the results shown here. He would like to remediate the server with the highest number of the most serious vulnerabilities first. Which one of the following servers should be on his highest priority list?

- 10.0.102.58
- 10.0.16.58
- 10.0.46.116
- 10.0.69.232
- Abella is configuring a vulnerability scanning tool. She recently learned about a privilege escalation vulnerability that requires the user already have local access to the system. She would like to ensure that her scanners are able to detect this vulnerability as well as future similar vulnerabilities. What action can she take that would best improve the scanner's ability to detect this type of issue?
- Enable credentialed scanning.
- Run a manual vulnerability feed update.
- Increase scanning frequency.
- Change the organization's risk appetite.
- Kylie reviewed the vulnerability scan report for a web server and found that it has multiple SQL injection and cross-site scripting vulnerabilities. What would be the least difficult way for Kylie to address these issues?
- Install a web application firewall.
- Recode the web application to include input validation.
- Apply security patches to the server operating system.
- Apply security patches to the web server service.
- Karen ran a vulnerability scan of a web server used on her organization's internal network. She received the report shown here. What circumstances would lead Karen to dismiss this vulnerability as a false positive?
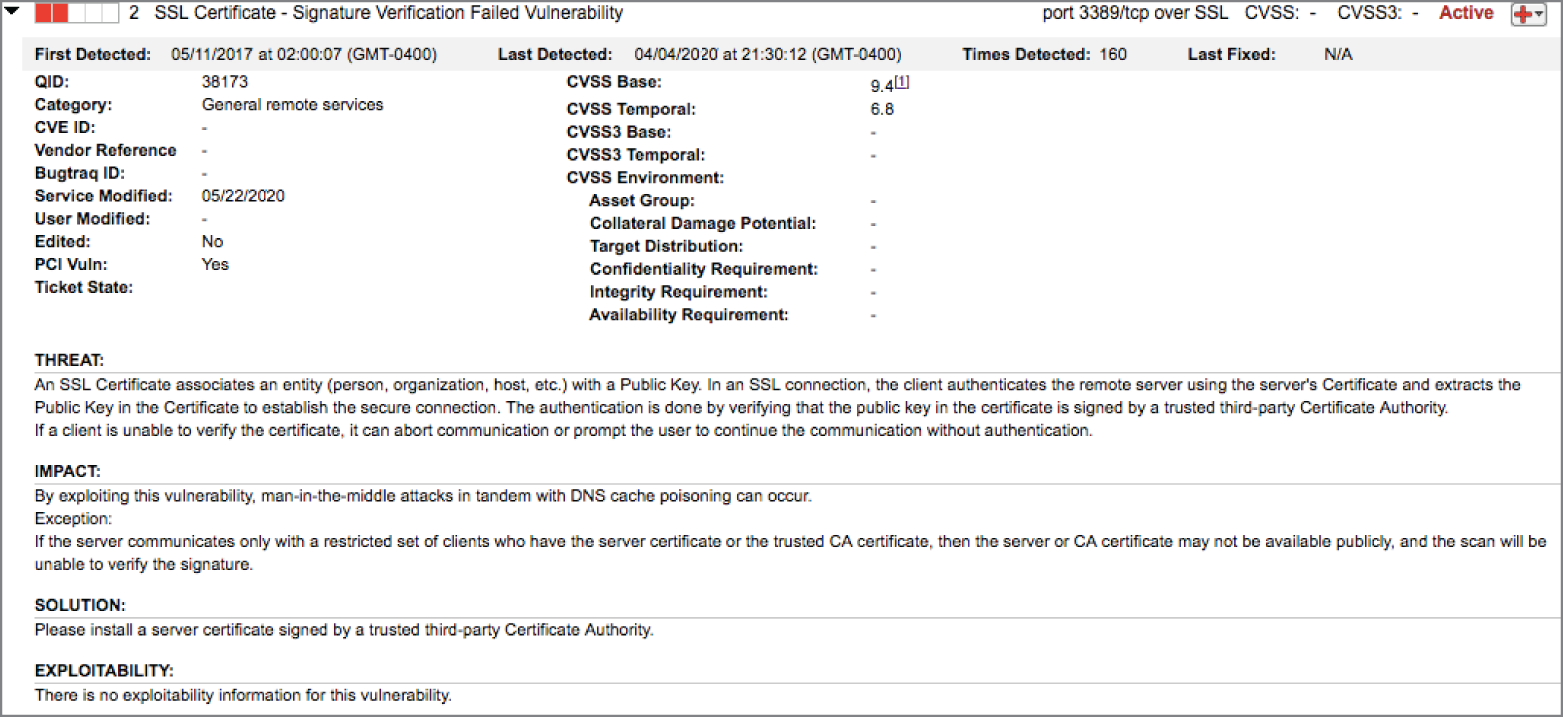
- The server is running SSL v2.
- The server is running SSL v3.
- The server is for internal use only.
- The server does not contain sensitive information.
- Which one of the following vulnerabilities is the most difficult to confirm with an external vulnerability scan?
- Cross-site scripting
- Cross-site request forgery
- Blind SQL injection
- Unpatched web server
- Holly ran a scan of a server in her datacenter, and the most serious result was the vulnerability shown here. What action is most commonly taken to remediate this vulnerability?
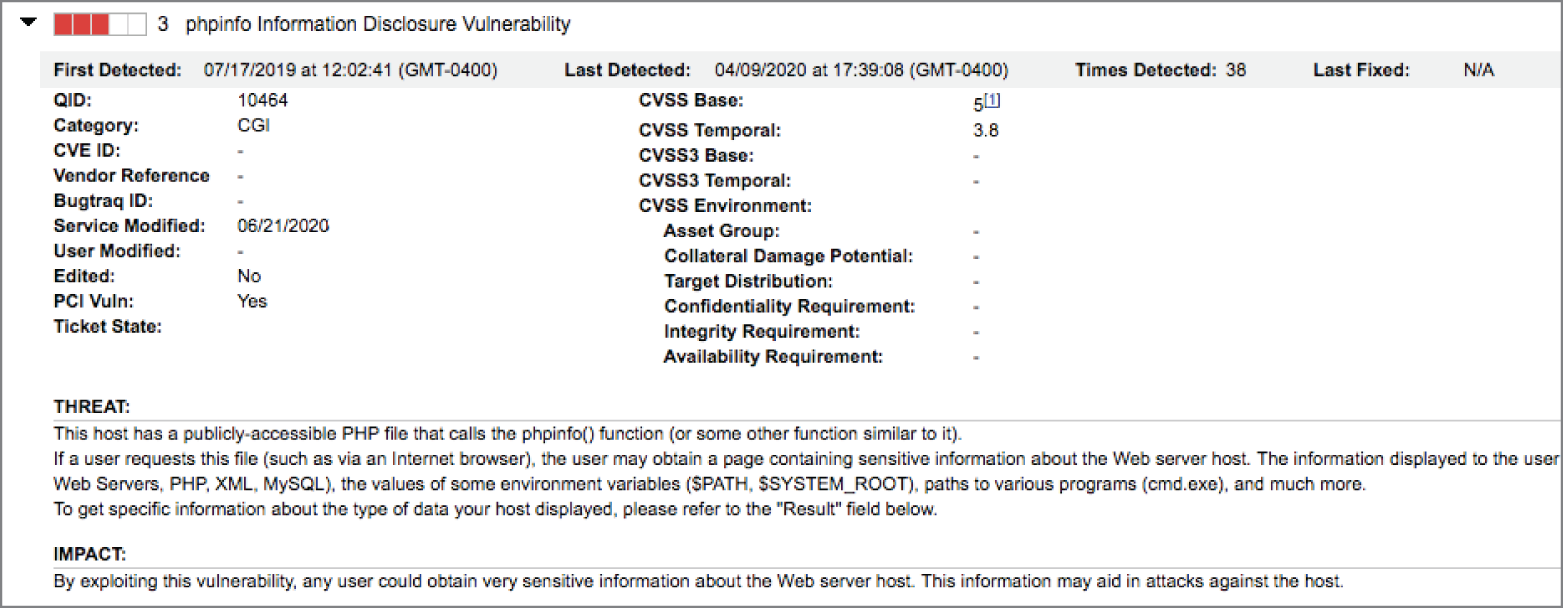
- Remove the file from the server.
