CHAPTER 3
Network Scanning and Enumeration
This chapter includes questions on the following topics:
• Conducting information gathering using appropriate techniques
• Performing a vulnerability scan
• Using Nmap to conduct information-gathering exercises
During penetration tests, network scanning and enumeration are among a penetration tester’s chief skills. In addition to simplifying host identification, the ability to confirm and identify running services in a network is a key tool for identifying potential target services and developing a path to successful network exploitation. Knowledge of ports used for various services can provide clear focus for further network enumeration as well—for instance, DNS or LDAP servers may be broadcasting critical information to anyone willing to listen. Occasionally, information that is beneficial to a penetration tester will be encoded as received from a host in the target network. Obtaining this useful information requires skills in packet inspection and decoding.
In addition to these general network scanning concerns, this chapter also addresses special considerations that must be taken into account when performing assessments of wireless networks.
Q QUESTIONS
1. Which component of the aircrack-ng suite of tools is used to put wireless adaptors into monitor mode?
A. Aireplay-ng
B. Airmon-ng
C. Airodump-ng
D. Airdecap-ng
2. Which type of primary frame (defined by the IEEE 802.11 wireless standard) enables stations to establish and sustain communication over the network with an access point?
A. Disassociation frame
B. Management frame
C. Data frame
D. Control frame
3. Which nmap flag is used to disable DNS resolution of hostnames?
A. -sL
B. -n
C. -oG
D. -Pn
4. What is the effect of the -PS flag in nmap?
A. Triggers SCTP discovery to named ports
B. Triggers TCP ACK discovery to named ports
C. Triggers UDP discovery to named ports
D. Triggers TCP SYN discovery to named ports
5. Which of the following is an active scanning technique used to aid in the process of information gathering, with the goal of identifying hosts that are alive and listening on the network?
A. Port scanning
B. Wardriving
C. Stumbling
D. Host discovery
6. Which open-source command-line tool is used for several penetration test–focused activities on both wired and wireless networks, such as surveying hosts for open ports, fingerprinting operating systems, and collecting service banners?
A. Shodan
B. Nmap
C. Aircrack-ng
D. Theharvester
7. What is the effect of the -v flag in nmap?
A. Denotes a list of targets to scan
B. Prevents DNS resolution
C. Increases the verbosity level of scan output
D. Disables ping and skips host discovery
8. Which of the following is an open-source suite of tools useful for conducting RF communication monitoring and security testing of wireless networks?
A. Shodan
B. Aircrack-ng
C. Nmap
D. Theharvester
9. Which popular tool is used for wireless discovery and offers many of the same features as airodump-ng?
A. Kismet
B. Nmap
C. Shodan
D. Onesixtyone
10. Which type of primary frame (defined by the IEEE 802.11 wireless standard) facilitates delivery of data frames to each station?
A. Deauthentication frame
B. Disassociation frame
C. Control frame
D. Management frame
11. Which subtype of management frame contains details about a wireless access point (including but not limited to the SSID, encryption details, MAC address, and Wi-Fi channel) that can enable a malicious agent to eavesdrop on a wireless network?
