Chapter 4
Reporting and Communication
- Kyong manages the vulnerability scans for his organization. The senior director that oversees Kyong's group provides a report to the CIO on a monthly basis on operational activity, and he includes the number of open critical vulnerabilities. He would like to provide this information to his director in as simple a manner as possible each month. What should Kyong do?
- Provide the director with access to the scanning system.
- Check the system each month for the correct number and email it to the director.
- Configure a report that provides the information to automatically send to the director's email at the proper time each month.
- Ask an administrative assistant to check the system and provide the director with the information.
- Carla is designing a vulnerability scanning workflow and has been tasked with selecting the person responsible for remediating vulnerabilities. Which one of the following people would normally be in the best position to remediate a server vulnerability?
- Cybersecurity analyst
- System administrator
- Network engineer
- IT manager
- During a vulnerability scan, Patrick discovered that the configuration management agent installed on all of his organization's Windows servers contains a serious vulnerability. The manufacturer is aware of this issue, and a patch is available. What process should Patrick follow to correct this issue?
- Immediately deploy the patch to all affected systems.
- Deploy the patch to a single production server for testing and then deploy to all servers if that test is successful.
- Deploy the patch in a test environment and then conduct a staged rollout in production.
- Disable all external access to systems until the patch is deployed.
- Ben is preparing to conduct a vulnerability scan for a new client of his security consulting organization. Which one of the following steps should Ben perform first?
- Conduct penetration testing.
- Run a vulnerability evaluation scan.
- Run a discovery scan.
- Obtain permission for the scans.
- Katherine coordinates the remediation of security vulnerabilities in her organization and is attempting to work with a system engineer on the patching of a server to correct a moderate impact vulnerability. The engineer is refusing to patch the server because of the potential interruption to a critical business process that runs on the server. What would be the most reasonable course of action for Katherine to take?
- Schedule the patching to occur during a regular maintenance cycle.
- Exempt the server from patching because of the critical business impact.
- Demand that the server be patched immediately to correct the vulnerability.
- Inform the engineer that if he does not apply the patch within a week that Katherine will file a complaint with his manager.
- Grace ran a vulnerability scan and detected an urgent vulnerability in a public-facing web server. This vulnerability is easily exploitable and could result in the complete compromise of the server. Grace wants to follow best practices regarding change control while also mitigating this threat as quickly as possible. What would be Grace's best course of action?
- Initiate a high-priority change through her organization's change management process and wait for the change to be approved.
- Implement a fix immediately and document the change after the fact.
- Schedule a change for the next quarterly patch cycle.
- Initiate a standard change through her organization's change management process.
- Joe discovered a critical vulnerability in his organization's database server and received permission from his supervisor to implement an emergency change after the close of business. He has eight hours before the planned change window. In addition to planning the technical aspects of the change, what else should Joe do to prepare for the change?
- Ensure that all stakeholders are informed of the planned outage.
- Document the change in his organization's change management system.
- Identify any potential risks associated with the change.
- All of the above.
- Sally discovered during a vulnerability scan that a system she manages has a high-priority vulnerability that requires a patch. The system is behind a firewall and there is no imminent threat, but Sally wants to get the situation resolved as quickly as possible. What would be her best course of action?
- Initiate a high-priority change through her organization's change management process.
- Implement a fix immediately and then document the change after the fact.
- Implement a fix immediately and then inform her supervisor of her action and the rationale.
- Schedule a change for the next quarterly patch cycle.
- Gene runs a vulnerability scan of his organization's datacenter and produces a summary report to share with his management team. The report includes the chart shown here. When Gene's manager reads the report, she points out that the report is burying important details because it is highlighting too many unimportant issues. What should Gene do to resolve this issue?

- Tell his manager that all vulnerabilities are important and should appear on the report.
- Create a revised version of the chart using Excel.
- Modify the sensitivity level of the scan.
- Stop sharing reports with the management team.
- Glenda routinely runs vulnerability scans of servers in her organization. She is having difficulty with one system administrator who refuses to correct vulnerabilities on a server used as a jump box by other IT staff. The server has had dozens of vulnerabilities for weeks and would require downtime to repair. One morning, her scan reports that all of the vulnerabilities suddenly disappeared overnight, while other systems in the same scan are reporting issues. She checks the service status dashboard, and the service appears to be running properly with no outages reported in the past week. What is the most likely cause of this result?