- Edit the file to limit information disclosure.
- Password protect the file.
- Limit file access to a specific IP range.
- During a recent vulnerability scan, Mark discovered a flaw in an internal web application that allows cross-site scripting attacks. He spoke with the manager of the team responsible for that application and was informed that he discovered a known vulnerability and the manager worked with other leaders and determined that the risk is acceptable and does not require remediation. What should Mark do?
- Object to the manager's approach and insist on remediation.
- Mark the vulnerability as a false positive.
- Schedule the vulnerability for remediation in six months.
- Mark the vulnerability as an exception.
- Jacquelyn recently read about a new vulnerability in Apache web servers that allows attackers to execute arbitrary code from a remote location. She verified that her servers have this vulnerability, but this morning's OpenVAS vulnerability scan report shows that the servers are secure. She contacted the vendor and determined that they have released a signature for this vulnerability and it is working properly at other clients. What action can Jacquelyn take that will most likely address the problem efficiently?
- Add the web servers to the scan.
- Reboot the vulnerability scanner.
- Update the vulnerability feed.
- Wait until tomorrow's scan.
- Sharon is designing a new vulnerability scanning system for her organization. She must scan a network that contains hundreds of unmanaged hosts. Which of the following techniques would be most effective at detecting system configuration issues in her environment?
- Agent-based scanning
- Credentialed scanning
- Server-based scanning
- Passive network monitoring
Use the following scenario to answer questions 184–186.
Arlene ran a vulnerability scan of a VPN server used by contractors and employees to gain access to her organization's network. An external scan of the server found the vulnerability shown here.

- Which one of the following hash algorithms would not trigger this vulnerability?
- MD4
- MD5
- SHA-1
- SHA-256
- What is the most likely result of failing to correct this vulnerability?
- All users will be able to access the site.
- All users will be able to access the site, but some may see an error message.
- Some users will be unable to access the site.
- All users will be unable to access the site.
- How can Arlene correct this vulnerability?
- Reconfigure the VPN server to only use secure hash functions.
- Request a new certificate.
- Change the domain name of the server.
- Implement an intrusion prevention system.
- After reviewing the results of a vulnerability scan, Bruce discovered that many of the servers in his organization are susceptible to a brute-force SSH attack. He would like to determine what external hosts attempted SSH connections to his servers and is reviewing firewall logs. What TCP port would relevant traffic most likely use?
- 22
- 636
- 1433
- 1521
- Joaquin runs a vulnerability scan of the network devices in his organization and sees the vulnerability report shown here for one of those devices. What action should he take?

- No action is necessary because this is an informational report.
- Upgrade the version of the certificate.
- Replace the certificate.
- Verify that the correct ciphers are being used.
- Lori is studying vulnerability scanning as she prepares for the CySA+ exam. Which of the following is not one of the principles she should observe when preparing for the exam to avoid causing issues for her organization?
- Run only nondangerous scans on production systems to avoid disrupting a production service.
- Run scans in a quiet manner without alerting other IT staff to the scans or their results to minimize the impact of false information.
- Limit the bandwidth consumed by scans to avoid overwhelming an active network link.
- Run scans outside of periods of critical activity to avoid disrupting the business.
- Meredith is configuring a vulnerability scan and would like to configure the scanner to perform credentialed scans. Of the menu options shown here, which will allow her to directly configure this capability?