A. Authentication frame
B. Request to Send (RTS) frame
C. Beacon frame
D. Association request frame
12. What is the effect of the -Pn flag in nmap?
A. Disables ping and skips host discovery
B. Prevents DNS resolution
C. Disables port scanning and forces a simple ping scan
D. Outputs scan details in XML format
13. Which nmap flag should precede a file containing a list of targets to be scanned?
A. -Pn
B. -iL
C. -sn
D. -oA
14. Which of the following is not a primary type of frame defined by the IEEE 802.11 wireless communication standard?
A. Control frame
B. Beacon frame
C. Data frame
D. Management frame
Consider the following nmap output for the next three questions:
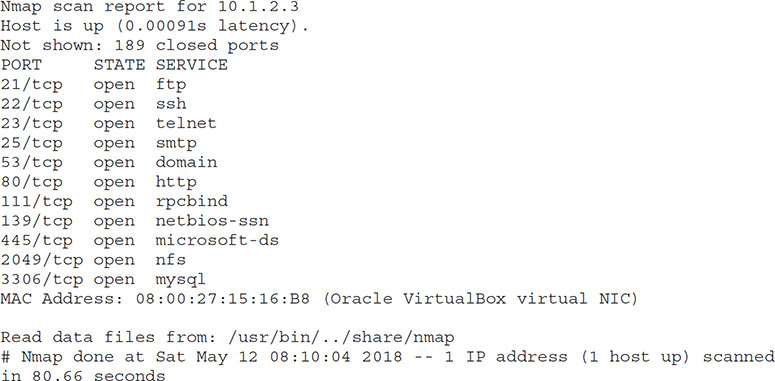
15. Which of the following nmap options would result in the ports shown being scanned?
A. -sL
B. -top-ports=200
C. -v
D. -sS
16. Of the following options, which nmap flag could produce output in the format shown?
A. -oX
B. -iL
C. -oN
D. -T
17. Which of the following flags would be recommended to further enumerate the server running on port 3306?
A. -sT
B. -script=mysql-info
C. -info3306
D. -script=http-enum
Consider the following nmap output passage for the next two questions:
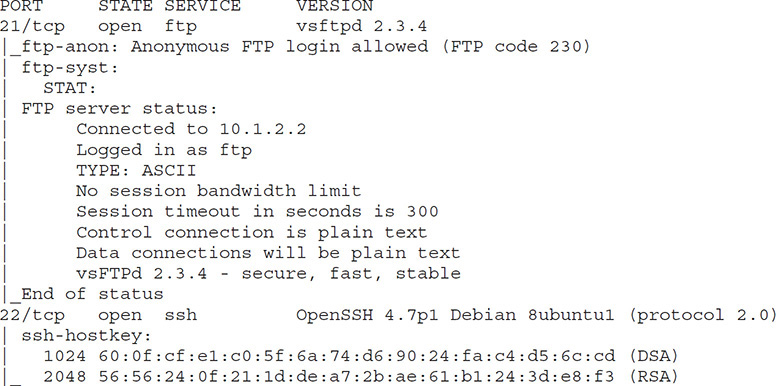
18. Of the following options, which flags could have produced the output presented?
A. -sU
B. -O
C. -sV
D. -A
19. In the output presented, which NSE script revealed that the FTP server present permits anonymous login?
A. ftp-syst
B. ssh-hostkey
C. ftp-anon
D. FTP server status
20. Which of the following NSE scripts would be best used to enumerate shared storage volumes on a network? (Choose two.)
A. smb-enum-shares
B. smb-enum-domains
C. smtp-enum-users
D. nfs-showmount
QUICK ANSWER KEY
1. B
2. B
3. B
4. D
5. D
6. B
7. C
8. B
9. A
10. C
11. C
12. A
13. B
14. B
15. B
16. C
17. B
18. D
19. C
20. A, D
A IN-DEPTH ANSWERS
1. Which component of the aircrack-ng suite of tools is used to put wireless adaptors into monitor mode?
A. Aireplay-ng
B. Airmon-ng
C. Airodump-ng
D. Airdecap-ng
![]() B. Airmon-ng is a component of the aircrack-ng suite of tools used to put wireless adaptors into monitor mode.
B. Airmon-ng is a component of the aircrack-ng suite of tools used to put wireless adaptors into monitor mode.
![]() A, C, and D are incorrect. A is incorrect because aireplay-ng is used to inject packets into a wireless network to generate traffic. C is incorrect because airodump-ng is used for wireless sniffing. D is incorrect because airdecap-ng is used for decryption of WEP- and WPA-encrypted PCAP files.