- The system administrator corrected the vulnerabilities.
- The server is down.
- The system administrator blocked the scanner.
- The scan did not run.
- Tom is planning a series of vulnerability scans and wants to ensure that the organization is meeting its customer commitments with respect to the scans' performance impact. What two documents should Tom consult to find these obligations?
- SLAs and MOUs
- SLAs and DRPs
- DRPs and BIAs
- BIAs and MOUs
- Zhang Wei is evaluating the success of his vulnerability management program and would like to include some metrics. Which one of the following would be the least useful metric?
- Time to resolve critical vulnerabilities
- Number of open critical vulnerabilities over time
- Total number of vulnerabilities reported
- Number of systems containing critical vulnerabilities
- Donna is working with a system engineer who wants to remediate vulnerabilities in a server that he manages. Of the report templates shown here, which would be most useful to the engineer?
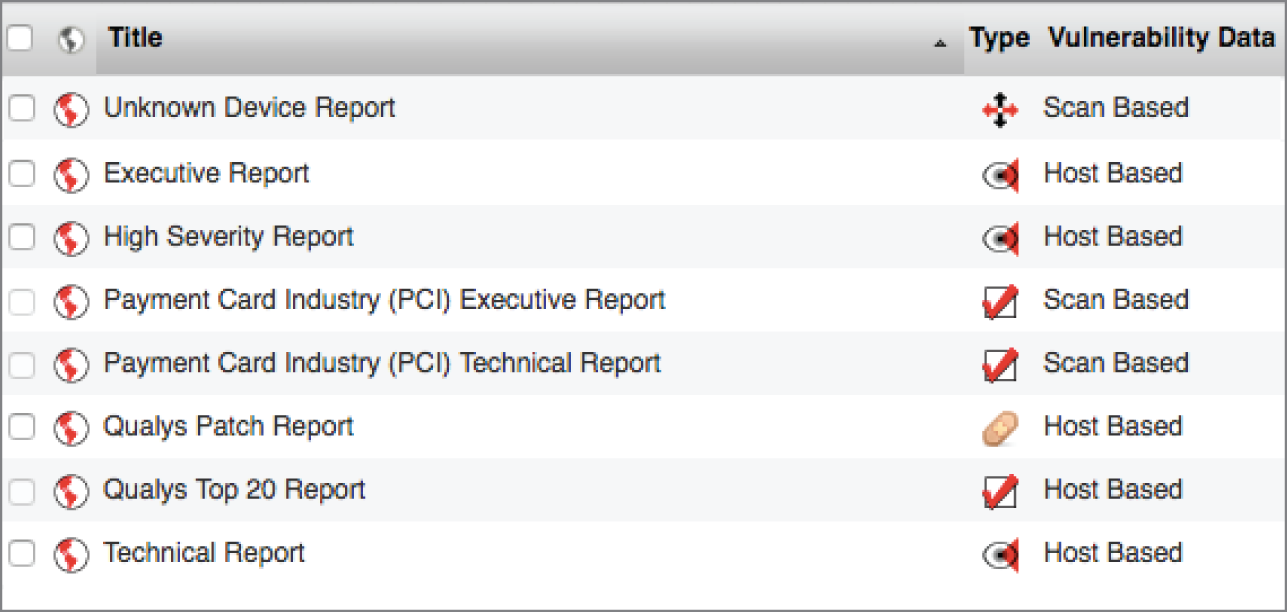
- Qualys Top 20 Report
- PCI Technical Report
- Executive Report
- Technical Report
- Abdul received the vulnerability report shown here for a server in his organization. The server runs a legacy application that cannot easily be updated. What risks does this vulnerability present?

- Unauthorized access to files stored on the server
- Theft of credentials
- Eavesdropping on communications
- All of the above
- William is preparing a legal agreement for his organization to purchase services from a vendor. He would like to document the requirements for system availability, including the vendor's allowable downtime for patching. What type of agreement should William use to incorporate this requirement?
- MOU
- SLA
- BPA
- BIA
- Raul is replacing his organization's existing vulnerability scanner with a new product that will fulfill that functionality moving forward. As Raul begins to build the policy, he notices some conflicts in the scanning settings between different documents. Which one of the following document sources should Raul give the highest priority when resolving these conflicts?