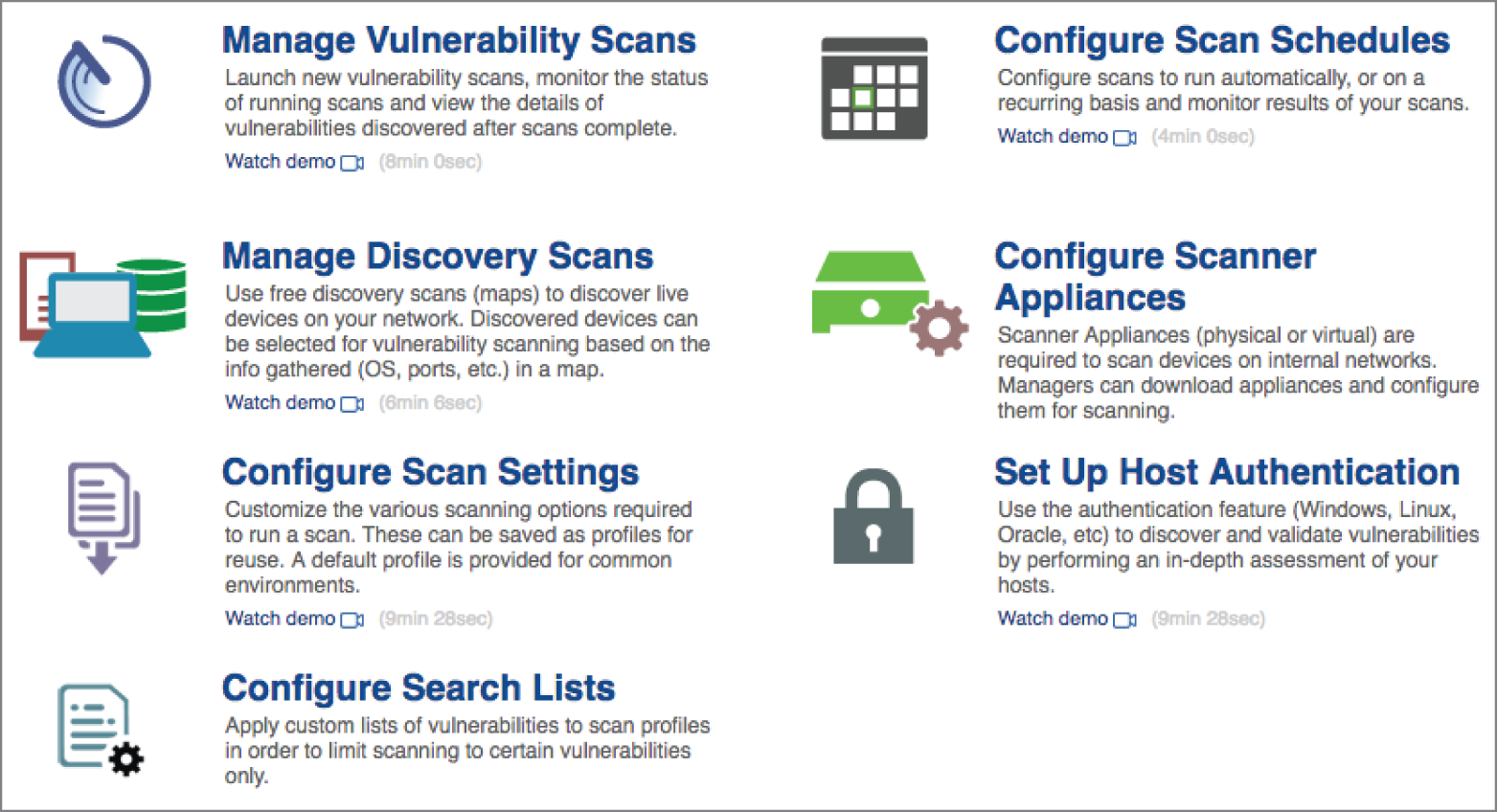
- Manage Discovery Scans
- Configure Scan Settings
- Configure Search Lists
- Set Up Host Authentication
- Norman is working with his manager to implement a vulnerability management program for his company. His manager tells him that he should focus on remediating critical and high-severity risks and that the organization does not want to spend time worrying about risks rated medium or lower. What type of criteria is Norman's manager using to make this decision?
- Risk appetite
- False positive
- False negative
- Data classification
- Sara's organization has a well-managed test environment. What is the most likely issue that Sara will face when attempting to evaluate the impact of a vulnerability remediation by first deploying it in the test environment?
- Test systems are not available for all production systems.
- Production systems require a different type of patch than test systems.
- Significant configuration differences exist between test and production systems.
- Test systems are running different operating systems than production systems.
- How many vulnerabilities listed in the report shown here are significant enough to warrant immediate remediation in a typical operating environment?

- 22
- 14
- 5
- 0
- Which one of the following types of data is subject to regulations in the United States that specify the minimum frequency of vulnerability scanning?
- Driver's license numbers
- Insurance records
- Credit card data
- Medical records
- Chang is responsible for managing his organization's vulnerability scanning program. He is experiencing issues with scans aborting because the previous day's scans are still running when the scanner attempts to start the current day's scans. Which one of the following solutions is least likely to resolve Chang's issue?
- Add a new scanner.
- Reduce the scope of the scans.
- Reduce the sensitivity of the scans.
- Reduce the frequency of the scans.
- Bhanu is scheduling vulnerability scans for her organization's datacenter. Which one of the following is a best practice that Bhanu should follow when scheduling scans?
- Schedule scans so that they are spread evenly throughout the day.
- Schedule scans so that they run during periods of low activity.
- Schedule scans so that they all begin at the same time.
- Schedule scans so that they run during periods of peak activity to simulate performance under load.
- Alan recently reviewed a vulnerability report and determined that an insecure direct object reference vulnerability existed on the system. He implemented a remediation to correct the vulnerability. After doing so, he verifies that his actions correctly mitigated the vulnerability. What term best describes the initial vulnerability report?
- True positive
- True negative
- False positive
- False negative
- Gwen is reviewing a vulnerability report and discovers that an internal system contains a serious flaw. After reviewing the issue with her manager, they decide that the system is sufficiently isolated and they will take no further action. What risk management strategy are they adopting?
- Risk avoidance
- Risk mitigation
- Risk transference
- Risk acceptance
Use the following scenario for questions 199–201.
Mike is in charge of the software testing process for his company. They perform a complete set of tests for each product throughout its life span. Use your knowledge of software assessment methods to answer the following questions.
- A new web application has been written by the development team in Mike's company. They used an Agile process and built a tool that fits all of the user stories that the participants from the division that asked for the application outlined. If they want to ensure that the functionality is appropriate for all users in the division, what type of testing should Mike perform?
- Stress testing
- Regression testing
- Static testing
- User acceptance testing
- Mike's development team wants to expand the use of the software to the whole company, but they are concerned about its performance. What type of testing should they conduct to ensure that the software will not fail under load?
- Stress testing
- Regression testing
- Static testing
- User acceptance testing
- Two years after deployment, Mike's team is ready to roll out a major upgrade to their web application. They have pulled code from the repository that it was checked into but are worried that old bugs may have been reintroduced because they restored additional functionality based on older code that had been removed in a release a year ago. What type of testing does Mike's team need to perform?
- Stress testing
- Regression testing
- Static testing
- User acceptance testing
- Padma is evaluating the security of an application developed within her organization. She would like to assess the application's security by supplying it with invalid inputs. What technique is Padma planning to use?
- Fault injection
- Stress testing
- Mutation testing
- Fuzz testing
- Which software development life cycle model is illustrated in the image?
- Waterfall
- Spiral
- Agile
- RAD
- The Open Worldwide Application Security Project (OWASP) maintains an application called Orizon. This application reviews Java classes and identifies potential security flaws. What type of tool is Orizon?
- Fuzzer
- Static code analyzer
- Web application assessor
- Fault injector
- Barney's organization mandates fuzz testing for all applications before deploying them into production. Which one of the following issues is this testing methodology most likely to detect?
- Incorrect firewall rules
- Unvalidated input
- Missing operating system patches
- Unencrypted data transmission
- Mia would like to ensure that her organization's cybersecurity team reviews the architecture of a new ERP application that is under development. During which SDLC phase should Mia expect the security architecture to be completed?
- Analysis and Requirements Definition
- Design
- Development
- Testing and Integration
- Which one of the following security activities is not normally a component of the Operations and Maintenance phase of the SDLC?
- Vulnerability scans
- Disposition
- Patching
- Regression testing
Use the following scenario for questions 208–210.
Olivia has been put in charge of performing code reviews for her organization and needs to determine which code analysis models make the most sense based on specific needs her organization has. Use your knowledge of code analysis techniques to answer the following questions.
