1.3. Comprehending the Security Process
It helps to think of security as a combination of three Ps: processes, procedures, and policies. The security of information involves both human and technical factors. The human factors are addressed by the policies that are enforced in the organization as well as the processes and procedures your organization has in place. The technology components include the tools you install on the systems you work with. There are several parts to this process, and each is described in the following sections.
1.3.1. Appreciating Antivirus Software
Computer viruses—applications that carry out malicious actions—are among the most annoying trends happening today. It seems that almost every day someone invents a new virus. Some of these viruses do nothing more than give you a big "gotcha." Others contaminate networks and wreak havoc on computer systems. A virus may act on your data or your operating system, but it's intent on doing harm—and doing so without your consent. Viruses often include replication as a primary objective and try to infect as many machines as they can, as quickly as possible.
The business of providing software to computer users to protect them from viruses has become a huge industry. Several very good and well-established suppliers of antivirus software exist, and new virus-protection methods come on the scene almost as fast as new viruses. Antivirus software scans a computer's memory, disk files, and incoming and outgoing e-mail. The software typically uses a virus definition file that is updated regularly by the manufacturer. If these files are kept up-to-date, the computer system will be relatively secure. Unfortunately, most people don't keep their virus definition files up-to-date. Users will exclaim that a new virus has come out, because they just got it. Upon examination, you'll often discover that their virus definition file is months out-of-date. As you can see, the software part of the system will break down if the definition files aren't updated on a regular basis.
1.3.2. Implementing Access Control
The process of implementing access control is critical. Access control defines how users and systems communicate and in what manner. In other words, it limits—or controls—access to system resources, including data, and thus protects information from unauthorized access. Three basic models are used to explain access control.
1.3.2.1. The Mandatory Access Control Method
The Mandatory Access Control (MAC) model is a static model that uses a predefined set of access privileges for files on the system. The system administrators establish these parameters and associate them with an account, files, or resources.
The MAC model can be very restrictive. In a MAC model, administrators establish access. Users can't share resources dynamically unless the static relationship already exists.
NOTE
The acronym MAC appears in numerous computer-related contexts. One of the most common uses is to represent the Media Access layer in networking. Be careful not to confuse MAC addressing as it relates to network cards with Mandatory Access Control.
MAC uses labels to identify the level of sensitivity that applies to objects. When a user attempts to access an object, the label is examined to see if the access should take place or be denied. One key element to remember is that when mandatory control is applied, labels are required and must exist for every object.
1.3.2.2. The Discretionary Access Control Method
The Discretionary Access Control (DAC) model allows the owner of a resource to establish privileges to the information they own. The difference between DAC and MAC is that labels are not mandatory but can be applied as needed.
The DAC model allows a user to share a file or use a file that someone else has shared. It establishes an access control list (ACL) that identifies the users who have authorization to access that information. This allows the owner to grant or revoke access to individuals or groups of individuals based on the situation. This model is dynamic in nature and allows information to be shared easily between users.
1.3.2.3. The Role-Based Access Control Method
The Role-Based Access Control (RBAC) model allows a user to act in a certain predetermined manner based on the role the user holds in the organization. The roles almost always shadow the organizational structure.
Users can be assigned roles systemwide and can then perform certain functions or duties based on the roles they're assigned. An example might be a role called salesperson. The user assigned the salesperson role can access only the information established for that role. Users may be able to access this information from any station in the network, based strictly on their role. A sales manager may have a different role that allows access to all of the individual salespersons' information.
The RBAC model is common in network administrative roles.
1.3.3. Understanding Authentication
Authentication proves that a user or system is actually who they say they are. This is one of the most critical parts of a security system. It's part of a process that is also referred to as identification and authentication (I&A). The identification process starts when a user ID or logon name is typed into a sign-on screen. Authentication is accomplished by challenging the claim about who is accessing the resource. Without authentication, anybody can claim to be anybody.
Authentication systems or methods are based on one or more of these three factors:
Something you know, such as a password or PIN
Something you have, such as a smart card or an identification device
Something physically unique to you, such as your fingerprints or retinal pattern
Systems authenticate each other using similar methods. Frequently, systems pass private information between each other to establish identity. Once authentication has occurred, the two systems can communicate in the manner specified in the design.
Several common methods are used for authentication. Each offers something to security and should be considered when you're evaluating authentication schemes or methods.
1.3.3.1. Biometrics
Biometric readers use physical characteristics to identify the user. Such devices are becoming more common in the business environment. Biometric readers include hand scanners, retinal scanners, and soon, possibly, DNA scanners. To gain access to resources, you must pass a physical screening process. In the case of a hand scanner, the screening may include fingerprints, scars, and markings on your hand. Retinal scanners compare your eye's retinal pattern to a stored retinal pattern to verify your identity. DNA scanners will examine a unique portion of your DNA structure to verify that you are who you say you are.
1.3.3.2. Certificates
Certificates are another common form of authentication. A server or certificate authority (CA) can issue a certificate that will be accepted by the challenging system. Certificates can be either physical access devices, such as smart cards, or electronic certificates that are used as part of the logon process. A Certificate Practice Statement (CPS) outlines the rules used for issuing and managing certificates. A Certificate Revocation List (CRL) lists the revocations that must be addressed (often due to expiration) in order to stay current.
NOTE
This chapter provides only an overview of certificates. Certificates, along with Public Key Infrastructure (PKI) and related topics, are discussed in detail in Chapter 7, "Cryptography Basics, Methods, and Standards."
A simple way to think of certificates is to think of hall passes at school. Figure 1.3 illustrates a certificate being handed from the server to the client after authentication has been established. If you have a hall pass, you can wander the halls of your school. If your pass is invalid, the hallway monitor can send you to the principal's office. Similarly, if you have a certificate, then you can prove to the system that you are who you say you are and are authenticated to work with the resources.
Figure 1.3. A certificate being issued after identification has been verified

