CHAPTER 4
Vulnerability Scanning and Analysis
This chapter includes questions on the following topics:
• Conducting information gathering using appropriate techniques
• Conducting vulnerability scans
• Analyzing vulnerability scan results
• The process of leveraging information to prepare for exploitation
• Weaknesses related to specialized systems
• Using nmap for information-gathering purposes
• Analysis of tool output or data related to a penetration test
Closely connected with network scanning and discovery, vulnerability scanning is another critical component of a penetration tester’s toolbox. Vulnerability scanning builds on the knowledge gleaned from network scanning and enumeration and is where a penetration tester begins to identify priority targets for attack and exploitation. Many considerations must be weighed when planning a vulnerability scan: the time available can limit the depth to which a penetration tester can investigate issues, for instance, or there could be compliance-based concerns that have special requirements as laid out by various laws or regulations. If a white box assessment is being performed, this may necessarily involve credential scans, wherein the scanning tool in use is provided legitimate authentication credentials; the goal in this case is to test not only the external portions of the service or resources in question, but to test the ability of the service or resource to properly “sandbox” a user, preventing them from accessing tools and options for which they have no need.
Once a vulnerability scan is completed, it falls to the penetration tester to not only categorize the information they have gained but to verify and prioritize it; the act of attempting active exploitation of discovered vulnerabilities is what distinguishes a penetration test from a simple vulnerability assessment. This means the tester cannot simply trust the output of a scanning tool; findings must be verified to prevent false positives, and identified vulnerabilities should be prioritized so the most likely means of ingress is tested first. This prioritization—commonly referred to as “finding low-hanging fruit”—is a key element of successful penetration testing. Given the fact that penetration tests take place over a finite amount of time, it is in a tester’s interest to minimize their time invested per activity while maximizing their return on that time. This further requires the tester to develop a plan of attack by mapping discovered vulnerabilities to potential exploits or attack methods. Even with this much work put in ahead of an attack, success is likely to require extra attention—exploit code may need to be modified or cross-compiled, or successful exploitation of a system may require the tester to chain together multiple, lower-criticality vulnerabilities, for example.
Finally, this chapter will assess a candidate’s awareness of specific weaknesses associated with specific, specialized computer system classes. IoT or embedded devices are prone to their own general group of vulnerabilities, for instance, as are point-of-sale and SCADA systems. Understanding these vulnerability types can be a real force multiplier for a penetration tester, as knowing these vulnerability trends can make it much easier to identify the “low-hanging fruit.”
Q QUESTIONS
1. Which of the following is not a publicly accessible list used for vulnerability research and analysis?
A. Common Vulnerabilities and Exposures (CVE)
B. The Japan Computer Emergency Response Team (JPCERT)
C. Common Weakness Enumeration (CWE)
D. Common Attack Pattern Enumeration and Classification (CAPEC)
2. Which of the following is a public, vendor-neutral forum and mailing list that publishes vulnerability analysis details, exploitation techniques, and other relevant information for the security community?
A. US-CERT
B. MITRE
C. NIST
D. Full Disclosure
3. Which of the following is a major benefit of running a credentialed vulnerability scan over a uncredentialed scan?
A. Uncredentialed vulnerability scans are known to more commonly produce false positives.
B. Credentialed vulnerability scans more accurately represent real-world conditions when facing an outside threat actor.
C. Uncredentialed vulnerability scans tend to reveal more issues, so credentialed scans are easier to report.
D. Credentialed vulnerability scans are usually faster.
4. The National Institute of Standards and Technology (NIST) maintains what public resource for analysis on vulnerabilities published to the CVE dictionary, using the Common Vulnerability Scoring System (CVSS)?
A. Full Disclosure
B. National Vulnerability Database (NVD)
C. CWE
D. OWASP
5. A discovery scan in nmap is described by which of the following statements? (Choose two.)
A. It’s an active scanning technique.
B. It scans all 65,000+ possible network ports.
C. It performs a simple ping test to determine if a host is up and alive on the network.
D. It identifies software and versions running on open ports.
6. A stealth scan in nmap is denoted by the __________ flag and leverages the use of __________ when probing ports.
A. -sT, TCP Connect() calls
B. -sT, SYN packets
C. -sU, RST packets
D. -sS, SYN and RST packets
7. Security Content Automation Protocol (SCAP) aware scanners, such as Tenable’s Nessus, test the implementation of best-practice security configuration baselines from the Center for Internet Security (CIS). For which type of scan are these baselines most helpful?
A. Full scan
B. Discovery scan
C. Compliance scan
D. Stealth scan
8. Supervisory Control and Data Acquisition (SCADA) is a real-time control system that monitors the health and status of components of what type of infrastructure?
A. Industrial control systems (ICS) used in manufacturing, power generation, water treatment, and other public works
B. Point-of-sale systems
C. Embedded systems such as MP3 players, smartphones, and e-readers
D. Biometric scanners such as fingerprint readers and retinal scanners
9. Which of the following is not an example of a nontraditional asset?
A. Real-time operating systems (RTOSs)
B. SCADA networks
C. Linux servers
D. IoT devices
10. The tool shown in the following illustration provides web and web application security testing capabilities. What is it called?
A. Nikto
B. W3AF
C. Burp Suite
D. OpenVAS
11. Which of the following is not an issue to consider when performing a vulnerability scan?
A. Services and protocols known to be in use in the environment
B. Bandwidth limitations
C. Overall topology of the network in question
D. The public reputation of the developers of the software or operating system being tested
12. Why might it be necessary to throttle queries to a target system during a penetration test?
A. To keep your testing system from getting slow
B. To prevent your hard drive from filling up due to the volume of data
C. To more accurately mirror real-world service-use conditions
D. To avoid taking down a system or service through effectively running a denial-of-service attack, or to avoid detection by not tripping log sensors or other alerts
13. In addition to their value in compliance-based penetration tests, which of the following is another benefit of the use of testing an environment against CIS preconfigured operational baseline scan templates?
A. Less work on the part of the penetration tester
B. Simplification of the scanning process
C. Aid in the development of organizational security policy
D. Assisting the organization with asset categorization and implementation of industry best practices
14. Which of the following is not a benefit of performing vulnerability scanning during a penetration test?
A. Aids penetration testers in prioritizing attack vectors for manual testing based on those most likely to produce findings
B. Thorough review of application code outside of a running system for details on the vulnerability
C. Assists in time management during a penetration test by automating vulnerability discovery
D. Improves the overall quality of the penetration test and the resulting report by providing the penetration tester a sense of focus on higher priority (that is, higher risk) vulnerabilities
15. As shown by the following output, this open-source command-line tool is a web server scanner that tests for dangerous files or CGIs, outdated server software, and other problems.
A. OpenVAS
B. Dirbuster
C. Nikto
D. Gobuster
16. Which of the following is not a commonly reported theme or issue in vulnerability scan results?
A. Observations
B. Exploits
C. Vulnerabilities
D. Failure to apply industry best practices
17. Which of the following is an example of a vulnerability identification that is typical of those detailed in the results of a vulnerability scan?
A. Software version numbers revealed during scanning.
B. HTTP Strict Transport Security is not enabled on a system web application.
C. OS fingerprinting reveals a system running Windows XP SP2, suggesting susceptibility to MS08-067.
D. SSLv2 and v3 found to be enabled.
18. Which of the following is an example of a failure to apply best practices typical of those detailed in the results of a vulnerability scan?
A. HTTP Strict Transport Security is not enabled on a system web application.
B. Target is identified as an Apache web server.
C. Software version numbers are revealed during scanning.
D. OS fingerprinting reveals a system running Windows XP SP2, suggesting susceptibility to MS08-067.
19. Which of the following is an example of an observation typical of those detailed in the results of a vulnerability scan?
A. OS fingerprinting reveals a system running Windows XP SP2, suggesting susceptibility to MS08-067.
B. A web application’s robots.txt file specifically denies all access to the /cgi-bin/ directory.
C. HTTP Strict Transport Security is not enabled on a system web application.
D. SSLv2 and v3 found to be enabled.
20. Which of the following is an example of static application analysis?
A. Scanning a running web application with Nikto and dirbuster to identify potential flaws
B. Analyzing the written code for an application outside of an actively running instance
C. Using Burp to crawl through the user interface for a web application
D. Fuzzing a running web application with garbage input to assess the application’s reaction
21. Which of the following is an example of dynamic application analysis?
A. Searching for programming flaws in written code for an application outside of an actively running instance
B. Fuzzing a running web application with garbage input to assess the application’s reaction
C. Searching for maliciously placed backdoors in written code
D. Analyzing application code and comparing functions to known best practices in programming such as query parameterization
22. Which of the following is not a detail of CVEs maintained by the CVE Numbering Authority?
A. PoC exploit code
B. CVE ID
C. Brief description of the vulnerability
D. External references or advisories
23. Which of the following is not a security weakness category as maintained by CWE?
A. Programming concepts
B. Development concepts
C. Research concepts
D. Architectural concepts
24. Which of the following is an identifier provided for CWE entries?
A. Weakness ID
B. Modes of introduction
C. Likelihood of exploit
D. Answers A, B, and C
25. The sample screen shown next displays the product of a scan from __________, a remote vulnerability-scanning tool that can help automate much of the penetration testing process. This tool supports both credentialed and uncredentialed scans, and is one of the most popular commercially available scanners on the market.
A. Nikto
B. OpenVAS
C. Burp Suite
D. Nessus
26. The CAPEC details thousands of known attack patterns and methodologies. Which of the following is not an attack domain recognized by CAPEC?
A. Social Engineering
B. Supply Chain
C. Physical Security
D. Firmware
27. During a penetration test, you identify and harvest encrypted user passwords from a web application database. You do not have access to a rainbow table for the encryption algorithm used, and do not have any success with dictionary attacks. What remaining attack method—typically one of last resort—could you leverage as an attacker to attempt to decrypt the passwords you have harvested?
A. Strategic guessing
B. Brute force
C. XSS
D. CSRF
28. Which password-cracking method leverages wordlists that are expanded with discovered real-world passwords as they are discovered?
A. Dictionary attack
B. Brute force
C. Calling the owner of the account and posing as a member of the IT department to get them to reveal the password
D. Rainbow tables
29. Which password-cracking method requires extensive storage capacity, sometimes more than 300 GB in total?
A. Brute force
B. Wordlist attack
C. Rainbow tables
D. Dictionary attack
30. Nessus incorporates NVD’s CVSS when producing vulnerability severity information. Which of the following is not a use for this information for a penetration tester?