- Olivia's security team has identified potential malicious code that has been uploaded to a webserver. If she wants to review the code without running it, what technique should she use?
- Dynamic analysis
- Fagan analysis
- Regression analysis
- Static analysis
- Olivia's next task is to test the code for a new mobile application. She needs to test it by executing the code and intends to provide the application with input based on testing scenarios created by the development team as part of their design work. What type of testing will Olivia conduct?
- Dynamic analysis
- Fagan analysis
- Regression analysis
- Static analysis
- After completing the first round of tests for her organization's mobile application, Olivia has discovered indications that the application may not handle unexpected data well. What type of testing should she conduct if she wants to test it using an automated tool that will check for this issue?
- Fault injection
- Fagan testing
- Fuzzing
- Failure injection
- Which one of the following characters would not signal a potential security issue during the validation of user input to a web application?
<'>$
- The Open Worldwide Application Security Project (OWASP) maintains a listing of the most important web application security controls. Which one of these items is least likely to appear on that list?
- Implement identity and authentication controls.
- Implement appropriate access controls.
- Obscure web interface locations.
- Leverage security frameworks and libraries.
- Kyle is developing a web application that uses a database back end. He is concerned about the possibility of an SQL injection attack against his application and is consulting the OWASP proactive security controls list to identify appropriate controls. Which one of the following OWASP controls is least likely to prevent a SQL injection attack?
- Parameterize queries.
- Validate all input.
- Encode data.
- Implement logging and intrusion detection.
- Jill's organization has adopted an asset management tool. If she wants to identify systems on the network based on a unique identifier per machine that will not normally change over time, which of the following options can she use for network-based discovery?
- IP address
- Hostname
- MAC address
- None of the above
- Which software development methodology is illustrated in the diagram?
- Spiral
- RAD
- Agile
- Waterfall
- Claire knows that a web application that her organization needs to have in production has vulnerabilities due to a recent scan using a web application security scanner. What is her best protection option if she knows that the vulnerability is a known SQL injection flaw?
- A firewall
- An IDS
- A WAF
- DLP
Use the following scenario to answer questions 217–219.
Donna has been assigned as the security lead for a DevSecOps team building a new web application. As part of the effort, she has to oversee the security practices that the team will use to protect the application. Use your knowledge of secure coding practices to help Donna guide her team through this process.
- A member of Donna's team recommends building a blocklist to avoid dangerous characters like
'and<script>tags. How could attackers bypass a blocklist that individually identified those characters?- They can use a binary attack.
- They can use alternate encodings.
- They can use different characters with the same meaning.
- The characters could be used together to avoid the blocklist.
- The design of the application calls for client-side validation of input. What type of tool could an attacker use to bypass this?
- An XSS injector
- A web proxy
- A JSON interpreter
- A SQL injector
- A member of Donna's security team suggests that output encoding should also be considered. What type of attack is the team member most likely attempting to prevent?
- Cross-site scripting
- SQL injection
- Cross-site request forgery
- All of the above
- Nathan downloads a BIOS/UEFI update from Dell's website, and when he attempts to install it on the PC, he receives an error that the hash of the download does not match the hash stored on Dell's servers. What type of protection is this?
- Full-disk encryption
- Firmware protection
- Operating system protection
- None of the above
- What practice is typical in a DevSecOps organization as part of a CI/CD pipeline?
- Automating some security gates
- Programmatic implementation of zero-day vulnerabilities
- Using security practitioners to control the flow of the CI/CD pipeline
- Removing security features from the IDE
- Valerie wants to prevent potential cross-site scripting attacks from being executed when previously entered information is displayed in user's browsers. What technique should she use to prevent this?
- A firewall
- A HIDS
- Output encoding
- String randomization
- While developing a web application, Chris sets his session ID length to 128 bits based on OWASP's recommended session management standards. What reason would he have for needing such a long session ID?
- To avoid duplication
- To allow for a large group of users
- To prevent brute-forcing
- All of the above
- Robert is reviewing a web application, and the developers have offered four different responses to incorrect logins. Which of the following four responses is the most secure option?
- Login failed for user; invalid password
- Login failed; invalid user ID or password
- Login failed; invalid user ID
- Login failed; account does not exist
- Nathan is reviewing PHP code for his organization and finds the following code in the application he is assessing. What technique is the developer using?
$stmt = $dbh->prepare(“INSERT INTO REGISTRY (var1, var2) VALUES (:var1, :var2)”);$stmt->bindParam(‘:var1’, $var1);$stmt->bindParam(‘:var2’, $var2);- Dynamic binding
- Parameterized queries
- Variable limitation
- None of the above
- Christina wants to check the firmware she has been provided to ensure that it is the same firmware that the manufacturer provides. What process should she follow to validate that the firmware is trusted firmware?
- Download the same file from the manufacturer and compare file size.
- Compare a hash of the file to a hash provided by the manufacturer.
- Run strings against the firmware to find any evidence of tempering.
- Submit the firmware to a malware scanning site to verify that it does not contain malware.
- What type of attack is the use of query parameterization intended to prevent?
- Buffer overflows
- Cross-site scripting
- SQL injection
- Denial-of-service attacks
- What type of attack is output encoding typically used against?
- DoS
- XSS
- XML
- DDoS
Use the following scenario for questions 229–231.
Scott has been asked to select a software development model for his organization and knows that there are a number of models that may make sense for what he has been asked to accomplish. Use your knowledge of SDLC models to identify an appropriate model for each of the following requirements.
- Scott's organization needs basic functionality of the effort to become available as soon as possible and wants to involve the teams that will use it heavily to ensure that their needs are met. What model should Scott recommend?
- Waterfall
- Spiral
- Agile
- Rapid Application Development
- A parallel coding effort needs to occur; however, this effort involves a very complex system and errors could endanger human lives. The system involves medical records and drug dosages, and the organization values stability and accuracy over speed. Scott knows the organization often adds design constraints throughout the process and that the model he selects must also deal with that need. What model should he choose?
- Waterfall
- Spiral
- Agile
- Rapid Application Development
- At the end of his development cycle, what SDLC phase will Scott enter as the new application is installed and replaces the old code?
- User acceptance testing
- Testing and integration
- Disposition
- Redesign
- The OWASP Session Management Cheatsheet advises that session IDs are meaningless and recommends that they should be used only as an identifier on the client side. Why should a session ID not have additional information encoded in it like the IP address of the client, their username, or other information?
- Processing complex session IDs will slow down the service.
- Session IDs cannot contain this information for legal reasons.
- Session IDs are sent to multiple different users, which would result in a data breach.
- Session IDs could be decoded, resulting in data leakage.
- Bounds checking, removing special characters, and forcing strings to match a limited set of options are all examples of what web application security technique?