A, C, and D are incorrect. A is incorrect because aireplay-ng is used to inject packets into a wireless network to generate traffic. C is incorrect because airodump-ng is used for wireless sniffing. D is incorrect because airdecap-ng is used for decryption of WEP- and WPA-encrypted PCAP files.
2. Which type of primary frame (defined by the IEEE 802.11 wireless standard) enables stations to establish and sustain communication over the network with an access point?
A. Disassociation frame
B. Management frame
C. Data frame
D. Control frame
![]() B. Management frames enable stations to establish and sustain communication over the network with an access point.
B. Management frames enable stations to establish and sustain communication over the network with an access point.
![]() A, C, and D are incorrect. A is incorrect because disassociation frames are not a primary frame type; rather, they are a subtype of management frame. C is incorrect because data frames transfer information from higher layers of the OSI model. D is incorrect because control frames ensure that data frames are delivered to each station.
A, C, and D are incorrect. A is incorrect because disassociation frames are not a primary frame type; rather, they are a subtype of management frame. C is incorrect because data frames transfer information from higher layers of the OSI model. D is incorrect because control frames ensure that data frames are delivered to each station.
3. Which nmap flag is used to disable DNS resolution of hostnames?
A. -sL
B. -n
C. -oG
D. -Pn
![]() B. The
B. The -n nmap flag disables DNS resolution of hostnames.
![]() A, C, and D are incorrect. A is incorrect because the
A, C, and D are incorrect. A is incorrect because the -sL flag is used when listing multiple targets to be scanned. C is incorrect because the -oG flag saves scan output to file in an easily grep-able format. D is incorrect because the -Pn flag disables ping and skips host discovery.
4. What is the effect of the -PS flag in nmap?
A. Triggers SCTP discovery to named ports
B. Triggers TCP ACK discovery to named ports
C. Triggers UDP discovery to named ports
D. Triggers TCP SYN discovery to named ports
![]() D. The
D. The -PS flag is used for TCP SYN discovery to declared ports.
![]() A, B, and C are incorrect. A is incorrect because SCTP discovery is the result of the
A, B, and C are incorrect. A is incorrect because SCTP discovery is the result of the -PY flag. B is incorrect because TCP ACK discovery is the result of the -PA flag. C is incorrect because UDP discovery is the result of the -PU flag.
5. Which of the following is an active scanning technique used to aid in the process of information gathering, with the goal of identifying hosts that are alive and listening on the network?
A. Port scanning
B. Wardriving
C. Stumbling
D. Host discovery
![]() D. Host discovery is an active scanning technique used to aid in the process of information gathering, with the goal of identifying hosts that are alive and listening on the network. The simplest method of host discovery is a discovery scan, which is typically a ping-only scan. A caveat must be given here, however, as oftentimes a target network will automatically drop all ICMP requests. In cases such as these, a stealth connection attempt to a common port or service such as SSH on port 22 or HTTP on port 80 can be an effective method of determining which hosts are up and available on a network.
D. Host discovery is an active scanning technique used to aid in the process of information gathering, with the goal of identifying hosts that are alive and listening on the network. The simplest method of host discovery is a discovery scan, which is typically a ping-only scan. A caveat must be given here, however, as oftentimes a target network will automatically drop all ICMP requests. In cases such as these, a stealth connection attempt to a common port or service such as SSH on port 22 or HTTP on port 80 can be an effective method of determining which hosts are up and available on a network.
![]() A, B, and C are incorrect. A is incorrect because port scanning is the process of querying individual ports at an IP address to determine if they are open and what services might be running. B is incorrect because wardriving is the practice of scanning for wireless access points from a moving vehicle. C is incorrect because stumbling is a surveillance technique that is used to discover SSIDs, router information, signal strength, MAC addresses, and other information pertinent to an 802.11 wireless network.