A. Mapping vulnerabilities to potential exploits
B. Informing the penetration tester’s plan of attack
C. Identifying potential exploits as appropriate for the software versions in use on a target
D. Populating graphs with data for press releases
31. During a penetration test, you identify a live local file inclusion (LFI) vulnerability on a web application that allows you to see any file on the target system, including the /etc/passwd and /etc/shadow files. With this information, you feed password hashes from the shadow file into hashcat and crack them with a dictionary attack, ultimately finding a match that allows you to obtain a low-privilege shell on the target system. What is this an example of?
A. Exploit chaining
B. Exploit modification
C. Social engineering
D. Failure to adhere to industry best practices
32. During a penetration test of a web application, you determine that user session IDs (or tokens) are revealed in the URL after authentication. You further discover that these session IDs are predictably incremented values, and not randomly generated numbers or strings. To which of the following attack types would this application likely be susceptible?
A. SQL injection
B. Remote file inclusion
C. Cross-site scripting
D. Session hijacking
33. Which of the following is a danger associated with the use of default authentication credentials on a system or service?
A. Admin passwords may be easily guessed.
B. Admin passwords are almost guaranteed to be in any major wordlist used in dictionary attacks.
C. Admin passwords will be found with a brief Internet search for the service in question.
D. All of the above.
34. Which of the following is not a potential characteristic of weak authentication credentials?
A. Password is a dictionary word.
B. Password is over 50 characters long with a large character set.
C. Password length is less than eight characters total.
D. Password is identical to username.
35. The tool shown next is a free and open-source password cracker available for many *nix and Windows variants that leverages the system CPU. This sample output shows the results of cracking a list of hashes using a wordlist.
A. John the Ripper
B. Hashcat
C. Cewl
D. Medusa
36. Which type of web application test attempts to provoke unexpected responses by feeding arbitrary values into web page parameters?
A. Error code analysis
B. Cross-site scripting
C. HTTP parameter pollution
D. Cross-site request forgery
37. Which of the following is not a potential consequence of a lack of error handling or excessively verbose error handling in servers, web applications, and databases?
A. OS or software version disclosure
B. Disclosure of the username context for the application or database
C. Clickjacking
D. Disclosure of directory information for the application or database
38. In a text field on a web application, you discover that by entering a semicolon and the *nix command `id`, you can find the username context for the application on the server. What is this an example of?
A. Brute force
B. Command injection
C. Session hijacking
D. Replay attack
39. What is the process of finding all available information on a target system or service in support of developing a plan of attack?
A. Vulnerability mapping
B. Vulnerability scanning
C. Enumeration
D. Fingerprinting
40. Which term describes the process of detailing identified security flaws and their locations?
A. Vulnerability mapping
B. Cross-compiling
C. Cross-building
D. Exploit modification
41. Which act describes the writing of a first-of-its-kind exploit to demonstrate or weaponize a vulnerability?
A. Exploit modification
B. Cross-compiling
C. Proof-of-concept development
D. Threat hunting
42. Which of the following is not a result of appropriately prioritizing activities in preparation for a penetration test?
A. Time required for individual activities is decreased, and return on time invested is increased.
B. “Low-hanging fruit” is identified and focused on faster.
C. A plan of attack with a greater chance of success can be developed faster.
D. None of these; all options present are effects of activity prioritization in preparation for and during a penetration test.
43. The tool shown in the following illustration is a free and open-source password cracker available for Linux, Windows, and macOS that leverages system CPUs or GPUs. This sample output shows the results of cracking a list of hashes using a wordlist.
A. Hashcat
B. John the Ripper
C. Cain and Abel
D. Hydra
44. Which CAPEC-recognized domain of attack focuses on the manipulation of computer hardware and software within their respective lifecycles?
A. Software
B. Supply Chain
C. Physical Security
D. Communications
45. Which knowledge base maintained by MITRE details techniques and adversarial behavior that can be used to attack organizations?
A. CWE
B. CVE
C. CAPEC
D. ATT&CK
46. Which of the following is not a vulnerability scanner commonly used in penetration testing?
A. Nessus
B. OpenVAS
C. SQLmap
D. IDA
47. In addition to serving as a method of policy compliance evaluation, __________ is a method for using specific standards for automated discovery and measurement of vulnerabilities.
A. HIPAA
B. FISMA
C. SCAP
D. PCI DSS
QUICK ANSWER KEY
1. B
2. D
3. A
4. B
5. A, C
6. D
7. C
8. A
9. C
10. C
11. D
12. D
13. D
14. B
15. C
16. B
17. C
18. A
19. B
20. B
21. B
22. A
23. A
24. D
25. D
26. D
27. B
28. A
29. C
30. D
31. A
32. D
33. D
34. B
35. A
36. C
37. C
38. B
39. C
40. A
41. C
42. D
43. A
44. B
45. D
46. D
47. C
A IN-DEPTH ANSWERS
1. Which of the following is not a publicly accessible list used for vulnerability research and analysis?
A. Common Vulnerabilities and Exposures (CVE)
B. The Japan Computer Emergency Response Team (JPCERT)
C. Common Weakness Enumeration (CWE)
D. Common Attack Pattern Enumeration and Classification (CAPEC)
![]() B is correct. The Japan Computer Emergency Response Team, or JPCERT, is a cybersecurity information-sharing organization backed by the Japanese government, rather than a specific resource provided by such an organization.
B is correct. The Japan Computer Emergency Response Team, or JPCERT, is a cybersecurity information-sharing organization backed by the Japanese government, rather than a specific resource provided by such an organization.
![]() A, C, and D are incorrect. A is incorrect because the Common Vulnerabilities and Exposures, or CVE (https://cve.mitre.org), is a list of entries for publicly known cybersecurity vulnerabilities provided by MITRE (which is the name of the company, rather than an acronym). Each entry contains an identification number, a description, and at least one public reference for further information. C is incorrect because the Common Weakness Enumeration, or CWE (https://cwe.mitre.org), is a community-developed list of common software security weaknesses managed by MITRE. Per MITRE, CWE provides a baseline for weakness identification, mitigation, and prevention efforts. D is incorrect because the Common Attack Pattern Enumeration and Classification, or CAPEC (https://capec.mitre.org), is a dictionary provided by MITRE that serves to help classify various types of attacks so that they can be better understood by analysts, developers, testers, and educators.
A, C, and D are incorrect. A is incorrect because the Common Vulnerabilities and Exposures, or CVE (https://cve.mitre.org), is a list of entries for publicly known cybersecurity vulnerabilities provided by MITRE (which is the name of the company, rather than an acronym). Each entry contains an identification number, a description, and at least one public reference for further information. C is incorrect because the Common Weakness Enumeration, or CWE (https://cwe.mitre.org), is a community-developed list of common software security weaknesses managed by MITRE. Per MITRE, CWE provides a baseline for weakness identification, mitigation, and prevention efforts. D is incorrect because the Common Attack Pattern Enumeration and Classification, or CAPEC (https://capec.mitre.org), is a dictionary provided by MITRE that serves to help classify various types of attacks so that they can be better understood by analysts, developers, testers, and educators.
2. Which of the following is a public, vendor-neutral forum and mailing list that publishes vulnerability analysis details, exploitation techniques, and other relevant information for the security community?
A. US-CERT
B. MITRE
C. NIST
D. Full Disclosure
![]() D is correct. Full Disclosure (http://seclists.org/fulldisclosure) is a public, vendor-neutral forum for detailed discussion of vulnerabilities and exploitation techniques. It also provides tools, papers, news, and events of interest to the cybersecurity community.
D is correct. Full Disclosure (http://seclists.org/fulldisclosure) is a public, vendor-neutral forum for detailed discussion of vulnerabilities and exploitation techniques. It also provides tools, papers, news, and events of interest to the cybersecurity community.
![]() A, B, and C are incorrect. A is incorrect because US-CERT—or the U.S. Computer Emergency Readiness Team—is a core sponsor of resources managed by MITRE, such as CVE and CWE, rather than a specific cybersecurity information resource. While US-CERT does maintain mailing lists and vulnerability information (for example, its alerts feed for current security issues and vulnerabilities, which may be found at www.us-cert.gov/ncas/alerts), the organization itself is not such a list. B is incorrect because while MITRE does perform security research and publish its findings publicly, it is the organization that provides the CVE, CWE, and CAPEC resources to the community, and is not a specific cybersecurity information resource. C is incorrect because NIST—or the National Institute of Standards and Technology—is a U.S. government organization under the U.S. Department of Commerce that conducts vulnerability research and publishes its findings publicly.
A, B, and C are incorrect. A is incorrect because US-CERT—or the U.S. Computer Emergency Readiness Team—is a core sponsor of resources managed by MITRE, such as CVE and CWE, rather than a specific cybersecurity information resource. While US-CERT does maintain mailing lists and vulnerability information (for example, its alerts feed for current security issues and vulnerabilities, which may be found at www.us-cert.gov/ncas/alerts), the organization itself is not such a list. B is incorrect because while MITRE does perform security research and publish its findings publicly, it is the organization that provides the CVE, CWE, and CAPEC resources to the community, and is not a specific cybersecurity information resource. C is incorrect because NIST—or the National Institute of Standards and Technology—is a U.S. government organization under the U.S. Department of Commerce that conducts vulnerability research and publishes its findings publicly.
3. Which of the following is a major benefit of running a credentialed vulnerability scan over a uncredentialed scan?
A. Uncredentialed vulnerability scans are known to more commonly produce false positives.
B. Credentialed vulnerability scans more accurately represent real-world conditions when facing an outside threat actor.
C. Uncredentialed vulnerability scans tend to reveal more issues, so credentialed scans are easier to report.
D. Credentialed vulnerability scans are usually faster.
![]() A is correct. Uncredentialed scans are known to more readily produce false positives when scanning systems and applications. As such, credentialed scans are desirable due to their tendency to cut down on such unwarranted alerts during a penetration test.
A is correct. Uncredentialed scans are known to more readily produce false positives when scanning systems and applications. As such, credentialed scans are desirable due to their tendency to cut down on such unwarranted alerts during a penetration test.
![]() B, C, and D are incorrect. In fact, they are patently false. B is incorrect because an outside threat actor is much less likely to have authorized credentials than an insider threat. C is incorrect because uncredentialed scans are not necessarily likely to reveal more security findings than credentialed scans. D is incorrect because credentialed scans generally take longer than uncredentialed scans, simply because they have more attack surface to scan.
B, C, and D are incorrect. In fact, they are patently false. B is incorrect because an outside threat actor is much less likely to have authorized credentials than an insider threat. C is incorrect because uncredentialed scans are not necessarily likely to reveal more security findings than credentialed scans. D is incorrect because credentialed scans generally take longer than uncredentialed scans, simply because they have more attack surface to scan.
4. The National Institute of Standards and Technology (NIST) maintains what public resource for analysis on vulnerabilities published to the CVE dictionary, using the Common Vulnerability Scoring System (CVSS)?