- NIST guidance documents
- Vendor best practices
- Corporate policy
- Configuration settings from the prior system
- Pietro is responsible for distributing vulnerability scan reports to system engineers who will remediate the vulnerabilities. What would be the most effective and secure way for Pietro to distribute the reports?
- Pietro should configure the reports to generate automatically and provide immediate, automated notification to administrators of the results.
- Pietro should run the reports manually and send automated notifications after he reviews them for security purposes.
- Pietro should run the reports on an automated basis and then manually notify administrators of the results after he reviews them.
- Pietro should run the reports manually and then manually notify administrators of the results after he reviews them.
- Nitesh would like to identify any systems on his network that are not registered with his asset management system because he is concerned that they might not be remediated to his organization's current security configuration baseline. He looks at the reporting console of his vulnerability scanner and sees the options shown here. Which of the following report types would be his best likely starting point?
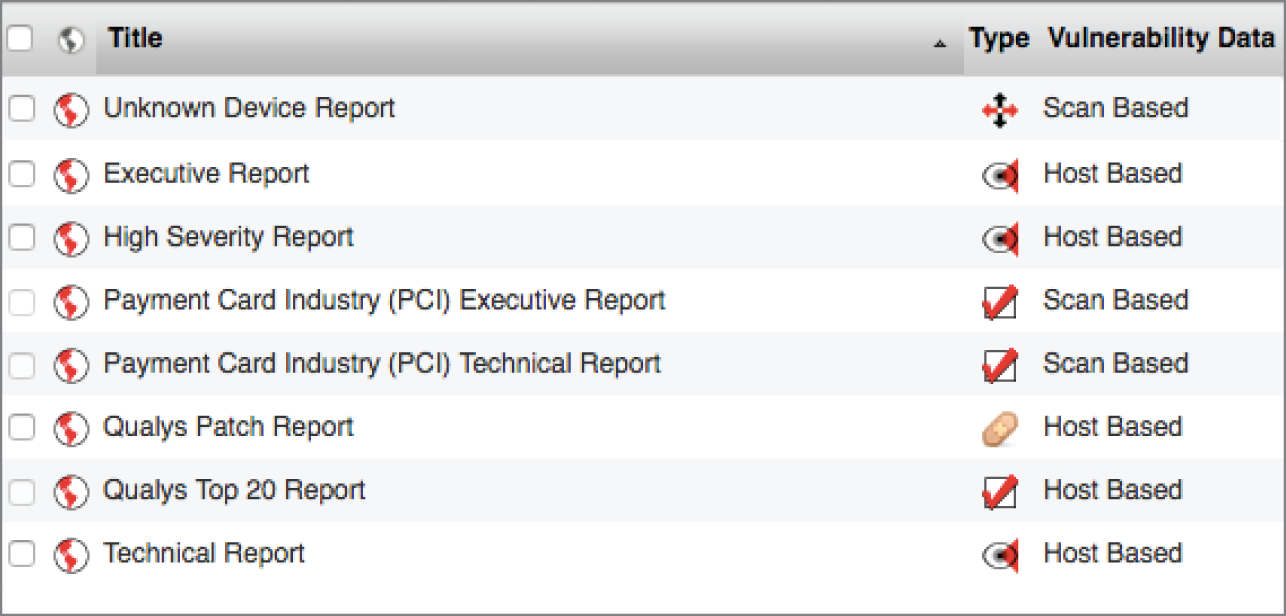
- Technical Report
- High Severity Report
- Qualys Patch Report
- Unknown Device Report
- Nabil is the vulnerability manager for his organization and is responsible for tracking vulnerability remediation. There is a critical vulnerability in a network device that Nabil has handed off to the device's administrator, but it has not been resolved after repeated reminders to the engineer. What should Nabil do next?
- Threaten the engineer with disciplinary action.
- Correct the vulnerability himself.
- Mark the vulnerability as an exception.
- Escalate the issue to the network administrator's manager.
- Maria discovered an operating system vulnerability on a system on her network. After tracing the IP address, she discovered that the vulnerability is on a proprietary search appliance installed on her network. She consulted with the responsible engineer who informed her that he has no access to the underlying operating system. What is the best course of action for Maria?
- Contact the vendor to obtain a patch.
- Try to gain access to the underlying operating system and install the patch.
- Mark the vulnerability as a false positive.
- Wait 30 days and rerun the scan to see whether the vendor corrected the vulnerability.