A, B, and C are incorrect. A is incorrect because port scanning is the process of querying individual ports at an IP address to determine if they are open and what services might be running. B is incorrect because wardriving is the practice of scanning for wireless access points from a moving vehicle. C is incorrect because stumbling is a surveillance technique that is used to discover SSIDs, router information, signal strength, MAC addresses, and other information pertinent to an 802.11 wireless network.
6. Which open-source command-line tool is used for several penetration test–focused activities on both wired and wireless networks, such as surveying hosts for open ports, fingerprinting operating systems, and collecting service banners?
A. Shodan
B. Nmap
C. Aircrack-ng
D. Theharvester
![]() B. Nmap is an open-source command-line tool that is used for several penetration test–focused activities, such as surveying hosts for open ports, fingerprinting operating systems, and collecting service banners. Nmap provides effective enumeration of networks (and identification of targets within the same), hosts (such as OS fingerprinting with the
B. Nmap is an open-source command-line tool that is used for several penetration test–focused activities, such as surveying hosts for open ports, fingerprinting operating systems, and collecting service banners. Nmap provides effective enumeration of networks (and identification of targets within the same), hosts (such as OS fingerprinting with the -O or -A flag), and services (with the -sV or -A flag) with its default options. With the use of NSE—the Nmap Scripting Engine—nmap can provide even greater levels of detail.
![]() A, C, and D are incorrect. A is incorrect because Shodan is an Internet of Things search engine. C is incorrect because aircrack-ng is a suite of tools used in penetration testing of wireless networks alone. In addition, aircrack-ng is unable to survey for open ports or operating system fingerprints; it instead is used for monitoring, attacking, and cracking 802.11 wireless traffic, in addition to testing Wi-Fi cards and driver capabilities (more information can be found at the aircrack-ng project website, www.aircrack-ng.org). D is incorrect because theharvester is a command-line tool for collecting information about a target domain name via targeted search engine queries.
A, C, and D are incorrect. A is incorrect because Shodan is an Internet of Things search engine. C is incorrect because aircrack-ng is a suite of tools used in penetration testing of wireless networks alone. In addition, aircrack-ng is unable to survey for open ports or operating system fingerprints; it instead is used for monitoring, attacking, and cracking 802.11 wireless traffic, in addition to testing Wi-Fi cards and driver capabilities (more information can be found at the aircrack-ng project website, www.aircrack-ng.org). D is incorrect because theharvester is a command-line tool for collecting information about a target domain name via targeted search engine queries.
7. What is the effect of the -v flag in nmap?
A. Denotes a list of targets to scan
B. Prevents DNS resolution
C. Increases the verbosity level of scan output
D. Disables ping and skips host discovery
![]() C. The
C. The -v flag in nmap increases the verbosity level of scan output.
![]() A, B, and D are incorrect. A is incorrect because a network (in the form of a CIDR notation subnet, such as 10.0.1.0/24) to scan should follow the
A, B, and D are incorrect. A is incorrect because a network (in the form of a CIDR notation subnet, such as 10.0.1.0/24) to scan should follow the -sL flag in nmap. It is important to note that the -sL flag will result in nmap not sending any packets to the targets in question; rather, nmap will simply perform reverse-DNS resolution on the target IP addresses to learn the relevant hostnames. B is incorrect because DNS resolution of hostnames is disabled when the -n flag is used. D is incorrect because pings are disabled and host discovery is skipped when the -Pn flag is used.
8. Which of the following is an open-source suite of tools useful for conducting RF communication monitoring and security testing of wireless networks?
A. Shodan
B. Aircrack-ng
C. Nmap
D. Theharvester
![]() B. Of the options listed, aircrack-ng is best described as an open-source suite of tools useful for conducting RF communication monitoring and security testing of wireless networks.
B. Of the options listed, aircrack-ng is best described as an open-source suite of tools useful for conducting RF communication monitoring and security testing of wireless networks.