- SQL injection prevention
- Input validation
- XSS prevention
- Fuzzing
- Abigail is performing input validation against an input field and uses the following regular expression:
^(AA|AE|AP|AL|AK|AS|AZ|AR|CA|CO|CT|DE|DC|FM|FL|GA|GU|HI|ID|IL|IN|IA|KS|KY|LA|ME|MH|MD|MA|MI|MN|MS|MO|MT|NE|NV|NH|NJ|NM|NY|NC|ND|MP|OH|OK|OR|PW|PA|PR|RI|SC|SD|TN|TX|UT|VT|VI|VA|WA|WV|WI|WY)$What is she checking with the regular expression?
- She is removing all typical special characters found in SQL injection.
- She is checking for all U.S. state names.
- She is removing all typical special characters for cross-site scripting attacks.
- She is checking for all U.S. state name abbreviations.
- Jennifer uses an application to send randomized data to her application to determine how it responds to unexpected input. What type of tool is she using?
- A UAT tool
- A stress testing tool
- A fuzzer
- A regression testing tool
- Greg wants to prevent SQL injection in a web application he is responsible for. Which of the following is not a common defense against SQL injection?
- Prepared statements with parameterized queries
- Output validation
- Stored procedures
- Escaping all user-supplied input
- While reviewing code that generates a SQL query, Aarav notices that the “address” field is appended to the query without input validation or other techniques applied. What type of attack is most likely to be successful against code like this?
- DoS
- XSS
- SQL injection
- Teardrop
Use the following diagram and scenario for questions 238–240.
Amanda has been assigned to lead the development of a new web application for her organization. She is following a standard SDLC model as shown here. Use the model and your knowledge of the software development life cycle to answer the following questions.

- Amanda's first task is to determine if there are alternative solutions that are more cost effective than in-house development. What phase is she in?
- Design
- Operations and maintenance
- Feasibility
- Analysis and requirements definition
- What phase of the SDLC typically includes the first code analysis and unit testing in the process?
- Analysis and requirements definition
- Design
- Coding
- Testing and integration
- After making it through most of the SDLC process, Amanda has reached point E on the diagram. What occurs at point E?
- Disposition
- Training and transition
- Unit testing
- Testing and integration
- Angela wants to prevent buffer overflow attacks on a Windows system. What two built-in technologies should she consider?
- The memory firewall and the stack guard
- ASLR and DEP
- ASLR and DLP
- The memory firewall and the buffer guard
- Amanda has been assigned to reduce the attack surface area for her organization, and she knows that the current network design relies on allowing systems throughout her organization to access the Internet directly via public IP addresses they are assigned. What should her first step be to reduce her organization's attack surface quickly and without large amounts of time invested?
- Install host firewalls on the systems.
- Move to a NAT environment.
- Install an IPS.
- None of the above.
- Matt believes that developers in his organization deployed code that did not implement cookies in a secure way. What type of attack would be aided by this security issue?
- SQL injection
- A denial-of-service attack
- Session hijacking
- XSS
- Chris operates the point-of-sale (POS) network for a company that accepts credit cards and is thus required to be compliant with PCI DSS. During his regular assessment of the POS terminals, he discovers that a recent Windows operating system vulnerability exists on all of them. Since they are all embedded systems that require a manufacturer update, he knows that he cannot install the available patch. What is Chris's best option to stay compliant with PCI DSS and protect his vulnerable systems?
- Replace the Windows embedded point-of-sale terminals with standard Windows systems.
- Build a custom operating system image that includes the patch.
- Identify, implement, and document compensating controls.
- Remove the POS terminals from the network until the vendor releases a patch.
- Tracy is validating the web application security controls used by her organization. She wants to ensure that the organization is prepared to conduct forensic investigations of future security incidents. Which one of the following OWASP control categories is most likely to contribute to this effort?
- Implement logging.
- Validate all inputs.
- Parameterize queries.
- Error and exception handling.
- While reviewing his Apache logs, Oscar discovers the following entry. What has occurred?
10.1.1.1 - - [27/Jun/2023:11:42:22 -0500] "GET/query.php?searchterm=stuff&%20lid=1%20UNION%20SELECT%200,username,user_id,password,name,%20email,%20FROM%20usersHTTP/1.1" 200 9918 "-" "Mozilla/4.0 (compatible; MSIE 6.0;Windows NT 5.1; SV1; .NET CLR 1.1.4322)"- A successful database query
- A PHP overflow attack
- A SQL injection attack
- An unsuccessful database query
- Joan is working as a security consultant to a company that runs a critical web application. She discovered that the application has a serious SQL injection vulnerability, but the company cannot take the system offline during the two weeks required to revise the code. Which one of the following technologies would serve as the best compensating control?
- IPS
- WAF
- Vulnerability scanning
- Encryption
- After conducting an
nmapscan of his network from outside of his network, James notes that a large number of devices are showing three TCP ports open on public IP addresses: 9100, 515, and 631. What type of devices has he found, and how could he reduce his organization's attack surface?- Wireless access points, disable remote administration
- Desktop workstations, enable the host firewall
- Printers, move the printers to an internal-only IP address range
- Network switches, enable encrypted administration mode
- Alex is working to understand his organization's attack surface. Services, input fields in a web application, and communication protocols are all examples of what component of an attack surface evaluation?
- Threats
- Attack vectors
- Risks
- Surface tension
- Michelle wants to implement a static application security testing (SAST) tool into her continuous integration pipeline. What challenge could she run into if her organization uses multiple programming languages for components of their application stack that will be tested?
- They will have to ensure the scanner works with all of the languages chosen.
- They will have to compile all of the code to the same binary output language.
- They will have to run the applications in a sandbox.
- They will have to run the applications under the same execution environment.
- Ken learns that an APT group is targeting his organization. What term best describes this situation?
- Risk
- Threat
- Countermeasure
- Vulnerability
- Which one of the following activities is least likely to occur during the risk identification process?
- Network segmentation
- Threat intelligence
- Vulnerability scanning
- System assessments
- What two factors are weighted most heavily when determining the severity of a risk?
- Probability and magnitude
- Likelihood and probability
- Magnitude and impact
- Impact and control
- Preemployment background screening is an example of what type of security control?
- Detective
- Preventive
- Corrective
- Compensating
- Roland received a security assessment report from a third-party assessor, and it indicated that one of the organization's web applications is susceptible to an OAuth redirect attack. What type of attack would this vulnerability allow an attacker to wage?
- Privilege escalation
- Cross-site scripting
- SQL injection
- Impersonation
Questions 256–258 refer to the following scenario.
Gary recently conducted a comprehensive security review of his organization. He identified the 25 top risks to the organization and is pursuing different risk management strategies for each of these risks. In some cases, he is using multiple strategies to address a single risk. His goal is to reduce the overall level of risk so that it lies within his organization's risk tolerance.