- Trevor is working with an application team on the remediation of a critical SQL injection vulnerability in a public-facing service. The team is concerned that deploying the fix will require several hours of downtime and will block customer transactions from completing. What is the most reasonable course of action for Trevor to suggest?
- Wait until the next scheduled maintenance window.
- Demand that the vulnerability be remediated immediately.
- Schedule an emergency maintenance for an off-peak time later in the day.
- Convene a working group to assess the situation.
- Thomas discovers a vulnerability in a web application that is part of a proprietary system developed by a third-party vendor, and he does not have access to the source code. Which one of the following actions can he take to mitigate the vulnerability without involving the vendor?
- Apply a patch.
- Update the source code.
- Deploy a web application firewall.
- Conduct dynamic testing.
- Walt is designing his organization's vulnerability management program and is working to identify potential inhibitors to vulnerability remediation. He has heard concern from functional leaders that remediating vulnerabilities will impact the ability of a new system to fulfill user requests. Which one of the following inhibitors does not apply to this situation?
- Degrading functionality
- Organizational governance
- Legacy systems
- Business process interruption
- The company that Brian works for processes credit cards and is required to be compliant with PCI DSS. If Brian's company experiences a breach of card data, what type of disclosure will they be required to provide?
- Notification to local law enforcement
- Notification to their acquiring bank
- Notification to federal law enforcement
- Notification to Visa and MasterCard
- As Lauren prepares her organization's security practices and policies, she wants to address as many threat vectors as she can using an awareness program. Which of the following threats can be most effectively dealt with via awareness?
- Attrition
- Impersonation
- Improper usage
- Web
- Laura wants to ensure that her team can communicate during an incident. Which of the following should the team prepare to be ready for an incident?
- A second, enterprise authenticated messaging system
- An enterprise VoIP system using encryption
- Enterprise email with TLS enabled
- A messaging capability that can function if enterprise authentication is unavailable
- Which of the following is not an important part of the incident response communication process?
- Limiting communication to trusted parties
- Disclosure based on public feedback
- Using a secure method of communication
- Preventing accidental release of incident-related information
- After law enforcement was called because of potential criminal activity discovered as part of a forensic investigation, the officers on the scene seized three servers. When can Joe expect his servers to be returned?
- After 30 days, which provides enough time for a reasonable imaging process
- After 6 months, as required by law
- After 1 year, as most cases resolve in that amount of time
- Joe should not plan on a timeframe for return
- NIST SP 800-61 identifies six outside parties that an incident response team will typically communicate with. Which of the following is not one of those parties?
- Customers, constituents, and media
- Internet service providers
- Law enforcement agencies
- Legal counsel
- Ben works at a U.S. federal agency that has experienced a data breach. Under FISMA, which organization does he have to report this incident to?
- US-CERT
- The National Cyber Security Authority
- The National Cyber Security Centre
- CERT/CC
- Which of the following organizations is not typically involved in post-incident communications?
- Developers
- Marketing
- Public relations
- Legal
- Tom is building his incident response team and is concerned about how the organization will address insider threats. Which business function would be most capable of assisting with the development of disciplinary policies?
- Information security
- Human resources
- Legal counsel
- Senior management
- Craig is revising his organization's incident response plan and wants to ensure that the plan includes coordination with all relevant internal and external entities. Which one of the following stakeholders should he be most cautious about coordinating with?
- Regulatory bodies
- Senior leadership
- Legal
- Human resources
- The vulnerability management action plan that was sent to Jacinda notes that a critical application that her organization uses relies on an insecure version of a software package because of a long-standing workflow requirement. Jacinda's organization's best practices state that the organization will select the most secure option that also permits business to be conducted. What should Jacinda do?
- Mark the vulnerability as “ignored.”
- Change the business requirements to enable the vulnerability to be handled.
- Disable the service.
- Install a third-party patch for the service.
- What section of an incident response report provides a brief, clear summary of the incident, response activities, and current state of the incident?
- The timeline
- The scope statement
- The executive summary
- The documentation of evidence
- Ian wants to prepare his organization for communications with the media as part of incident related public relations. What should he recommend that his organization do to prepare?
- Build a list of phrases and topics to avoid.
- Hire a reputation defense firm.
- Engage legal counsel.
- Conduct media training.