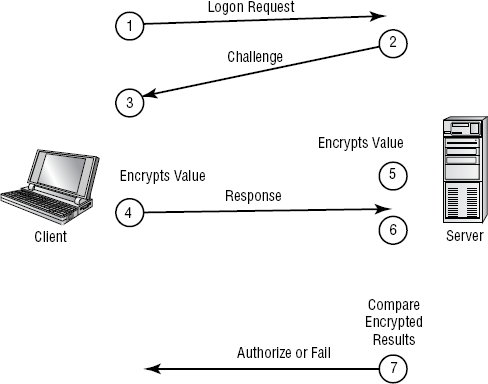
1.3.3.3. Challenge Handshake Authentication Protocol
Challenge Handshake Authentication Protocol (CHAP) challenges a system to verify identity. CHAP doesn't use a user ID/password mechanism. Instead, the initiator sends a logon request from the client to the server. The server sends a challenge back to the client. The challenge is encrypted and then sent back to the server. The server compares the value from the client and, if the information matches, grants authorization. If the response fails, the session fails, and the request phase starts over. Figure 1.4 illustrates the CHAP procedure. This handshake method involves a number of steps and is usually automatic between systems.
Figure 1.4. CHAP authentication
1.3.3.4. Kerberos
Kerberos is an authentication protocol named after the mythical three-headed dog that stood at the gates of Hades. Originally designed by MIT, Kerberos is becoming very popular as an authentication method. It allows for a single sign-on to a distributed network.
Kerberos authentication uses a Key Distribution Center (KDC) to orchestrate the process. The KDC authenticates the principle (which can be a user, a program, or a system) and provides it with a ticket. After this ticket is issued, it can be used to authenticate against other principles. This occurs automatically when a request or service is performed by another principle.
Kerberos is quickly becoming a common standard in network environments. Its only significant weakness is that the KDC can be a single point of failure. If the KDC goes down, the authentication process will stop. Figure 1.5 shows the Kerberos authentication process and the ticket being presented to systems that are authorized by the KDC.
1.3.3.5. Multi-Factor Authentication
When two or more access methods are included as part of the authentication process, you're implementing a multi-factor system. A system that uses smart cards and passwords is referred to as a two-factor authentication system. Two-factor authentication is shown in Figure 1.6. This example requires both a smart card and a logon password process.
Figure 1.5. Kerberos authentication process

Figure 1.6. Two-factor authentication

1.3.3.6. Mutual Authentication
Whenever two or more parties authenticate each other, this is known as mutual authentication. A client may authenticate to a server, and a server authenticate to a client when there is a need to establish a secure session between the two and employ encryption. Mutual authentication ensures that the client is not unwittingly connecting and giving its credentials to a rogue server; which can then turn around and steal the data from the real server.
Commonly, mutual authentication will be implemented when the data to be sent during the session is of a critical nature—such as financial or medical records.
1.3.3.7. Password Authentication Protocol
Password Authentication Protocol (PAP) offers no true security, but it's one of the simplest forms of authentication. The username and password values are both sent to the server as clear text and checked for a match. If they match, the user is granted access; if they don't match, the user is denied access. In most modern implementations, PAP is shunned in favor of other, more secure authentication methods.
1.3.3.8. Security Tokens
Security tokens are similar to certificates. They contain the rights and access privileges of the token bearer as part of the token. Think of a token as a small piece of data that holds a sliver of information about the user.
Many operating systems generate a token that is applied to every action taken on the computer system. If your token doesn't grant you access to certain information, then either that information won't be displayed or your access will be denied. The authentication system creates a token every time a user connects or a session begins. At the completion of a session, the token is destroyed. Figure 1.7 shows the security token process.
Figure 1.7. Security token authentication

1.3.3.9. Smart Cards
A smart card is a type of badge or card that gives you access to resources, including buildings, parking lots, and computers. It contains information about your identity and access privileges. Each area or computer has a card scanner or a reader in which you insert your card. Smart Cards often also require the use of a small password called a PIN (personal identification number); which further secures the smart card if lost by the true card holder, so that it cannot be used by someone else to gain access to data and resources.
Figure 1.8 depicts a user inserting a smart card into a reader to verify identity. The reader is connected to the workstation and validates against the security system. This increases the security of the authentication process because you must be in physical possession of the smart card to use the resources. Of course, if the card is lost or stolen, the person who finds the card can access the resources allowed by the smart card.
Figure 1.8. The smart card authentication process

1.3.3.10. Username/Password
A username and password are unique identifiers for a logon process. When users sit down in front of a computer system, the first thing a security system requires is that they establish who they are. Identification is typically confirmed through a logon process. Most operating systems use a user ID and password to accomplish this. These values can be sent across the connection as plain text or can be encrypted.
The logon process identifies to the operating system, and possibly the network, that you are who you say you are. Figure 1.9 illustrates this logon and password process. Notice that the operating system compares this information to the stored information from the security processor and either accepts or denies the logon attempt. The operating system might establish privileges or permissions based on stored data about that particular ID.
Figure 1.9. A logon process occurring on a workstation