A. Full Disclosure
B. National Vulnerability Database (NVD)
C. CWE
D. OWASP
![]() B is correct. NIST maintains the National Vulnerability Database, or NVD.
B is correct. NIST maintains the National Vulnerability Database, or NVD.
![]() A, C, and D are incorrect. A is incorrect because Full Disclosure is a public forum and is not managed by NIST, nor does it strictly provide analysis on vulnerabilities published to the CVE dictionary. Indeed, vulnerabilities are regularly found on Full Disclosure before they are assigned a CVE number. C is incorrect because the CWE is maintained by MITRE, and it provides a community-developed list of common software security weaknesses. D is incorrect because the OWASP, or Open Web Application Security Project, is an open community designed to enable organizations to conceive, develop, acquire, operate, and maintain applications that can be trusted. OWASP is managed by the OWASP Foundation.
A, C, and D are incorrect. A is incorrect because Full Disclosure is a public forum and is not managed by NIST, nor does it strictly provide analysis on vulnerabilities published to the CVE dictionary. Indeed, vulnerabilities are regularly found on Full Disclosure before they are assigned a CVE number. C is incorrect because the CWE is maintained by MITRE, and it provides a community-developed list of common software security weaknesses. D is incorrect because the OWASP, or Open Web Application Security Project, is an open community designed to enable organizations to conceive, develop, acquire, operate, and maintain applications that can be trusted. OWASP is managed by the OWASP Foundation.
5. A discovery scan in nmap is described by which of the following statements? (Choose two.)
A. It’s an active scanning technique.
B. It scans all 65,000+ possible network ports.
C. It performs a simple ping test to determine if a host is up and alive on the network.
D. It identifies software and versions running on open ports.
![]() A and C are correct. A discovery scan is an active scanning technique that relies on performing a ping test to determine if a host is up and alive on a network.
A and C are correct. A discovery scan is an active scanning technique that relies on performing a ping test to determine if a host is up and alive on a network.
![]() B and D are incorrect. B and D are incorrect because both a scan of all 65,535 ports and the identification of software and versions running on open ports would be part of a full scan, not a discovery scan.
B and D are incorrect. B and D are incorrect because both a scan of all 65,535 ports and the identification of software and versions running on open ports would be part of a full scan, not a discovery scan.
6. A stealth scan in nmap is denoted by the __________ flag and leverages the use of __________ when probing ports.
A. -sT, TCP Connect() calls
B. -sT, SYN packets
C. -sU, RST packets
D. -sS, SYN and RST packets
![]() D is correct. A stealth scan in nmap is denoted by the
D is correct. A stealth scan in nmap is denoted by the -sS flag and leverages the use of SYN and RST packets when probing ports. If a server responds with a SYN/ACK packet to continue a three-way TCP handshake, nmap trashes the connection by sending an RST packet; this often prevents scans from showing up in server logs.
![]() A, B, and C are incorrect. A is incorrect because the
A, B, and C are incorrect. A is incorrect because the -sT flag denotes a full TCP connect scan, which does use TCP Connect() calls. B is incorrect because the -sT flag denotes a full TCP connect scan, as detailed for answer A. C is incorrect because the -sU flag denotes a UDP scan, which does not perform a three-way handshake.
7. Security Content Automation Protocol (SCAP) aware scanners, such as Tenable’s Nessus, test the implementation of best-practice security configuration baselines from the Center for Internet Security (CIS). For which type of scan are these baselines most helpful?
A. Full scan
B. Discovery scan
C. Compliance scan
D. Stealth scan
![]() C is correct. The baselines established by SCAP and embedded in scanners such as Nessus are most helpful during a compliance scan.
C is correct. The baselines established by SCAP and embedded in scanners such as Nessus are most helpful during a compliance scan.
![]() A, B, and D are incorrect. A and B are incorrect because while Nessus can be configured to run a full system scan or a host discovery scan, these scan types are more broadly useful in general to penetration testers and are often more easily performed with another tool, such as nmap. D is incorrect because a stealth scan is a specific type of nmap scan that only performs a portion of a standard TCP three-way handshake in order to prevent establishing a full connection (which would often be detectable in application or server logs). While helpful in many penetration tests, SCAP guidelines (managed by NIST) are specifically designed to test compliance with regulatory frameworks. Since the question specifically refers to vulnerability scanners with respect to SCAP information, the best answer here is C.
A, B, and D are incorrect. A and B are incorrect because while Nessus can be configured to run a full system scan or a host discovery scan, these scan types are more broadly useful in general to penetration testers and are often more easily performed with another tool, such as nmap. D is incorrect because a stealth scan is a specific type of nmap scan that only performs a portion of a standard TCP three-way handshake in order to prevent establishing a full connection (which would often be detectable in application or server logs). While helpful in many penetration tests, SCAP guidelines (managed by NIST) are specifically designed to test compliance with regulatory frameworks. Since the question specifically refers to vulnerability scanners with respect to SCAP information, the best answer here is C.
8. Supervisory Control and Data Acquisition (SCADA) is a real-time control system that monitors the health and status of components of what type of infrastructure?
A. Industrial control systems (ICS) used in manufacturing, power generation, water treatment, and other public works
B. Point-of-sale systems
C. Embedded systems such as MP3 players, smartphones, and e-readers
D. Biometric scanners such as fingerprint readers and retinal scanners
![]() A is correct. Supervisory Control and Data Acquisition (SCADA) is a real-time control system that monitors the health and status of components of industrial control systems (ICS) used in manufacturing, power generation, water treatment, and other public works.
A is correct. Supervisory Control and Data Acquisition (SCADA) is a real-time control system that monitors the health and status of components of industrial control systems (ICS) used in manufacturing, power generation, water treatment, and other public works.
![]() B, C, and D are incorrect. All answer choices presented are specialized systems with their own quirks. Point-of-sale systems are going to need to meet PCI compliance guidelines and are updated irregularly due to the nature of how retail businesses approach information security. Embedded systems are hardwired combinations of computer hardware and software, designed and programmed for a single purpose. Due to their nature as being wholly contained computer environments, upgrading individual physical components of embedded devices is often difficult or impossible. It is worth noting that while embedded systems can be part of SCADA architecture, a SCADA system does not monitor all embedded devices—it would only monitor those that are components of industrial control systems for which the behavior and data need to be accessible by SCADA system users. Biometric scanners are going to need to meet HIPAA guidelines as biometric data is personally identifiable medical information, and they are often embedded devices on top of that.
B, C, and D are incorrect. All answer choices presented are specialized systems with their own quirks. Point-of-sale systems are going to need to meet PCI compliance guidelines and are updated irregularly due to the nature of how retail businesses approach information security. Embedded systems are hardwired combinations of computer hardware and software, designed and programmed for a single purpose. Due to their nature as being wholly contained computer environments, upgrading individual physical components of embedded devices is often difficult or impossible. It is worth noting that while embedded systems can be part of SCADA architecture, a SCADA system does not monitor all embedded devices—it would only monitor those that are components of industrial control systems for which the behavior and data need to be accessible by SCADA system users. Biometric scanners are going to need to meet HIPAA guidelines as biometric data is personally identifiable medical information, and they are often embedded devices on top of that.
9. Which of the following is not an example of a nontraditional asset?
A. Real-time operating systems (RTOSs)
B. SCADA networks
C. Linux servers
D. IoT devices
![]() C is correct. Linux servers are common computer hardware, and as such are considered a rather traditional sort of information system asset.
C is correct. Linux servers are common computer hardware, and as such are considered a rather traditional sort of information system asset.
![]() A, B, and D are incorrect. These are all nontraditional assets. Real-time operating systems, or RTOS, are chiefly required to adhere to deadlines associated with their tasks. SCADA networks consist of a control system and various industrial control systems used in manufacturing, power management, water treatment, or other public works. IoT devices are nontraditional assets because they often consist of embedded systems that are infrequently patched or updated.
A, B, and D are incorrect. These are all nontraditional assets. Real-time operating systems, or RTOS, are chiefly required to adhere to deadlines associated with their tasks. SCADA networks consist of a control system and various industrial control systems used in manufacturing, power management, water treatment, or other public works. IoT devices are nontraditional assets because they often consist of embedded systems that are infrequently patched or updated.
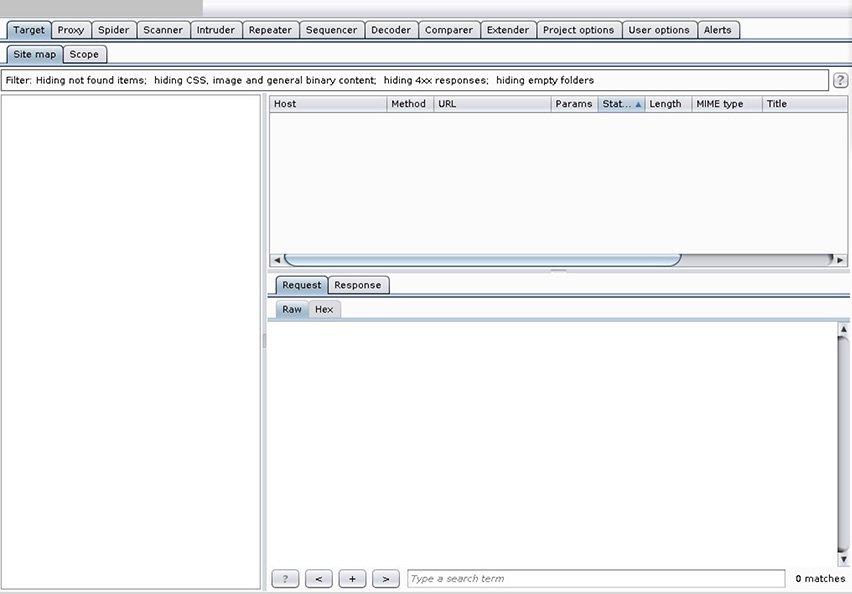
10. The tool shown in the following illustration provides web and web application security testing capabilities. What is it called?