![]() A, C, and D are incorrect. Neither Shodan, nmap, nor theharvester is a suite of tools used for security testing of wireless networks. Shodan is an Internet of Things search engine and, as such, focuses on items that are connected to the Internet. Nmap is a port-scanning tool used for active reconnaissance of a target organization, network, or host. Theharvester is a command-line tool for collecting information about a target domain name via targeted search engine queries.
A, C, and D are incorrect. Neither Shodan, nmap, nor theharvester is a suite of tools used for security testing of wireless networks. Shodan is an Internet of Things search engine and, as such, focuses on items that are connected to the Internet. Nmap is a port-scanning tool used for active reconnaissance of a target organization, network, or host. Theharvester is a command-line tool for collecting information about a target domain name via targeted search engine queries.
9. Which popular tool is used for wireless discovery and offers many of the same features as airodump-ng?
A. Kismet
B. Nmap
C. Shodan
D. Onesixtyone
![]() A. Kismet is used for wireless discovery and has many of the same features as airodump-ng. Kismet excels at detecting existing networks in wireless channels, sniffing out data, and detecting intrusions.
A. Kismet is used for wireless discovery and has many of the same features as airodump-ng. Kismet excels at detecting existing networks in wireless channels, sniffing out data, and detecting intrusions.
![]() B, C, and D are incorrect. Neither nmap, Shodan, nor onesixtyone is used for wireless discovery. Nmap is a port-scanning tool that is used for active reconnaissance of a target organization, network, or host. Shodan is an Internet of Things search engine and, as such, focuses on items that are connected to the Internet. Finally, onesixtyone is an SNMP scanner and enumerator. All these tools may be used over wired or wireless connections.
B, C, and D are incorrect. Neither nmap, Shodan, nor onesixtyone is used for wireless discovery. Nmap is a port-scanning tool that is used for active reconnaissance of a target organization, network, or host. Shodan is an Internet of Things search engine and, as such, focuses on items that are connected to the Internet. Finally, onesixtyone is an SNMP scanner and enumerator. All these tools may be used over wired or wireless connections.
10. Which type of primary frame (defined by the IEEE 802.11 wireless standard) facilitates delivery of data frames to each station?
A. Deauthentication frame
B. Disassociation frame
C. Control frame
D. Management frame
![]() C. Control frames facilitate data frame delivery to each station.
C. Control frames facilitate data frame delivery to each station.
![]() A, B, and D are incorrect. A and B are incorrect because deauthentication and disassociation frames are subtypes of the management frame and do not facilitate data frame delivery. D is incorrect because management frames enable stations to establish and sustain communication.
A, B, and D are incorrect. A and B are incorrect because deauthentication and disassociation frames are subtypes of the management frame and do not facilitate data frame delivery. D is incorrect because management frames enable stations to establish and sustain communication.
11. Which subtype of management frame contains details about a wireless access point (including but not limited to the SSID, encryption details, MAC address, and Wi-Fi channel) that can enable a malicious agent to eavesdrop on a wireless network?
A. Authentication frame
B. Request to Send (RTS) frame
C. Beacon frame
D. Association request frame
![]() C. A beacon frame contains details about a wireless access point (such as the SSID, encryption details, MAC address, and Wi-Fi channel) that can enable a malicious agent to eavesdrop on a wireless network. This is because of the way devices “remember” wireless networks. A beacon frame says to all devices in the area, “This is $Company_Network,” whether the device represents that network or not. When a device tries to connect to a Wi-Fi network after powering on or checking for a signal, it runs through its internal list of remembered Wi-Fi networks until it finds a network that is broadcasting. The problem is that there is no verification mechanism that confirms that the source of the beacon frame is legitimately the network in question; therefore, a malicious agent could run a rogue access point with the same SSID name to trick devices into connecting to it, and then route all incoming traffic through Burp or another proxy to monitor network use, collect passwords, or identify shared storage on the host in question.