- Gary decides that the organization should integrate a threat intelligence feed with the firewall. What type of risk management strategy is this?
- Risk mitigation
- Risk acceptance
- Risk transference
- Risk avoidance
- Gary discovers that his organization is storing some old files in a cloud service that are exposed to the world. He deletes those files. What type of risk management strategy is this?
- Risk mitigation
- Risk acceptance
- Risk transference
- Risk avoidance
- Gary is working with his financial team to purchase a cyber-liability insurance policy to cover the financial impact of a data breach. What type of risk management strategy is he using?
- Risk mitigation
- Risk acceptance
- Risk transference
- Risk avoidance
- Which one of the following risk management strategies is most likely to limit the probability of a risk occurring?
- Risk acceptance
- Risk avoidance
- Risk transference
- Risk mitigation
- Saanvi would like to reduce the probability of a data breach that affects sensitive personal information. Which one of the following compensating controls is most likely to achieve that objective?
- Minimizing the amount of data retained and the number of places where it is stored
- Limiting the purposes for which data may be used
- Purchasing cyber-risk insurance
- Installing a new firewall
- Kwame recently completed a risk assessment and is concerned that the level of residual risk exceeds his organization's risk tolerance. What should he do next?
- Have a discussion with his manager.
- Implement new security controls.
- Modify business processes to lower risk.
- Purge data from systems.
Questions 262–267 refer to the following scenario.
Alan is a risk manager for Acme University, a higher education institution located in the western United States. He is concerned about the threat that an earthquake will damage his organization's primary datacenter. He recently undertook a replacement cost analysis and determined that the datacenter is valued at $10 million.
After consulting with seismologists, Alan determined that an earthquake is expected in the area of the datacenter once every 200 years. Datacenter specialists and architects helped him determine that an earthquake would likely cause $5 million in damage to the facility.
- Based on the information in this scenario, what is the exposure factor (EF) for the effect of an earthquake on Acme University's datacenter?
- 10 percent
- 25 percent
- 50 percent
- 75 percent
- Based on the information in this scenario, what is the annualized rate of occurrence (ARO) for an earthquake at the datacenter?
- .0025
- .005
- .01
- .015
- Based on the information in this scenario, what is the annualized loss expectancy (ALE) for an earthquake at the datacenter?
- $25,000
- $50,000
- $250,000
- $500,000
- Referring to the previous scenario, if Alan's organization decides to move the datacenter to a location where earthquakes are not a risk, what risk management strategy are they using?
- Risk mitigation
- Risk avoidance
- Risk acceptance
- Risk transference
- Referring to the previous scenario, if the organization decides not to relocate the datacenter but instead purchases an insurance policy to cover the replacement cost of the datacenter, what risk management strategy are they using?
- Risk mitigation
- Risk avoidance
- Risk acceptance
- Risk transference
- Referring to the previous scenario, assume that the organization decides that relocation is too difficult and the insurance is too expensive. They instead decide that they will carry on despite the risk of earthquake and handle the impact if it occurs. What risk management strategy are they using?
- Risk mitigation
- Risk avoidance
- Risk acceptance
- Risk transference
- Colin would like to implement a detective security control in his accounting department, which is specifically designed to identify cases of fraud that are able to occur despite the presence of other security controls. Which one of the following controls is best suited to meet Colin's need?
- Separation of duties
- Least privilege
- Dual control
- Mandatory vacations
- Rob is an auditor reviewing the managerial controls used in an organization. He is examining the payment process used by the company to issue checks to vendors. He notices that Helen, a staff accountant, is the person responsible for creating new vendors. Norm, another accountant, is responsible for issuing payments to vendors. Helen and Norm are cross-trained to provide backup for each other. What security issue, if any, exists in this situation?
- Least privilege violation
- Separation of duties violation
- Dual control violation
- No issue
- Mei recently completed a risk management review and identified that the organization is susceptible to an on-path (also known as man-in-the-middle) attack. After review with her manager, they jointly decided that accepting the risk is the most appropriate strategy. What should Mei do next?
- Implement additional security controls.
- Design a remediation plan.
- Repeat the business impact assessment.
- Document the decision.
- Robin is planning to conduct a risk assessment in her organization. She is concerned that it will be difficult to perform the assessment because she needs to include information about both tangible and intangible assets. What would be the most effective risk assessment strategy for her to use?
- Quantitative risk assessment
- Qualitative risk assessment
- Combination of quantitative and qualitative risk assessment
- Neither quantitative nor qualitative risk assessment
- Barry's organization is running a security exercise and Barry was assigned to conduct offensive operations. What term best describes Barry's role in the process?
- Red team
- Purple team
- Blue team
- White team
- Vlad's organization recently underwent a security audit that resulted in a finding that the organization fails to promptly remove the accounts associated with users who have left the organization. This resulted in at least one security incident where a terminated user logged into a corporate system and took sensitive information. What identity and access management control would best protect against this risk?
- Automated deprovisioning
- Quarterly user account reviews
- Separation of duties
- Two-person control
- Jay is the CISO for his organization and is responsible for conducting periodic reviews of the organization's information security policy. The policy was written three years ago and has undergone several minor revisions after audits and assessments. Which one of the following would be the most reasonable frequency to conduct formal reviews of the policy?
- Monthly
- Quarterly
- Annually
- Every five years
- Terri is undertaking a risk assessment for her organization. Which one of the following activities would normally occur first?
- Risk identification
- Risk calculation
- Risk mitigation
- Risk management
- Kai is attempting to determine whether he can destroy a cache of old records that he discovered. What type of policy would most directly answer his question?
- Data ownership
- Data classification
- Data minimization
- Data retention
- Fences are a widely used security control that can be described by several different control types. Which one of the following control types would least describe a fence?
- Deterrent
- Corrective
- Preventive
- Physical
- Ian is designing an authorization scheme for his organization's deployment of a new accounting system. He is considering putting a control in place that would require that two accountants approve any payment request over $100,000. What security principle is Ian seeking to enforce?
- Security through obscurity
- Least privilege
- Separation of duties
- Dual control
- Carmen is working with a new vendor on the design of a penetration test. She would like to ensure that the vendor does not conduct any physical intrusions as part of their testing. Where should Carmen document this requirement?
- Rules of engagement
- Service level objectives
- Nondisclosure agreement
- Counterparty agreement
- Gavin is drafting a document that provides a detailed step-by-step process that users may follow to connect to the VPN from remote locations. Alternatively, users may ask IT to help them configure the connection. What term best describes this document?
- Policy
- Procedure
- Standard
- Guideline
- Which one of the following security controls is designed to help provide continuity for security responsibilities?