A. Nikto
B. W3AF
C. Burp Suite
D. OpenVAS
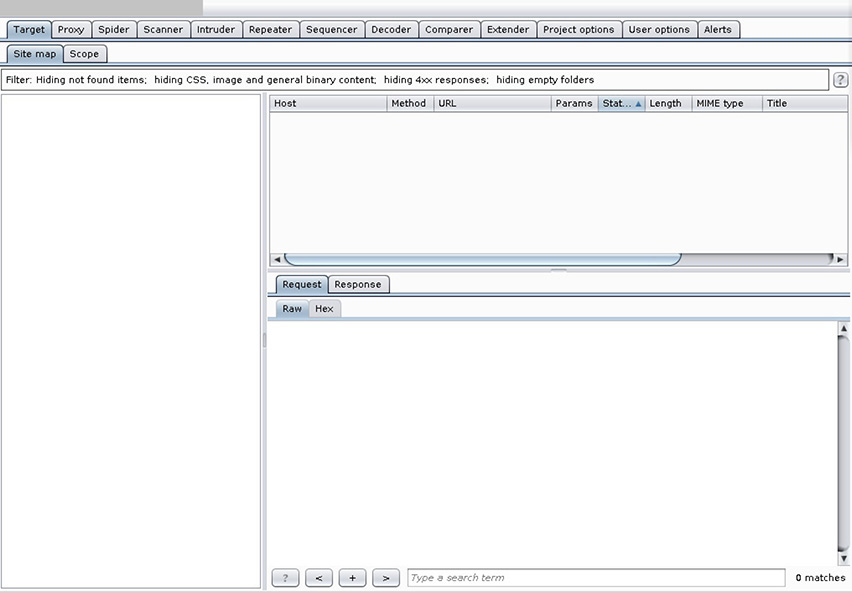
![]() C is correct. The screenshot shows the main tool window of Burp Suite Pro.
C is correct. The screenshot shows the main tool window of Burp Suite Pro.
![]() A, B, and D are incorrect. A is easily identifiable as incorrect, as Nikto is a command-line tool exclusively. Since the image in question is of a graphical interface, you can determine that Nikto is incorrect. B and D are tools that, while presented in a graphical interface, look quite different from Burp Suite Pro. You will need to be familiar with the interface of many of these tools—not only to obtain your Pentester+ certification, but to be an effective penetration tester.
A, B, and D are incorrect. A is easily identifiable as incorrect, as Nikto is a command-line tool exclusively. Since the image in question is of a graphical interface, you can determine that Nikto is incorrect. B and D are tools that, while presented in a graphical interface, look quite different from Burp Suite Pro. You will need to be familiar with the interface of many of these tools—not only to obtain your Pentester+ certification, but to be an effective penetration tester.
11. Which of the following is not an issue to consider when performing a vulnerability scan?
A. Services and protocols known to be in use in the environment
B. Bandwidth limitations
C. Overall topology of the network in question
D. The public reputation of the developers of the software or operating system being tested
![]() D is correct. The public reputation of the developers of software or an operating system are the concern of those developers alone; the job of the penetration tester is to test and verify system security.
D is correct. The public reputation of the developers of software or an operating system are the concern of those developers alone; the job of the penetration tester is to test and verify system security.
![]() A, B, and C are incorrect. All of these are concerns that need to be tracked by a penetration tester. Services and protocols in use in the environment may respond to a simple port scan by crashing entirely, which would be detrimental to production in a live environment. Bandwidth limitations could be problematic in that aggressive scans could inadvertently cause a denial of service for real-world users; the topology of the network in question is also a concern for the same reason.
A, B, and C are incorrect. All of these are concerns that need to be tracked by a penetration tester. Services and protocols in use in the environment may respond to a simple port scan by crashing entirely, which would be detrimental to production in a live environment. Bandwidth limitations could be problematic in that aggressive scans could inadvertently cause a denial of service for real-world users; the topology of the network in question is also a concern for the same reason.
12. Why might it be necessary to throttle queries to a target system during a penetration test?
A. To keep your testing system from getting slow
B. To prevent your hard drive from filling up due to the volume of data
C. To more accurately mirror real-world service-use conditions
D. To avoid taking down a system or service through effectively running a denial-of-service attack, or to avoid detection by not tripping log sensors or other alerts
![]() D is correct. Throttling queries to a target system necessarily adds to the load that system encounters. Since some scanners can be aggressive, letting them run at full speed can sometimes be enough to take the system down, since overloading a system in such a manner is only distinguishable from an intentional denial of service (DoS) attack in that it was not intended to be malicious. Moreover, aggressive scans can trip warning sensors or alerts; if conducting a red team assessment, this could be detrimental to your success as a penetration tester since an alert blue team is able to counter your activities more readily.
D is correct. Throttling queries to a target system necessarily adds to the load that system encounters. Since some scanners can be aggressive, letting them run at full speed can sometimes be enough to take the system down, since overloading a system in such a manner is only distinguishable from an intentional denial of service (DoS) attack in that it was not intended to be malicious. Moreover, aggressive scans can trip warning sensors or alerts; if conducting a red team assessment, this could be detrimental to your success as a penetration tester since an alert blue team is able to counter your activities more readily.
![]() A, B, and C are incorrect. None of these are concerns for the penetration tester. What’s more, C is patently false, as real-world service use would not be as thorough as a vulnerability scan in making requests or queries.
A, B, and C are incorrect. None of these are concerns for the penetration tester. What’s more, C is patently false, as real-world service use would not be as thorough as a vulnerability scan in making requests or queries.
13. In addition to their value in compliance-based penetration tests, which of the following is another benefit of the use of testing an environment against CIS preconfigured operational baseline scan templates?
A. Less work on the part of the penetration tester
B. Simplification of the scanning process
C. Aid in the development of organizational security policy
D. Assisting the organization with asset categorization and implementation of industry best practices
![]() D is correct. Preconfigured operational baseline scan templates allow an organization to better understand their technological footprint, which simplifies asset categorization and empowers them to identify and implement industry best practices that may be applicable to their architecture and environment.
D is correct. Preconfigured operational baseline scan templates allow an organization to better understand their technological footprint, which simplifies asset categorization and empowers them to identify and implement industry best practices that may be applicable to their architecture and environment.
![]() A, B, and C are incorrect. A and B are incorrect because the use of preconfigured scan templates only serves to highlight specific concerns relevant to the organization and the environment in question. The penetration tester will still need to review scan results, and the amount of complication added by clicking an option to perform a scan with a predefined template is essentially zero. C is incorrect because these baseline scan templates are designed to assess compliance to an existing regulatory framework such as HIPAA or PCI DSS. In other words, organizational security policy should already have been developed with those frameworks in mind. The scan serves to verify their implementation by existing policy, rather than design policy from scratch.
A, B, and C are incorrect. A and B are incorrect because the use of preconfigured scan templates only serves to highlight specific concerns relevant to the organization and the environment in question. The penetration tester will still need to review scan results, and the amount of complication added by clicking an option to perform a scan with a predefined template is essentially zero. C is incorrect because these baseline scan templates are designed to assess compliance to an existing regulatory framework such as HIPAA or PCI DSS. In other words, organizational security policy should already have been developed with those frameworks in mind. The scan serves to verify their implementation by existing policy, rather than design policy from scratch.
14. Which of the following is not a benefit of performing vulnerability scanning during a penetration test?
A. Aids penetration testers in prioritizing attack vectors for manual testing based on those most likely to produce findings
B. Thorough review of application code outside of a running system for details on the vulnerability
C. Assists in time management during a penetration test by automating vulnerability discovery
D. Improves the overall quality of the penetration test and the resulting report by providing the penetration tester a sense of focus on higher priority (that is, higher risk) vulnerabilities
![]() B is correct. This is an example of the potential benefits of static application analysis, not a benefit of vulnerability scanning.
B is correct. This is an example of the potential benefits of static application analysis, not a benefit of vulnerability scanning.
![]() A, C, and D are incorrect. These are all examples of benefits of leveraging vulnerability mapping during a penetration test, making them all incorrect answers. Prioritization of likely successful attack vectors, time management, and overall penetration test quality improvement are all expected benefits of thorough vulnerability mapping.
A, C, and D are incorrect. These are all examples of benefits of leveraging vulnerability mapping during a penetration test, making them all incorrect answers. Prioritization of likely successful attack vectors, time management, and overall penetration test quality improvement are all expected benefits of thorough vulnerability mapping.
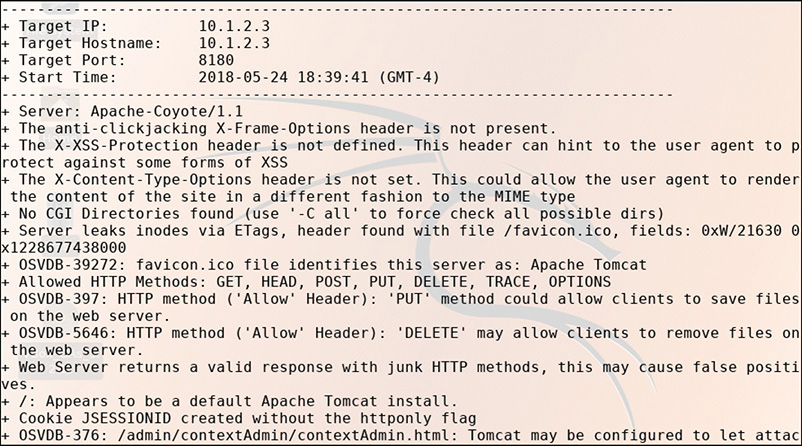
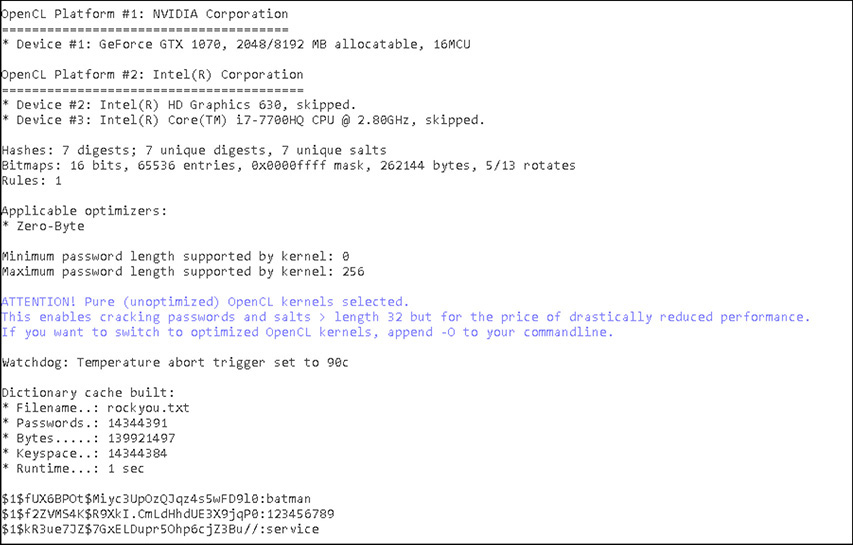
15. As shown by the following output, this open-source command-line tool is a web server scanner that tests for dangerous files or CGIs, outdated server software, and other problems.