C. A beacon frame contains details about a wireless access point (such as the SSID, encryption details, MAC address, and Wi-Fi channel) that can enable a malicious agent to eavesdrop on a wireless network. This is because of the way devices “remember” wireless networks. A beacon frame says to all devices in the area, “This is $Company_Network,” whether the device represents that network or not. When a device tries to connect to a Wi-Fi network after powering on or checking for a signal, it runs through its internal list of remembered Wi-Fi networks until it finds a network that is broadcasting. The problem is that there is no verification mechanism that confirms that the source of the beacon frame is legitimately the network in question; therefore, a malicious agent could run a rogue access point with the same SSID name to trick devices into connecting to it, and then route all incoming traffic through Burp or another proxy to monitor network use, collect passwords, or identify shared storage on the host in question.
![]() A, B, and D are incorrect. A and D are incorrect because while subtypes of management frame, neither authentication frames nor association request frames can be described as detailed in the question, with numerous descriptions of the wireless network in question. B is incorrect because a Request to Send (RTS) frame is a subtype of the control frame rather than a subtype of the management frame.
A, B, and D are incorrect. A and D are incorrect because while subtypes of management frame, neither authentication frames nor association request frames can be described as detailed in the question, with numerous descriptions of the wireless network in question. B is incorrect because a Request to Send (RTS) frame is a subtype of the control frame rather than a subtype of the management frame.
12. What is the effect of the -Pn flag in nmap?
A. Disables ping and skips host discovery
B. Prevents DNS resolution
C. Disables port scanning and forces a simple ping scan
D. Outputs scan details in XML format
![]() A. The
A. The -Pn flag in nmap disables ping and skips host discovery.
![]() B, C, and D are incorrect. B is incorrect because the disabling of DNS resolution is the expected outcome of adding the
B, C, and D are incorrect. B is incorrect because the disabling of DNS resolution is the expected outcome of adding the -n flag to an nmap command. C is incorrect because the -sn flag in nmap disables port scanning, forcing a simple ping scan. D is incorrect because the -oX flag dumps scan output to an XML file for future use.
13. Which nmap flag should precede a file containing a list of targets to be scanned?
A. -Pn
B. -iL
C. -sn
D. -oA
![]() B. The
B. The -iL nmap flag should precede a file containing a list of targets to be scanned.
![]() A, C, and D are incorrect. A is incorrect because pings are disabled and host discovery is skipped when the
A, C, and D are incorrect. A is incorrect because pings are disabled and host discovery is skipped when the -Pn flag is used. C is incorrect because port scanning is disabled with the -sn flag, resulting in only a ping scan to the named target. D is incorrect because the -oA flag is used to save the scan output in each of the three formats nmap can provide: normal text, grep-able formatting, and XML.
14. Which of the following is not a primary type of frame defined by the IEEE 802.11 wireless communication standard?
A. Control frame
B. Beacon frame
C. Data frame
D. Management frame
![]() B. A beacon frame is a subtype of the management frame. As such, it is not a primary frame type and is therefore the correct answer for this question.
B. A beacon frame is a subtype of the management frame. As such, it is not a primary frame type and is therefore the correct answer for this question.
![]() A, C, and D are incorrect. The control, data, and management frames are all primary frame types. Pay careful attention to questions that are stated with a negating term such as “is not” or “are not.”
A, C, and D are incorrect. The control, data, and management frames are all primary frame types. Pay careful attention to questions that are stated with a negating term such as “is not” or “are not.”