- Jason is required to notify the company that provides credit card processing services to his organization if an incident impacting credit card data occurs. What type of communications does he need to perform?
- Regulatory reporting
- Customer communications
- Law enforcement communications
- None of the above
- The incident response report that Kathleen has prepared includes the following statement:
“Unnecessary services including HTTP and FTP should be disabled on all devices of this type that are deployed.”
What incident response reporting component will most commonly include this type of statement?
- Scope
- Executive summary
- Recommendations
- Timeline
- What common score is used to help with prioritization of vulnerability remediation in many organizations?
- CVE
- ATT&CK
- CVSS
- PASTA
- Olivia has been notified that a vulnerability has recurred on a server after being marked as remediated through a compensating control by an administrator. Which of the following is the most likely reason that a vulnerability may recur in this circumstance?
- An attacker has removed the patch to expose the vulnerability.
- The system has been reinstalled by the administrator.
- A patch has caused the compensating control to fail.
- The service has been re-enabled by a user.
- The incident response report that Brian is reading includes a statement that says “Impacted systems were limited to those in the organization's AWS VPC.” What part of an incident response report will typically contain this type of information?
- The timeline
- The evidence statement
- The impact statement
- The scope statement
- Nila's incident response team has discovered evidence of an employee who may have been engaged in criminal activity while they were conducting an incident investigation. The team has suggested that law enforcement should be contacted. What significant concern should Nila raise about this potential communication?
- Law enforcement can't enforce organizational policy.
- Law enforcement engagement may hinder the organization's ability to respond or operate.
- Law enforcement involvement may create communications issues.
- Law enforcement may arrest a critical employee.
- Sameer wants to establish and track a metric for his organization that will help him know if his IoC monitoring processes are working well. Which of the following metrics is best suited to determining if IoCs are being effectively captured and analyzed?
- Mean time to detect
- Mean time to respond
- Mean time to remediate
- Mean time to compromise
- Sameer is continuing to improve his metrics to report to his organization's board of directors. The board has requested that he include alert volumes in his reporting. What issue should Sameer discuss with the board after receiving this request?
- High-alert volumes indicate poor incident response processes.
- Low-alert volumes indicate effective incident response processes.
- Alert volume is not an effective security metric.
- Alert volume requires other measures like number of patches installed to be an effective security metric.
- What important incident response report section relies heavily on NTP to be successful?
- The executive summary
- The recommendations
- The timeline
- The scope statement
- What type of agreement between two organizations is a common inhibitor to remediation because of uptime requirements?
- An NDA
- An SLA
- A TLA
- A KPI
- Valerie needs to explain CVSS score metrics to her team. Which of the following is not part of the basic metric group for CVSS scores?
- The attack vector
- The maturity of the exploit code
- The attack complexity
- The privileges required
- The scientific instrument that Chas is responsible for has multiple critical severity vulnerabilities in its operating system and services. The device cannot be patched according to instructions from the vendor who provides it. Which of the following is not an appropriate compensating control in this scenario?
- Place a network security device configured to prevent access to the system between the instrument and the network.
- Install vendor patches against recommendations.
- Disable network connectivity to the device.
- Place the device on a protected network segment.
- Hui's incident response report includes log entries showing that a user logged in from another country, despite living and working in the country that the company Hui works for is located in. What incident response report section is most likely to contain this type of information?
- The impact section
- The scope section
- The evidence section
- The timeline section
- Melissa is conducting a root-cause analysis. Which of the following is not a common step in RCA processes?
- Identify problems and events.
- Establish a timeline.
- Differentiate causal factors and the root cause.
- Implement compensating controls.
- What information is typically included in a list of affected hosts in a vulnerability management report?
- Hostname and IP address
- IP address and MAC address
- Hostname and MAC address
- Hostname and subnet mask
- Hannah wants to establish a metric that will help her organization determine if their response process completes in a timely manner. Which common metric should she select to help assess this?
- Mean time to detect
- Mean time to report
- Mean time to respond
- Mean time to remediate
- Mikayla's team has determined that a previously remediated vulnerability has re-appeared after installation of a vendor supplied patch. What type of vulnerability management issue is this?
- Risk scoring
- Prioritization
- Mitigation
- Recurrence
- Gurvinder wants to consider impact metrics like the integrity impact, availability impact, and compatibility impact of a vulnerability that is scored using CVSS. What metric group includes this information?