A. OpenVAS
B. Dirbuster
C. Nikto
D. Gobuster
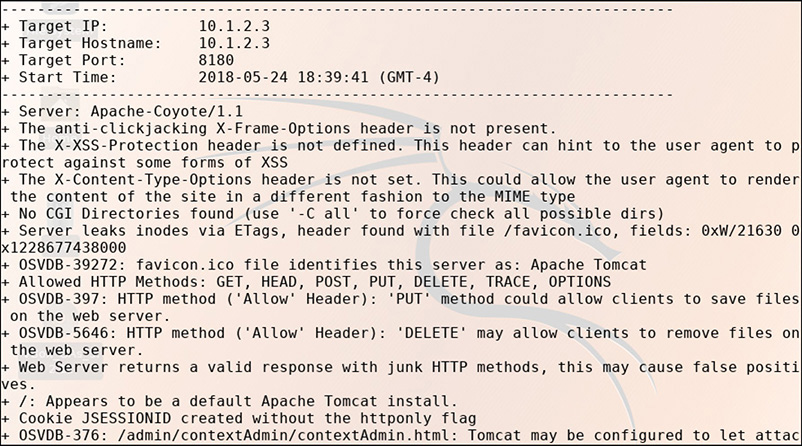
![]() C is correct. The screenshot shows the beginning of a scan using Nikto.
C is correct. The screenshot shows the beginning of a scan using Nikto.
![]() A, B, and D are incorrect. A may be safely ruled out as OpenVAS is a graphical interface tool. Since the image in question is of a command-line interface, you can easily determine that OpenVAS is incorrect. B and D are tools that serve to help enumerate directories and file names present on web servers; dirbuster may be used via the command line or graphical interface, and gobuster is a simplified, functionally similar tool exclusive to the command line.
A, B, and D are incorrect. A may be safely ruled out as OpenVAS is a graphical interface tool. Since the image in question is of a command-line interface, you can easily determine that OpenVAS is incorrect. B and D are tools that serve to help enumerate directories and file names present on web servers; dirbuster may be used via the command line or graphical interface, and gobuster is a simplified, functionally similar tool exclusive to the command line.
16. Which of the following is not a commonly reported theme or issue in vulnerability scan results?
A. Observations
B. Exploits
C. Vulnerabilities
D. Failure to apply industry best practices
![]() B is correct. While it is common for vulnerability scan results to detail vulnerabilities specific to a system, a functional exploit that takes advantage of that vulnerability is not going to be presented in the vulnerability scan results.
B is correct. While it is common for vulnerability scan results to detail vulnerabilities specific to a system, a functional exploit that takes advantage of that vulnerability is not going to be presented in the vulnerability scan results.
![]() A, C, and D are incorrect because all are examples of commonly reported themes or issues found in vulnerability scan results. Observations may include items such as software or OS version numbers. Vulnerabilities would be highlighted when identified, such as through software or OS build version numbers or based on port scan results. Failure to apply industry best practices is highlighted with vulnerability scanners such as Nessus and Burp Suite, and may include items such as a failure to enable HTTP Secure Transport Security or leaving SSLv2 or v3 enabled on a system.
A, C, and D are incorrect because all are examples of commonly reported themes or issues found in vulnerability scan results. Observations may include items such as software or OS version numbers. Vulnerabilities would be highlighted when identified, such as through software or OS build version numbers or based on port scan results. Failure to apply industry best practices is highlighted with vulnerability scanners such as Nessus and Burp Suite, and may include items such as a failure to enable HTTP Secure Transport Security or leaving SSLv2 or v3 enabled on a system.
17. Which of the following is an example of a vulnerability identification that is typical of those detailed in the results of a vulnerability scan?
A. Software version numbers revealed during scanning.
B. HTTP Strict Transport Security is not enabled on a system web application.
C. OS fingerprinting reveals a system running Windows XP SP2, suggesting susceptibility to MS08-067.
D. SSLv2 and v3 found to be enabled.
![]() C is correct. OS fingerprinting revealing susceptibility to exploits targeting MS08-067 would be an example of a vulnerability identified by a vulnerability scan.
C is correct. OS fingerprinting revealing susceptibility to exploits targeting MS08-067 would be an example of a vulnerability identified by a vulnerability scan.
![]() A, B, and D are incorrect. A is incorrect because it is an example of an observation that may be identified during a vulnerability scan. B and D are incorrect because they are examples of identified failure to apply industry best practices.
A, B, and D are incorrect. A is incorrect because it is an example of an observation that may be identified during a vulnerability scan. B and D are incorrect because they are examples of identified failure to apply industry best practices.
18. Which of the following is an example of a failure to apply best practices typical of those detailed in the results of a vulnerability scan?
A. HTTP Strict Transport Security is not enabled on a system web application.
B. Target is identified as an Apache web server.
C. Software version numbers are revealed during scanning.
D. OS fingerprinting reveals a system running Windows XP SP2, suggesting susceptibility to MS08-067.
![]() A is correct. Not requiring HTTP Strict Transport Security is an example of a failure to apply best practices that may be identified during a vulnerability scan.
A is correct. Not requiring HTTP Strict Transport Security is an example of a failure to apply best practices that may be identified during a vulnerability scan.
![]() B, C, and D are incorrect. B and C are incorrect because these are examples of observations that may be identified during a vulnerability scan. D is incorrect because it is an example of a specific vulnerability identified during a penetration test.
B, C, and D are incorrect. B and C are incorrect because these are examples of observations that may be identified during a vulnerability scan. D is incorrect because it is an example of a specific vulnerability identified during a penetration test.
19. Which of the following is an example of an observation typical of those detailed in the results of a vulnerability scan?
A. OS fingerprinting reveals a system running Windows XP SP2, suggesting susceptibility to MS08-067.
B. A web application’s robots.txt file specifically denies all access to the /cgi-bin/ directory.
C. HTTP Strict Transport Security is not enabled on a system web application.
D. SSLv2 and v3 found to be enabled.
![]() B is correct. The contents of a web application’s robots.txt file are often valuable to a malicious attacker or penetration tester, and are therefore provided as an observation in many vulnerability scanners.
B is correct. The contents of a web application’s robots.txt file are often valuable to a malicious attacker or penetration tester, and are therefore provided as an observation in many vulnerability scanners.
![]() A, C, and D are incorrect. A is incorrect because it is an example of a specific vulnerability identified during a penetration test. C and D are incorrect because they are examples of industry best practices found to not be applied to a running system.
A, C, and D are incorrect. A is incorrect because it is an example of a specific vulnerability identified during a penetration test. C and D are incorrect because they are examples of industry best practices found to not be applied to a running system.
20. Which of the following is an example of static application analysis?
A. Scanning a running web application with Nikto and dirbuster to identify potential flaws
B. Analyzing the written code for an application outside of an actively running instance
C. Using Burp to crawl through the user interface for a web application
D. Fuzzing a running web application with garbage input to assess the application’s reaction
![]() B is correct. Analyzing written code without seeing it executed on a live system is a classic example of static application analysis.
B is correct. Analyzing written code without seeing it executed on a live system is a classic example of static application analysis.
![]() A, C, and D are incorrect because all options listed are assessments made against a currently running system or application. As such, they are all examples of dynamic application analysis.
A, C, and D are incorrect because all options listed are assessments made against a currently running system or application. As such, they are all examples of dynamic application analysis.
21. Which of the following is an example of dynamic application analysis?
A. Searching for programming flaws in written code for an application outside of an actively running instance
B. Fuzzing a running web application with garbage input to assess the application’s reaction
C. Searching for maliciously placed backdoors in written code
D. Analyzing application code and comparing functions to known best practices in programming such as query parameterization
![]() B is correct. Fuzzing a running web application with garbage input to hunt for DoS or buffer overflow opportunities is a classic example of dynamic application analysis.
B is correct. Fuzzing a running web application with garbage input to hunt for DoS or buffer overflow opportunities is a classic example of dynamic application analysis.
![]() A, C, and D are incorrect because all options listed are assessments made against code that is not actively being run. As such, they are all examples of static application analysis.
A, C, and D are incorrect because all options listed are assessments made against code that is not actively being run. As such, they are all examples of static application analysis.
22. Which of the following is not a detail of CVEs maintained by the CVE Numbering Authority?
A. PoC exploit code
B. CVE ID
C. Brief description of the vulnerability
D. External references or advisories
![]() A is correct. PoC exploit code is not a detail of CVEs maintained by the CVE Numbering Authority. Note, however, that such code could be found in the external references or advisories that are maintained as a detail of a given CVE.
A is correct. PoC exploit code is not a detail of CVEs maintained by the CVE Numbering Authority. Note, however, that such code could be found in the external references or advisories that are maintained as a detail of a given CVE.
![]() B, C, and D are incorrect because all three items are key details of CVEs as maintained by the CVE Numbering Authority.
B, C, and D are incorrect because all three items are key details of CVEs as maintained by the CVE Numbering Authority.
23. Which of the following is not a security weakness category as maintained by CWE?
A. Programming concepts
B. Development concepts
C. Research concepts
D. Architectural concepts
![]() A is correct. Programming concepts are not a security weakness category as maintained by CWE. Be cautious with questions like this; programming-related weaknesses would likely be categorized as development concepts. Remember that the categories monitored by CWE are broad in scope.
A is correct. Programming concepts are not a security weakness category as maintained by CWE. Be cautious with questions like this; programming-related weaknesses would likely be categorized as development concepts. Remember that the categories monitored by CWE are broad in scope.
![]() B, C, and D are incorrect. Development concepts, research concepts, and architectural concepts are all security weakness categories as maintained by CWE, and are therefore incorrect answers for this question.
B, C, and D are incorrect. Development concepts, research concepts, and architectural concepts are all security weakness categories as maintained by CWE, and are therefore incorrect answers for this question.
24. Which of the following is an identifier provided for CWE entries?
A. Weakness ID
B. Modes of introduction
C. Likelihood of exploit
D. Answers A, B, and C
![]() D is correct. All specific items listed (weakness ID, modes of introduction, and likelihood of exploit) are identifiers provided for each CWE entry. As such, answer C (which explicitly includes all three named answers) is the correct choice.
D is correct. All specific items listed (weakness ID, modes of introduction, and likelihood of exploit) are identifiers provided for each CWE entry. As such, answer C (which explicitly includes all three named answers) is the correct choice.
![]() A, B, and C are incorrect. Be cautious with questions where answers such as “All of the above” or “Answers A, B, and C” are options. If you have difficulty choosing an individual choice, chances are excellent that the “All of the above” type answer is correct.
A, B, and C are incorrect. Be cautious with questions where answers such as “All of the above” or “Answers A, B, and C” are options. If you have difficulty choosing an individual choice, chances are excellent that the “All of the above” type answer is correct.