Consider the following nmap output for the next three questions:
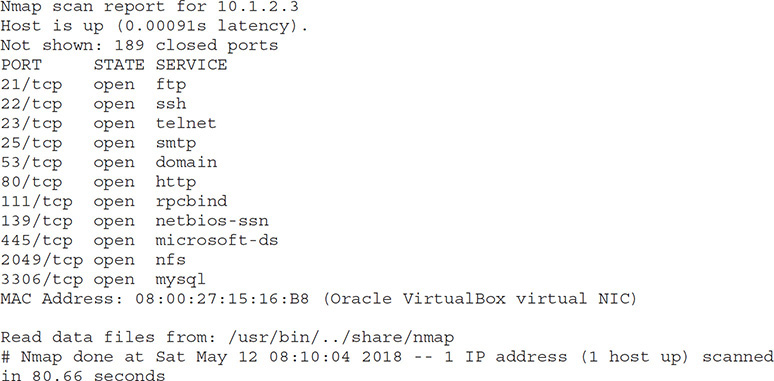
15. Which of the following nmap options would result in the ports shown being scanned?
A. -sL
B. -top-ports=200
C. -v
D. -sS
![]() B. The correct answer is
B. The correct answer is -top-ports=200. The clue here is in the total count of ports listed as scanned; 11 open ports shown plus 189 closed ports not shown would mean that only 200 ports were probed in this scan.
![]() A, C, and D are incorrect. None of the options listed impact which ports are probed in an nmap scan. A is incorrect because a network (in the form of a CIDR notation subnet, such as 10.0.1.0/24) to scan should follow the
A, C, and D are incorrect. None of the options listed impact which ports are probed in an nmap scan. A is incorrect because a network (in the form of a CIDR notation subnet, such as 10.0.1.0/24) to scan should follow the -sL flag in nmap. It is important to note that the -sL flag will result in nmap not sending any packets to the targets in question; rather, nmap will simply perform reverse-DNS resolution on the target IP addresses to learn the relevant hostnames. C is also incorrect because the -v flag increases output verbosity in nmap. D is incorrect because the -sS flag is used to denote a TCP SYN scan, which is also known as a stealth scan. This is due to the way TCP communications are conducted, requiring what is known as a three-way handshake. Typically, a client reaches out to a server with a SYN request. The server responds with a SYN/ACK response. In a normal three-way handshake, the client would then respond with an ACK, and a TCP socket connection would be established. The -sS flag subverts this structured connection mechanism by replacing the final ACK response (which would establish a TCP socket connection, and almost certainly ensure that the attacker’s IP address would end up in the target system’s logs) with an RST request, effectively destroying the three-way handshake before it is completed. In doing this, most services will discard the connection attempt entirely, not bothering to log anything. Compare this with the -sT flag, which completes TCP connect() attempts. Rather than tearing down the three-way handshake with an RST packet, the -sT flag ensures that the final ACK is sent; this scan method is by far the most reliable (in that it perfectly emulates how clients connect to TCP-based services) but is noisy and will almost certainly result in the attacking IP address being logged on the target system or network.
16. Of the following options, which nmap flag could produce output in the format shown?
A. -oX
B. -iL
C. -oN
D. -T
![]() C. Of the options listed, only
C. Of the options listed, only -oN would produce the output shown in the sample.
![]() A, B, and D are incorrect. A is incorrect because while it is the only other option that produces an output file, the
A, B, and D are incorrect. A is incorrect because while it is the only other option that produces an output file, the -oX flag produces an XML document, not an easily human-readable document like in the sample. B and D are incorrect because neither of these options affect file output format; the -iL flag precedes a file containing a series of targets for the scan, and the -T flag is used to modify the timing of the scan, either with a 0–5 scale or with the associated timing definitions: paranoid, sneaky, polite, normal, aggressive, and insane. More aggressive scan timings are noisier, more likely to generate detectable network traffic, and carry a greater risk of dropped packets as the timing is increased.
17. Which of the following flags would be recommended to further enumerate the server running on port 3306?
A. -sT
B. -script=mysql-info
C. -info3306
D. -script=http-enum
![]() B. Port 3306 is the standard port for MySQL installations; as such,
B. Port 3306 is the standard port for MySQL installations; as such, --script=mysql-info would be an excellent way to leverage the nmap scripting engine to glean further information about that possible target.