- Succession planning
- Separation of duties
- Mandatory vacation
- Dual control
- After conducting a security review, Oskar determined that his organization is not conducting regular backups of critical data. What term best describes the type of control gap that exists in Oskar's organization?
- Preventive
- Corrective
- Detective
- Deterrent
- Carla is reviewing the cybersecurity policies used by her organization. What policy might she put in place as a failsafe to cover employee behavior situations where no other policy directly applies?
- Data monitoring policy
- Account management policy
- Code of conduct
- Data ownership policy
- Which one of the following items is not normally included in a request for an exception to security policy?
- Description of a compensating control
- Description of the risks associated with the exception
- Proposed revision to the security policy
- Business justification for the exception
- What policy should contain provisions for removing user access upon termination?
- Data ownership policy
- Data classification policy
- Data retention policy
- Account management policy
Questions 286–288 refer to the following scenario:
Karen is the CISO of a major manufacturer of industrial parts. She is currently performing an assessment of the firm's financial controls, with an emphasis on implementing security practices that will reduce the likelihood of theft from the firm.
- Karen would like to ensure that the same individual is not able to both create a new vendor in the system and authorize a payment to that vendor. She is concerned that an individual who could perform both of these actions would be able to send payments to false vendors. What type of control should Karen implement?
- Mandatory vacations
- Separation of duties
- Job rotation
- Two-person control
- The accounting department has a policy that requires the signatures of two individuals on checks valued over $5,000. What type of control do they have in place?
- Mandatory vacations
- Separation of duties
- Job rotation
- Two-person control
- Karen would also like to implement controls that would help detect potential malfeasance by existing employees. Which one of the following controls is least likely to detect malfeasance?
- Mandatory vacations
- Background investigations
- Job rotation
- Privilege use reviews
- Kevin is conducting a security exercise for his organization that uses both offensive and defensive operations. His role is to serve as the moderator of the exercise and to arbitrate disputes. What role is Kevin playing?
- White team
- Red team
- Swiss team
- Blue team
- Bohai is concerned about access to the main account for a cloud service that his company uses to manage payment transactions. He decides to implement a new process for multifactor authentication to that account where an individual on the IT team has the password to the account, while an individual in the accounting group has the token. What security principle is Bohai using?
- Dual control
- Separation of duties
- Least privilege
- Security through obscurity
- Tina is preparing for a penetration test and is working with a new vendor. She wants to make sure that the vendor understands exactly what technical activities are permitted within the scope of the test. Where should she document these requirements?
- MOA
- Contract
- RoE
- SLA
- Azra is reviewing a draft of the Domer Doodads information security policy and finds that it contains the following statements. Which one of these statements would be more appropriately placed in a different document?
- Domer Doodads designates the chief information security officer as the individual with primary responsibility for information security.
- The chief information security officer is granted the authority to create specific requirements that implement this policy.
- All access to financial systems must use multifactor authentication for remote connections.
- Domer Doodads considers cybersecurity and compliance to be of critical importance to the business.
- Which one of the following security policy framework documents never includes mandatory employee compliance?
- Policy
- Guideline
- Procedure
- Standard
- Kaitlyn is on the red team during a security exercise, and she has a question about whether an activity is acceptable under the exercise's rules of engagement. Who would be the most appropriate person to answer her question?
- Red team leader.
- White team leader.
- Blue team leader.
- Kaitlyn should act without external advice.
Questions 295–299 refer to the following scenario.
Seamus is conducting a business impact assessment for his organization. He is attempting to determine the risk associated with a denial-of-service attack against his organization's datacenter.
Seamus consulted with various subject-matter experts (SMEs) and determined that the attack would not cause any permanent damage to equipment, applications, or data. The primary damage would come in the form of lost revenue. Seamus believes that the organization would lose $75,000 in revenue during a successful attack.
Seamus also consulted with his threat management vendor, who considered the probability of a successful attack against his organization and determined that there is a 10 percent chance of a successful attack in the next 12 months.
- What is the ARO for this assessment?
- 8 percent
- 10 percent
- 12 percent
- 100 percent
- What is the SLE for this scenario?
- $625
- $6,250
- $7,500
- $75,000
- What is the ALE for this scenario?
- $625
- $6,250
- $7,500
- $75,000
- Seamus is considering purchasing a DDoS protection system that would reduce the likelihood of a successful attack. What type of control is he considering?
- Detective
- Corrective
- Preventive
- Deterrent
- Seamus wants to make sure that he can accurately describe the category of the DDoS protection service to auditors. Which term best describes the category of this control?
- Compensating
- Physical
- Operational
- Technical
Questions 300 and 301 refer to the following scenario:
Piper's organization handles credit card information and is, therefore, subject to the Payment Card Industry Data Security Standard (PCI DSS). She is working to implement the PCI DSS requirements.
- As Piper attempts to implement PCI DSS requirements, she discovers that she is unable to meet one of the requirements because of a technical limitation in her point-of-sale system. She decides to work with regulators to implement a second layer of logical isolation to protect this system from the Internet to allow its continued operation despite not meeting one of the requirements. What term best describes the type of control Piper has implemented?
- Physical control
- Operational control
- Compensating control
- Deterrent control
- When Piper implements this new isolation technology, what type of risk management action is she taking?
- Risk acceptance
- Risk avoidance
- Risk transference
- Risk mitigation
- Ruth is helping a business leader determine the appropriate individuals to consult about sharing information with a third-party organization. Which one of the following policies would likely contain the most relevant guidance for her?
- Data retention policy
- Information security policy
- Data validation policy
- Data ownership policy
- Samantha is investigating a cybersecurity incident where an internal user used his computer to participate in a denial-of-service attack against a third party. What type of policy was most likely violated?
- AUP
- SLA
- BCP
- Information classification policy
- Ryan is compiling a list of allowable encryption algorithms for use in his organization. What type of document would be most appropriate for this list?
- Policy
- Standard
- Guideline
- Procedure
- During the design of an identity and access management authorization scheme, Katie took steps to ensure that members of the security team who can approve database access requests do not have access to the database themselves. What security principle is Katie most directly enforcing?
- Least privilege
- Separation of duties
- Dual control
- Security through obscurity
- Which one of the following controls is useful to both facilitate the continuity of operations and serve as a deterrent to fraud?
- Succession planning
- Dual control
- Cross-training
- Separation of duties
- Which one of the following requirements is often imposed by organizations as a way to achieve their original control objective when they approve an exception to a security policy?
- Documentation of scope
- Limited duration
- Compensating control
- Business justification
- Berta is reviewing the security procedures surrounding the use of a cloud-based online payment service by her company. She set the access permissions for this service so that the same person cannot add funds to the account and transfer funds out of the account. What security principle is most closely related to Berta's action?
- Least privilege
- Security through obscurity
- Separation of duties
- Dual control
- Thomas found himself in the middle of a dispute between two different units in his business that are arguing over whether one unit may analyze data collected by the other. What type of policy would most likely contain guidance on this issue?