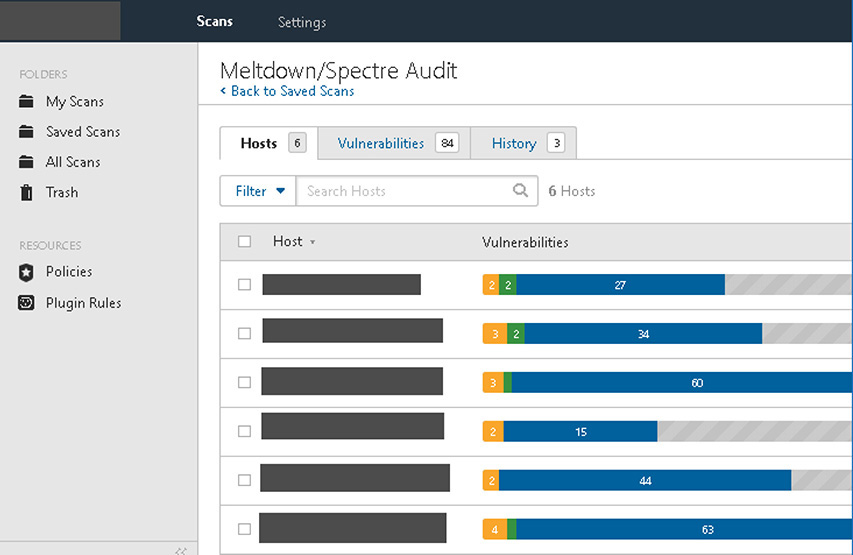
25. The sample screen shown next displays the product of a scan from __________, a remote vulnerability-scanning tool that can help automate much of the penetration testing process. This tool supports both credentialed and uncredentialed scans, and is one of the most popular commercially available scanners on the market.
A. Nikto
B. OpenVAS
C. Burp Suite
D. Nessus
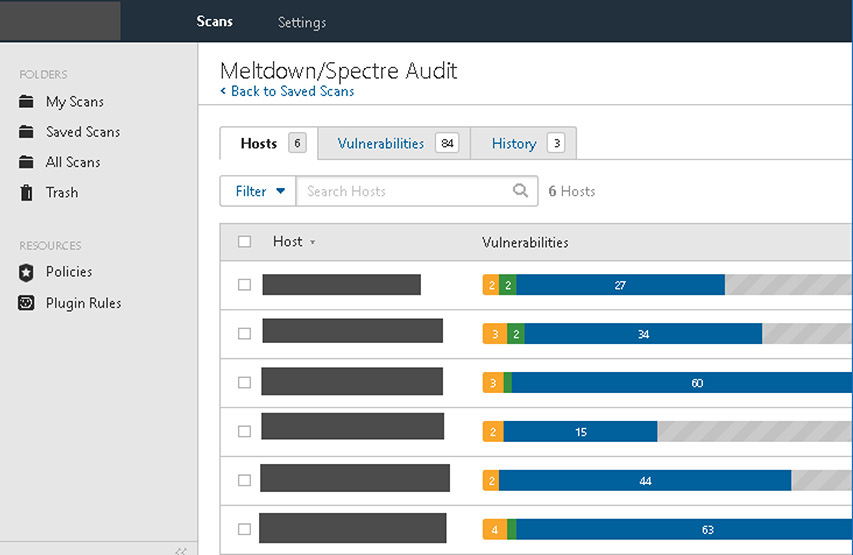
![]() D is correct. The screenshot shows a report that is typical of Tenable’s Nessus scanner.
D is correct. The screenshot shows a report that is typical of Tenable’s Nessus scanner.
![]() A, B, and C are incorrect. A is easily identifiable as incorrect, as Nikto is a command-line tool exclusively. Since the image in question is of a graphical interface, you can determine that Nikto is incorrect. B and C are tools that, while presented in a graphical interface, look quite different from Nessus. You will need to be familiar with the interface of many of these tools for the certification exam!
A, B, and C are incorrect. A is easily identifiable as incorrect, as Nikto is a command-line tool exclusively. Since the image in question is of a graphical interface, you can determine that Nikto is incorrect. B and C are tools that, while presented in a graphical interface, look quite different from Nessus. You will need to be familiar with the interface of many of these tools for the certification exam!
26. The CAPEC details thousands of known attack patterns and methodologies. Which of the following is not an attack domain recognized by CAPEC?
A. Social Engineering
B. Supply Chain
C. Physical Security
D. Firmware
![]() D is correct. Firmware attacks is not a dedicated category of attack domain per CAPEC categorization, making it the correct answer here. Real-world firmware attacks would likely be categorized as supply chain or hardware vulnerabilities.
D is correct. Firmware attacks is not a dedicated category of attack domain per CAPEC categorization, making it the correct answer here. Real-world firmware attacks would likely be categorized as supply chain or hardware vulnerabilities.
![]() A, B, and C are incorrect. Social engineering, supply chain attacks, and physical security attacks are all independently recognized domains of attack per CAPEC, and are therefore incorrect answers for this question.
A, B, and C are incorrect. Social engineering, supply chain attacks, and physical security attacks are all independently recognized domains of attack per CAPEC, and are therefore incorrect answers for this question.
27. During a penetration test, you identify and harvest encrypted user passwords from a web application database. You do not have access to a rainbow table for the encryption algorithm used, and do not have any success with dictionary attacks. What remaining attack method—typically one of last resort—could you leverage as an attacker to attempt to decrypt the passwords you have harvested?
A. Strategic guessing
B. Brute force
C. XSS
D. CSRF
![]() B is correct. Brute force is a valid means of password cracking or recovery, but is typically considered the approach of last resort due to its general unreliability when compared to dictionary or rainbow table attacks.
B is correct. Brute force is a valid means of password cracking or recovery, but is typically considered the approach of last resort due to its general unreliability when compared to dictionary or rainbow table attacks.
![]() A, C, and D are incorrect. A is incorrect because brute-force attempts are decidedly not strategic in their approach. Using raw computational power can be effective, but success rates with dictionary attacks are generally much higher. C and D are incorrect as cross-site scripting (XSS) and cross-site request forgery (CSRF) are vulnerabilities specific to websites and web applications, and are therefore not applicable in the context of password cracking.
A, C, and D are incorrect. A is incorrect because brute-force attempts are decidedly not strategic in their approach. Using raw computational power can be effective, but success rates with dictionary attacks are generally much higher. C and D are incorrect as cross-site scripting (XSS) and cross-site request forgery (CSRF) are vulnerabilities specific to websites and web applications, and are therefore not applicable in the context of password cracking.
28. Which password-cracking method leverages wordlists that are expanded with discovered real-world passwords as they are discovered?
A. Dictionary attack
B. Brute force
C. Calling the owner of the account and posing as a member of the IT department to get them to reveal the password
D. Rainbow tables
![]() A is correct. A dictionary attack uses existing wordlists that get expanded whenever real-world passwords are discovered.
A is correct. A dictionary attack uses existing wordlists that get expanded whenever real-world passwords are discovered.
![]() B, C, and D are incorrect. B is incorrect because brute-force attacks leverage raw computational power to attempt to crack a password, by trying every possible character combination with the given character set. C is incorrect because it describes a generic social engineering attempt. D is incorrect because rainbow tables are collections of pre-calculated password hashes for a given algorithm.
B, C, and D are incorrect. B is incorrect because brute-force attacks leverage raw computational power to attempt to crack a password, by trying every possible character combination with the given character set. C is incorrect because it describes a generic social engineering attempt. D is incorrect because rainbow tables are collections of pre-calculated password hashes for a given algorithm.
29. Which password-cracking method requires extensive storage capacity, sometimes more than 300 GB in total?
A. Brute force
B. Wordlist attack
C. Rainbow tables
D. Dictionary attack
![]() C is correct. Rainbow tables are effective but consist of massive tables of data for a given algorithm. It is not unheard of to see a rainbow table around 300 GB in total.
C is correct. Rainbow tables are effective but consist of massive tables of data for a given algorithm. It is not unheard of to see a rainbow table around 300 GB in total.
![]() A, B, and D are incorrect. A is incorrect because brute force is a valid means of password cracking or recovery, but is typically considered the approach of last resort due to its general inefficiency. B and D are incorrect because a wordlist attack is simply another name for a dictionary attack—and dictionary attacks do not require such massive volumes of storage.
A, B, and D are incorrect. A is incorrect because brute force is a valid means of password cracking or recovery, but is typically considered the approach of last resort due to its general inefficiency. B and D are incorrect because a wordlist attack is simply another name for a dictionary attack—and dictionary attacks do not require such massive volumes of storage.
30. Nessus incorporates NVD’s CVSS when producing vulnerability severity information. Which of the following is not a use for this information for a penetration tester?
A. Mapping vulnerabilities to potential exploits
B. Informing the penetration tester’s plan of attack
C. Identifying potential exploits as appropriate for the software versions in use on a target
D. Populating graphs with data for press releases
![]() D is correct. While Nessus, OpenVAS, and other scanners provide a great deal of information that can be useful to drive business decisions, such decisions are the purview of the client alone.
D is correct. While Nessus, OpenVAS, and other scanners provide a great deal of information that can be useful to drive business decisions, such decisions are the purview of the client alone.
![]() A, B, and C are incorrect because these are all valid uses of Nessus output for a penetration tester.
A, B, and C are incorrect because these are all valid uses of Nessus output for a penetration tester.
31. During a penetration test, you identify a live local file inclusion (LFI) vulnerability on a web application that allows you to see any file on the target system, including the /etc/passwd and /etc/shadow files. With this information, you feed password hashes from the shadow file into hashcat and crack them with a dictionary attack, ultimately finding a match that allows you to obtain a low-privilege shell on the target system. What is this an example of?
A. Exploit chaining
B. Exploit modification
C. Social engineering
D. Failure to adhere to industry best practices
![]() A is correct. This is an example of exploit chaining; in the example given, a local file inclusion vulnerability gives access to weak password hashes, which are then cracked to reveal valid logon credentials.
A is correct. This is an example of exploit chaining; in the example given, a local file inclusion vulnerability gives access to weak password hashes, which are then cracked to reveal valid logon credentials.
![]() B, C, and D are incorrect. B is incorrect because exploit modification indicates some change has been made to exploit code or the conditions under which the exploit is executed. C is incorrect because social engineering indicates that contact of another person has taken place to solicit information, usually in a manner that defuses any suspicion on the part of the target. D is incorrect because while a failure to adhere to best practices could have resulted in this vulnerability (by way of not updating, patching, or configuring the web application properly), the vulnerability in question could have been unknown to the developers. In such a case, a patch would not exist, and therefore adherence to best practices would be unable to stop the exploit of this vulnerability.