![]() A, C, and D are incorrect. A is incorrect because the
A, C, and D are incorrect. A is incorrect because the -sT flag is used to force TCP connect() scanning. In a full TCP connect() scan, rather than tearing down the three-way handshake with an RST packet, the -sT flag ensures that the final ACK is sent; this scan method is by far the most reliable (in that it perfectly emulates how clients connect to TCP-based services) but is noisy and will almost certainly result in the attacking IP address being logged on the target system or network. C is incorrect because -info3306 is not an nmap flag and will cause the tool to throw errors. D is incorrect because -script=http-enum would be useful for an HTTP server, not MySQL, as in this example.
Consider the following nmap output passage for the next two questions:
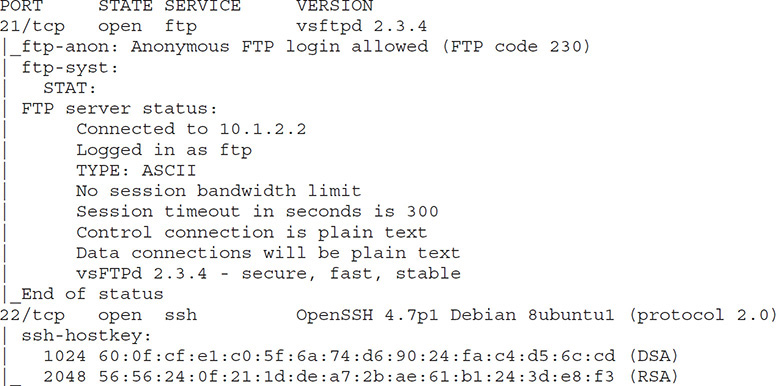
18. Of the following options, which flags could have produced the output presented?
A. -sU
B. -O
C. -sV
D. -A
![]() D. The
D. The -A flag will perform both service identification (as denoted by the identification of the FTP server software and version in use) and NSE scripting scanning (as denoted by the breakdown of scripting output results under the FTP scan heading), in addition to OS detection and traceroute data.
![]() A, B, and C are incorrect. A is incorrect because the
A, B, and C are incorrect. A is incorrect because the -sU flag is used to run UDP scans of targets. B is incorrect because the -O flag only causes nmap to perform OS fingerprinting. C is incorrect because the -sV flag only causes service identification.
19. In the output presented, which NSE script revealed that the FTP server present permits anonymous login?
A. ftp-syst
B. ssh-hostkey
C. ftp-anon
D. FTP server status
![]() C. Based on the output shown, the
C. Based on the output shown, the ftp-anon script reveals that anonymous FTP connections are allowed.
![]() A, B, and D are incorrect. A is incorrect because the
A, B, and D are incorrect. A is incorrect because the ftp-syst script harvests simple data about the FTP server in question. B is incorrect because the ssh-hostkey script identifies the DSA and RSA SSH hostkeys for the server. D is incorrect because the line FTP server status is only part of the output of the ftp-syst script.
20. Which of the following NSE scripts would be best used to enumerate shared storage volumes on a network? (Choose two.)
A. smb-enum-shares
B. smb-enum-domains
C. smtp-enum-users
D. nfs-showmount
![]() A and D. SMB and NFS are common network storage protocols. As such,
A and D. SMB and NFS are common network storage protocols. As such, smb-enum-shares is an excellent candidate to further enumerate an SMB share. The nfs-showmount script identifies all shared directories as advertised by an NFS server, similar to the *nix showmount -e command, which identifies all directories on a local system that are being exported or made available to external systems.
![]() B and C are incorrect. B is incorrect because the
B and C are incorrect. B is incorrect because the smb-enum-domains NSE script would be most effective at enumerating domains on a target system and their policies. C is incorrect because SMTP is the Simple Mail Transfer Protocol, and the smtp-enum-users NSE script would be effective at identifying valid users on an SMTP server.