- Data ownership policy
- Data classification policy
- Data retention policy
- Account management policy
- Mara is designing a new data mining system that will analyze access control logs for signs of unusual login attempts. Any suspicious logins will be automatically locked out of the system. What type of control is Mara designing?
- Physical control
- Operational control
- Managerial control
- Technical control
- Which one of the following elements is least likely to be found in a data retention policy?
- Minimum retention period for data
- Maximum retention period for data
- Description of information to retain
- Classification of information elements
- Kevin leads the IT team at a small business and does not have a dedicated security team. He would like to develop a security baseline of his organization's system configurations but does not have a team of security experts available to assist him. Which of the following is the most appropriate tool for Kevin to use?
- Penetration testing tool
- Patch management tool
- Vulnerability scanning tool
- Network monitoring tool
- Jenna is helping her organization choose a set of security standards that will be used to secure a variety of operating systems. She is looking for industry guidance on the appropriate settings to use for Windows and Linux systems. Which one of the following tools will serve as the best resource?
- ISO 27001
- OWASP
- PCI DSS
- CIS benchmarks
- Linda is attempting to configure Angry IP Scanner on her Linux scanning workstation and is receiving errors about missing required software. What component must be installed prior to using Angry IP Scanner?
nmap- Java
gcc- Nessus
- Chris is investigating a malware outbreak and would like to reverse engineer the code. Which one of the following tools is specifically designed for this task?
- Immunity debugger
- ZAP
- Recon-ng
- GDB
- Jim is working with a penetration testing contractor who proposes using Metasploit as part of his penetration testing effort. What should Jim expect to occur when Metasploit is used?
- Systems will be scanned for vulnerabilities.
- Systems will have known vulnerabilities exploited.
- Services will be probed for buffer overflow and other unknown flaws.
- Systems will be tested for zero-day exploits.
- Which one of the following best describes recon-ng as a security tool?
- Vulnerability scanner
- Web application reconnaissance tool
- Network mapper
- Password cracker
- Ashley is investigating an attack that compromised an account of one of her users. In the attack, the attacker forced the submission of an authenticated request to a third-party site by exploiting trust relationships in the user's browser. What type of attack most likely took place?
- XSS
- CSRF
- SQL injection
- Session hijacking
- Juanita is a cybersecurity professional who works with data scientists at a company that uses machine learning (ML) models to predict customer behavior. She believes that their work has been the target of a data poisoning attack.
Which of the following actions should she take to address the situation?
- Ignore the problem as it is unlikely to have an operational effect.
- Remove affected data from the training dataset and generate a new model.
- Generate a new model using the same dataset and machine learning algorithm.
- Generate a new model using the same dataset and a different machine learning algorithm.
- Joshua is concerned about insecure software design practices and is developing a software threat modeling program for his organization. Which of the following is not an appropriate goal for this program?
- To reduce the number of security-related design flaws
- To reduce the number of security-related coding flaws
- To reduce the severity of non-security-related flaws
- To reduce the number of threat vectors
- Gavin works as a cybersecurity analyst and notices that issues continually arise in his organization where system administrators modify system configuration files without providing advance notice to other teams. In several situations, this resulted in a security misconfiguration. What control would best prevent these issues from recurring in the future?
- Change management program
- Security-enhanced operating system
- Configuration lockdown
- File integrity monitoring
- Brenda maintains a web application and learned that the application contains a remote code execution vulnerability that is triggered by sending a carefully crafted message to a logging service that runs on the underlying server. What action should Brenda take to best address this risk?
- Modify the code of the web application to eliminate the vulnerability.
- Install an intrusion detection system.
- Check for and apply patches from the logging vendor.
- Ignore the issue because the logging service is not her responsibility.
- Viola is analyzing an attack that occurred against her organization. The attacker was able to manipulate a web application to display a confidential data file that was stored on the server by traversing the directory structure in the URL. What term best describes this type of attack?
- SQL injection
- Server-side request forgery
- Local file inclusion
- Remote file inclusion
- Melissa is concerned that users in her organization are connecting to corporate systems over insecure networks and begins a security awareness campaign designed to encourage them to use the VPN. What category of control has Melissa implemented?
- Compensating
- Technical
- Operational
- Managerial
- The company Chris works for has notifications posted at each door reminding employees to be careful not to allow people to enter when they do. Which type of control is this?
- Detective
- Responsive
- Preventive
- Corrective
- Kevin has discovered a security vulnerability in one of his organization's business-critical systems. He evaluates the situation and determines that it presents a low risk to the organization but would like to correct it. There is a patch available from the vendor. When should Kevin plan to apply the patch?
- Immediately
- During the next scheduled maintenance window
- As soon as possible outside of normal business hours
- During the next major system upgrade
- Ben is responsible for the security of payment card information stored in a database. Policy directs that he remove the information from the database, but he cannot do this for operational reasons. He obtained an exception to policy and is seeking an appropriate compensating control to mitigate the risk. What would be his best option?
- Purchasing insurance
- Encrypting the database contents
- Removing the data
- Objecting to the exception
- Isabelle wants to prevent privilege escalation attacks via her organization's service accounts. Which of the following security practices is best suited to this?
- Remove unnecessary rights.
- Disable interactive login for service accounts.
- Limit when accounts can log in.
- Use meaningless or randomized names for service accounts.
- Brandon is validating the security of systems and devices in his organization, but he is permitted to use only passive techniques. Which one of the following actions would be considered passive discovery?
- Monitoring network traffic and analyzing the contents for signs of unpatched systems and applications
- Running vulnerability scans of an organization's servers
- Running port scans of an organization's servers
- Using carefully scoped penetration testing techniques to identify vulnerabilities
- Ryan's organization wants to ensure that proper account management is occurring but does not have a central identity and access management tool in place. Ryan has a limited amount of time to do his verification process. What is his best option to test the account management process as part of an internal audit?
- Validate all accounts changed in the past 90 days.
- Select high value administrative accounts for validation.
- Validate all accounts changed in the past 180 days.
- Validate a random sample of accounts.
- Which one of the following security testing programs is designed to attract the participation of external testers and incentivize them to uncover security flaws?
- Penetration test
- Internal vulnerability scan
- Bug bounty
- External vulnerability scan
- Frank's team is testing a new API that his company's developers have built for their application infrastructure. Which of the following is not a common API issue that you would expect Frank's team to find?
- Improper encryption
- Object level authorization issues
- User authentication issues
- Lack of rate limiting
- Ryan is considering the use of fuzz testing in his web application testing program. Which one of the following statements about fuzz testing is true?
- Fuzzers find only complex faults.
- Testers must manually generate input.
- Fuzzers may not fully cover the code.
- Fuzzers can't reproduce errors.