B, C, and D are incorrect. B is incorrect because exploit modification indicates some change has been made to exploit code or the conditions under which the exploit is executed. C is incorrect because social engineering indicates that contact of another person has taken place to solicit information, usually in a manner that defuses any suspicion on the part of the target. D is incorrect because while a failure to adhere to best practices could have resulted in this vulnerability (by way of not updating, patching, or configuring the web application properly), the vulnerability in question could have been unknown to the developers. In such a case, a patch would not exist, and therefore adherence to best practices would be unable to stop the exploit of this vulnerability.
32. During a penetration test of a web application, you determine that user session IDs (or tokens) are revealed in the URL after authentication. You further discover that these session IDs are predictably incremented values, and not randomly generated numbers or strings. To which of the following attack types would this application likely be susceptible?
A. SQL injection
B. Remote file inclusion
C. Cross-site scripting
D. Session hijacking
![]() D is correct. Since the session IDs are predictable, connecting to the web application with another user’s session ID would be relatively trivial. Given the options listed, this makes session hijacking the most likely vulnerability for this hypothetical web application.
D is correct. Since the session IDs are predictable, connecting to the web application with another user’s session ID would be relatively trivial. Given the options listed, this makes session hijacking the most likely vulnerability for this hypothetical web application.
![]() A, B, and C are incorrect. A can be safely ruled out here as there is no mention anywhere of a SQL database in the question. B is likewise eliminated, as there is no mention of the inclusion of a file from a source external to the web application server. C may also be ruled out because there is no mention of malicious code being sent to the target in secret as is expected of a cross-site scripting vulnerability.
A, B, and C are incorrect. A can be safely ruled out here as there is no mention anywhere of a SQL database in the question. B is likewise eliminated, as there is no mention of the inclusion of a file from a source external to the web application server. C may also be ruled out because there is no mention of malicious code being sent to the target in secret as is expected of a cross-site scripting vulnerability.
33. Which of the following is a danger associated with the use of default authentication credentials on a system or service?
A. Admin passwords may be easily guessed.
B. Admin passwords are almost guaranteed to be in any major wordlist used in dictionary attacks.
C. Admin passwords will be found with a brief Internet search for the service in question.
D. All of the above.
![]() D is correct. All the options listed are equally valid concerns for the use of default authentication credentials, making D the most correct choice.
D is correct. All the options listed are equally valid concerns for the use of default authentication credentials, making D the most correct choice.
![]() A, B, and C are incorrect. These are all are imperfect answers given the presence of “All of the above” for answer D. Passwords that can be easily guessed, found in existing dictionary attack wordlists, or found via a search engine are all threats to system and service security.
A, B, and C are incorrect. These are all are imperfect answers given the presence of “All of the above” for answer D. Passwords that can be easily guessed, found in existing dictionary attack wordlists, or found via a search engine are all threats to system and service security.
34. Which of the following is not a potential characteristic of weak authentication credentials?
A. Password is a dictionary word.
B. Password is over 50 characters long with a large character set.
C. Password length is less than eight characters total.
D. Password is identical to username.
![]() B is correct. A password over 50 characters long with a large character set would be nontrivially difficult to crack by any means—there is no metric by which such a password could be considered weak.
B is correct. A password over 50 characters long with a large character set would be nontrivially difficult to crack by any means—there is no metric by which such a password could be considered weak.
![]() A, C, and D are incorrect. Passwords that are dictionary words, identical to usernames, or less than eight characters long are all generally trivial to crack via dictionary attack, rainbow tables, or brute force. As such, they would all be examples of weak authentication credentials.
A, C, and D are incorrect. Passwords that are dictionary words, identical to usernames, or less than eight characters long are all generally trivial to crack via dictionary attack, rainbow tables, or brute force. As such, they would all be examples of weak authentication credentials.
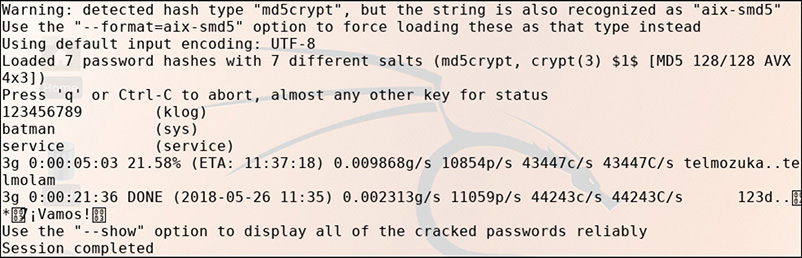
35. The tool shown next is a free and open-source password cracker available for many *nix and Windows variants that leverages the system CPU. This sample output shows the results of cracking a list of hashes using a wordlist.
A. John the Ripper
B. Hashcat
C. Cewl
D. Medusa
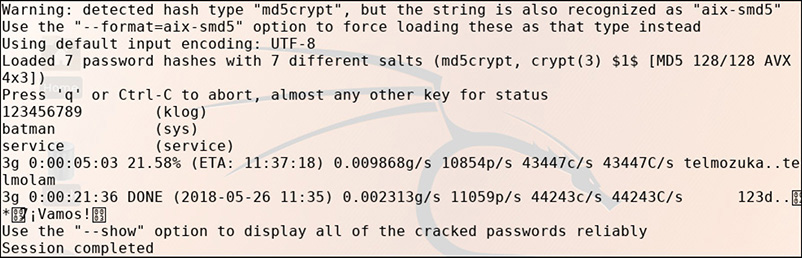
![]() A is correct. The screenshot shows output typical of John the Ripper when used to crack hashes using a wordlist.
A is correct. The screenshot shows output typical of John the Ripper when used to crack hashes using a wordlist.
![]() B, C, and D are incorrect. B is incorrect because Hashcat provides much more detail in its output, and is most often used to leverage GPUs rather than the system CPU; this would be annotated in the initial output of Hashcat. C is incorrect because Cewl is a custom wordlist generator that will crawl through a target website, identify unique words used on the site, and save them in a text file for the user. That text file may then be used to help crack password hashes with JTR or Hashcat. D is incorrect because Medusa is a parallelized, modular login brute-forcing tool that can be used to attack multiple services and protocols. Output typical of Medusa would show the results of each individual live attempt at brute-forcing a login.
B, C, and D are incorrect. B is incorrect because Hashcat provides much more detail in its output, and is most often used to leverage GPUs rather than the system CPU; this would be annotated in the initial output of Hashcat. C is incorrect because Cewl is a custom wordlist generator that will crawl through a target website, identify unique words used on the site, and save them in a text file for the user. That text file may then be used to help crack password hashes with JTR or Hashcat. D is incorrect because Medusa is a parallelized, modular login brute-forcing tool that can be used to attack multiple services and protocols. Output typical of Medusa would show the results of each individual live attempt at brute-forcing a login.
36. Which type of web application test attempts to provoke unexpected responses by feeding arbitrary values into web page parameters?
A. Error code analysis
B. Cross-site scripting
C. HTTP parameter pollution
D. Cross-site request forgery
![]() C is correct. The modification—or pollution—of HTTP parameters as they are sent to the web server is used to attempt to trigger unexpected behavior that may reveal other vulnerabilities or information disclosures.
C is correct. The modification—or pollution—of HTTP parameters as they are sent to the web server is used to attempt to trigger unexpected behavior that may reveal other vulnerabilities or information disclosures.
![]() A, B, and D are incorrect. A is incorrect because while error code analysis may be performed on the output of an HTTP parameter pollution test, it is not itself an attempt to invoke an unexpected response from a system. B is incorrect because there is no mention of malicious code being injected onto the site in question. D is incorrect because the issue presented fails to describe CSRF; there is no mention of a valid, authenticated user being tricked into sending a malicious request.
A, B, and D are incorrect. A is incorrect because while error code analysis may be performed on the output of an HTTP parameter pollution test, it is not itself an attempt to invoke an unexpected response from a system. B is incorrect because there is no mention of malicious code being injected onto the site in question. D is incorrect because the issue presented fails to describe CSRF; there is no mention of a valid, authenticated user being tricked into sending a malicious request.
37. Which of the following is not a potential consequence of a lack of error handling or excessively verbose error handling in servers, web applications, and databases?
A. OS or software version disclosure
B. Disclosure of the username context for the application or database
C. Clickjacking
D. Disclosure of directory information for the application or database
![]() C is correct. Improper error handling broadly is an information disclosure vulnerability; the type of data revealed varies depending on the developer and the programming language in question, but clickjacking is not a potential consequence of improper error handling.
C is correct. Improper error handling broadly is an information disclosure vulnerability; the type of data revealed varies depending on the developer and the programming language in question, but clickjacking is not a potential consequence of improper error handling.
![]() A, B, and D are incorrect. All these options are some sort of information disclosure; as such, they are commonly expected with improper error handling. In the context of this question, that makes these incorrect answers.
A, B, and D are incorrect. All these options are some sort of information disclosure; as such, they are commonly expected with improper error handling. In the context of this question, that makes these incorrect answers.
38. In a text field on a web application, you discover that by entering a semicolon and the *nix command `id`, you can find the username context for the application on the server. What is this an example of?
A. Brute force
B. Command injection
C. Session hijacking
D. Replay attack
![]() B is correct. The use of a semicolon and another OS-level command indicates that the application in question is feeding raw input from the user into a command on the local server operating system. As such, this is a clear example of command injection.
B is correct. The use of a semicolon and another OS-level command indicates that the application in question is feeding raw input from the user into a command on the local server operating system. As such, this is a clear example of command injection.
![]() A, C, and D are incorrect. Brute force is incorrect because it is a technique used for password cracking and recovery, rather than a type of attack on a web application. Session hijacking and replay attacks are incorrect because they rely on predictable or easily identifiable session ID tokens to execute, rather than improper user input sanitation.
A, C, and D are incorrect. Brute force is incorrect because it is a technique used for password cracking and recovery, rather than a type of attack on a web application. Session hijacking and replay attacks are incorrect because they rely on predictable or easily identifiable session ID tokens to execute, rather than improper user input sanitation.
39. What is the process of finding all available information on a target system or service in support of developing a plan of attack?
A. Vulnerability mapping
B. Vulnerability scanning
C. Enumeration
D. Fingerprinting
![]() C is correct. Enumeration is the process of finding all available information on a target system or service in support of developing a plan of attack.
C is correct. Enumeration is the process of finding all available information on a target system or service in support of developing a plan of attack.
![]() A, B, and D are incorrect. A is incorrect because vulnerability mapping is the process of detailing identified vulnerabilities and their locations (for example, “Apache web server, version 2.2.14, port 8080”). A vulnerability map does not need to be anything particularly detailed or laid out in a specific format; in fact, nmap output files can often serve adequately in this respect. B is incorrect because vulnerability scanning is the process of inspecting an information system for known security weaknesses. D is incorrect because fingerprinting may be thought of as a component of enumeration, and is the process of determining the names and versions of services running on a system to identify potential methods of attack.