- Basic
- Environmental
- Temporal
- Residual
- Which of the following is not a type of stakeholder that will frequently need to understand an organization's overall vulnerability stance or status?
- Security practitioners
- Legal counsel
- Auditors
- Compliance stakeholders
- Which of the following CVSS scores indicates the highest impact to an organization?
- 9.6
- 7.5
- 3.2
- 1.3
- Expectations of time to remediate and time to patch by a vendor are both examples of what in a vulnerability management program?
- Service level objectives
- Risks
- Vulnerabilities
- Internal policies
- What issue is organizational governance likely to cause in a vulnerability management program?
- It may prevent vulnerabilities from being patched or compensating controls being used.
- It may increase the number of vulnerabilities that need patched.
- It may slow down patching.
- It may limit the vulnerabilities that will be patched.
- Jacob has initiated the incident response process in his organization. IoCs have been identified, and Jacob is ready to take the next step in the process. What typically happens next?
- Legal counsel is notified.
- Incident responders collect forensic data.
- Law enforcement is notified.
- Incident responders determine if it is a real incident.
- Asha wants to reduce the alert volumes her team are dealing with due to the numbers of emails and SMS alerts they are receiving. Which of the following is most likely to help reduce the volume of alerts?
- Tune alerting thresholds.
- Subscribe to more IoC feeds.
- Create additional IoCs.
- Set work hours to avoid after hours alerts.
- What NIST standard provides information on incident handling practices?
- NIST SP 800-61
- ISO 27001
- NIST SP 800-53
- SOC 2
- Jaime want to consider critical components of public relations as part of her incident communications plan. What two topics are best aligned to this?
- Customer and law enforcement communications
- Customer and executive communications
- Customer and media communications
- Customer and legal counsel communications
- Annie's organization makes divisional administrators responsible for patching vulnerabilities after they are notified of them using a ticketing system. Annie has noticed that the administrators are not promptly patching systems. What should she do to most effectively address this issue?
- Switch notification to automated emails.
- Invest in an awareness and training campaign.
- Use the vulnerabilities to compromise the systems to prove a point.
- Involve HR due to a lack of job performance.
- Henry's organization handles credit card data as part of their operations. What type of vulnerability management report is Henry most likely to need to run due to this?
- PCI compliance reporting
- GLBA compliance reporting
- A list of compromised systems
- A list of unpatched systems
- Jen has discovered that many systems in her organization are being deployed with a vulnerable service active. What solution is best suited to addressing this type of issue in a large organization?
- An awareness program
- Compensating controls
- Changing business requirements
- Configuration management
- An incident report should indicate the individuals involved, as well as which of the following items?
- The hardware addresses of the systems involved
- The time frame the event or incident occurred
- A written statement from each individual interviewed
- A police report
- Jason has defined the problem as part of a root-cause analysis effort. What step typically comes next in RCA?
- Collecting data about the problem
- Determining the root cause of the problem
- Determining potential causal factors
- Analyzing the causes
- Mean time to respond is an example of what?
- An incident response report target
- An industry standard SOW
- An industry standard SLA
- An incident response KPI
- What information is gathered as part of a lessons learned exercise conducted at the end of an incident response process?
- Issues that will positively impact future incident response processes
- Both positive and negative lessons learned during the process
- Issues that will negatively impact future incident response processes
- Root causes of the incident
- Jason wants to quickly understand the content of an incident report. What should he read?
- The scope statement
- The timeline
- The executive summary
- The evidence
- What important role does criticality and impact information play in organizational use of CVSS scores?
- It helps with prioritization.
- It determines if a patch should be installed.
- It determines if a compensating control should be used.
- It helps prevent recurrence.
- Natalie has signed a service level agreement with a customer that specifies performance requirements for a service that her company provides. How is this most likely to impact her ability to remediate vulnerabilities on the underlying containerized services that provide the service?
- It will require Natalie to seek customer approval for each patch that is deployed via their governance process.
- It will require Natalie to ensure that the service is not disrupted when new, patched containers are deployed and vulnerable containers are disabled.
- It will allow as much downtime as needed as patches are deployed to the containerized services.
- It will prevent Natalie from upgrading the legacy systems the customer relies on.
- Angela's organization has discovered that their Windows workstations have a vulnerability that was discovered more than a year ago. What solution is best suited to handling this known vulnerability?