A, B, and D are incorrect. A is incorrect because vulnerability mapping is the process of detailing identified vulnerabilities and their locations (for example, “Apache web server, version 2.2.14, port 8080”). A vulnerability map does not need to be anything particularly detailed or laid out in a specific format; in fact, nmap output files can often serve adequately in this respect. B is incorrect because vulnerability scanning is the process of inspecting an information system for known security weaknesses. D is incorrect because fingerprinting may be thought of as a component of enumeration, and is the process of determining the names and versions of services running on a system to identify potential methods of attack.
40. Which term describes the process of detailing identified security flaws and their locations?
A. Vulnerability mapping
B. Cross-compiling
C. Cross-building
D. Exploit modification
![]() A is correct. Vulnerability mapping is the process of detailing identified vulnerabilities and their locations, whether they are physical (no cameras or guards at a back entrance, for instance) or logical (such as SMBv1 being enabled on a Windows 2008 server).
A is correct. Vulnerability mapping is the process of detailing identified vulnerabilities and their locations, whether they are physical (no cameras or guards at a back entrance, for instance) or logical (such as SMBv1 being enabled on a Windows 2008 server).
![]() B, C, and D are incorrect. B is incorrect because cross-compiling is the creation of an executable for one operating system or platform from within another, different operating system or platform. This is done with special compilers such as MinGW-w64 when a Windows .exe file is compiled from within Kali Linux, for instance. C is incorrect because “cross-building” is a red herring term that has no real meaning in the context of computer science, but sounds close enough to throw off certification candidates; be wary of such answers on the exam! D is incorrect because exploit modification is the process of tweaking a known, public exploit to render it usable or perhaps more suitable for a given use during a penetration test.
B, C, and D are incorrect. B is incorrect because cross-compiling is the creation of an executable for one operating system or platform from within another, different operating system or platform. This is done with special compilers such as MinGW-w64 when a Windows .exe file is compiled from within Kali Linux, for instance. C is incorrect because “cross-building” is a red herring term that has no real meaning in the context of computer science, but sounds close enough to throw off certification candidates; be wary of such answers on the exam! D is incorrect because exploit modification is the process of tweaking a known, public exploit to render it usable or perhaps more suitable for a given use during a penetration test.
41. Which act describes the writing of a first-of-its-kind exploit to demonstrate or weaponize a vulnerability?
A. Exploit modification
B. Cross-compiling
C. Proof-of-concept development
D. Threat hunting
![]() C is correct. Proof-of-concept development is the process by which first-in-kind exploits are written to demonstrate or weaponize a vulnerability.
C is correct. Proof-of-concept development is the process by which first-in-kind exploits are written to demonstrate or weaponize a vulnerability.
![]() A, B, and D are incorrect. A is incorrect because exploit modification is the process of tweaking a known, public exploit to render it usable or perhaps more suitable for a given use during a penetration test. B is incorrect because cross-compiling is the creation of an executable for one operating system or platform from within another, different operating system or platform. D is incorrect because threat hunting is the process by which a security team identifies and contains an active threat actor who is capable of evading existing security measures in a system, network, or environment.
A, B, and D are incorrect. A is incorrect because exploit modification is the process of tweaking a known, public exploit to render it usable or perhaps more suitable for a given use during a penetration test. B is incorrect because cross-compiling is the creation of an executable for one operating system or platform from within another, different operating system or platform. D is incorrect because threat hunting is the process by which a security team identifies and contains an active threat actor who is capable of evading existing security measures in a system, network, or environment.
42. Which of the following is not a result of appropriately prioritizing activities in preparation for a penetration test?
A. Time required for individual activities is decreased, and return on time invested is increased.
B. “Low-hanging fruit” is identified and focused on faster.
C. A plan of attack with a greater chance of success can be developed faster.
D. None of these; all options present are effects of activity prioritization in preparation for and during a penetration test.
![]() D is correct.
D is correct.
![]() A, B, and C are incorrect because all options listed are positive impacts borne by appropriate prioritization of activities in preparation for a penetration test.
A, B, and C are incorrect because all options listed are positive impacts borne by appropriate prioritization of activities in preparation for a penetration test.
43. The tool shown in the following illustration is a free and open-source password cracker available for Linux, Windows, and macOS that leverages system CPUs or GPUs. This sample output shows the results of cracking a list of hashes using a wordlist.
A. Hashcat
B. John the Ripper
C. Cain and Abel
D. Hydra
![]() A is correct. The screenshot shows output that is typical of Hashcat. One of the key indicators in this image is the reference to the NVIDIA GeForce GTX 1070, a GPU that can greatly accelerate the cracking process over the use of CPU cycles.
A is correct. The screenshot shows output that is typical of Hashcat. One of the key indicators in this image is the reference to the NVIDIA GeForce GTX 1070, a GPU that can greatly accelerate the cracking process over the use of CPU cycles.
![]() B, C, and D are incorrect. B is incorrect because while John the Ripper is also a command-line tool, it does not leverage GPUs in its execution as does the tool shown in the screenshot. C is incorrect because Cain and Abel is a password recovery tool for Windows that operates in a graphical interface; since the image in question is of a command-line interface, you may safely eliminate C as a potential answer. Cain and Abel is able to recover various manner of passwords via network sniffing, hash cracking, recovery of wireless network keys, and other methods. D is incorrect because Hydra is a parallelized login brute-force tool that can support numerous protocols. Hydra is lightweight, flexible, fast, and modular.
B, C, and D are incorrect. B is incorrect because while John the Ripper is also a command-line tool, it does not leverage GPUs in its execution as does the tool shown in the screenshot. C is incorrect because Cain and Abel is a password recovery tool for Windows that operates in a graphical interface; since the image in question is of a command-line interface, you may safely eliminate C as a potential answer. Cain and Abel is able to recover various manner of passwords via network sniffing, hash cracking, recovery of wireless network keys, and other methods. D is incorrect because Hydra is a parallelized login brute-force tool that can support numerous protocols. Hydra is lightweight, flexible, fast, and modular.
44. Which CAPEC-recognized domain of attack focuses on the manipulation of computer hardware and software within their respective lifecycles?
A. Software
B. Supply Chain
C. Physical Security
D. Communications
![]() B is correct. Manipulation of computer hardware and software during their respective lifecycles is descriptive of CAPEC’s Supply Chain domain.
B is correct. Manipulation of computer hardware and software during their respective lifecycles is descriptive of CAPEC’s Supply Chain domain.
![]() A, C, and D are incorrect. A is incorrect because the software domain focuses on the exploitation of software applications. C is incorrect because the Physical Security domain focuses on exploitation of weaknesses in physical security. D is incorrect because the Communications domain focuses on attacking communications between computer systems and the protocols used to make that communication possible.
A, C, and D are incorrect. A is incorrect because the software domain focuses on the exploitation of software applications. C is incorrect because the Physical Security domain focuses on exploitation of weaknesses in physical security. D is incorrect because the Communications domain focuses on attacking communications between computer systems and the protocols used to make that communication possible.
45. Which knowledge base maintained by MITRE details techniques and adversarial behavior that can be used to attack organizations?
A. CWE
B. CVE
C. CAPEC
D. ATT&CK
![]() D is correct. The ATT&CK knowledge base (https://attack.mitre.org) details techniques and adversarial behavior that can be used to attack organizations.
D is correct. The ATT&CK knowledge base (https://attack.mitre.org) details techniques and adversarial behavior that can be used to attack organizations.
![]() A, B, and C are incorrect. A is incorrect because the Common Weakness Enumeration, or CWE (https://cwe.mitre.org), is a community-developed list of common software security weaknesses. B is incorrect because the Common Vulnerabilities and Exposures, or CVE (https://cve.mitre.org), is a list of entries for publicly known cybersecurity vulnerabilities. C is incorrect because the Common Attack Pattern Enumeration and Classification, or CAPEC (https://capec.mitre.org), is a dictionary that serves to help classify various types of attacks so that they can be better understood by analysts, developers, testers, and educators. It is worth noting, however, that all these resources are managed by MITRE.
A, B, and C are incorrect. A is incorrect because the Common Weakness Enumeration, or CWE (https://cwe.mitre.org), is a community-developed list of common software security weaknesses. B is incorrect because the Common Vulnerabilities and Exposures, or CVE (https://cve.mitre.org), is a list of entries for publicly known cybersecurity vulnerabilities. C is incorrect because the Common Attack Pattern Enumeration and Classification, or CAPEC (https://capec.mitre.org), is a dictionary that serves to help classify various types of attacks so that they can be better understood by analysts, developers, testers, and educators. It is worth noting, however, that all these resources are managed by MITRE.
46. Which of the following is not a vulnerability scanner commonly used in penetration testing?
A. Nessus
B. OpenVAS
C. SQLmap
D. IDA
![]() D is correct. IDA—or the Interactive Disassembler—is a disassembly tool that can generate assembly language source code for an application or executable from the executable directly, and is not a vulnerability scanning tool.
D is correct. IDA—or the Interactive Disassembler—is a disassembly tool that can generate assembly language source code for an application or executable from the executable directly, and is not a vulnerability scanning tool.
![]() A, B, and C are incorrect. Nessus and OpenVAS are web-based vulnerability scanners that can detect and alert on seemingly countless potential vulnerabilities on target systems. SQLmap is a single-purpose vulnerability scanner, serving to detect and exploit database vulnerabilities, thereby automating the process of exploiting SQL injection flaws and the taking over of database servers.
A, B, and C are incorrect. Nessus and OpenVAS are web-based vulnerability scanners that can detect and alert on seemingly countless potential vulnerabilities on target systems. SQLmap is a single-purpose vulnerability scanner, serving to detect and exploit database vulnerabilities, thereby automating the process of exploiting SQL injection flaws and the taking over of database servers.
47. In addition to serving as a method of policy compliance evaluation, __________ is a method for using specific standards for automated discovery and measurement of vulnerabilities.
A. HIPAA
B. FISMA
C. SCAP
D. PCI DSS
![]() C is correct. SCAP—or the Security Content Automation Protocol—is a method for using specific standards for automated discovery and the measurement of vulnerabilities, as well as policy compliance evaluation.
C is correct. SCAP—or the Security Content Automation Protocol—is a method for using specific standards for automated discovery and the measurement of vulnerabilities, as well as policy compliance evaluation.
![]() A, B, and D are incorrect. These are all examples of regulatory frameworks used to help in the design of SCAP guidelines.
A, B, and D are incorrect. These are all examples of regulatory frameworks used to help in the design of SCAP guidelines.