- Patching
- Awareness, education, and training
- Changing business requirements
- Compensating controls
- Jacob wants to update mitigation notes for a vulnerability on a server. Which of the following is not a common mitigation option?
- Installing a patch
- Deploying a compensating control
- Disabling a service or software
- Turning the system off
- Which of the following is the most critical to have involved in incident escalation processes?
- End users
- Legal
- Management
- Law enforcement
- Gurvinder's organization is required to report breaches within 24 hours of the breach being detected, regardless of how far into the investigation the organization is. What type of requirement is most likely to drive this type of communication?
- Contractual requirements
- Social media requirements
- Regulatory requirements
- Reputational requirements
- Xuan's organization uses an old, no longer updated or sold software package that has an embedded web server that it exposes on every workstation that runs the software allowing file transfer between workstations. During a vulnerability scan the web browser was highlighted as a critical vulnerability. Which of the following solutions should Xuan recommend to best resolve the issue?
- An awareness program
- Compensating controls
- Changing business requirements
- Configuration management
- Jackie is reviewing the risk scores round in a vulnerability report and notes that the risk she is reviewing scores a 1.0. What recommendation should Jackie make about the vulnerability?
- It should be patched immediately because the risk score is high.
- The risk is very low and can likely be ignored.
- The risk is low and should be patched in the next patch cycle.
- It should be patched immediately because it is in the top 10 percent of risks.
- Log entries are commonly found in what part of an incident response report?
- Recommendations
- Executive summary
- Evidence
- Timeline
- Kathleen wants to build a prioritized list of vulnerabilities for her organization. What part of the CVSS metric will help her adjust the score to best match her organization's availability requirements?
- The base metric group
- The advanced metric group
- The temporal metric group
- The environmental metric group
- Derek is the lead of his organization's finance and accounting team and has expressed concerns about installing patches because his team relies on the service that is being patched. Derek noted that the team is at a critical time because of annual financial reports. What type of inhibitor to remediation is this?
- A potential MOU violation
- A legacy system issue
- A business process interruption issue
- A potential SLA violation
- What part of an incident response report describes detailed ways to avoid similar issues in the future?
- The executive summary
- Lessons learned
- The scope
- Evidence
- Potential compensating controls can be found in what section of a vulnerability management report?
- The mitigations section
- The risk scores
- The recurrence section
- The affected hosts list
- The company that Amari works for uses an embedded system as part of a manufacturing process. The system relies on an operating system created by the machine's vendor and Amari's team has identified vulnerabilities during a network scan. What type of system should Amari identify this device as?
- A proprietary system
- A legacy system
- A primary system
- A secondary system
- Amari wants to ensure that her team can meet her organization's service level agreement for the embedded system that has been identified as vulnerable. Which of the following compensating controls would be the most appropriate solution to allow the system to stay online while remaining secure?
- Install a hardware-based IDS between the system and the network.
- Place a hardware firewall between the system and the network.
- Disable the device's network connection.
- Install a nonproprietary operating system on the embedded system.
- Amari has deployed a compensating control to protect the vulnerable embedded system that she is responsible for. What step should she take next?
- Create an incident report and distribute it to appropriate recipients.
- Remove the device from the vulnerability scanning process to avoid continued false positives.
- Note the compensating control and flag the device for follow-up to see if patches become available.
- Flag the vulnerabilities previously discovered as false positives.
- NIST provides recommendations for communication with the media as part of incident response. Which of the following is a NIST recommended preparation for working with the media?
- Pre-writing all incident communications before incident occur
- Holding media practice sessions for incident responders as part of IR exercises
- Creating procedures on media avoidance as part of incident response planning
- Contacting law enforcement to prepare for media concerns
- Michele's root-cause analysis has determined a number of events that contributed to the problem but were not the root cause. What has she identified?
- Compensating controls
- Causal factors
- Branch causes
- Nonroot causes
- What three groups of metrics make up a CVSS score?
- The Core Metric Group, the Impact Metric Group, and the Organizational Metric Group
- The Core Metric Group, the Temporal Metric Group, and the Organizational Metric Group
- The Basic Metric Group, the Impact Metric Group, and the Environmental Metric Group
- The Basic Metric Group, the Temporal Metric Group, and the Environmental Metric Group
- Which of the following questions is not typically answered as part of an incident response report?
- Who?
- When?
- What?
- With whom?
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
